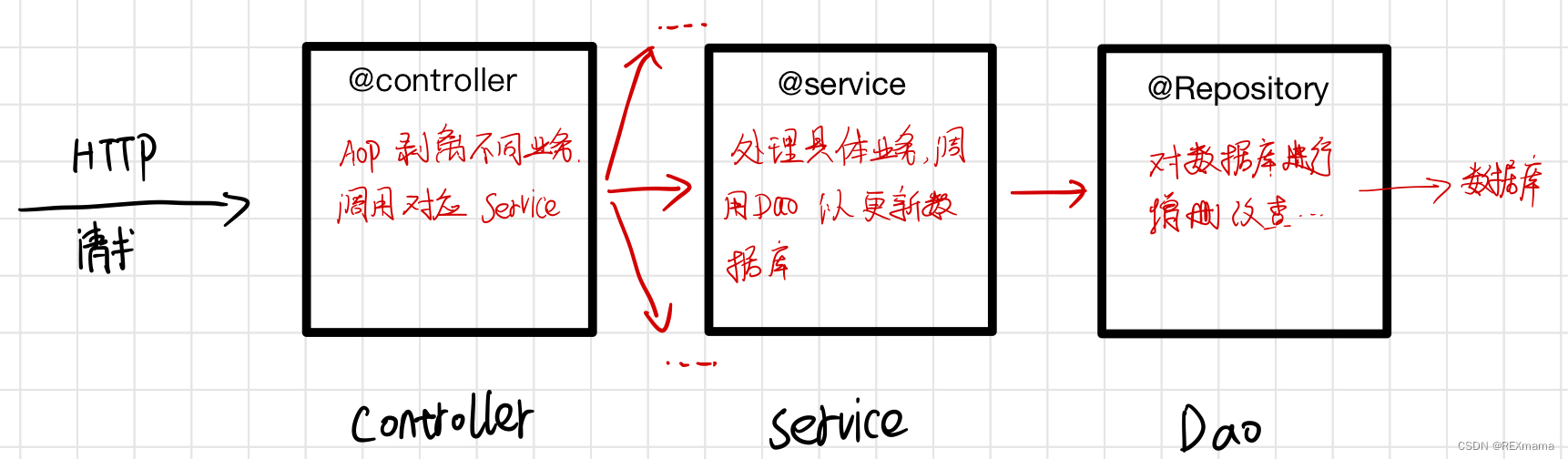
总体分为SpringSecurityOauth2授权码模式演示和密码模式演示
一直下一步,依赖手动导入,SpringBoot版本改成2.2.5.RELEASE,JDK版本1.8
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<parent>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-parent</artifactId>
<version>2.2.5.RELEASE</version>
<relativePath/> <!-- lookup parent from repository -->
</parent>
<groupId>com.example</groupId>
<artifactId>springsecurityoauth2-demo</artifactId>
<version>0.0.1-SNAPSHOT</version>
<name>springsecurityoauth2-demo</name>
<description>Demo project for Spring Boot</description>
<properties>
<java.version>1.8</java.version>
<spring-cloud.version>Greenwich.SR2</spring-cloud.version>
</properties>
<dependencies>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-oauth2</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-security</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
</dependency>
</dependencies>
<dependencyManagement>
<dependencies>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-dependencies</artifactId>
<version>${spring-cloud.version}</version>
<type>pom</type>
<scope>import</scope>
</dependency>
</dependencies>
</dependencyManagement>
<build>
<plugins>
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
</plugin>
</plugins>
</build>
</project>授权码模式演示:
SpringSecurity引入之后会有一个默认用户user和默认密码,项目启动后控制台输出的那个
需要先自定义一个SpringSecurity登录逻辑,然后去修改用户密码
自定义SpringSecurity登录逻辑需要用到PasswordEncode对密码进行单向加密
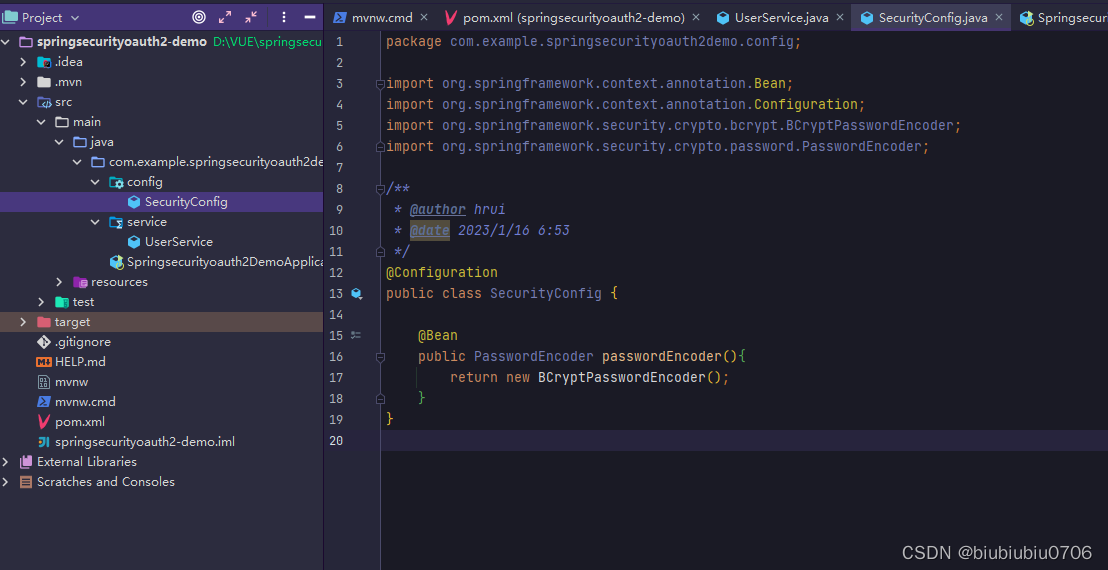

