【微|信|公|众|号:厦门微思网络】
部署华为防火墙确保园区出口安全案例
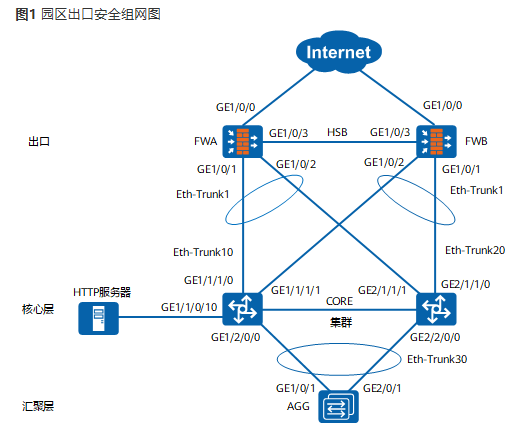
本案例将以园区典型组网为例,主要介绍园区出口安全的部署。具体业务安全要求如下:
-
内网用户可以正常访问Internet资源,但只能访问教育/科学类、搜索/门户类网站。
-
为了防止公司机密文件的泄露,禁止员工上传常见文档文件、开发文件(C、CPP、JAVA)以及压缩文件到Internet。
-
为了降低病毒进入公司内部的风险,禁止员工从Internet下载可执行文件。
-
为了保证员工的工作效率,禁止员工从Internet下载视频类文件。
-
为了防止公司机密信息的泄露以及违规信息的传播,对内网用户上传到Internet的文件、发送到Internet的邮件、发布的帖子和微博、浏览网页和搜索的内容进行过滤。
-
外网用户可以访问内网中的HTTP服务器资源。为了保障服务器的正常运行,对SYN Flood、UDP Flood和HTTP Flood攻击进行防范。
-
为了防止邮件引入病毒,需要对HTTP和POP3协议进行反病毒检测。
-
为了防止蠕虫、木马和僵尸网络等攻击,需要对这些攻击进行防范。
-
为了不影响正常业务,在任何时间内限制P2P、在线视频等最大带宽不超过30Mbps。为了更好的控制P2P、在线视频流量,可以通过限制连接数的方式,限制最大连接数不超过10000。为了让Email、ERP等应用不受到影响,此类流量可获得的最小带宽不少于60Mbps。
-
记录员工的上网行为,从而采取更加精确的安全策略控制。
部署需求
-
配置安全区域和安全策略,使得内网用户能够访问Internet资源,外网用户能够访问HTTP服务器
-
配置过滤功能:
•URL过滤功能:实现只能访问教育/科学类、搜索/门户类网站•文件过滤:实现禁止员工上传常见文档文件、开发文件(C、CPP、JAVA)以及压缩文件到Internet,禁止员工从Internet下载可执行文件、视频类文件
•内容过滤:实现防止公司机密信息的泄露以及违规信息的传播
-
配置反病毒和入侵防御,实现防止邮件引入病毒,屏蔽蠕虫、木马和僵尸网络等攻击
-
配置DDoS攻击防御,实现屏蔽SYN Flood、UDP Flood和HTTP Flood攻击
-
配置带宽策略,保证Email、ERP等应用正常工作
-
配置上网行为审计和管理,记录员工的上网行为,从而采取更加精确的安全策略控制
配置步骤
1、配置安全区域和安全策略
a、配置安全区域。
系统缺省已经创建了四个安全区域。但是如果用户还需要划分更多的安全等级,可以自行创建新的安全区域并定义其安全等级。安全区域创建完成后,还需要将相应接口加入安全区域。之后,从该接口接收的或发送出去的报文才会被认为是属于该安全区域。否则接口默认不属于任何安全区域,将不能通过该接口与其他安全区域通信。
将FW接口划分不同的安全区域。
[FWA] firewall zone trust
[FWA-zone-trust] set priority 85
[FWA-zone-trust] add interface eth-trunk 1 //将连接内网的Eth-Trunk1加入安全区域
[FWA-zone-trust] quit
[FWA] firewall zone name untrust //将连接外网的接口加入安全区域
[FWA-zone-untrust] set priority 5
[FWA-zone-untrust] add interface gigabitethernet 1/0/0
[FWA-zone-untrust] quit
[FWA] firewall zone dmz
[FWA-zone-dmz] set priority 50
[FWA-zone-dmz] add interface gigabitethernet 1/0/3 //将心跳口加入DMZ区域
[FWA-zone-dmz] quit
[FWB] firewall zone trust
[FWB-zone-trust] set priority 85
[FWB-zone-trust] add interface eth-trunk 1 //将连接内网的Eth-Trunk1加入安全区域
[FWB-zone-trust] quit
[FWB] firewall zone name untrust //将连接外网的接口加入安全区域
[FWB-zone-untrust] set priority 5
[FWB-zone-untrust] add interface gigabitethernet 1/0/0
[FWB-zone-untrust] quit
[FWB] firewall zone dmz
[FWB-zone-dmz] set priority 50
[FWB-zone-dmz] add interface gigabitethernet 1/0/3 //将心跳口加入DMZ区域
[FWB-zone-dmz] quitb、配置安全策略。
双机热备状态成功建立后,FWA的安全策略配置会自动备份到FWB上。双机热备配置请参见防火墙部署IPSec与总部互联。
HRP_M[FWA] security-policy
HRP_M[FWA-policy-security] rule name policy_dmz //允许本地和DMZ区域间互访
HRP_M[FWA-policy-security-rule-policy_dmz] source-zone local
