网址
aHR0cHM6Ly93d3cucWNjLmNvbS93ZWIvZWxpYi90ZWNsaXN0P3RlYz1UX1RTTUVT
抓包
GET /api/elib/getTecList?countyCode=110101&flag=&industry=&isSortAsc=&pageIndex=2&pageSize=20&province=BJ®istCapiBegin=®istCapiEnd=&searchKey=&startDateBegin=&startDateEnd=&tec=T_TSMES HTTP/1.1
Host: www.****.com
44a6e75f36fde6af26fa: 1c6eafaaad172ac178afff475b3a08b6c4d4050b125285fefa7cd8b971a40611ad8abbf71c50446ce58cbfda3a66d0c3aab0f00ee87e4aebe69c6d1ce13f199d
authority: www.****.com
accept: application/json, text/plain, */*
accept-language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
cache-control: no-cache
cookie: **********
pragma: no-cache
referer: https://www.****.com/web/elib/teclist?tec=T_TSMES
sec-ch-ua: "Microsoft Edge";v="113", "Chromium";v="113", "Not-A.Brand";v="24"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
sec-fetch-dest: empty
sec-fetch-mode: cors
sec-fetch-site: same-origin
user-agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36 Edg/113.0.1774.50
x-pid: **********
x-requested-with: XMLHttpRequest
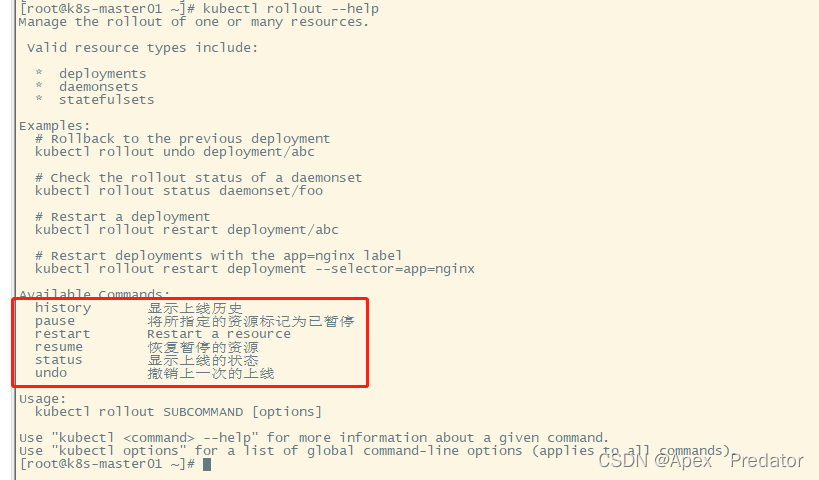
加密参数查找以及位置确定
可以看到header里边有一个加密参数 44 a 6 e 75 f 36 f d e 6 a f 26 f a \color{red}{44a6e75f36fde6af26fa} 44a6e75f36fde6af26fa,而且这个参数是变动的,包括key和value都会根据请求的不同而改变, x − p i d \color{blue}{x-pid} x−pid这个参数登录后是不会改变的,还有就是cookie,自行登录复制;
全局搜索header
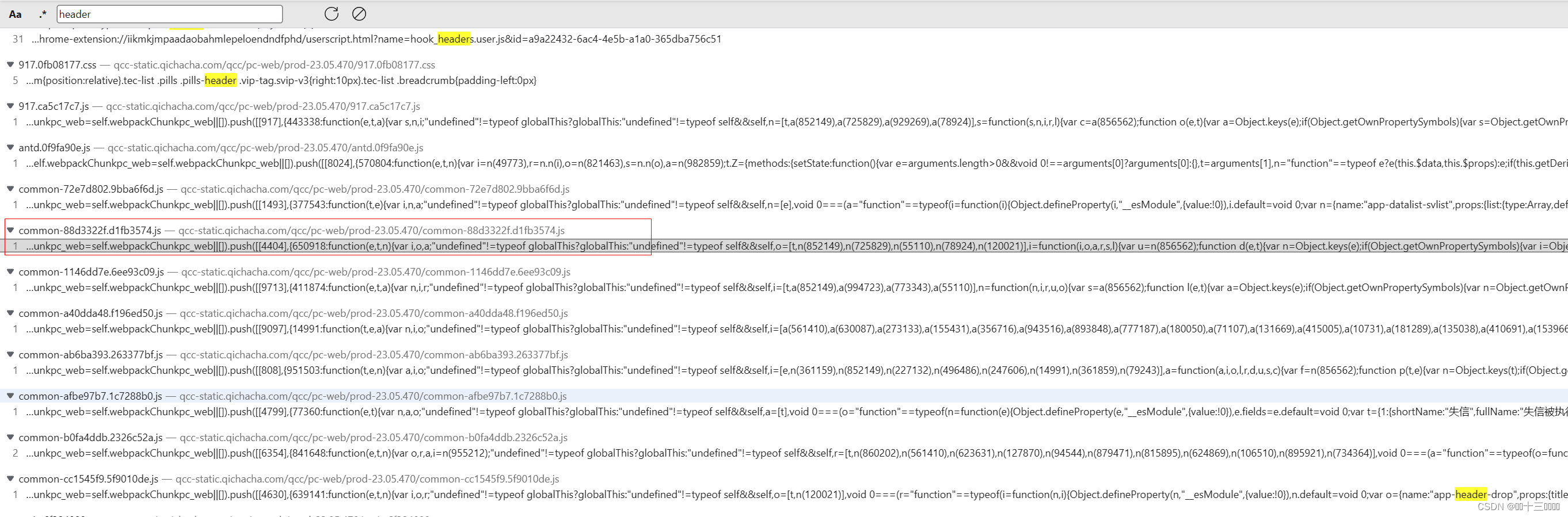
此处我直接贴答案了,有兴趣的同学可以一个一个挨个看看,标记的文件就是我们此处需要的参数的加密位置
点进去打上断点
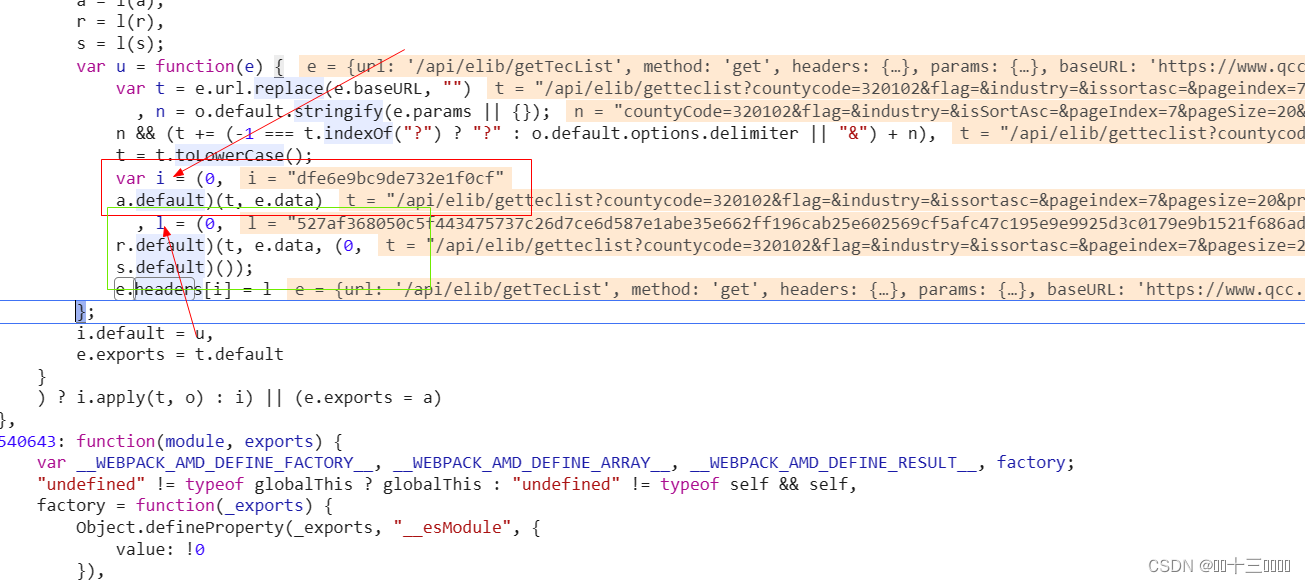
可以看到 i 和 l 就是我们需要的参数,那么我们只需要找到
a
.
