目录
- 1. 组网需求
- 1.1 网络拓扑
- 1.2 配置思路
- 1.3 版本
- 2. 配置USG5500 A
- 2.1 基本配置
- 2.2 配置域间包过滤规则
- 2.3 配置到达分支的静态路由
- 2.4 定义被保护的数据流
- 2.5 配置名称为tran1的IPSec安全提议
- 2.6 配置序号为10的IKE安全提议
- 2.7 配置IKE Peer
- 2.8 配置IPSec安全策略组map1
- 2.9 在接口G/0/1上应用安全策略组map1
- 3. 配置USG5500 B
- 3.1 基本配置
- 3.2 配置域间包过滤规则
- 3.3 配置到达总部的静态路由
- 3.4 定义被保护的数据流
- 3.5 配置名称为tran1的IPSec安全提议
- 3.6 配置序号为10的IKE安全提议
- 3.7 配置名称为a的IKE peer
- 3.8 配置名称为map1序号为10的安全策略
- 3.9 在接口G/0/1上应用安全策略组map1
- 4. 配置USG5500 C
- 5. 查看结果
- 5.1 查看PC互通
- 5.2 抓包查看IPSec建立
- 5.3 IKE peer默认开启NAT穿越
- 5.4 查看防火墙会话
- 5.5 查看IKE sa
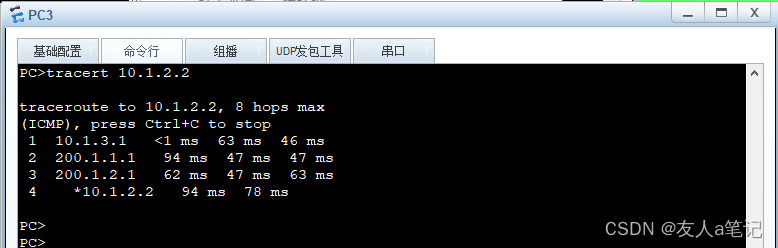
- 5.6 PC2到PC3的ping
- 5.7 PC2、PC3通过USG5500A进行安全通信
1. 组网需求
公司总部(网络A)和两个分公司(网络B、网络C)分别通过USG5500 A、USG5500 B和USG5500 C连接到Internet。USG5500 A和USG5500 B、USG5500 C路由可达。
1.1 网络拓扑
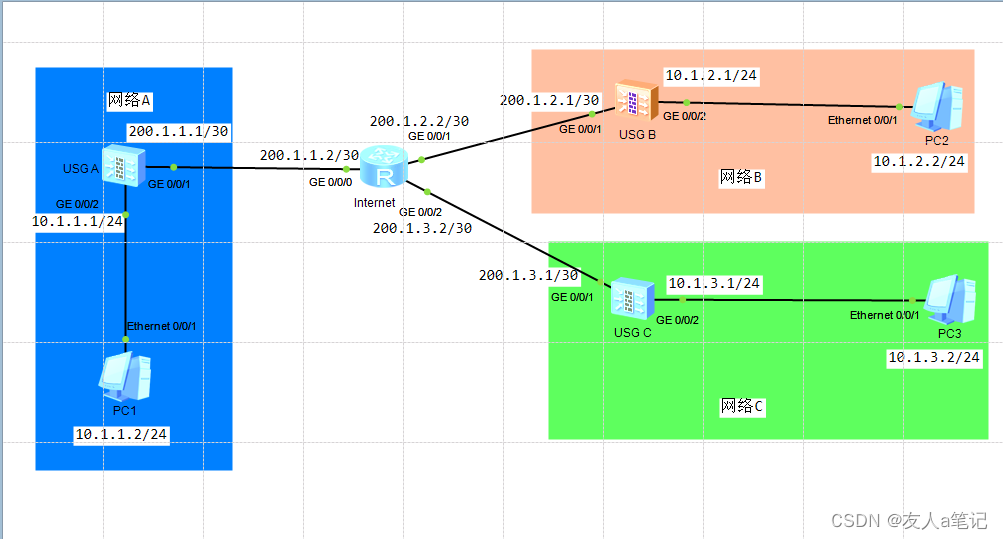
- 主机PC1与PC2、PC3之间可以安全的通信,PC2、PC3通过USG5500A进行安全通信,USG5500 A与USG5500B、USG5500C之间使用IKE自动协商建立安全通道,USG5500B、USG5500C不直接建立任何IPSec连接。
- USG5500A与USG5500B、USG5500C均为固定公网地址。
1.2 配置思路
- 基本配置,包括配置接口IP地址,将接口加入相应的安全区域。
- 配置公网路由, 一般情况下,防火墙上配置静态路由。
- 通过配置ACL规则组来定义需要保护的数据流。
- 配置包过滤。
- 配置IPSec安全提议。
- 配置IKE安全提议。
- 配置IKE Peer。
- 配置IPSec安全策略。
- 应用IPSec安全策略。
1.3 版本
模拟器:

防火墙:
路由器:
2. 配置USG5500 A
2.1 基本配置
配置接口IP地址
<USG5500A> system-view
[USG5500A] interface GigabitEthernet 0/0/2
[USG5500A-GigabitEthernet0/0/2] ip address 10.1.1.1 24
[USG5500A-GigabitEthernet0/0/2] quit
[USG5500A] interface GigabitEthernet 0/0/1
[USG5500A-GigabitEthernet0/0/1] ip address 200.1.1.1 30