HRP_M[FWA-policy-security-rule-policy_dmz] source-zone dmz
HRP_M[FWA-policy-security-rule-policy_dmz] destination-zone local
HRP_M[FWA-policy-security-rule-policy_dmz] destination-zone dmz
HRP_M[FWA-policy-security-rule-policy_dmz] action permit
HRP_M[FWA-policy-security-rule-policy_dmz] quit
HRP_M[FWA-policy-security] rule name trust_to_untrust //允许内网用户访问外网
HRP_M[FWA-policy-security-rule-trust_to_untrust] source-zone trust
HRP_M[FWA-policy-security-rule-trust_to_untrust] destination-zone untrust
HRP_M[FWA-policy-security-rule-trust_to_untrust] source-address 10.6.0.0 24
HRP_M[FWA-policy-security-rule-trust_to_untrust] action permit
HRP_M[FWA-policy-security-rule-trust_to_untrust] quit
HRP_M[FWA-policy-security] rule name untrust_to_trust //允许外网用户访问HTTP服务器
HRP_M[FWA-policy-security-rule-untrust_to_trust] source-zone untrust
HRP_M[FWA-policy-security-rule-untrust_to_trust] destination-zone trust
HRP_M[FWA-policy-security-rule-untrust_to_trust] destination-address 10.7.0.0 24
HRP_M[FWA-policy-security-rule-untrust_to_trust] action permit
HRP_M[FWA-policy-security-rule-untrust_to_trust] quit
HRP_M[FWAA-policy-security] quit2、配置过滤功能
a、URL过滤
配置URL过滤配置文件。
HRP_M[FWA] profile type url-filter name profile_url_research
HRP_M[FWA-profile-url-filter-profile_url_research] category user-defined action block
HRP_M[FWA-profile-url-filter-profile_url_research] category pre-defined action block
HRP_M[FWA-profile-url-filter-profile_url_research] category pre-defined category-id 15 action allow //允许访问搜索/门户类网站
HRP_M[FWA-profile-url-filter-profile_url_research] category pre-defined category-id 17 action allow //允许访问教育/科学类网站
HRP_M[FWA-profile-url-filter-profile_url_research] quit
配置安全策略
HRP_M[FWA] security-policy
HRP_M[FWA-policy-security] rule name policy_sec_research
HRP_M[FWA-policy-security-rule-policy_sec_research] source-zone trust
HRP_M[FWA-policy-security-rule-policy_sec_research] destination-zone untrust
HRP_M[FWA-policy-security-rule-policy_sec_research] user user-group /default/priuser
HRP_M[FWA-policy-security-rule-policy_sec_research] action permit
HRP_M[FWA-policy-security-rule-policy_sec_research] profile url-filter profile_url_research
HRP_M[FWA-policy-security-rule-policy_sec_research] quit
提交内容安全配置文件
HRP_M[FWA] engine configuration commit
Info: The operation may last for several minutes, please wait.
