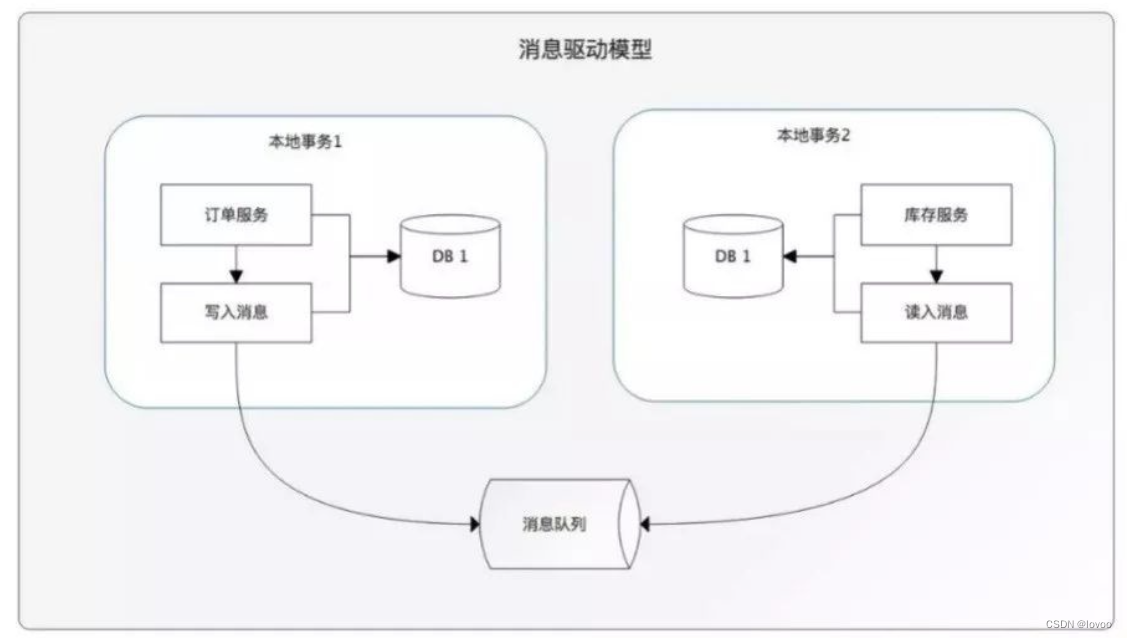
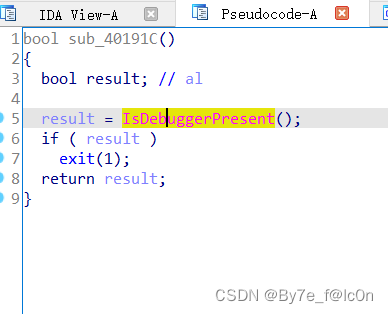
Patch掉反调试
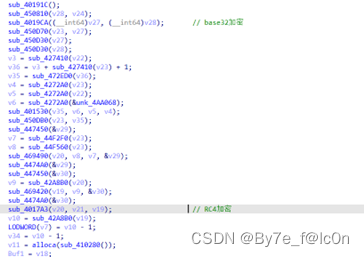
先进行了Base32解密,之后是RC4加密
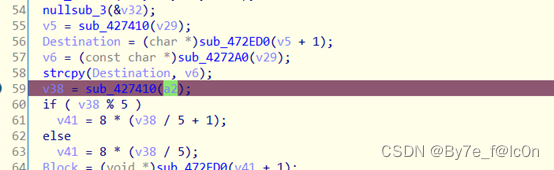
Base32编码表是RC4加密后存储的,动调得到
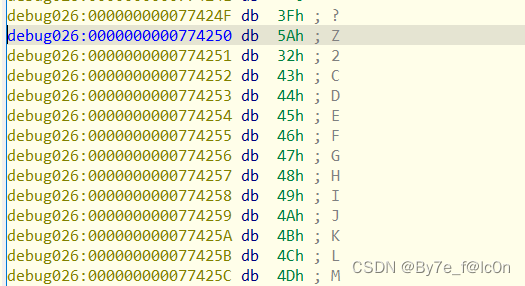
动调可以看出,经过base32编码密文会在首部添加M7WGC76B
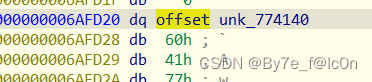
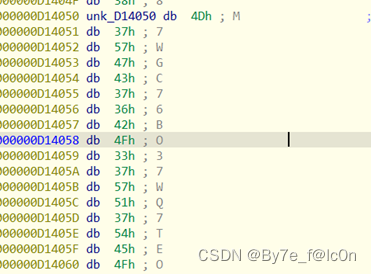
之后密文进行RC4加密
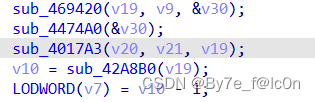
动调得到第二处RC4加密的密钥
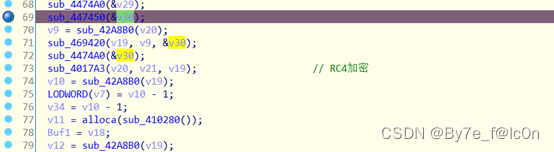
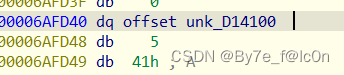
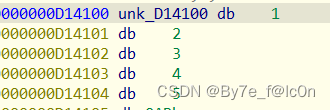
解密过程
def rc4(data, key):
S = list(range(256))
j = 0
out = []
# Key-Scheduling Algorithm
for i in range(256):
j = (j + S[i] + key[i % len(key)]) % 256
S[i], S[j] = S[j], S[i]
# Pseudo-Random Generation Algorithm
i = j = 0
for char in data:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
out.append(char ^ S[(S[i] + S[j]) % 256])
return bytes(out)
data = bytes([0xff, 0x0e, 0x34, 0x42, 0xb3, 0x0a, 0xf6, 0x65, 0x87, 0x8a, 0x65, 0x1c, 0x4b, 0x5c, 0x54, 0xfc, 0x25, 0xb1, 0xc1, 0x18, 0x2c, 0xcf, 0xc6, 0x93, 0xc6, 0x8e, 0x50, 0xfc, 0x3d, 0x3e, 0x4d, 0x53, 0xf8, 0xb8, 0x2c, 0x93, 0xb0, 0x28, 0xe5, 0x1f])
key = bytes([0x01, 0x02, 0x03, 0x04, 0x05])
decrypted = rc4(data, key)
string = decrypted.decode('utf-8')
encoded = string[7:]
print(encoded)
import base64
# 自定义 base32 编码表
base32_table = b"Z2CDEFGHIJKLMNOPQRSTUVWXY76543AB"
def decode_base32(text):
return base64.b32decode(
bytes(text.translate(bytes.maketrans(base32_table, b"ABCDEFGHIJKLMNOPQRSTUVWXYZ234567")), 'utf-8')).decode(
'utf-8')
encoded="KI7VAMLTL3UW43DFOJSXG3DJN7TQ===="
decrypted_text = decode_base32(encoded)
print("flag{"+decrypted_text+"}")