[USG5500A-GigabitEthernet0/0/1] quit
配置接口加入相对应安全区域
[USG5500A] firewall zone trust
[USG5500A-zone-trust] add interface GigabitEthernet 0/0/2
[USG5500A-zone-trust] quit
[USG5500A] firewall zone untrust
[USG5500A-zone-untrust] add interface GigabitEthernet 0/0/1
[USG5500A-zone-untrust] quit
2.2 配置域间包过滤规则
打开Trust域与Untrust域的域间过滤规则
[USG5500A] policy interzone trust untrust outbound
[USG5500A-policy interzone trust untrust outbound] policy 1
[USG5500A-policy interzone trust untrust outbound-1] policy source 10.1.1.0 0.0.0.255
[USG5500A-policy interzone trust untrust outbound-1] policy destination 10.1.2.0 0.0.0.255
[USG5500A-policy interzone trust untrust outbound-1] policy destination 10.1.3.0 0.0.0.255
[USG5500A-policy interzone trust untrust outbound-1] action permit
[USG5500A-policy interzone trust untrust outbound-1] quit
[USG5500A] policy interzone trust untrust inbound
[USG5500A-policy interzone trust untrust inbound] policy 1
[USG5500A-policy interzone trust untrust inbound-1] policy source 10.1.2.0 0.0.0.255
[USG5500A-policy interzone trust untrust inbound-1] policy source 10.1.3.0 0.0.0.255
[USG5500A-policy interzone trust untrust inbound-1] policy destination 10.1.1.0 0.0.0.255
[USG5500A-policy interzone trust untrust inbound-1] action permit
[USG5500A-policy interzone trust untrust inbound-1] quit
打开Local域与Untrust域的域间过滤规则
[USG5500A] policy interzone local untrust inbound
[USG5500A-policy interzone local untrust inbound] policy 1