Info: URL submitted configurations successfully.-
Info: Finish committing engine compiling.b.文件过滤
新建配置文件profile_file_user1,禁止上传文档文件、开发文件和压缩文件,以及从Internet下载可执行文件和音视频文件。
HRP_M[FWA] profile type file-block name profile_file_user1
HRP_M[FWA-profile-file-block-profile_file_user1] rule name rule1
HRP_M[FWA-profile-file-block-profile_file_user1-rule-rule1] application all
HRP_M[FWA-profile-file-block-profile_file_user1-rule-rule1] file-type pre-defined name DOC PPT XLS MSOFFICE DOCX PPTX XLSX PDF VSD MPP
HRP_M[FWA-profile-file-block-profile_file_user1-rule-rule1] file-type pre-defined name ODS ODT ODP EML UOF RAR TAR ZIP GZIP CAB
HRP_M[FWA-profile-file-block-profile_file_user1-rule-rule1] file-type pre-defined name BZ2 Z 7ZIP JAR C CPP JAVA VBS
HRP_M[FWA-profile-file-block-profile_file_user1-rule-rule1] direction upload
HRP_M[FWA-profile-file-block-profile_file_user1-rule-rule1] action block
HRP_M[FWA-profile-file-block-profile_file_user1-rule-rule1] quit
HRP_M[FWA-profile-file-block-profile_file_user1] rule name rule2
HRP_M[FWA-profile-file-block-profile_file_user1-rule-rule2] application all
HRP_M[FWA-profile-file-block-profile_file_user1-rule-rule2] file-type pre-defined name EXE MSI RPM OCX A ELF DLL PE SYS MDI
HRP_M[FWA-profile-file-block-profile_file_user1-rule-rule2] file-type pre-defined name MOV MPEG AVI RMVB ASF SWF MP3 MP4 MIDI
HRP_M[FWA-profile-file-block-profile_file_user1-rule-rule2] direction download
HRP_M[FWA-profile-file-block-profile_file_user1-rule-rule2] action block
HRP_M[FWA-profile-file-block-profile_file_user1-rule-rule2] quit
HRP_M[FWA-profile-file-block-profile_file_user1] quit
配置trust到untrust的安全策略policy_sec_user1,并引用配置文件profile_file_user1。
HRP_M[FWA] security-policy
HRP_M[FWA-policy-security] rule name policy_sec_user1
HRP_M[FWA-policy-security-rule-policy_sec_user1] source-zone trust
HRP_M[FWA-policy-security-rule-policy_sec_user1] destination-zone untrust
HRP_M[FWA-policy-security-rule-policy_sec_user1] user user-group /default/priuser
HRP_M[FWA-policy-security-rule-policy_sec_user1] profile file-block profile_file_user1
HRP_M[FWA-policy-security-rule-policy_sec_user1] action permit
HRP_M[FWA-policy-security-rule-policy_sec_user1] quit提交内容安全配置文件。
HRP_M[FWA] engine configuration commit
Info: The operation may last for several minutes, please wait.
Info: DLP submitted configurations successfully.
Info: Finish committing engine compiling.c.内容过滤
配置关键字组keyword1。
HRP_M[FWA] keyword-group name keyword1
HRP_M[FWA-keyword-group-keyword1] pre-defined-keyword name confidentiality weight 1
HRP_M[FWA-keyword-group-keyword1] user-defined-keyword name abc
HRP_M[FWA-keyword-group-keyword1-keyword-abc] expression match-mode text "abcd" //定义信息关键字为abcd
HRP_M[FWA-keyword-group-keyword1-keyword-abc] weight 1
HRP_M[FWA-keyword-group-keyword1-keyword-abc] quit
为用户新建配置文件profile_data_research。
HRP_M[FWA] profile type data-filter name profile_data_research
HRP_M[FWA-profile-data-filter-profile_data_research] rule name rule1
HRP_M[FWA-profile-data-filter-profile_data_research-rule-rule1] keyword-group name keyword1
HRP_M[FWA-profile-data-filter-profile_data_research-rule-rule1] application all
HRP_M[FWA-profile-data-filter-profile_data_research-rule-rule1] file-type all
HRP_M[FWA-profile-data-filter-profile_data_research-rule-rule1] direction upload
HRP_M[FWA-profile-data-filter-profile_data_research-rule-rule1] action block
HRP_M[FWA-profile-data-filter-profile_data_research-rule-rule1] quit
为用户配置安全策略policy_sec_research,并引用配置文件profile_data_research。
HRP_M[FWA] security-policy
HRP_M[FWA-policy-security] rule name policy_sec_research
HRP_M[FWA-policy-security-rule-policy_sec_research] source-zone trust
HRP_M[FWA-policy-security-rule-policy_sec_research] destination-zone untrust
HRP_M[FWA-policy-security-rule-policy_sec_research] user user-group /default/priuser
HRP_M[FWA-policy-security-rule-policy_sec_research] profile data-filter profile_data_research
HRP_M[FWA-policy-security-rule-policy_sec_research] action permit
HRP_M[FWA-policy-security-rule-policy_sec_research] quit提交内容安全配置文件。
HRP_M[FWA] engine configuration commit
Info: The operation may last for several minutes, please wait.
