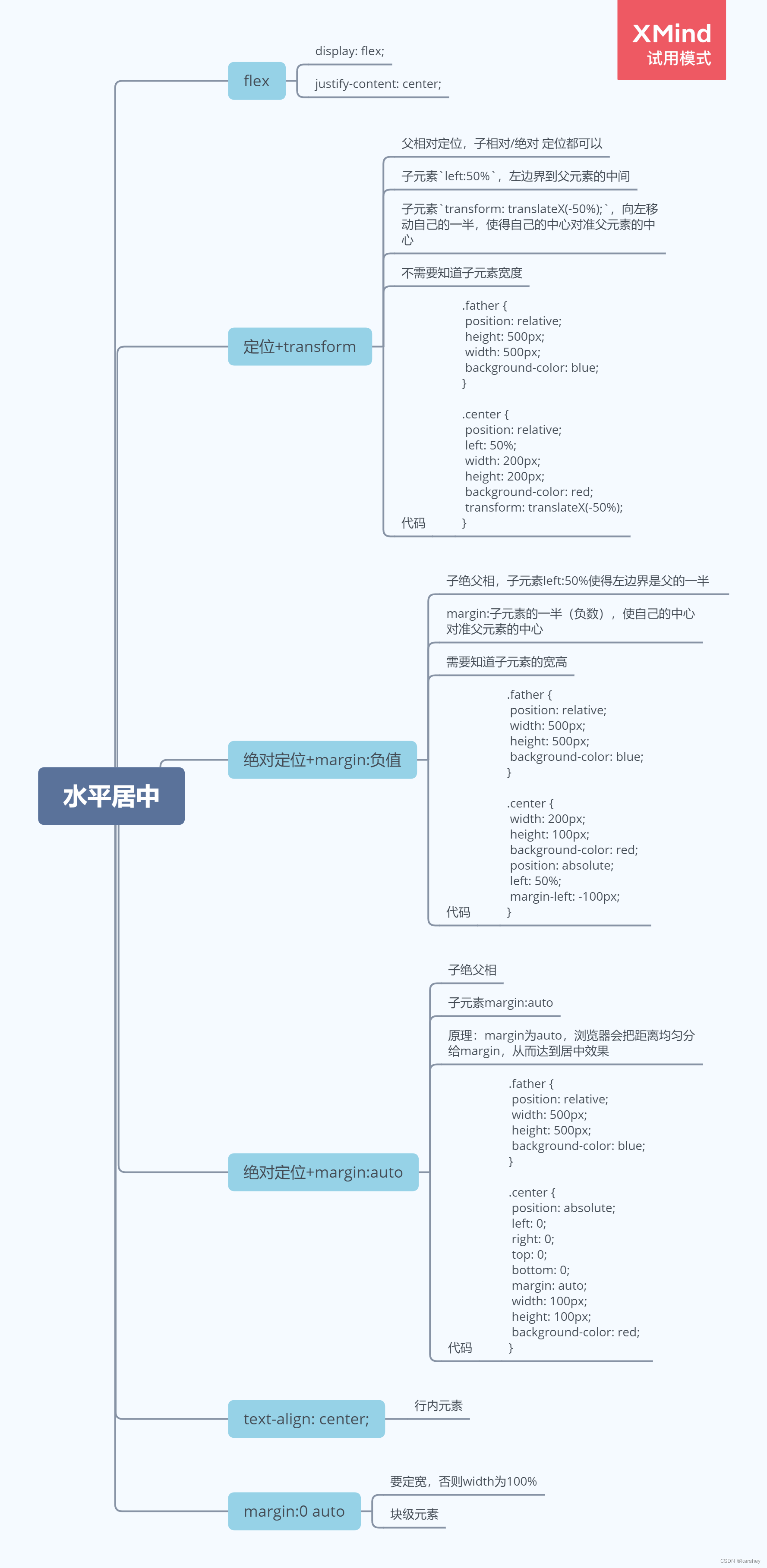
文章目录
- 前言
- 1.yum安装openldap
- 2.配置密码
- 3.导入配置
- 4.定义域
- 5.配置memberof
- 6.配置base dn
- 7.安装phpldapadmin管理
- 8.调整httpd的配置
- 9.调整php的配置
- 10.登陆php管理页面
- 11.同步旧ldapsever用户数据(可省略)
- 12.客户端配置
- 13.对接jumpserver
前言
介绍如何在centos7上部署openldap,并配置memberof进行组管理用户并介入jumpserver堡垒机
openldap参考的是这位大佬的博客,大佬文章的ldif格式有点乱,添加的时候不处理会报错 https://blog.csdn.net/weixin_41004350/article/details/89521170
1.yum安装openldap
[root@ldapserver 10:37:52 ~]# yum install -y openldap openldap-clients openldap-servers
[root@ldapserver 10:39:08 ~]# cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
[root@ldapserver 10:39:10 ~]# chown -R ldap. /var/lib/ldap/DB_CONFIG
[root@ldapserver 10:39:14 ~]# systemctl start slapd
[root@ldapserver 10:39:14 ~]#systemctl enable slapd
[root@ldapserver 10:39:20 ~]# systemctl status slapd
● slapd.service - OpenLDAP Server Daemon
Loaded: loaded (/usr/lib/systemd/system/slapd.service; disabled; vendor preset: disabled)
Active: active (running) since 三 2023-07-12 10:39:20 CST; 3s ago
2.配置密码
我这里涉及到的密码都是000000
[root@ldapserver 10:39:24 ~]# slappasswd -s 000000
{SSHA}LSgYPTUW4zjGtIVtuZ8cRUqqFRv1tWpE
最后一行使用上面生成的密码
[root@ldapserver 10:39:32 ~]# vim changepwd.ldif
dn: olcDatabase={0}config,cn=config
changetype: modify
add: olcRootPW
olcRootPW: {SSHA}LSgYPTUW4zjGtIVtuZ8cRUqqFRv1tWpE
[root@ldapserver 10:39:47 ~]# ldapadd -Y EXTERNAL -H ldapi:/// -f changepwd.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "olcDatabase={0}config,cn=config"
3.导入配置
这里可以根据需要导入,不知道需要什么都执行一遍
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/collective.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/corba.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/duaconf.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/dyngroup.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/java.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/misc.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/openldap.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/pmi.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/ppolicy.ldif
4.定义域
我这里定义的是:dc=yinhan,dc=com,可根据自己的修改,比如改成dc=test,dc=com
这里修改建议是在vim模式下批量改:%s/dc=yinhan,dc=com/dc=xxx,dc=xxxx/g
这里olcRootPW的密码使用的也是前面生成的000000加密后的密文
[root@ldapserver ~]# cat changedomain.ldif
dn: olcDatabase={1}monitor,cn=config
changetype: modify
replace: olcAccess
olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" read by dn.base="cn=admin,dc=yinhan,dc=com" read by * none
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcSuffix
olcSuffix: dc=yinhan,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootDN
olcRootDN: cn=admin,dc=yinhan,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootPW
olcRootPW: {SSHA}LSgYPTUW4zjGtIVtuZ8cRUqqFRv1tWpE
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcAccess
olcAccess: {0}to attrs=userPassword,shadowLastChange by dn="cn=admin,dc=yinhan,dc=com" write by anonymous auth by self write by * none
olcAccess: {1}to dn.base="" by * read
olcAccess: {2}to * by dn="cn=admin,dc=yinhan,dc=com" write by * read
[root@ldapserver ~]# ldapmodify -Y EXTERNAL -H ldapi:/// -f changedomain.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "olcDatabase={1}monitor,cn=config"
