概述:
运行mbedtls自带 ssl demo的记录;
操作过程:
编译Demo,请看我专栏中的相关文章
先运行服务端程序,运行ssl_server.exe,运行结果如下:
mbedtls-3.2.1\mbedtls-3.2.1\programs\ssl> .\ssl_server.exe
. Seeding the random number generator... ok
. Loading the server cert. and key... ok
. Bind on https://localhost:4433/ ... ok
. Setting up the SSL data.... ok
. Waiting for a remote connection ... ok
. Performing the SSL/TLS handshake... ok
< Read from client: 18 bytes read
GET / HTTP/1.0
> Write to client: 156 bytes written
HTTP/1.0 200 OK
Content-Type: text/html
<h2>mbed TLS Test Server</h2>
<p>Successful connection using: TLS-ECDHE-RSA-WITH-CHACHA20-POLY1305-SHA256</p>
. Closing the connection... ok
. Waiting for a remote connection ... ok
. Performing the SSL/TLS handshake... ok
< Read from client: 18 bytes read
GET / HTTP/1.0
> Write to client: 156 bytes written
HTTP/1.0 200 OK
Content-Type: text/html
<h2>mbed TLS Test Server</h2>
<p>Successful connection using: TLS-ECDHE-RSA-WITH-CHACHA20-POLY1305-SHA256</p>
. Closing the connection... ok
. Waiting for a remote connection ...再运行服务端,ssl_client1.exe, 运行结果如下;
mbedtls-3.2.1\mbedtls-3.2.1\programs\ssl> .\ssl_client1.exe
. Seeding the random number generator... ok
. Loading the CA root certificate ... ok (0 skipped)
. Connecting to tcp/localhost/4433... ok
. Setting up the SSL/TLS structure... ok
. Performing the SSL/TLS handshake...ssl_client.c:0261: got supported group(001d)
ssl_client.c:0261: got supported group(0017)
ssl_client.c:0261: got supported group(0018)
ssl_client.c:0261: got supported group(001e)
ssl_client.c:0261: got supported group(0019)
ssl_client.c:0261: got supported group(001a)
ssl_client.c:0261: got supported group(001b)
ssl_client.c:0261: got supported group(001c)
ok
. Verifying peer X.509 certificate... ok
> Write to server: 18 bytes written
GET / HTTP/1.0
< Read from server: 156 bytes read
HTTP/1.0 200 OK
Content-Type: text/html
<h2>mbed TLS Test Server</h2>
<p>Successful connection using: TLS-ECDHE-RSA-WITH-CHACHA20-POLY1305-SHA256</p>
ssl_msg.c:3900: mbedtls_ssl_handle_message_type() returned -30848 (-0x7880)
ssl_msg.c:5472: mbedtls_ssl_read_record() returned -30848 (-0x7880)