如果想用自己自定义可以这么干
package com.example.springsecurityoauth2demo.pojo;
import org.springframework.security.core.GrantedAuthority;
import org.springframework.security.core.userdetails.UserDetails;
import java.util.Collection;
import java.util.List;
/**
* @author hrui
* @date 2023/1/16 8:47
*/
public class User implements UserDetails {
private String username;
private String password;
private List<GrantedAuthority> authorities;
public User(String username, String password, List<GrantedAuthority> authorities) {
this.username = username;
this.password = password;
this.authorities = authorities;
}
@Override
public Collection<? extends GrantedAuthority> getAuthorities() {
return authorities;
}
@Override
public String getPassword() {
return password;
}
@Override
public String getUsername() {
return username;
}
@Override
public boolean isAccountNonExpired() {
return true;
}
@Override
public boolean isAccountNonLocked() {
return true;
}
@Override
public boolean isCredentialsNonExpired() {
return true;
}
@Override
public boolean isEnabled() {
return true;
}
}那么引入自定义的User就可以了
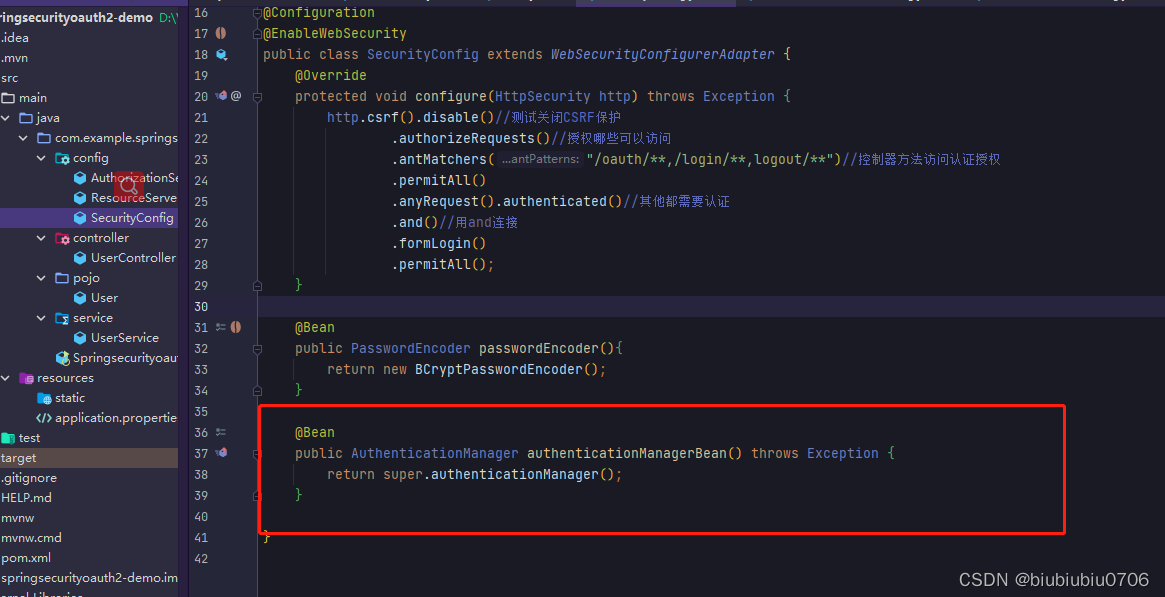
SpringSecurity配置

Oauth2的授权服务器和资源服务器配置

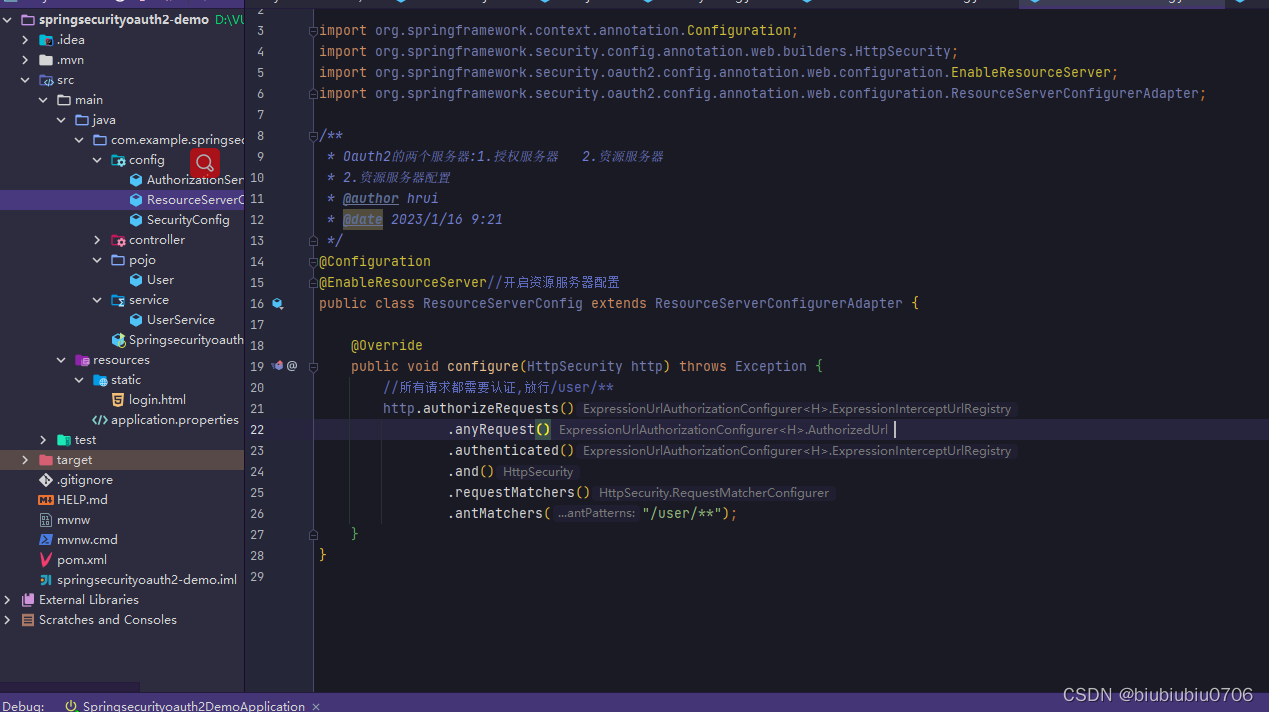

测试获取授权码
http://localhost:8080/oauth/authorize?response_type=code&client_id=admin&redirect_uri=http://www.baidu.com&scope=all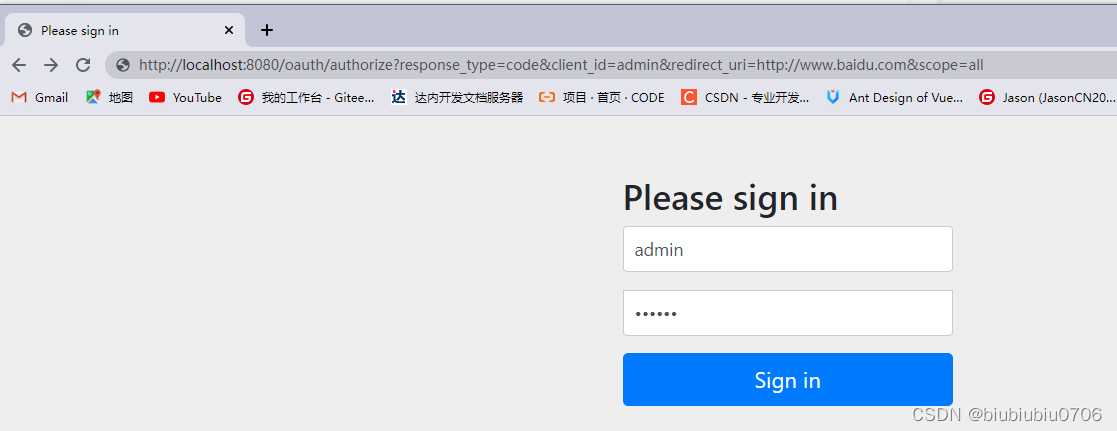
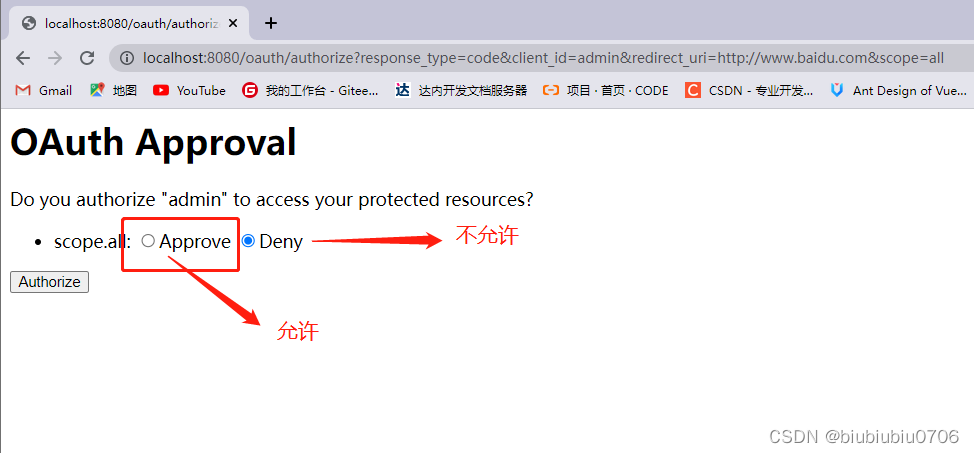