modifying entry "olcDatabase={2}hdb,cn=config"
modifying entry "olcDatabase={2}hdb,cn=config"
modifying entry "olcDatabase={2}hdb,cn=config"
modifying entry "olcDatabase={2}hdb,cn=config"
5.配置memberof
[root@ldapserver ~]# cat add-memberof.ldif
dn: cn=module{0},cn=config
cn: modulle{0}
objectClass: olcModuleList
objectclass: top
olcModuleload: memberof.la
olcModulePath: /usr/lib64/openldap
dn: olcOverlay={0}memberof,olcDatabase={2}hdb,cn=config
objectClass: olcConfig
objectClass: olcMemberOf
objectClass: olcOverlayConfig
objectClass: top
olcOverlay: memberof
olcMemberOfDangling: ignore
olcMemberOfRefInt: TRUE
olcMemberOfGroupOC: groupOfUniqueNames
olcMemberOfMemberAD: uniqueMember
olcMemberOfMemberOfAD: memberOf
[root@etcd-test 10:45:41 ~]# vim refint1.ldif
dn: cn=module{0},cn=config
add: olcmoduleload
olcmoduleload: refint
[root@etcd-test 10:45:53 ~]# vim refint2.ldif
dn: olcOverlay=refint,olcDatabase={2}hdb,cn=config
objectClass: olcConfig
objectClass: olcOverlayConfig
objectClass: olcRefintConfig
objectClass: top
olcOverlay: refint
olcRefintAttribute: memberof uniqueMember manager owner
[root@ldapserver ~]# ldapadd -Q -Y EXTERNAL -H ldapi:/// -f add-memberof.ldif
adding new entry "cn=module{0},cn=config"
adding new entry "olcOverlay={0}memberof,olcDatabase={2}hdb,cn=config"
[root@ldapserver ~]# echo $?
0
[root@ldapserver ~]# ldapmodify -Q -Y EXTERNAL -H ldapi:/// -f refint1.ldif
modifying entry "cn=module{0},cn=config"
[root@ldapserver ~]# ldapadd -Q -Y EXTERNAL -H ldapi:/// -f refint2.ldif
adding new entry "olcOverlay=refint,olcDatabase={2}hdb,cn=config"
6.配置base dn
[root@ldapserver ~]# cat base.ldif
dn: dc=yinhan,dc=com
objectClass: top
objectClass: dcObject
objectClass: organization
o: yinhan Company
dc: yinhan
dn: cn=admin,dc=yinhan,dc=com
objectClass: organizationalRole
cn: admin
dn: ou=People,dc=yinhan,dc=com
objectClass: organizationalUnit
ou: People
dn: ou=Group,dc=yinhan,dc=com
objectClass: organizationalRole
cn: Group
[root@ldapserver ~]# ldapadd -x -D cn=admin,dc=yinhan,dc=com -f base.ldif -w 000000
Enter LDAP Password:
adding new entry "dc=yinhan,dc=com"
adding new entry "cn=admin,dc=yinhan,dc=com"
adding new entry "ou=People,dc=yinhan,dc=com"
adding new entry "ou=Group,dc=yinhan,dc=com"
7.安装phpldapadmin管理
这里需要有epel的yum源
[root@ldapserver ~]# yum install phpldapadmin -y
8.调整httpd的配置
增加12行IP为自己的网段
[root@ldapserver ~]# cat -n /etc/httpd/conf.d/phpldapadmin.conf
1 #
2 # Web-based tool for managing LDAP servers
3 #
4
5 Alias /phpldapadmin /usr/share/phpldapadmin/htdocs
6 Alias /ldapadmin /usr/share/phpldapadmin/htdocs
7
8 <Directory /usr/share/phpldapadmin/htdocs>
9 <IfModule mod_authz_core.c>
10 # Apache 2.4
11 Require local
12 Require ip 192.168.0.0/16
13 </IfModule>
14 <IfModule !mod_authz_core.c>
15 # Apache 2.2
16 Order Deny,Allow
17 Allow from 127.0.0.1
18 Allow from ::1
19 </IfModule>
20 </Directory>
9.调整php的配置
注释掉389行 开启397行
[root@ldapserver ~]#vim /etc/phpldapadmin/config.php
397 $servers->setValue('login','attr','dn');
398 //$servers->setValue('login','attr','uid');
[root@ldapserver phpldapadmin]# systemctl restart httpd
10.登陆php管理页面
登陆地址: http://ip/ldapadmin
账号为第四步定义的:cn=admin,dc=yinhan,dc=com
密码也是前面定义的
登陆报错解决
[root@ldapserver ~]# setsebool -P httpd_can_connect_ldap on

