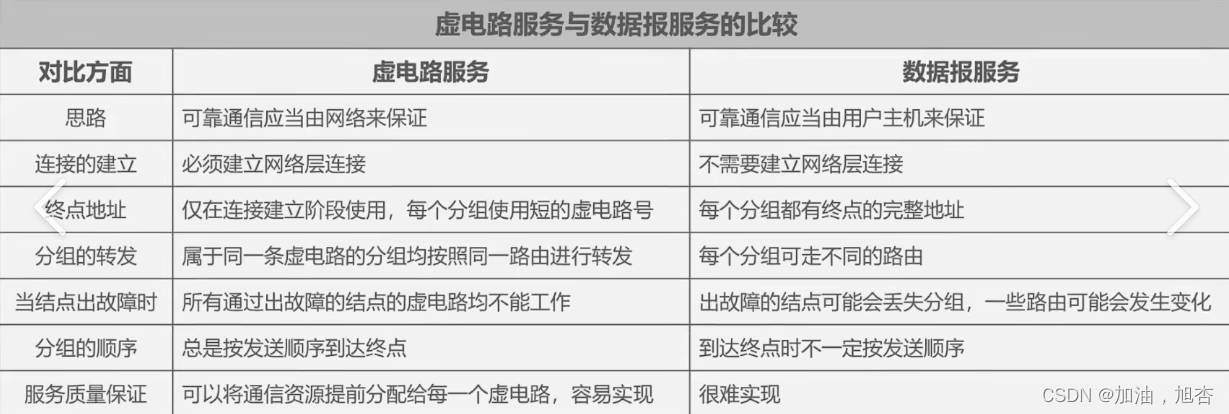
**验证步骤:**
# 终端随机生成一对RSA key pair pem文件
# 终端把sn及公钥发过去
# KIF返回公钥加密后的IPEK及明文IPEK的KCV (加密机处理加密等操作:把sn和Base Derivation Key分散生成IPEK用加密机的Local Master Key存入加密机,加密机再用公钥加密 用LMK解出来的IPEK 和 明文IPEK的KCV)
# 终端用私钥解密出IPEK明文
# 终端计算IPEK明文的KCV (3DES 对全0加密) 与发过来的KCV对比一致即OK。存入终端。
随机生成一对RSA key pair pem文件
-----BEGIN PRIVATE KEY-----
MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQC3W78rWYRcMiV7
dcj0iIg4gptJeT9wGZPTCtI2BXEsYxj33SVI0K3R4JPtclV4DfSIK3kuLuKzf3hL
BcvuMwlcZvLTUsTy/Ac5RE64Dhag8g2RQ4Q7ikBdgbws0W5ZuZFXuL8fGgI1K4Qf
25jlVx6VVfJVPT80JaYJcN/3R++XxXNZ/CSskobsXAuuoOwto5p/0EBljsr2LPqH
VSl/7OzfSPfacAxQWEXC7Sm91nNWtyKqYbU1k0FqehKCIxCWq6dr6aSizeRHjS3N
JFiynLBA7z0RKeC/fhdAHmeNtCRXMG35YgF+EfVtwangqYe/YYBv4jeYzAcD/gUo
JVbklRtLAgMBAAECggEAB/bBrmHUeGarLxoWENzvQbkWgpH0GevaelOhfrwsxrdF
KdremDOMIS4Gbs1E/hJpGRL+T+20ZgR21pdZXK61zOAh0uDo8f7VV3zqiF8AR5xL
z4/lqepe0lDkufOcvePr9qntDy5Dg0ixE+snUGrAxs61WFNxL9QkyosvByAGPYrA
kB4asMBzDu7QMfakB5Ygy/Nl5NQipYnKZRt3tWKtBeIfAjxeLml2aS+6cnM8Nqq6
42Lvfxf+slKFI5M8HZHBMJVF7bvAvnKa9hH6MvQ3tHxYaqqwpiID+n5i/A2lvQUY
z5nB+uWS2ruBiQI4dhJ+YZJvtOeCqRQkpA+Al60oBQKBgQDp7po4xPdoDhKyG5eJ
