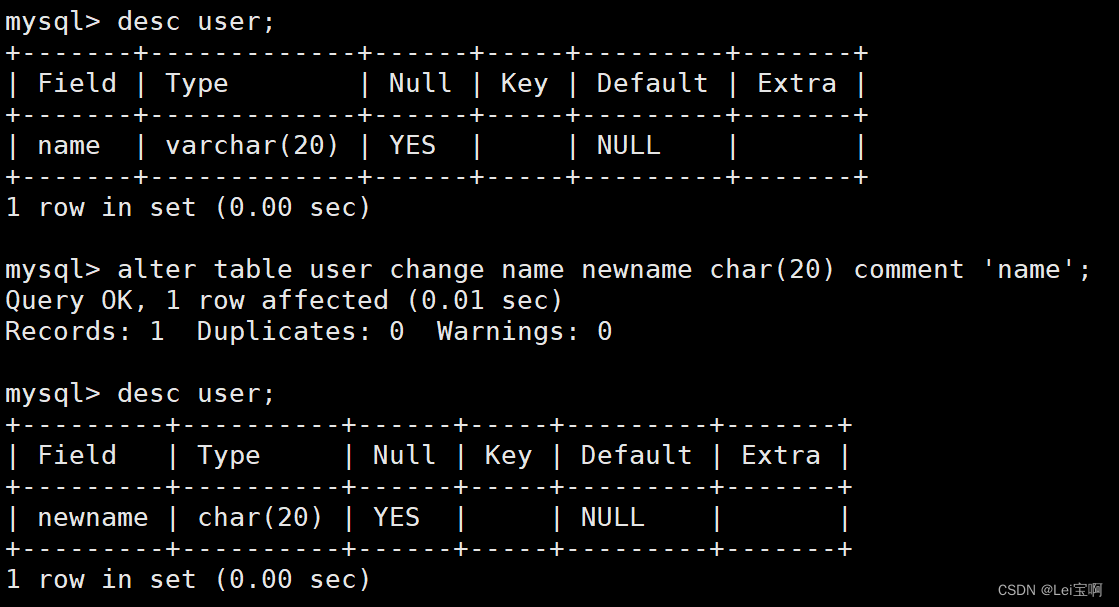
链接:https://pan.baidu.com/s/1n6tYUtYYL_3Gn_Mjp4QEWg?pwd=h23n
提取码:h23n
Block and Stream Ciphers
Two fundamental types of encryption algorithms are Block Ciphers and Stream Ciphers.
- Block Ciphers : These work on data blocks of fixed sizes, transforming plaintext blocks into encrypted blocks (ciphertext). When encrypting more data than one block allows, several operational modes can be utilized (e.g., ECB, CBC, CFB, OFB, CTR).
- Stream Ciphers : These work on continuous streams of data. They typically involve generating a key stream and performing a bitwise XOR with the plaintext.
Popular examples include Advanced Encryption Standard (AES), a type of block cipher and RC4, a type of stream cipher.
Message Digests, MACs, HMACs, and KDFs
Message digests (aka hash functions), MACs (Message Authentication Codes), HMACs (Hash-based Message Authentication Codes), and KDFs (Key Derivation Functions) are cryptographic tools designed for ensuring data integrity and authenticity.
- Message Digests : These produce a fixed-size hash value from a variable-size message. Any alteration in the original message, however small, results in a different hash.
- MACs : While a hash function guarantees integrity, a MAC adds a layer of authentication. It involves a secret key shared between the sender and receiver, and any alteration in the message or the MAC can be detected.
- HMACs : HMACs uses a secret key and a cryptographic hash function to produce a MAC. Unlike traditional MACs, this can operate on messages of variable length.
- KDFs : KDFs are used to derive keys from a shared secret value (like a password). They help in creating cryptographically strong and random keys.
Authenticated Modes, Key Wrapping, and the SealedObject
Authenticated encryption modes like GCM (Galois/Counter Mode) combine confidentiality, integrity, and authenticity in a single process - providing robust protection to your data.
Key wrapping refers to securely encapsulating (or ‘wrapping’) keys under a master key. This is used in great part to safeguard the lifecycle of keys.
The SealedObject is a feature in Java Cryptography Architecture (JCA) that allows for the serialization and de-serialization of encrypted objects, containing the serialized representation of an object and the parameters used during encryption.
Password-Based Key Generation and Key Splitting
Password-Based Key Generation involves generating a cryptographic key from a user password. An important function used for this purpose is Password-Based Key Derivation Function 2 (PBKDF2). It applies a pseudorandom function to the input password along with a salt and repeats the process many times to generate a key.
