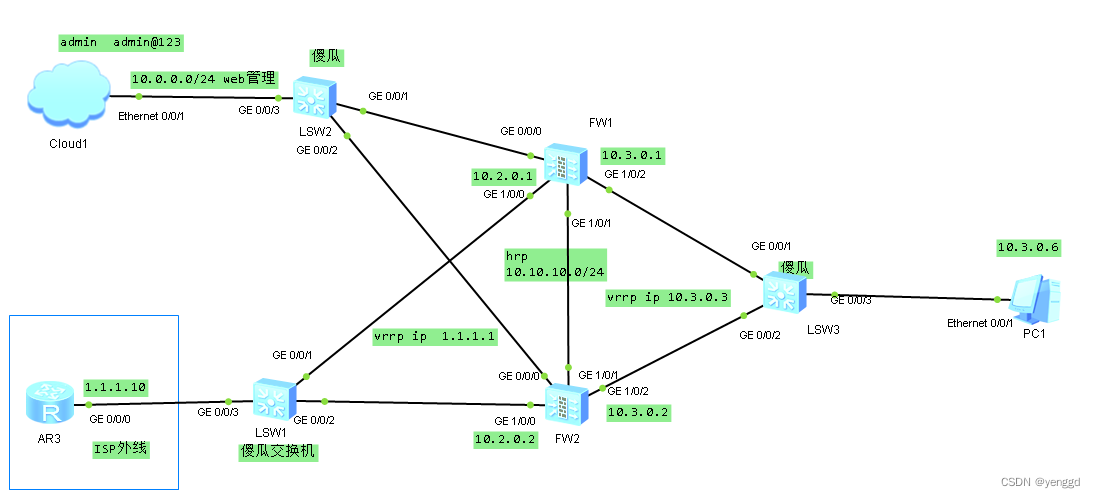
主防火墙FW1:
HRP_Mdis current-configuration
2023-06-02 15:51:48.270 +08:00
!Software Version V500R005C10SPC300
sysname USG6000V1
l2tp domain suffix-separator @
undo info-center enable
ipsec sha2 compatible enable
undo telnet server enable
undo telnet ipv6 server enable
clock timezone Beijing add 08:00:00
hrp enable
hrp interface GigabitEthernet1/0/1 remote 10.10.10.2
hrp auto-sync config static-route
update schedule location-sdb weekly Sun 06:23
firewall defend action discard
banner enable
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
firewall dataplane to manageplane application-apperceive default-action drop
undo ips log merge enable
decoding uri-cache disable
update schedule ips-sdb daily 03:25
update schedule av-sdb daily 03:25
update schedule sa-sdb daily 03:25
update schedule cnc daily 03:25
update schedule file-reputation daily 03:25
ip vpn-instance default
ipv4-family
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%8F-~%Vzyf8|!9{#yY^S=V-iK_qrjP|_TCJ)@c2G{|]7"-iNV@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%.2py+nH=|Ca]fN,2\49A/IPR^o97@QlGu@'Q7[+7o3eMIPU/@%@%
level 15
manager-user admin
password cipher @%@%ff~*28sVO7O,(dS)gf;Y.v==5E=%)DA21UV&CzRHL,:.v=@.@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
l2tp-group default-lns
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 10.0.0.6 255.255.255.0
alias GE0/METH
service-manage https permit
service-manage ping permit
interface GigabitEthernet1/0/0
undo shutdown
ip address 10.2.0.1 255.255.255.0
vrrp vrid 1 virtual-ip 1.1.1.1 255.255.255.0 active
service-manage ping permit
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.10.10.1 255.255.255.0
interface GigabitEthernet1/0/2
undo shutdown
ip address 10.3.0.1 255.255.255.0
vrrp vrid 2 virtual-ip 10.3.0.3 active
service-manage ping permit
interface GigabitEthernet1/0/3
undo shutdown
interface GigabitEthernet1/0/4
undo shutdown
interface GigabitEthernet1/0/5
undo shutdown
interface GigabitEthernet1/0/6
undo shutdown
interface Virtual-if0
interface NULL0
firewall zone local
set priority 100
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/2
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/1
ip route-static 0.0.0.0 0.0.0.0 1.1.1.10
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
firewall detect ftp
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
pki realm default
sa
location
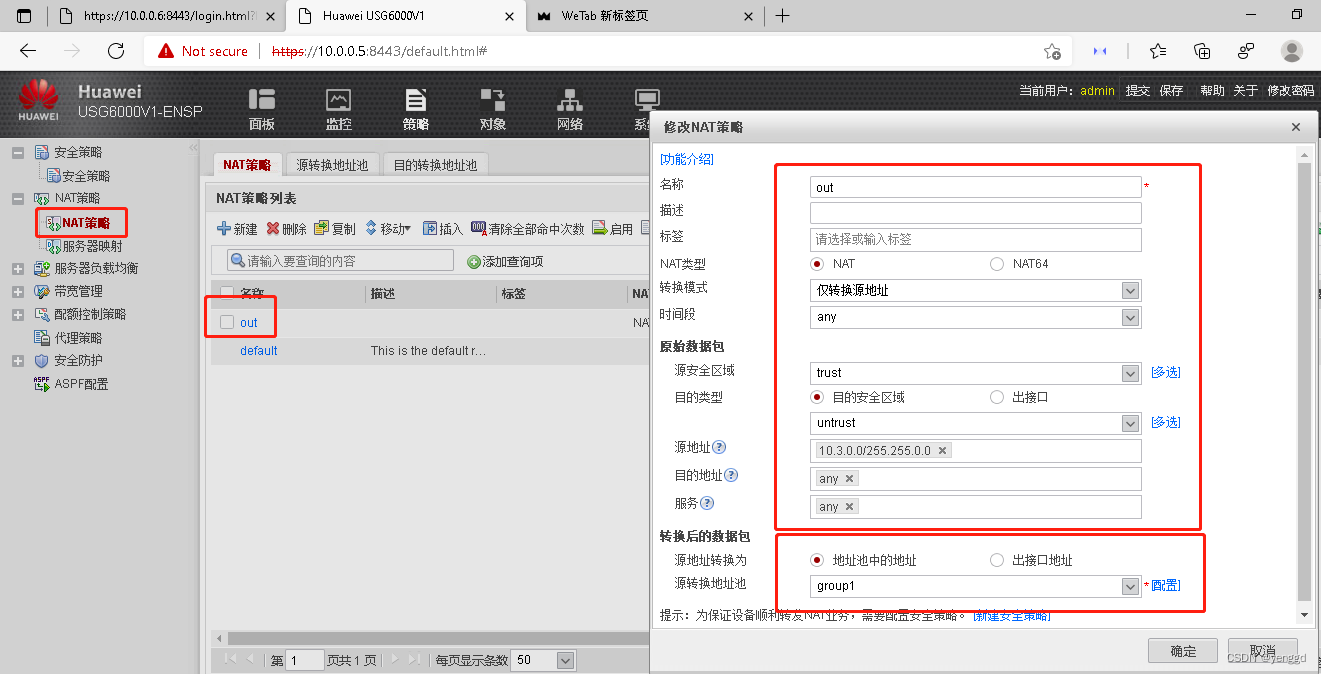
nat address-group group1 0 //这种vrrp虚拟ip和接口ip不在同个广播域必须要用这种nat池
mode pat
section 0 1.1.1.1
multi-linkif
mode proportion-of-weight
right-manager server-group
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
user-manage server-sync tsm
security-policy
default action permit
rule name dmz_local
rule name trust_to_untrust
source-zone trust
destination-zone untrust
source-address 10.3.0.0 mask 255.255.255.0
action permit
auth-policy
traffic-policy
policy-based-route
nat-policy
rule name out
source-zone trust
destination-zone untrust
source-address 10.3.0.0 mask 255.255.0.0
action source-nat address-group group1
quota-policy
pcp-policy
dns-transparent-policy
