Billah, Md Fazlay Rabbi Masum, et al. “BLE Can See: A Reinforcement Learning Approach for RF-based Indoor Occupancy Detection.” Proceedings of the 20th International Conference on Information Processing in Sensor Networks (co-located with CPS-IoT Week 2021). 2021. CCF_B
Paper: BLE Can See
BLE Can See: A Reinforcement Learning Approach for RF-based Indoor Occupancy Detection
Summary
- propose BLECS, a Bluetooth-dependent indoor occupancy detection system which can adapt itself in th edynamic environment.
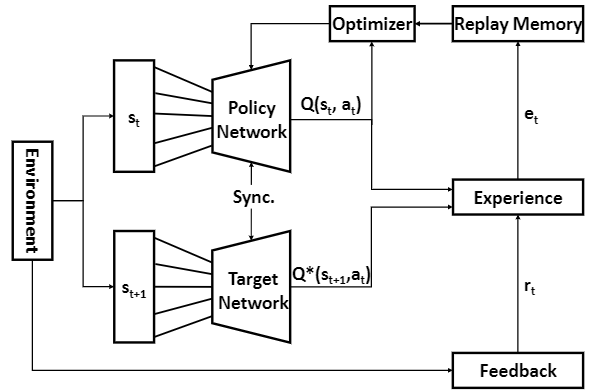
- The system uses a reinforcement learning approach to predict the occupancy of an indoor environment and updates its decision policy by interacting with existing IoT devices and sensors in the room.
Proble Statement
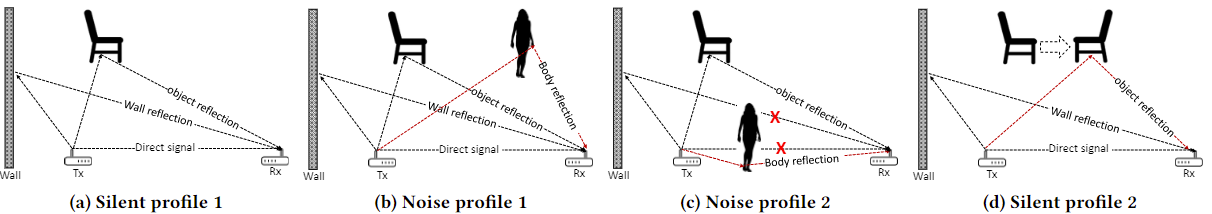
- signals propagating in an empty room follows a certain multipath pattern
- the presence of a human can add additional multipath effect
- the presence of human can also alter existing multipath effect
- movement of objects can alter the pattern as well.
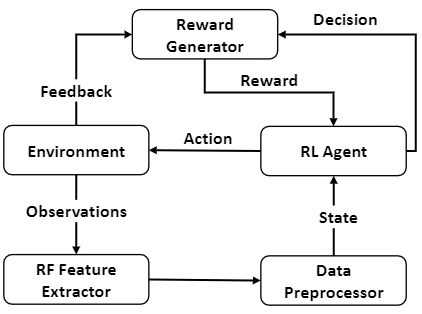
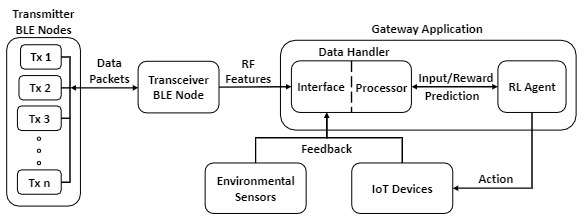
System overview
RF feature extraction
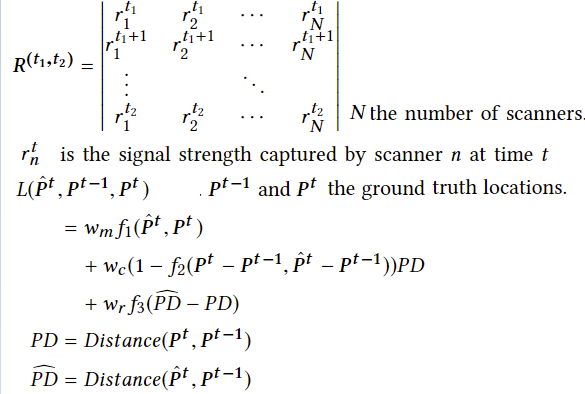
- Time of flight(ToF): lack of synchronized clocks, adopts a round-trip time(RTT) based ToF measurement technique.