下面通过授权码
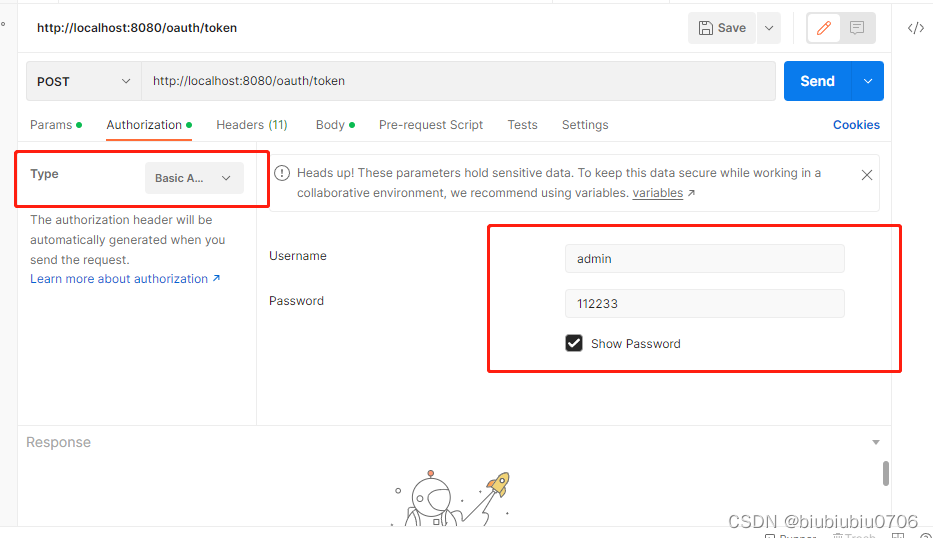
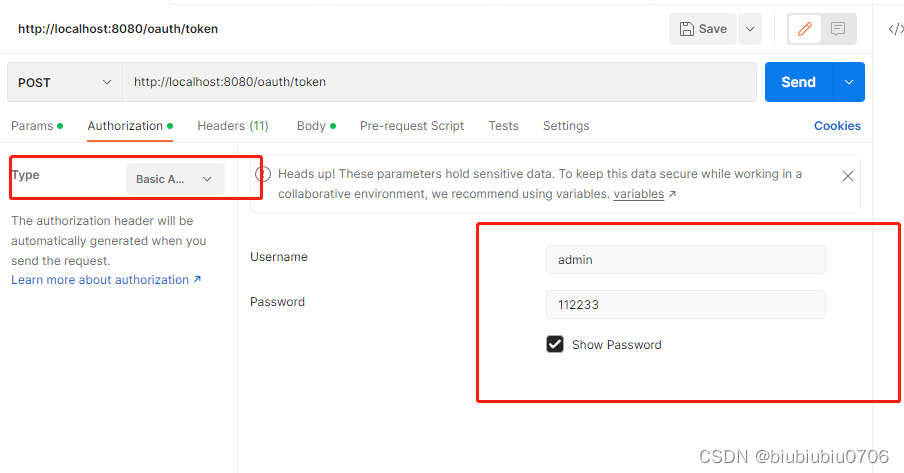
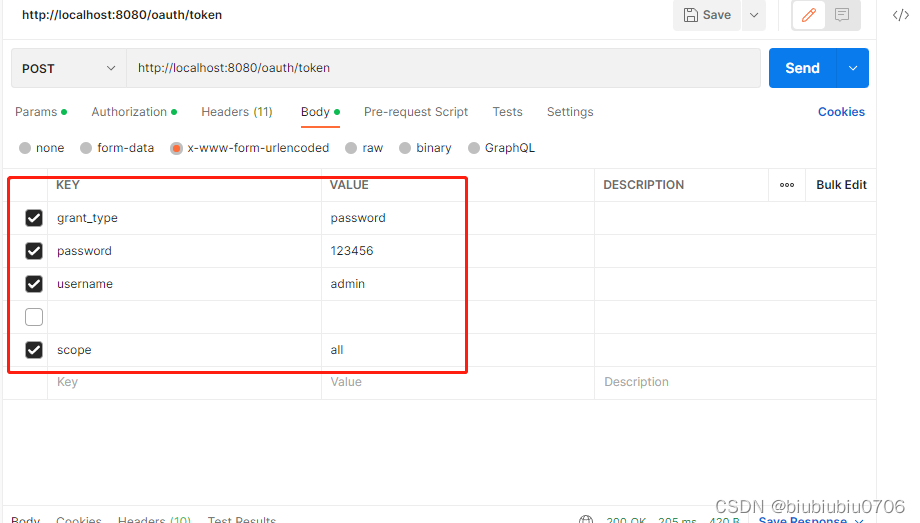
使用工具POSTMAN去获取令牌