rightm-policy
备设备FW2:
HRP_S[USG6000V1]dis current-configuration
2023-06-02 15:57:33.210 +08:00
!Software Version V500R005C10SPC300
sysname USG6000V1
l2tp domain suffix-separator @
ipsec sha2 compatible enable
undo telnet server enable
undo telnet ipv6 server enable
clock timezone Beijing add 08:00:00
hrp enable
hrp interface GigabitEthernet1/0/1 remote 10.10.10.1
hrp auto-sync config static-route
update schedule location-sdb weekly Sun 01:28
firewall defend action discard
banner enable
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
firewall dataplane to manageplane application-apperceive default-action drop
undo ips log merge enable
decoding uri-cache disable
update schedule ips-sdb daily 03:25
update schedule av-sdb daily 03:25
update schedule sa-sdb daily 03:25
update schedule cnc daily 03:25
update schedule file-reputation daily 03:25
ip vpn-instance default
ipv4-family
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%8F-~%Vzyf8|!9{#yY^S=V-iK_qrjP|_TCJ)@c2G{|]7"-iNV@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%.2py+nH=|Ca]fN,2\49A/IPR^o97@QlGu@'Q7[+7o3eMIPU/@%@%
level 15
manager-user admin
password cipher @%@%ff~*28sVO7O,(dS)gf;Y.v==5E=%)DA21UV&CzRHL,:.v=@.@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
l2tp-group default-lns
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 10.0.0.5 255.255.255.0
alias GE0/METH
service-manage https permit
service-manage ping permit
interface GigabitEthernet1/0/0
undo shutdown
ip address 10.2.0.2 255.255.255.0
vrrp vrid 1 virtual-ip 1.1.1.1 255.255.255.0 standby
service-manage ping permit
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.10.10.2 255.255.255.0
service-manage ping permit
interface GigabitEthernet1/0/2
undo shutdown
ip address 10.3.0.2 255.255.255.0
vrrp vrid 2 virtual-ip 10.3.0.3 standby
service-manage ping permit
interface GigabitEthernet1/0/3
undo shutdown
interface GigabitEthernet1/0/4
undo shutdown
interface GigabitEthernet1/0/5
undo shutdown
interface GigabitEthernet1/0/6
undo shutdown
interface Virtual-if0
interface NULL0
firewall zone local
set priority 100
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/2
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/1
ip route-static 0.0.0.0 0.0.0.0 1.1.1.10
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
firewall detect ftp
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
pki realm default
sa
location
nat address-group group1 0 //两边主备上面必须都得有这个地址,并且相同
mode pat
section 0 1.1.1.1
multi-linkif
mode proportion-of-weight
right-manager server-group
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
user-manage server-sync tsm
security-policy
default action permit
rule name dmz_local
rule name trust_to_untrust
source-zone trust
destination-zone untrust
source-address 10.3.0.0 mask 255.255.255.0
action permit
auth-policy
traffic-policy
policy-based-route
nat-policy
rule name out
source-zone trust
destination-zone untrust
source-address 10.3.0.0 mask 255.255.0.0
action source-nat address-group group1
quota-policy
pcp-policy
dns-transparent-policy
rightm-policy
return
两边都要有这个地址池,不然主挂了,备上面没有这个池子,上不了网