Info: DLP submitted configurations successfully.
Info: Finish committing engine compiling.
3.配置反病毒和入侵防御。
a.配置反病毒。
当内网用户通过HTTP协议下载带有病毒的文件时,下载连接被阻断。当内网用户通过POP3协议下载带有病毒的邮件时,附件被删除。
配置针对HTTP和POP3协议的反病毒配置文件。
HRP_M[FWA] profile type av name av_http_pop3
HRP_M[FWA-profile-av-av_http_pop3] http-detect direction download action block
HRP_M[FWA-profile-av-av_http_pop3] pop3-detect action delete-attachment
HRP_M[FWA-profile-av-av_http_pop3] exception application name Netease_Webmail
HRP_M[FWA-profile-av-av_http_pop3] exception av-signature-id 1000
HRP_M[FWA-profile-av-av_http_pop3] quit
配置内网用户到外网服务器方向(trust到untrust方向)的安全策略。
HRP_M[FWA] security-policy
HRP_M[FWA-policy-security] rule name policy_av_1
HRP_M[FWA-policy-security-rule-policy_av_1] source-zone trust
HRP_M[FWA-policy-security-rule-policy_av_1] destination-zone untrust
HRP_M[FWA-policy-security-rule-policy_av_1] action permit
HRP_M[FWA-policy-security-rule-policy_av_1] profile av av_http_pop3
HRP_M[FWA-policy-security-rule-policy_av_1] quitb.配置入侵防御。
创建入侵防御配置文件profile_ips_pc,保护内网用户。
HRP_M[FWA] profile type ips name profile_ips_pc
HRP_M[FWA-profile-ips-profile_ips_pc] description profile for intranet users
HRP_M[FWA-profile-ips-profile_ips_pc] capture-packet enable
HRP_M[FWA-profile-ips-profile_ips_pc] signature-set name filter1
HRP_M[FWA-profile-ips-profile_ips_pc-sigset-filter1] target client
HRP_M[FWA-profile-ips-profile_ips_pc-sigset-filter1] severity high
HRP_M[FWA-profile-ips-profile_ips_pc-sigset-filter1] protocol HTTP
HRP_M[FWA-profile-ips-profile_ips_pc-sigset-filter1] quit
HRP_M[FWA-profile-ips-profile_ips_pc] quit提交配置。
HRP_M[FWA] engine configuration commit
Info: The operation may last for several minutes, please wait.
Info: DLP submitted configurations successfully.
Info: Finish committing engine compiling.配置Trust区域和Untrust区域之间的安全策略,引用入侵防御配置文件profile_ips_pc。
HRP_M[FWA] security-policy
HRP_M[FWA-policy-security] rule name policy_sec_1
HRP_M[FWA-policy-security-rule-policy_sec_1] source-zone trust
HRP_M[FWA-policy-security-rule-policy_sec_1] destination-zone untrust
HRP_M[FWA-policy-security-rule-policy_sec_1] source-address 10.6.0.0 24
HRP_M[FWA-policy-security-rule-policy_sec_1] profile ips profile_ips_pc
HRP_M[FWA-policy-security-rule-policy_sec_1] action permit
HRP_M[FWA-policy-security-rule-policy_sec_1] quit4.配置DDoS攻击防范。
经检测,服务器经常受到SYN Flood、UDP Flood和HTTP Flood攻击,为了保障服务器的正常运行,需开启攻击防范功能,用来防范以上三种类型的DDoS攻击。
配置攻击防范参数。
HRP_M[FWA] interface GigabitEthernet1/0/0
HRP_M[FWA-GigabitEthernet1/0/0] anti-ddos flow-statistic enable
HRP_M[FWA-GigabitEthernet1/0/0] quit
HRP_M[FWA] ddos-mode detect-clean配置阈值学习功能。
HRP_M[FWA] anti-ddos baseline-learn start
HRP_M[FWA] anti-ddos baseline-learn tolerance-value 100
HRP_M[FWA] anti-ddos baseline-learn apply开启攻击防范功能。
HRP_M[FWA] anti-ddos syn-flood source-detect
HRP_M[FWA] anti-ddos udp-flood dynamic-fingerprint-learn
HRP_M[FWA] anti-ddos udp-frag-flood dynamic-fingerprint-learn
HRP_M[FWA] anti-ddos http-flood defend alert-rate 2000
HRP_M[FWA] anti-ddos http-flood source-detect mode basic
5.配置带宽策略。
针对P2P、在线视频应用配置带宽通道。