11.同步旧ldapsever用户数据(可省略)
我这里原来有一套ldapserver已经跑了很多年了,可以通过slapcat跟slapadd把数据导入到新的server里
[root@ldapserver bak]# systemctl stop slapd
[root@ldapserver bak]# grep 'dn: uid=' user.ldif
dn: uid=test1,ou=People,dc=yinhan,dc=com
dn: uid=test2,ou=People,dc=yinhan,dc=com
[root@ldapserver bak]# slapadd -n 2 -l user.ldif
.#################### 100.00% eta none elapsed none fast!
Closing DB...
[root@ldapserver bak]# systemctl start slapd
12.客户端配置
[root@compute02_11bak]# yum install -y openldap-clients nss-pam-ldapd
[root@compute02_11:58:44_~ $ip a|grep 'inet 17'
inet 172.16.4.80/16 brd 172.16.255.255 scope global eth0
inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0
inet 172.20.0.1/16 brd 172.20.255.255 scope global br-b76db9453ac8
inet 172.23.0.1/16 brd 172.23.255.255 scope global br-f422a62a0cc9
root@compute02_11:58:55_~ $authconfig --enablemkhomedir --enableshadow --enableldap --enableldapauth --ldapserver=ldap://192.168.11.21 --ldapbasedn=dc=yinhan,dc=com --disableldaptls --enablecache --disablewinbindauth --disablesssdauth --updateall
getsebool: SELinux is disabled
getsebool: SELinux is disabled
root@compute02_11:59:03_~ $id liliangde
uid=1000(liliangde) gid=500(sa_test) 组=908(monitorUsers),917(hc_group),902(sa_group),903(dba_group),500(sa_test)
root@compute02_11:59:06_~ $id liliangde1
uid=1001(liliangde1) gid=500(sa_test) 组=500(sa_test)
root@compute02_11:59:07_~ $ssh liliangde1@172.16.4.80
liliangde1@172.16.4.80's password:
Creating directory '/data/home/liliangde1'.
Last login: Tue Jun 28 18:37:23 2022
liliangde1@compute02_11:59:35_~ $who
root pts/0 2023-08-11 11:57 (mirrors.yh.com)
liliangde1 pts/1 2023-08-11 11:59 (compute02)
13.对接jumpserver
添加一个新的组,按照红色框勾选的操作

这里需要勾选groupOfUnxxx

新组的名称我设置为 test_mem

添加完成通过命令可以通过uniqueMember查看组里面包含哪些用户
[root@ldapserver bak]# ldapsearch -LL -Y EXTERNAL -H ldapi:/// "(cn=test_mem)" -b dc=yinhan,dc=com uniqueMember
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
version: 1
dn: cn=test_mem,ou=Group,dc=yinhan,dc=com
uniqueMember: cn=liliangde,ou=People,dc=yinhan,dc=com
jumpserver上面配置

配置完导入可以看到新的组