d
e
f
a
u
l
t
\color{red}{a.default}
a.default 、
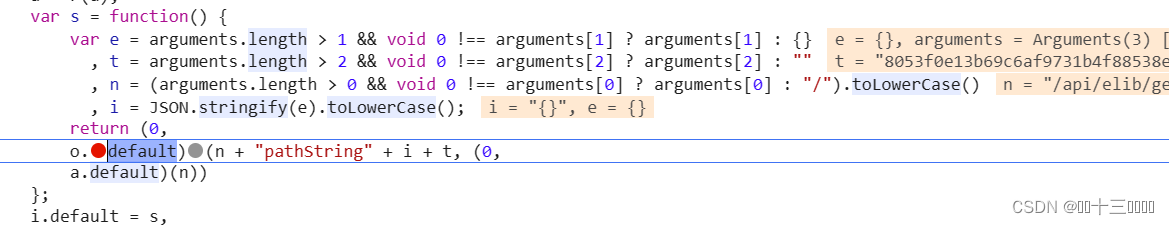
r . d e f a u l t \color{red}{r.default} r.default 、 e . d e f a u l t \color{red}{e.default} e.default的值
a.default
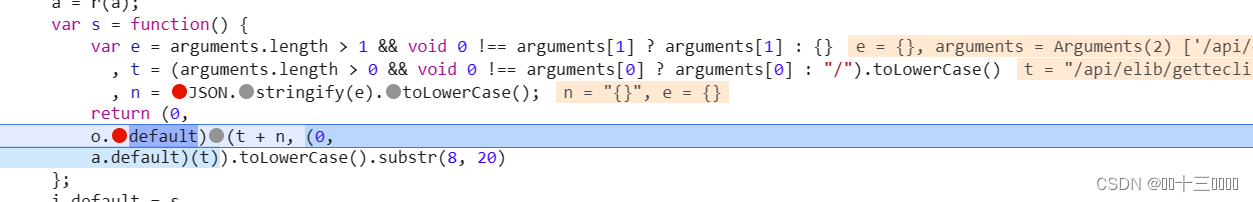
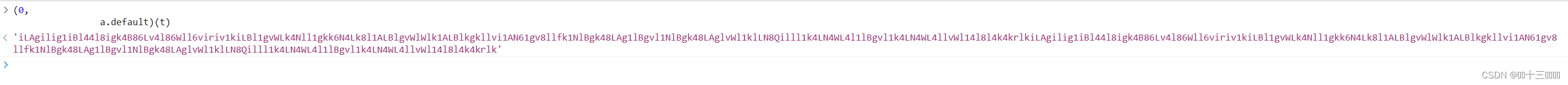
此处是我们上面拿到的

最后进行了hash加密
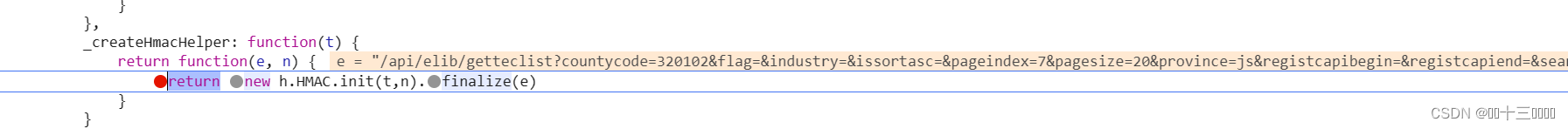
这是我们可以看到固定的key值
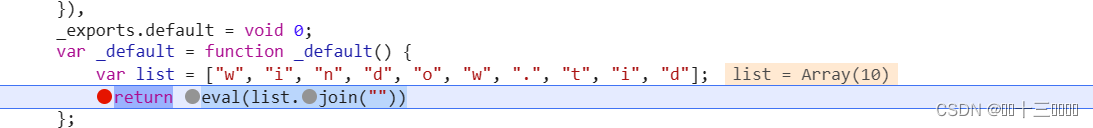
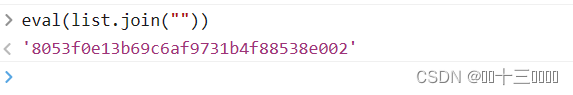
此处是字典键值返回的加密的地方,其他的逻辑和上述差不多
python翻译的代码
# -*- coding: utf-8 -*-
# @Author : yueyue
# @Time : 2023-05-26 16:40
import hashlib
import hmac
import json
def seeds_generator(s):
seeds = {
"0": "W",
"1": "l",
"2": "k",
"3": "B",
"4": "Q",
"5": "g",
"6": "f",
"7": "i",
"8": "i",
"9": "r",
"10": "v",
"11": "6",
"12": "A",
"13": "K",
"14": "N",
"15": "k",
"16": "4",
"17": "L",
"18": "1",
"19": "8"
}
seeds_n = 20
if not s:
s = "/"
s = s.lower()
s = s + s
res = ''
for i in s:
res += seeds[str(ord(i) % seeds_n)]
return res
def header_twenty(key: str = '', url: str = '', data: str = '', tid: str = ''):
msg_ad = url.lower() + data
print(msg_ad)
a_default = hmac.new(bytes(key, encoding='utf-8'), bytes(msg_ad, encoding='utf-8'), hashlib.sha512).hexdigest()
msg_rd = url.lower() + 'pathString' + data + tid
print(msg_rd)
r_default = hmac.new(bytes(key, encoding='utf-8'), bytes(msg_rd, encoding='utf-8'), hashlib.sha512).hexdigest()
return {a_default.lower()[8:28]: r_default.lower()}
if __name__ == '__main__':
url = '此处是url'
data = '{}'
tid = '此处是生成的那个key值'
print(header_twenty(key=seeds_generator(url), url=url, data=data, tid=tid))
结尾
逆向之路漫漫,以上是一个简单的例子,如果有侵权请联系我删除
各位巨巨点点赞,谢谢