xbZpI9mqPZNdTk6qVXZKda+3VP+TPDGyGzf5qARLptKUgKmSmoKn+NC9OpeDveyC
4o3PLJSEJLwlN4YBH7YiAIXKNkRhSldovQyoUJNb9/+YqrFt3QfpNnl7DNX+Ntzz
YKkibInOeaHfNchJF/Oo2godhwKBgQDIp83FVeYNs4iylctf9RC6Rzc4BNCfGriX
brlXBsl4lNdR+DCOB6atFizvs3xS3HGFQmK6In/ktCjvcCKdo8KVFJ3iHzduX3RG
HQAb5rV8FHc+nTe1C98ZXJn59oIn4Dk54FBraSL0kp9KqsPy0gVbFZLX5BpSM6yb
5KcThErlHQKBgB9oYJ5km48F7K6rE7J0sCP3oz6/G6z4WYl3BfXDTT9BEztSZp2y
F9bWHxWFJVq414uOYSJqPqRZXIRcmIeOIVoCc0I2qGgax0wZVNvF1DCtDos9bvTq
BOwIPXCooFGAAWhtt6UxIihKNeT2ur2Wab7scageHoSYdPaTV6yA8cC7AoGAL8NB
x+dai4hg0aG2d3DuOmkZS8xZnIXPyrwgggarjnhfiLN7W1OW6TyOFcCzp0Wx//Z9
abEsoFQCKnyWwM9qUfJGYrzrhOpT0xy0GfAg4xg8CjuCNyZMRM02GboD4VoORSiP
/AFawLzmDe/4FKTJgZTxD1LMsSR7wd/7pTmoWkECgYEAxBexT+wP17G5cgML2mfc
t/ocLM15cOfm/oScC8groH8axm//6zghZASO4kt0xxpy9rhZnX92+6l+IsNgwBRn
5MZ/CDPp2k7M4teZzyS6hWaMNniPj97HbcKo7hy8kQBUsLtwqy8GlLE2LQQK4Fwc
nEQ5elAzAyvYMBOlqezithE=
-----END PRIVATE KEY-----
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAt1u/K1mEXDIle3XI9IiI
OIKbSXk/cBmT0wrSNgVxLGMY990lSNCt0eCT7XJVeA30iCt5Li7is394SwXL7jMJ
XGby01LE8vwHOUROuA4WoPINkUOEO4pAXYG8LNFuWbmRV7i/HxoCNSuEH9uY5Vce
lVXyVT0/NCWmCXDf90fvl8VzWfwkrJKG7FwLrqDsLaOaf9BAZY7K9iz6h1Upf+zs
30j32nAMUFhFwu0pvdZzVrciqmG1NZNBanoSgiMQlquna+mkos3kR40tzSRYspyw
