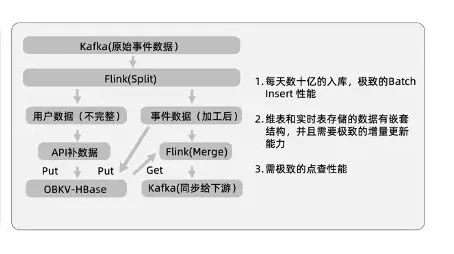
keepalived可用来解决haproxy挂掉后集群无法使用的问题
一.高可用集群
1.1 集群类型
·LB:Load Balance 负载均衡 (lvs和haproxy解决的)
LVS/HAProxy/nginx(http/upstream, stream/upstream)
·HA:High Availability 高可用集群
数据库、Redis
·SPoF: Single Point of Failure,解决单点故障
HPC:High Performance Computing 高性能集群 (解决单个主机运算能力达不到要求)
1.2 系统可用性
SLA:Service-Level Agreement 服务等级协议(提供服务的企业与客户之间就服务的品质、水准、性能
等方面所达成的双方共同认可的协议或契约)
A = MTBF / (MTBF+MTTR)(平均故障间隔/(平均故障间隔+修复前平均时间))
99.95%:(60*24*30)*(1-0.9995)=21.6分钟 #一般按一个月停机时间统计指标 :99.9%, 99.99%, 99.999%,99.9999%
1.3 系统故障
硬件故障:设计缺陷、wear out(损耗)、非人为不可抗拒因素
软件故障:设计缺陷 bug
1.4 实现高可用
提升系统高用性的解决方案:降低MTTR- Mean Time To Repair(平均故障时间)
解决方案:建立冗余机制
·active/passive 主/备
·active/active 双主
·active --> HEARTBEAT(心跳) --> passive (主备)
·active <--> HEARTBEAT <--> active (双主)
双主

1.5.VRRP:Virtual Router Redundancy Protocol (虚拟路由冗余协议)
虚拟路由冗余协议,解决静态网关单点风险
·物理层:路由器、三层交换机
·软件层:keepalived
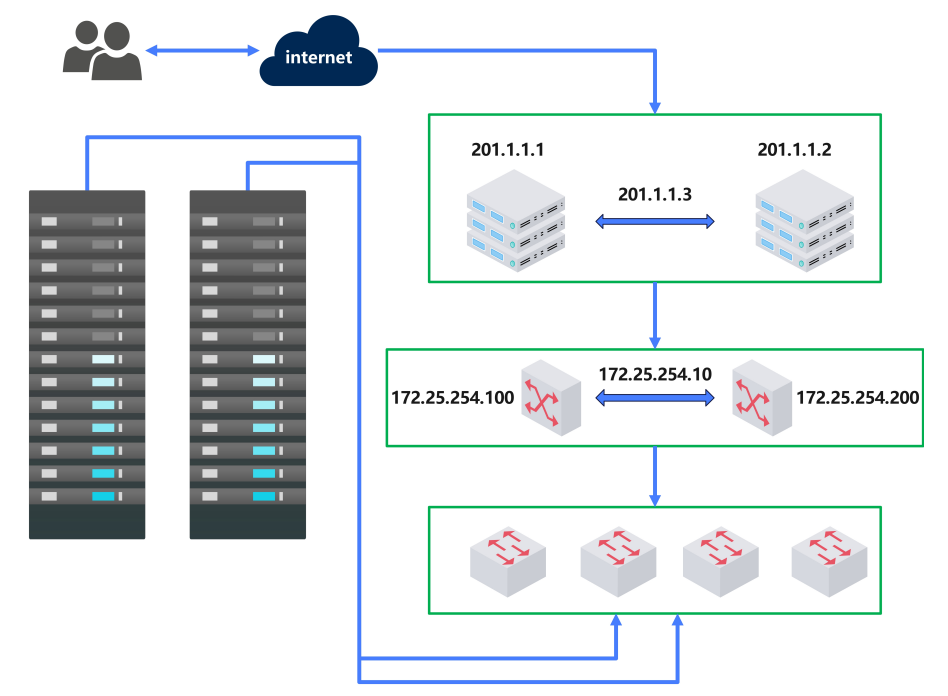
虚拟路由冗余协议:为了让外部人员访问内部网络
如果主机(201.1.1.1)挂了会自动把ip(201.1.1.3)迁移到另一个主机(201.1.1.2)上面
1.5.1 VRRP 相关术语
·虚拟路由器:Virtual Router
·虚拟路由器标识:VRID(0-255),唯一标识虚拟路由器
·VIP:Virtual IP
·VMAC:Virutal MAC (00-00-5e-00-01-VRID)
·物理路由器:
master:主设备
backup:备用设备
priority:优先级 (vip最后会到哪里取决于路由器的优先级)
1.5.2 VRRP 相关技术
通告:心跳,优先级等;周期性
工作方式:抢占式,非抢占式 (抢占模式:如果主机挂了ip已经给了别的主机,当该主机好了之后IP还会回来,非抢占式模式不回来)
安全认证:
·无认证
·简单字符认证:预共享密钥 (明文加密)
·MD5 (对称加密)
工作模式:
·主/备:单虚拟路由器
·主/主:主/备(虚拟路由器1),备/主(虚拟路由器2),(两个主机都有业务,互为主备)(两个主机同时挂的可能性很小)
二.Keepalived 部署

2.1 keepalived 简介
vrrp 协议的软件实现,原生设计目的为了高可用 ipvs服务
官网:http://keepalived.org/

功能:
·基于vrrp协议完成地址流动 (来回迁移)
·为vip地址所在的节点生成ipvs规则(在配置文件中预先定义)
·为ipvs集群的各RS做健康状态检测
·基于脚本调用接口完成脚本中定义的功能,进而影响集群事务,以此支持nginx、haproxy等服务
2.2 Keepalived 架构
官方文档:
https://keepalived.org/doc/
http://keepalived.org/documentation.html
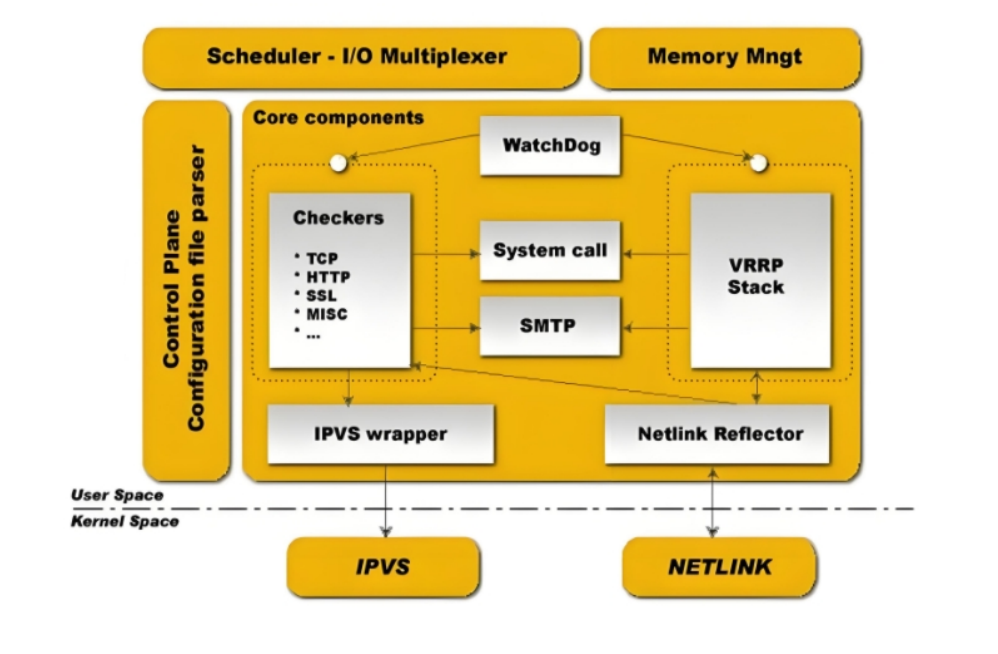
·用户空间核心组件:
vrrp stack:VIP消息通告 (心跳)
checkers:监测real server
system call:实现 vrrp 协议状态转换时调用脚本的功能
SMTP:邮件组件 (主机挂了之后除了迁移vip之外,还需要给管理员发送邮件)
IPVS wrapper:生成IPVS规则
Netlink Reflector:网络接口
WatchDog:监控进程
·控制组件:提供keepalived.conf 的解析器,完成Keepalived配置
·IO复用器:针对网络目的而优化的自己的线程抽象
·内存管理组件:为某些通用的内存管理功能(例如分配,重新分配,发布等)提供访问权限
其中控制组件,IO复用器,内存管理组件不需要控制(自动控制的)
2.3 Keepalived 环境准备


#IP环境搭建
#ka1
[root@ka1 ~]# ip ad
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:73:de:b2 brd ff:ff:ff:ff:ff:ff
inet 172.25.254.10/24 brd 172.25.254.255 scope global noprefixroute eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe73:deb2/64 scope link tentative
valid_lft forever preferred_lft forever
3: virbr0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default qlen 1000
link/ether 52:54:00:f1:ee:92 brd ff:ff:ff:ff:ff:ff
inet 192.168.122.1/24 brd 192.168.122.255 scope global virbr0
valid_lft forever preferred_lft forever
4: virbr0-nic: <BROADCAST,MULTICAST> mtu 1500 qdisc pfifo_fast master virbr0 state DOWN group default qlen 1000
link/ether 52:54:00:f1:ee:92 brd ff:ff:ff:ff:ff:ff
#ka2
[root@ka2 ~]# ip ad
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:c2:71:75 brd ff:ff:ff:ff:ff:ff
inet 172.25.254.20/24 brd 172.25.254.255 scope global noprefixroute eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fec2:7175/64 scope link tentative
valid_lft forever preferred_lft forever
3: virbr0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default qlen 1000
link/ether 52:54:00:f1:ee:92 brd ff:ff:ff:ff:ff:ff
inet 192.168.122.1/24 brd 192.168.122.255 scope global virbr0
valid_lft forever preferred_lft forever
4: virbr0-nic: <BROADCAST,MULTICAST> mtu 1500 qdisc pfifo_fast master virbr0 state DOWN group default qlen 1000
link/ether 52:54:00:f1:ee:92 brd ff:ff:ff:ff:ff:ff
#relserver1
[root@relserver1 ~]# ip ad
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:22:84:f2 brd ff:ff:ff:ff:ff:ff
inet 172.25.254.110/24 brd 172.25.254.255 scope global noprefixroute eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe22:84f2/64 scope link tentative
valid_lft forever preferred_lft forever
3: virbr0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default qlen 1000
link/ether 52:54:00:f1:ee:92 brd ff:ff:ff:ff:ff:ff
inet 192.168.122.1/24 brd 192.168.122.255 scope global virbr0
valid_lft forever preferred_lft forever
4: virbr0-nic: <BROADCAST,MULTICAST> mtu 1500 qdisc pfifo_fast master virbr0 state DOWN group default qlen 1000
link/ether 52:54:00:f1:ee:92 brd ff:ff:ff:ff:ff:ff
#relserver2
[root@relserver2 ~]# ip ad
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:27:bb:85 brd ff:ff:ff:ff:ff:ff
inet 172.25.254.120/24 brd 172.25.254.255 scope global noprefixroute eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe27:bb85/64 scope link tentative
valid_lft forever preferred_lft forever
3: virbr0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default qlen 1000
link/ether 52:54:00:f1:ee:92 brd ff:ff:ff:ff:ff:ff
inet 192.168.122.1/24 brd 192.168.122.255 scope global virbr0
valid_lft forever preferred_lft forever
4: virbr0-nic: <BROADCAST,MULTICAST> mtu 1500 qdisc pfifo_fast master virbr0 state DOWN group default qlen 1000
link/ether 52:54:00:f1:ee:92 brd ff:ff:ff:ff:ff:ff
#安装httpd
[root@relserver1 ~]# yum install httpd -y
[root@relserver1 ~]# echo 172.25.254.110 > /var/www/html/index.html
[root@relserver1 ~]# systemctl enable httpd
[root@relserver1 ~]# systemctl start httpd
[root@relserver1 ~]# systemctl stop firewalld
[root@relserver1 ~]# setenforce 0
setenforce: SELinux is disabled
[root@relserver2 ~]# yum install httpd -y
[root@relserver2 ~]# echo 172.25.254.120 > /var/www/html/index.html
[root@relserver2 ~]# systemctl enable httpd
[root@relserver2 ~]# systemctl start httpd
[root@relserver2 ~]# systemctl stop firewalld
[root@relserver2 ~]# setenforce 0
setenforce: SELinux is disabled#测试
[root@ka1 ~]# curl 172.25.254.110
172.25.254.110
[root@ka1 ~]# curl 172.25.254.120
172.25.254.120·各节点时间必须同步:ntp, chrony
·关闭防火墙及SELinux
·各节点之间可通过主机名互相通信:非必须
·建议使用/etc/hosts文件实现:非必须
·各节点之间的root用户可以基于密钥认证的ssh服务完成互相通信:非必须
2.4 Keepalived 相关文件
·软件包名:keepalived
·主程序文件:/usr/sbin/keepalived
·主配置文件:/etc/keepalived/keepalived.conf
·配置文件示例:/usr/share/doc/keepalived/
·Unit File:/lib/systemd/system/keepalived.service
·Unit File的环境配置文件:/etc/sysconfig/keepalived
RHEL7中可能会遇到一下bug
systemctl restart keepalived #新配置可能无法生效
systemctl stop keepalived;systemctl start keepalived #无法停止进程,需要 kill 停止2.5 Keepalived 安装
安装 keepalived
[root@ka1 ~]# yum install keepalived -y
[root@ka2 ~]# yum install keepalived -y#查看文件
[root@ka1 ~]# rpm -ql keepalived
/etc/keepalived
/etc/keepalived/keepalived.conf
/etc/sysconfig/keepalived
/usr/bin/genhash
/usr/lib/systemd/system/keepalived.service
/usr/libexec/keepalived
/usr/sbin/keepalived
/usr/share/doc/keepalived-1.3.5
/usr/share/doc/keepalived-1.3.5/AUTHOR
/usr/share/doc/keepalived-1.3.5/CONTRIBUTORS
/usr/share/doc/keepalived-1.3.5/COPYING
/usr/share/doc/keepalived-1.3.5/ChangeLog
/usr/share/doc/keepalived-1.3.5/NOTE_vrrp_vmac.txt
/usr/share/doc/keepalived-1.3.5/README
/usr/share/doc/keepalived-1.3.5/TODO
/usr/share/doc/keepalived-1.3.5/keepalived.conf.SYNOPSIS
/usr/share/doc/keepalived-1.3.5/samples
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.HTTP_GET.port
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.IPv6
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.SMTP_CHECK
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.SSL_GET
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.fwmark
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.inhibit
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.misc_check
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.misc_check_arg
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.quorum
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.sample
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.status_code
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.track_interface
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.virtual_server_group
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.virtualhost
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.vrrp
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.vrrp.localcheck
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.vrrp.lvs_syncd
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.vrrp.routes
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.vrrp.rules
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.vrrp.scripts
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.vrrp.static_ipaddress
/usr/share/doc/keepalived-1.3.5/samples/keepalived.conf.vrrp.sync
/usr/share/doc/keepalived-1.3.5/samples/sample.misccheck.smbcheck.sh
/usr/share/man/man1/genhash.1.gz
/usr/share/man/man5/keepalived.conf.5.gz
/usr/share/man/man8/keepalived.8.gz
/usr/share/snmp/mibs/KEEPALIVED-MIB.txt
/usr/share/snmp/mibs/VRRP-MIB.txt
/usr/share/snmp/mibs/VRRPv3-MIB.txt2.6 KeepAlived 配置说明
2.6.1 配置文件组成部分
配置文件:/etc/keepalived/keepalived.conf
配置文件组成
·GLOBAL CONFIGURATION
·Global definitions: 定义邮件配置,route_id,vrrp配置,多播地址等
·VRRP CONFIGURATION
VRRP instance(s): 定义每个vrrp虚拟路由器
·LVS CONFIGURATION
Virtual server group(s)
Virtual server(s): LVS集群的VS和RS
2.6.2 配置语法说明
帮助
man keepalived.conf2.6.2.1 全局配置
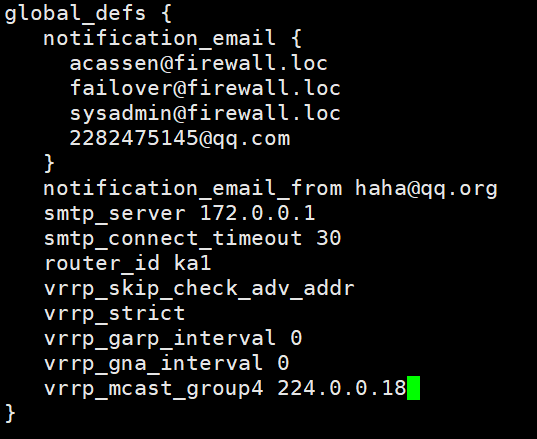
[root@ka1 ~]# vim /etc/keepalived/keepalived.confglobal_defs {
notification_email {
acassen@firewall.loc
failover@firewall.loc
sysadmin@firewall.loc
2282475145@qq.com #发生故障切换时邮件发送的目标邮箱,可以按行区分写多个
}
notification_email_from haha@qq.org #发邮件的地址
smtp_server 172.0.0.1 #邮件服务器地址
smtp_connect_timeout 30 #邮件服务器连接timeout
router_id ka1 #每个keepalived主机唯一标识
#建议使用当前主机名,但多节点
vrrp_skip_check_adv_addr #对所有通告报文都检查,会比较消耗性能
#启用此配置后,如果收到的通告报文和上一个报文是同一 #个路由器,则跳过检查,默认值为全检查
vrrp_strict #严格遵循vrrp协议
#启用此项后以下状况将无法启动服务:
#1.无VIP地址
#2.配置了单播邻居
#3.在VRRP版本2中有IPv6地址
#建议不加此项配置
vrrp_garp_interval 0 #报文发送延迟,0表示不延迟
vrrp_gna_interval 0 #消息发送延迟
vrrp_mcast_group4 224.0.0.18 #指定组播IP地址范围:
}
2.6.2.2 配置虚拟路由器
vrrp_instance VI_1 {
state MASTER
interface eth0 #绑定为当前虚拟路由器使用的物理接口,如:eth0,可以和VIP不在一个网卡
virtual_router_id 51 #每个虚拟路由器惟一标识,范围:0-255,每个虚拟路由器此值必须唯一
#否则服务无法启动
#同属一个虚拟路由器的多个keepalived节点必须相同
#务必要确认在同一网络中此值必须唯一
priority 100 #当前物理节点在此虚拟路由器的优先级,范围:1-254
#值越大优先级越高,每个keepalived主机节点此值不同
advert_int 1 #vrrp通告的时间间隔,默认1s
authentication { #认证机制
auth_type AH|PASS #AH为IPSEC认证(不推荐),PASS为简单密码(建议使用)
auth_pass 1111 #预共享密钥,仅前8位有效
#同一个虚拟路由器的多个keepalived节点必须一样
}
virtual_ipaddress { #虚拟IP,生产环境可能指定上百个IP地址
<IPADDR>/<MASK> brd <IPADDR> dev <STRING> scope <SCOPE> label <LABEL>
172.25.254.100 #指定VIP,不指定网卡,默认为eth0,注意:不指定/prefix,默认32
172.25.254.101/24 dev eth1
172.25.254.102/24 dev eth2 label eth2:1
}
}vrrp_instance VI_1 {
state MASTER
interface eth0
virtual_router_id 100
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 lable eth0:1
}
}