[USG5500A-policy interzone local untrust inbound-1] policy source 200.1.2.0 0.0.0.3
[USG5500A-policy interzone local untrust inbound-1] policy source 200.1.3.0 0.0.0.3
[USG5500A-policy interzone local untrust inbound-1] action permit
[USG5500A-policy interzone local untrust inbound-1] quit
说明:
- 配置Local域和Untrust域的域间缺省包过滤规则的目的为允许IPSec隧道两端设备通信,使其能够进行隧道协商。
2.3 配置到达分支的静态路由
[USG5500A] ip route-static 0.0.0.0 0.0.0.0 200.1.1.2
2.4 定义被保护的数据流
配置高级ACL 3000,定义总部到网络B的数据流
[USG5500A] acl 3000
[USG5500A-acl-adv-3000] rule permit ip source 10.1.0.0 0.0.255.255 destination 10.1.2.0 0.0.0.255
[USG5500A-acl-adv-3000] quit
配置高级ACL 3001,定义总部到网络C的数据流
[USG5500A] acl 3001
[USG5500A-acl-adv-3001] rule permit ip source 10.1.0.0 0.0.255.255 destination 10.1.3.0 0.0.0.255
[USG5500A-acl-adv-3001] quit
说明:
- 为了实现分支的互通,高级ACL的源地址(Source)定义为包括总部和分支的所有网段,目的地址(Destination)定义为各个分支的精确网段。
2.5 配置名称为tran1的IPSec安全提议
[USG5500A] ipsec proposal tran1
[USG5500A-ipsec-proposal-tran1] encapsulation-mode tunnel
[USG5500A-ipsec-proposal-tran1] transform esp
[USG5500A-ipsec-proposal-tran1] esp authentication-algorithm md5
[USG5500A-ipsec-proposal-tran1] esp encryption-algorithm des
[USG5500A-ipsec-proposal-tran1] quit
或者简单配置:
[USG5500A] ipsec proposal tran1
[USG5500A-ipsec-proposal-tran1] quit
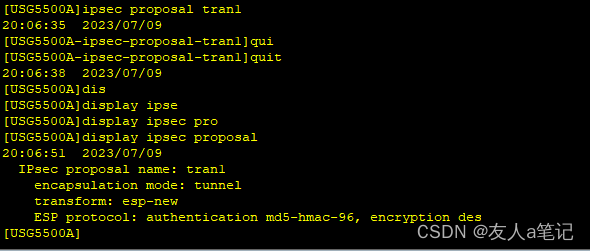
说明:
- 其中的ESP为默认的安全协议,Tunnel为默认的封装模式,可以不配置。MD5为ESP默认的认证算法,DES为ESP默认的加密算法,可以不配置。
2.6 配置序号为10的IKE安全提议
[USG5500A] ike proposal 10
[USG5500A-ike-proposal-10] authentication-method pre-share
