关闭所有软件(except 安全),wireshark抓包
set filter==tcp,抓取所有tcp包,
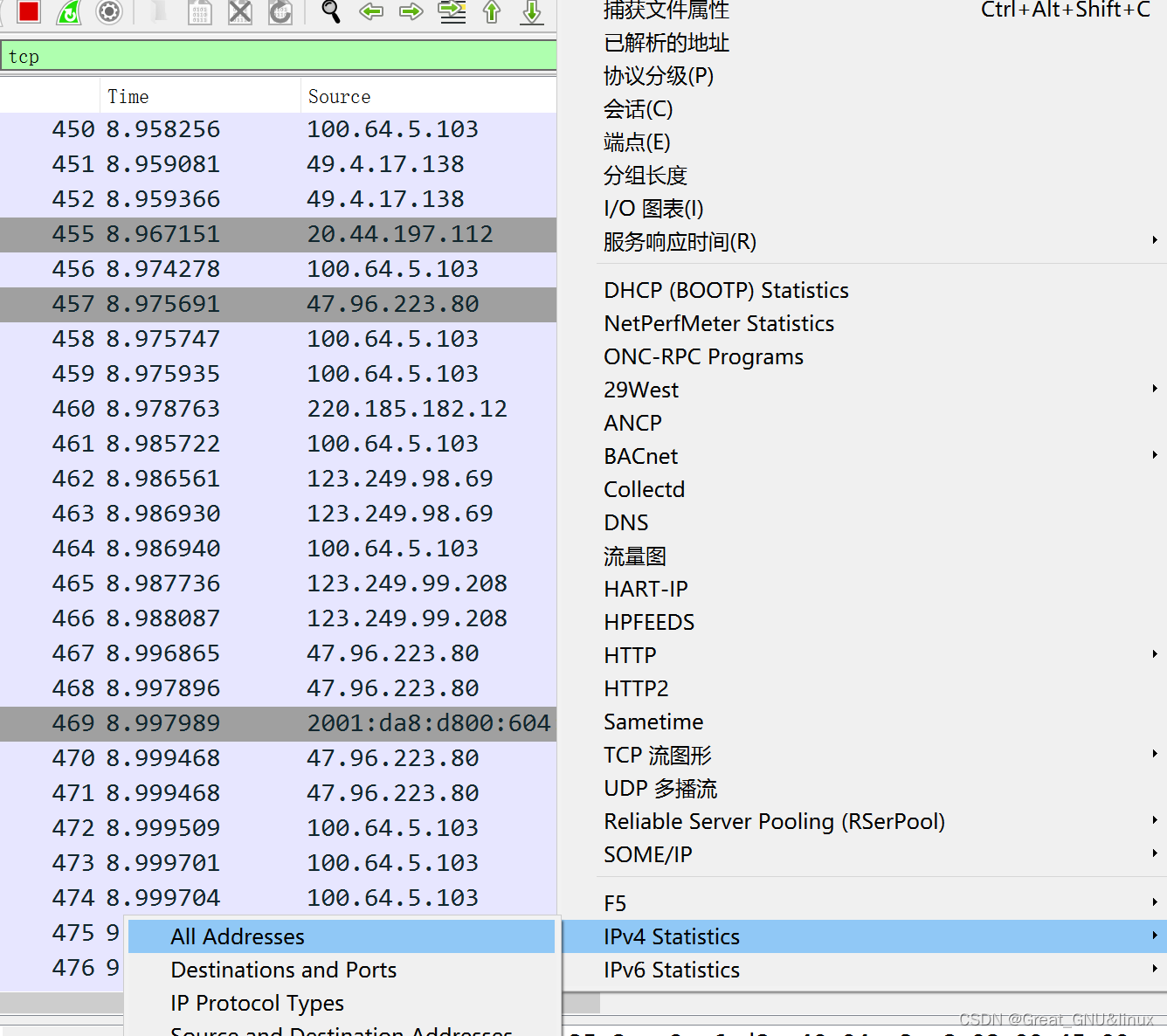
抓包文件导出为tcp.txt
过滤出ip address
去掉文件头尾,执行以下程序获得ip address
#cut_file.py
def copy_first_10_chars(input_file, output_file):
with open(input_file, 'r') as file_in:
with open(output_file, 'w') as file_out:
# in_len=len(file_in.readlines())
# print(f'input file possessc.ees {len(file_in.readlines())} lines')
for line in file_in:
first_10_chars = line[:13]
file_out.write(first_10_chars + '\n')