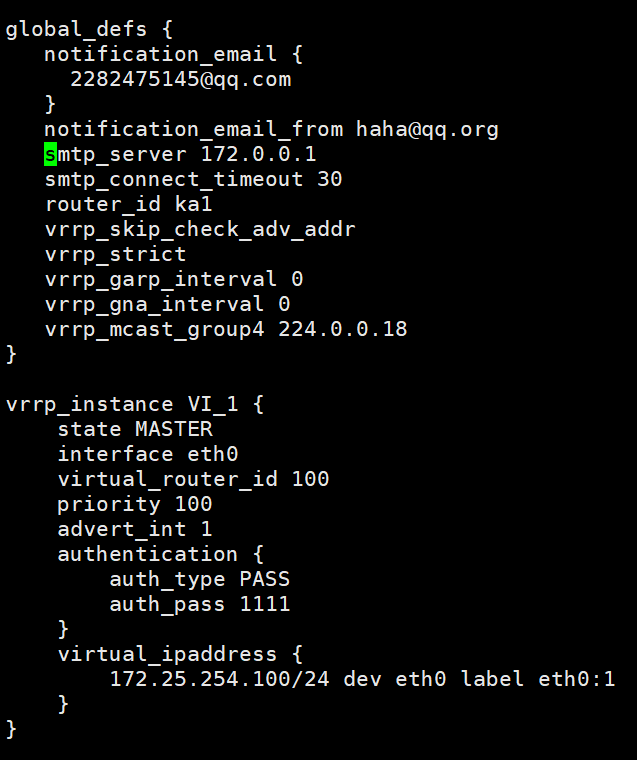
示例
#配置master端,ka1
[root@KA1 ~]# vim /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
2282475145@qq.com
}
notification_email_from haha@qq.org
smtp_server 172.0.0.1
smtp_connect_timeout 30
router_id ka1
vrrp_skip_check_adv_addr
vrrp_strict
vrrp_garp_interval 0
vrrp_gna_interval 0
vrrp_mcast_group4 224.0.0.18
}
vrrp_instance VI_1 {
state MASTER
interface eth0
virtual_router_id 100
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:1
}
}
[root@ka1 ~]# systemctl enable --now keepalived.service
Created symlink from /etc/systemd/system/multi-user.target.wants/keepalived.service to /usr/lib/systemd/system/keepalived.service.
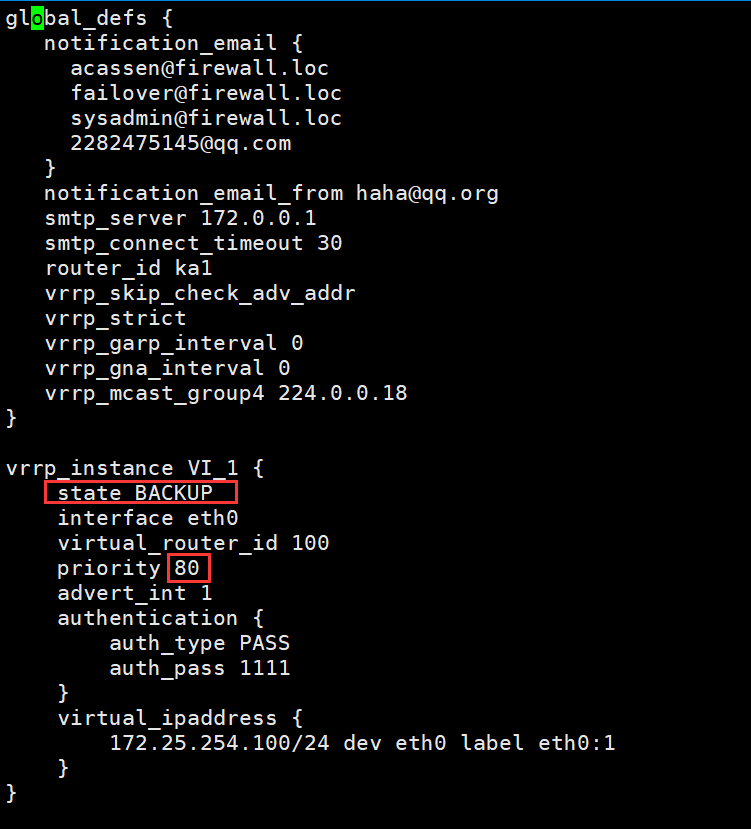
#配置slave端,ka2
[root@KA2 ~]# vim /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
acassen@firewall.loc
failover@firewall.loc
sysadmin@firewall.loc
2282475145@qq.com
}
notification_email_from haha@qq.org
smtp_server 172.0.0.1
smtp_connect_timeout 30
router_id ka1
vrrp_skip_check_adv_addr
vrrp_strict
vrrp_garp_interval 0
vrrp_gna_interval 0
vrrp_mcast_group4 224.0.0.18
}
vrrp_instance VI_1 {
state BACKUP
interface eth0
virtual_router_id 100 #相同id管理同一个虚拟路由
priority 80 #低优先级
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:1
}
}
[root@ka2 ~]# systemctl enable --now keepalived.service
Created symlink from /etc/systemd/system/multi-user.target.wants/keepalived.service to /usr/lib/systemd/system/keepalived.service.
#查看是否成功
[root@ka1 ~]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.10 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::20c:29ff:fe73:deb2 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
RX packets 70754 bytes 7169742 (6.8 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 65410 bytes 5606595 (5.3 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
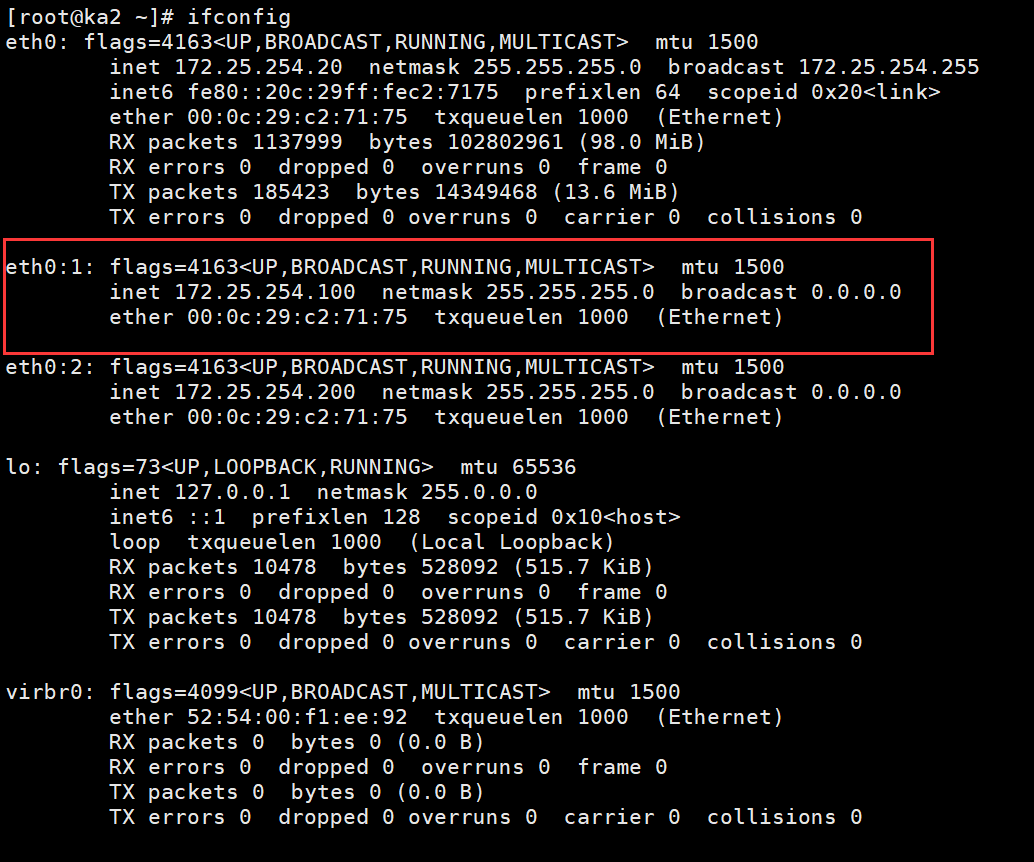
eth0:1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.100 netmask 255.255.255.0 broadcast 0.0.0.0
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 649 bytes 47761 (46.6 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 649 bytes 47761 (46.6 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255
ether 52:54:00:f1:ee:92 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
#测试
[root@ka2 ~]# tcpdump -i eth0 -nn host 224.0.0.18
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
11:15:31.584875 IP 172.25.254.10 > 224.0.0.18: VRRPv2, Advertisement, vrid 100, prio 100, authtype simple, intvl 1s, length 20
11:15:32.585691 IP 172.25.254.10 > 224.0.0.18: VRRPv2, Advertisement, vrid 100, prio 100, authtype simple, intvl 1s, length 20
11:15:33.586961 IP 172.25.254.10 > 224.0.0.18: VRRPv2, Advertisement, vrid 100, prio 100, authtype simple, intvl 1s, length 20
11:15:34.587594 IP 172.25.254.10 > 224.0.0.18: VRRPv2, Advertisement, vrid 100, prio 100, authtype simple, intvl 1s, length 20
#关闭KA1后再看组播信息
[root@ka1 ~]# systemctl stop keepalived.service
[root@ka2 ~]# tcpdump -i eth0 -nn host 224.0.0.18
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
11:15:59.322785 IP 172.25.254.20 > 224.0.0.18: VRRPv2, Advertisement, vrid 100, prio 80, authtype simple, intvl 1s, length 20
11:16:00.323385 IP 172.25.254.20 > 224.0.0.18: VRRPv2, Advertisement, vrid 100, prio 80, authtype simple, intvl 1s, length 20
11:16:01.323864 IP 172.25.254.20 > 224.0.0.18: VRRPv2, Advertisement, vrid 100, prio 80, authtype simple, intvl 1s, length 20
11:16:02.324344 IP 172.25.254.20 > 224.0.0.18: VRRPv2, Advertisement, vrid 100, prio 80, authtype simple, intvl 1s, length 20
抓包测试
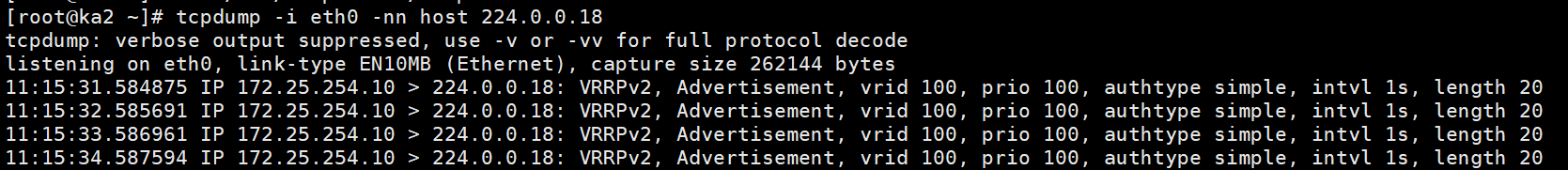
关闭KA1后再看组播信息

2.6.2.3让vip可以通信
通过上述的方法会出现问题:relserver无法访问172.25.254.100
解决方法:
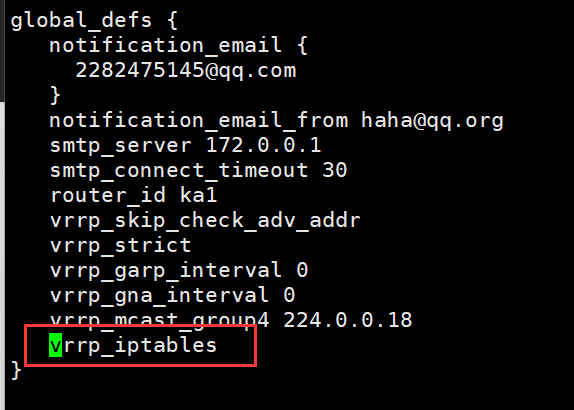
方法1:(添加vrrp_iptable)
[root@ka1 ~]# vim /etc/keepalived/keepalived.conf
global_defs {
notification_email {
2282475145@qq.com
}
notification_email_from haha@qq.org
smtp_server 172.0.0.1
smtp_connect_timeout 30
router_id ka1
vrrp_skip_check_adv_addr
vrrp_strict
vrrp_garp_interval 0
vrrp_gna_interval 0
vrrp_mcast_group4 224.0.0.18
vrrp_iptables #添加
}
[root@ka1 ~]# systemctl restart keepalived.service
[root@ka2 ~]# vim /etc/keepalived/keepalived.conf
global_defs {
notification_email {
acassen@firewall.loc
failover@firewall.loc
sysadmin@firewall.loc
2282475145@qq.com
}
notification_email_from haha@qq.org
smtp_server 172.0.0.1
smtp_connect_timeout 30
router_id ka1
vrrp_skip_check_adv_addr
vrrp_strict
vrrp_garp_interval 0
vrrp_gna_interval 0
vrrp_mcast_group4 224.0.0.18
vrrp_iptables #添加
}
[root@ka2 ~]# systemctl restart keepalived.service
#查看效果:
#原本
[root@relserver1 ~]# ping 172.25.254.100
PING 172.25.254.100 (172.25.254.100) 56(84) bytes of data.
ping: sendmsg: 网络不可达
^C
--- 172.25.254.100 ping statistics ---
5 packets transmitted, 0 received, 100% packet loss, time 4014ms
#现在
[root@relserver1 ~]# ping 172.25.254.100
PING 172.25.254.100 (172.25.254.100) 56(84) bytes of data.
64 bytes from 172.25.254.100: icmp_seq=2 ttl=64 time=5.63 ms
64 bytes from 172.25.254.100: icmp_seq=3 ttl=64 time=0.255 ms
64 bytes from 172.25.254.100: icmp_seq=4 ttl=64 time=0.296 ms
^C
--- 172.25.254.100 ping statistics ---
4 packets transmitted, 3 received, 25% packet loss, time 3012ms
rtt min/avg/max/mdev = 0.255/2.061/5.634/2.526 ms