HRP_M[FWA] traffic-policy
HRP_M[FWA-policy-traffic] profile profile_p2p
HRP_M[FWA-policy-traffic-profile-profile_p2p] bandwidth maximum-bandwidth whole both 30000
HRP_M[FWA-policy-traffic-profile-profile_p2p] bandwidth connection-limit whole both 10000
HRP_M[FWA-policy-traffic-profile-profile_p2p] quit针对P2P、在线视频应用配置带宽策略。
此处仅给出了BT、优酷网两种应用作为例子,具体配置时请根据实际需求指定应用。
HRP_M[FWA-policy-traffic] rule name policy_p2p
HRP_M[FWA-policy-traffic-rule-policy_p2p] source-zone trust
HRP_M[FWA-policy-traffic-rule-policy_p2p] destination-zone untrust
HRP_M[FWA-policy-traffic-rule-policy_p2p] application app BT YouKu
HRP_M[FWA-policy-traffic-rule-policy_p2p] action qos profile profile_p2p
HRP_M[FWA-policy-traffic-rule-policy_p2p] quit针对Email、ERP应用配置带宽通道。
HRP_M[FWA-policy-traffic] profile profile_email
HRP_M[FWA-policy-traffic-profile-profile_email] bandwidth guaranteed-bandwidth whole both 60000
HRP_M[FWA-policy-traffic-profile-profile_email] quit针对Email、ERP应用配置带宽策略。
此处仅给出了OWA(Outlook Web Access)、LotusNotes两种应用作为例子,具体配置时请根据实际需求指定应用。
HRP_M[FWA-policy-traffic] rule name policy_email
HRP_M[FWA-policy-traffic-rule-policy_email] source-zone trust
HRP_M[FWA-policy-traffic-rule-policy_email] destination-zone untrust
HRP_M[FWA-policy-traffic-rule-policy_email] application app LotusNotes OWA
HRP_M[FWA-policy-traffic-rule-policy_email] action qos profile profile_email
HRP_M[FWA-policy-traffic-rule-policy_email] quit
6.配置上网行为审计和管理。
针对用户配置审计配置文件,对HTTP行为、FTP行为、邮件行为进行审计。
HRP_M[FWA] profile type audit name profile_audit_1
HRP_M[FWA-profile-audit-profile_audit_1] http-audit url all
HRP_M[FWA-profile-audit-profile_audit_1] http-audit url recorded-title
HRP_M[FWA-profile-audit-profile_audit_1] http-audit file direction download
HRP_M[FWA-profile-audit-profile_audit_1] ftp-audit file direction download
HRP_M[FWA-profile-audit-profile_audit_1] http-audit bbs-content
HRP_M[FWA-profile-audit-profile_audit_1] http-audit micro-blog
HRP_M[FWA-profile-audit-profile_audit_1] quit针对用户配置审计策略并引用审计配置文件。
HRP_M[FWA] audit-policy
HRP_M[FWA-policy-audit] rule name policy_audit_1
HRP_M[FWA-policy-audit-rule-policy_audit_1] description Policy of auditing for priuser.
HRP_M[FWA-policy-audit-rule-policy_audit_1] source-zone trust
HRP_M[FWA-policy-audit-rule-policy_audit_1] destination-zone untrust
HRP_M[FWA-policy-audit-rule-policy_audit_1] user user-group /default/priuser
HRP_M[FWA-policy-audit-rule-policy_audit_1] action audit profile profile_audit_1
HRP_M[FWA-policy-audit-rule-policy_audit_1] quit提交配置。
HRP_M[FWA] engine configuration commit
Info: The operation may last for several minutes, please wait.
Info: Audit submitted configurations successfully.
Info: Finish committing engine compiling.后续处理。
通过查看各种报表和审计日志、用户活动日志信息,获取员工的上网行为,从而采取更加精确的安全策略控制。
结果验证
-
内网用户可以访问教育/科学类、搜索/门户类网站,但其他网站都被阻断不能访问。
-
内网用户从Internet上传文档文件、压缩文件、代码文件失败,从Internet下载可执行文件和视频文件失败。
-
内网用户发送包含机密信息的内容到Internet或者浏览和搜索包含违规信息的内容时,内容被阻断。
-
内网用户通过HTTP协议下载带有病毒的文件时,下载连接被阻断。
-
内网用户通过POP3协议下载带有病毒的邮件时,附件被删除。
-
收到蠕虫、木马、僵尸网络等攻击时,攻击被阻断。
-
外网用户可以访问内网中的HTTP服务器资源,当服务器收到SYN Flood、UDP Flood和HTTP Flood攻击时,攻击被阻断。