# 使用示例
input_file = 'input.txt' # 输入文件名
output_file = 'output.txt' # 输出文件名
copy_first_10_chars("tcp.txt", "target.txt")
执行python得到ip地址,
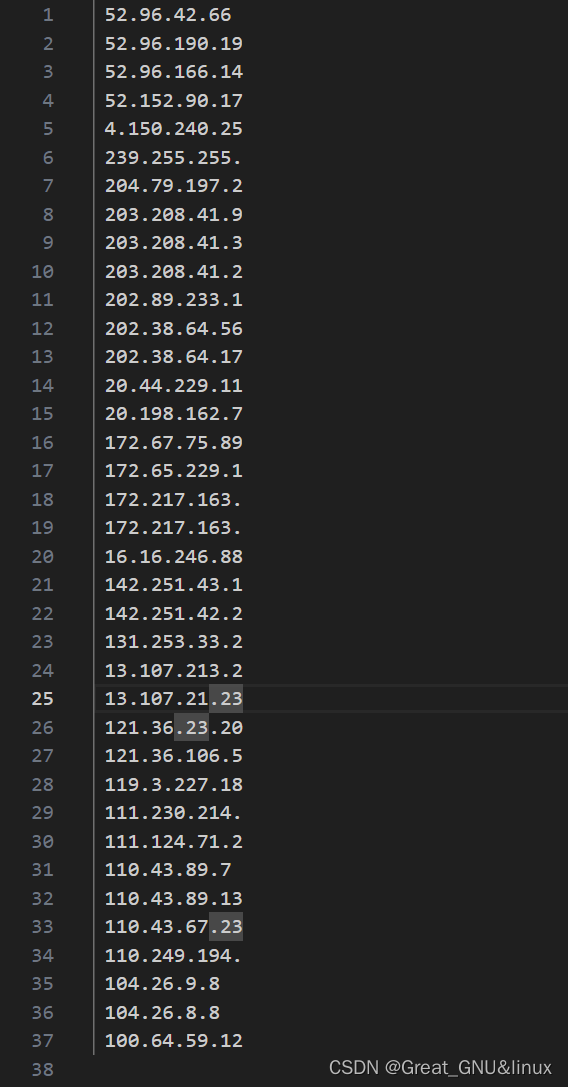
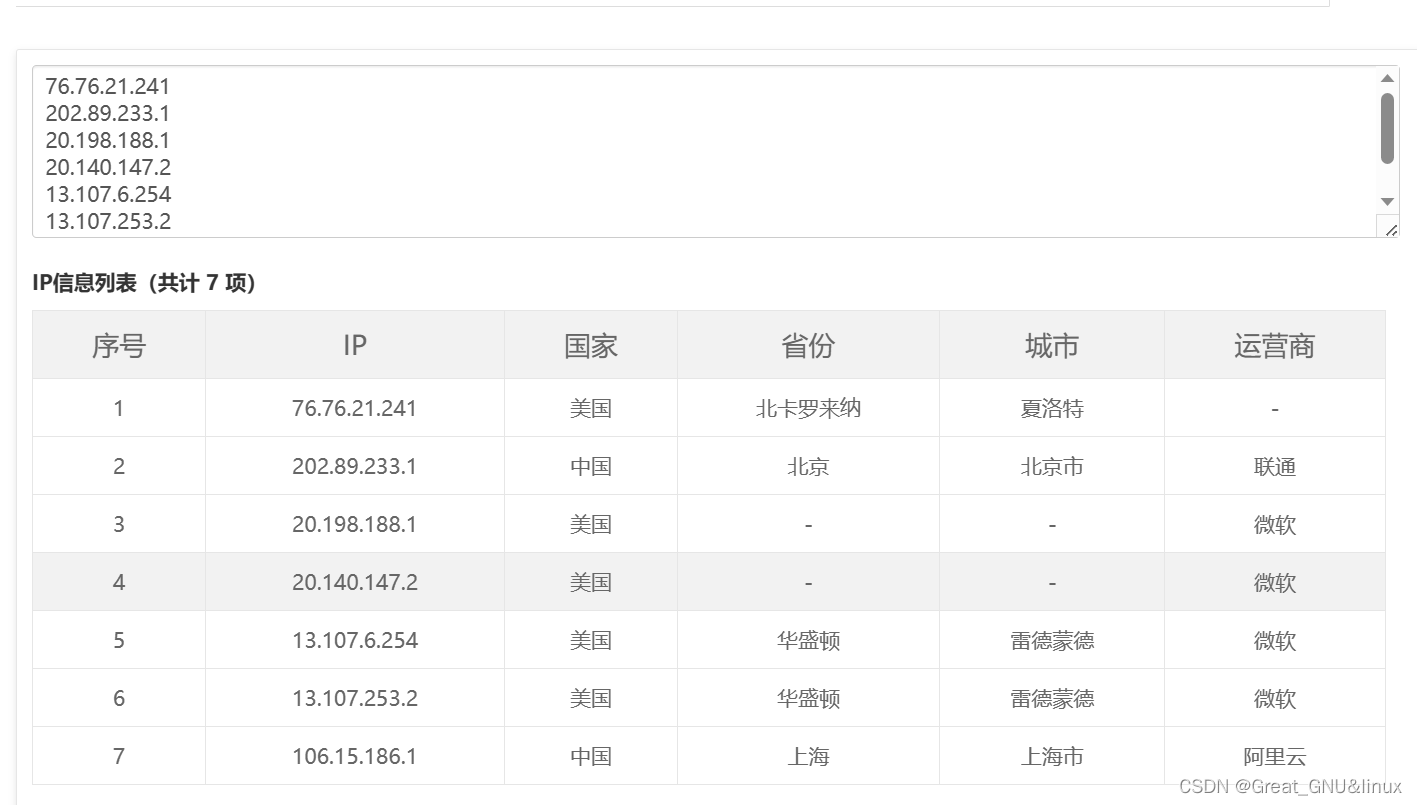
visit site for batch query
复制target.txt到input box,start query,
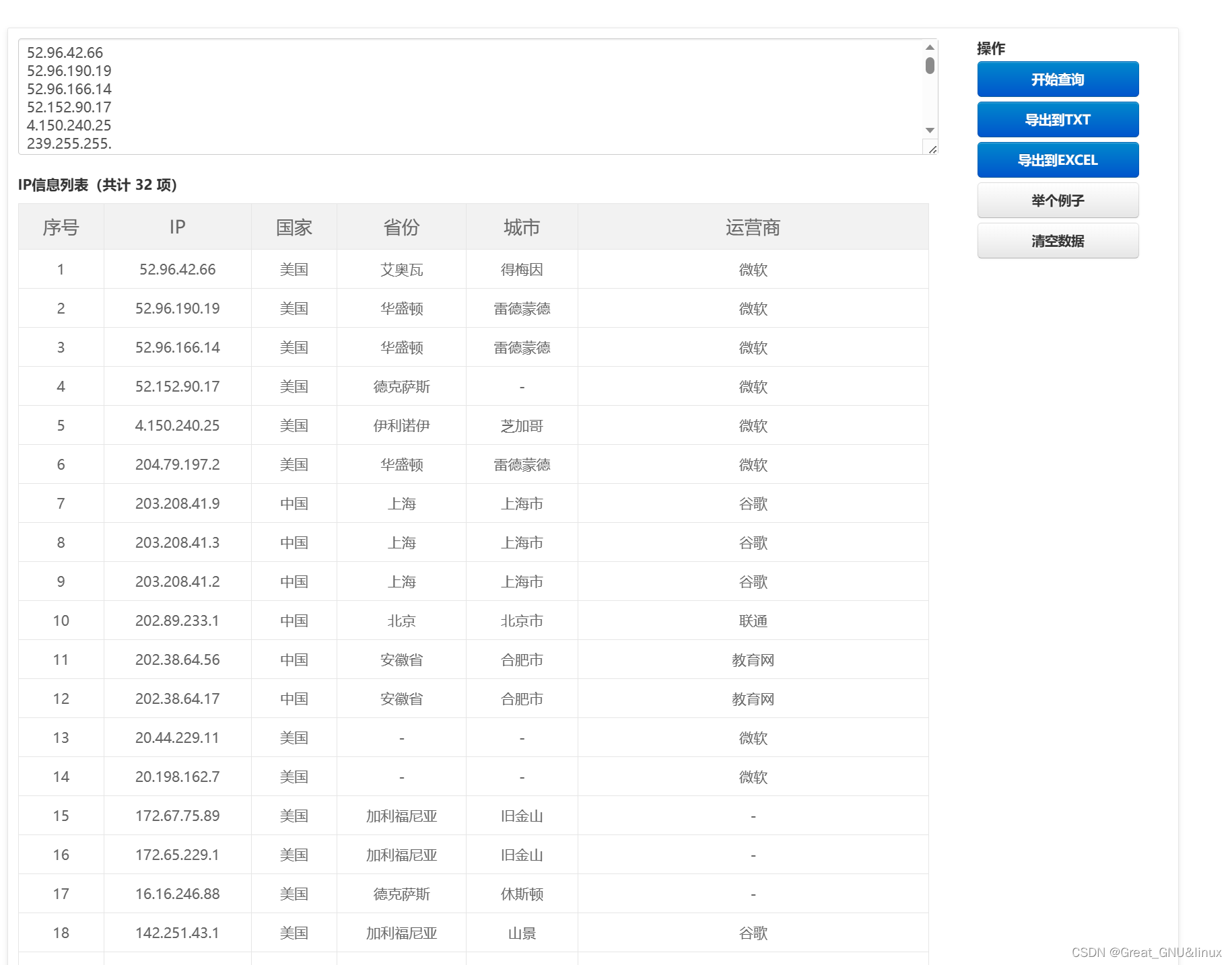
然后防火墙屏蔽掉非microsoft的网段
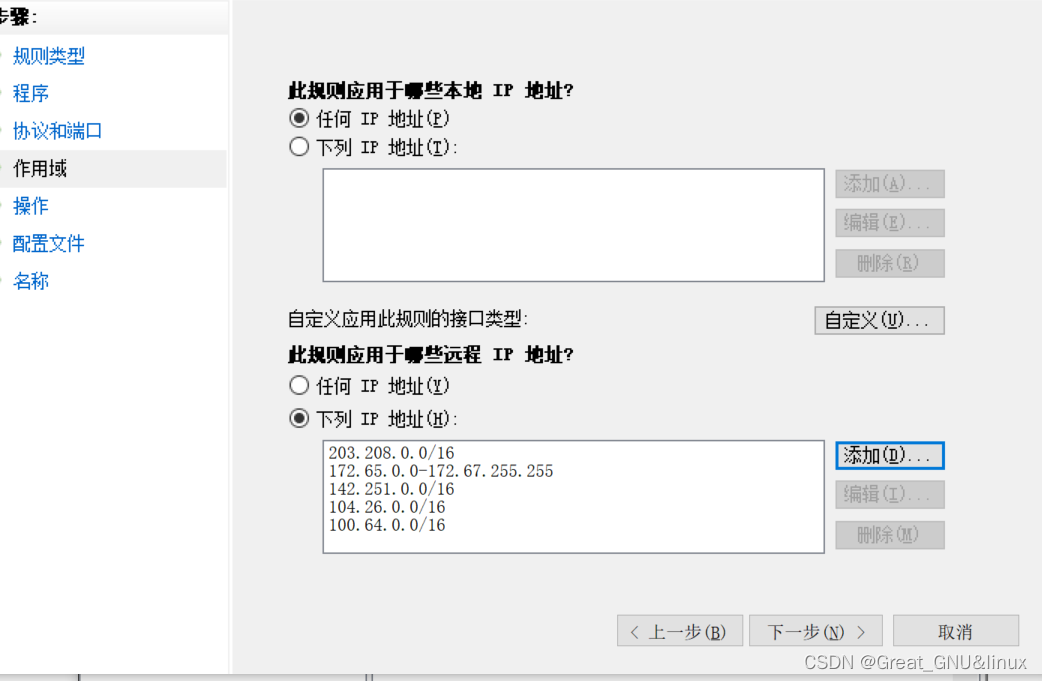
- 出战/入站 all demand block
- 屏蔽网段不要放到/8,不然容易误伤https的友军
查看软件发起的连接方法:
- 软件关闭下,保存ip addresstxt
- 开启软件,再次保存address.txt
- 比较2个txt,得到软件发起的ip连接