QO89ESngv34XQB5njbQkVzBt+WIBfhH1bcGp4KmHv2GAb+I3mMwHA/4FKCVW5JUb
SwIDAQAB
-----END PUBLIC KEY-----
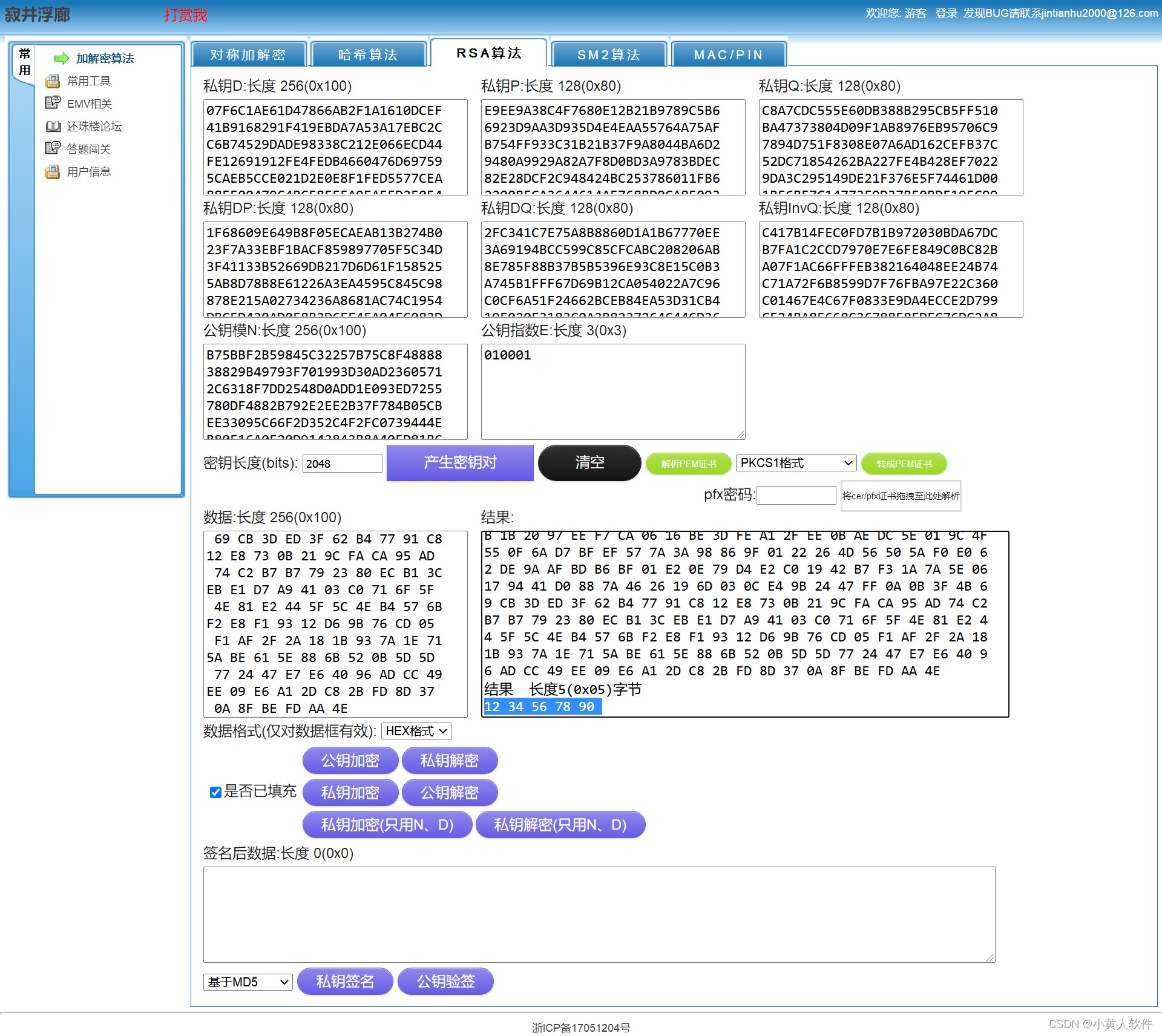
用公钥pem文件加密12 34 56 78 90得到密文
98 3F F5 80 0D 0A 99 3F B5 80 91 4D A8 E3 C5 92 98 B9 5C 4F BE 1F E9 2A 18 AF 76 18 C5 BE 51 73 F5 53 C7 CC 1A AE ED 95 A7 4B 78 4C C9 01 52 53 27 85 28 1F 13 EB A8 BE C1 AE A0 31 59 00 35 76 8B 1B 20 97 EE F7 CA 06 16 BE 3D FE A1 2F EE 0B AE DC 5E 01 9C 4F 55 0F 6A D7 BF EF 57 7A 3A 98 86 9F 01 22 26 4D 56 50 5A F0 E0 62 DE 9A AF BD B6 BF 01 E2 0E 79 D4 E2 C0 19 42 B7 F3 1A 7A 5E 06 17 94 41 D0 88 7A 46 26 19 6D 03 0C E4 9B 24 47 FF 0A 0B 3F 4B 69 CB 3D ED 3F 62 B4 77 91 C8 12 E8 73 0B 21 9C FA CA 95 AD 74 C2 B7 B7 79 23 80 EC B1 3C EB E1 D7 A9 41 03 C0 71 6F 5F 4E 81 E2 44 5F 5C 4E B4 57 6B F2 E8 F1 93 12 D6 9B 76 CD 05 F1 AF 2F 2A 18 1B 93 7A 1E 71 5A BE 61 5E 88 6B 52 0B 5D 5D 77 24 47 E7 E6 40 96 AD CC 49 EE 09 E6 A1 2D C8 2B FD 8D 37 0A 8F BE FD AA 4E
用私钥pem文件解密得到明文
测试RSA密钥对OK
公钥发过去(就是上面pem格式 ascii)
返回公钥加密后的IPEK及明文IPEK的KCV

用私钥解密出IPEK明文

计算IPEK明文的KCV (3DES 对全0加密) 与发过来的KCV对比一致即OK。
解密出明文IPEK:B6A9337BCF5757FA208B687B71AF5B1F
明文IPEK的KCV:43A01EF7164D7E92