PS D:\Drive\SynologyDrive\NFC\16_开源项目\mbedtls-3.2.1\mbedtls-3.2.1\programs\ssl> .\ssl_client1.exe
. Seeding the random number generator... ok
. Loading the CA root certificate ... ok (0 skipped)
. Connecting to tcp/localhost/4433... ok
. Setting up the SSL/TLS structure... ok
. Performing the SSL/TLS handshake...ssl_client.c:0261: got supported group(001d)
ssl_client.c:0261: got supported group(0017)
ssl_client.c:0261: got supported group(0018)
ssl_client.c:0261: got supported group(001e)
ssl_client.c:0261: got supported group(0019)
ssl_client.c:0261: got supported group(001a)
ssl_client.c:0261: got supported group(001b)
ssl_client.c:0261: got supported group(001c)
ok
. Verifying peer X.509 certificate... ok
> Write to server: 18 bytes written
GET / HTTP/1.0
< Read from server: 156 bytes read
HTTP/1.0 200 OK
Content-Type: text/html
<h2>mbed TLS Test Server</h2>
<p>Successful connection using: TLS-ECDHE-RSA-WITH-CHACHA20-POLY1305-SHA256</p>
ssl_msg.c:3900: mbedtls_ssl_handle_message_type() returned -30848 (-抓取SSL过程分析:
使用wireshark 工具,可以实现抓包分析,抓取Demo的数据进行分析:
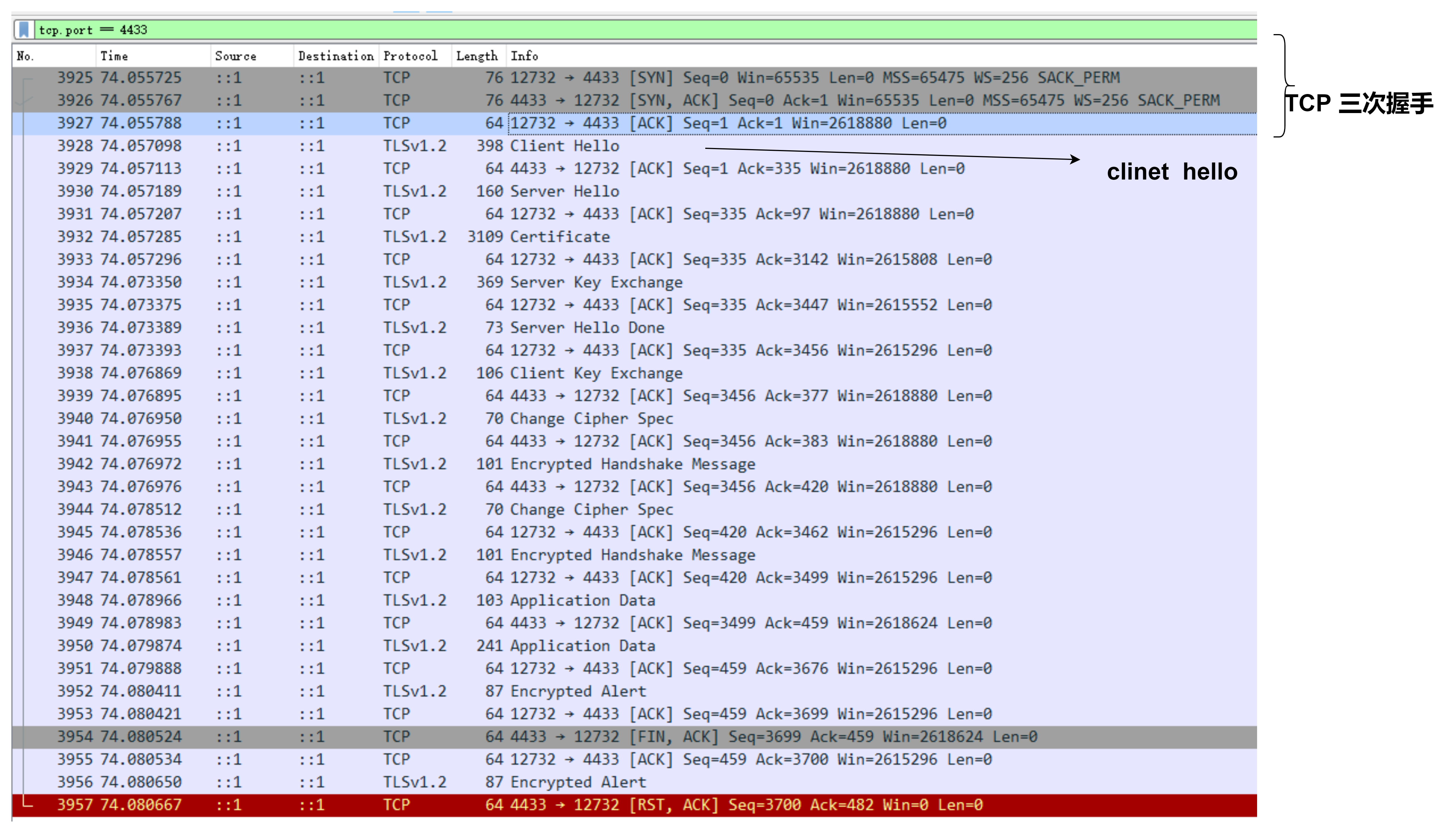
从抓包中可以看出,在进行完TCP连接后,进行了SSL连接过程:
Client Hello
Server Hell
Certification
Server key exchange
Server Hello done
Client Key exchange
Handshake 等操作
Demo代码:
贴出 client 端代码
int main( void )
{
int ret = 1, len;
int exit_code = MBEDTLS_EXIT_FAILURE;
mbedtls_net_context server_fd;
uint32_t flags;
unsigned char buf[1024];
const char *pers = "ssl_client1";
mbedtls_entropy_context entropy;
mbedtls_ctr_drbg_context ctr_drbg;
mbedtls_ssl_context ssl;
mbedtls_ssl_config conf;
mbedtls_x509_crt cacert;
#if defined(MBEDTLS_DEBUG_C)
mbedtls_debug_set_threshold( DEBUG_LEVEL );
#endif
/*
* 0. Initialize the RNG and the session data
*/
mbedtls_net_init( &server_fd );
mbedtls_ssl_init( &ssl );
mbedtls_ssl_config_init( &conf );
mbedtls_x509_crt_init( &cacert );
mbedtls_ctr_drbg_init( &ctr_drbg );
mbedtls_printf( "\n . Seeding the random number generator..." );
fflush( stdout );
mbedtls_entropy_init( &entropy );
if( ( ret = mbedtls_ctr_drbg_seed( &ctr_drbg, mbedtls_entropy_func, &entropy,
(const unsigned char *) pers,
strlen( pers ) ) ) != 0 )
{