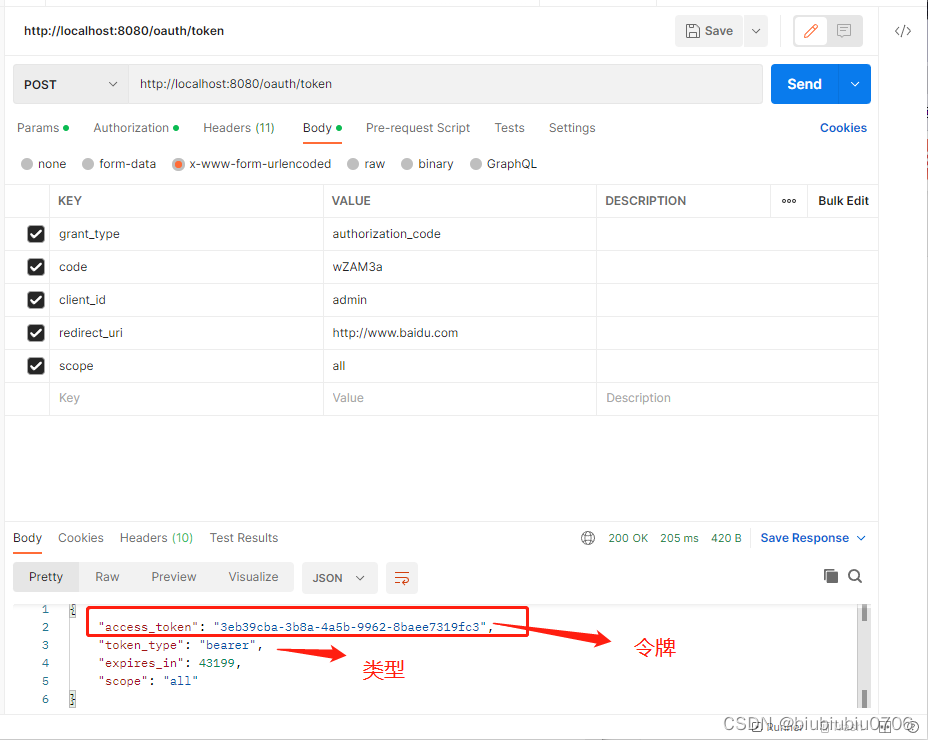
再开个资源

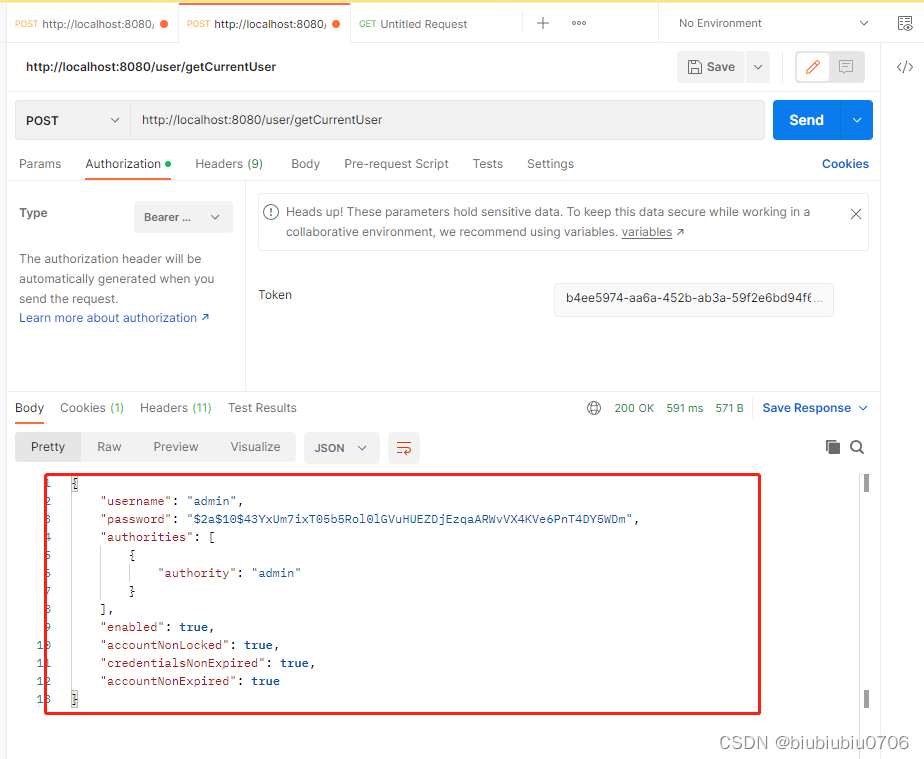
获得当前用户主体



下面演示密码模式演示
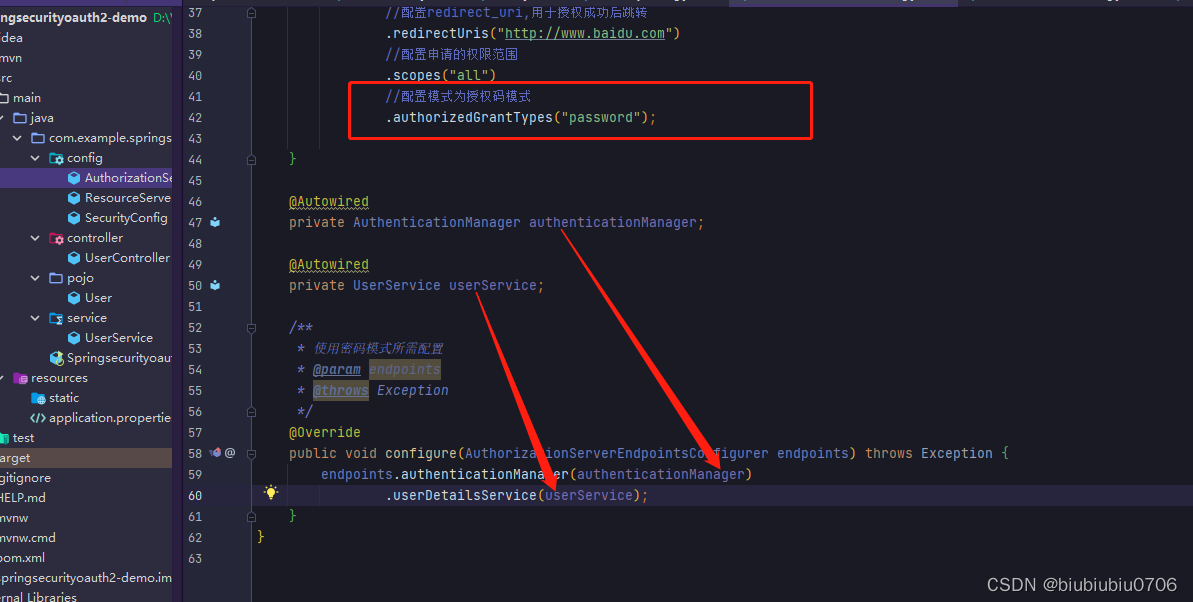
测试
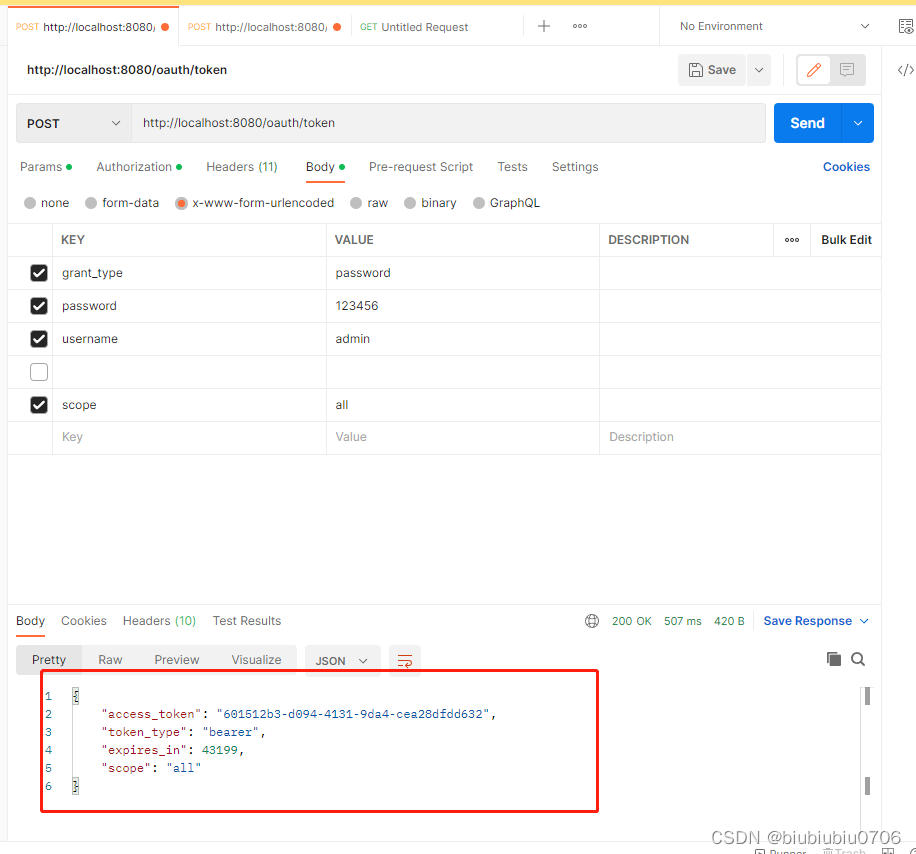