[USG5500A-ike-proposal-10] authentication-algorithm sha1
[USG5500A-ike-proposal-10] quit
或者简单配置:
[USG5500A] ike proposal 10
[USG5500A-ike-proposal-10] quit
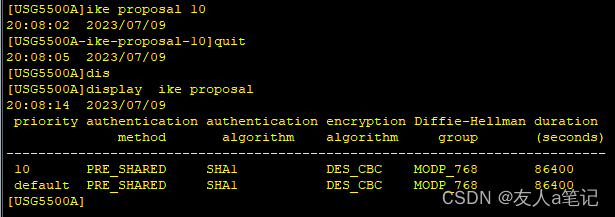
说明:
- pre-shared-key验证方法为IKE默认的验证方法,SHA1为默认验证算法,可以不配置。
2.7 配置IKE Peer
配置名称为b的IKE Peer
[USG5500A] ike peer b
[USG5500A-ike-peer-b] ike-proposal 10
[USG5500A-ike-peer-b] remote-address 200.1.2.1
[USG5500A-ike-peer-b] pre-shared-key abcde
[USG5500A-ike-peer-b] quit
配置名称为c的IKE Peer
[USG5500A] ike peer c
[USG5500A-ike-peer-b] ike-proposal 10
[USG5500A-ike-peer-b] remote-address 200.1.3.1
[USG5500A-ike-peer-b] pre-shared-key abcde
[USG5500A-ike-peer-b] quit
说明:
-
USG5500同时开启IKEv1和IKEv2,缺省情况下采用IKEv2进行协商,若对端不支持IKEv2,请禁用IKEv2,采用IKEv1进行协商。请在IKE
Peer视图下执行命令[ undo ] version { 1 | 2 }进行配置。 -
隧道对端IP地址分别为USG5500 B、USG5500 C与Internet相连的接口的IP地址。
-
验证字的配置需要与对端设备相同。
2.8 配置IPSec安全策略组map1
配置序号为10的安全策略
[USG5500A] ipsec policy map1 10 isakmp
[USG5500A-ipsec-policy-isakmp-map1-10] security acl 3000
[USG5500A-ipsec-policy-isakmp-map1-10] proposal tran1
[USG5500A-ipsec-policy-isakmp-map1-10] ike-peer b
[USG5500A-ipsec-policy-isakmp-map1-10] quit
配置序号为20的安全策略
[USG5500A] ipsec policy map1 20 isakmp
[USG5500A-ipsec-policy-isakmp-map1-20] security acl 3001
[USG5500A-ipsec-policy-isakmp-map1-20] proposal tran1
[USG5500A-ipsec-policy-isakmp-map1-20] ike-peer c
[USG5500A-ipsec-policy-isakmp-map1-20] quit
2.9 在接口G/0/1上应用安全策略组map1
[USG5500A] interface GigabitEthernet 0/0/1