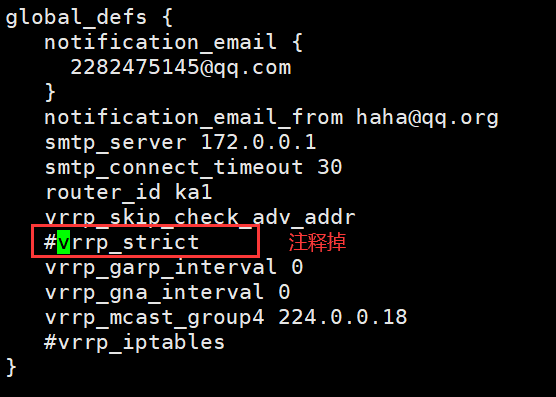
#方法2(注释掉vrrp_strict)
global_defs {
notification_email {
2282475145@qq.com
}
notification_email_from haha@qq.org
smtp_server 172.0.0.1
smtp_connect_timeout 30
router_id ka1
vrrp_skip_check_adv_addr
#vrrp_strict #注释
vrrp_garp_interval 0
vrrp_gna_interval 0
vrrp_mcast_group4 224.0.0.18
#vrrp_iptables
}
[root@ka1 ~]# systemctl restart keepalived.service
[root@relserver1 ~]# ping 172.25.254.100
PING 172.25.254.100 (172.25.254.100) 56(84) bytes of data.
64 bytes from 172.25.254.100: icmp_seq=1 ttl=64 time=62.3 ms
64 bytes from 172.25.254.100: icmp_seq=2 ttl=64 time=0.375 ms
64 bytes from 172.25.254.100: icmp_seq=3 ttl=64 time=0.505 ms
^C
--- 172.25.254.100 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2004ms
rtt min/avg/max/mdev = 0.375/21.083/62.371/29.195 ms

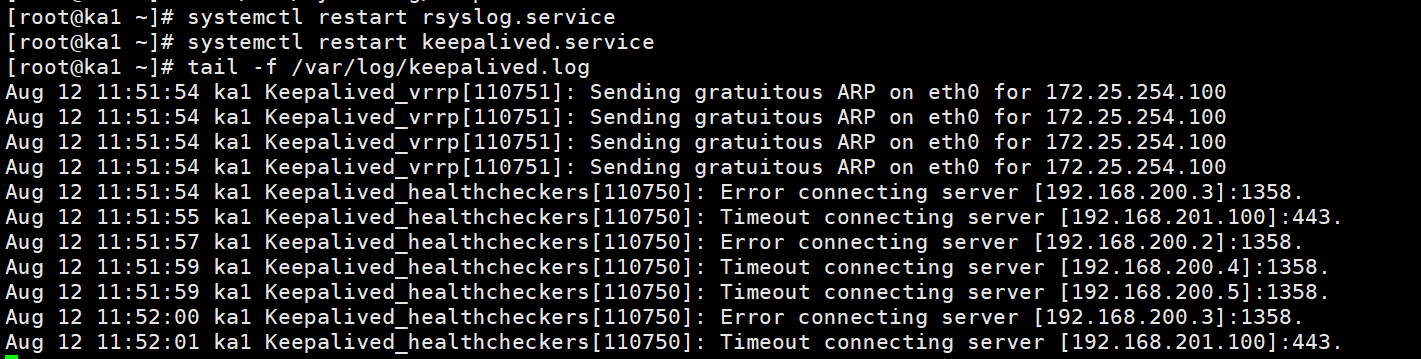
2.6.2.4 启用keepalived日志功能
示例:
#指定日志
[root@KA1 ~]# vim /etc/sysconfig/keepalived
KEEPALIVED_OPTIONS="-D -S 6"
#指定采集方法
[root@ka1 ~]#vim /etc/rsyslog.conf
local6.* /var/log/keepalived.log #前面写的6这个就要写6
#重启服务
[root@ka1 ~]# systemctl restart rsyslog.service
[root@ka1 ~]# systemctl restart keepalived.service
#查看日志
[root@ka1 ~]#tail -f /var/log/keepalived.log
Apr 14 09:25:51 ka1 Keepalived_vrrp[1263]: Sending gratuitous ARP on eth0 for
10.0.0.10
Apr 14 09:25:51 ka1 Keepalived_vrrp[1263]: Sending gratuitous ARP on eth0 for
10.0.0.10
Apr 14 09:25:51 ka1 Keepalived_vrrp[1263]: Sending gratuitous ARP on eth0 for
10.0.0.10
Apr 14 09:25:51 ka1 Keepalived_vrrp[1263]: Sending gratuitous ARP on eth0 for
10.0.0.10
Apr 14 09:25:56 ka1 Keepalived_vrrp[1263]: Sending gratuitous ARP on eth0 for
10.0.0.10
Apr 14 09:25:56 ka1 Keepalived_vrrp[1263]: (VI_1) Sending/queueing gratuitous
ARPs on eth0 for 10.0.0.10
Apr 14 09:25:56 ka1 Keepalived_vrrp[1263]: Sending gratuitous ARP on eth0 for
10.0.0.10
Apr 14 09:25:56 ka1 Keepalived_vrrp[1263]: Sending gratuitous ARP on eth0 for
10.0.0.10
Apr 14 09:25:56 ka1 Keepalived_vrrp[1263]: Sending gratuitous ARP on eth0 for
10.0.0.10
Apr 14 09:25:56 ka1 Keepalived_vrrp[1263]: Sending gratuitous ARP on eth0 for
10.0.0.10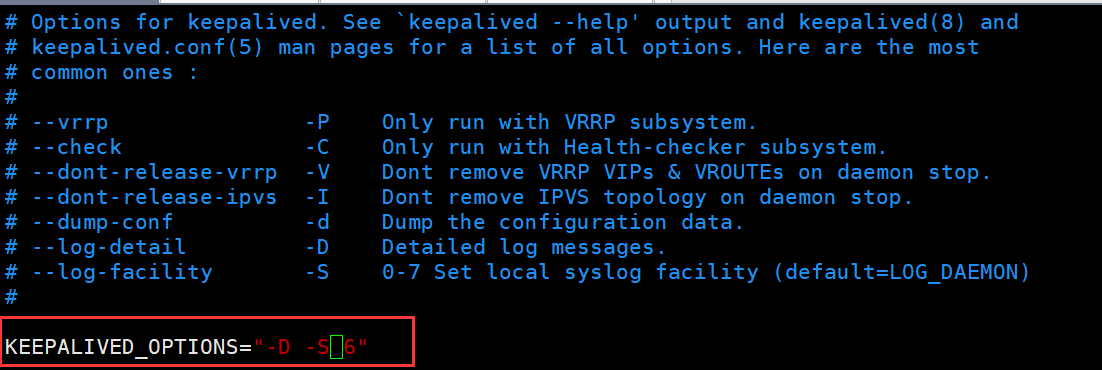

2.6.2.5 实现独立子配置文件
当生产环境复杂时, /etc/keepalived/keepalived.conf 文件中内容过多,不易管理将不同集群的配置,比如:不同集群的VIP配置放在独立的子配置文件中利用include 指令可以实现包含子配置文件
格式:
include /path/file[root@ka1 ~]# vim /etc/keepalived/keepalived.conf
#注释
#vrrp_instance VI_1 {
# state MASTER
# interface eth0
# virtual_router_id 100
# priority 100
# advert_int 1
# authentication {
# auth_type PASS
# auth_pass 1111
# }
# virtual_ipaddress {
# 172.25.254.100/24 dev eth0 label eth0:1
# }
#}
#添加
include "/etc/keepalived/conf.d/*.conf" #子配置文件位置
[root@ka1 ~]# mkdir -p /etc/keepalived/conf.d
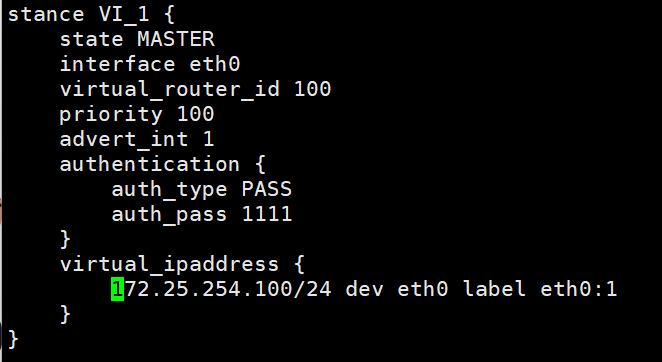
[root@ka1 ~]# vim /etc/keepalived/conf.d/172.25.254.100.conf
stance VI_1 {
state MASTER
interface eth0
virtual_router_id 100
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:1
}
}
[root@ka1 ~]# systemctl restart keepalived.service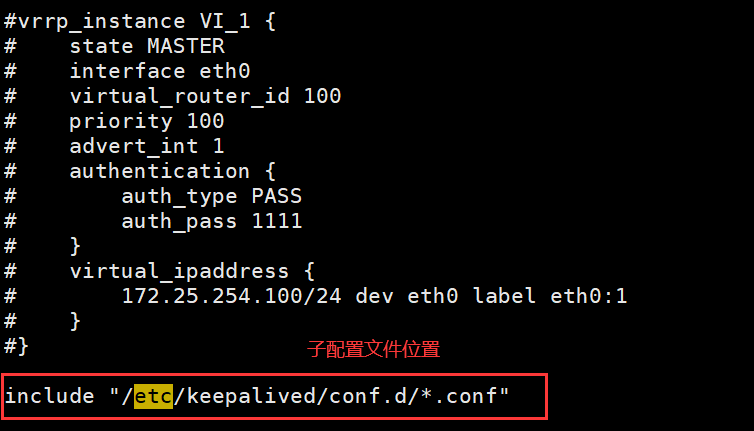
三.Keepalived 企业应用示例
3.1 实现master/slave的 Keepalived 单主架构
配置如下:
#配置master端,ka1
[root@KA1 ~]# vim /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
2282475145@qq.com
}
notification_email_from haha@qq.org
smtp_server 172.0.0.1
smtp_connect_timeout 30
router_id ka1
vrrp_skip_check_adv_addr
#vrrp_strict #添加此选项无法访问vip
vrrp_garp_interval 0
vrrp_gna_interval 0
vrrp_mcast_group4 224.0.0.18
}
vrrp_instance VI_1 {
state MASTER
interface eth0
virtual_router_id 100
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:1
}
}
[root@ka1 ~]# systemctl enable --now keepalived.service
Created symlink from /etc/systemd/system/multi-user.target.wants/keepalived.service to /usr/lib/systemd/system/keepalived.service.
#配置slave端,ka2
[root@KA2 ~]# vim /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
acassen@firewall.loc
failover@firewall.loc
sysadmin@firewall.loc
2282475145@qq.com
}
notification_email_from haha@qq.org
smtp_server 172.0.0.1
smtp_connect_timeout 30
router_id ka1
vrrp_skip_check_adv_addr
#vrrp_strict #添加此选项无法访问vip
vrrp_garp_interval 0
vrrp_gna_interval 0
vrrp_mcast_group4 224.0.0.18
}
vrrp_instance VI_1 {
state BACKUP
interface eth0
virtual_router_id 100 #相同id管理同一个虚拟路由
priority 80 #低优先级
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:1
}
}
[root@ka2 ~]# systemctl enable --now keepalived.service
Created symlink from /etc/systemd/system/multi-user.target.wants/keepalived.service to /usr/lib/systemd/system/keepalived.service.
#查看是否成功
[root@ka1 ~]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.10 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::20c:29ff:fe73:deb2 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
RX packets 70754 bytes 7169742 (6.8 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 65410 bytes 5606595 (5.3 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0:1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.100 netmask 255.255.255.0 broadcast 0.0.0.0
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 649 bytes 47761 (46.6 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 649 bytes 47761 (46.6 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255
ether 52:54:00:f1:ee:92 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
#测试
[root@ka2 ~]# tcpdump -i eth0 -nn host 224.0.0.18
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
11:15:31.584875 IP 172.25.254.10 > 224.0.0.18: VRRPv2, Advertisement, vrid 100, prio 100, authtype simple, intvl 1s, length 20
11:15:32.585691 IP 172.25.254.10 > 224.0.0.18: VRRPv2, Advertisement, vrid 100, prio 100, authtype simple, intvl 1s, length 20
11:15:33.586961 IP 172.25.254.10 > 224.0.0.18: VRRPv2, Advertisement, vrid 100, prio 100, authtype simple, intvl 1s, length 20
11:15:34.587594 IP 172.25.254.10 > 224.0.0.18: VRRPv2, Advertisement, vrid 100, prio 100, authtype simple, intvl 1s, length 20
#关闭KA1后再看组播信息
[root@ka1 ~]# systemctl stop keepalived.service
[root@ka2 ~]# tcpdump -i eth0 -nn host 224.0.0.18
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
11:15:59.322785 IP 172.25.254.20 > 224.0.0.18: VRRPv2, Advertisement, vrid 100, prio 80, authtype simple, intvl 1s, length 20
11:16:00.323385 IP 172.25.254.20 > 224.0.0.18: VRRPv2, Advertisement, vrid 100, prio 80, authtype simple, intvl 1s, length 20
11:16:01.323864 IP 172.25.254.20 > 224.0.0.18: VRRPv2, Advertisement, vrid 100, prio 80, authtype simple, intvl 1s, length 20
11:16:02.324344 IP 172.25.254.20 > 224.0.0.18: VRRPv2, Advertisement, vrid 100, prio 80, authtype simple, intvl 1s, length 20
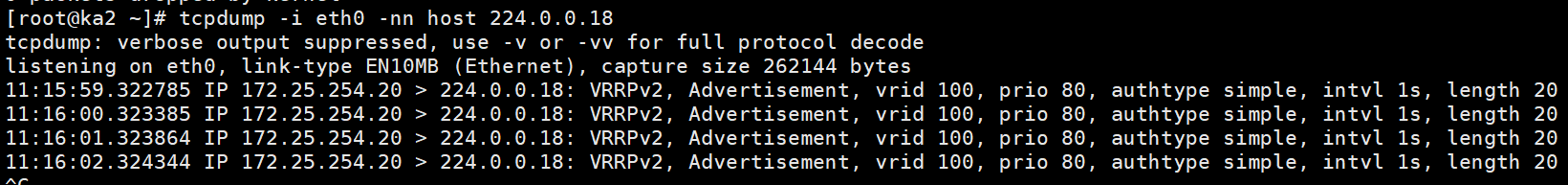
抓包测试
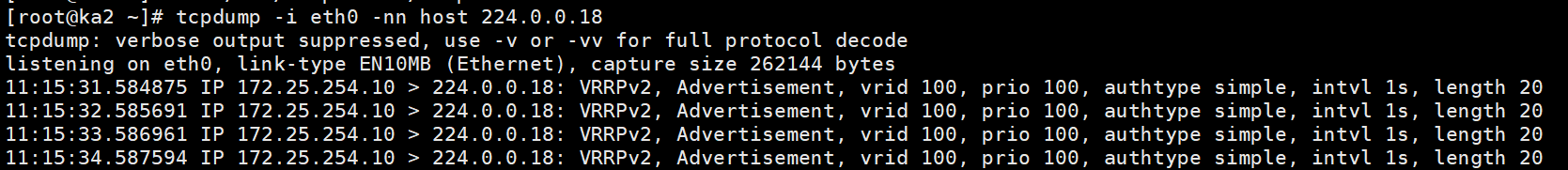
关闭KA1后再看组播信息
3.2 抢占模式和非抢占模式
3.2.1 非抢占模式 nopreempt
默认为抢占模式preempt,即当高优先级的主机恢复在线后,会抢占低先级的主机的master角色,
这样会使vip在KA主机中来回漂移,造成网络抖动,
建议设置为非抢占模式 nopreempt ,即高优先级主机恢复后,并不会抢占低优先级主机的master角色
非抢占模块下,如果原主机down机, VIP迁移至的新主机, 后续也发生down时,仍会将VIP迁移回原主机
注意:要关闭 VIP抢占,必须将各 keepalived 服务器state配置为BACKUP
设置抢占模式具体步骤:
·注释vrrp_strict(#vrrp_strict)
·各个keeppalived为BACKUP(state BACKUP )
·添加nopreempt(nopreempt)
[root@ka1 ~]# vim /etc/keepalived/keepalived.conf
vrrp_instance VI_1 {
state BACKUP #MASTER改为BACKUP
interface eth0
virtual_router_id 100
priority 100
advert_int 1
nopreempt
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:1
}
}
[root@ka2 ~]# vim /etc/keepalived/keepalived.conf
vrrp_instance VI_1 {
state BACKUP
interface eth0
virtual_router_id 100
priority 80
advert_int 1
nopreempt
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:1
}
}
[root@ka2 ~]# systemctl restart keepalived.service
[root@ka1 ~]# systemctl restart keepalived.service
#测试,ka2拿到了vip
[root@ka2 ~]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.20 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::20c:29ff:fec2:7175 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:c2:71:75 txqueuelen 1000 (Ethernet)
RX packets 291571 bytes 29211263 (27.8 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 87070 bytes 6946331 (6.6 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0:1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.100 netmask 255.255.255.0 broadcast 0.0.0.0
ether 00:0c:29:c2:71:75 txqueuelen 1000 (Ethernet)
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 44 bytes 3500 (3.4 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 44 bytes 3500 (3.4 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255
ether 52:54:00:f1:ee:92 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
#测试,ka2拿到vip之后即使ka1的优先级高也无法获得vip
[root@ka1 ~]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.10 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::20c:29ff:fe73:deb2 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
RX packets 292262 bytes 29495280 (28.1 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 73948 bytes 6338605 (6.0 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 649 bytes 47761 (46.6 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 649 bytes 47761 (46.6 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255
ether 52:54:00:f1:ee:92 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
#关闭服务
[root@ka2 ~]# systemctl stop keepalived.service
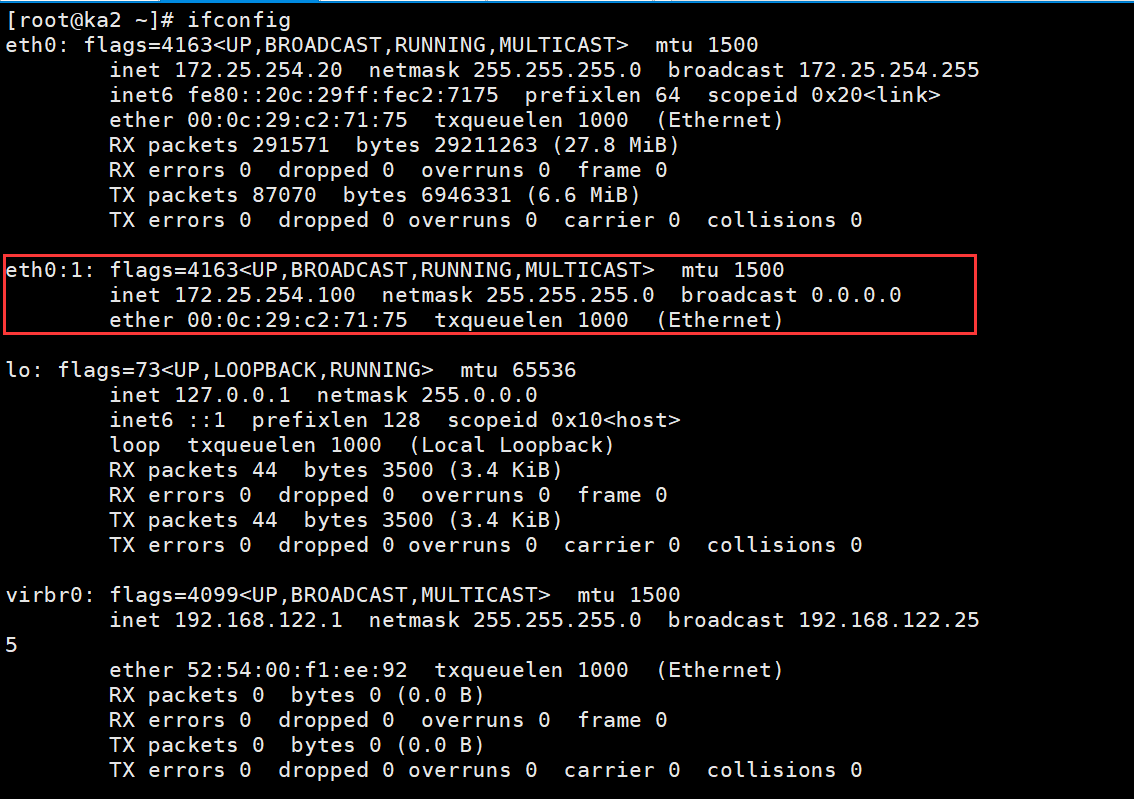
#测试,ka1成功获得vip
[root@ka1 ~]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.10 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::20c:29ff:fe73:deb2 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
RX packets 294689 bytes 29752373 (28.3 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 74153 bytes 6355341 (6.0 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0:1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.100 netmask 255.255.255.0 broadcast 0.0.0.0
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 649 bytes 47761 (46.6 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 649 bytes 47761 (46.6 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255
ether 52:54:00:f1:ee:92 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions

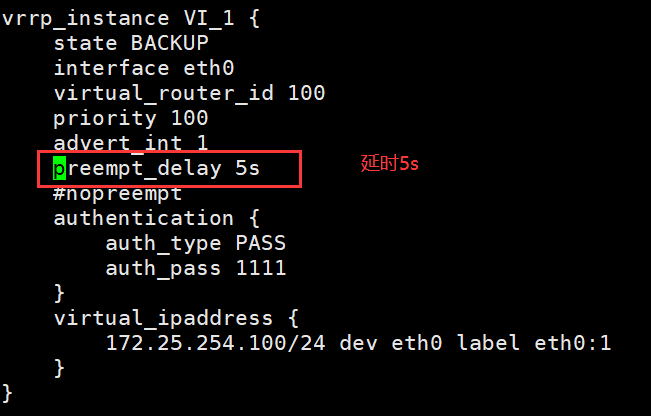
3.2.2 抢占延迟模式 preempt_delay
抢占延迟模式,即优先级高的主机恢复后,不会立即抢回VIP,而是延迟一段时间(默认300s)再抢回VIP
preempt_delay # #指定抢占延迟时间为#s,默认延迟300s注意:需要各keepalived服务器state为BACKUP,并且不要启用 vrrp_strict
设置延迟模式具体步骤(5s为例):
·注释vrrp_strict(#vrrp_strict)
·各个keeppalived为BACKUP(state BACKUP )
·添加preempt_delay 5s(preempt_delay 5s)
配置如下:
#配置文件
[root@ka1 ~]# vim /etc/keepalived/keepalived.conf
global_defs {
notification_email {
2282475145@qq.com
}
notification_email_from haha@qq.org
smtp_server 172.0.0.1
smtp_connect_timeout 30
router_id ka1
vrrp_skip_check_adv_addr
#vrrp_strict #注释掉
vrrp_garp_interval 0
vrrp_gna_interval 0
vrrp_mcast_group4 224.0.0.18
#vrrp_iptables
}
vrrp_instance VI_1 {
state BACKUP #MASTER变成BACKU
interface eth0
virtual_router_id 100
priority 100
advert_int 1
preempt_delay 5s #延时5s,两边都要添加
#nopreempt
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:1
}
}
[root@ka2 ~]# systemctl restart keepalived.service
[root@ka2 ~]# vim /etc/keepalived/keepalived.conf
global_defs {
notification_email {
2282475145@qq.com
}
notification_email_from haha@qq.org
smtp_server 172.0.0.1
smtp_connect_timeout 30
router_id ka1
vrrp_skip_check_adv_addr
#vrrp_strict #注释掉
vrrp_garp_interval 0
vrrp_gna_interval 0
vrrp_mcast_group4 224.0.0.18
#vrrp_iptables
}
vrrp_instance VI_1 {
state BACKUP
interface eth0
virtual_router_id 100
priority 80
advert_int 1
preempt_delay 5s #延时5s,两边都要添加
#nopreempt
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:1
}
}
[root@ka2 ~]# systemctl restart keepalived.service
#测试
[root@ka1 ~]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.10 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::20c:29ff:fe73:deb2 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
RX packets 299714 bytes 30246564 (28.8 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 74899 bytes 6413249 (6.1 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0:1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.100 netmask 255.255.255.0 broadcast 0.0.0.0
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 649 bytes 47761 (46.6 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 649 bytes 47761 (46.6 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255
ether 52:54:00:f1:ee:92 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
#ka1关闭服务
[root@ka1 ~]# systemctl stop keepalived.service
#ka2测试
[root@ka2 ~]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.20 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::20c:29ff:fec2:7175 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:c2:71:75 txqueuelen 1000 (Ethernet)
RX packets 299775 bytes 30060475 (28.6 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 87589 bytes 6994507 (6.6 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0:1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.100 netmask 255.255.255.0 broadcast 0.0.0.0
ether 00:0c:29:c2:71:75 txqueuelen 1000 (Ethernet)
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 44 bytes 3500 (3.4 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 44 bytes 3500 (3.4 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255
ether 52:54:00:f1:ee:92 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
#重启ka1的服务,等5s之后vip又回来了
[root@ka1 ~]# systemctl restart keepalived.service
[root@ka1 ~]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.10 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::20c:29ff:fe73:deb2 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
RX packets 301756 bytes 30457843 (29.0 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 75227 bytes 6444329 (6.1 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0:1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.100 netmask 255.255.255.0 broadcast 0.0.0.0
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 649 bytes 47761 (46.6 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 649 bytes 47761 (46.6 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255
ether 52:54:00:f1:ee:92 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 
ka1
ka2
3.3 VIP单播配置
默认keepalived主机之间利用多播相互通告消息,会造成网络拥塞,可以替换成单播,减少网络流量
注意:启用 vrrp_strict 时,不能启用单播
#在所有节点vrrp_instance语句块中设置对方主机的IP,建议设置为专用于对应心跳线网络的地址,而非使用业务网络
unicast_src_ip <IPADDR> #指定发送单播的源IP
unicast_peer {
<IPADDR> #指定接收单播的对方目标主机IP
......
}
#启用 vrrp_strict 时,不能启用单播,否则服务无法启动,并在messages文件中记录下面信息
Jun 16 17:50:06 centos8 Keepalived_vrrp[23180]: (m44) Strict mode does not
support authentication. Ignoring.
Jun 16 17:50:06 centos8 Keepalived_vrrp[23180]: (m44) Unicast peers are not
supported in strict mode
Jun 16 17:50:06 centos8 Keepalived_vrrp[23180]: Stopped - used 0.000606 user
time, 0.000000 system time
Jun 16 17:50:06 centos8 Keepalived[23179]: Keepalived_vrrp exited with permanent
error CONFIG. Terminating
Jun 16 17:50:06 centos8 systemd[1]: keepalived.service: Succeeded.
Jun 16 17:50:06 centos8 Keepalived[23179]: Stopped Keepalived v2.0.10
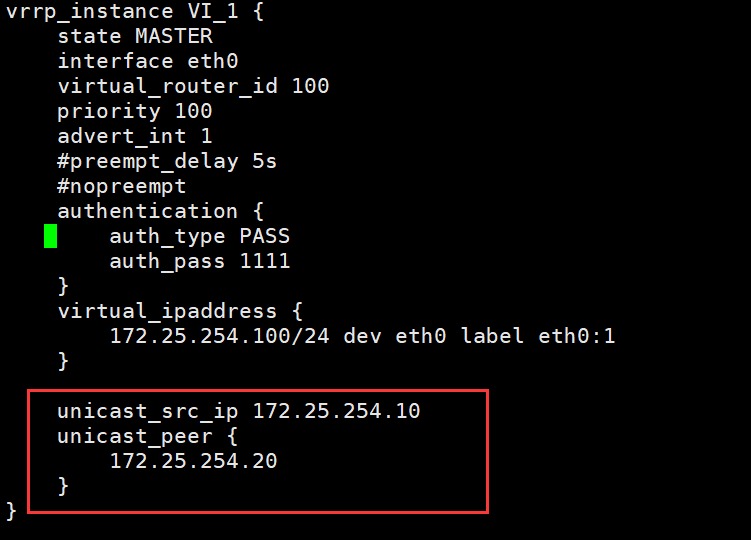
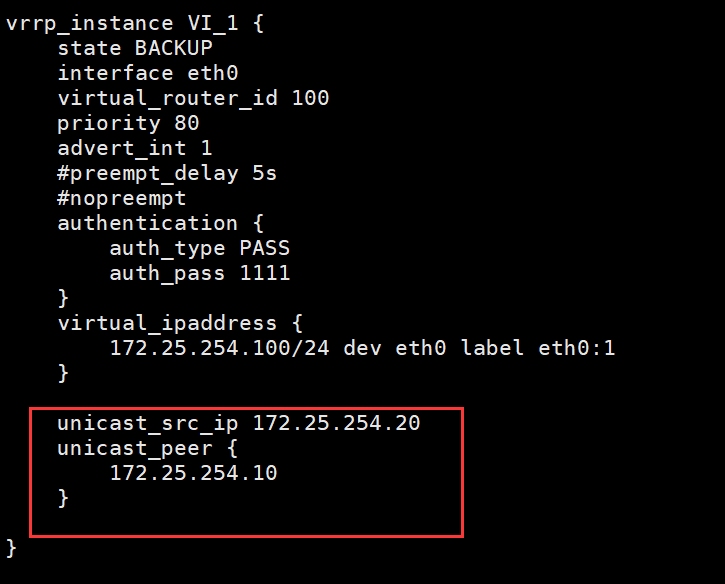
(11/12,2018)vip单播配置具体步骤:
·注释vrrp_strict(#vrrp_strict)
·一个keeppalived为MASTER一个keeppalived为BACKUP(state MASTER,state BACKUP )(都为BACKUP也可以)
·添加(两边都写):
unicast_src_ip 172.25.254.10 #本机IP
unicast_peer {
172.25.254.20 #指向对方主机IP,如果有多个keepalived,再加其它节点的IP
}
配置如下:
[root@ka1 ~]# vim /etc/keepalived/keepalived.conf
global_defs {
notification_email {
2282475145@qq.com
}
notification_email_from haha@qq.org
smtp_server 172.0.0.1
smtp_connect_timeout 30
router_id ka1
vrrp_skip_check_adv_addr
#vrrp_strict #注释此参数,与vip单播模式冲突
vrrp_garp_interval 0
vrrp_gna_interval 0
vrrp_mcast_group4 224.0.0.18
#vrrp_iptables
}
vrrp_instance VI_1 {
state MASTER
interface eth0
virtual_router_id 100
priority 100
advert_int 1
#preempt_delay 5s
#nopreempt
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:1
}
unicast_src_ip 172.25.254.10 #本机IP
unicast_peer {
172.25.254.20 #指向对方主机IP,如果有多个keepalived,再加其它节点的IP
}
}
[root@ka1 ~]# systemctl restart keepalived.service
[root@ka2 ~]# vim /etc/keepalived/keepalived.conf
global_defs {
notification_email {
2282475145@qq.com
}
notification_email_from haha@qq.org
smtp_server 172.0.0.1
smtp_connect_timeout 30
router_id ka1
vrrp_skip_check_adv_addr
#vrrp_strict #注释此参数,与vip单播模式冲突
vrrp_garp_interval 0
vrrp_gna_interval 0
vrrp_mcast_group4 224.0.0.18
#vrrp_iptables
}
vrrp_instance VI_1 {
state BACKUP
interface eth0
virtual_router_id 100
priority 80
advert_int 1
#preempt_delay 5s
#nopreempt
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:1
}
unicast_src_ip 172.25.254.20
unicast_peer {
172.25.254.10
}
}
[root@ka2 ~]# systemctl restart keepalived.service
#抓包查看单播效果,-i指定网卡
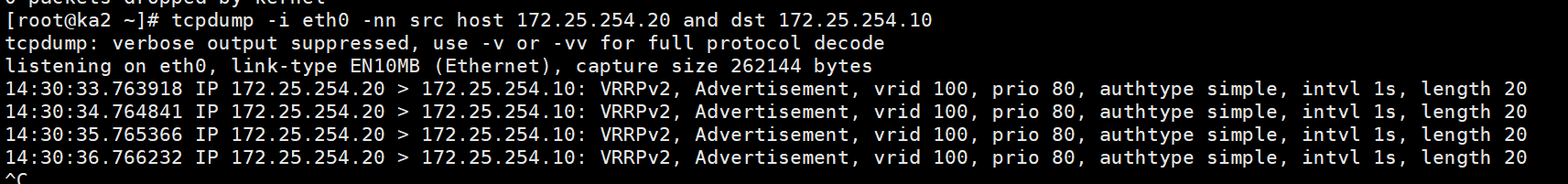
[root@ka1 ~]# tcpdump -i eth0 -nn src host 172.25.254.10 and dst 172.25.254.20
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
14:29:44.867773 IP 172.25.254.10 > 172.25.254.20: VRRPv2, Advertisement, vrid 100, prio 100, authtype simple, intvl 1s, length 20
14:29:45.869259 IP 172.25.254.10 > 172.25.254.20: VRRPv2, Advertisement, vrid 100, prio 100, authtype simple, intvl 1s, length 20
14:29:46.870494 IP 172.25.254.10 > 172.25.254.20: VRRPv2, Advertisement, vrid 100, prio 100, authtype simple, intvl 1s, length 20
14:29:47.871914 IP 172.25.254.10 > 172.25.254.20: VRRPv2, Advertisement, vrid 100, prio 100, authtype simple, intvl 1s, length 20
[root@ka1 ~]# systemctl stop keepalived.service
[root@ka2 ~]# tcpdump -i eth0 -nn src host 172.25.254.20 and dst 172.25.254.10
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
14:30:33.763918 IP 172.25.254.20 > 172.25.254.10: VRRPv2, Advertisement, vrid 100, prio 80, authtype simple, intvl 1s, length 20
14:30:34.764841 IP 172.25.254.20 > 172.25.254.10: VRRPv2, Advertisement, vrid 100, prio 80, authtype simple, intvl 1s, length 20
14:30:35.765366 IP 172.25.254.20 > 172.25.254.10: VRRPv2, Advertisement, vrid 100, prio 80, authtype simple, intvl 1s, length 20
14:30:36.766232 IP 172.25.254.20 > 172.25.254.10: VRRPv2, Advertisement, vrid 100, prio 80, authtype simple, intvl 1s, length 20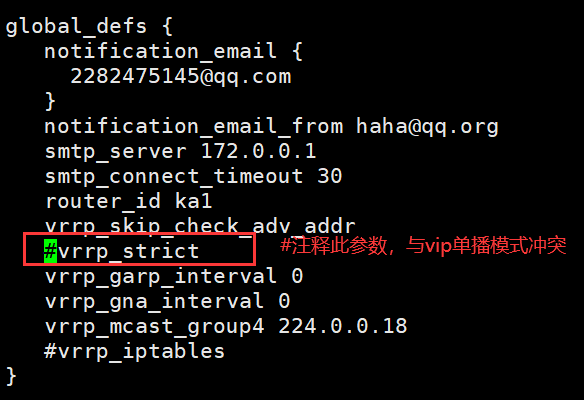