也可以拿到用户主体信息
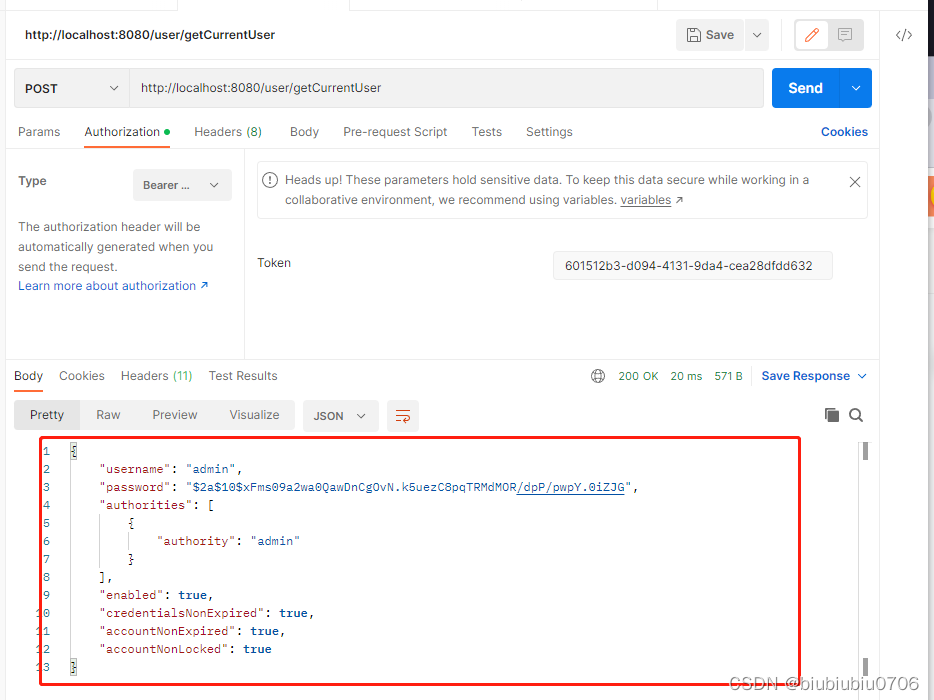
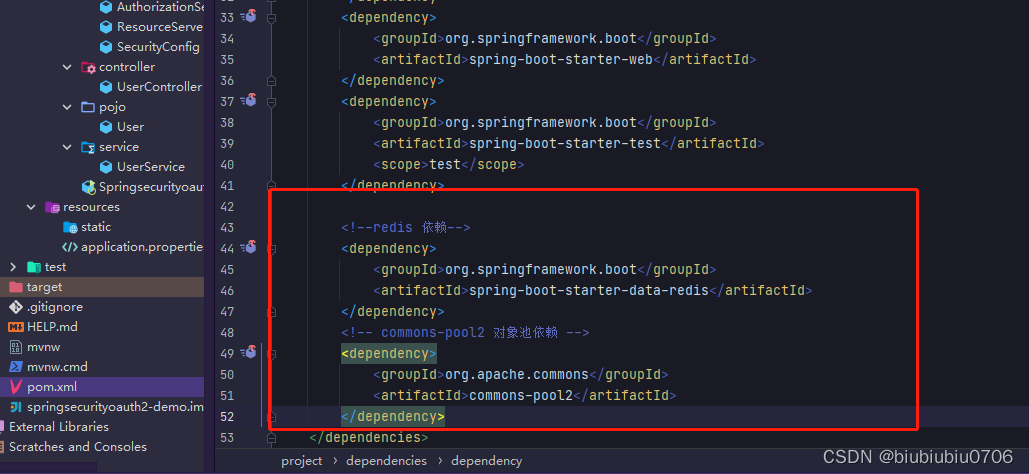
这里token都是存在内存中,实际工作中可能考虑从存到Redis中

Redis配置类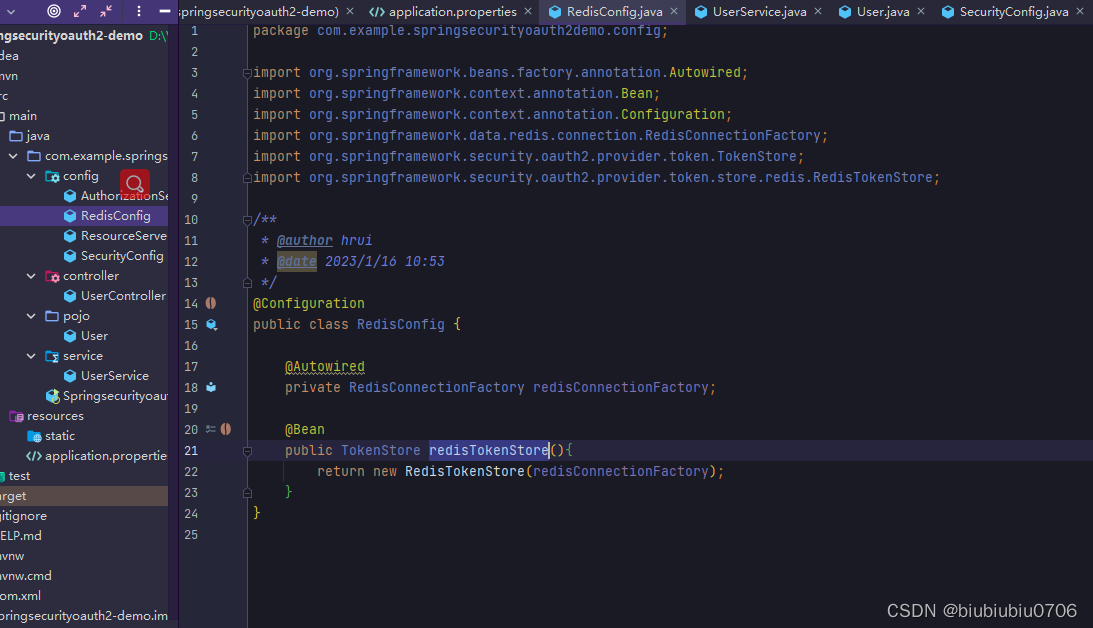
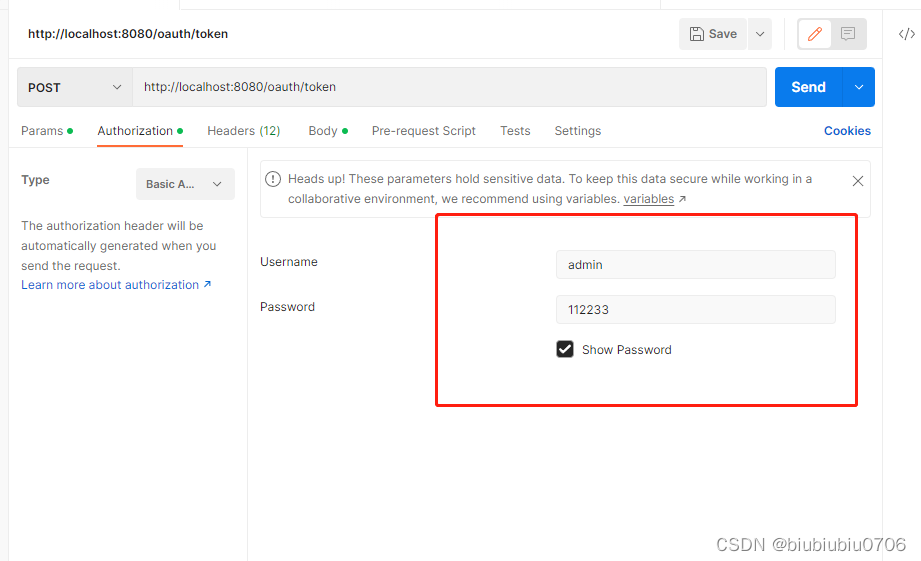
测试
还是原先方式获取token