[USG5500A-GigabitEthernet0/0/1] ipsec policy map1
[USG5500A-GigabitEthernet0/0/1] quit
3. 配置USG5500 B
3.1 基本配置
配置接口IP地址
<USG5500B> system-view
[USG5500B] interface GigabitEthernet 0/0/2
[USG5500B-GigabitEthernet0/0/2] ip address 10.1.2.1 24
[USG5500B-GigabitEthernet0/0/2] quit
[USG5500B] interface GigabitEthernet 0/0/1
[USG5500B-GigabitEthernet0/0/1] ip address 200.1.2.1 30
[USG5500B-GigabitEthernet0/0/1] quit
配置接口加入相对应安全区域
[USG5500B] firewall zone trust
[USG5500B-zone-trust] add interface GigabitEthernet 0/0/2
[USG5500B-zone-trust] quit
[USG5500B] firewall zone untrust
[USG5500B-zone-untrust] add interface GigabitEthernet 0/0/1
[USG5500B-zone-untrust] quit
3.2 配置域间包过滤规则
打开Trust域与Untrust域的域间过滤规则
[USG5500B] policy interzone trust untrust outbound
[USG5500B-policy interzone trust untrust outbound] policy 1
[USG5500B-policy interzone trust untrust outbound-1] policy source 10.1.2.0 0.0.0.255
[USG5500B-policy interzone trust untrust outbound-1] policy destination 10.1.0.0 0.0.255.255
[USG5500B-policy interzone trust untrust outbound-1] action permit
[USG5500B-policy interzone trust untrust outbound-1] quit
[USG5500B] policy interzone trust untrust inbound
[USG5500B-policy interzone trust untrust inbound] policy 1
[USG5500B-policy interzone trust untrust inbound-1] policy source 10.1.0.0 0.0.255.255
[USG5500B-policy interzone trust untrust inbound-1] policy destination 10.1.2.0 0.0.0.255
[USG5500B-policy interzone trust untrust inbound-1] action permit
