一、KunLun-M简介
KunLun-M是一个完全开源的静态白盒扫描工具,支持PHP、JavaScript的语义扫描,基础安全、组件安全扫描,Chrome Ext\Solidity的基础扫描。开源地址:https://github.com/LoRexxar/Kunlun-M
Cobra是一款源代码安全审计工具,支持检测多种开发语言源代码中的大部分显著的安全问题和漏洞。 GitHub - FeeiCN/Cobra: Source Code Security Audit (源代码安全审计)
Cobra-W是从Cobra2.0发展而来的分支,将工具重心从尽可能的发现威胁转变为提高发现漏洞的准确率以及精度。 https://github.com/LoRexxar/Kunlun-M/tree/cobra-w
Kunlun-Mirror是从Cobra-W2.0发展而来,在经历了痛苦的维护改进原工具之后,昆仑镜将工具的发展重心放在安全研究员的使用上,将会围绕工具化使用不断改进使用体验。
目前工具主要支持php、javascript的语义分析,以及chrome ext, solidity的基础扫描.
KunLun-M(昆仑镜)已进入弱维护阶段,如果有bug或者明显的问题会更新,但不会再更新新功能,主要是我认为Kunlun-M的架构拖累了后续的发展方向,仅在PHP扫描中以当前的架构已经几乎做到极限了,后续可能会有新的工具?也可能没有?敬请期待~
请使用python3.6+运行该工具,已停止维护python2.7环境
二、特点
与其他代码审计相比:
-
静态分析,环境依赖小。
-
语义分析,对漏洞有效性判断程度更深。
-
多种语言支持。
-
开源python实现,更易于二次开发。
与Cobra相比:
-
深度重写AST,大幅度减少漏洞误报率。
-
底层api重写,支持windows、linux等多平台。
-
多层语义解析、函数回溯,secret机制,新增多种机制应用于语义分析。
-
新增javascript语义分析,用于扫描包含js相关代码。
与Cobra-W相比(todo):
-
深度优化AST分析流程,使其更符合QL的概念,便于下一阶段的优化。
-
深度优化辅助审计的流程,使其更符合人类安全研究员审计辅助的习惯。
-
深度重构代码结构,使其更符合可拓展,可优化的开源理念。
三、安装
3.1 源码安装
3.1.1 下载源代码
D:\opt>git clone https://github.com/LoRexxar/Kunlun-M.git
Cloning into 'Kunlun-M'...
remote: Enumerating objects: 12076, done.
remote: Counting objects: 100% (1175/1175), done.
remote: Compressing objects: 100% (398/398), done.
remote: Total 12076 (delta 819), reused 1106 (delta 777), pack-reused 10901
% (12076/12076), 16.14 MiB | 53.00 KiB/s
Receiving objects: 100% (12076/12076), 16.16 MiB | 37.00 KiB/s, done.
Resolving deltas: 100% (4295/4295), done.3.1.2 安装依赖
cd Kunlun_M
pip3 install -r requirements.txt
#使用清华源
pip3 install -r requirements.txt -i https://pypi.tuna.tsinghua.edu.cn/simple/3.1.3 配置文件迁移
#linux系统
cp Kunlun_M/settings.py.bak Kunlun_M/settings.py
#windows系统
copy Kunlun_M\settings.py.bak Kunlun_M\settings.py3.1.4 初始化数据库,默认采用sqlite作为数据库
python kunlun.py init initialize
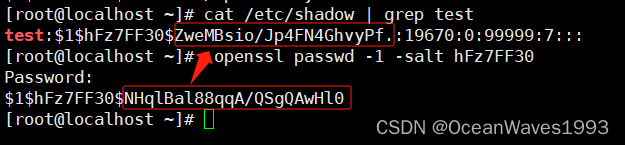
#注意不能用python3 kunlun.py init initialize3.1.5 加载规则进数据库
注意:每次修改规则文件都需要加载
python kunlun.py config load3.2 docker安装
sudo docker build -t kunlun-m -f ./docker/Dockerfile .四、使用方法
4.1 命令行模式
4.1.1 使用scan模式扫描各类源代码
python kunlun.py scan -t ./tests/vulnerabilities/D:\opt\Kunlun-M>python kunlun.py scan -t ./tests/vulnerabilities/
D:\opt\Kunlun-M
[15:30:35] [INIT] start Scan Task...
[15:30:35] [INIT] set logging level: 10
[15:30:35] [INIT] ScanTask for vulnerabilities has been executed.
[15:30:35] [INIT] whether rescan Task vulnerabilities?(Y/N) (Default N)
[15:30:44] TaskID: 2
[15:30:44] [INIT] New Log file ScanTask_2.log .
