→b站直通车,感谢大佬←
→eNSP中小型园区网络拓扑搭建(上)←
不带配置命令的拓扑图已上传~

配置ospf
SW5
#
ospf 1 router-id 5.5.5.5
area 0.0.0.0
network 192.168.51.5 0.0.0.0
network 192.168.52.5 0.0.0.0
area 0.0.0.10
network 192.168.10.5 0.0.0.0
area 0.0.0.20
network 192.168.20.5 0.0.0.0
area 0.0.0.30
network 192.168.30.5 0.0.0.0
area 0.0.0.40
network 192.168.40.5 0.0.0.0
#
SW6
#
ospf 1 router-id 6.6.6.6
area 0.0.0.0
network 192.168.61.6 0.0.0.0
network 192.168.62.6 0.0.0.0
area 0.0.0.10
network 192.168.10.6 0.0.0.0
area 0.0.0.20
network 192.168.20.6 0.0.0.0
area 0.0.0.30
network 192.168.30.6 0.0.0.0
area 0.0.0.40
network 192.168.40.6 0.0.0.0
#
AR1
#
ospf 1 router-id 1.1.1.1
area 0.0.0.0
network 192.168.12.1 0.0.0.0
network 192.168.13.1 0.0.0.0
network 192.168.18.1 0.0.0.0
network 192.168.51.1 0.0.0.0
network 192.168.52.1 0.0.0.0
#
AR2
#
ospf 1 router-id 2.2.2.2
area 0.0.0.0
network 192.168.12.2 0.0.0.0
network 192.168.23.2 0.0.0.0
network 192.168.28.2 0.0.0.0
network 192.168.61.2 0.0.0.0
network 192.168.62.2 0.0.0.0
#
AR3
#
ospf 1 router-id 3.3.3.3
default-route-advertise always
area 0.0.0.0
network 192.168.13.3 0.0.0.0
network 192.168.23.3 0.0.0.0
#
SW8
#
ospf 1 router-id 8.8.8.8
area 0.0.0.0
network 192.168.18.8 0.0.0.0
network 192.168.28.8 0.0.0.0
area 0.0.0.100
network 192.168.100.8 0.0.0.0
#
PC连通性测试
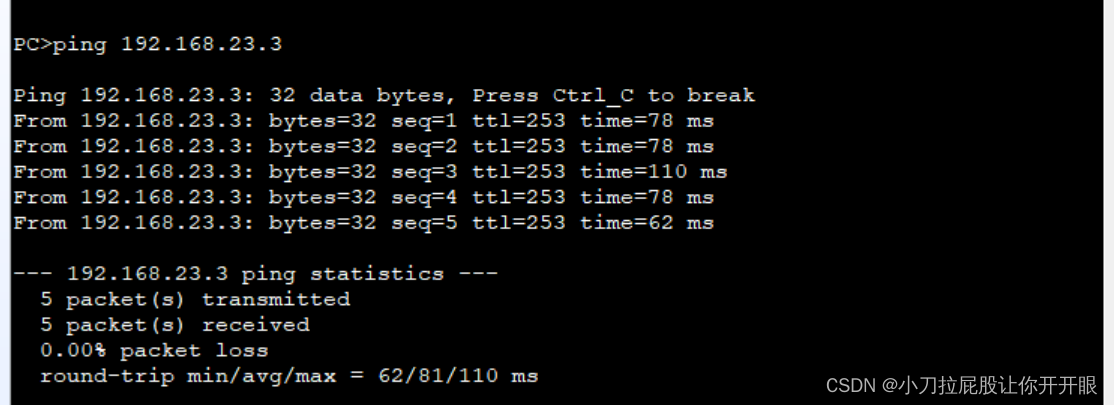
配置出口默认路由
#
ip route-static 0.0.0.0 0.0.0.0 123.123.123.4 preference 120
ip route-static 0.0.0.0 0.0.0.0 123.123.124.4
#
配置ACL+NAT
出口配置动态nat,访客部、市场部、行政部可访问internet
#
acl number 2000
rule 5 permit source 192.168.10.0 0.0.0.255
rule 10 permit source 192.168.20.0 0.0.0.255
rule 15 permit source 192.168.30.0 0.0.0.255
#
[AR3-GigabitEthernet0/0/0]nat outbound 2000
[AR3-GigabitEthernet4/0/0]nat outbound 2000
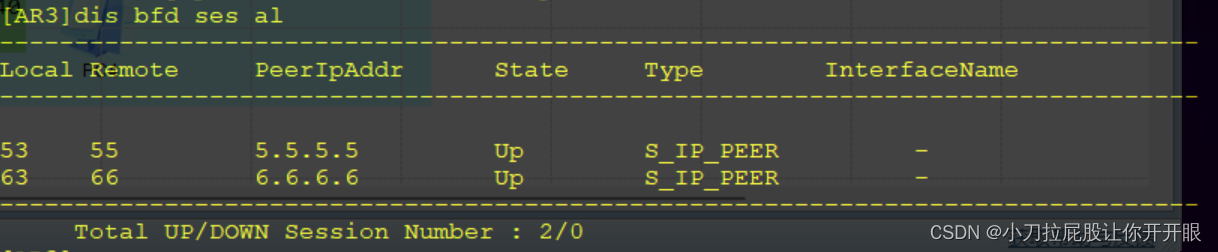
配置bfd
AR3
[AR3]bfd
#
interface LoopBack0
ip address 3.3.3.3 255.255.255.255
#
bfd tosw5 bind peer-ip 5.5.5.5 source-ip 3.3.3.3
discriminator local 53
discriminator remote 55
min-tx-interval 100
min-rx-interval 100
commit
#
bfd tosw6 bind peer-ip 6.6.6.6 source-ip 3.3.3.3
discriminator local 63
discriminator remote 66
min-tx-interval 100