naive 代码如下,python还是有点用的(没装Code的对比插件)
def copy_first_10_chars(input_file, output_file):
with open(input_file, 'r') as file_in:
with open(output_file, 'w') as file_out:
# in_len=len(file_in.readlines())
# print(f'input file possessc.ees {len(file_in.readlines())} lines')
for line in file_in:
first_10_chars = line[:13]
file_out.write(first_10_chars + '\n')
# 使用示例
copy_first_10_chars("ip_0.txt", "tar_0.txt")
copy_first_10_chars("open_typora.txt", "tar_1.txt")
def compare(file1,file2,out_file):
with open(file2,'r') as f1:
with open(file1,'r') as f2:
with open(out_file,'w') as of:
l1=[]; l2=[]; sub=[]
for line1 in f1:
l1.append(line1[:13])
for line2 in f2:
l2.append(line2[:13])
for ip1 in l1:
sig=0
for ip2 in l2:
if ip2==ip1: sig=1
if sig==0: #不再l2中
sub.append(ip1)
for ip in sub:
of.write(ip+'\n')
compare('tar_0.txt','tar_1.txt','typora.txt')


![【傅里叶级数与傅里叶变换】数学推导——3、[Part4:傅里叶级数的复数形式] + [Part5:从傅里叶级数推导傅里叶变换] + 总结](https://img-blog.csdnimg.cn/77e1ce52f4ea477b86155158a95cfa46.png)