如果Redis端口不是6379,有密码的话一定要配置


Redis里

JWT demo
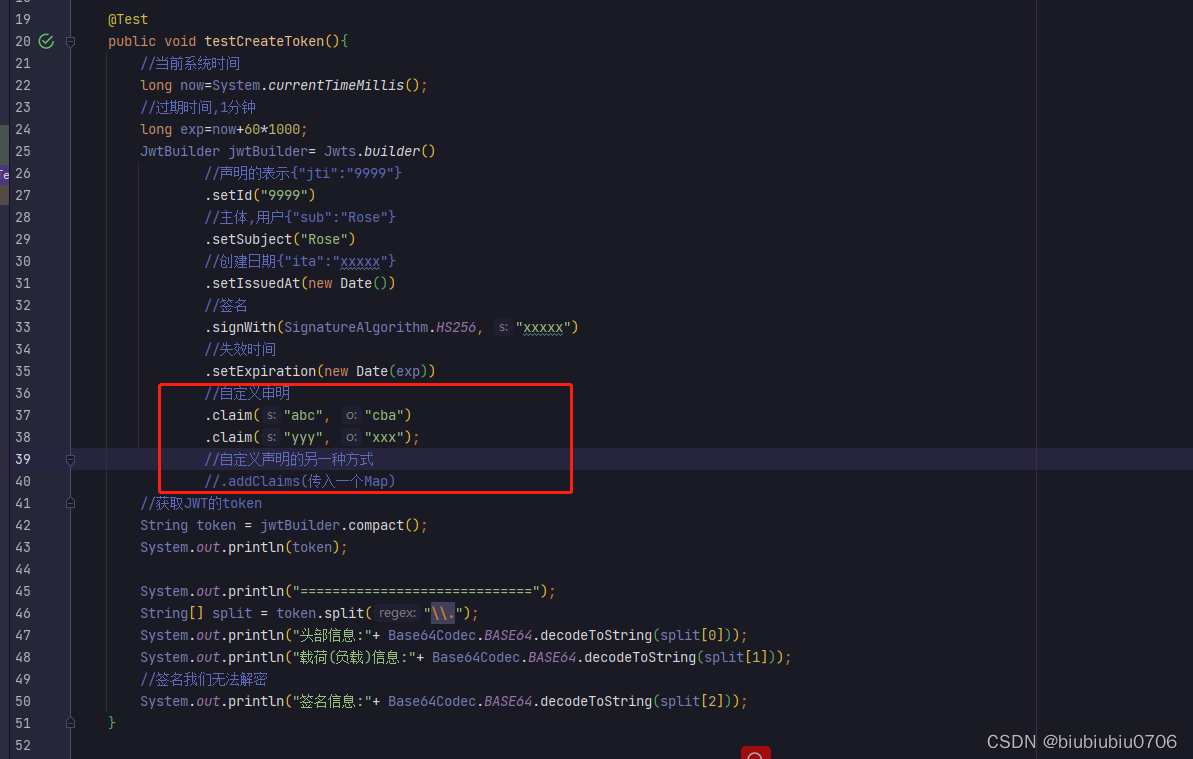
创建token

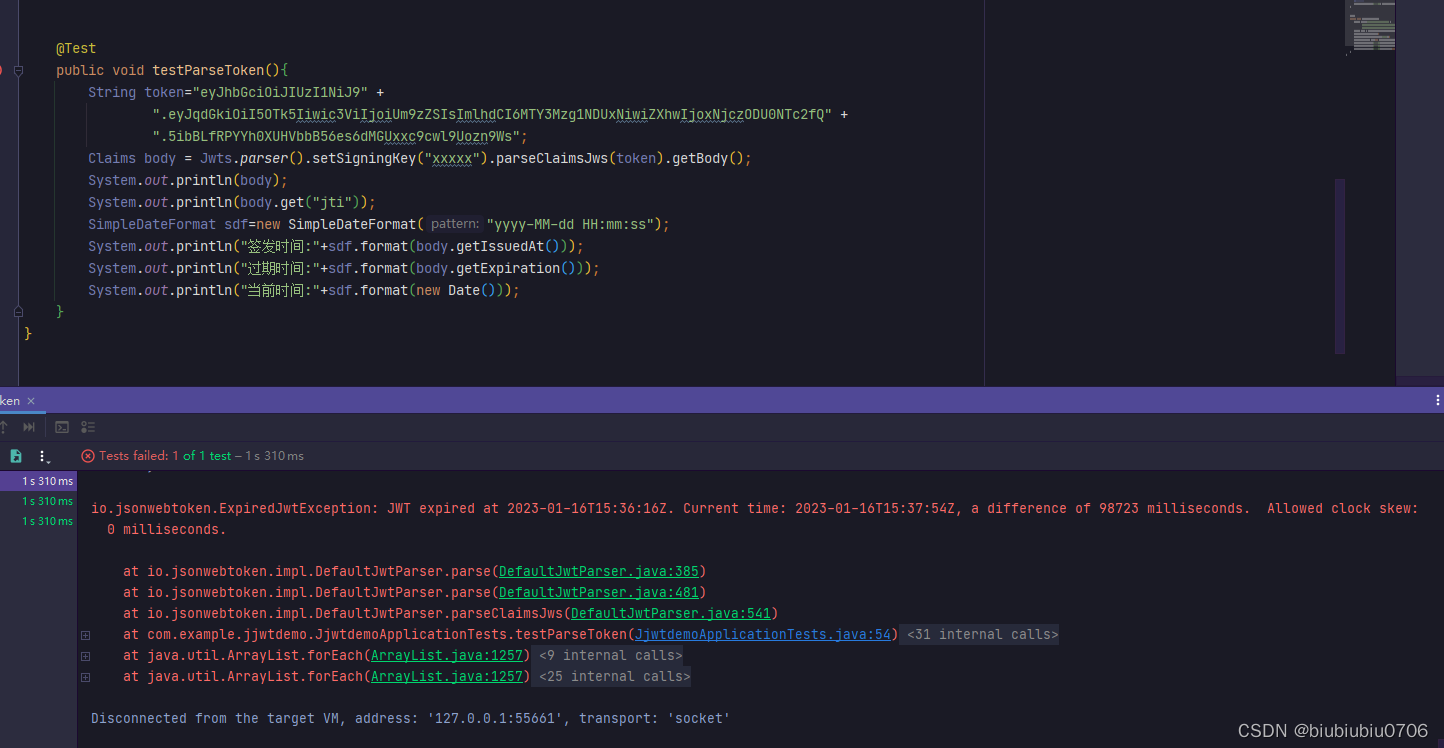
解析token

校验token失效

失效后
 关于自定义声明
关于自定义声明
SpringSecurityOauth2整合JWT(用原来那个demo)
原先我们用的accessToken放到了Redis里面,现在不用了,用JWT