- received signal strength indicator (RSSI)
- packet drop effect (PDE): introduces a delay-based mechanism
Feedback generation:
- takes feed-back from environmental sensors;
- orchestrates this mechanism by receiving feedback from smart devices whenever an occupant interacts with a device.
Mewborne T, Zhang L, Tan S. A Wearable-based Distracted Driving Detection Leveraging BLE[C]//Proceedings of the 19th ACM Conference on Embedded Networked Sensor Systems. 2021: 365-366.
Paper: Distracted Driving
A Wearable-based Distracted Driving Detection Leveraging BLE
Summary
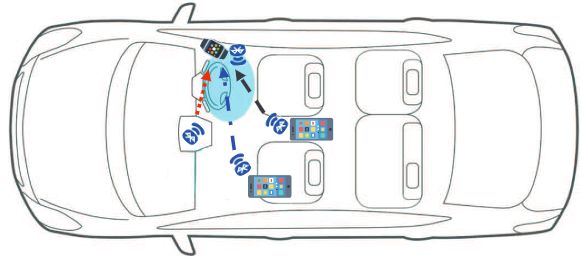
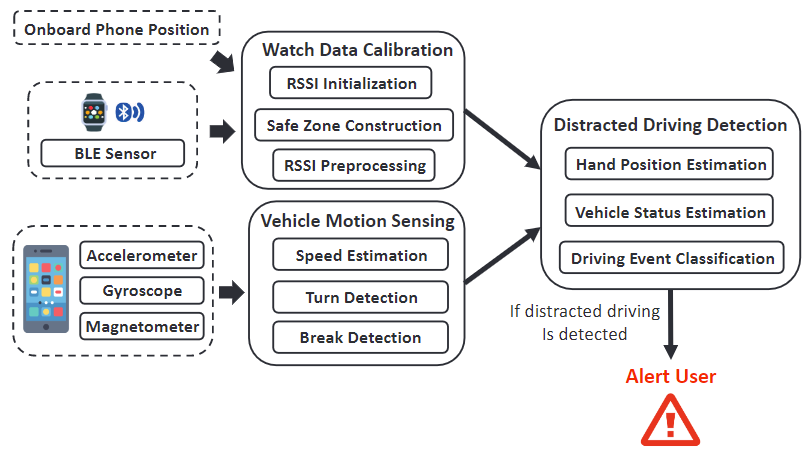
- present a wearable-based distracted driving detection system that leverages Bluetooth.
- the system exploits already in-vehicle BLE compatible devices to
track the drivers's hand position and infer potential unsafe driving behaviors.- the wearable device records the received signal strength indicator (RSSI) and processes the data to infer its current position.
- due to the unkown processing delay and unstable BLE signal, the system relies on the
RSSIs from multiple devices to infer thhe relative position of the dirvers's hand with respect to the steering wheel.
- advantage:
- not require any additional hardware or vehicle motion data separation.