[USG5500B-policy interzone trust untrust inbound-1] quit
打开Local域与Untrust域的域间过滤规则
[USG5500B] policy interzone local untrust inbound
[USG5500B-policy interzone local untrust inbound] policy 1
[USG5500B-policy interzone local untrust inbound-1] policy source 200.1.1.0 0.0.0.3
[USG5500B-policy interzone local untrust inbound-1] action permit
[USG5500B-policy interzone local untrust inbound-1] quit
说明:
- 配置Local域和Untrust域的域间缺省包过滤规则的目的为允许IPSec隧道两端设备通信,使其能够进行隧道协商。
3.3 配置到达总部的静态路由
[USG5500B] ip route-static 0.0.0.0 0.0.0.0 200.1.2.2
3.4 定义被保护的数据流
配置高级ACL 3000,定义总部到网络B的数据流
[USG5500B] acl 3000
[USG5500B-acl-adv-3000] rule permit ip source 10.1.2.0 0.0.0.255 destination 10.1.0.0 0.0.255.255
[USG5500B-acl-adv-3000] quit
说明:
- 为了实现和总部及分支的通信,Source定义为分支节点的精确网段,Destination定义为总部和分支的所有网段。
3.5 配置名称为tran1的IPSec安全提议
[USG5300B] ipsec proposal tran1
[USG5300B-ipsec-proposal-tran1] encapsulation-mode tunnel
[USG5300B-ipsec-proposal-tran1] transform esp
[USG5300B-ipsec-proposal-tran1] esp authentication-algorithm md5
[USG5300B-ipsec-proposal-tran1] esp encryption-algorithm des
[USG5300B-ipsec-proposal-tran1] quit
3.6 配置序号为10的IKE安全提议
[USG5300B] ike proposal 10
[USG5300B-ike-proposal-10] authentication-method pre-share
[USG5300B-ike-proposal-10] authentication-algorithm sha1
[USG5300B-ike-proposal-10] quit
3.7 配置名称为a的IKE peer
[USG5300B] ike peer a
[USG5300B-ike-peer-a] ike-proposal 10
[USG5300B-ike-peer-a] remote-address 200.1.1.1