Key splitting involves dividing a key into multiple parts, and it’s typically used to add a layer of security when storing or transmitting a key. A well-known method for key splitting is the Shamir’s Secret Sharing algorithm.
Signatures
Digital signatures use public-key cryptography to provide authentication, non-repudiation, and integrity, ensuring the receiver of a message that it has indeed come from the legitimate sender and hasn’t been tampered with during transit.
Key Transport, Key Agreement, Key Exchange
Key transport involves securely transmitting a key from one party to another. Key agreement, on the other hand, involves two or more parties generating a shared secret key, each contributing a key component.
Key exchange protocols like the Diffie–Hellman help to establish shared keys securely even over insecure channels.
X.509 Certificates and Attribute Certificates
X.509 is a standard defining the format of public key certificates. A certificate binds a public key to an entity.
Attribute certificates, on the other hand, are a kind of credential that can be used to create a wide range of flexible, robust, secure identity systems. They provide privileges or access rights to a user rather than just confirming their identity.
Certificate Revocation and Certificate Paths
Certificate Revocation Lists (CRLs) and Online Certificate Status Protocol (OCSP) are ways used to deal with certificate revocation - the process of revoking a previously issued certificate before its expiration in case it’s compromised or no longer needed.
Certificate Path or Chain is a list of certificates, used to authenticate an entity, starting from a trusted root certificate authority (CA) to the entity’s certificate.
Key and Certificate Storage
Key and certificate storage involves securely storing cryptographic keys and certificates. This includes Hardware Security Modules (HSMs), cloud-based HSM services, and protected files.
Certificate Requests and Certificate Management
Certificate Signing Request (CSR) is a message sent from an applicant to a certificate authority to apply for a digital certificate. Certificate management, also known as Public Key Infrastructure (PKI) management, is the process of managing digital certificates to enable secure communication in a network.
In conclusion, the successful application of these cryptographic tools and processes forms the basis of a robust security ecosystem, allowing organizations to secure their data in transit and at rest, ensure its integrity and authenticity, and provide non-repudiation where necessary.
On the other hand
- Block and Stream Ciphers: 块密码和流密码是两种主要的加密算法。块密码按固定大小的块处理数据,而流密码则是按位处理数据。这两种密码都在许多安全系统中使用。
- Message Digests, MACs, HMACs, KDFs: 这些是用于数据完整性验证和密码强化的技术。消息摘要(Message Digests)是使用散列函数生成的数据表示。MAC(Message Authentication Code)是一种用于验证消息完整性和身份认证的算法。HMAC(Hash-based Message Authentication Code)是使用加密哈希函数生成的消息认证码。KDF(Key Derivation Function)是生成密钥的方法。
- Authenticated Modes, Key Wrapping, and the SealedObject: 这部分内容涉及的是加密模式和密钥封装。Authenticated Mode是用于保证数据完整性和身份认证的加密模式。Key Wrapping是一种将密钥封装在另一个密钥中的技术,以提供额外的保护。SealedObject是一种将对象加密并封装在自身中的数据结构。
- Password Based Key Generation and Key Splitting: 这部分讲述的是基于密码的密钥生成和密钥分割。这种方法使用用户提供的密码来生成用于加密和解密的密钥。密钥分割是将密钥分成几部分,以便于更安全地存储或传输。
- Signatures: 签名是验证消息来源和完整性的方法。数字签名是使用私钥对消息进行签名,然后使用公钥验证签名的过程。
- Key Transport, Key Agreement, Key Exchange: 这部分内容涉及的是密钥传输、密钥协议和密钥交换。Key Transport是将密钥从一个实体传输到另一个实体的过程。密钥协议是两个或多个实体之间建立共享密钥的过程。密钥交换是两个实体之间建立共享密钥,但不直接传输密钥的过程。
- X.509 Certificates and Attribute Certificates: X.509证书是用于验证实体身份的标准格式。它们通常用于公钥基础设施(PKI)中,其中包含证书持有人的信息以及颁发机构的数字签名。Attribute Certificates则包含持有人的属性信息,而不是公钥。
- Certificate Revocation and Certificate Paths: 证书撤销是撤销证书有效性的过程,以防止被恶意使用。证书路径是验证证书真实性的过程,从信任的根证书开始,直到目标证书。
- Key and Certificate Storage: 密钥和证书的存储是网络安全的重要组成部分。这包括选择安全的存储位置和存储方式,例如硬件安全模块(HSM)或虚拟安全模块(VSM)。
- Certificate Requests and Certificate Management: 证书请求是实体向颁发机构申请证书的过程。证书管理包括维护和更新证书,以及处理证书撤销和吊销列表(CRL)。
GPT
oracle.com
youtube.com