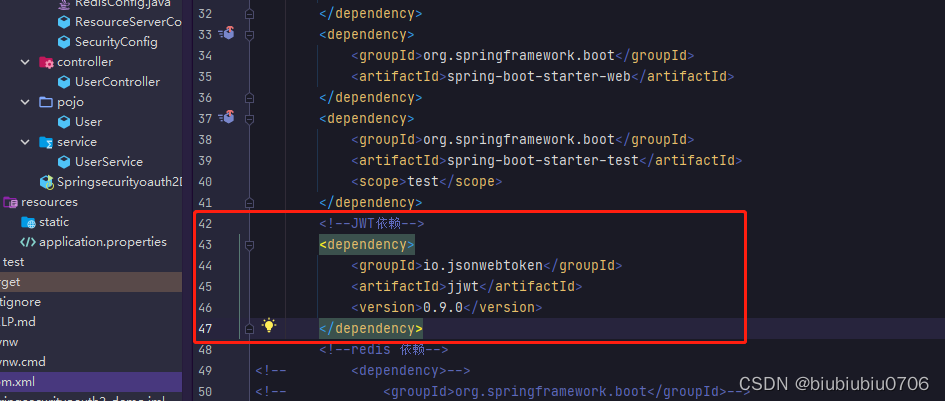
因此Redis依赖可以注释掉
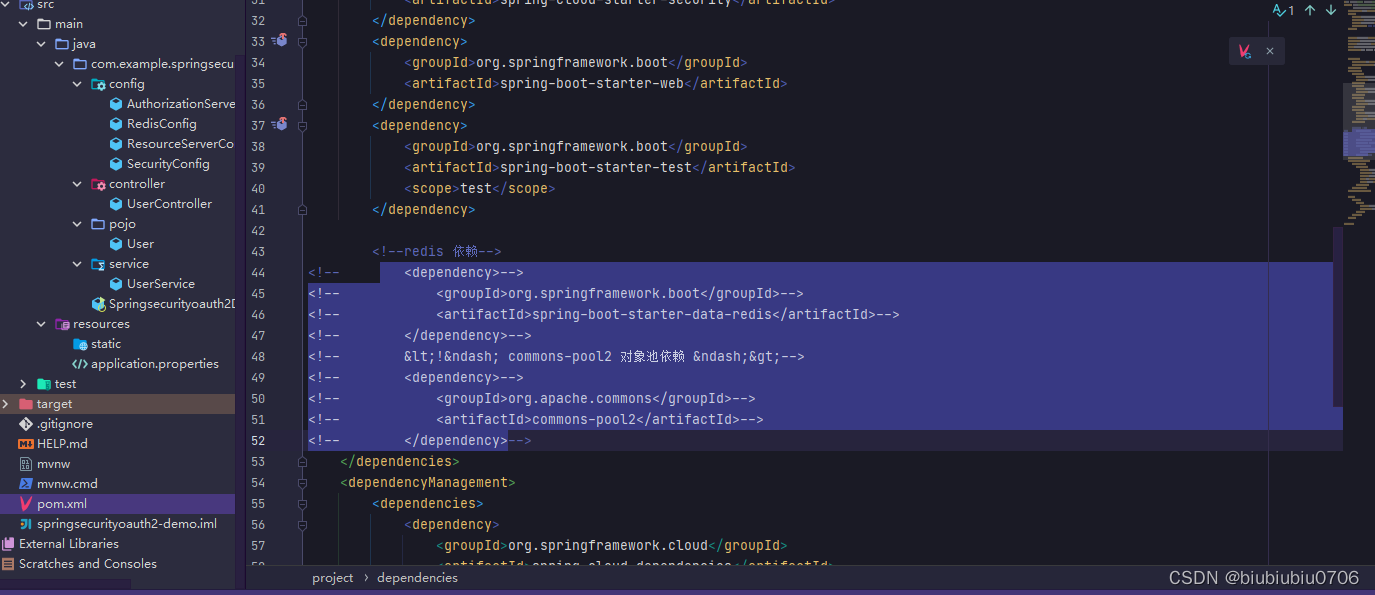
properties里Redis配置也去掉
 RedisConfig注释掉
RedisConfig注释掉
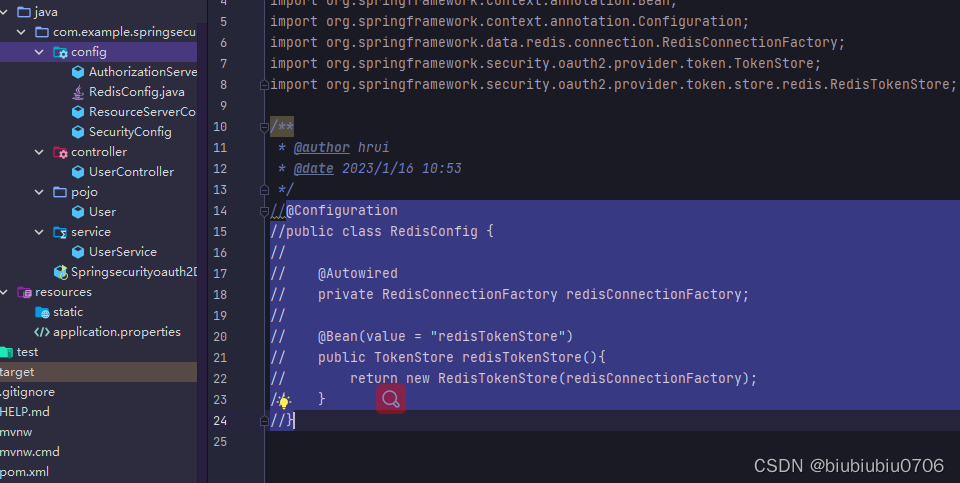
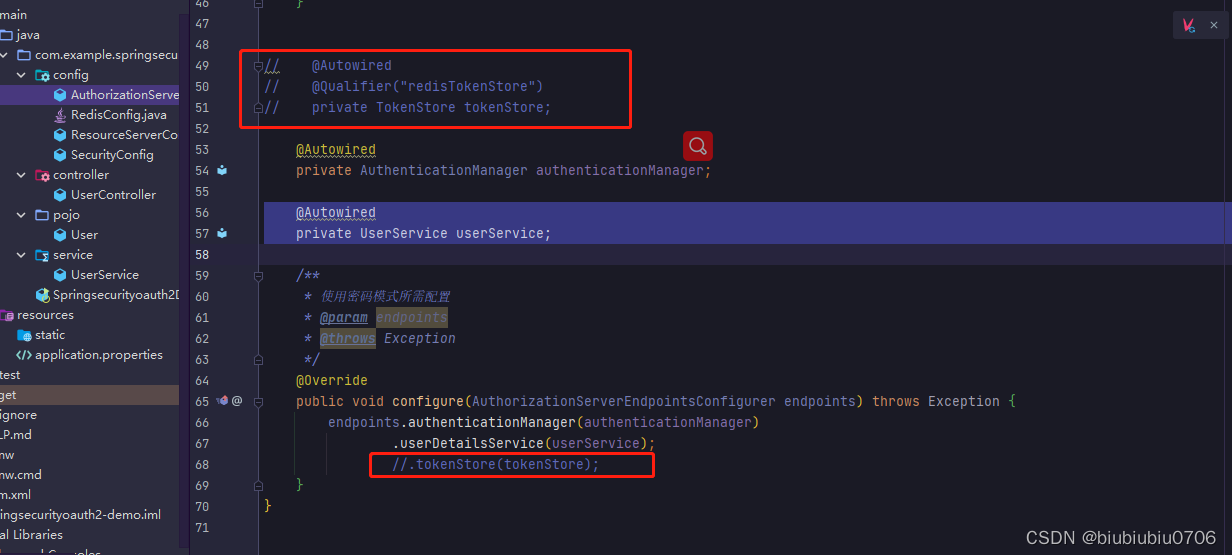
配置JwtToken