[USG5300B-ike-peer-a] pre-shared-key abcde
[USG5300B-ike-peer-a] quit
3.8 配置名称为map1序号为10的安全策略
[USG5300B] ipsec policy map1 10 isakmp
[USG5300B-ipsec-policy-isakmp-map1-10] security acl 3000
[USG5300B-ipsec-policy-isakmp-map1-10] proposal tran1
[USG5300B-ipsec-policy-isakmp-map1-10] ike-peer a
[USG5300B-ipsec-policy-isakmp-map1-10] quit
3.9 在接口G/0/1上应用安全策略组map1
[USG5300B] interface GigabitEthernet 0/0/1
[USG5300B-GigabitEthernet0/0/1] ipsec policy map1
[USG5300B-GigabitEthernet0/0/1] quit
4. 配置USG5500 C
USG5500 C的配置参考USG5500B的配置
5. 查看结果
5.1 查看PC互通
PC1 ping PC2
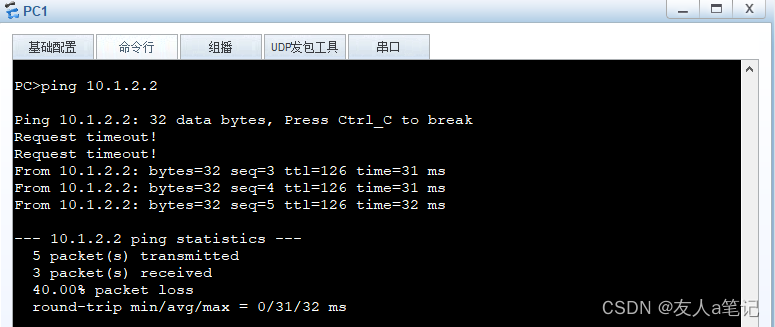
PC1 ping PC3
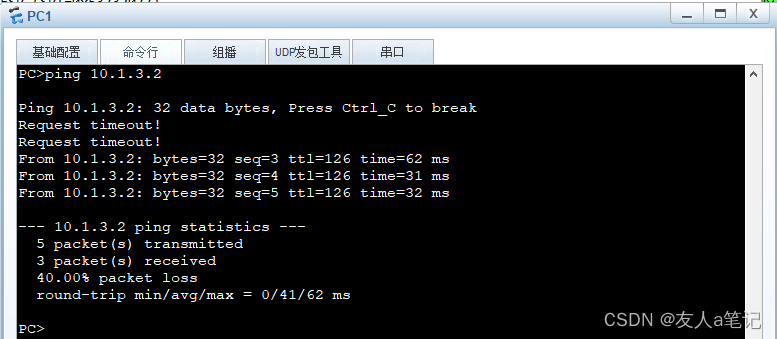
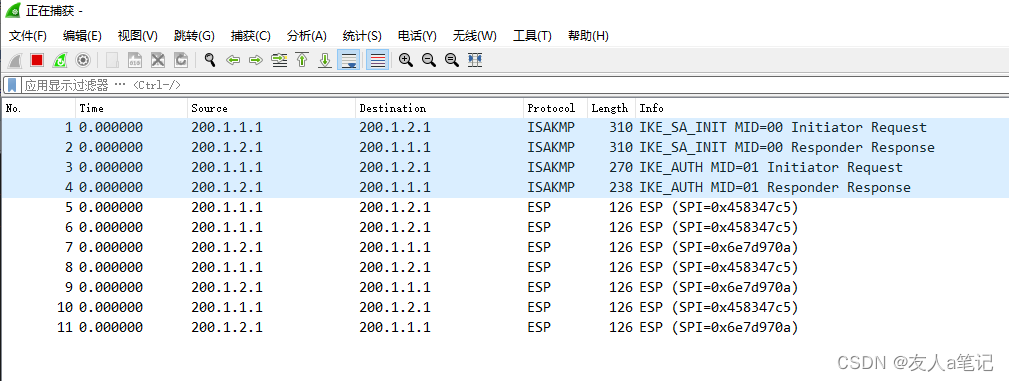
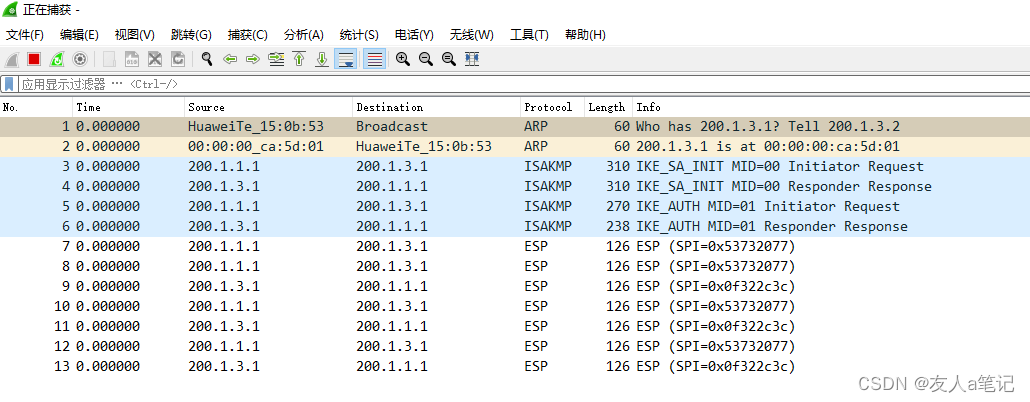
5.2 抓包查看IPSec建立
PC1 ping PC2 抓包过程,数据是通过ESP协议加密
PC1 ping PC3 抓包过程,数据是通过ESP协议加密
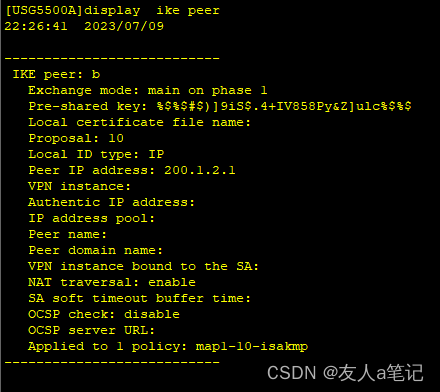
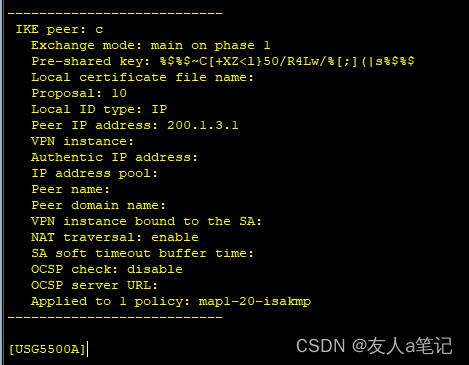
5.3 IKE peer默认开启NAT穿越
不需要额外配置NAT策略,ike peer默认NAT traversal
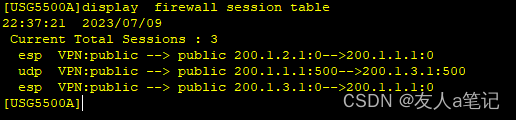
5.4 查看防火墙会话
PC1 ping PC2
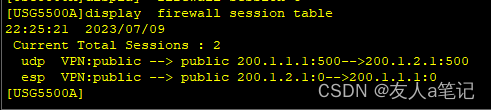
PC1 ping PC3
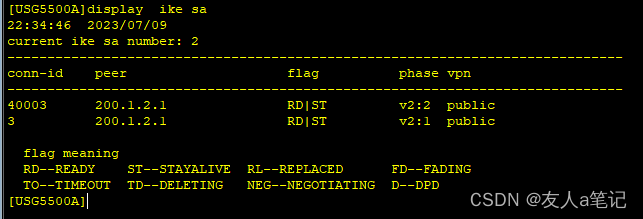
5.5 查看IKE sa
PC1 ping PC2
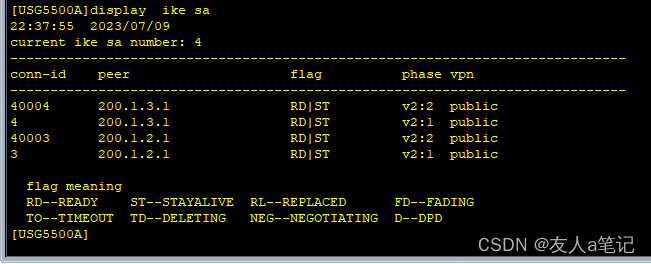
PC1 ping PC3 增加
5.6 PC2到PC3的ping
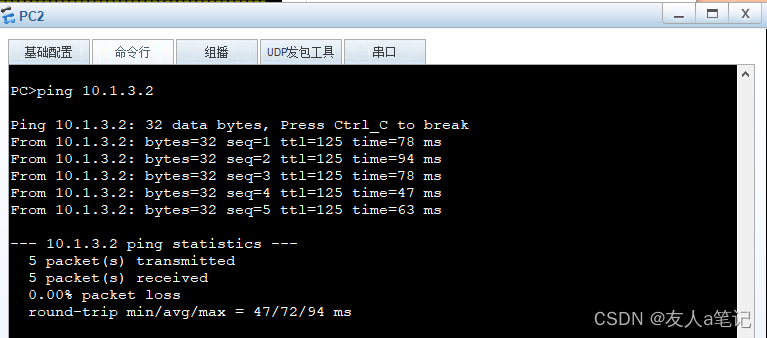
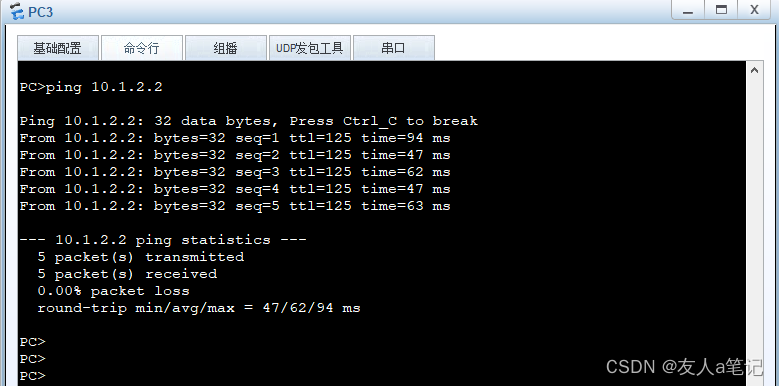
5.7 PC2、PC3通过USG5500A进行安全通信
路径:PC2 > USG550B > USG5500A > USG550C >PC3
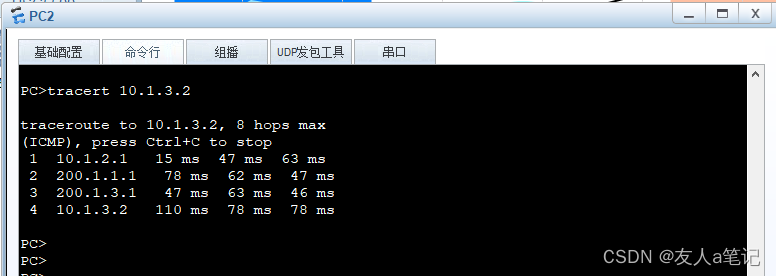
路径:PC3 > USG550C > USG5500A > USG550B >PC2