接前一篇文章:PAM从入门到精通(二十一)
本文参考:
《The Linux-PAM Application Developers' Guide》
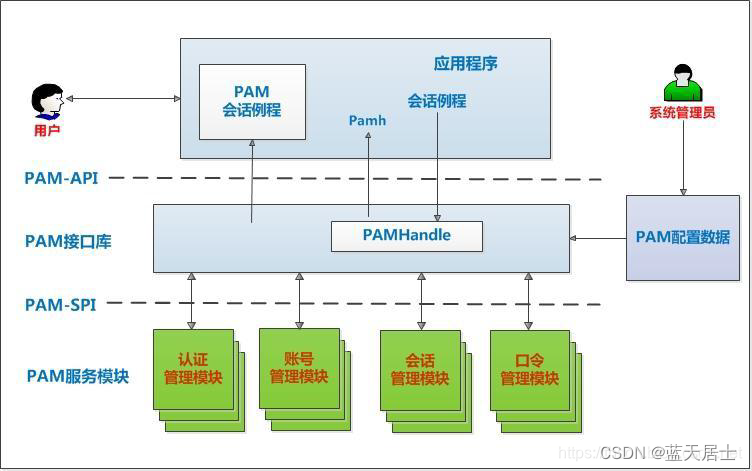
先再来重温一下PAM系统架构:

更加形象的形式:
七、PAM-API各函数源码详解
前边的文章讲解了各PAM-API函数以及总体流程,但是也只是从接口层面介绍的,并没有深入到代码层面。从本篇文章开始,将对于各个接口函数从源码级进行讲解,以使大家不但知其然,还要知其所以然。
1. pam_start函数
上回讲到_pam_start_internal函数的第二部分,本文继续往下进行讲解。为了便于理解,再次贴出_pam_start_internal函数源码。在libpam/pam_start.c中,如下所示:
static int _pam_start_internal (
const char *service_name,
const char *user,
const struct pam_conv *pam_conversation,
const char *confdir,
pam_handle_t **pamh)
{
D(("called pam_start: [%s] [%s] [%p] [%p]"
,service_name, user, pam_conversation, pamh));
if (pamh == NULL) {
pam_syslog(NULL, LOG_CRIT,
"pam_start: invalid argument: pamh == NULL");
return (PAM_SYSTEM_ERR);
}
if (service_name == NULL) {
pam_syslog(NULL, LOG_CRIT,
"pam_start: invalid argument: service == NULL");
return (PAM_SYSTEM_ERR);
}
if (pam_conversation == NULL) {
pam_syslog(NULL, LOG_CRIT,
"pam_start: invalid argument: conv == NULL");
return (PAM_SYSTEM_ERR);
}
if ((*pamh = calloc(1, sizeof(**pamh))) == NULL) {
pam_syslog(NULL, LOG_CRIT, "pam_start: calloc failed for *pamh");
return (PAM_BUF_ERR);
}
/* All service names should be files below /etc/pam.d and nothing
else. Forbid paths. */
if (strrchr(service_name, '/') != NULL)
service_name = strrchr(service_name, '/') + 1;
/* Mark the caller as the application - permission to do certain
things is limited to a module or an application */
__PAM_TO_APP(*pamh);
if (((*pamh)->service_name = _pam_strdup(service_name)) == NULL) {
pam_syslog(*pamh, LOG_CRIT,
"pam_start: _pam_strdup failed for service name");
_pam_drop(*pamh);
return (PAM_BUF_ERR);
} else {
char *tmp;
for (tmp=(*pamh)->service_name; *tmp; ++tmp)
*tmp = tolower(*tmp); /* require lower case */
}
if (user) {
if (((*pamh)->user = _pam_strdup(user)) == NULL) {
pam_syslog(*pamh, LOG_CRIT,
"pam_start: _pam_strdup failed for user");
_pam_drop((*pamh)->service_name);
_pam_drop(*pamh);
return (PAM_BUF_ERR);
}
} else
(*pamh)->user = NULL;
if (confdir) {
if (((*pamh)->confdir = _pam_strdup(confdir)) == NULL) {
pam_syslog(*pamh, LOG_CRIT,
"pam_start: _pam_strdup failed for confdir");
_pam_drop((*pamh)->service_name);
_pam_drop((*pamh)->user);
_pam_drop(*pamh);
return (PAM_BUF_ERR);
}
} else
(*pamh)->confdir = NULL;
(*pamh)->tty = NULL;
(*pamh)->prompt = NULL; /* prompt for pam_get_user() */
(*pamh)->ruser = NULL;
(*pamh)->rhost = NULL;
(*pamh)->authtok = NULL;
(*pamh)->oldauthtok = NULL;
(*pamh)->fail_delay.delay_fn_ptr = NULL;
(*pamh)->former.choice = PAM_NOT_STACKED;
(*pamh)->former.substates = NULL;
#ifdef HAVE_LIBAUDIT
(*pamh)->audit_state = 0;
#endif
(*pamh)->xdisplay = NULL;
(*pamh)->authtok_type = NULL;
(*pamh)->authtok_verified = 0;
memset (&((*pamh)->xauth), 0, sizeof ((*pamh)->xauth));
if (((*pamh)->pam_conversation = (struct pam_conv *)
malloc(sizeof(struct pam_conv))) == NULL) {
pam_syslog(*pamh, LOG_CRIT, "pam_start: malloc failed for pam_conv");
_pam_drop((*pamh)->service_name);
_pam_drop((*pamh)->user);
_pam_drop((*pamh)->confdir);
_pam_drop(*pamh);
return (PAM_BUF_ERR);
} else {
memcpy((*pamh)->pam_conversation, pam_conversation,
sizeof(struct pam_conv));
}
(*pamh)->data = NULL;
if ( _pam_make_env(*pamh) != PAM_SUCCESS ) {
pam_syslog(*pamh,LOG_ERR,"pam_start: failed to initialize environment");
_pam_drop((*pamh)->pam_conversation);
_pam_drop((*pamh)->service_name);
_pam_drop((*pamh)->user);
_pam_drop((*pamh)->confdir);
_pam_drop(*pamh);
return PAM_ABORT;
}
_pam_reset_timer(*pamh); /* initialize timer support */