抓包查看单播效果
ka1

ka2
3.4 Keepalived 通知脚本配置
当keepalived的状态变化时,可以自动触发脚本的执行,比如:发邮件通知用户
默认以用户keepalived_script身份执行脚本
如果此用户不存在,以root执行脚本可以用下面指令指定脚本执行用户的身份
global_defs {
......
script_user <USER>
......
}3.4.1 通知脚本类型
当前节点成为主节点时触发的脚本
notify_master <STRING>|<QUOTED-STRING>当前节点转为备节点时触发的脚本
notify_backup <STRING>|<QUOTED-STRING>当前节点转为“失败”状态时触发的脚本
notify_fault <STRING>|<QUOTED-STRING>通用格式的通知触发机制,一个脚本可完成以上三种状态的转换时的通知
notify <STRING>|<QUOTED-STRING>当停止VRRP时触发的脚本
notify_stop <STRING>|<QUOTED-STRING>3.4.2 脚本的调用方法
在 vrrp_instance VI_1 语句块的末尾加下面行
notify_master "/etc/keepalived/notify.sh master"
notify_backup "/etc/keepalived/notify.sh backup"
notify_fault "/etc/keepalived/notify.sh fault"3.4.3 创建通知脚本
[root@ka1 ~]# vim /etc/keepalived/mail.sh
#!/bin/bash
mail_dest='2282475145@qq.com'
mail_message()
{
mail_sub="$HOSTNAME to be $1 vip 转移"
mail_msg="`date +%F\ %T`: vrrp 转移,$HOSTNAME 变为 $1"
echo "$mail_msg" | mail -s "$mail_sub" $mail_dest
}
case $1 in
master)
mail_message master
;;
backup)
mail_message backup
;;
fault)
mail_message fault
;;
*)
exit 1
;;
esac3.4.4 邮件配置
安装邮件发送工具
#下载mail
[root@ka1 ~]# yum install mailx -y
[root@ka2 ~]# yum install mailx -yQQ邮箱配置

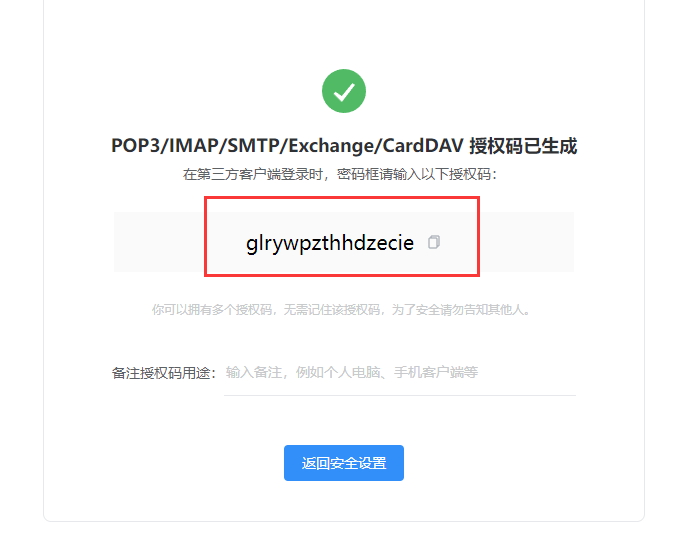
[root@KA1 ~]# vim /etc/mail.rc
#######mail set##########
#在最后添加
set from=2282475145@qq.com
set smtp=smtp.qq.com
set smtp-auth-user=2282475145@qq.com
set smtp-auth-password=glrywpzthhdzecie #授权码
set smtp-auth=login
set ssl-verify=ignore
发送测试邮件
[root@KA1 ~]# echo test message |mail -s test 2282475145@qq.com使用上面的方法后邮箱会收到一封邮件
3.4.5 实战案例:实现 Keepalived 状态切换的通知脚本
[root@ka2 ~]# vim /etc/keepalived/mail.sh
#!/bin/bash
mail_dest='2282475145@qq.com'
mail_message()
{
mail_sub="$HOSTNAME to be $1 vip 转移"
mail_msg="`date +%F\ %T`: vrrp 转移,$HOSTNAME 变为 $1"
echo "$mail_msg" | mail -s "$mail_sub" $mail_dest
}
case $1 in
master)
mail_message master
;;
backup)
mail_message backup
;;
fault)
mail_message fault
;;
*)
exit 1
;;
esac
#添加权限
[root@ka2 ~]# chmod +x /etc/keepalived/mail.sh
#测试脚本
[root@ka1 ~]# bash /etc/keepalived/mail.sh master
#添加引用脚本的配置
[root@ka1 ~]# vim /etc/keepalived/keepalived.conf
vrrp_instance VI_1 {
state MASTER
interface eth0
virtual_router_id 100
priority 100
advert_int 1
#preempt_delay 5s
#nopreempt
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:1
}
unicast_src_ip 172.25.254.10
unicast_peer {
172.25.254.20
}
notify_master "/etc/keepalived/mail.sh master"
notify_backup "/etc/keepalived/mail.sh backup"
notify_fault "/etc/keepalived/mail.sh fault"
}
[root@ka1 ~]# systemctl restart keepalived.service
[root@ka2 ~]# vim /etc/keepalived/keepalived.conf
vrrp_instance VI_1 {
state BACKUP
interface eth0
virtual_router_id 100
priority 80
advert_int 1
#preempt_delay 5s
#nopreempt
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:1
}
unicast_src_ip 172.25.254.20
unicast_peer {
172.25.254.10
}
notify_master "/etc/keepalived/mail.sh master"
notify_backup "/etc/keepalived/mail.sh backup"
notify_fault "/etc/keepalived/mail.sh fault"
}
[root@ka2 ~]# systemctl restart keepalived.service
#重启服务后会收到邮件脚本如下:

测试:在浏览器中观察邮件即可
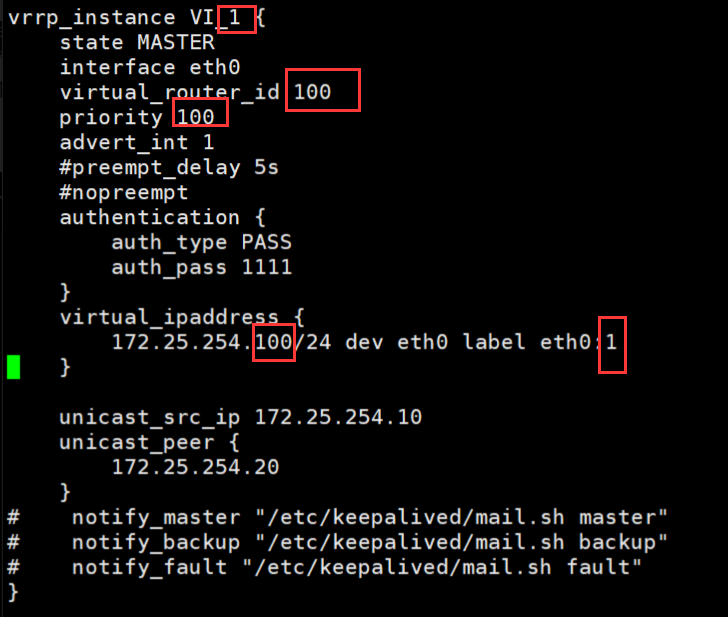
3.5 实现 master/master 的 Keepalived 双主架构
master/slave的单主架构,同一时间只有一个Keepalived对外提供服务,此主机繁忙,而另一台主机却很空闲,利用率低下,可以使用master/master的双主架构,解决此问题。
master/master 的双主架构:
即将两个或以上VIP分别运行在不同的keepalived服务器,以实现服务器并行提供web访问的目的,提高服务器资源利用率
主备需要修改的地方:
·state MASTER(BACKUP)
·virtual_router_id 100(两个主机的一个主备的ip要相同)
·priority 100(主的优先级要高于备用的)
·虚拟的IP如下:
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:1 #同一个主备ip要相同,网卡要相同且没有被占用
}
[root@ka1 ~]# vim /etc/keepalived/keepalived.conf
vrrp_instance VI_1 {
state MASTER #主
interface eth0
virtual_router_id 100
priority 100
advert_int 1
#preempt_delay 5s
#nopreempt
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:1
}
unicast_src_ip 172.25.254.10
unicast_peer {
172.25.254.20
}
# notify_master "/etc/keepalived/mail.sh master"
# notify_backup "/etc/keepalived/mail.sh backup"
# notify_fault "/etc/keepalived/mail.sh fault"
}
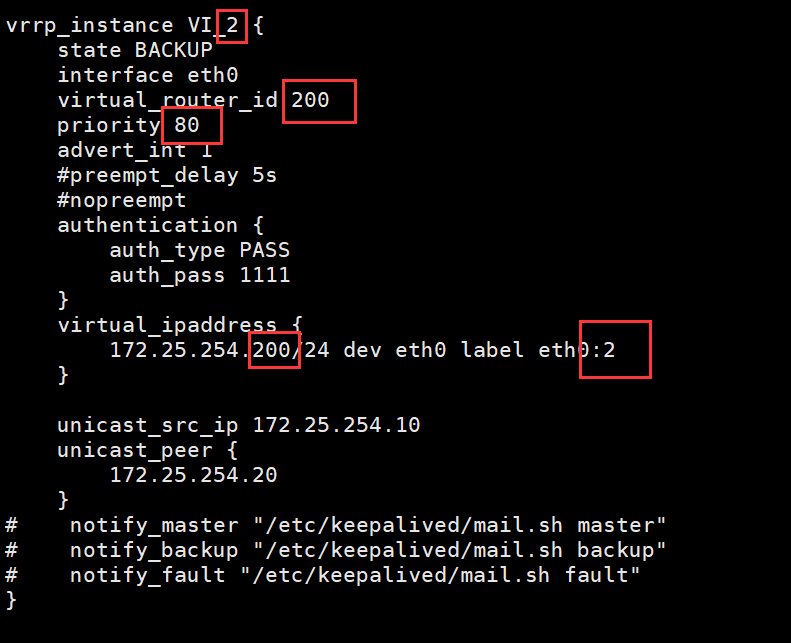
vrrp_instance VI_2 {
state BACKUP #备
interface eth0
virtual_router_id 200
priority 80
advert_int 1
#preempt_delay 5s
#nopreempt
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.200/24 dev eth0 label eth0:2
}
unicast_src_ip 172.25.254.10
unicast_peer {
172.25.254.20
}
# notify_master "/etc/keepalived/mail.sh master"
# notify_backup "/etc/keepalived/mail.sh backup"
# notify_fault "/etc/keepalived/mail.sh fault"
}
[root@ka1 ~]# systemctl restart keepalived.service
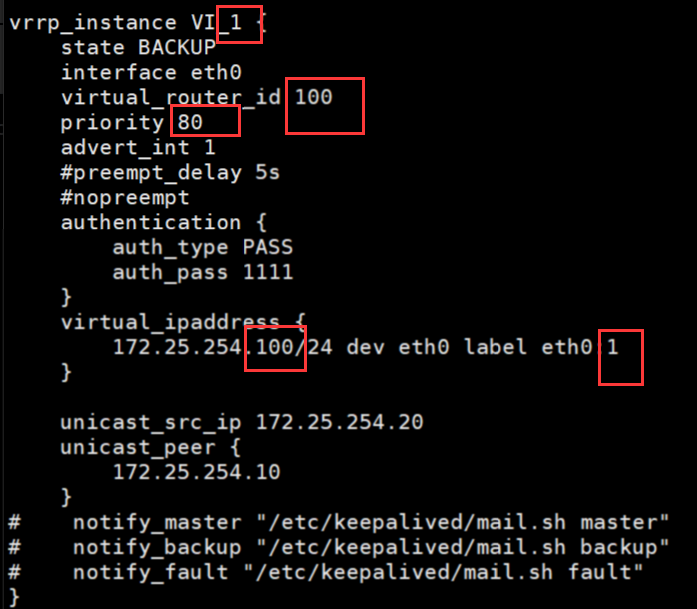
[root@ka2 ~]# vim /etc/keepalived/keepalived.conf
vrrp_instance VI_1 {
state BACKUP #备
interface eth0
virtual_router_id 100
priority 80
advert_int 1
#preempt_delay 5s
#nopreempt
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:1
}
unicast_src_ip 172.25.254.20
unicast_peer {
172.25.254.10
}
# notify_master "/etc/keepalived/mail.sh master"
# notify_backup "/etc/keepalived/mail.sh backup"
# notify_fault "/etc/keepalived/mail.sh fault"
}
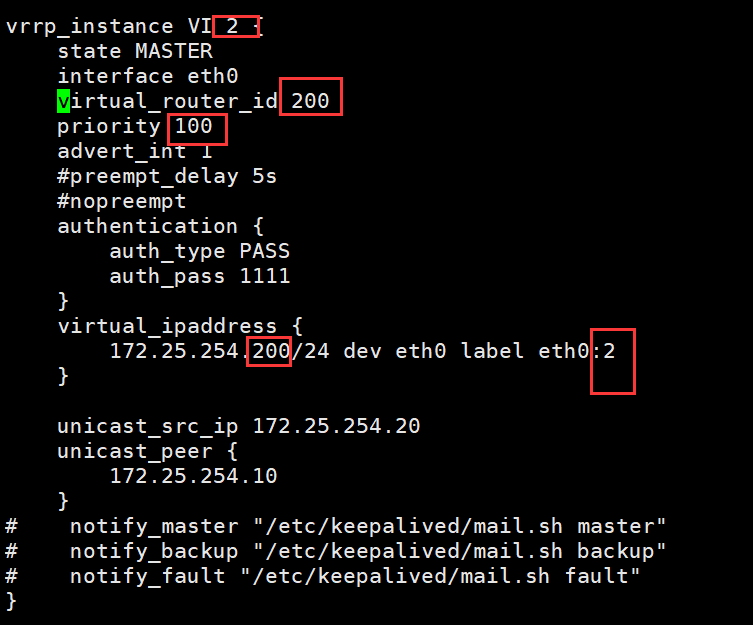
vrrp_instance VI_2 {
state MASTER #主
interface eth0
virtual_router_id 200
priority 100
advert_int 1
#preempt_delay 5s
#nopreempt
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.200/24 dev eth0 label eth0:2
}
unicast_src_ip 172.25.254.20
unicast_peer {
172.25.254.10
}
# notify_master "/etc/keepalived/mail.sh master"
# notify_backup "/etc/keepalived/mail.sh backup"
# notify_fault "/etc/keepalived/mail.sh fault"
}
[root@ka2 ~]# systemctl restart keepalived.service
#测试
[root@ka1 ~]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.10 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::20c:29ff:fe73:deb2 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
RX packets 513894 bytes 51976853 (49.5 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 96148 bytes 8275534 (7.8 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0:1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.100 netmask 255.255.255.0 broadcast 0.0.0.0
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 655 bytes 48137 (47.0 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 655 bytes 48137 (47.0 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether 52:54:00:f1:ee:92 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@ka2 ~]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.20 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::20c:29ff:fec2:7175 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:c2:71:75 txqueuelen 1000 (Ethernet)
RX packets 513134 bytes 51651531 (49.2 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 106890 bytes 8453025 (8.0 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0:2: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.200 netmask 255.255.255.0 broadcast 0.0.0.0
ether 00:0c:29:c2:71:75 txqueuelen 1000 (Ethernet)
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 46 bytes 3598 (3.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 46 bytes 3598 (3.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether 52:54:00:f1:ee:92 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
#关闭ka2测试
[root@ka2 ~]# systemctl stop keepalived.service
[root@ka1 ~]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.10 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::20c:29ff:fe73:deb2 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
RX packets 515312 bytes 52094815 (49.6 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 96317 bytes 8290464 (7.9 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0:1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.100 netmask 255.255.255.0 broadcast 0.0.0.0
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
eth0:2: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.200 netmask 255.255.255.0 broadcast 0.0.0.0
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 655 bytes 48137 (47.0 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 655 bytes 48137 (47.0 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether 52:54:00:f1:ee:92 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
ka1
主
备
ka2
测试:

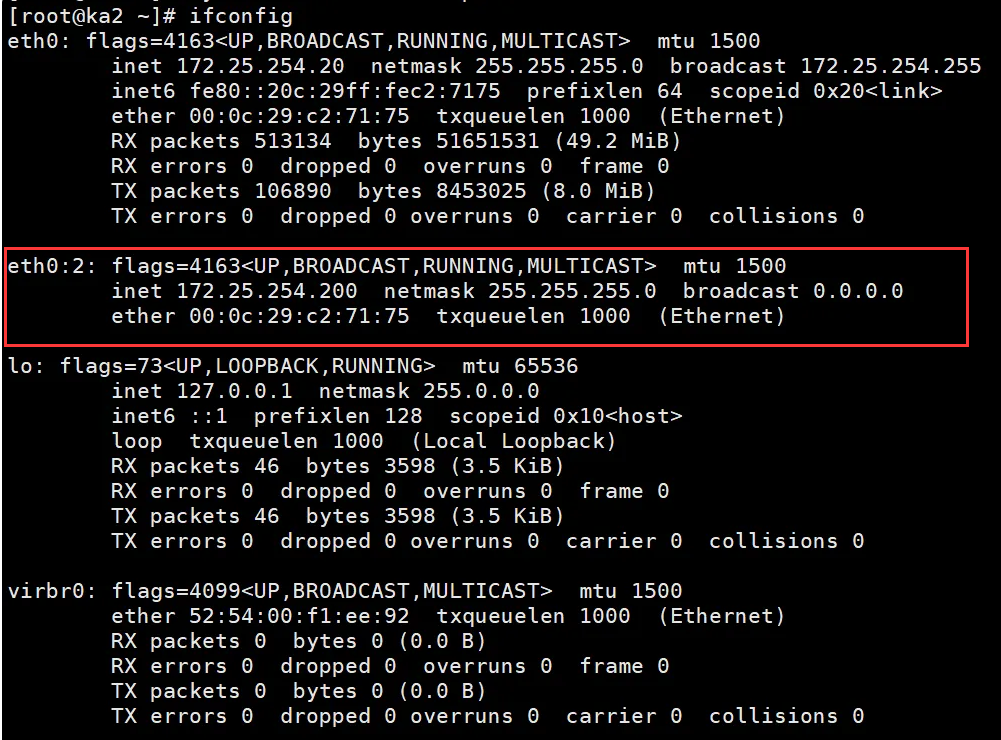
关掉ka2的keepalive服务后

实战案例:三个节点的三主架构实现
#第一个节点ka1配置:
Vrrp instance 1:MASTER,优先级100
Vrrp instance 2:BACKUP,优先级80
Vrrp instance 3:BACKUP,优先级60
#第二个节点ka2配置:
Vrrp instance 1:BACKUP,优先级60
Vrrp instance 2:MASTER,优先级100
Vrrp instance 3:BACKUP,优先级80
#第三个节点ka3配置:
Vrrp instance 1:BACKUP,优先级80
Vrrp instance 2:BACKUP,优先级60
Vrrp instance 3:MASTER,优先级100
3.6 实现IPVS的高可用性
3.6.1 IPVS相关配置
3.6.1.1 虚拟服务器配置结构
virtual_server IP port {
...
real_server {
...
}
real_server {
...
}
…
}3.6.1.2 virtual server (虚拟服务器)的定义格式
virtual_server IP port #定义虚拟主机IP地址及其端口
virtual_server fwmark int #ipvs的防火墙打标,实现基于防火墙的负载均衡集群
virtual_server group string #使用虚拟服务器组3.6.1.3 虚拟服务器配置
virtual_server IP port { #VIP和PORT
delay_loop <INT> #检查后端服务器的时间间隔
lb_algo rr|wrr|lc|wlc|lblc|sh|dh #定义调度方法
lb_kind NAT|DR|TUN #集群的类型,注意要大写
persistence_timeout <INT> #持久连接时长
protocol TCP|UDP|SCTP #指定服务协议,一般为TCP
sorry_server <IPADDR> <PORT> #所有RS故障时,备用服务器地址
real_server <IPADDR> <PORT> { #RS的IP和PORT
weight <INT> #RS权重
notify_up <STRING>|<QUOTED-STRING> #RS上线通知脚本
notify_down <STRING>|<QUOTED-STRING> #RS下线通知脚本
HTTP_GET|SSL_GET|TCP_CHECK|SMTP_CHECK|MISC_CHECK { ... } #定义当前主机健康状态检测方法
}
}
#注意:括号必须分行写,两个括号写在同一行,如: }} 会出错3.6.1.4 应用层监测
应用层检测:HTTP_GET|SSL_GET
HTTP_GET|SSL_GET {
url {
path <URL_PATH> #定义要监控的URL
status_code <INT> #判断上述检测机制为健康状态的响应码,一般为 200
}
connect_timeout <INTEGER> #客户端请求的超时时长, 相当于haproxy的timeout server
nb_get_retry <INT> #重试次数
delay_before_retry <INT> #重试之前的延迟时长
connect_ip <IP ADDRESS> #向当前RS哪个IP地址发起健康状态检测请求
connect_port <PORT> #向当前RS的哪个PORT发起健康状态检测请求
bindto <IP ADDRESS> #向当前RS发出健康状态检测请求时使用的源地址
bind_port <PORT> #向当前RS发出健康状态检测请求时使用的源端口
}3.6.1.5 TCP监测
传输层检测:TCP_CHECK
TCP_CHECK {
connect_ip <IP ADDRESS> #向当前RS的哪个IP地址发起健康状态检测请求
connect_port <PORT> #向当前RS的哪个PORT发起健康状态检测请求
bindto <IP ADDRESS> #发出健康状态检测请求时使用的源地址
bind_port <PORT> #发出健康状态检测请求时使用的源端口
connect_timeout <INTEGER> #客户端请求的超时时长
#等于haproxy的timeout server
}3.6.2 实战案例
3.6.2.1 实战案例1:实现单主的 LVS-DR 模式
准备web服务器并使用脚本绑定VIP至web服务器lo网卡
具体流程:
·rel主机需要有vip(可以在虚拟网卡中添加)
·rel主机需要关闭arp的响应
·ka1和ka2编写keepalive配置文件
#安装httpd
[root@relserver1 ~]# yum install httpd -y
[root@relserver1 ~]# echo rel - 172.25.254.110 > /var/www/html/index.html
[root@relserver1 ~]# systemctl start httpd
[root@relserver2 ~]# yum install httpd -y
[root@relserver2 ~]# echo rel - 172.25.254.120 > /var/www/html/index.html
[root@relserver2 ~]# systemctl start httpd
#准备两台后端RS主机
[root@relserver1 ~]# ip addr add 172.25.254.100/32 dev lo
[root@relserver2 ~]# ip addr add 172.25.254.100/32 dev lo
#如果想要永久设置,可以在环回的配置文件中直接更改
[root@ka1 ~]# vim /etc/sysconfig/network-scripts/ifcfg-lo
#在里面修改ip和掩码即可
#然后重启
[root@ka1 ~]# systemctl restart network
#关闭响应(临时的)
[root@relserver1 ~]# echo 1 > /proc/sys/net/ipv4/conf/all/arp_ignore
[root@relserver1 ~]# echo 1 > /proc/sys/net/ipv4/conf/lo/arp_ignore
[root@relserver1 ~]# echo 2 > /proc/sys/net/ipv4/conf/lo/arp_announce
[root@relserver1 ~]# echo 2 > /proc/sys/net/ipv4/conf/all/arp_announce
#关闭响应(永久的)
[root@relserver2 ~]# sysctl -a | grep arp
dev.parport.default.spintime = 500
dev.parport.default.timeslice = 200
net.ipv4.conf.all.arp_accept = 0
net.ipv4.conf.all.arp_announce = 0
net.ipv4.conf.all.arp_filter = 0
net.ipv4.conf.all.arp_ignore = 0
net.ipv4.conf.all.arp_notify = 0
。。。。。
#写配置文件
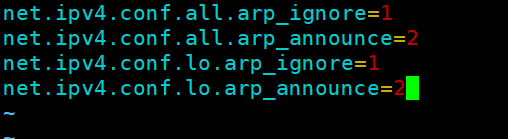
[root@relserver2 ~]# vim /etc/sysctl.d/arp.conf
net.ipv4.conf.all.arp_ignore=1
net.ipv4.conf.all.arp_announce=2
net.ipv4.conf.lo.arp_ignore=1
net.ipv4.conf.lo.arp_announce=2
#重启
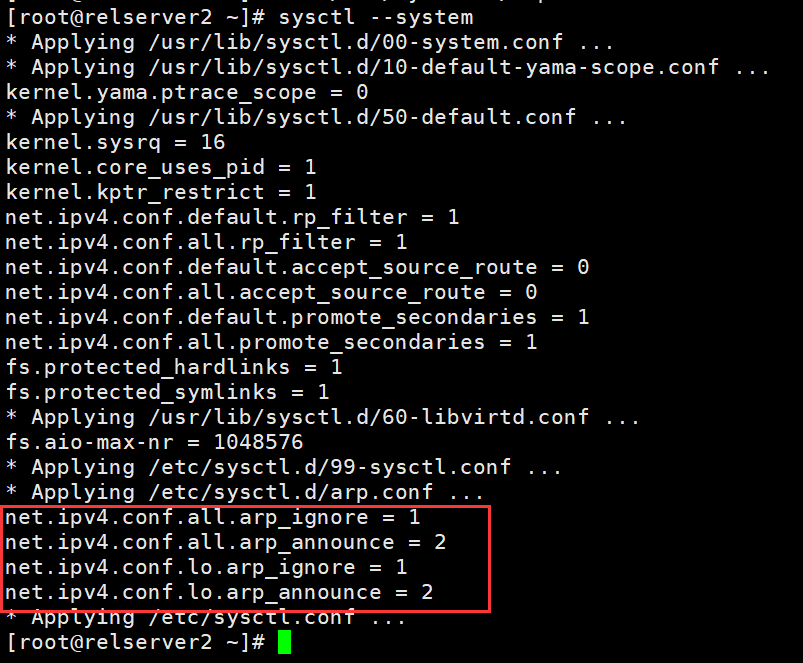
[root@relserver2 ~]# sysctl --system
* Applying /usr/lib/sysctl.d/00-system.conf ...
* Applying /usr/lib/sysctl.d/10-default-yama-scope.conf ...
kernel.yama.ptrace_scope = 0
* Applying /usr/lib/sysctl.d/50-default.conf ...
kernel.sysrq = 16
kernel.core_uses_pid = 1
kernel.kptr_restrict = 1
net.ipv4.conf.default.rp_filter = 1
net.ipv4.conf.all.rp_filter = 1
net.ipv4.conf.default.accept_source_route = 0
net.ipv4.conf.all.accept_source_route = 0
net.ipv4.conf.default.promote_secondaries = 1
net.ipv4.conf.all.promote_secondaries = 1
fs.protected_hardlinks = 1
fs.protected_symlinks = 1
* Applying /usr/lib/sysctl.d/60-libvirtd.conf ...
fs.aio-max-nr = 1048576
* Applying /etc/sysctl.d/99-sysctl.conf ...
* Applying /etc/sysctl.d/arp.conf ...
net.ipv4.conf.all.arp_ignore = 1
net.ipv4.conf.all.arp_announce = 2
net.ipv4.conf.lo.arp_ignore = 1
net.ipv4.conf.lo.arp_announce = 2
* Applying /etc/sysctl.conf ...
#下载ipvsadm,便于检测
[root@ka1 ~]# yum install ipvsadm -y
[root@ka2 ~]# yum install ipvsadm -y
#编写配置文件
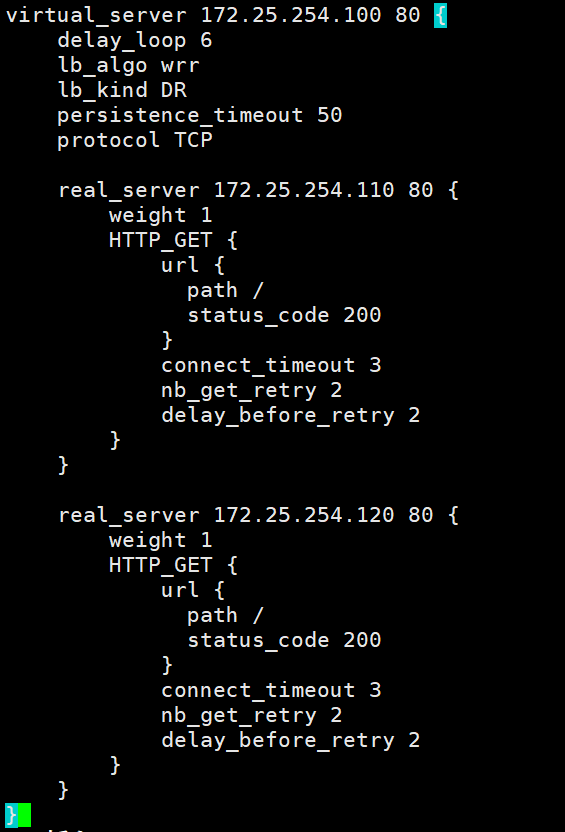
[root@ka1 ~]# vim /etc/keepalived/keepalived.conf
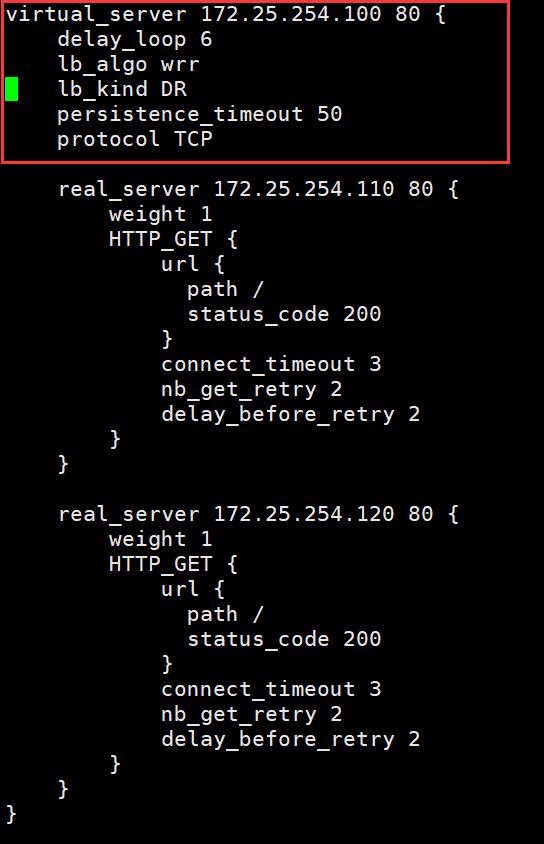
virtual_server 172.25.254.100 80 {
delay_loop 6
lb_algo wrr
lb_kind DR
persistence_timeout 50
protocol TCP
real_server 172.25.254.110 80 {
weight 1
HTTP_GET {
url {
path /
status_code 200
}
connect_timeout 3
nb_get_retry 2
delay_before_retry 2
}
}
real_server 172.25.254.120 80 {
weight 1
HTTP_GET {
url {
path /
status_code 200
}
connect_timeout 3
nb_get_retry 2
delay_before_retry 2
}
}
}
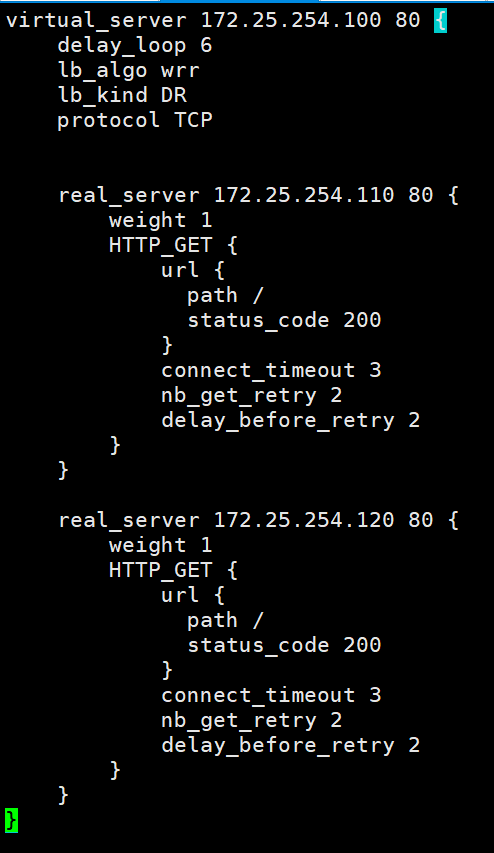
[root@ka2 ~]# vim /etc/keepalived/keepalived.conf
virtual_server 172.25.254.100 80 {
delay_loop 6
lb_algo wrr
lb_kind DR
protocol TCP
real_server 172.25.254.110 80 {
weight 1
HTTP_GET {
url {
path /
status_code 200
}
connect_timeout 3
nb_get_retry 2
delay_before_retry 2
}
}
real_server 172.25.254.120 80 {
weight 1
HTTP_GET {
url {
path /
status_code 200
}
connect_timeout 3
nb_get_retry 2
delay_before_retry 2
}
}
}
[root@ka2 ~]# systemctl restart keepalived.service
#测试
[root@ka1 ~]# ipvsadm -Ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 192.168.200.100:443 rr persistent 50
TCP 10.10.10.2:1358 rr persistent 50
-> 192.168.200.200:1358 Masq 1 0 0
TCP 10.10.10.3:1358 rr persistent 50
[root@ka1 ~]# systemctl restart keepalived.service
[root@ka1 ~]# ipvsadm -Ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 172.25.254.100:80 wrr persistent 50
-> 172.25.254.110:80 Route 1 0 0
-> 172.25.254.120:80 Route 1 0 0
TCP 192.168.200.100:443 rr persistent 50
-> 192.168.201.100:443 Masq 1 0 0
TCP 10.10.10.2:1358 rr persistent 50
-> 192.168.200.2:1358 Masq 1 0 0
-> 192.168.200.3:1358 Masq 1 0 0
#模拟故障
#关闭一个http服务进行测试
[root@relserver1 ~]# systemctl stop httpd.service
[root@ka1 ~]# ipvsadm -Ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 172.25.254.100:80 wrr persistent 50
-> 172.25.254.120:80 Route 1 0 0
TCP 192.168.200.100:443 rr persistent 50
TCP 10.10.10.2:1358 rr persistent 50
-> 192.168.200.200:1358 Masq 1 0
#关闭ka1的keepalive
[root@ka1 ~]# systemctl stop keepalived.service
[root@ka1 ~]# ipvsadm -Ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 192.168.0.100:80 wrr
[root@ka2 ~]# ipvsadm -Ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 172.25.254.100:80 wrr
-> 172.25.254.120:80 Route 1 0 0
TCP 192.168.200.100:443 rr persistent 50
TCP 10.10.10.3:1358 rr persistent 50
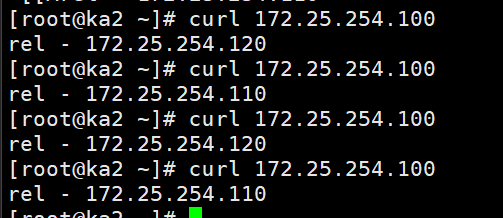
#访问测试
[root@ka2 ~]# curl 172.25.254.100
rel - 172.25.254.120
[root@ka2 ~]# curl 172.25.254.100
rel - 172.25.254.110
[root@ka2 ~]# curl 172.25.254.100
rel - 172.25.254.120
[root@ka2 ~]# curl 172.25.254.100
rel - 172.25.254.110
关闭arp响应
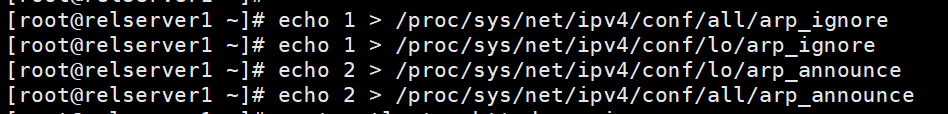
永久关闭的配置文件如下:
![]()
编写配置文件
rel1:
rel2:
理解:
类似于:
![]()
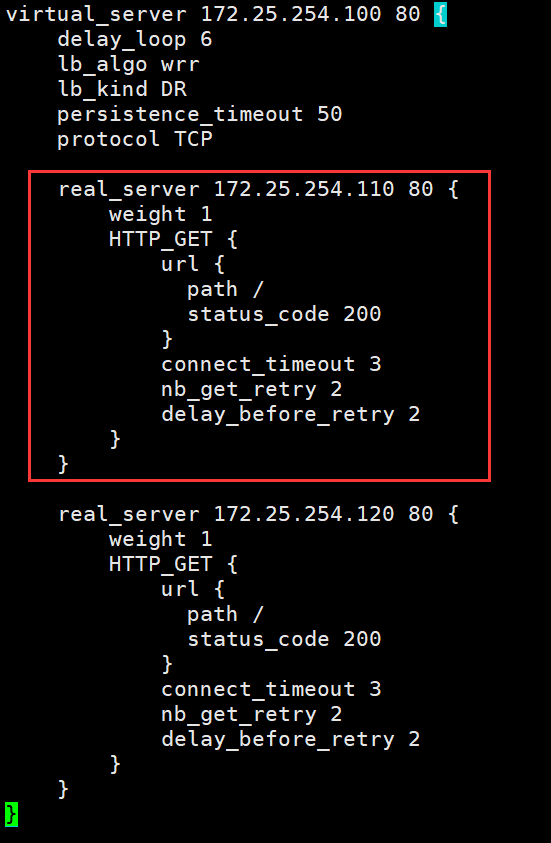
类似于:
![]()
测试:
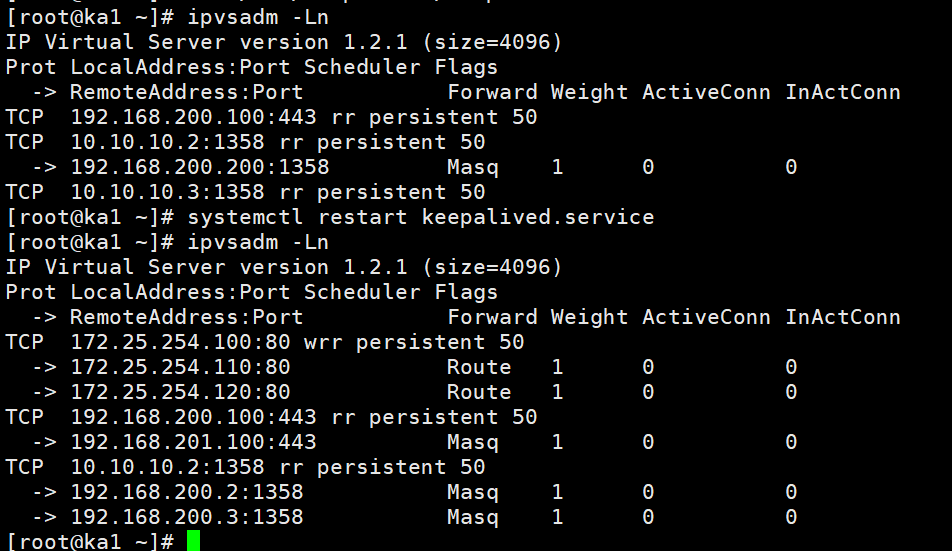
模拟故障
关闭一个http服务后,再进行测试
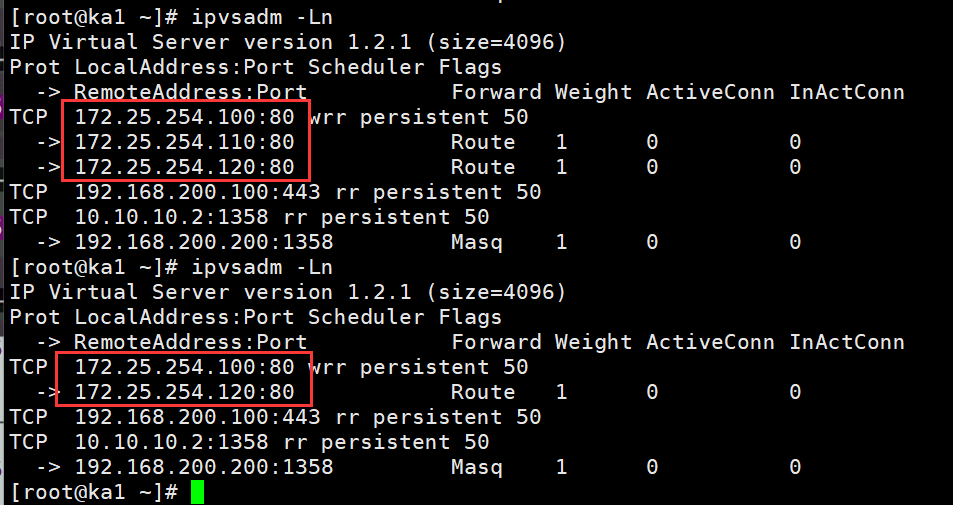
关闭ka1的keepalive
ka1
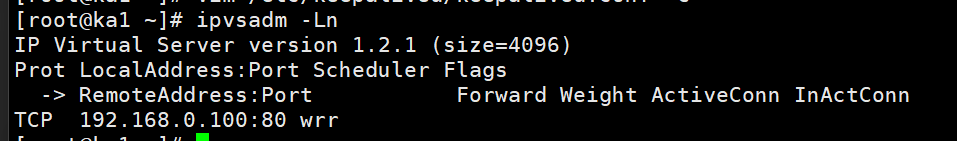
ka2