解析
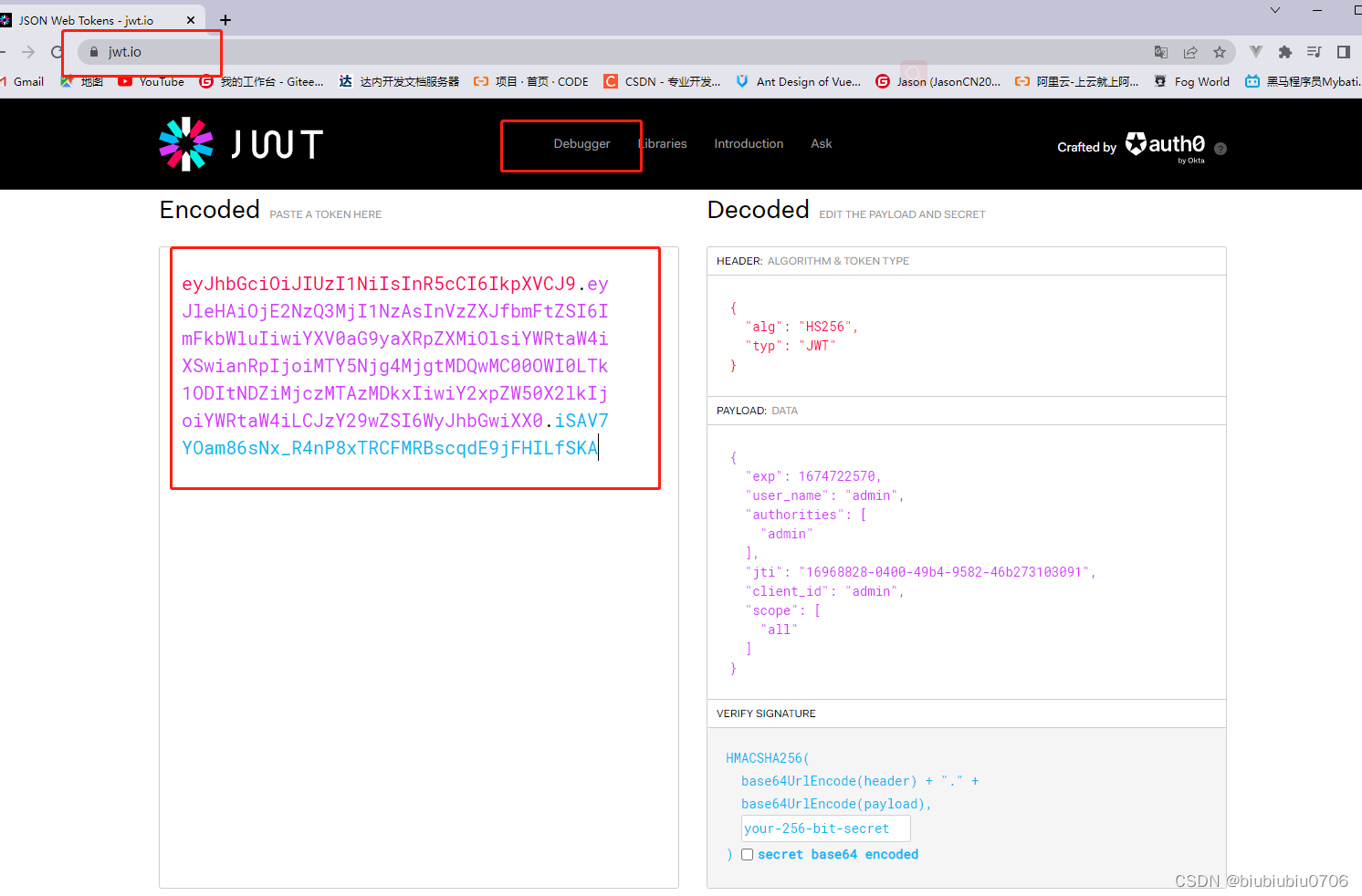
扩展JwtToken中的内容(自定义声明)




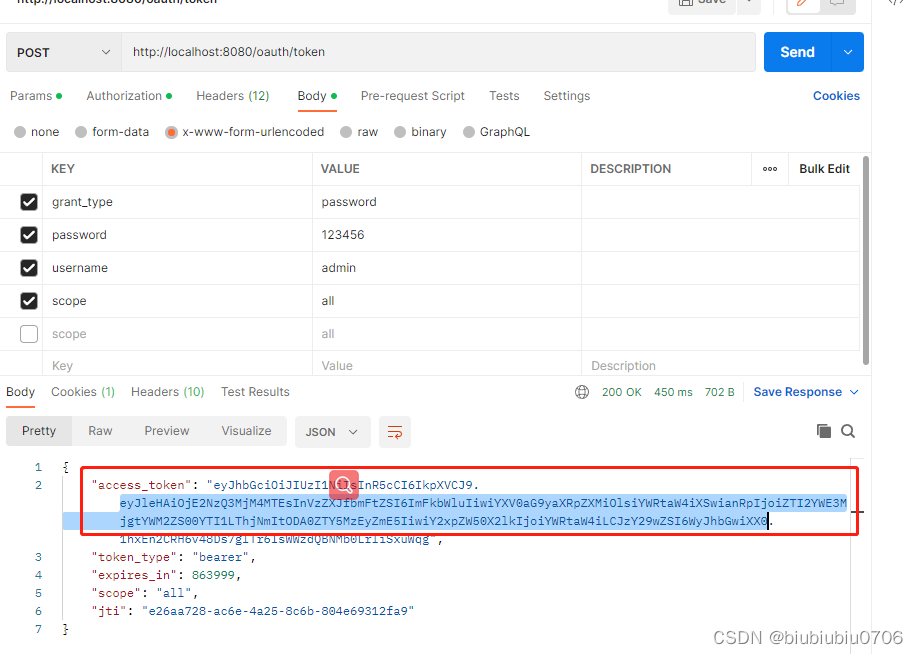

解析JWT中的内容
添加依赖