mbedtls_printf( " failed\n ! mbedtls_ctr_drbg_seed returned %d\n", ret );
goto exit;
}
mbedtls_printf( " ok\n" );
/*
* 0. Initialize certificates
*/
mbedtls_printf( " . Loading the CA root certificate ..." );
fflush( stdout );
ret = mbedtls_x509_crt_parse( &cacert, (const unsigned char *) mbedtls_test_cas_pem,
mbedtls_test_cas_pem_len );
if( ret < 0 )
{
mbedtls_printf( " failed\n ! mbedtls_x509_crt_parse returned -0x%x\n\n", (unsigned int) -ret );
goto exit;
}
mbedtls_printf( " ok (%d skipped)\n", ret );
/*
* 1. Start the connection
*/
mbedtls_printf( " . Connecting to tcp/%s/%s...", SERVER_NAME, SERVER_PORT );
fflush( stdout );
if( ( ret = mbedtls_net_connect( &server_fd, SERVER_NAME,
SERVER_PORT, MBEDTLS_NET_PROTO_TCP ) ) != 0 )
{
mbedtls_printf( " failed\n ! mbedtls_net_connect returned %d\n\n", ret );
goto exit;
}
mbedtls_printf( " ok\n" );
/*
* 2. Setup stuff
*/
mbedtls_printf( " . Setting up the SSL/TLS structure..." );
fflush( stdout );
if( ( ret = mbedtls_ssl_config_defaults( &conf,
MBEDTLS_SSL_IS_CLIENT,
MBEDTLS_SSL_TRANSPORT_STREAM,
MBEDTLS_SSL_PRESET_DEFAULT ) ) != 0 )
{
mbedtls_printf( " failed\n ! mbedtls_ssl_config_defaults returned %d\n\n", ret );
goto exit;
}
mbedtls_printf( " ok\n" );
/* OPTIONAL is not optimal for security,
* but makes interop easier in this simplified example */
mbedtls_ssl_conf_authmode( &conf, MBEDTLS_SSL_VERIFY_OPTIONAL );
mbedtls_ssl_conf_ca_chain( &conf, &cacert, NULL );
mbedtls_ssl_conf_rng( &conf, mbedtls_ctr_drbg_random, &ctr_drbg );
mbedtls_ssl_conf_dbg( &conf, my_debug, stdout );
if( ( ret = mbedtls_ssl_setup( &ssl, &conf ) ) != 0 )
{
mbedtls_printf( " failed\n ! mbedtls_ssl_setup returned %d\n\n", ret );
goto exit;
}
if( ( ret = mbedtls_ssl_set_hostname( &ssl, SERVER_NAME ) ) != 0 )
{
mbedtls_printf( " failed\n ! mbedtls_ssl_set_hostname returned %d\n\n", ret );
goto exit;
}
mbedtls_ssl_set_bio( &ssl, &server_fd, mbedtls_net_send, mbedtls_net_recv, NULL );
/*
* 4. Handshake
*/
mbedtls_printf( " . Performing the SSL/TLS handshake..." );
fflush( stdout );
while( ( ret = mbedtls_ssl_handshake( &ssl ) ) != 0 )
{
if( ret != MBEDTLS_ERR_SSL_WANT_READ && ret != MBEDTLS_ERR_SSL_WANT_WRITE )
{