但由于是抢占模式,即使此时开启了ka1的keepalive也无法获得
访问测试:
3.7 实现其它应用的高可用性 VRRP Script
keepalived利用 VRRP Script 技术,可以调用外部的辅助脚本进行资源监控,并根据监控的结果实现优先
动态调整,从而实现其它应用的高可用性功能
参考配置文件:/usr/share/doc/keepalived/keepalived.conf.vrrp.localcheck
总结:vrrp_script中可以运行一个脚本,而这个脚本检测某个文件是否存在返回一个值,如果这个值是非零则会根据策略选择降低或者提高优先级。
3.7.1 VRRP Script 配置
分两步实现:
·定义脚本
vrrp_script:自定义资源监控脚本,vrrp实例根据脚本返回值,公共定义,可被多个实例调用,定义在vrrp实例之外的独立配置块,一般放在global_defs设置块之后。
通常此脚本用于监控指定应用的状态。一旦发现应用的状态异常,则触发对MASTER节点的权重减至低于SLAVE节点,从而实现 VIP 切换到 SLAVE 节点
#定义脚本
vrrp_script <SCRIPT_NAME> {
script <STRING>|<QUOTED-STRING> #此脚本返回值为非0时,会触发下面OPTIONS执行
OPTIONS
}·调用脚本
track_script:调用vrrp_script定义的脚本去监控资源,定义在VRRP实例之内,调用事先定义的vrrp_script
#调用脚本
track_script {
SCRIPT_NAME_1
SCRIPT_NAME_2
}3.7.1.1 定义 VRRP script
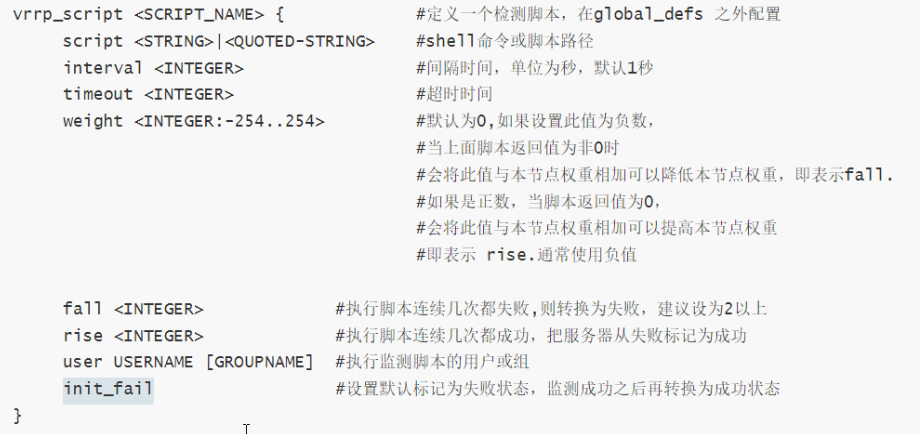
vrrp_script <SCRIPT_NAME> { #定义一个检测脚本,在global_defs 之外配置(也可以在下面配置)
script <STRING>|<QUOTED-STRING> #shell命令或脚本路径
interval <INTEGER> #间隔时间,单位为秒,默认1秒
timeout <INTEGER> #超时时间
weight <INTEGER:-254..254> #默认为0,如果设置此值为负数,
#当上面脚本返回值为非0时
#会将此值与本节点权重相加可以降低本节点权重,
#即表示fall.
#如果是正数,当脚本返回值为0,
#会将此值与本节点权重相加可以提高本节点权重
#即表示 rise.通常使用负值
fall <INTEGER> #执行脚本连续几次都失败,则转换为失败,建议设为2以上
rise <INTEGER> #执行脚本连续几次都成功,把服务器从失败标记为成功
user USERNAME [GROUPNAME] #执行监测脚本的用户或组
init_fail #设置默认标记为失败状态,监测成功之后再转换为成功状态
}
3.7.1.2 调用 VRRP script
vrrp_instance test {
... ...
track_script {
check_down
}
}3.7.2 实战案例:利用脚本实现主从角色切换
[root@ka1 ~]# vim /etc/keepalived/test.sh
#!/bin/bash
[ ! -f "/mnt/haha" ] #判断有没有这个haha文件,没有就为真(0)
[root@ka1 ~]# chmod +x /etc/keepalived/test.sh
[root@ka1 ~]# vim /etc/keepalived/keepalived.conf
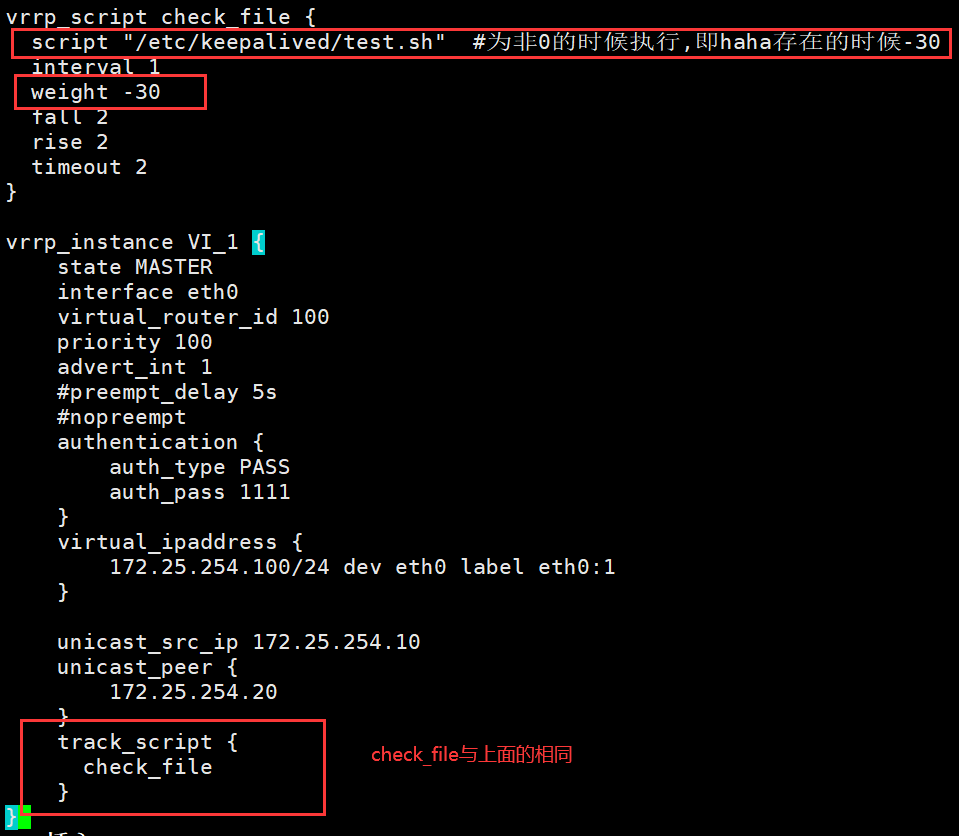
vrrp_script check_file {
script "/etc/keepalived/test.sh" #为非0的时候执行,即haha存在的时候-30
interval 1
weight -30
fall 2
rise 2
timeout 2
}
vrrp_instance VI_1 {
state MASTER
interface eth0
virtual_router_id 100
priority 100
advert_int 1
#preempt_delay 5s
#nopreempt
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:1
}
unicast_src_ip 172.25.254.10
unicast_peer {
172.25.254.20
}
track_script {
check_file
}
}
[root@ka1 mnt]# systemctl restart keepalived.service
#没有haha文件时
[root@ka1 mnt]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.10 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::20c:29ff:fe73:deb2 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
RX packets 737477 bytes 70679904 (67.4 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 126567 bytes 10684608 (10.1 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0:1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.100 netmask 255.255.255.0 broadcast 0.0.0.0
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 655 bytes 48137 (47.0 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 655 bytes 48137 (47.0 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether 52:54:00:f1:ee:92 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
#有haha文件时
[root@ka1 mnt]# touch haha
[root@ka1 mnt]# systemctl restart keepalived.service
[root@ka1 mnt]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.10 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::20c:29ff:fe73:deb2 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
RX packets 945796 bytes 87514535 (83.4 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 152652 bytes 12586792 (12.0 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 655 bytes 48137 (47.0 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 655 bytes 48137 (47.0 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether 52:54:00:f1:ee:92 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
没有haha文件时
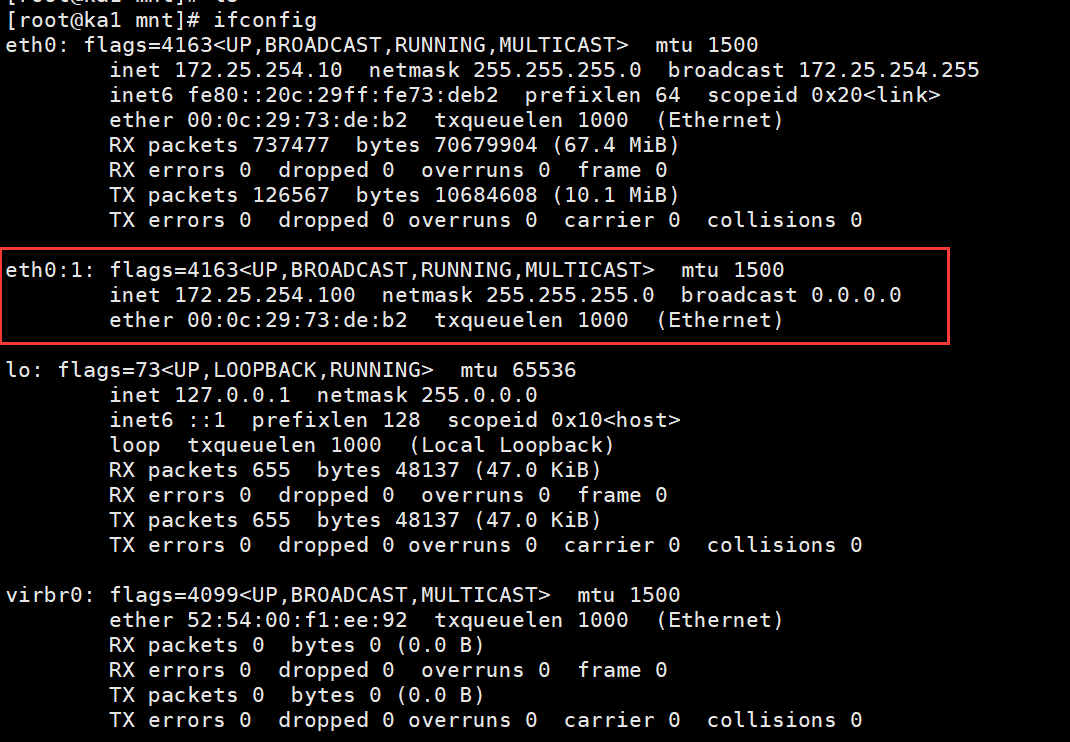
有haha文件时,会100-30=70<80,vip会转移到ka2中

