如果网关是在核心设备上面,还能用MAC地址进行控制吗?
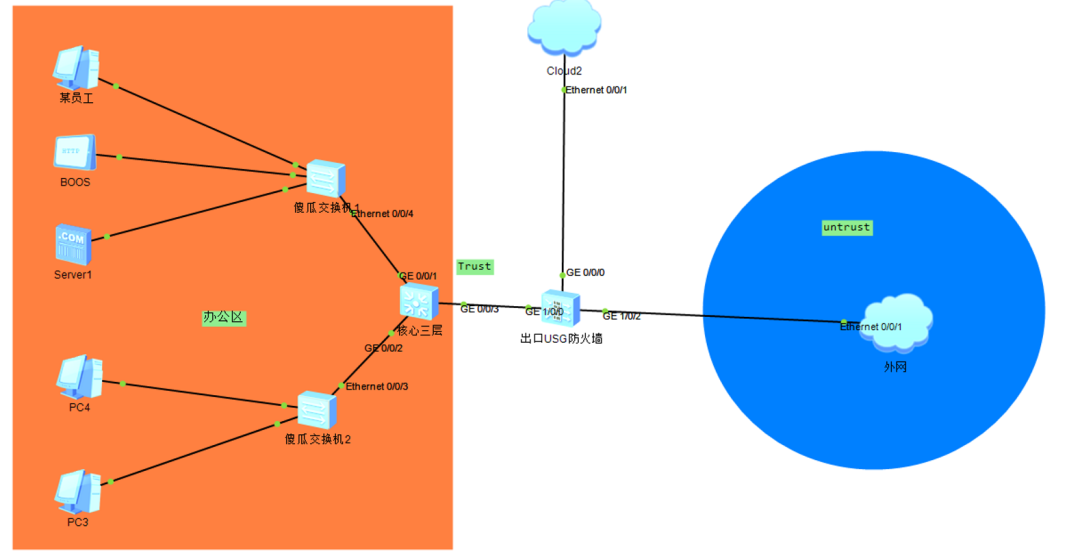
办公区域的网段都在三层上面,防火墙还能基于MAC来控制吗?
采用正常配置模式的步骤与思路
(1)配置思路与上面一样
(2)与上面区别的地方在于网关都配置在三层交换机上面,三层需要与防火墙有一个对接
(3)三层需要划分VLAN以及写默认路由,防火墙需要写回程路由
当这些配置完成后,测试你会发现基于MAC控制的安全策略会失效!!,这是因为数据包在经过一个三层设备的时候,该数据包的源MAC会变成该三层设备出接口的MAC地址,这是IP通信基础转发的原理。

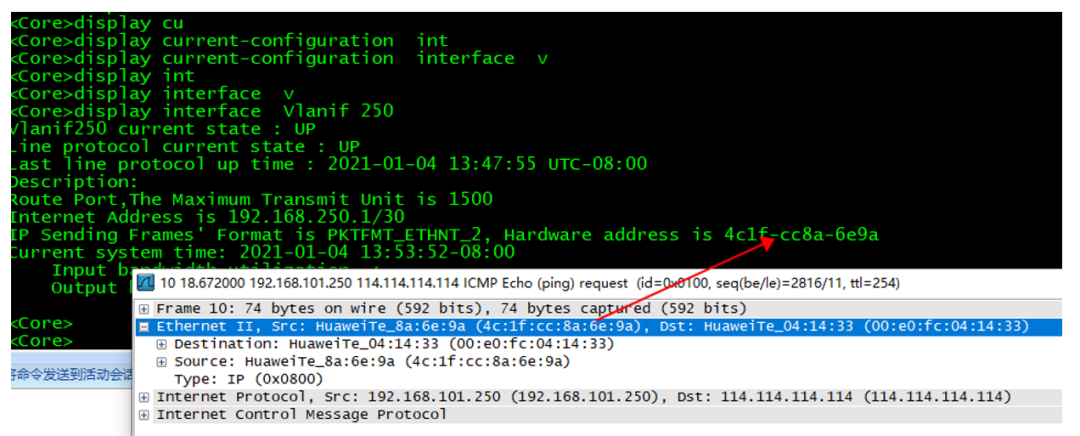
(4)配置跨三层MAC识别,让防火墙从交换机获取正确的ARP表项(注意三层需要开启SNMP功能,防火墙需要制定三层的地址与正确的团体名),注意放行防火墙local_any的流量,否则同步不成功。
三层交换机配置展示
#dhcp enable#vlan batch 101 to 102 250##interface Vlanif101ip address 192.168.101.254 255.255.255.0dhcp select interfacedhcp server dns-list 223.5.5.5 114.114.114.114#interface Vlanif102ip address 192.168.102.254 255.255.255.0dhcp select interfacedhcp server dns-list 223.5.5.5 114.114.114.114#interface Vlanif250ip address 192.168.250.1 255.255.255.252#interfaceGigabitEthernet0/0/1port link-type accessport default vlan 101#interfaceGigabitEthernet0/0/2port link-type accessport default vlan 102#interfaceGigabitEthernet0/0/3port link-type accessport default vlan 250#ip route-static 0.0.0.0 0.0.0.0 192.168.250.2#snmp-agentsnmp-agent communityread ccieh3c.comsnmp-agent sys-infoversion v2c v3防火墙配置展示#interfaceGigabitEthernet1/0/0undo shutdownip address 192.168.250.2 255.255.255.252service-manage http permitservice-manage https permitservice-manage ping permitservice-manage ssh permit#interfaceGigabitEthernet1/0/2undo shutdownip address dhcp-alloc#firewall zone trustset priority 85add interface GigabitEthernet0/0/0add interface GigabitEthernet1/0/0add interface GigabitEthernet1/0/1#firewall zone untrustset priority 5add interface GigabitEthernet1/0/2##ip address-set 不允许上网type objectaddress 0 192.168.102.250 mask 32#ip address-set 102允许上网type objectaddress 0 192.168.102.0 mask 24#ip address-setBOSS_server type objectaddress 0 5489-9864-0d2caddress 1 192.168.101.249 mask 32#ip address-set 101网段type objectaddress 0 192.168.101.0 mask 24#time-range 休息时间period-range 12:00:00 to 13:30:00 working-day#security-policyrule name PC4_deny_internetsource-zone trustdestination-zone untrustsource-address address-set 不允许上网action denyrule name 允许102其他上网source-zone trustdestination-zone untrustsource-address address-set 102允许上网action permitrule name Local_anysource-zone localaction permitrule name BOSSsource-zone trustdestination-zone untrustsource-address address-set BOSS_serveraction permitrule name 休息时间允许上网source-zone trustdestination-zone untrustsource-address address-set 101网段time-range 休息时间action permit#nat-policyrule name 允许上网source-zone trustdestination-zone untrustaction source-nat easy-ip#ip route-static192.168.101.0 255.255.255.0 192.168.250.1ip route-static192.168.102.0 255.255.255.0 192.168.250.1#snmp-server arp-sync enablesnmp-server target-host arp-sync address 192.168.250.1community ccieh3c.com
容易忽略的点
(1)三层交换机需要支持标准的SNMP功能(现在主流都支持),配置团体名跟版本
(2)防火墙开启跨三层MAC识别功能,指定核心交换机的地址与团体名(这里地址跟团体名不要错误,否则会获取失败)
(3)容易忘记三层写默认路由,防火墙忘记写回程路由,导致上不了网
(4)防火墙一定要放行Local到Trust(以实际拓扑为准,防火墙对接三层交换机接口所在的区域),如果不放行,防火墙的流量是发送不出去,导致失败。