[15:30:44] [INIT] Vendor Vuls Scan Status: True
[15:30:44] [INIT][IGNORE] New ignore regex \.crx_files
[15:30:44] [INIT][IGNORE] New ignore regex [\/\\]vendor[\/\\]
[15:30:44] [INIT][IGNORE] New ignore regex [\/\\]\.idea[\/\\]
[15:30:44] [INIT][IGNORE] New ignore regex [\/\\]static[\/\\]
[15:30:44] [PARSE-ARGS] Target Mode: folder
[15:30:44] [PARSE-ARGS] Output Mode: stream
[15:30:44] [CLI] Target Mode: folder
[15:30:44] [PARSE-ARGS] target directory: ./tests/vulnerabilities/
[15:30:44] [CLI] Target : D:\opt\Kunlun-M\tests\vulnerabilities/
[15:30:44] [PICKUP] D:\opt\Kunlun-M\tests\vulnerabilities/
[15:30:44] [PICKUP] [FILES] |--v.p12
[15:30:44] [PICKUP] [FILES] |--v.php
[15:30:44] [PICKUP] [FILES] |--v_parser.php
-------------------------------------------------------------------------
[15:30:47] [Chain] Vul 20
[15:30:47] [SCAN] ending
-------------------------------------------------------------------------
[15:30:47] [SCAN] Trigger Vulnerabilities (20)
+----+-------+-------------------------+-------------+----------+-------------------------+-------------------+------------------------------------------+-----------------------------+
| # | CVI | Rule(ID/Name) | Lang/CVE-id | Level | Target-File:Line-Number | Commit(Author) | Source Code Content | Analysis |
+----+-------+-------------------------+-------------+----------+-------------------------+-------------------+------------------------------------------+-----------------------------+
| 1 | 1000 | Reflected XSS | php | medium | v.php:58 | LoRexxar/wufeifei | print("Hello " . $cmd) | Function-param-controllable |
| 2 | 1000 | Reflected XSS | php | medium | v_parser.php:7 | LoRexxar/wufeifei | print(system(trim('ls'.$_GET['test']))) | Function-param-controllable |
| 3 | 10002 | Reflected XSS | php | medium | v.php:10 | LoRexxar | echo($callback . "; | Function-param-controllable |
| 4 | 10002 | Reflected XSS | php | medium | v.php:55 | LoRexxar | echo get_headers($url,1); | Function-param-controllable |
| 5 | 10002 | Reflected XSS | php | medium | v.php:58 | LoRexxar | print("Hello " . $cmd); | Function-param-controllable |
| 6 | 10002 | Reflected XSS | php | medium | v.php:121 | LoRexxar | echo "a".$a; | Function-param-controllable |
| 7 | 10002 | Reflected XSS | php | medium | v_parser.php:7 | LoRexxar | print(system(trim('ls'.$_GET['test']))); | Function-param-controllable |
| 8 | 1001 | SSRF | php | medium | v.php:44 | LoRexxar/wufeifei | curl($cmd) | Vustomize-Match |
| 9 | 1002 | SSRF | php | medium | v.php:50 | LoRexxar/wufeifei | file_get_contents($url) | Function-param-controllable |
| 10 | 1004 | SQLI | php | high | v.php:77 | LoRexxar/wufeifei | "select name from users where id =$id"; | Vustomize-Match |
| 11 | 1007 | RFI | php | high | v.php:81 | LoRexxar/wufeifei | require_once($cmd) | Function-param-controllable |
| 12 | 1008 | Xml injection | php | medium | v.php:101 | LoRexxar/wufeifei | simplexml_load_string($xml) | Function-param-controllable |
| 13 | 1009 | RCE | php | critical | v.php:19 | LoRexxar/wufeifei | eval($cmd) | Function-param-controllable |
| 14 | 1011 | RCE | php | critical | v.php:20 | LoRexxar/wufeifei | system('ls' + $cmd) | Function-param-controllable |
| 15 | 1011 | RCE | php | critical | v_parser.php:7 | LoRexxar/wufeifei | system(trim('ls'.$_GET['test']))) | Function-param-controllable |
| 16 | 1012 | Information Disclosure | php | low | v.php:84 | LoRexxar/wufeifei | highlight_file($cmd) | Function-param-controllable |
| 17 | 1013 | URL Redirector Abuse | php | low | v.php:94 | LoRexxar/wufeifei | header("Location: ".$url) | Function-param-controllable |
| 18 | 1014 | variable shadowing | php | high | v.php:12 | LoRexxar/wufeifei | extract($cmd) | Function-param-controllable |
| 19 | 1015 | unserialize vulerablity | php | medium | v.php:98 | LoRexxar/wufeifei | unserialize($test) | Function-param-controllable |
| 20 | 5001 | 硬编码密码 | base | low | v.php | LoRexxar | password = $_POST[' | Regex-only-match |
+----+-------+-------------------------+-------------+----------+-------------------------+-------------------+------------------------------------------+-----------------------------+
[15:30:47] [MainThread] New evil Function list by NewCore:
+---+-------------+-----------------+------------------+
| # | NewFunction | OriginFunction | Related Rules id |
+---+-------------+-----------------+------------------+
| 1 | curl | ['curl_setopt'] | 1001 |
| 2 | curl | ['curl_setopt'] | 1001 |
+---+-------------+-----------------+------------------+
[15:30:47] [EXPORT] No filename given, save into default path(result/).