- consumes much less battery power
Liu R, Yin Z, Jiang W, et al. WiBeacon: expanding BLE location-based services via wifi[C]//Proceedings of the 27th Annual International Conference on Mobile Computing and Networking. 2021: 83-96. [pdf]
Liu R, Yin Z, Jiang W, et al. BLE Location-based Services via WiFi[C]//Proceedings of the 19th ACM Conference on Embedded Networked Sensor Systems. 2021: 353-354. [pdf]
Paper: WiBeacon
WiBeacon: expanding BLE location-based services via wifi
Summary
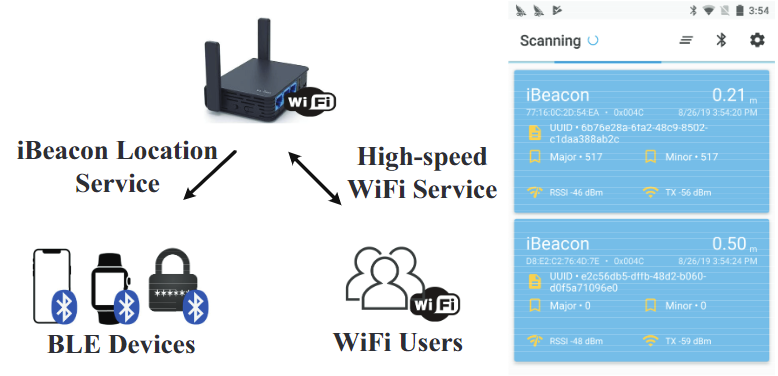
- present WiBeacon which repurposes ubiquitously depllyed WiFi access points into virtual beacons via corss-technology communication, which solves the high cost in BLE beacon deployment.
- the WiFi Aps installed with WiBeacon software
periodically broadcast legitimate WiFi probe request frames, recognized asstandard BLE packetsby unmodified BLE devices.
Research Objective
- Application Area: instant delivery(eg. real time courier tracking and order scheduling), a city-wide BLE system was deployed more than 10000 restaurants in Shanghai.
- Purpose:
- BLE location service must be strictly compatible with both hardware and software of mobile devices requiring zero modification
- software upgrades of the AP should also be compatible with native WiFi services and transparent to WiFi clients.
- Motivation
- why are large-scale Deployments of BLE Beacon Challenging? dedicated beacons, deployment and administrative cost, battery
- why cannot WiFi LBS replace iBeacon? the list of scanned WiFi APs are not accessible to developers on some mobile OS due to security concers; WiFi scans incur high power consumption to mobile devices, large latency. large low-cost smart devices only equipped with BLE chipsets.
- Benifits of BLE LBS via Ubiquitous WiFi APs: large deployment already, remote management, battery.
Proble Statement
- conventionally, BLE infrastrutures need to be massively installed and configud to brodcast BLE location identifiers.
trmendous deployment costs, long-term maintenance burdens - BLE LBS requires periodic frequency hopping to increase the detection probability, how to
accomplish th eservice-level integration iwthout scarificing WiFi networks - how to overcome commucation errors
previous work:
cross-technology communication(CTC): 31, 44, 48 enable direct communication among heterogeneous wirelss protocals
System overview:
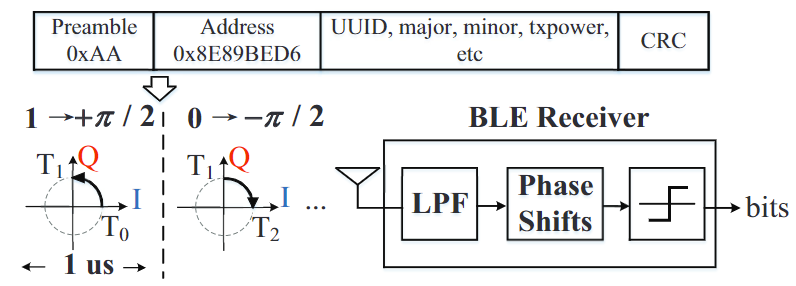
【iBeacon Preliminary】
- modulated using BLE 4.x 1 Mbps Gaussian Frequency Shift Key (GFSK)
- transmitted at BLE advertising channels, each data bit is modulated to one BLE chip, 0,1 phase shift of 1us.
to broadcast with zero chip error - mobile devices captures the broadcast signal at BLE advertising channels, and passes it through 1 MHz low pass filter.
- demodulate the filtered signal via quadrature demodulation
- the receiver interprets the sign of phase shifts into bits.