3.7.3 实战案例:实现HAProxy高可用
#在两个ka1和ka2先实现haproxy的配置
[root@ka1 ~]# yum install haproxy -y
[root@ka2 ~]# yum install haproxy -y
[root@ka1 ~]# vim /etc/haproxy/haproxy.cfg
listen webcluster
bind 172.25.254.100:80
mode http
balance roundrobin
server web1 172.25.254.110:80 check inter 3 fall 2 rise 5
server web2 172.25.254.120:80 check inter 3 fall 2 rise 5
[root@ka2 ~]# vim /etc/haproxy/haproxy.cfg
listen webcluster
bind 172.25.254.100:80
mode http
balance roundrobin
server web1 172.25.254.110:80 check inter 3 fall 2 rise 5
server web2 172.25.254.120:80 check inter 3 fall 2 rise 5
#启动haproxy服务
[root@ka1 ~]# systemctl enable --now haproxy.service
Created symlink from /etc/systemd/system/multi-user.target.wants/haproxy.service to /usr/lib/systemd/system/haproxy.service.
[root@ka2 ~]# systemctl enable --now haproxy.service
Created symlink from /etc/systemd/system/multi-user.target.wants/haproxy.service to /usr/lib/systemd/system/haproxy.service.
#在两个ka1和ka2两个节点启用内核参数,即使本地没有172.25.254.100的iphaproxy也可以启动
[root@ka1 ~]# vim /etc/sysctl.conf
net.ipv4.ip_nonlocal_bind = 1
[root@ka1 ~]# sysctl -p
net.ipv4.ip_nonlocal_bind = 1
[root@ka2 ~]# vim /etc/sysctl.conf
net.ipv4.ip_nonlocal_bind = 1
[root@ka2 ~]# sysctl -p
net.ipv4.ip_nonlocal_bind = 1
#还原环境
#去除上面配置的vip,原本就是临时配置的所以可以使用此方法
[root@relserver1 ~]# systemctl restart network
[root@relserver2 ~]# systemctl restart network
#去除arp
[root@relserver1 ~]# echo 0 > /proc/sys/net/ipv4/conf/all/arp_ignore
[root@relserver1 ~]# echo 0 > /proc/sys/net/ipv4/conf/lo/arp_ignore
[root@relserver1 ~]# echo 0 > /proc/sys/net/ipv4/conf/lo/arp_announce
[root@relserver1 ~]# echo 0 > /proc/sys/net/ipv4/conf/all/arp_announce
#rel2配置的是永久配置,用此方法
[root@relserver2 ~]# vim /etc/sysctl.d/arp.conf
net.ipv4.conf.all.arp_ignore=0
net.ipv4.conf.all.arp_announce=0
net.ipv4.conf.lo.arp_ignore=0
net.ipv4.conf.lo.arp_announce=0
[root@relserver2 ~]# sysctl --system
#注释上文lvs的访问
[root@ka1 ~]# vim /etc/keepalived/keepalived.conf
#virtual_server 172.25.254.100 80 {
# delay_loop 6
# lb_algo wrr
# lb_kind DR
# persistence_timeout 50
# protocol TCP
#
# real_server 172.25.254.110 80 {
# weight 1
# HTTP_GET {
# url {
# path /
# status_code 200
# }
# connect_timeout 3
# nb_get_retry 2
# delay_before_retry 2
# }
# }
#
# real_server 172.25.254.120 80 {
# weight 1
# HTTP_GET {
# url {
# path /
# status_code 200
# }
# connect_timeout 3
# nb_get_retry 2
# delay_before_retry 2
# }
# }
#}
[root@ka2 ~]# vim /etc/keepalived/keepalived.conf
#virtual_server 172.25.254.100 80 {
# delay_loop 6
# lb_algo wrr
# lb_kind DR
# protocol TCP
#
#
# real_server 172.25.254.110 80 {
# weight 1
# HTTP_GET {
# url {
# path /
# status_code 200
# }
# connect_timeout 3
# nb_get_retry 2
# delay_before_retry 2
# }
# }
#
# real_server 172.25.254.120 80 {
# weight 1
# HTTP_GET {
# url {
# path /
# status_code 200
# }
# connect_timeout 3
# nb_get_retry 2
# delay_before_retry 2
# }
# }
#}
#访问测试
[root@ka1 ~]# systemctl restart keepalived.service
[root@ka2 ~]# systemctl restart keepalived.service
[root@ka1 ~]# curl 172.25.254.100
rel - 172.25.254.120
[root@ka1 ~]# curl 172.25.254.100
rel - 172.25.254.110
#在ka1中编写检测脚本
[root@ka1 ~]# vim /etc/keepalived/test1.sh
#!/bin/bash
killall -0 haproxy
[root@ka2 ~]# vim /etc/keepalived/test1.sh
#!/bin/bash
killall -0 haproxy
[root@ka1 ~]# chmod +x /etc/keepalived/test1.sh
[root@ka2 ~]# chmod +x /etc/keepalived/test1.sh
#配置keepalived
[root@ka1 ~]# vim /etc/keepalived/keepalived.conf
vrrp_script check_haproxy {
script "/etc/keepalived/test1.sh" #为非0的时候执行,即haha存在的时候-30
interval 1
weight -30
fall 2
rise 2
timeout 2
}
vrrp_instance VI_1 {
state MASTER
interface eth0
virtual_router_id 100
priority 100
advert_int 1
#preempt_delay 5s
#nopreempt
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:1
}
unicast_src_ip 172.25.254.10
unicast_peer {
172.25.254.20
}
track_script {
check_haproxy
}
}
[root@ka1 ~]# systemctl restart keepalived.service
#由于是双主的配置,所以写在ka2的主上
[root@ka2 ~]# vim /etc/keepalived/keepalived.conf
vrrp_script check_haproxy {
script "/etc/keepalived/test1.sh" #为非0的时候执行,即haha存在的时候-30
interval 1
weight -30
fall 2
rise 2
timeout 2
}
vrrp_instance VI_2 {
state MASTER
interface eth0
virtual_router_id 200
priority 100
advert_int 1
#preempt_delay 5s
#nopreempt
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.200/24 dev eth0 label eth0:2
}
unicast_src_ip 172.25.254.20
unicast_peer {
172.25.254.10
}
track_script {
check_haproxy
}
}
[root@ka2 ~]# systemctl restart keepalived.service
#测试,关闭ka1的haproxy服务
#原本
[root@ka1 ~]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.10 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::20c:29ff:fe73:deb2 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
RX packets 1775928 bytes 150099938 (143.1 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1537220 bytes 109628444 (104.5 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0:1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.100 netmask 255.255.255.0 broadcast 0.0.0.0
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 96217 bytes 20634611 (19.6 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 96217 bytes 20634611 (19.6 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether 52:54:00:f1:ee:92 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
#关掉之后
[root@ka1 ~]# systemctl stop haproxy.service
[root@ka1 ~]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.10 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::20c:29ff:fe73:deb2 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:73:de:b2 txqueuelen 1000 (Ethernet)
RX packets 1833904 bytes 154510389 (147.3 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1629301 bytes 116153484 (110.7 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 102308 bytes 21946985 (20.9 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 102308 bytes 21946985 (20.9 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether 52:54:00:f1:ee:92 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@ka2 ~]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.20 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::20c:29ff:fec2:7175 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:c2:71:75 txqueuelen 1000 (Ethernet)
RX packets 1137999 bytes 102802961 (98.0 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 185423 bytes 14349468 (13.6 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0:1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.100 netmask 255.255.255.0 broadcast 0.0.0.0
ether 00:0c:29:c2:71:75 txqueuelen 1000 (Ethernet)
eth0:2: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.200 netmask 255.255.255.0 broadcast 0.0.0.0
ether 00:0c:29:c2:71:75 txqueuelen 1000 (Ethernet)
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 10478 bytes 528092 (515.7 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 10478 bytes 528092 (515.7 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether 52:54:00:f1:ee:92 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
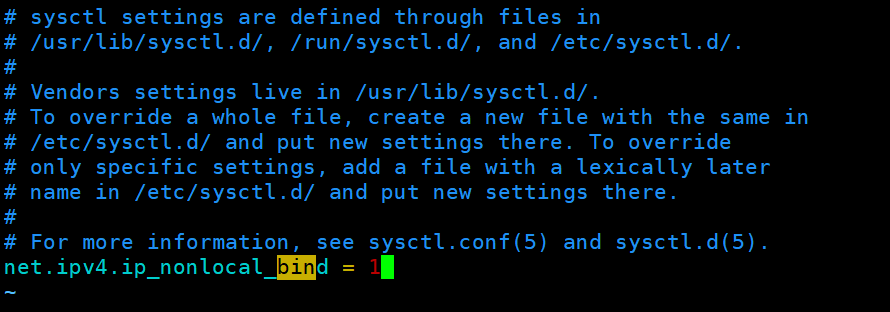

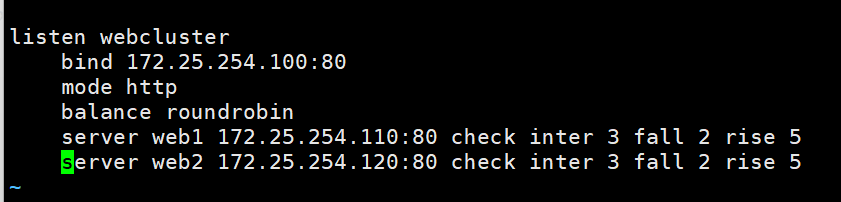
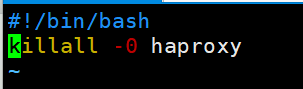
两边都配置
ka1

ka2
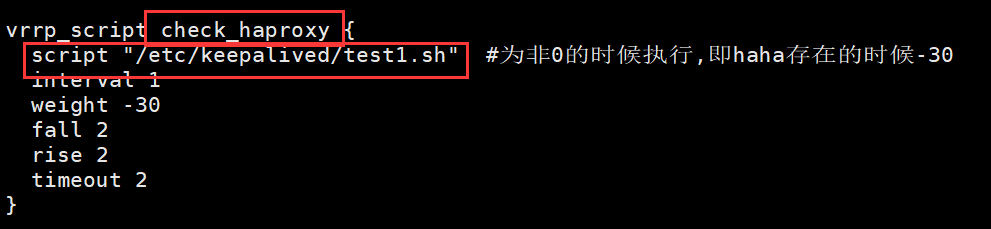
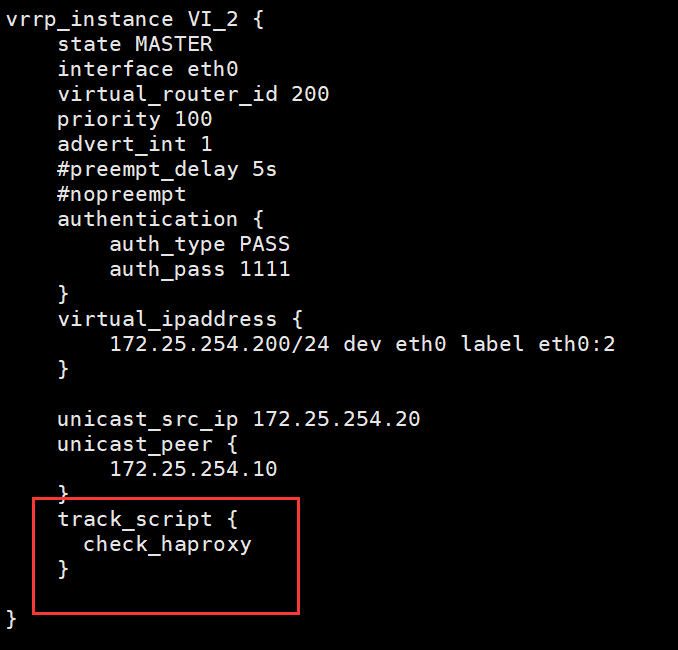
测试,ka1关闭haproxy
原

现
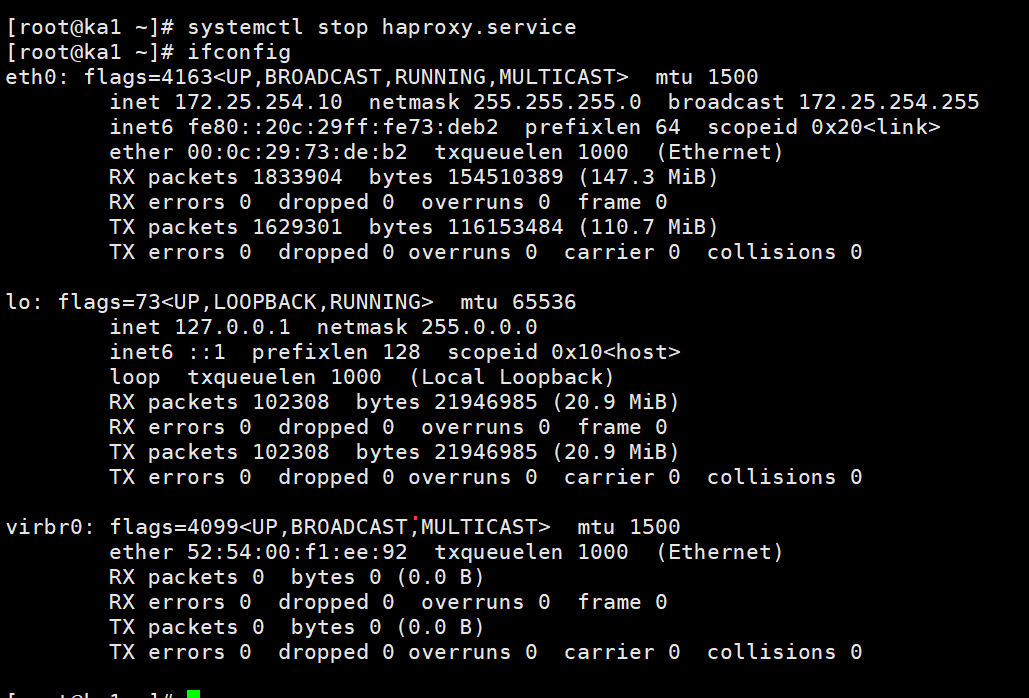
ka2