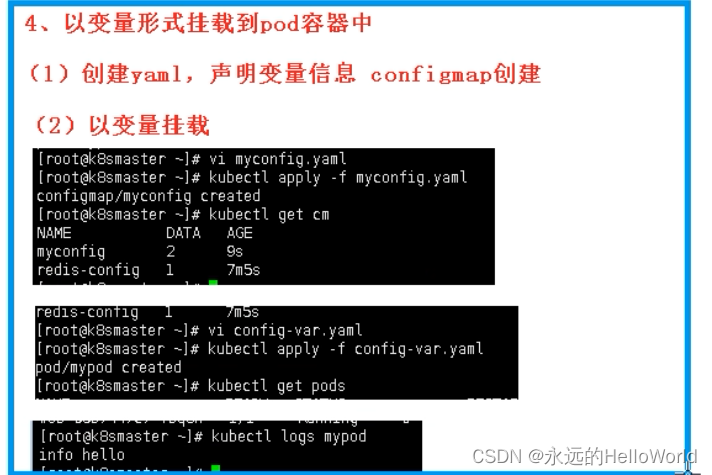
IPSec加密GRE通道
由于GRE隧道不提供安全性保障,使用ipsec加密gre隧道是现网中比较常用的VPN部署,它的加密方式分为两种:
-
可以使用IPsec来加密隧道进行传输,叫做IPsec over GRE;
-
加密数据流后从隧道传输,称为GRE over IPsec。
下面将配置一个简单的IPsec over GRE实验。

一、搭建模拟环境
首先我们先搭建环境,先根据拓扑图把基本的IP地址配好,然后分别在AR1、AR3加两条静态路由,使得两个公网互通。
[AR1]in g0/0/0
[AR1-GigabitEthernet0/0/0]ip add 192.168.1.254 24
[AR1-GigabitEthernet0/0/0]q
[AR1]in g0/0/1
[AR1-GigabitEthernet0/0/1]ip add 200.1.1.1 24
[AR1-GigabitEthernet0/0/1]q
[AR1]ip route-static 200.2.2.0 24 200.1.1.2
[AR2]in g0/0/0
[AR2-GigabitEthernet0/0/0]ip add 200.1.1.2 24
[AR2-GigabitEthernet0/0/0]q
[AR2]in g0/0/1
[AR2-GigabitEthernet0/0/1]ip add 200.2.2.2 24
[AR2-GigabitEthernet0/0/1]q
[AR3]in g0/0/0
[AR3-GigabitEthernet0/0/0]ip add 200.2.2.1 24
[AR3-GigabitEthernet0/0/0]q
[AR3]in g0/0/1
[AR3-GigabitEthernet0/0/1]ip add 192.168.2.254 24
[AR3-GigabitEthernet0/0/1]q
[AR3]ip route-static 200.1.1.0 24 200.2.2.2
验证结果:
[AR1]ping -a 200.1.1.1 200.2.2.1
PING 200.2.2.1: 56 data bytes, press CTRL_C to break
Reply from 200.2.2.1: bytes=56 Sequence=1 ttl=254 time=60 ms
Reply from 200.2.2.1: bytes=56 Sequence=2 ttl=254 time=20 ms
Reply from 200.2.2.1: bytes=56 Sequence=3 ttl=254 time=40 ms
Reply from 200.2.2.1: bytes=56 Sequence=4 ttl=254 time=10 ms
Reply from 200.2.2.1: bytes=56 Sequence=5 ttl=254 time=30 ms
--- 200.2.2.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 10/32/60 ms
二、GRE的配置
AR1
interface Tunnel0/0/0 #新建隧道
description zongbu #这个是描述,不是目标地址,需要注意
ip address 10.1.1.1 255.255.255.0 #给隧道配置地址
tunnel-protocol gre #隧道协议
source 200.1.1.1 #源地址,注意这里是公网地址
destination 200.2.2.1 #目标地址,注意这里是公网地址
AR3
interface Tunnel0/0/0
description fengongsi
ip address 10.1.1.2 255.255.255.0
tunnel-protocol gre
source 200.2.2.1
destination 200.1.1.1
两边各加1条静态路由
[AR1]ip route-static 192.168.2.0 24 Tunnel 0/0/0 #这里我们用隧道接口,也可以用隧道IP
[AR1]ip route-static 192.168.2.0 24 ? #这里除了加接口还可以直接IP
IP_ADDR<X.X.X.X> Gateway address
GigabitEthernet GigabitEthernet interface
NULL NULL interface
Tunnel Tunnel interface
vpn-instance Destination VPN-Instance for Gateway address
[AR3]ip route-static 192.168.1.0 24 Tunnel 0/0/0
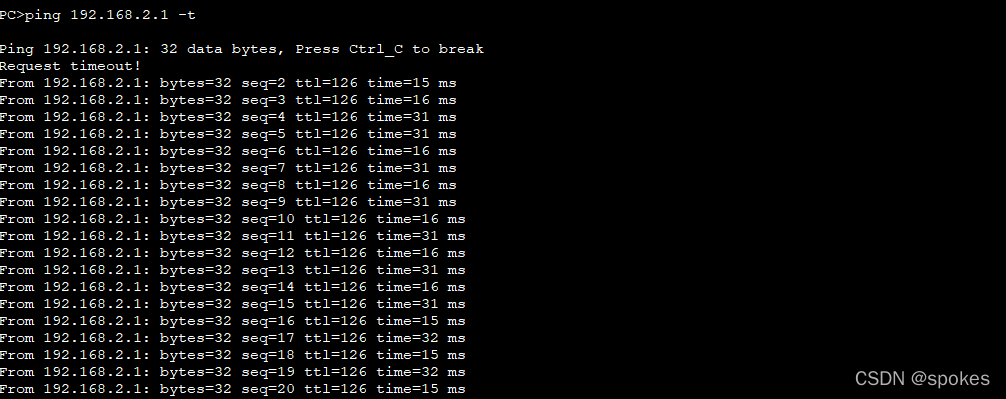
验证一下:PC1 > PC2
PC>ping 192.168.2.1
Ping 192.168.2.1: 32 data bytes, Press Ctrl_C to break
From 192.168.2.1: bytes=32 seq=1 ttl=126 time=31 ms
From 192.168.2.1: bytes=32 seq=2 ttl=126 time=16 ms
From 192.168.2.1: bytes=32 seq=3 ttl=126 time=31 ms
From 192.168.2.1: bytes=32 seq=4 ttl=126 time=15 ms
From 192.168.2.1: bytes=32 seq=5 ttl=126 time=16 ms
--- 192.168.2.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 15/21/31 ms
三、配置IPSec加密
#创建IKE提议
ike proposal 1
encryption-algorithm 3des-cbc #指定加密算法
authentication-algorithm md5 #认证算法
#配置IKE对等体
ike peer 1 v2
pre-shared-key simple 123456 #共享密钥
ike-proposal 1
#配置IPSec提议
ipsec proposal 1
esp encryption-algorithm 3des #esp的加密算法
#配置IPSec文件,其实也就是调用上面的IKE提议和IPSec提议
ipsec profile gre
ike-peer 1
proposal 1
interface Tunnel0/0/0
ipsec profile gre
interface Tunnel0/0/0
description zongbu
ip address 10.1.1.1 255.255.255.0
tunnel-protocol gre
source 200.1.1.1
destination 200.2.2.1
ipsec profile gre
####以上配置AR1、AR3完全一样
四、加密验证
我们选择下图中AR1的g0/0/1接口抓包

然后用PC1去pingPC2的抓包效果