【Cross-technology communications Limitations】
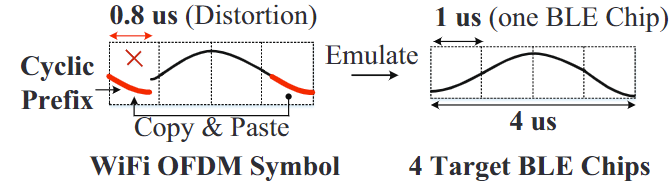
- the emulated sgnal inherently suffers from signal imperfections due to hardware restrictions of a WiFi radio, which cann’t satisfy the zero chip error for BLE becons.
- each OFDM symbol has a cyclic prefix (CP), the first 0.8us signal of an 4 us OFDM symbol has to be exactly the same as the signal at the last 0.8us.
the BLE signals do not have such repetition
【Modulation】
- Amplitude Shift Keying: changing the power level of the waveform.
- Frequency Shift Keying: changing the frequency of the waveform.
- Phase Shift Keying: frequency stays constant but changes made to relative to a reference point.

- Quadrature Amplitude Modulation (QAM)
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-FHMlN7Mq-1671195096247)(null)]
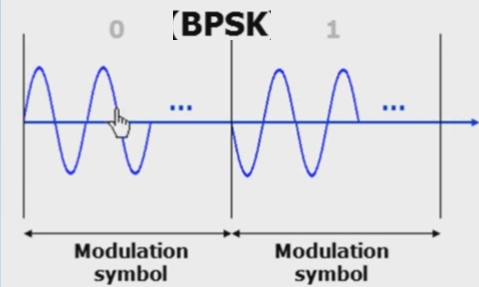
【PSK】
- BPSK:
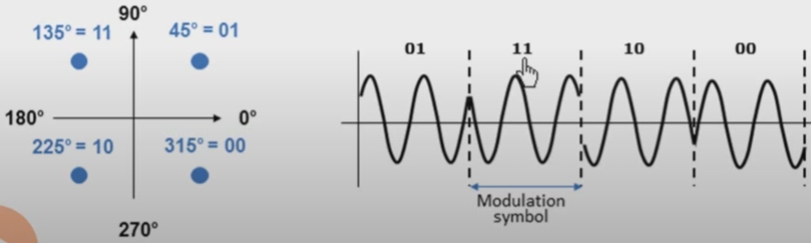
- QPSK
调制器输入的数据是二进制数字序列,为了能和四进制的载波相位配合起来,则需要把二进制数据变换为四进制数据,这就是说需要把二进制数字序列中每两个比特分成一组,共有四种组合,即00,01,10,11,其中每一组称为双比特码元。
【OFDM】
将信道分成许多正交子信道,在每个子信道上进行窄带调制和传输,这样减少了子信道之间的相互干扰。每个子信道上的信号带宽小于信道的相关带宽,因此每个子信道上的频率选择性衰落是平坦的,大大消除了符号间干扰。
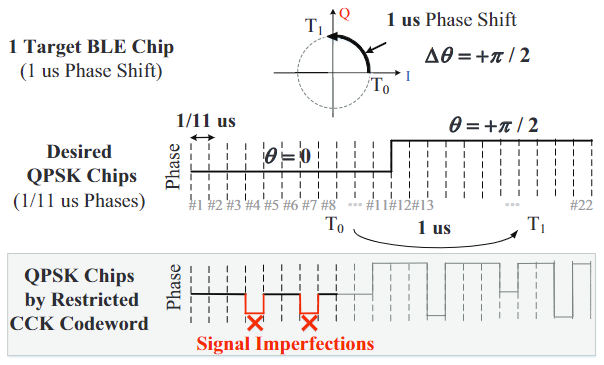
【CKC Preliminary】
- every 8 bits are encoded into a codeword ( C i C_i Ci) containing 8 complex chips
- the chips are modulated by Quadrature Phase Shift Keying (QPSK)(正交相移键控).