min-rx-interval 100
commit
#
//lo口宣告进ospf area0
[AR3-ospf-1-area-0.0.0.0]net 3.3.3.3 0.0.0.0
AR5
[SW5]bfd
#
interface LoopBack0
ip address 5.5.5.5 255.255.255.255
#
bfd tor3 bind peer-ip 3.3.3.3 source-ip 5.5.5.5
discriminator local 55
discriminator remote 53
min-tx-interval 100
min-rx-interval 100
commit
#
//lo口宣告进ospf area0
[SW5-ospf-1-area-0.0.0.0]net 5.5.5.5 0.0.0.0
[SW5-Vlanif10]vrrp vrid 10 track bfd-session 55 reduced 30
[SW5-Vlanif20]vrrp vrid 20 track bfd-session 55 reduced 30
[SW5-Vlanif30]vrrp vrid 30 track bfd-session 55 reduced 30
AR6
[SW6]bfd
#
interface LoopBack0
ip address 6.6.6.6 255.255.255.255
#
bfd tor3 bind peer-ip 3.3.3.3 source-ip 6.6.6.6
discriminator local 66
discriminator remote 63
min-tx-interval 100
min-rx-interval 100
commit
#
//lo口宣告进ospf area0
[SW6-ospf-1-area-0.0.0.0]net 6.6.6.6 0.0.0.0
[SW5-Vlanif40]vrrp vrid 40 track bfd-session 66 reduced 30
进行调优防护
二层安全
- 在二层网络中确保根桥位置不被抢占(根防护)
SW5、SW6
[SW5]port-group 1
[SW5-port-group-1]group-member g0/0/1 to g0/0/4
[SW5-port-group-1]stp root-protection
- 连接终端的接口要快速进入转发状态(边缘端口)
SW1~4
[SW1-GigabitEthernet0/0/1]stp edged-port en
- 确保连接终端接口不能接受处理budu(bpdu防护)
SW1~4
[SW1]stp bpdu-protection
- 为抵御mac范洪攻击,需要在交换机上限制学习mac地址的数量(端口安全)
SW1~4
[SW1-GigabitEthernet0/0/1]port-security en
[SW1-GigabitEthernet0/0/1]port-security max-mac-num 100
三层安全
- 仅允许访客区可以访问Internet,不允许访问其他任何部门
SW1
#
acl number 3001
rule 5 deny ip destination 192.168.20.0 0.0.0.255
rule 10 deny ip destination 192.168.30.0 0.0.0.255
rule 15 deny ip destination 192.168.40.0 0.0.0.255
#
[SW1-GigabitEthernet0/0/1]traffic-filter inbound acl 3001
- 市场部与行政部之间可以互相访问,但不允许访问研发部
- 研发部作为公司核心部门,掌握公司核心数据,仅允许其访问FTP服务器,不允许其 访问其他部门和访问Internet
SW4
#
acl number 3001
rule 5 deny ip destination 192.168.30.0 0.0.0.255
rule 10 deny ip destination 192.168.20.0 0.0.0.255
#
[SW4-GigabitEthernet0/0/1]traffic-filter inbound acl 3001
SW8
#
acl number 3001
rule 5 permit ip source 192.168.40.0 0.0.0.255
rule 10 deny ip
#
[SW8-GigabitEthernet0/0/1]traffic-filter outbound acl 3001







![[AutoSar]BSW_Diagnostic_002 DCM模块介绍](https://img-blog.csdnimg.cn/direct/ac80931da2dc41cda9c6bc3a85cca59a.png)