mbedtls_printf( " failed\n ! mbedtls_ssl_handshake returned -0x%x\n\n", (unsigned int) -ret );
goto exit;
}
}
mbedtls_printf( " ok\n" );
/*
* 5. Verify the server certificate
*/
mbedtls_printf( " . Verifying peer X.509 certificate..." );
/* In real life, we probably want to bail out when ret != 0 */
if( ( flags = mbedtls_ssl_get_verify_result( &ssl ) ) != 0 )
{
#if !defined(MBEDTLS_X509_REMOVE_INFO)
char vrfy_buf[512];
#endif
mbedtls_printf( " failed\n" );
#if !defined(MBEDTLS_X509_REMOVE_INFO)
mbedtls_x509_crt_verify_info( vrfy_buf, sizeof( vrfy_buf ), " ! ", flags );
mbedtls_printf( "%s\n", vrfy_buf );
#endif
}
else
mbedtls_printf( " ok\n" );
/*
* 3. Write the GET request
*/
mbedtls_printf( " > Write to server:" );
fflush( stdout );
len = sprintf( (char *) buf, GET_REQUEST );
while( ( ret = mbedtls_ssl_write( &ssl, buf, len ) ) <= 0 )
{
if( ret != MBEDTLS_ERR_SSL_WANT_READ && ret != MBEDTLS_ERR_SSL_WANT_WRITE )
{
mbedtls_printf( " failed\n ! mbedtls_ssl_write returned %d\n\n", ret );
goto exit;
}
}
len = ret;
mbedtls_printf( " %d bytes written\n\n%s", len, (char *) buf );
/*
* 7. Read the HTTP response
*/
mbedtls_printf( " < Read from server:" );
fflush( stdout );
do
{
len = sizeof( buf ) - 1;
memset( buf, 0, sizeof( buf ) );
ret = mbedtls_ssl_read( &ssl, buf, len );
if( ret == MBEDTLS_ERR_SSL_WANT_READ || ret == MBEDTLS_ERR_SSL_WANT_WRITE )
continue;
if( ret == MBEDTLS_ERR_SSL_PEER_CLOSE_NOTIFY )
break;
if( ret < 0 )
{
mbedtls_printf( "failed\n ! mbedtls_ssl_read returned %d\n\n", ret );
break;
}
if( ret == 0 )
{
mbedtls_printf( "\n\nEOF\n\n" );
break;
}
len = ret;
mbedtls_printf( " %d bytes read\n\n%s", len, (char *) buf );
}
while( 1 );
mbedtls_ssl_close_notify( &ssl );
exit_code = MBEDTLS_EXIT_SUCCESS;
exit:
#ifdef MBEDTLS_ERROR_C
if( exit_code != MBEDTLS_EXIT_SUCCESS )
{
char error_buf[100];
mbedtls_strerror( ret, error_buf, 100 );
mbedtls_printf("Last error was: %d - %s\n\n", ret, error_buf );
}
#endif
mbedtls_net_free( &server_fd );
mbedtls_x509_crt_free( &cacert );
mbedtls_ssl_free( &ssl );
mbedtls_ssl_config_free( &conf );
mbedtls_ctr_drbg_free( &ctr_drbg );
mbedtls_entropy_free( &entropy );
mbedtls_exit( exit_code );
}Demo代码比较简单,