_pam_start_handlers(*pamh); /* cannot fail */
/* According to the SunOS man pages, loading modules and resolving
* symbols happens on the first call from the application. */
if ( _pam_init_handlers(*pamh) != PAM_SUCCESS ) {
pam_syslog(*pamh, LOG_ERR, "pam_start: failed to initialize handlers");
_pam_drop_env(*pamh); /* purge the environment */
_pam_drop((*pamh)->pam_conversation);
_pam_drop((*pamh)->service_name);
_pam_drop((*pamh)->user);
_pam_drop((*pamh)->confdir);
_pam_drop(*pamh);
return PAM_ABORT;
}
D(("exiting pam_start successfully"));
return PAM_SUCCESS;
}接下来来到以下代码片段:
if (((*pamh)->service_name = _pam_strdup(service_name)) == NULL) {
pam_syslog(*pamh, LOG_CRIT,
"pam_start: _pam_strdup failed for service name");
_pam_drop(*pamh);
return (PAM_BUF_ERR);
} else {
char *tmp;
for (tmp=(*pamh)->service_name; *tmp; ++tmp)
*tmp = tolower(*tmp); /* require lower case */
}
_pam_strdum函数在libpam/pam_misc.c中,代码如下:
/*
* Safe duplication of character strings. "Paranoid"; don't leave
* evidence of old token around for later stack analysis.
*/
char *_pam_strdup(const char *x)
{
register char *new=NULL;
if (x != NULL) {
register int len;
len = strlen (x) + 1; /* length of string including NUL */
if ((new = malloc(len)) == NULL) {
len = 0;
pam_syslog(NULL, LOG_CRIT, "_pam_strdup: failed to get memory");
} else {
strcpy (new, x);
}
x = NULL;
}
return new; /* return the duplicate or NULL on error */
}综合这两段代码,实际的作用如下:
将经过处理后保留'/'之后的service_name,以实参的形式传入_pam_strdup函数。_pam_strdup函数一上来先判断x是否为空,只有不为空的情况下才进行进一步处理,否则直接返回NULL。
接下来看不为空时的处理:len得到的是包含字符串结束符'\0'的长度;之后分配len大小的内存空间,使new指向这段空间。如果分配失败,则将len置为0,并且给出错误提示信息"_pam_strdup: failed to get memory",并返回NULL;如果分配成功,则将x拷贝给new,即拷贝了一份service_name,并返回新分配的new指向的这段内存。
回到上边的调用代码片段:
if (((*pamh)->service_name = _pam_strdup(service_name)) == NULL) {
pam_syslog(*pamh, LOG_CRIT,
"pam_start: _pam_strdup failed for service name");
_pam_drop(*pamh);
return (PAM_BUF_ERR);
} else {
char *tmp;
for (tmp=(*pamh)->service_name; *tmp; ++tmp)
*tmp = tolower(*tmp); /* require lower case */
}
如果_pam_strdup函数返回了NULL,则给出错误信息"pam_start: _pam_strdup failed for service name",并且调用_pam_drop函数,之后返回PM_BUF_ERR;
如果_pam_strdup函数返回非空,则说明已经复制service_name成功,此时(*pamh)->service_name的值就是复制后的service_name。接下来所做的就是将(*pamh)->service_name即复制后的字符串的各个字符都转换为小写。
再来看一下刚才没有讲的_pam_drop。_pam_drop是一个宏,在libpam/include/security/_pam_macros.h中定义,如下:
/*
* Don't just free it, forget it too.
*/
#define _pam_drop(X) \
do { \
if (X) { \
free(X); \
X=NULL; \
} \
} while (0)_pam_drop很简单,实际上就是free函数的封装,功能一目了然。
再来看一下PAM_BUF_ERR。PAM_BUF_ERR在libpam/include/security/_pam_types.h中定义,代码如下:
/* ----------------- The Linux-PAM return values ------------------ */
#define PAM_SUCCESS 0 /* Successful function return */
#define PAM_OPEN_ERR 1 /* dlopen() failure when dynamically */
/* loading a service module */
#define PAM_SYMBOL_ERR 2 /* Symbol not found */
#define PAM_SERVICE_ERR 3 /* Error in service module */
#define PAM_SYSTEM_ERR 4 /* System error */
#define PAM_BUF_ERR 5 /* Memory buffer error */
#define PAM_PERM_DENIED 6 /* Permission denied */
#define PAM_AUTH_ERR 7 /* Authentication failure */
#define PAM_CRED_INSUFFICIENT 8 /* Can not access authentication data */
/* due to insufficient credentials */
#define PAM_AUTHINFO_UNAVAIL 9 /* Underlying authentication service */
/* can not retrieve authentication */
/* information */
#define PAM_USER_UNKNOWN 10 /* User not known to the underlying */
/* authentication module */
……_pam_start_internal函数的其余部分将在后续文章中继续讲解。