- each QPSK chip C i , j C_{i,j} Ci,j takes one of the four values correspond to 4 quadrature phase(0,90,180,-90)
- QPSK chips takes 1/11 us and 8/11us in total to transmit a CCK codeword of 8 chips.

【WiBeacon Broadcast】
using complementary code keying(CCK) modulationmethods to produce no ship errors and is fully compatible with unmodified mobile devices.
- the first 8 QPSK chips are desired to be eight consecutive value is not a vaid codeword in the codebook, and a close approximation like [1 1 1 -1 1 1 -1 1], cause 2/8 imperfections.
- CCK codewords can be smoothed out b the
low pass filterand thus incur zero chip error.
- create a standard iBeacon BLE frame with the location service information.
- generate the target BLE signal using Gaussian frequency shift keying( GFSK)
- conduct CCK emulation and misalignment compensation
- codewords are reverse engineered into WiFi payload.
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-TZKmHXPs-1671195096218)(null)]
to eliminate the imperfections of CCK signal without modifying mobile devices
- ble receiver employs a low-pass filter at its front end for noise reduction, similar to
moving average.
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-u2xBJC0w-1671195096392)(null)]
【CCK Codeword Selection】
- how to find CCK codewords that can take advantage of low-pass filtering and produce correct BLE chips.
- a good CCK codeword is expected to produce phases that are as similar to desired ones as possible.
computing the desired QPSK sequence with basic CCK method - iterate through the codebook to find the codeword C i Ci Ci that is closest to the desired sequence C d C^d Cd in the phase domain.
- the more separated unmatched QPSK chips are, the higher chances they can be eliminated by low-pass filtering.
pick the codeword in the subset, such that the minimum interval between consecutive unmatched chips is maximized.
- a good CCK codeword is expected to produce phases that are as similar to desired ones as possible.
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-RvURyEQy-1671195096483)(null)]
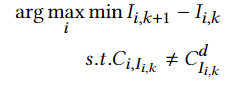
【Misalignment Compensation】
- 蓝牙:
- 物理层(Physical Layer):通过2.4G无线电与外界连接,完成无线电信号的传输与接收工作即采用2.4G无线电,输出0和1的信号或解码无线电接受识别0和1。
- 频段:低功耗蓝牙使用2.4GHz频段(2400MHz-2483.5MHz)
- 调制方式:高斯频移键控(GFSK)。(以中心频率为基准,负频偏为比特0,正频偏为比特1)。
- 信道:使用
40个无线信道(3个广播信道,37个数据信道),信道中心频率计算公式为:fm=2402+2*K(MHz)(k:0,1…无线信道编号),即最低频率为2402MHz,最高频率为2480MHz,与ISM频段的最低频率有2MHz间隙,与最高频率有3.8MHz间隙。
- assume that the center frequencies of WiFi and BLE are perfectly aligned, the detail channels are not aligned, like BLE channel 39 (2480 MHZ) and its nearest WiFi channel(2472 MHz).
when emulating a BLE waveform with a misaligned center frequency, the WiFi transmitter essentially performs the emulation with an adjusted codebook from the BLE receiver’s viewpoint.
- WiBeacon adjusts the codebook to BLE’s viewpoint before conducting CCK method.
- shift each codeword of the standard codebook in the frequency domain by Δ f = f w − f b \Delta f=f_w-f_b Δf=fw−fb, by the dot-product of each codeword with a digital carrier.