[15:30:47] [EXPORT] Scan result exported successfully: D:\opt\Kunlun-M\result\vulnerabilities.csv
[15:30:47] [INIT] Done! Consume Time:11.81710433959961s4.1.2 使用config模式加载本地的rule/tamper
python kunlun.py config load # 加载rule进数据库
python kunlun.py config recover # 将数据库中的rule恢复到文件
python kunlun.py config loadtamper # 加载tamper进数据库
python kunlun.py config retamper # 将数据库中的tamper恢复到文件使用show模式查看目前的所有rule/tamper
python kunlun.py show rule # 展示所有的rule
python kunlun.py show rule -k php # 展示所有php的rule
python kunlun.py show tamper # 展示所有的tamper4.2 web页面模式
KunLun-M Dashbroad,并且允许通过apitoken来访问api获取数据,默认9999端口。
4.2.1 启动命令
python .\kunlun.py web -p 9999
[16:09:51] Start KunLun-M Web in Port: 9999
Watching for file changes with StatReloader
November 09, 2023 - 16:09:51
Django version 4.2.7, using settings 'Kunlun_M.settings'
Starting development server at http://127.0.0.1:9999/
Quit the server with CTRL-BREAK.4.2.2 浏览器访问http://127.0.0.1:9999/
4.2.3 注册账号
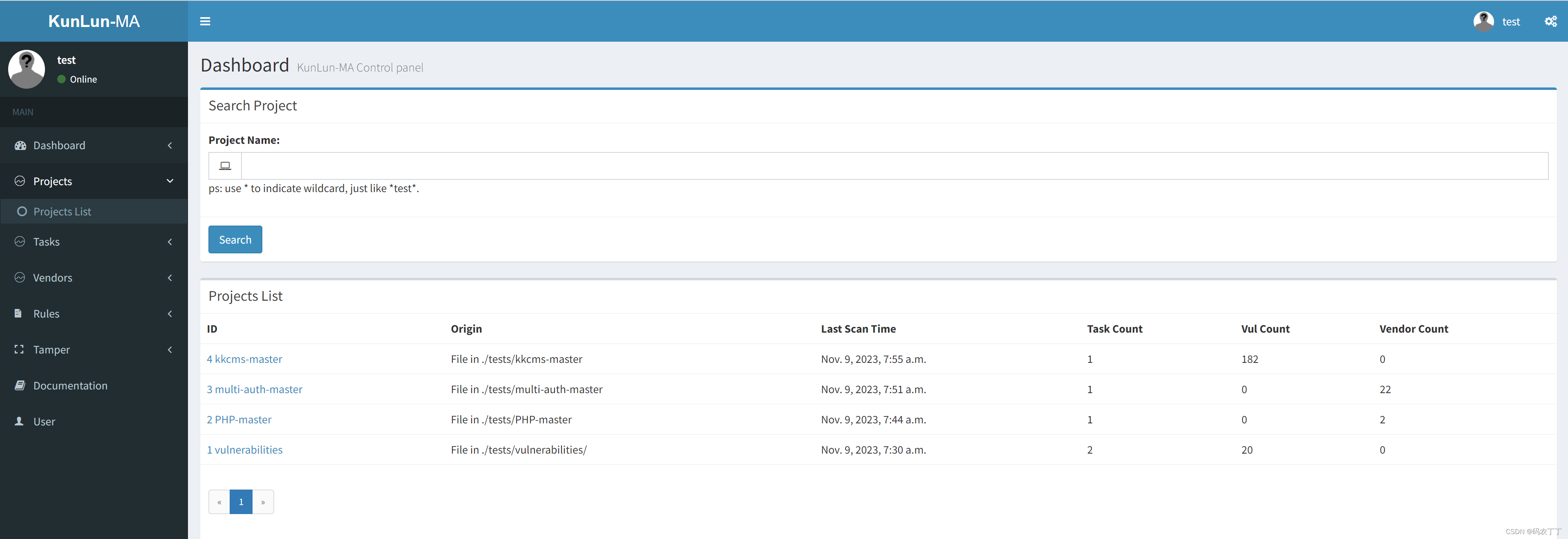
4.2.4 功能界面





![文件包含 [ZJCTF 2019]NiZhuanSiWei1](https://img-blog.csdnimg.cn/b7e62b4fb0f34c8bb28efaef82e61a14.png)