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-x4NLKG3e-1671195096424)(null)]
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-VLtsfqDg-1671195096455)(null)]
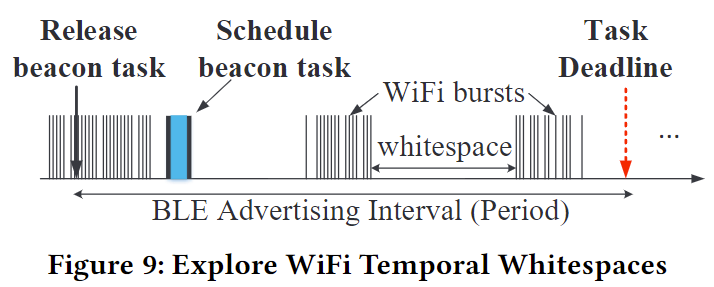
【Shedule Service】
- develop a dynamic WiBeacon scheduling algorithm to guarantee the reliability of iBeacon service while minimizing its impact on WiFi performance。
- propose a methods that entirely uses standard features of 802.11 Ap.
- Frequency hopping preparation: to avoid packet loss
- disable the outgoing gate of data queue and buffer incoming data to prevent downlink WiFi packets
- transmit cts-to-self-an 802.11 control frame to silent the clients for a specific short period of time.
- frequency hopping: reuse offchannel function of WiFi APs to detect sources of interferene or unauthorized ad-hoc networks.
offchannel function can switches th eradio to another WiFi channel for a small amount of time (10-15ms), while preserving entire states of the AP, avoids reset of the network and disconecting clients - frequency hopping completion: immediately switch WiFi radio back to the operating channel.
- Frequency hopping preparation: to avoid packet loss
- a WiBeacon scheduler to guarantee the reliability of LBS, while minimizing its impact on the performance of WiFi service.
- iBeacon broadcast is the connection-less
- the Internet data traffic through WiFi is bursty in nature, leaving plenty of temporal whitespace for WiBeacon.
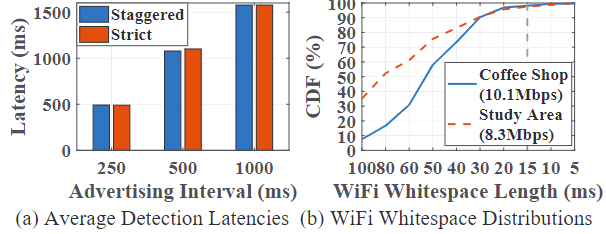
- in various advertising intervals the average detection latencies are not increased by the random delay.
Evaluation
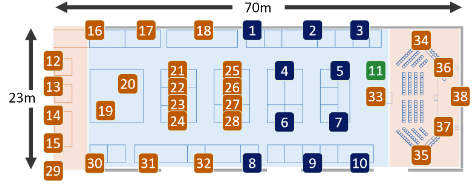
- Environment:
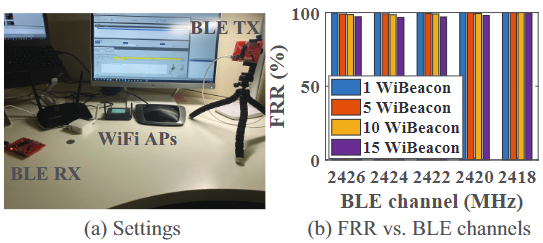
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-1lppa0MD-1671195096341)(null)]
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-ImsmZ52g-1671195096308)(null)]
deploys BLE beacons in the restaurants to detect the arrivals and departures of meal couriers for indoor navigation, courier scheduling, late delivery detection, map information correction, etc
Urano K, Hiroi K, Yonezawa T, et al. Basic study of BLE indoor localization using LSTM-based neural network (Poster)[C]//Proceedings of the 17th Annual International Conference on Mobile Systems, Applications, and Services. 2019: 558-559. [pdf]
Paper: BLE location
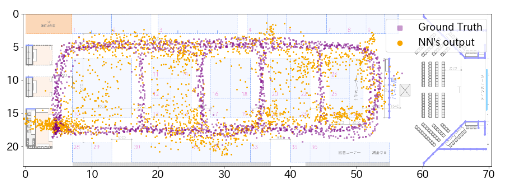
Basic study of BLE indoor localization using LSTM-based neural network
Summary
- LSTM-based neural network is applied to indoor localization using moblie BLE tag’s signal strength collected by multiple scanners.